This vulnerability allows the attackers
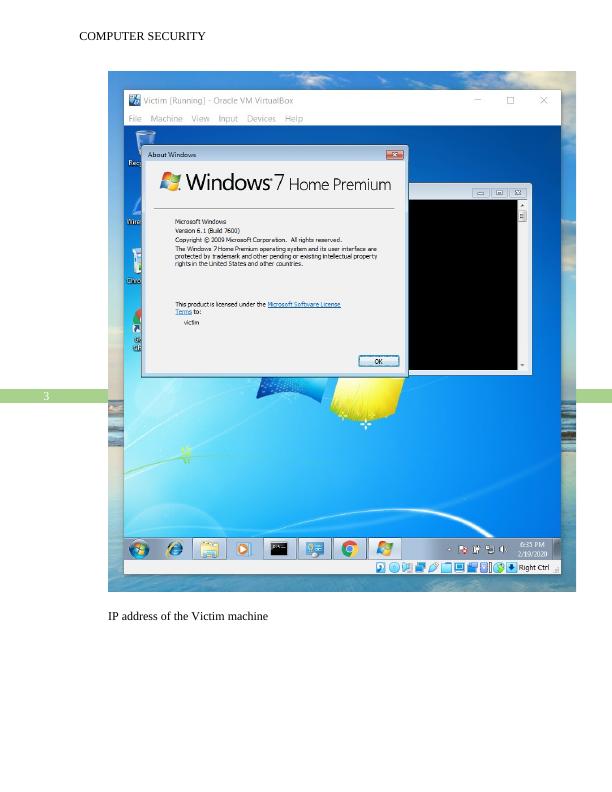
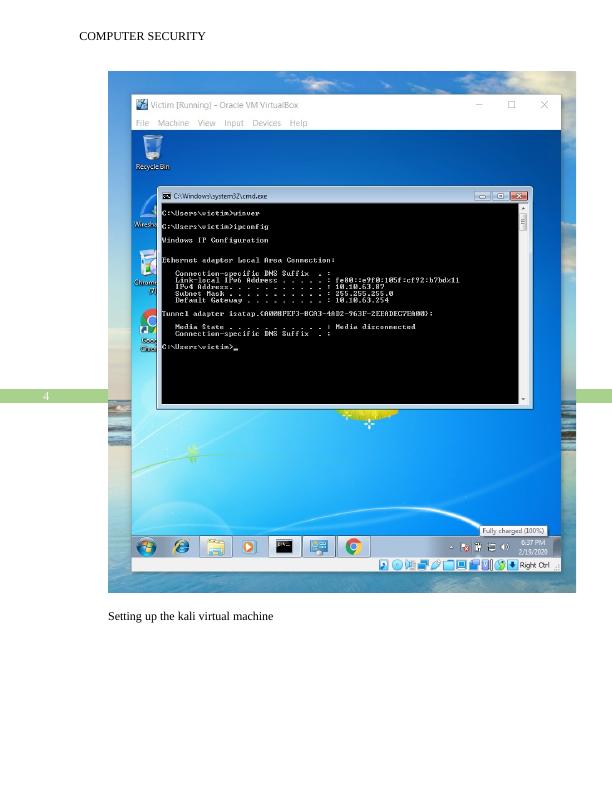
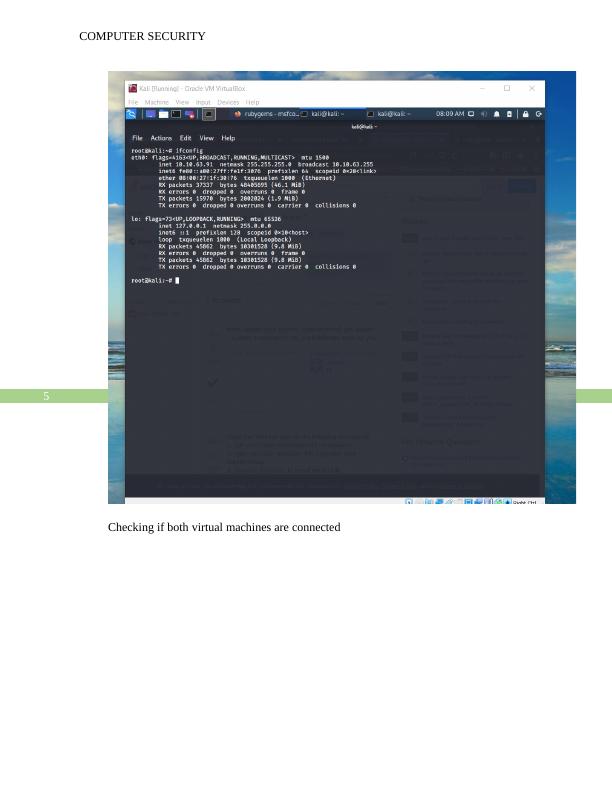
Simulate a MITM attack (ARP Poisoning) using Kali Linux and another VM. Include a detailed description complete with screenshots of how you achieved the task. A working presentation of your solution is also required.
21 Pages1135 Words15 Views
Added on 2022-08-24
This vulnerability allows the attackers
Simulate a MITM attack (ARP Poisoning) using Kali Linux and another VM. Include a detailed description complete with screenshots of how you achieved the task. A working presentation of your solution is also required.
Added on 2022-08-24
ShareRelated Documents
End of preview
Want to access all the pages? Upload your documents or become a member.
Conducting Vulnerability on Windows XP-SP2 System using Nessus and Metasploit
|42
|2354
|77
CVE-2017-0144 Vulnerability and EternalBlue Exploit: Risk Assessment and Preventative Measures
|10
|1104
|258
EternalBlue Exploit: Demonstration and Risk Assessment
|15
|2257
|268
Network Vulnerability And Cyber Security
|15
|1453
|15
Analysis of Security Vulnerability of WidgetsInc Virtual Machine Image
|23
|3636
|97
Kali Linux Exploit using Metasploit for Windows OS
|4
|820
|500