Computer Systems Architecture
VerifiedAdded on 2023/01/09
|13
|3589
|80
AI Summary
This document provides an overview of computer systems architecture, including the relationships between hardware and network addresses, setup and configuration of hardware and software systems for network connectivity, troubleshooting methods, and maintenance activities. It also includes information on network devices and components. Study material and solved assignments on this topic are available on Desklib.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Computer Systems
Architecture
Architecture
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
INTRODUCTION ..........................................................................................................................1
TASK 3............................................................................................................................................1
P5. Explain the relationships between hardware and network addresses including their use
with regards to networking devices and components.................................................................1
P6. Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity.........................................................................................3
TASK 4............................................................................................................................................4
P7. Use information gathering methods to assess, troubleshoot and document solutions to a
number of different technical hardware, software and networking issues..................................4
P8. Conduct and document a range of maintenance activities with regards to computer
hardware and software................................................................................................................4
CONCLUSION................................................................................................................................4
REFERENCES................................................................................................................................5
INTRODUCTION ..........................................................................................................................1
TASK 3............................................................................................................................................1
P5. Explain the relationships between hardware and network addresses including their use
with regards to networking devices and components.................................................................1
P6. Setup, configure and document appropriate hardware and software systems to establish
computer based network connectivity.........................................................................................3
TASK 4............................................................................................................................................4
P7. Use information gathering methods to assess, troubleshoot and document solutions to a
number of different technical hardware, software and networking issues..................................4
P8. Conduct and document a range of maintenance activities with regards to computer
hardware and software................................................................................................................4
CONCLUSION................................................................................................................................4
REFERENCES................................................................................................................................5

INTRODUCTION
A computer system is considered as the nutshell as it include looking back to the timeline
of the computer evolution over the decades. A computer is a machine which is instructed in
terms of carrying out the significant sequence of logical operations automatically through
computer programming. These programmes include computers in terms of performing wide
range of task as it include hardware, operating system, software and other concerning
equipments that are used for the further operations and referred as the computer system (Lao and
et. al., 2020). It is a programmable device which automatically perform prominent sequence of
calculations and other operations as it can store, process, retrieve and process data as per the
internal instructions. The report is going to cover the relationship among hardware and network
address including their usage concerning the networking devices and also setup, configure and
document hardware and software system for the effectively developing computer based network.
Furthermore, it also use the prominent information of collecting various methods to assess and
document solutions to the number of various technical hardware and other networking issues.
Lastly, it conduct a range of care activities for computer.
TASK 3
P5. Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components
Network communication technology include ICT network which consider explanation of
various technologies like intranet, internet and extranet. For this, it leads to include various
network protocols that deliver reliable and fast communication over large distances. As computer
system relies on the networks on the repeatable operations in terms of maintaining network
integrity for executing transfer protocol models that forces information to adhere to primary
rules. Few network protocols are mentioned below:
TCP/IP Protocol: This protocol represents the significant activities that are used as the
protocol stack as by resembling the OSI, TCP/IP work on its own particular manner. In terms of
this, IP refers to the internet protocol of data transmission in which data is separated into units of
data and also sent over the routing information that direct to the destination (Dickerson and
Mavris, 2016). Along with this, TCP depicts the transmission control protocol that develop
1
A computer system is considered as the nutshell as it include looking back to the timeline
of the computer evolution over the decades. A computer is a machine which is instructed in
terms of carrying out the significant sequence of logical operations automatically through
computer programming. These programmes include computers in terms of performing wide
range of task as it include hardware, operating system, software and other concerning
equipments that are used for the further operations and referred as the computer system (Lao and
et. al., 2020). It is a programmable device which automatically perform prominent sequence of
calculations and other operations as it can store, process, retrieve and process data as per the
internal instructions. The report is going to cover the relationship among hardware and network
address including their usage concerning the networking devices and also setup, configure and
document hardware and software system for the effectively developing computer based network.
Furthermore, it also use the prominent information of collecting various methods to assess and
document solutions to the number of various technical hardware and other networking issues.
Lastly, it conduct a range of care activities for computer.
TASK 3
P5. Explain the relationships between hardware and network addresses including their use with
regards to networking devices and components
Network communication technology include ICT network which consider explanation of
various technologies like intranet, internet and extranet. For this, it leads to include various
network protocols that deliver reliable and fast communication over large distances. As computer
system relies on the networks on the repeatable operations in terms of maintaining network
integrity for executing transfer protocol models that forces information to adhere to primary
rules. Few network protocols are mentioned below:
TCP/IP Protocol: This protocol represents the significant activities that are used as the
protocol stack as by resembling the OSI, TCP/IP work on its own particular manner. In terms of
this, IP refers to the internet protocol of data transmission in which data is separated into units of
data and also sent over the routing information that direct to the destination (Dickerson and
Mavris, 2016). Along with this, TCP depicts the transmission control protocol that develop
1

significant connections and send data concerning the receipt of information and the receiver
notifies the sender regarding the information that remain intact.
UDP: It refers to the User Datagram protocol which is used as the transport layer and the
application developers use UDP at the place of TCP. It is the scaled down economy model and it
does not offer prominent bells and signal of TCP as it does a very good job for transporting
information which does not need reliable delivery and also use far fewer network resources. It is
also undertaken as the unreliable transport protocol that sends segments over the network and
also forget about other networks and also permit for the acknowledgement of safe arrival.
OSI Protocol task: This model of network data moves from one computer to another in
terms of succeeding the layers of computer software. Moreover, this model set up the prominent
system of layers including physical layer of wires and electricity at the lowermost section. In
terms of this, when an individual send data over the network, it moves down to the heap by each
layer acquiring several data headers, address the information and security checking devices at
every level before reaching over the physical medium (Hwang and Jotwani, 2016).
ICMP: It refers to the Internet Control Message Protocol that leads to support protocol
for the internet suite and also used by network devices considering routers to send fault messages
and other operational information that indicate towards the success and failure in terms of
communicating with another IP address. It differs from the transport protocols including TCP
and UDP which is not used to exchange information and data among systems and also regularly
employed by end user network applications.
Relationship between Hardware and network address
An IP address is the unique set of numbers that leads to examine the device which is
connected to the internet in order to understand that from where the address come and also
understand that how it works. It is a bunch of various networks that are connected together and
also work together in terms of purchasing a services from an ISP as it connect ISP network from
all other networks (Firouzi and et. al., 2018). On the other hand, MAC address examines the
unique network interface within the device as the IP addresses are delegated by the ISPs that can
be re-assigned to other devices that connect and disconnect to its addresses and tied to the
physical adapter. Moreover, both of these work together and interlinked with each other for the
effective use of transport data from one to another network by using prominent TCP/IP protocol
and MAC deliver data to the significant devices on the network.
2
notifies the sender regarding the information that remain intact.
UDP: It refers to the User Datagram protocol which is used as the transport layer and the
application developers use UDP at the place of TCP. It is the scaled down economy model and it
does not offer prominent bells and signal of TCP as it does a very good job for transporting
information which does not need reliable delivery and also use far fewer network resources. It is
also undertaken as the unreliable transport protocol that sends segments over the network and
also forget about other networks and also permit for the acknowledgement of safe arrival.
OSI Protocol task: This model of network data moves from one computer to another in
terms of succeeding the layers of computer software. Moreover, this model set up the prominent
system of layers including physical layer of wires and electricity at the lowermost section. In
terms of this, when an individual send data over the network, it moves down to the heap by each
layer acquiring several data headers, address the information and security checking devices at
every level before reaching over the physical medium (Hwang and Jotwani, 2016).
ICMP: It refers to the Internet Control Message Protocol that leads to support protocol
for the internet suite and also used by network devices considering routers to send fault messages
and other operational information that indicate towards the success and failure in terms of
communicating with another IP address. It differs from the transport protocols including TCP
and UDP which is not used to exchange information and data among systems and also regularly
employed by end user network applications.
Relationship between Hardware and network address
An IP address is the unique set of numbers that leads to examine the device which is
connected to the internet in order to understand that from where the address come and also
understand that how it works. It is a bunch of various networks that are connected together and
also work together in terms of purchasing a services from an ISP as it connect ISP network from
all other networks (Firouzi and et. al., 2018). On the other hand, MAC address examines the
unique network interface within the device as the IP addresses are delegated by the ISPs that can
be re-assigned to other devices that connect and disconnect to its addresses and tied to the
physical adapter. Moreover, both of these work together and interlinked with each other for the
effective use of transport data from one to another network by using prominent TCP/IP protocol
and MAC deliver data to the significant devices on the network.
2
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Network devices and components
Router: It is undertaken as the hardware device which is useful in terms of connecting to
LAN with the internet connection and also used to receive, identify and forward the incoming
packets to other network
s. It works as the network layer which include 3 layers of the OSI model and also forward on the
basis of information which is available in routing table. It also determine the best suited path
from the available paths for the effective transmission of bundle. Router is more secure, reliable,
enhances the overall performance for the network and also has effective network range.
Switch: It is the hardware devices that connects with various devices and contain
advanced features instead of Hub. It contain the updated table the leads to decide about the data
is transmitted or not (Sharma and Park, 2018). It delivers about the message for the correct
destination which is based on physical address that present at the incoming message. It does not
broadcast the message to the entire network just like Hub. Switch leads to determine the device
regarding the message which is to be transmitted.
P6. Setup, configure and document appropriate hardware and software systems to establish
computer- based network connectivity
For this, first of all thee is requirement of setting up two computers or more than two
computers with basic components that are: motherboard, memory, processor, power supply,
keyboard, hard disk, monitor and mouse.
All the computers should have one switch so that packets can be routed between two
computers. Switch will also help in connecting both the system together. Connection between
all the system should be made. Similarly, other computers should be connected and with the
help of routers all the other computers can be connected to each other. In this, all the
switches can be connected to router.
3
Router: It is undertaken as the hardware device which is useful in terms of connecting to
LAN with the internet connection and also used to receive, identify and forward the incoming
packets to other network
s. It works as the network layer which include 3 layers of the OSI model and also forward on the
basis of information which is available in routing table. It also determine the best suited path
from the available paths for the effective transmission of bundle. Router is more secure, reliable,
enhances the overall performance for the network and also has effective network range.
Switch: It is the hardware devices that connects with various devices and contain
advanced features instead of Hub. It contain the updated table the leads to decide about the data
is transmitted or not (Sharma and Park, 2018). It delivers about the message for the correct
destination which is based on physical address that present at the incoming message. It does not
broadcast the message to the entire network just like Hub. Switch leads to determine the device
regarding the message which is to be transmitted.
P6. Setup, configure and document appropriate hardware and software systems to establish
computer- based network connectivity
For this, first of all thee is requirement of setting up two computers or more than two
computers with basic components that are: motherboard, memory, processor, power supply,
keyboard, hard disk, monitor and mouse.
All the computers should have one switch so that packets can be routed between two
computers. Switch will also help in connecting both the system together. Connection between
all the system should be made. Similarly, other computers should be connected and with the
help of routers all the other computers can be connected to each other. In this, all the
switches can be connected to router.
3
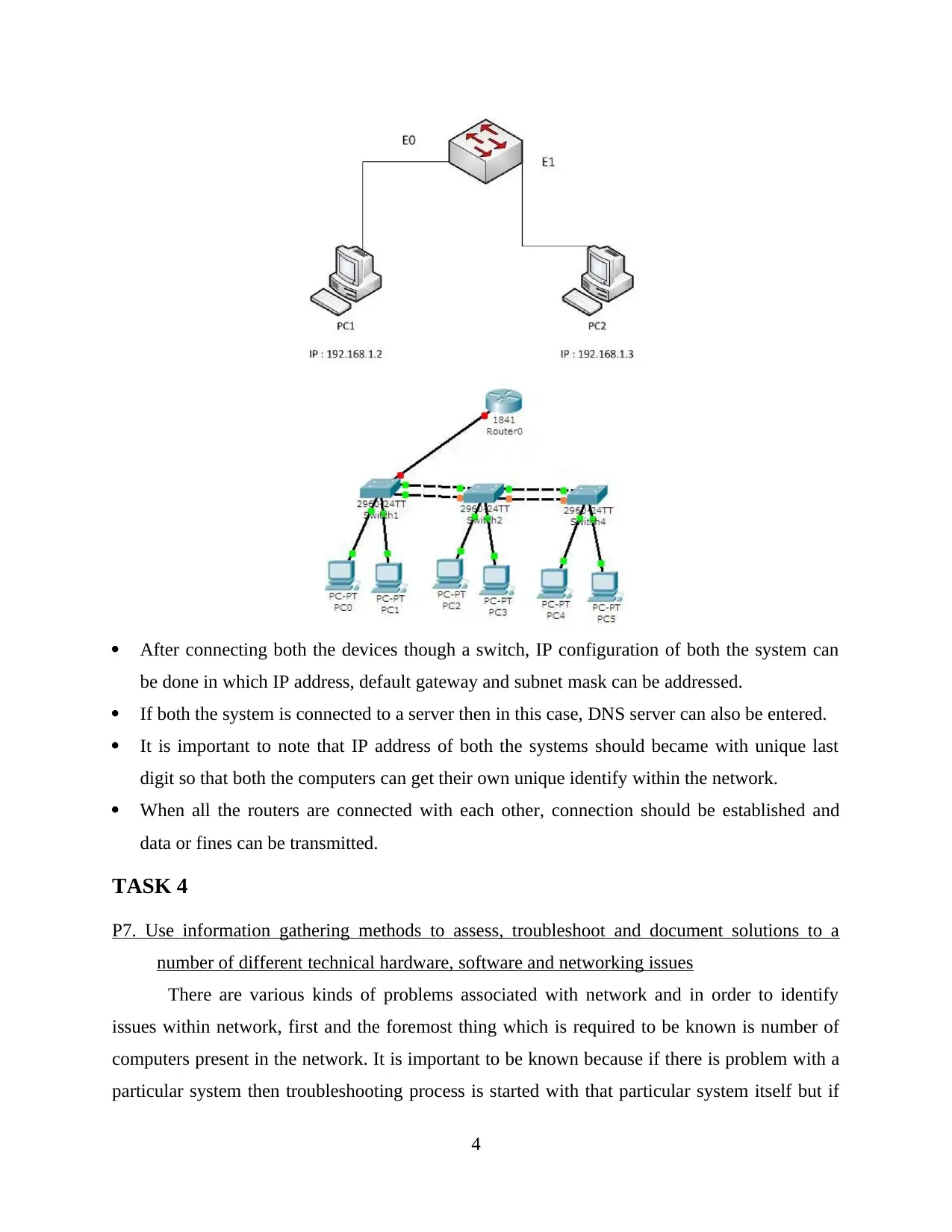
After connecting both the devices though a switch, IP configuration of both the system can
be done in which IP address, default gateway and subnet mask can be addressed.
If both the system is connected to a server then in this case, DNS server can also be entered.
It is important to note that IP address of both the systems should became with unique last
digit so that both the computers can get their own unique identify within the network.
When all the routers are connected with each other, connection should be established and
data or fines can be transmitted.
TASK 4
P7. Use information gathering methods to assess, troubleshoot and document solutions to a
number of different technical hardware, software and networking issues
There are various kinds of problems associated with network and in order to identify
issues within network, first and the foremost thing which is required to be known is number of
computers present in the network. It is important to be known because if there is problem with a
particular system then troubleshooting process is started with that particular system itself but if
4
be done in which IP address, default gateway and subnet mask can be addressed.
If both the system is connected to a server then in this case, DNS server can also be entered.
It is important to note that IP address of both the systems should became with unique last
digit so that both the computers can get their own unique identify within the network.
When all the routers are connected with each other, connection should be established and
data or fines can be transmitted.
TASK 4
P7. Use information gathering methods to assess, troubleshoot and document solutions to a
number of different technical hardware, software and networking issues
There are various kinds of problems associated with network and in order to identify
issues within network, first and the foremost thing which is required to be known is number of
computers present in the network. It is important to be known because if there is problem with a
particular system then troubleshooting process is started with that particular system itself but if
4

problem is associated all the system on the network then trouble shotting process stats at the
system where all the systems are connected.
So, first method of gathering information is to identify system where problem is
occurring so that network administrator can identify point from where troubleshooting is
required to be started, so that timely solution can be idented.
It is also important for network administrator to adopt a logical sequential method of
diagnosing problem So that solution for the same can be identified and problem can be resolved
easily. Adopting a logical and sequential method helps in identifying whether the problem is in
hardware or software. Or is there any kind of issues on connectivity.
First step is to collect relevant data for identification of starting point of troubleshot. This
helps the network administrator to identify to identify next step towards identification of
issue and resolving it.
Next step is to check most common problem that can occur because of which network issue
can be generated. First is to check all the cables because if there is any weak connection in
cables then network issue can arise and in this situation by simply resolving cable
connectivity, issue can be resolved. This can also be resolved by removing and connecting
cables again. Another most common problem is invalid IP addressed that can be simply
resolved by checking and correcting IP addresses or by repairing or reactivating network
connection.
If the problem is still not resolved then next step is to gather information about software and
hard ware. Checking hardware connections in order to make sure the connection properly and
turn it on for effective working. It could become the prominent problem behind the
networking issues as there is no point to go through with the process of troubleshooting
network issues and also make sure the prominent switches that are at correct position.
Next step is to ping one’s own network card or by pinging another computer from same
network. If rely comes then there is no problem but id waiting time is too long or there is no
reply then the problem is in the particular system from which reply is not coming back.
Above steps can help in resolve most of the errors or issues in network easily. but despite of
these steps if the problem is not resolved then in this case senior network administrators can be
contracted for further review of problem and for resolving the issue.
5
system where all the systems are connected.
So, first method of gathering information is to identify system where problem is
occurring so that network administrator can identify point from where troubleshooting is
required to be started, so that timely solution can be idented.
It is also important for network administrator to adopt a logical sequential method of
diagnosing problem So that solution for the same can be identified and problem can be resolved
easily. Adopting a logical and sequential method helps in identifying whether the problem is in
hardware or software. Or is there any kind of issues on connectivity.
First step is to collect relevant data for identification of starting point of troubleshot. This
helps the network administrator to identify to identify next step towards identification of
issue and resolving it.
Next step is to check most common problem that can occur because of which network issue
can be generated. First is to check all the cables because if there is any weak connection in
cables then network issue can arise and in this situation by simply resolving cable
connectivity, issue can be resolved. This can also be resolved by removing and connecting
cables again. Another most common problem is invalid IP addressed that can be simply
resolved by checking and correcting IP addresses or by repairing or reactivating network
connection.
If the problem is still not resolved then next step is to gather information about software and
hard ware. Checking hardware connections in order to make sure the connection properly and
turn it on for effective working. It could become the prominent problem behind the
networking issues as there is no point to go through with the process of troubleshooting
network issues and also make sure the prominent switches that are at correct position.
Next step is to ping one’s own network card or by pinging another computer from same
network. If rely comes then there is no problem but id waiting time is too long or there is no
reply then the problem is in the particular system from which reply is not coming back.
Above steps can help in resolve most of the errors or issues in network easily. but despite of
these steps if the problem is not resolved then in this case senior network administrators can be
contracted for further review of problem and for resolving the issue.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
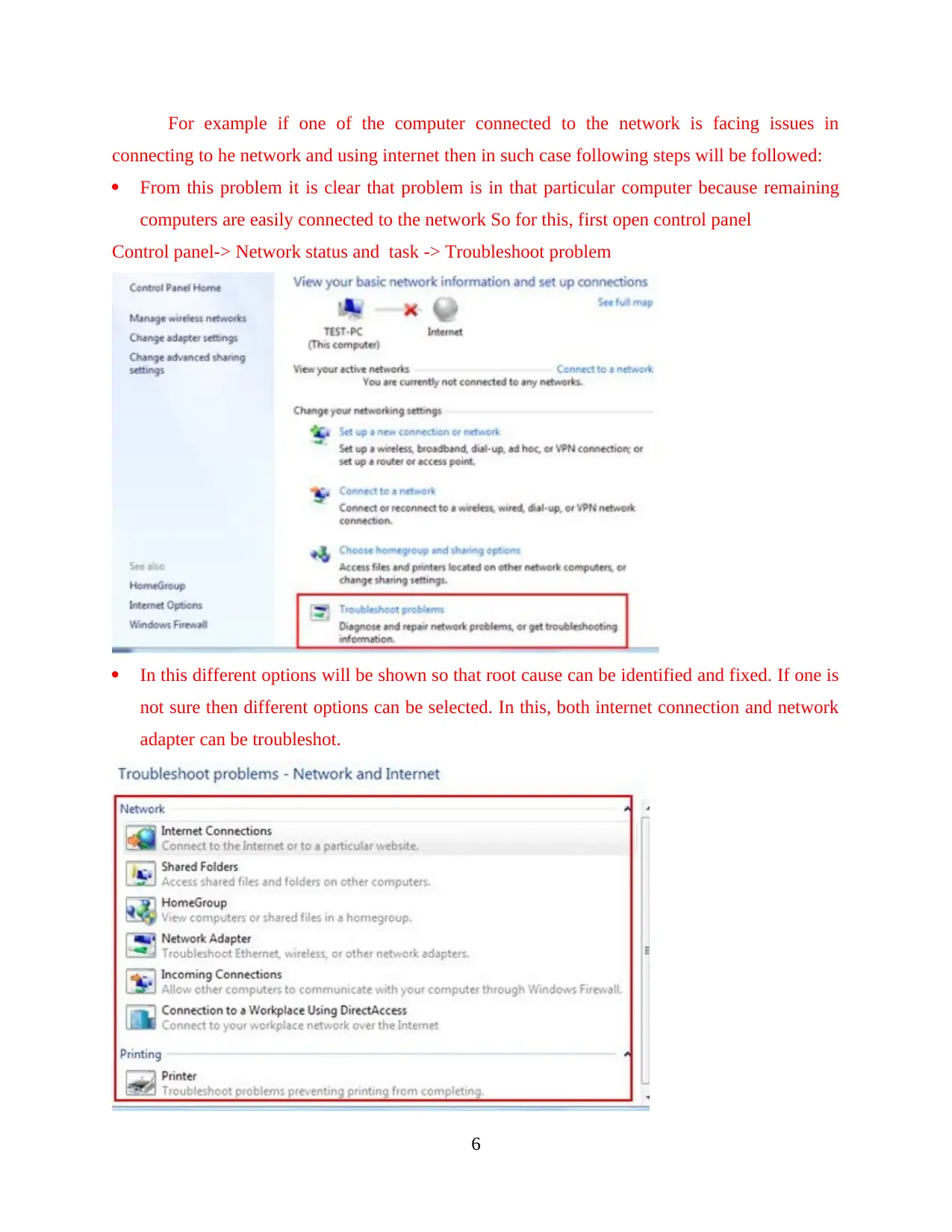
For example if one of the computer connected to the network is facing issues in
connecting to he network and using internet then in such case following steps will be followed:
From this problem it is clear that problem is in that particular computer because remaining
computers are easily connected to the network So for this, first open control panel
Control panel-> Network status and task -> Troubleshoot problem
In this different options will be shown so that root cause can be identified and fixed. If one is
not sure then different options can be selected. In this, both internet connection and network
adapter can be troubleshot.
6
connecting to he network and using internet then in such case following steps will be followed:
From this problem it is clear that problem is in that particular computer because remaining
computers are easily connected to the network So for this, first open control panel
Control panel-> Network status and task -> Troubleshoot problem
In this different options will be shown so that root cause can be identified and fixed. If one is
not sure then different options can be selected. In this, both internet connection and network
adapter can be troubleshot.
6
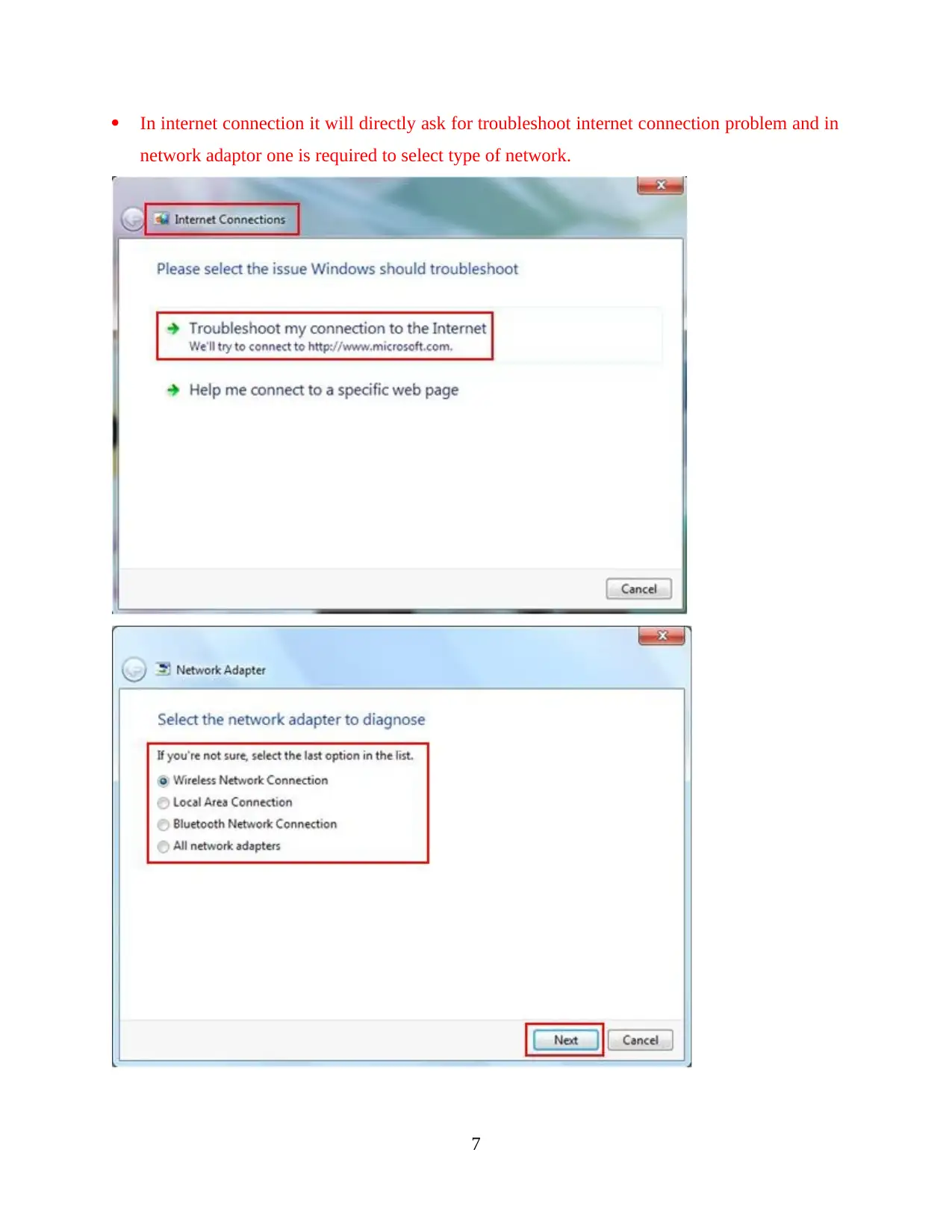
In internet connection it will directly ask for troubleshoot internet connection problem and in
network adaptor one is required to select type of network.
7
network adaptor one is required to select type of network.
7

This troubleshooting will most probably resolve the problem and if not then IP address can
be checked.
P8. Conduct and document a range of maintenance activities with regards to computer hardware
and software
The effective management of hardware and software become more complex for the
corporate running for small number of applications. It depicts the complexity which leads to
increase the number of corporate users working on the road and remote areas for effective
management system. Moreover, it include the effective diagnostic and troubleshooting skills that
describe various ways for improvement like availability of heuristic which contains thinking for
the actual cause, confirmation bias that cause response for time metric for the evidence of
problem and so on. In terms of improving the troubleshooting skills, it is important to aware, get
feedback, practice, consider data and also identify what is happening. For this, an individual need
to consider data, identify and aware about the biases and other challenges for troubleshooting in
order to get problem solve much faster with better accuracy. Moreover, the future of IT
troubleshooting is based on analytical approaches.
Information gathering methods and techniques
System document: It depicts the system which is used in terms of receiving, tracking,
managing and storing documents for the elimination of paper. In terms of this, it is quite capable
in terms of keeping record for several versions that are created and modified by various users.
For this, the digital documents of management is based on computer programs (Benhlima, 2018).
As this term has some overlap with the prominent concept of content management system. It is
also viewed as the component of enterprise content management which is related with digital
asset management, document imagining, effective workflow system and recording management
systems.
User information: It include significant user related information which is duplication of
IP addresses for quickly fixing the issues and taking preventive measures. Exhaustion of IP
address as it use ipconfig command for the troubleshoot problem and other factors (Madhavan
and et. al., 2018). For this, at the time of network troubleshooting it is important to undertake
various informations for effective networking field which is important for the number of tools as
it is used for troubleshoot for the variety of several network conditions. In terms of this, specific
8
be checked.
P8. Conduct and document a range of maintenance activities with regards to computer hardware
and software
The effective management of hardware and software become more complex for the
corporate running for small number of applications. It depicts the complexity which leads to
increase the number of corporate users working on the road and remote areas for effective
management system. Moreover, it include the effective diagnostic and troubleshooting skills that
describe various ways for improvement like availability of heuristic which contains thinking for
the actual cause, confirmation bias that cause response for time metric for the evidence of
problem and so on. In terms of improving the troubleshooting skills, it is important to aware, get
feedback, practice, consider data and also identify what is happening. For this, an individual need
to consider data, identify and aware about the biases and other challenges for troubleshooting in
order to get problem solve much faster with better accuracy. Moreover, the future of IT
troubleshooting is based on analytical approaches.
Information gathering methods and techniques
System document: It depicts the system which is used in terms of receiving, tracking,
managing and storing documents for the elimination of paper. In terms of this, it is quite capable
in terms of keeping record for several versions that are created and modified by various users.
For this, the digital documents of management is based on computer programs (Benhlima, 2018).
As this term has some overlap with the prominent concept of content management system. It is
also viewed as the component of enterprise content management which is related with digital
asset management, document imagining, effective workflow system and recording management
systems.
User information: It include significant user related information which is duplication of
IP addresses for quickly fixing the issues and taking preventive measures. Exhaustion of IP
address as it use ipconfig command for the troubleshoot problem and other factors (Madhavan
and et. al., 2018). For this, at the time of network troubleshooting it is important to undertake
various informations for effective networking field which is important for the number of tools as
it is used for troubleshoot for the variety of several network conditions. In terms of this, specific
8
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

tools are useful that are subjective and discretion for the effective selection of tools as it based on
generality and common use.
Error codes: At the time of doing computer programming an error code is occur in the
numbered or alphanumeric code as it is determined as the nature of the error and why it is
occurred. In C programming, it is mostly seen as many error codes are defined under the header
file shown as <error.h>. Moreover, it is also found in consumer electronics and other devices for
the effective attempt to do something (Xu, Lin and Yu, 2017). They also passed off to the error
handlers as it leads to determine about the actions that should be taken.
Error messages: It is undertaken as the message for the information display and it occurs
at the time of unforeseen problem occurs. These messages are used when the user intervention is
needed for the effective indication to desired operation and also relay on important warnings.
These messages are widely seen throughout computing and also a part of every operating system.
Computer maintenance checklist
It include various steps for the effective implementation and also try to improve the
overall performance of computer and its steps are as follows:
Update the anti-virus that depend on the program which run on the screen and also clear
regarding the prominent instructions.
Undertake anti-virus programs as there are various options for the spyware and the
removal of software undertaking super antispyware and malware bytes pro.
It is also important to empty the recycle bin and it is effectively done with the Ccleaner.
Scan the significant disk and running application for the software clean up in order to
remove unwanted data that tends to occur error messages and codes.
Again defragment the program in order to free up the windows with the help of disk clean
up.
Configure the system and start up that tends to run automatically when you switch the
computer on.
Regularly check the windows and its updates and plug in for the basic applications.
Check file and its back up plan in order to create system recovery disk as if it is
applicable.
Clean the internal function of computer and its parts in order to maintain its temperature.
Maintenance guide to defragment hard drive
9
generality and common use.
Error codes: At the time of doing computer programming an error code is occur in the
numbered or alphanumeric code as it is determined as the nature of the error and why it is
occurred. In C programming, it is mostly seen as many error codes are defined under the header
file shown as <error.h>. Moreover, it is also found in consumer electronics and other devices for
the effective attempt to do something (Xu, Lin and Yu, 2017). They also passed off to the error
handlers as it leads to determine about the actions that should be taken.
Error messages: It is undertaken as the message for the information display and it occurs
at the time of unforeseen problem occurs. These messages are used when the user intervention is
needed for the effective indication to desired operation and also relay on important warnings.
These messages are widely seen throughout computing and also a part of every operating system.
Computer maintenance checklist
It include various steps for the effective implementation and also try to improve the
overall performance of computer and its steps are as follows:
Update the anti-virus that depend on the program which run on the screen and also clear
regarding the prominent instructions.
Undertake anti-virus programs as there are various options for the spyware and the
removal of software undertaking super antispyware and malware bytes pro.
It is also important to empty the recycle bin and it is effectively done with the Ccleaner.
Scan the significant disk and running application for the software clean up in order to
remove unwanted data that tends to occur error messages and codes.
Again defragment the program in order to free up the windows with the help of disk clean
up.
Configure the system and start up that tends to run automatically when you switch the
computer on.
Regularly check the windows and its updates and plug in for the basic applications.
Check file and its back up plan in order to create system recovery disk as if it is
applicable.
Clean the internal function of computer and its parts in order to maintain its temperature.
Maintenance guide to defragment hard drive
9

In by typing "Defragment and Optimize Drives" into search bar and selecting the resulting
program disk can be defragmented.
When the program open analyze each and every drive on the list by selecting it and clicking
"Analyze".
If even a slightest level of fragmentation occur then select that drive once again and click
"Optimize".
Maintenance guide for cleaning a laptop
In order to clean a laptop a dry cloth ca be used and dusted from keyboard area and other
areas but away from electric components. Dry cloth can also be used to clean laptop screen
as well.
Cables like network cable, charger cable should be managed problems and tied properly so
that cables are together and not jumbled up.
CONCLUSION
From the preceding information, it is analysed that computer system is prominently a
machine that leads to simplify the complicated task. Moreover, it leads to increase the overall
performance and leads to eliminate cost for the effective power consumption. In the above
report, various protocols and effective network devices are discussed. It also depicts the
significant topologies and represent the effective use of information gathering methods. Lastly, it
represent the information gathering techniques and methods that are used at the time of
troubleshooting.
10
program disk can be defragmented.
When the program open analyze each and every drive on the list by selecting it and clicking
"Analyze".
If even a slightest level of fragmentation occur then select that drive once again and click
"Optimize".
Maintenance guide for cleaning a laptop
In order to clean a laptop a dry cloth ca be used and dusted from keyboard area and other
areas but away from electric components. Dry cloth can also be used to clean laptop screen
as well.
Cables like network cable, charger cable should be managed problems and tied properly so
that cables are together and not jumbled up.
CONCLUSION
From the preceding information, it is analysed that computer system is prominently a
machine that leads to simplify the complicated task. Moreover, it leads to increase the overall
performance and leads to eliminate cost for the effective power consumption. In the above
report, various protocols and effective network devices are discussed. It also depicts the
significant topologies and represent the effective use of information gathering methods. Lastly, it
represent the information gathering techniques and methods that are used at the time of
troubleshooting.
10

REFERENCES
Books and Journals
Ahmadi, A and et. al., 2018, June. Evolution of 3C cyber-physical systems architecture for
industry 4.0. In International Workshop on Service Orientation in Holonic and Multi-
Agent Manufacturing (pp. 448-459). Springer, Cham.
Benhlima, L., 2018. Big data management for healthcare systems: architecture, requirements,
and implementation. Advances in bioinformatics, 2018.
Bondar, S and et. al., 2017. Agile digital transformation of System-of-Systems architecture
models using Zachman framework. Journal of Industrial Information Integration, 7,
pp.33-43.
Dickerson, C. and Mavris, D.N., 2016. Architecture and principles of systems engineering. CRC
Press.
Firouzi, F and et. al., 2018. Internet-of-Things and big data for smarter healthcare: From device
to architecture, applications and analytics.
Hwang, K. and Jotwani, N., 2016. Advanced computer architecture, 3e. McGraw-Hill
Education.
Jiang, J.R., 2018. An improved cyber-physical systems architecture for Industry 4.0 smart
factories. Advances in Mechanical Engineering, 10(6), p.1687814018784192.
Lao, L and et. al., 2020. A survey of IoT applications in blockchain systems: Architecture,
consensus, and traffic modeling. ACM Computing Surveys (CSUR), 53(1), pp.1-32.
Madhavan, G and et. al., 2018. Vision for a systems architecture to integrate and transform
population health. Proceedings of the National Academy of Sciences, 115(50),
pp.12595-12602.
Sharma, P.K. and Park, J.H., 2018. Blockchain based hybrid network architecture for the smart
city. Future Generation Computer Systems, 86, pp.650-655.
Siewiorek, D. and Swarz, R., 2017. Reliable computer systems: design and evaluatuion. Digital
Press.
Wells, C.C. and Wells, K., Tornaditech LLC, 2017. Multimedia teleconference streaming
architecture between heterogeneous computer systems. U.S. Patent Application
14/833,141.
Xu, H., Lin, J. and Yu, W., 2017. Smart Transportation Systems: Architecture, Enabling
Technologies, and Open Issues. In Secure and Trustworthy Transportation Cyber-
Physical Systems (pp. 23-49). Springer, Singapore.
11
Books and Journals
Ahmadi, A and et. al., 2018, June. Evolution of 3C cyber-physical systems architecture for
industry 4.0. In International Workshop on Service Orientation in Holonic and Multi-
Agent Manufacturing (pp. 448-459). Springer, Cham.
Benhlima, L., 2018. Big data management for healthcare systems: architecture, requirements,
and implementation. Advances in bioinformatics, 2018.
Bondar, S and et. al., 2017. Agile digital transformation of System-of-Systems architecture
models using Zachman framework. Journal of Industrial Information Integration, 7,
pp.33-43.
Dickerson, C. and Mavris, D.N., 2016. Architecture and principles of systems engineering. CRC
Press.
Firouzi, F and et. al., 2018. Internet-of-Things and big data for smarter healthcare: From device
to architecture, applications and analytics.
Hwang, K. and Jotwani, N., 2016. Advanced computer architecture, 3e. McGraw-Hill
Education.
Jiang, J.R., 2018. An improved cyber-physical systems architecture for Industry 4.0 smart
factories. Advances in Mechanical Engineering, 10(6), p.1687814018784192.
Lao, L and et. al., 2020. A survey of IoT applications in blockchain systems: Architecture,
consensus, and traffic modeling. ACM Computing Surveys (CSUR), 53(1), pp.1-32.
Madhavan, G and et. al., 2018. Vision for a systems architecture to integrate and transform
population health. Proceedings of the National Academy of Sciences, 115(50),
pp.12595-12602.
Sharma, P.K. and Park, J.H., 2018. Blockchain based hybrid network architecture for the smart
city. Future Generation Computer Systems, 86, pp.650-655.
Siewiorek, D. and Swarz, R., 2017. Reliable computer systems: design and evaluatuion. Digital
Press.
Wells, C.C. and Wells, K., Tornaditech LLC, 2017. Multimedia teleconference streaming
architecture between heterogeneous computer systems. U.S. Patent Application
14/833,141.
Xu, H., Lin, J. and Yu, W., 2017. Smart Transportation Systems: Architecture, Enabling
Technologies, and Open Issues. In Secure and Trustworthy Transportation Cyber-
Physical Systems (pp. 23-49). Springer, Singapore.
11
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





