Vulnerability Analysis and Exploitation of Windows XP SP2 System
VerifiedAdded on 2023/01/12
|42
|2354
|77
Practical Assignment
AI Summary
This assignment details a practical computer security project involving the vulnerability analysis and exploitation of a Windows XP SP2 system. The process begins with installing Kali Linux and Windows XP on a virtual machine. The student then uses Nessus to identify vulnerabilities in the Windows XP SP2 system. Subsequently, the student utilizes Metasploit to gain access to the system, demonstrating the exploitation of identified weaknesses. The assignment covers various aspects of the exploitation process, including gaining system information, password cracking, and file manipulation. The student demonstrates the use of tools like nmap, msfconsole, and meterpreter to achieve these objectives. Finally, the student successfully implements methods to prevent attacks on Windows XP.

Computer security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction................................................................................................................................2
Nessus........................................................................................................................................3
Kali Linux and Windows XP.....................................................................................................3
Install kali Linux........................................................................................................................3
Install windows xp...................................................................................................................24
Attack against a Windows XP SP2 System..............................................................................31
Part a)..............................................................................................................................................31
Part b)..............................................................................................................................................33
Part c)..............................................................................................................................................34
Part d)..............................................................................................................................................35
Part e)..............................................................................................................................................36
Part f)...............................................................................................................................................37
Part g)..............................................................................................................................................38
Part h)..............................................................................................................................................39
Conclusion................................................................................................................................40
Reference..................................................................................................................................41
Introduction................................................................................................................................2
Nessus........................................................................................................................................3
Kali Linux and Windows XP.....................................................................................................3
Install kali Linux........................................................................................................................3
Install windows xp...................................................................................................................24
Attack against a Windows XP SP2 System..............................................................................31
Part a)..............................................................................................................................................31
Part b)..............................................................................................................................................33
Part c)..............................................................................................................................................34
Part d)..............................................................................................................................................35
Part e)..............................................................................................................................................36
Part f)...............................................................................................................................................37
Part g)..............................................................................................................................................38
Part h)..............................................................................................................................................39
Conclusion................................................................................................................................40
Reference..................................................................................................................................41

Introduction
In this project the main aim is to conduct vulnerability for the window XP-SP2 system
using Nessus and then gain access into this system using Metasploit. First step is to install the
Kali Linux and Windows XP on the virtual machine. It contains information such as last
name, IP address, process ID, cracked password etc. We will hack the password using Kali
Linux and Windows XP on the virtual machine.
Nessus
Nessus is used to identify common vulnerabilities and exposures architecture for linking
between security tools. It is an open source network vulnerability scanner and used for
security purpose. The individual threats and potential attacks are described by simple
language, called as Nessus attack scripting language (Nsouli-Lalardrie, 2010). It consists of
servers, remote clients and conducts scanning which allows for administrator interaction. It
has the same features such as a computer and server size compatibility, updates the missing
security, detects missing security, local or remote hosts are detected by Nessus, execution of
security tests and security audits. It is available for UNIX, FreeBSD and Linux. It scans a
computer and raises an alert that access to any computer connected to the network for any
hacking or malicious intent. It accesses different remote clients and servers. Each computer
has thousands of ports and these may work or may not be working. Nessus is used to test
these ports and then displays which ports are working and which are not.
Kali Linux and Windows XP
Kali Linux is mainly used to perform penetration testing and is based on debian Linux. It
contains several hundreds of tools and these can perform information security tasks such as
computer forensics, reverse engineering, security research and penetration test. Backtrack is
one of Kali Linux tools which is used to test the duplicated tools. Kali Linux kernel has the
latest innovation which performs the needs to do wireless assessments (Höhl, 2013). Kali
Linux includes multilingual support and allows multi users. It supports single board system
like beagle bone black and raspberry Pi. It has ARM repositories integrated with mainline
distributors and it is available on a wide range of id ARM devices. We have used the
penetration test for this project and for that Kali Linux and Windows XP have been installed.
Windows has two types of version i.e. Window XP Home and Window XP Professional. It
includes plug and play features for connecting to wireless networks and this focuses on
mobility. It is used to update the system for protection against viruses and malware. We have
In this project the main aim is to conduct vulnerability for the window XP-SP2 system
using Nessus and then gain access into this system using Metasploit. First step is to install the
Kali Linux and Windows XP on the virtual machine. It contains information such as last
name, IP address, process ID, cracked password etc. We will hack the password using Kali
Linux and Windows XP on the virtual machine.
Nessus
Nessus is used to identify common vulnerabilities and exposures architecture for linking
between security tools. It is an open source network vulnerability scanner and used for
security purpose. The individual threats and potential attacks are described by simple
language, called as Nessus attack scripting language (Nsouli-Lalardrie, 2010). It consists of
servers, remote clients and conducts scanning which allows for administrator interaction. It
has the same features such as a computer and server size compatibility, updates the missing
security, detects missing security, local or remote hosts are detected by Nessus, execution of
security tests and security audits. It is available for UNIX, FreeBSD and Linux. It scans a
computer and raises an alert that access to any computer connected to the network for any
hacking or malicious intent. It accesses different remote clients and servers. Each computer
has thousands of ports and these may work or may not be working. Nessus is used to test
these ports and then displays which ports are working and which are not.
Kali Linux and Windows XP
Kali Linux is mainly used to perform penetration testing and is based on debian Linux. It
contains several hundreds of tools and these can perform information security tasks such as
computer forensics, reverse engineering, security research and penetration test. Backtrack is
one of Kali Linux tools which is used to test the duplicated tools. Kali Linux kernel has the
latest innovation which performs the needs to do wireless assessments (Höhl, 2013). Kali
Linux includes multilingual support and allows multi users. It supports single board system
like beagle bone black and raspberry Pi. It has ARM repositories integrated with mainline
distributors and it is available on a wide range of id ARM devices. We have used the
penetration test for this project and for that Kali Linux and Windows XP have been installed.
Windows has two types of version i.e. Window XP Home and Window XP Professional. It
includes plug and play features for connecting to wireless networks and this focuses on
mobility. It is used to update the system for protection against viruses and malware. We have
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
used Kali Linux and Windows XP on virtual machine for protection against malware. The
Kali Linux and Windows XP have to be downloaded and installed on the virtual machine.
Install Kali Linux
First step is to download and install Kali Linux on the virtual machine.
Open the virtual machine for installing the Kali Linux ("Kali Linux – Assuring Security by
Penetration Testing", 2014).
Kali Linux and Windows XP have to be downloaded and installed on the virtual machine.
Install Kali Linux
First step is to download and install Kali Linux on the virtual machine.
Open the virtual machine for installing the Kali Linux ("Kali Linux – Assuring Security by
Penetration Testing", 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Click on “create a new virtual machine” for creating a new VM.
The new virtual machine wizard then opens, choose the typical option and then click on the
next button.
The new virtual machine wizard then opens, choose the typical option and then click on the
next button.
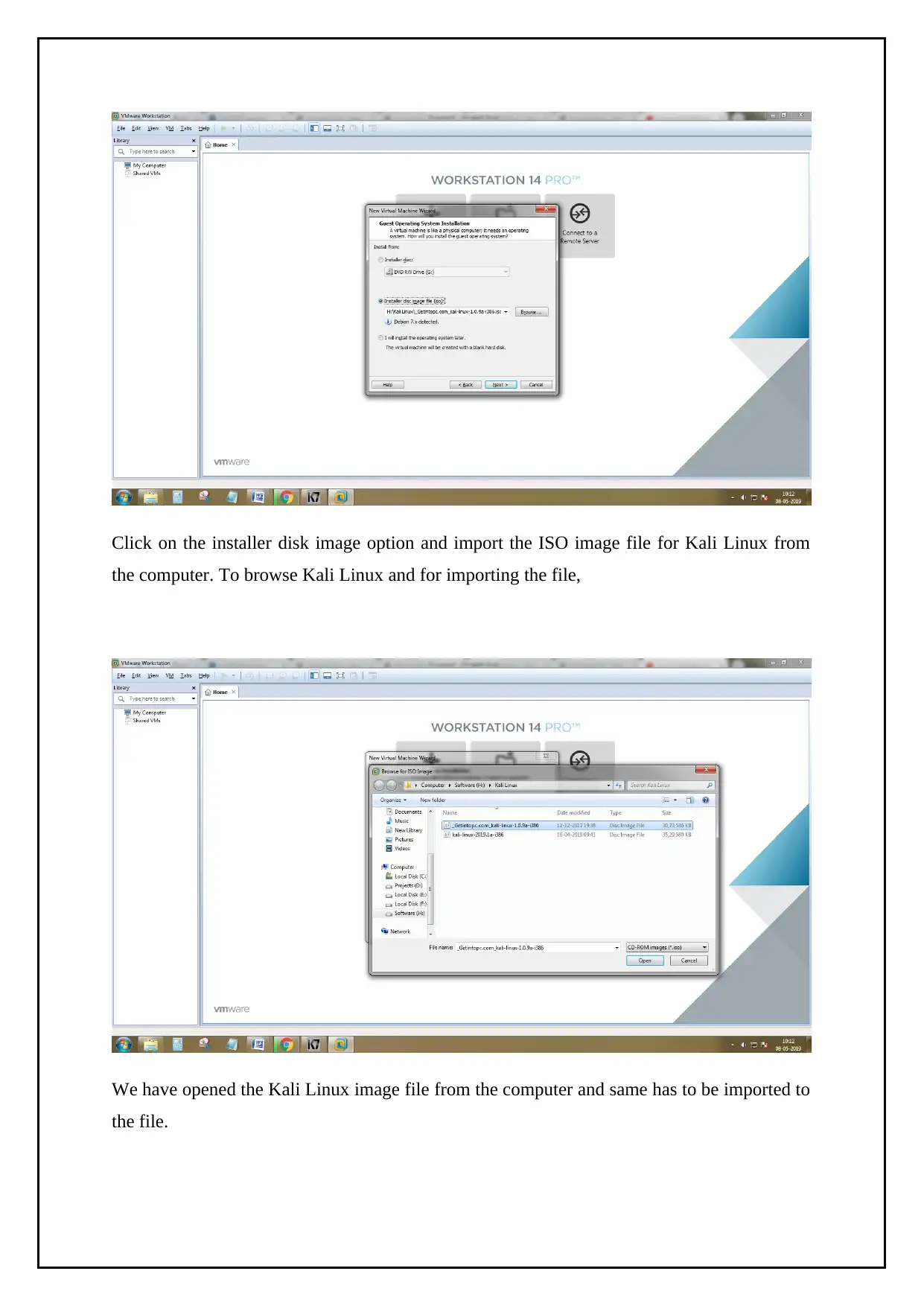
Click on the installer disk image option and import the ISO image file for Kali Linux from
the computer. To browse Kali Linux and for importing the file,
We have opened the Kali Linux image file from the computer and same has to be imported to
the file.
the computer. To browse Kali Linux and for importing the file,
We have opened the Kali Linux image file from the computer and same has to be imported to
the file.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
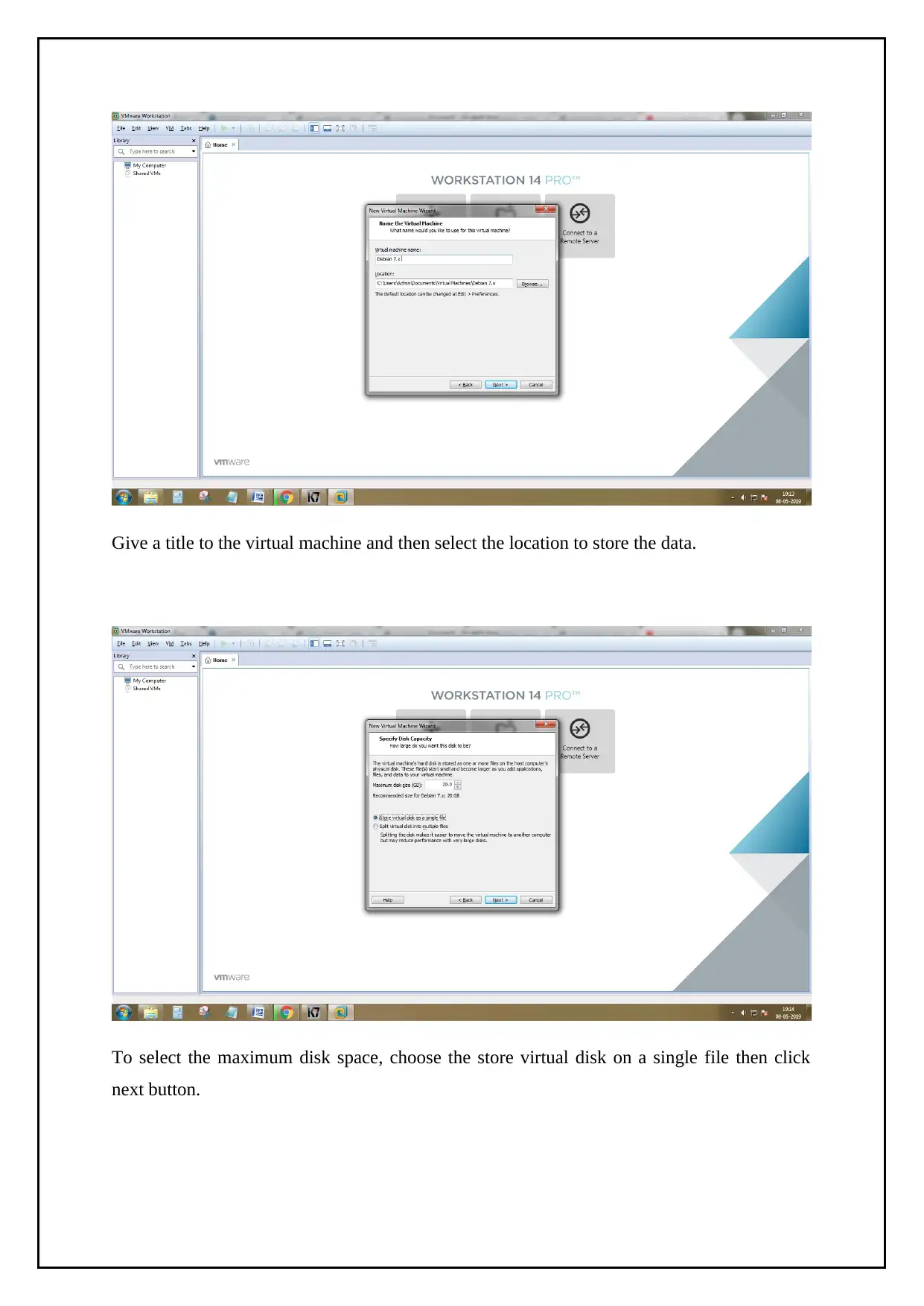
Give a title to the virtual machine and then select the location to store the data.
To select the maximum disk space, choose the store virtual disk on a single file then click
next button.
To select the maximum disk space, choose the store virtual disk on a single file then click
next button.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
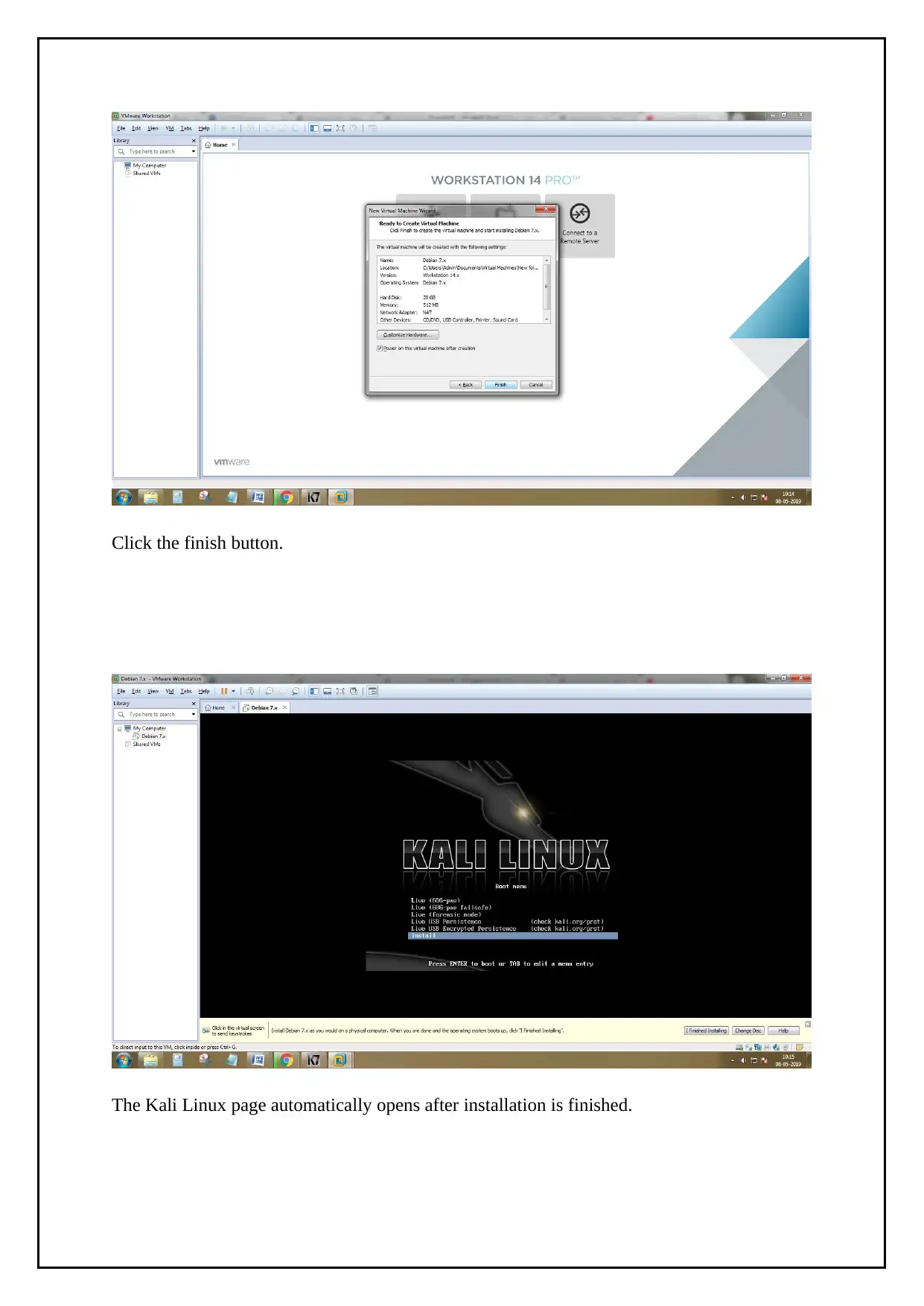
Click the finish button.
The Kali Linux page automatically opens after installation is finished.
The Kali Linux page automatically opens after installation is finished.
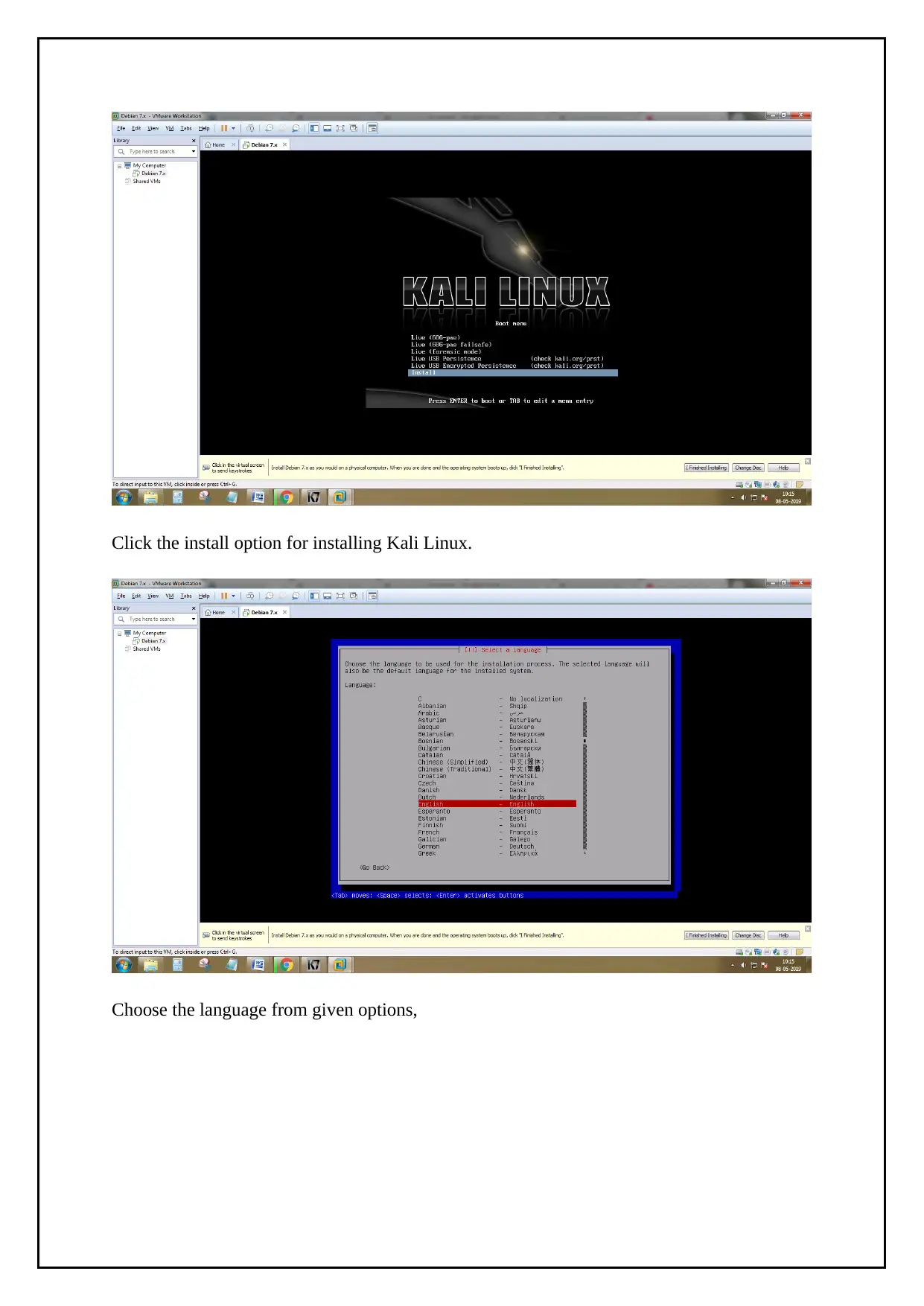
Click the install option for installing Kali Linux.
Choose the language from given options,
Choose the language from given options,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
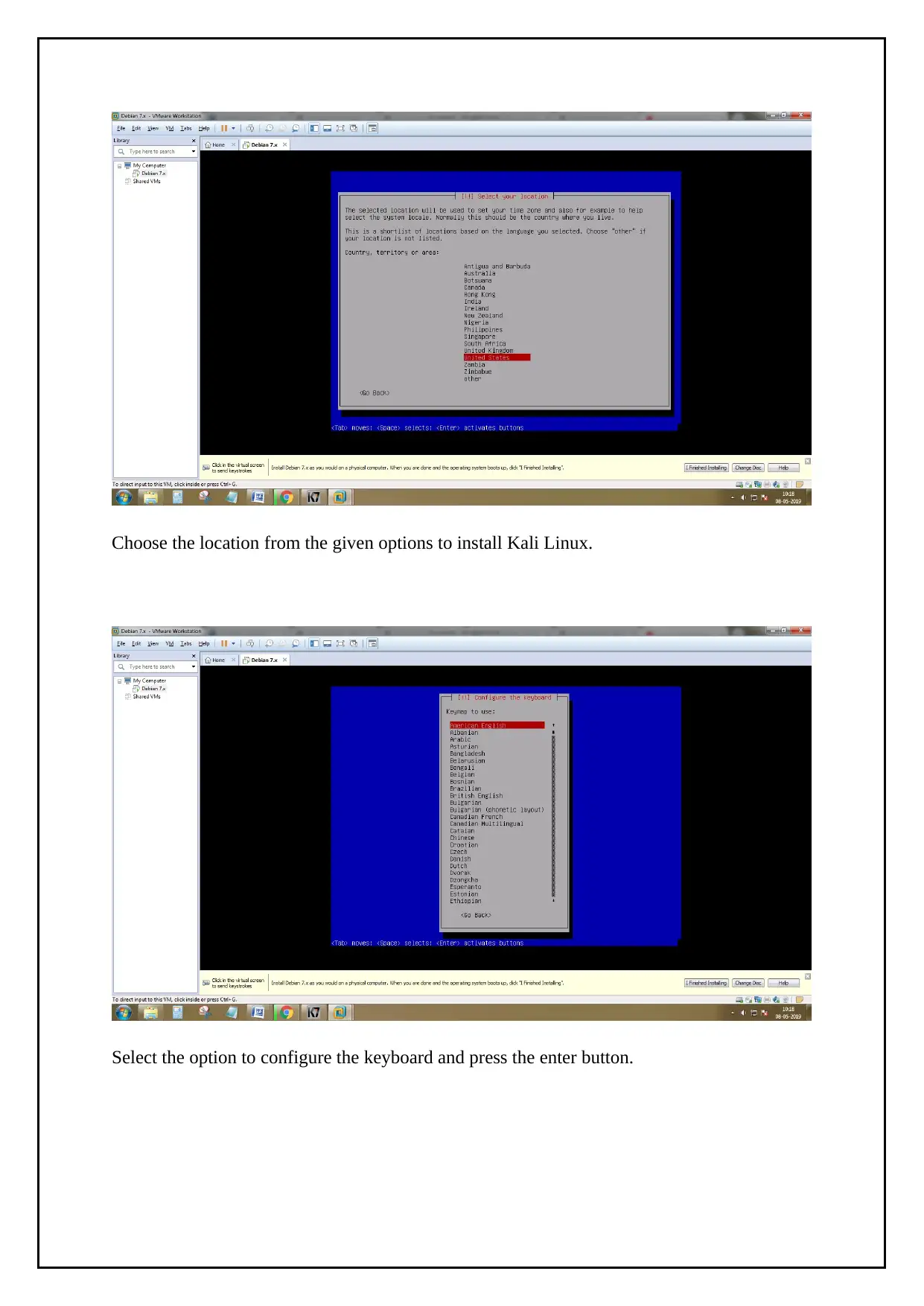
Choose the location from the given options to install Kali Linux.
Select the option to configure the keyboard and press the enter button.
Select the option to configure the keyboard and press the enter button.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
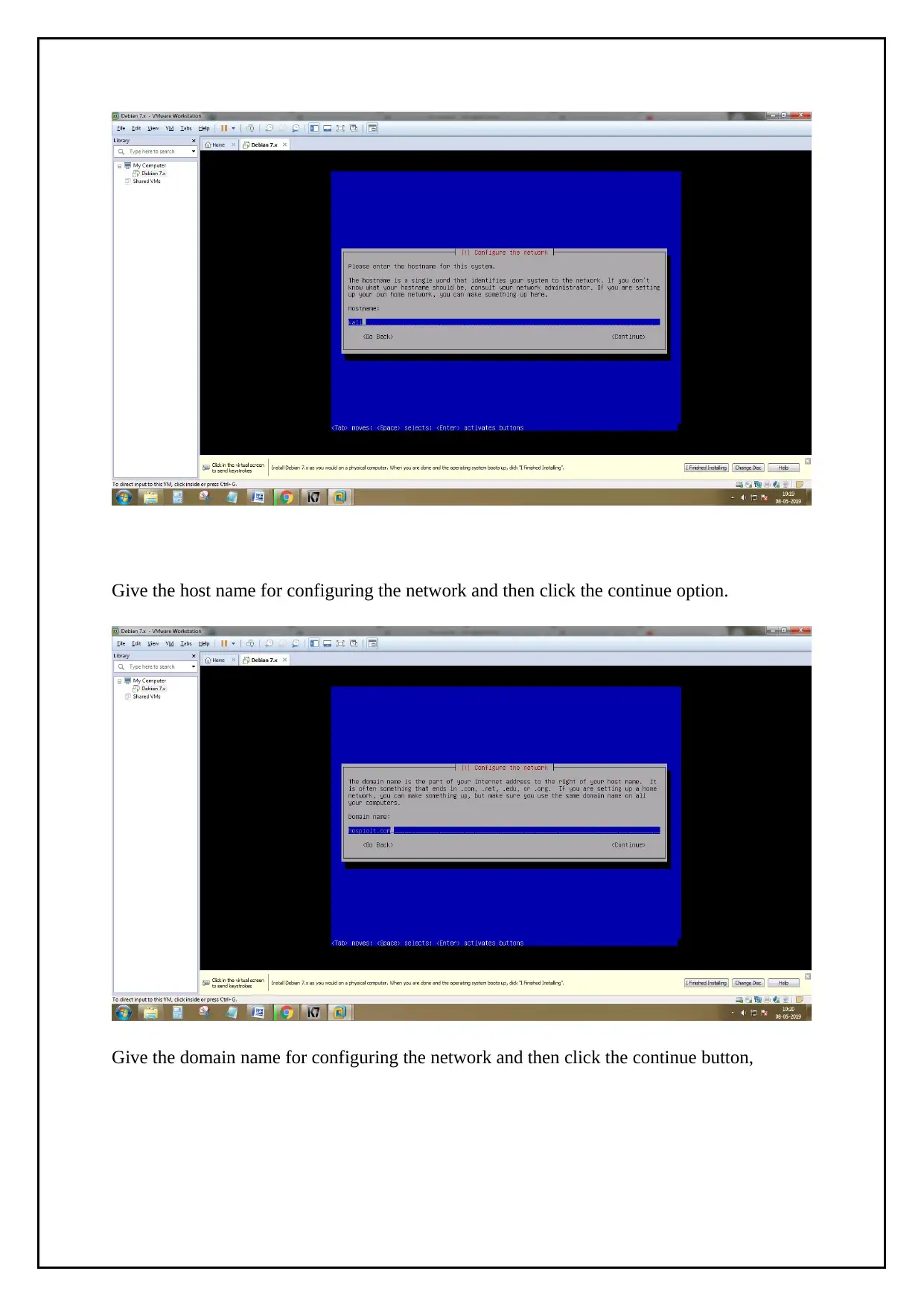
Give the host name for configuring the network and then click the continue option.
Give the domain name for configuring the network and then click the continue button,
Give the domain name for configuring the network and then click the continue button,
Set the root password and click the continue button.
Again re-enter the password and then click the continue button.
Again re-enter the password and then click the continue button.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 42
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


