Detailed Report on DDoS Attacks: Operation, Stages, and Case Analysis
VerifiedAdded on 2023/06/07
|13
|2230
|463
Report
AI Summary
This report provides a comprehensive analysis of Distributed Denial of Service (DDoS) attacks, detailing their operation and various stages, including disabling computer parts, configuration information, and physical networking aspects. It examines a real-world example involving an attack allegedly launched against Swim Australia following a controversy involving Olympic athletes. The report discusses the outcome, impact (financial and device-related), and consequences of the attack, highlighting the violation of cyber security laws. It also covers the actions taken by Swim Australia to address the problem, including government investigation and involvement of AusCert. The report concludes with recommendations for companies to use proper anti-virus software and highlights the importance of cyber security in preventing such attacks.

Running head: COMPUTER SECURITY
COMPUTER SECURITY
COMPUTER SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER SECURITY
1
Executive Summary
This research sheds light on the distributed denial of service attack (DDoS) that happens at the
time when several systems flood the bandwidth of a targeted system. The use of this attack
mainly intends to slow down servers. According to the analysis it has been suggested that this
attack mainly commenced over a large group of computers. In this case, the attackers mainly use
a zombie network that are group of virus infected computers on which DOS attacking installed
silently. Vulnerability of such attacks is effective as infected machine gets completely
unprotected to the attackers. Necessary information is generally stole or accessed from the
storage.
1
Executive Summary
This research sheds light on the distributed denial of service attack (DDoS) that happens at the
time when several systems flood the bandwidth of a targeted system. The use of this attack
mainly intends to slow down servers. According to the analysis it has been suggested that this
attack mainly commenced over a large group of computers. In this case, the attackers mainly use
a zombie network that are group of virus infected computers on which DOS attacking installed
silently. Vulnerability of such attacks is effective as infected machine gets completely
unprotected to the attackers. Necessary information is generally stole or accessed from the
storage.

COMPUTER SECURITY
2
Table of Contents
Introduction......................................................................................................................................4
1. Distributed Denial of Service operation and representation of its various stages.......................4
Stages of Dos attack are as follows.................................................................................................5
2. Selecting the type of attack and analysis of following questions................................................8
Conclusion and recommendation..................................................................................................10
Reference list.................................................................................................................................11
2
Table of Contents
Introduction......................................................................................................................................4
1. Distributed Denial of Service operation and representation of its various stages.......................4
Stages of Dos attack are as follows.................................................................................................5
2. Selecting the type of attack and analysis of following questions................................................8
Conclusion and recommendation..................................................................................................10
Reference list.................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER SECURITY
3
Introduction
The term cyber security refers to the process of protecting the various internet connected systems
and computer peripherals like software’s, hardware’s and various amount of data that is under
the threat of cyber attacks. In this study, the attack system of Denial of Service (DDoS) has been
selected. Hence, the entire procedure of attack along with specific example has been elaborated
in order to conduct the study in an appropriate manner.
The problem statement of study is to identify specific attack system of DDoS and effective
recommendation has been mentioned.
1. Distributed Denial of Service operation and representation of its various
stages
The term denial of service attack refers that cyber attack that makes the user’s machine and
network inaccessible. The dos attack fills the network with unwanted traffic and sending a
information which helps the system to crash totally. As mentioned by Yu, Tian, Guo, & Wu.
(2014), the users that are affected by dos attack are unable to use the internet services properly.
There are various types of dos attacks that can be used against the targeted users, they are as
follows.
3
Introduction
The term cyber security refers to the process of protecting the various internet connected systems
and computer peripherals like software’s, hardware’s and various amount of data that is under
the threat of cyber attacks. In this study, the attack system of Denial of Service (DDoS) has been
selected. Hence, the entire procedure of attack along with specific example has been elaborated
in order to conduct the study in an appropriate manner.
The problem statement of study is to identify specific attack system of DDoS and effective
recommendation has been mentioned.
1. Distributed Denial of Service operation and representation of its various
stages
The term denial of service attack refers that cyber attack that makes the user’s machine and
network inaccessible. The dos attack fills the network with unwanted traffic and sending a
information which helps the system to crash totally. As mentioned by Yu, Tian, Guo, & Wu.
(2014), the users that are affected by dos attack are unable to use the internet services properly.
There are various types of dos attacks that can be used against the targeted users, they are as
follows.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COMPUTER SECURITY
4
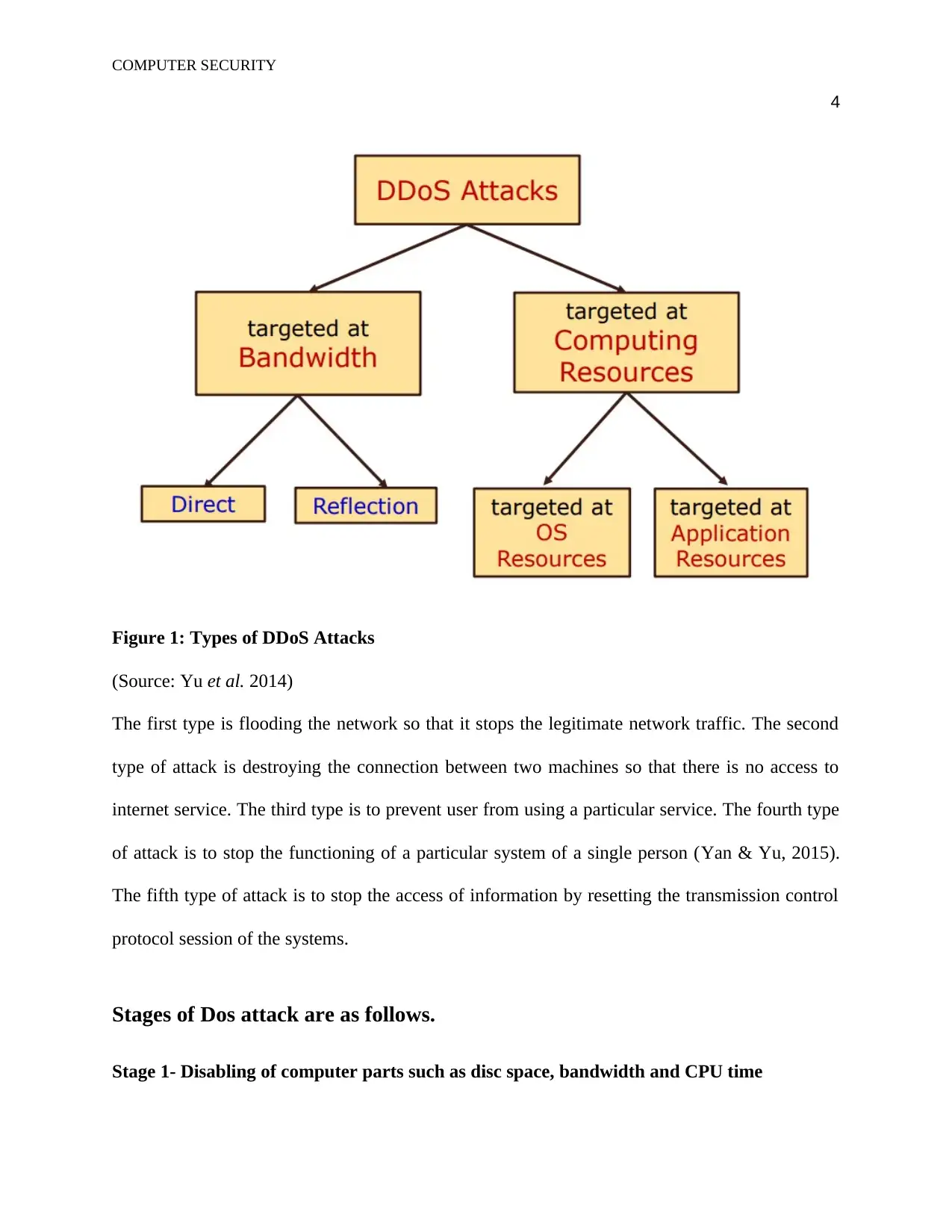
Figure 1: Types of DDoS Attacks
(Source: Yu et al. 2014)
The first type is flooding the network so that it stops the legitimate network traffic. The second
type of attack is destroying the connection between two machines so that there is no access to
internet service. The third type is to prevent user from using a particular service. The fourth type
of attack is to stop the functioning of a particular system of a single person (Yan & Yu, 2015).
The fifth type of attack is to stop the access of information by resetting the transmission control
protocol session of the systems.
Stages of Dos attack are as follows.
Stage 1- Disabling of computer parts such as disc space, bandwidth and CPU time
4
Figure 1: Types of DDoS Attacks
(Source: Yu et al. 2014)
The first type is flooding the network so that it stops the legitimate network traffic. The second
type of attack is destroying the connection between two machines so that there is no access to
internet service. The third type is to prevent user from using a particular service. The fourth type
of attack is to stop the functioning of a particular system of a single person (Yan & Yu, 2015).
The fifth type of attack is to stop the access of information by resetting the transmission control
protocol session of the systems.
Stages of Dos attack are as follows.
Stage 1- Disabling of computer parts such as disc space, bandwidth and CPU time
COMPUTER SECURITY
5
The first stage of the attack is the stage where the hacker disables the various computer parts
such as the disc space of the computer. According to Wang, Zheng, Lou, & Hou (2015), then the
attacker disables the main Central Processing Unit so that it takes a huge amount of time to
repair the problem and then he can get sufficient amount of time to launch the virus. Then the
attacker floods the entire bandwidth with spam emails and viruses.
Figure 2: Targeting bandwidth
(Source: Wang et al. 2015)
Stage 2- Disabling the configuration information and routing information
In this stage the hacker starts to stop the configuration information and routing information of the
server that he has decided to penetrate. Once this stage is complete not all the computers linked
to the server can access the internet and various websites that they access everyday (Singn &
Gupta, 2016). The hacker is doing this in order to get his revenge or to get money from the
organisation.
5
The first stage of the attack is the stage where the hacker disables the various computer parts
such as the disc space of the computer. According to Wang, Zheng, Lou, & Hou (2015), then the
attacker disables the main Central Processing Unit so that it takes a huge amount of time to
repair the problem and then he can get sufficient amount of time to launch the virus. Then the
attacker floods the entire bandwidth with spam emails and viruses.
Figure 2: Targeting bandwidth
(Source: Wang et al. 2015)
Stage 2- Disabling the configuration information and routing information
In this stage the hacker starts to stop the configuration information and routing information of the
server that he has decided to penetrate. Once this stage is complete not all the computers linked
to the server can access the internet and various websites that they access everyday (Singn &
Gupta, 2016). The hacker is doing this in order to get his revenge or to get money from the
organisation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
COMPUTER SECURITY
6
Figure 3: Reaction of attack
(Source: Singn & Gupta, 2016)
Stage 3- Disabling the physical aspects of the networking components
In this stage the hacker starts to stop the various networking aspects related the user’s computer
such as creating slow networking speed (where the files and websites take longer time to access).
Then the hacker disables any particular website that the user is going to use. As asserted by Modi
& Quadir (2014), in this process the user cannot get legal access to the websites. At the end of
this stage huge amount of spam mail is received by the user which disables or crashes the entire
networking system.
Figure 4: Online attacking procedure
6
Figure 3: Reaction of attack
(Source: Singn & Gupta, 2016)
Stage 3- Disabling the physical aspects of the networking components
In this stage the hacker starts to stop the various networking aspects related the user’s computer
such as creating slow networking speed (where the files and websites take longer time to access).
Then the hacker disables any particular website that the user is going to use. As asserted by Modi
& Quadir (2014), in this process the user cannot get legal access to the websites. At the end of
this stage huge amount of spam mail is received by the user which disables or crashes the entire
networking system.
Figure 4: Online attacking procedure
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER SECURITY
7
(Source: Modi & Quadir, 2014)
2. Selecting the type of attack and analysis of following questions
a. The time of attack and providing a name of the attack
The time or situation of the attack is that when Olympic gold medalist Mack Horton brought up
the issue that his Chinese opponent Sun Yang was under the influence of drugs. Mack thought
that Sun Yang has used unfair means to win his medal. On the other hand he was very angry with
the Australian Swimming Association (Swim Australia). He thought that he would take his
revenge by launching a denial of service attack on the website of Swim Australia. He made up
his plan and started to infiltrate Swim Australia’s website (abc.net.au, 2018). He slowly filled the
company’s email with huge amount of spam mails. Then he disabled the company’s central
processing unit and Swim Australia’s website cannot be accessed.
b. Outcome of incident
However Swim Australia’s website was working fine but after the attack it became really slow.
Then after that suddenly all the computers of Swim Australia were filled with huge amount of
spam mails and their CPU was not functioning properly. As mentioned by Jakari et al. (2016),
after this incident Swim Australia called their IT team but they were unable to locate the
problem. Their entire computing system had faced shut down. None of the officials or employees
could access the internet nor were they able to register their attendance in the system. Everything
came to a standstill. Their whole system had gone haywire and they had no idea what was
happening with their system. Finally their entire computer system crashed and they were helpless
to do anything about it.
7
(Source: Modi & Quadir, 2014)
2. Selecting the type of attack and analysis of following questions
a. The time of attack and providing a name of the attack
The time or situation of the attack is that when Olympic gold medalist Mack Horton brought up
the issue that his Chinese opponent Sun Yang was under the influence of drugs. Mack thought
that Sun Yang has used unfair means to win his medal. On the other hand he was very angry with
the Australian Swimming Association (Swim Australia). He thought that he would take his
revenge by launching a denial of service attack on the website of Swim Australia. He made up
his plan and started to infiltrate Swim Australia’s website (abc.net.au, 2018). He slowly filled the
company’s email with huge amount of spam mails. Then he disabled the company’s central
processing unit and Swim Australia’s website cannot be accessed.
b. Outcome of incident
However Swim Australia’s website was working fine but after the attack it became really slow.
Then after that suddenly all the computers of Swim Australia were filled with huge amount of
spam mails and their CPU was not functioning properly. As mentioned by Jakari et al. (2016),
after this incident Swim Australia called their IT team but they were unable to locate the
problem. Their entire computing system had faced shut down. None of the officials or employees
could access the internet nor were they able to register their attendance in the system. Everything
came to a standstill. Their whole system had gone haywire and they had no idea what was
happening with their system. Finally their entire computer system crashed and they were helpless
to do anything about it.

COMPUTER SECURITY
8
c. Impact of incident (financial, affected devices, etc.)
Swim Australia faced huge amount of financial loss and many of their expensive devices were
all destroyed. All the computers CPUs, routers, Wi-Fi devices were destroyed in one instance.
Rebuilding the entire setup is going to require billions of dollars. Swim Australia already had
spent a large sum of money creating the previous setup and their funds are really low. On the
other hand, Hui, Kim & Wang (2017) stated that now they have to think how to bring in funds
and create a new computing setup for their association. Swim Australia is now thinking how to
come out of this problem situation and who is behind all these activities occurring in their
association. Swim Australia has started to analyse in what ways this situation can be overcome.
Swim Australia is bewildered.
d. Consequences of the attack and which part of security was violated
The cyber security law has been violated in this context. The consequences that are going to be
faced by the hacker is that he has to face severe legal action. The hacker might not be able to
participate in further sporting events. Hoque, Bhattacharyya & Kalita (2015) commented that the
hacker may have to pay heavy fines to the association for the damages that he has done to the
company. The association can blacklist the hacker in their list and his medals and accolades can
be confiscated by the association. Swim Australia can file a legal case against the hacker and he
can be imprisoned in the prison. If the hacker is identified then he is going to be heavily
penalised. Swim Australia is going to face severe consequences as well.
e. Type of action selected by the company to solve the problem
Swim Australia reported this incident to the government and the government has ordered an
investigation into the matter. AusCert a Non-Profit organisation is going to carry on the
8
c. Impact of incident (financial, affected devices, etc.)
Swim Australia faced huge amount of financial loss and many of their expensive devices were
all destroyed. All the computers CPUs, routers, Wi-Fi devices were destroyed in one instance.
Rebuilding the entire setup is going to require billions of dollars. Swim Australia already had
spent a large sum of money creating the previous setup and their funds are really low. On the
other hand, Hui, Kim & Wang (2017) stated that now they have to think how to bring in funds
and create a new computing setup for their association. Swim Australia is now thinking how to
come out of this problem situation and who is behind all these activities occurring in their
association. Swim Australia has started to analyse in what ways this situation can be overcome.
Swim Australia is bewildered.
d. Consequences of the attack and which part of security was violated
The cyber security law has been violated in this context. The consequences that are going to be
faced by the hacker is that he has to face severe legal action. The hacker might not be able to
participate in further sporting events. Hoque, Bhattacharyya & Kalita (2015) commented that the
hacker may have to pay heavy fines to the association for the damages that he has done to the
company. The association can blacklist the hacker in their list and his medals and accolades can
be confiscated by the association. Swim Australia can file a legal case against the hacker and he
can be imprisoned in the prison. If the hacker is identified then he is going to be heavily
penalised. Swim Australia is going to face severe consequences as well.
e. Type of action selected by the company to solve the problem
Swim Australia reported this incident to the government and the government has ordered an
investigation into the matter. AusCert a Non-Profit organisation is going to carry on the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER SECURITY
9
investigation. They found out that Swim Australia’s website was under the Dos attack and this
was a common problem all over Australia (Geva, Herzberg & Gev, 2014). This Dos attack on
Swim Australia’s website was a heavily planned attack. After the investigation was over Swim
Australia found that it was done by Mack Horton.
Conclusion and recommendation
In order to conclude this study it can be seen that how dos attack is done in various levels of
computing system. Then what are the different types of DDos attack and its various stages. It can
be recommended that the company has to use proper anti-virus software to safeguard their
computers. Cyber security helps in the prevention of cyber attacks, breaches of data and
identifying risk management. This attack has been done in order to take revenge on Swim
Australia by Mack Horton and he has accused his Chinese counterpart in being under the
influence of drugs and winning by unfair means.
9
investigation. They found out that Swim Australia’s website was under the Dos attack and this
was a common problem all over Australia (Geva, Herzberg & Gev, 2014). This Dos attack on
Swim Australia’s website was a heavily planned attack. After the investigation was over Swim
Australia found that it was done by Mack Horton.
Conclusion and recommendation
In order to conclude this study it can be seen that how dos attack is done in various levels of
computing system. Then what are the different types of DDos attack and its various stages. It can
be recommended that the company has to use proper anti-virus software to safeguard their
computers. Cyber security helps in the prevention of cyber attacks, breaches of data and
identifying risk management. This attack has been done in order to take revenge on Swim
Australia by Mack Horton and he has accused his Chinese counterpart in being under the
influence of drugs and winning by unfair means.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER SECURITY
10
Reference list
Journals:
Geva, M., Herzberg, A., & Gev, Y. (2014). Bandwidth distributed denial of service: Attacks and
defenses. IEEE Security & Privacy, 12(1), 54-61. Retrieved from:
http://mallikarjunainfosys.com/IEEE-PAPERS-2013-14/Bandwidth%20Distributed
%20Denial%20of%20Service/Bandwidth%20Distributed%20Denial%20of
%20Service.pdf
Hoque, N., Bhattacharyya, D. K., & Kalita, J. K. (2015). Botnet in DDoS Attacks: Trends and
Challenges. IEEE Communications Surveys and Tutorials, 17(4), 2242-2270. Retrieved
from:
https://www.researchgate.net/profile/Nazrul_Hoque2/publication/280308220_Botnet_in_
DDoS_Attacks_Trends_and_Challenges/links/55b10e1808ae9289a084ab4b/Botnet-in-
DDoS-Attacks-Trends-and-Challenges.pdf
Hui, K. L., Kim, S. H., & Wang, Q. H. (2017). Cybercrime deterrence and international
legislation: evidence from distributed denial of service attacks. Mis Quarterly, 41(2), 497.
Retrieved from: http://ink.library.smu.edu.sg/cgi/viewcontent.cgi?
article=4421&context=sis_research
Jakaria, A. H. M., Yang, W., Rashidi, B., Fung, C., & Rahman, M. A. (2016, June). Vfence: A
defense against distributed denial of service attacks using network function virtualization.
In Computer Software and Applications Conference (COMPSAC), 2016 IEEE 40th
10
Reference list
Journals:
Geva, M., Herzberg, A., & Gev, Y. (2014). Bandwidth distributed denial of service: Attacks and
defenses. IEEE Security & Privacy, 12(1), 54-61. Retrieved from:
http://mallikarjunainfosys.com/IEEE-PAPERS-2013-14/Bandwidth%20Distributed
%20Denial%20of%20Service/Bandwidth%20Distributed%20Denial%20of
%20Service.pdf
Hoque, N., Bhattacharyya, D. K., & Kalita, J. K. (2015). Botnet in DDoS Attacks: Trends and
Challenges. IEEE Communications Surveys and Tutorials, 17(4), 2242-2270. Retrieved
from:
https://www.researchgate.net/profile/Nazrul_Hoque2/publication/280308220_Botnet_in_
DDoS_Attacks_Trends_and_Challenges/links/55b10e1808ae9289a084ab4b/Botnet-in-
DDoS-Attacks-Trends-and-Challenges.pdf
Hui, K. L., Kim, S. H., & Wang, Q. H. (2017). Cybercrime deterrence and international
legislation: evidence from distributed denial of service attacks. Mis Quarterly, 41(2), 497.
Retrieved from: http://ink.library.smu.edu.sg/cgi/viewcontent.cgi?
article=4421&context=sis_research
Jakaria, A. H. M., Yang, W., Rashidi, B., Fung, C., & Rahman, M. A. (2016, June). Vfence: A
defense against distributed denial of service attacks using network function virtualization.
In Computer Software and Applications Conference (COMPSAC), 2016 IEEE 40th

COMPUTER SECURITY
11
Annual (Vol. 2, pp. 431-436). IEEE. Retrieved from:
http://users.csc.tntech.edu/~marahman/papers/Workshop/STPSA16_Jakaria.pdf
Modi, K., & Quadir, A. (2014). Detection and Prevention of DDoS Attacks on the Cloud using
Double-Tcp Mechanism and HMM-based Architecture. International Journal of Cloud
Computing and Services Science, 3(2), 113. Retrieved from:
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.889.7493&rep=rep1&type=pdf
Singn, G., & Gupta, M. (2016, April). Distributed denial-of-service. In 3rd International
Conference on Recent Trends in Engineering Science and Management (pp. 1131-1139).
Retrieved from: http://www.ijirse.com/wp-content/upload/2016/02/464V.pdf
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, 308-319.
Retrieved from: http://tarjomeh20.com/wp-content/uploads/2015/05/DDoS-attack-
protection______s65df1sdfgddgfdfg.pdf
Yan, Q., & Yu, F. R. (2015). Distributed denial of service attacks in software-defined
networking with cloud computing. IEEE Communications Magazine, 53(4), 52-59.
Retrieved from:
https://ieeeprojectsmadurai.com/2015-16%20IEEE%20PAPERS/ns2/ns2%20basepaper/
distributed%20denial.pdf
Yu, S., Tian, Y., Guo, S., & Wu, D. O. (2014). Can we beat DDoS attacks in clouds?. IEEE
Transactions on Parallel and Distributed Systems, 25(9), 2245-2254. Retrieved from:
http://nsp.org.au/syu/papers/DDoSinCloudMain.pdf
11
Annual (Vol. 2, pp. 431-436). IEEE. Retrieved from:
http://users.csc.tntech.edu/~marahman/papers/Workshop/STPSA16_Jakaria.pdf
Modi, K., & Quadir, A. (2014). Detection and Prevention of DDoS Attacks on the Cloud using
Double-Tcp Mechanism and HMM-based Architecture. International Journal of Cloud
Computing and Services Science, 3(2), 113. Retrieved from:
http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.889.7493&rep=rep1&type=pdf
Singn, G., & Gupta, M. (2016, April). Distributed denial-of-service. In 3rd International
Conference on Recent Trends in Engineering Science and Management (pp. 1131-1139).
Retrieved from: http://www.ijirse.com/wp-content/upload/2016/02/464V.pdf
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, 308-319.
Retrieved from: http://tarjomeh20.com/wp-content/uploads/2015/05/DDoS-attack-
protection______s65df1sdfgddgfdfg.pdf
Yan, Q., & Yu, F. R. (2015). Distributed denial of service attacks in software-defined
networking with cloud computing. IEEE Communications Magazine, 53(4), 52-59.
Retrieved from:
https://ieeeprojectsmadurai.com/2015-16%20IEEE%20PAPERS/ns2/ns2%20basepaper/
distributed%20denial.pdf
Yu, S., Tian, Y., Guo, S., & Wu, D. O. (2014). Can we beat DDoS attacks in clouds?. IEEE
Transactions on Parallel and Distributed Systems, 25(9), 2245-2254. Retrieved from:
http://nsp.org.au/syu/papers/DDoSinCloudMain.pdf
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




