Computer Security: Report on DDoS Attacks, Components, and Examples
VerifiedAdded on 2023/06/07
|11
|2444
|233
Report
AI Summary
This report delves into the realm of computer security, specifically focusing on Distributed Denial of Service (DDoS) attacks. It begins with a detailed walkthrough of how DDoS attacks operate, illustrating the components and stages involved, including the role of botnets and various attack layers. The report then presents a real-world example: the 2016 Dyn Cyber Attack, providing specifics such as the attack's occurrence, the outcome, its impact on users and services, and the security aims that were breached. The report further examines the actions taken to address the issue. It utilizes diagrams to clarify the attack mechanisms and provides a comprehensive analysis of the chosen incident, making it a valuable resource for understanding DDoS attacks and their implications in the context of computer security. The report concludes with a concise summary of the key findings and implications of DDoS attacks.

Running head: DDOS ATTACKS
Computer Security: DDoS Attacks
Name of the Student
Name of the University
Author’s Note:
Computer Security: DDoS Attacks
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
DDOS ATTACKS
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
1. Detailed Walk Through of Distributed Denial of Service Attack......................................2
2. Real World Example of DDoS Attack...............................................................................5
a) Occurrence of Attack with Specific Name....................................................................5
b) Outcome of the Selected Incident..................................................................................5
c) Impact of Selected Incident............................................................................................6
d) Aims of Security Breach with Consequences................................................................6
e) Specific Actions taken for Addressing the Issue...........................................................7
Conclusion..................................................................................................................................7
References..................................................................................................................................9
DDOS ATTACKS
Table of Contents
Introduction................................................................................................................................2
Discussion..................................................................................................................................2
1. Detailed Walk Through of Distributed Denial of Service Attack......................................2
2. Real World Example of DDoS Attack...............................................................................5
a) Occurrence of Attack with Specific Name....................................................................5
b) Outcome of the Selected Incident..................................................................................5
c) Impact of Selected Incident............................................................................................6
d) Aims of Security Breach with Consequences................................................................6
e) Specific Actions taken for Addressing the Issue...........................................................7
Conclusion..................................................................................................................................7
References..................................................................................................................................9

2
DDOS ATTACKS
Introduction
The computer security can be significantly defined as the security or protectiveness of
various computer systems either from damage or from theft for the software, electronic data
or software (Von Solms & Van Niekerk, 2013). This type of security is also effective for the
misdirection or disruption of fewer services, provided by them. There is an incrementing
reliance on the computer systems, smart devices like smart televisions as well as smart
phones, and other tiny devices together comprise of the IoT or Internet of Things. The
computer security or IT security is for the protection of several computer systems from the
various cyber attacks. The computer security consists of the physical security and cyber
security. These two types of securities are utilized by the various companies for properly
protecting against the unauthenticated or unauthorized access for the data centres or other
digitalized systems (Wang & Lu, 2013). The confidentiality, integrity or availability of
information is well maintained with this computer security. The following report outlines a
brief discussion on the computer security and the significant cyber threat of distributed denial
of service or DDoS attack.
Discussion
1. Detailed Walk Through of Distributed Denial of Service Attack
The distributed denial of service attack or DDoS attack is the significant malicious
attempt for the purpose of disrupting the normal traffic of any targeted server, network or
service by the overwhelming target or infrastructure with the respective flood of this Internet
traffic (Hahn et al., 2013). These types of attacks solely achieve the effectiveness or
efficiency by the proper utilization of several compromised or dangerous computer based
systems as the typical sources of any attack traffic. The exploited machines could eventually
DDOS ATTACKS
Introduction
The computer security can be significantly defined as the security or protectiveness of
various computer systems either from damage or from theft for the software, electronic data
or software (Von Solms & Van Niekerk, 2013). This type of security is also effective for the
misdirection or disruption of fewer services, provided by them. There is an incrementing
reliance on the computer systems, smart devices like smart televisions as well as smart
phones, and other tiny devices together comprise of the IoT or Internet of Things. The
computer security or IT security is for the protection of several computer systems from the
various cyber attacks. The computer security consists of the physical security and cyber
security. These two types of securities are utilized by the various companies for properly
protecting against the unauthenticated or unauthorized access for the data centres or other
digitalized systems (Wang & Lu, 2013). The confidentiality, integrity or availability of
information is well maintained with this computer security. The following report outlines a
brief discussion on the computer security and the significant cyber threat of distributed denial
of service or DDoS attack.
Discussion
1. Detailed Walk Through of Distributed Denial of Service Attack
The distributed denial of service attack or DDoS attack is the significant malicious
attempt for the purpose of disrupting the normal traffic of any targeted server, network or
service by the overwhelming target or infrastructure with the respective flood of this Internet
traffic (Hahn et al., 2013). These types of attacks solely achieve the effectiveness or
efficiency by the proper utilization of several compromised or dangerous computer based
systems as the typical sources of any attack traffic. The exploited machines could eventually
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
DDOS ATTACKS
involve the networked resources or systems in this attack and the most targeted resources in
this case are devices of Internet of Things (Buczak & Guven, 2016). The distributed denial of
service attack subsequently jams the network traffic and hence the regular network traffic is
prevented from the packets reaching to the desired location.
Figure 1: Components of DDoS Attacks
(Source: Created by the Author in MS Word)
The DDoS attack needs a hacker for obtaining the complete control of the network for
executing the attack (Compagno et al., 2013). The entire procedure of this attack is quite
simplified. The computer systems as well as other machineries are at first infected with the
malware, hence turning the machines into bots. The significant hacker then comprises of the
remote control on the collection of bots, known as botnet. When this botnet is being
established, the hacker has the capability for directing the respective systems by simply
AttackerHandlerBotnetBotnetHandlerBotnetVictimBotnet
DDOS ATTACKS
involve the networked resources or systems in this attack and the most targeted resources in
this case are devices of Internet of Things (Buczak & Guven, 2016). The distributed denial of
service attack subsequently jams the network traffic and hence the regular network traffic is
prevented from the packets reaching to the desired location.
Figure 1: Components of DDoS Attacks
(Source: Created by the Author in MS Word)
The DDoS attack needs a hacker for obtaining the complete control of the network for
executing the attack (Compagno et al., 2013). The entire procedure of this attack is quite
simplified. The computer systems as well as other machineries are at first infected with the
malware, hence turning the machines into bots. The significant hacker then comprises of the
remote control on the collection of bots, known as botnet. When this botnet is being
established, the hacker has the capability for directing the respective systems by simply
AttackerHandlerBotnetBotnetHandlerBotnetVictimBotnet
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
Attacker
Bot
Bot
Bot
HTTP GET/ index.php
Target Victim
DDOS ATTACKS
sending updated and current instructions to each and every bot through the methodology of
remote control (Yan et al., 2016). As soon as the specific IP address of the victim is observed
by the botnet, all the bots would be substantially responding by the sending of requests to the
victims and hence causing the specific network or server for overflowing capacity and the
occurrence of DDoS attack.
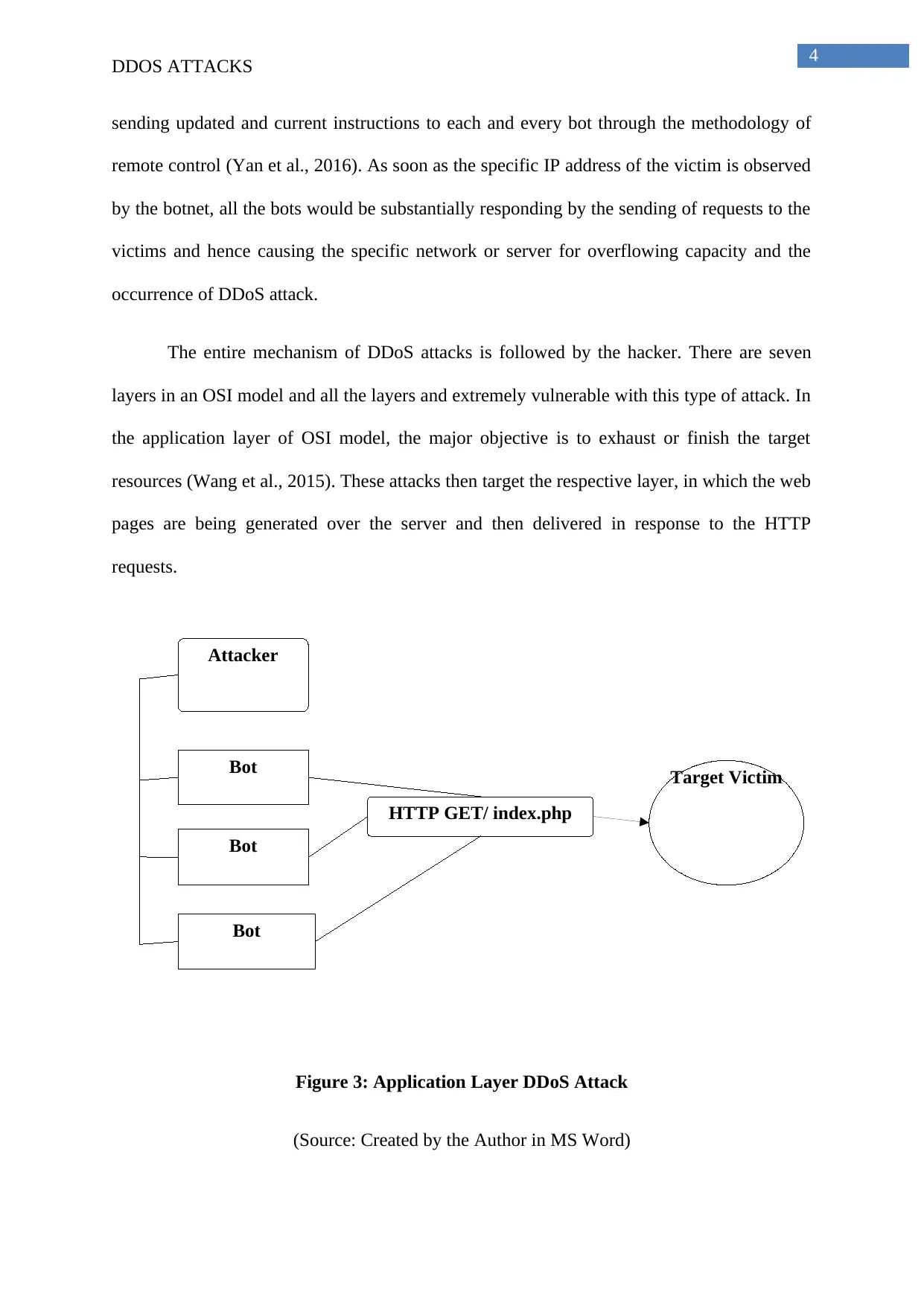
The entire mechanism of DDoS attacks is followed by the hacker. There are seven
layers in an OSI model and all the layers and extremely vulnerable with this type of attack. In
the application layer of OSI model, the major objective is to exhaust or finish the target
resources (Wang et al., 2015). These attacks then target the respective layer, in which the web
pages are being generated over the server and then delivered in response to the HTTP
requests.
Figure 3: Application Layer DDoS Attack
(Source: Created by the Author in MS Word)
Attacker
Bot
Bot
Bot
HTTP GET/ index.php
Target Victim
DDOS ATTACKS
sending updated and current instructions to each and every bot through the methodology of
remote control (Yan et al., 2016). As soon as the specific IP address of the victim is observed
by the botnet, all the bots would be substantially responding by the sending of requests to the
victims and hence causing the specific network or server for overflowing capacity and the
occurrence of DDoS attack.
The entire mechanism of DDoS attacks is followed by the hacker. There are seven
layers in an OSI model and all the layers and extremely vulnerable with this type of attack. In
the application layer of OSI model, the major objective is to exhaust or finish the target
resources (Wang et al., 2015). These attacks then target the respective layer, in which the web
pages are being generated over the server and then delivered in response to the HTTP
requests.
Figure 3: Application Layer DDoS Attack
(Source: Created by the Author in MS Word)

5
DDOS ATTACKS
The next dangerous attack is the protocol attacks (Yu et al., 2014). These are also
called as the state exhaustion attacks, which cause major service disruptions by the proper
consumption of the available state table capacities of the web application servers or the two
intermediate resources such as load balances as well as firewalls.
2. Real World Example of DDoS Attack
a) Occurrence of Attack with Specific Name
One of the most popular and significant distributed denial of service attacks, the 2016
Dyn Cyber Attack, is considered as the most deadly example of this attack. This DDoS cyber
attack took place in Europe and North America on 21st October, 2016 (Woolf, 2018). This
attack involved several DDoS or distributed denial of service attacks, hence targeting the
systems, which are operated by DNS or Domain Name System provider Dyn. This Dyn
eventually caused most of the Internet services or platforms completely unavailable for the
larger swathes of the users in North America and Europe.
b) Outcome of the Selected Incident
The outcome of this 2016 Dyn Cyber Attack was extremely dangerous as well as
vulnerable for all of the users of the entire North America and Europe (Bhuyan,
Bhattacharyya & Kalita, 2015). The entire major Internet based services as well Internet
based platforms were made absolutely unavailable for the intended users. The specific
hackers’ groups, namely New World Hackers and Anonymous eventually claimed the
responsibility for this particular attack, however, strong evidence was not provided in the
case. Dyn is a DNS provider, which subsequently provides mapping service to its end users.
The mapping is done in the Internet domain name, whenever it is being entered into the web
browser with its corresponding IP addresses (Santanna et al., 2015). The malware that caused
this distributed denial of service attack is Mirai. It turned the networked devices that are
DDOS ATTACKS
The next dangerous attack is the protocol attacks (Yu et al., 2014). These are also
called as the state exhaustion attacks, which cause major service disruptions by the proper
consumption of the available state table capacities of the web application servers or the two
intermediate resources such as load balances as well as firewalls.
2. Real World Example of DDoS Attack
a) Occurrence of Attack with Specific Name
One of the most popular and significant distributed denial of service attacks, the 2016
Dyn Cyber Attack, is considered as the most deadly example of this attack. This DDoS cyber
attack took place in Europe and North America on 21st October, 2016 (Woolf, 2018). This
attack involved several DDoS or distributed denial of service attacks, hence targeting the
systems, which are operated by DNS or Domain Name System provider Dyn. This Dyn
eventually caused most of the Internet services or platforms completely unavailable for the
larger swathes of the users in North America and Europe.
b) Outcome of the Selected Incident
The outcome of this 2016 Dyn Cyber Attack was extremely dangerous as well as
vulnerable for all of the users of the entire North America and Europe (Bhuyan,
Bhattacharyya & Kalita, 2015). The entire major Internet based services as well Internet
based platforms were made absolutely unavailable for the intended users. The specific
hackers’ groups, namely New World Hackers and Anonymous eventually claimed the
responsibility for this particular attack, however, strong evidence was not provided in the
case. Dyn is a DNS provider, which subsequently provides mapping service to its end users.
The mapping is done in the Internet domain name, whenever it is being entered into the web
browser with its corresponding IP addresses (Santanna et al., 2015). The malware that caused
this distributed denial of service attack is Mirai. It turned the networked devices that are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
DDOS ATTACKS
running on Linux to remotely controlled bots for using them as the specific part of botnet
within this large scale networked attacks.
c) Impact of Selected Incident
The impact of the 2016 Dyn Cyber Attack was extremely high on the users of North
America and Europe. There were total three attacks in this DDoS attack. As per Dyn, the first
attack started at 7 am in the morning and was resolved by 9.20 am (Woolf, 2018). The next
attack occurred at 11.52 am and all the users of Internet were facing difficulties in accessing
the websites. The final attack occurred after 4 pm in the afternoon; however at 6.11 pm, it
was resolved by Dyn. The particular distributed denial of service or DDoS attack was caused
by the Mirai malware and was accomplished by the larger number of lookup requests of
Domain Name System form billions of generated IP addresses (Dai et al., 2013). These
malicious activities were eventually carried out through a specific botnet that comprised of
huge numbers or Internet connected or Internet based devices like the IP cameras, baby
monitors, printers, residential gateways and many others. All of the above mentioned devices
were being affected by the Mirai malware. The various popular and significant affected
services in this particular DDoS attack were Amazon.com, Airbnb, BBC, Quora, CNN,
Starbucks, Box, HBO, Twitter, Verizon Communications, Fox News, Heroku, Tumblr,
Netflix, Pinterest, PayPal, PlayStation Network, The New York Times, WWE Network,
GitHub and many more (Woolf, 2018).
d) Aims of Security Breach with Consequences
There were some of the major aims of this security breach. The first and the foremost
aim was to attack the devices of Internet of Things. The consequence was that this attack was
the botnet that was coordinated by a huge number of IoT enabled devices that included IP
cameras, baby monitors, printers and residential gateways (Wang et al., 2015). The second
aim of this specific DDoS attack of 2016 Dyn cyber attack was to spread Mirai malware. This
DDOS ATTACKS
running on Linux to remotely controlled bots for using them as the specific part of botnet
within this large scale networked attacks.
c) Impact of Selected Incident
The impact of the 2016 Dyn Cyber Attack was extremely high on the users of North
America and Europe. There were total three attacks in this DDoS attack. As per Dyn, the first
attack started at 7 am in the morning and was resolved by 9.20 am (Woolf, 2018). The next
attack occurred at 11.52 am and all the users of Internet were facing difficulties in accessing
the websites. The final attack occurred after 4 pm in the afternoon; however at 6.11 pm, it
was resolved by Dyn. The particular distributed denial of service or DDoS attack was caused
by the Mirai malware and was accomplished by the larger number of lookup requests of
Domain Name System form billions of generated IP addresses (Dai et al., 2013). These
malicious activities were eventually carried out through a specific botnet that comprised of
huge numbers or Internet connected or Internet based devices like the IP cameras, baby
monitors, printers, residential gateways and many others. All of the above mentioned devices
were being affected by the Mirai malware. The various popular and significant affected
services in this particular DDoS attack were Amazon.com, Airbnb, BBC, Quora, CNN,
Starbucks, Box, HBO, Twitter, Verizon Communications, Fox News, Heroku, Tumblr,
Netflix, Pinterest, PayPal, PlayStation Network, The New York Times, WWE Network,
GitHub and many more (Woolf, 2018).
d) Aims of Security Breach with Consequences
There were some of the major aims of this security breach. The first and the foremost
aim was to attack the devices of Internet of Things. The consequence was that this attack was
the botnet that was coordinated by a huge number of IoT enabled devices that included IP
cameras, baby monitors, printers and residential gateways (Wang et al., 2015). The second
aim of this specific DDoS attack of 2016 Dyn cyber attack was to spread Mirai malware. This
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
DDOS ATTACKS
malware was created juts two months prior to the attack and it was designed to the brute force
for controlling the IoT enabled devices remotely.
e) Specific Actions taken for Addressing the Issue
The cyber security investigator of Brian Krebs eventually noted that the respective
source code for the malware Mirai malware had been previously released by the hackers over
the Internet within an open source manner. Hence, the overall investigation of the attacker
was extremely difficult in this case. The then President of the United States of America took
necessary actions in this attack and the attackers were substantially punished (Woolf, 2018).
Three men, namely, Paras Jha, Josiah white and Dalton Norman were arrested in the popular
DDoS attack of the 2016 Dyn cyber attack.
Conclusion
Therefore, from the above discussion, it can be concluded that computer security
refers to the collection of tools and techniques that are utilized for the proper protection of
network, data or programs from the damages, attacks as well as unauthorized access. The
most significant functionality of this computer security majorly includes protection of the
information as well as information systems from several cyber threats. There are several
forms of cyber threats, which are malware, phishing, application attacks, exploit kits,
ransomware, worm attacks, distributed denial of service attacks and many others. Amongst
them, the most dangerous attack is the distributed denial of service attack or DDoS attack.
The intended machine is made unavailable by the attacker so that the user cannot access it
eventually. The services are denied for the significant victims and hence these are extremely
vulnerable for any information system. The above report has clearly outlined the brief
discussion on distributed denial of service attack and computer security. The case study of
DDOS ATTACKS
malware was created juts two months prior to the attack and it was designed to the brute force
for controlling the IoT enabled devices remotely.
e) Specific Actions taken for Addressing the Issue
The cyber security investigator of Brian Krebs eventually noted that the respective
source code for the malware Mirai malware had been previously released by the hackers over
the Internet within an open source manner. Hence, the overall investigation of the attacker
was extremely difficult in this case. The then President of the United States of America took
necessary actions in this attack and the attackers were substantially punished (Woolf, 2018).
Three men, namely, Paras Jha, Josiah white and Dalton Norman were arrested in the popular
DDoS attack of the 2016 Dyn cyber attack.
Conclusion
Therefore, from the above discussion, it can be concluded that computer security
refers to the collection of tools and techniques that are utilized for the proper protection of
network, data or programs from the damages, attacks as well as unauthorized access. The
most significant functionality of this computer security majorly includes protection of the
information as well as information systems from several cyber threats. There are several
forms of cyber threats, which are malware, phishing, application attacks, exploit kits,
ransomware, worm attacks, distributed denial of service attacks and many others. Amongst
them, the most dangerous attack is the distributed denial of service attack or DDoS attack.
The intended machine is made unavailable by the attacker so that the user cannot access it
eventually. The services are denied for the significant victims and hence these are extremely
vulnerable for any information system. The above report has clearly outlined the brief
discussion on distributed denial of service attack and computer security. The case study of

8
DDOS ATTACKS
2016 Dyn Cyber Attack by Anonymous and New World Hackers is taken in this report as a
real world example of DDoS attack.
DDOS ATTACKS
2016 Dyn Cyber Attack by Anonymous and New World Hackers is taken in this report as a
real world example of DDoS attack.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
DDOS ATTACKS
References
Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2015). An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern
Recognition Letters, 51, 1-7.
Buczak, A. L., & Guven, E. (2016). A survey of data mining and machine learning methods
for cyber security intrusion detection. IEEE Communications Surveys &
Tutorials, 18(2), 1153-1176.
Compagno, A., Conti, M., Gasti, P., & Tsudik, G. (2013, October). Poseidon: Mitigating
interest flooding DDoS attacks in named data networking. In Local Computer
Networks (LCN), 2013 IEEE 38th Conference on (pp. 630-638). IEEE.
Dai, H., Wang, Y., Fan, J., & Liu, B. (2013, April). Mitigate ddos attacks in ndn by interest
traceback. In Computer Communications Workshops (INFOCOM WKSHPS), 2013
IEEE Conference on (pp. 381-386). IEEE.
Hahn, A., Ashok, A., Sridhar, S., & Govindarasu, M. (2013). Cyber-physical security
testbeds: Architecture, application, and evaluation for smart grid. IEEE Transactions
on Smart Grid, 4(2), 847-855.
Santanna, J. J., van Rijswijk-Deij, R., Hofstede, R., Sperotto, A., Wierbosch, M., Granville,
L. Z., & Pras, A. (2015, May). Booters—An analysis of DDoS-as-a-service attacks.
In Integrated Network Management (IM), 2015 IFIP/IEEE International Symposium
on (pp. 243-251). IEEE.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
DDOS ATTACKS
References
Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2015). An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern
Recognition Letters, 51, 1-7.
Buczak, A. L., & Guven, E. (2016). A survey of data mining and machine learning methods
for cyber security intrusion detection. IEEE Communications Surveys &
Tutorials, 18(2), 1153-1176.
Compagno, A., Conti, M., Gasti, P., & Tsudik, G. (2013, October). Poseidon: Mitigating
interest flooding DDoS attacks in named data networking. In Local Computer
Networks (LCN), 2013 IEEE 38th Conference on (pp. 630-638). IEEE.
Dai, H., Wang, Y., Fan, J., & Liu, B. (2013, April). Mitigate ddos attacks in ndn by interest
traceback. In Computer Communications Workshops (INFOCOM WKSHPS), 2013
IEEE Conference on (pp. 381-386). IEEE.
Hahn, A., Ashok, A., Sridhar, S., & Govindarasu, M. (2013). Cyber-physical security
testbeds: Architecture, application, and evaluation for smart grid. IEEE Transactions
on Smart Grid, 4(2), 847-855.
Santanna, J. J., van Rijswijk-Deij, R., Hofstede, R., Sperotto, A., Wierbosch, M., Granville,
L. Z., & Pras, A. (2015, May). Booters—An analysis of DDoS-as-a-service attacks.
In Integrated Network Management (IM), 2015 IFIP/IEEE International Symposium
on (pp. 243-251). IEEE.
Von Solms, R., & Van Niekerk, J. (2013). From information security to cyber
security. computers & security, 38, 97-102.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
DDOS ATTACKS
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of
cloud computing and software-defined networking. Computer Networks, 81, 308-319.
Wang, W., & Lu, Z. (2013). Cyber security in the smart grid: Survey and
challenges. Computer Networks, 57(5), 1344-1371.
Woolf, N. (2018). DDoS attack that disrupted internet was largest of its kind in history,
experts say. Retrieved from
https://www.theguardian.com/technology/2016/oct/26/ddos-attack-dyn-mirai-botnet
Yan, Q., Yu, F. R., Gong, Q., & Li, J. (2016). Software-defined networking (SDN) and
distributed denial of service (DDoS) attacks in cloud computing environments: A
survey, some research issues, and challenges. IEEE Communications Surveys &
Tutorials, 18(1), 602-622.
Yu, S., Tian, Y., Guo, S., & Wu, D. O. (2014). Can we beat DDoS attacks in clouds?. IEEE
Transactions on Parallel and Distributed Systems, 25(9), 2245-2254.
DDOS ATTACKS
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of
cloud computing and software-defined networking. Computer Networks, 81, 308-319.
Wang, W., & Lu, Z. (2013). Cyber security in the smart grid: Survey and
challenges. Computer Networks, 57(5), 1344-1371.
Woolf, N. (2018). DDoS attack that disrupted internet was largest of its kind in history,
experts say. Retrieved from
https://www.theguardian.com/technology/2016/oct/26/ddos-attack-dyn-mirai-botnet
Yan, Q., Yu, F. R., Gong, Q., & Li, J. (2016). Software-defined networking (SDN) and
distributed denial of service (DDoS) attacks in cloud computing environments: A
survey, some research issues, and challenges. IEEE Communications Surveys &
Tutorials, 18(1), 602-622.
Yu, S., Tian, Y., Guo, S., & Wu, D. O. (2014). Can we beat DDoS attacks in clouds?. IEEE
Transactions on Parallel and Distributed Systems, 25(9), 2245-2254.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




