QAC020N253: Network Design and Troubleshooting Report Analysis
VerifiedAdded on 2022/08/17
|19
|3677
|24
Report
AI Summary
This report presents a network design and troubleshooting solution tailored for the IT company speedfix.co.uk. It begins with an introduction that outlines the company's departmental structure and server requirements, followed by an analysis of network design principles. The report then delves into the application and analysis of various network components, including switches, routers, and wireless access points, alongside the OSI model. The evaluation and judgment section focuses on network reliability, redundancy, and security measures. The design and implementation segment details the application of a hierarchical network model, VLAN configuration, and security protocols, including access control lists. Finally, the report concludes with a summary of the findings and recommendations for optimizing the network infrastructure, ensuring robust performance and security.

Running head: COMPUTING TECHNOLOGIES
Network Design and Troubleshooting
Name of the Student
Name of the University
Author’s Note
Network Design and Troubleshooting
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
COMPUTING TECHNOLOGIES
Table of Contents
Introduction......................................................................................................................................2
Knowledge and Understanding........................................................................................................2
Application and Analysis.................................................................................................................4
Evaluation and Judgement...............................................................................................................7
Design and Implementation.............................................................................................................8
Testing and Documentation...........................................................................................................12
Conclusion.....................................................................................................................................14
References......................................................................................................................................16
COMPUTING TECHNOLOGIES
Table of Contents
Introduction......................................................................................................................................2
Knowledge and Understanding........................................................................................................2
Application and Analysis.................................................................................................................4
Evaluation and Judgement...............................................................................................................7
Design and Implementation.............................................................................................................8
Testing and Documentation...........................................................................................................12
Conclusion.....................................................................................................................................14
References......................................................................................................................................16

2
COMPUTING TECHNOLOGIES
Introduction
The report is created for an IT company speedfix.co.uk for designing and implementation
of a network infrastructure. The company have four departments i.e. finance/hr, engineers, sales
and admin and the number of network device needed to be installed in each of the department for
management of their operation is needed to be identified. There are four servers that are used by
the users such as WEB, Email, DNS and a File server that is needed to be accessed by each of
the department for management of their daily operation. A network diagram is created after
analyzing the departments and the devices that are needed to be installed and an appropriate
subnet plan is needed to be created such that each of the requirements are fulfilled. For assigning
the subnet different VLANs are created and the switch is needed to be configured as VTP server
and Client such that the VLAN information are distributed with the switch (Alabady, Al-
Turjman and Din 2018). The access of the subnet for each of the VLAN is needed to be managed
following the business rules of the origination. DHCP protocol is used for configuring router
device with address pool for routinely allocating IP address the host allowed access of the
specific VLAN.
Knowledge and Understanding
In the traditional network perimeter defense technique is used for protecting the data
center and the servers from vulnerable threats and enforcing little protection from this agents.
The segmentation of the network with the implementation of VLAN helps in creation of multiple
isolated network and each of the network have broadcast domain separated. With the proper
configuration of the network the VLAN can create a barrier for the attacker to access the system
surface (Sasaki, Yokotani and Mukai 2018). The packet sniffing capabilities can also be reduced
COMPUTING TECHNOLOGIES
Introduction
The report is created for an IT company speedfix.co.uk for designing and implementation
of a network infrastructure. The company have four departments i.e. finance/hr, engineers, sales
and admin and the number of network device needed to be installed in each of the department for
management of their operation is needed to be identified. There are four servers that are used by
the users such as WEB, Email, DNS and a File server that is needed to be accessed by each of
the department for management of their daily operation. A network diagram is created after
analyzing the departments and the devices that are needed to be installed and an appropriate
subnet plan is needed to be created such that each of the requirements are fulfilled. For assigning
the subnet different VLANs are created and the switch is needed to be configured as VTP server
and Client such that the VLAN information are distributed with the switch (Alabady, Al-
Turjman and Din 2018). The access of the subnet for each of the VLAN is needed to be managed
following the business rules of the origination. DHCP protocol is used for configuring router
device with address pool for routinely allocating IP address the host allowed access of the
specific VLAN.
Knowledge and Understanding
In the traditional network perimeter defense technique is used for protecting the data
center and the servers from vulnerable threats and enforcing little protection from this agents.
The segmentation of the network with the implementation of VLAN helps in creation of multiple
isolated network and each of the network have broadcast domain separated. With the proper
configuration of the network the VLAN can create a barrier for the attacker to access the system
surface (Sasaki, Yokotani and Mukai 2018). The packet sniffing capabilities can also be reduced
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
COMPUTING TECHNOLOGIES
and thus the agents needs to put more effort for gathering information for accessing the system
components. Thus, the implementation of the VLAN increases the security, flexibility and the
mobility of the user and helps in development of an efficient network for speedfix.co.uk. The
users of the network can be assigned with a specific VLAN would be always connected to that
VLAN irrespective of the location (Owada et al. 2019). The use of the VLAN concept also helps
in creating an efficient design for the wireless network and eliminates the security constraints.
The switches that are used in the network operates on IEEE 802.1D standard at the
second layer (data link) of the OSI model. The OSI model is used as the guideline for the
manufacturers to build the interface along with other network technology. Address resolution
protocol is needed for enabling communication with the network device that is attached. An IP
address is needed to be assigned to each of the network device with a network identifier for
broadcasting the packets and getting response from the targeted device with the destination IP
address (Fujikawa et al. 2017). The switch receives the broadcast message and broadcasts to the
port expect from the port where it has received the message. The delivery of the pack can
become an issue since the broadcast of the message generates unnecessary network traffic and
causes a degradation in the network performance. An issue is also faced in the network visibility
because it cannot identify the authorization of a requesting device for establishing connection
with the targeted device. If the device exists in the network with the targeted IP address, it picks
the broadcast message and processes the message (Wong and Wan 2017). Using the MAC
address of the source present in the broadcast message a response is sent to requesting device
including the MAC address of the target.
For reducing the network traffic 802.1Q compatible switches are needed to be used since
it has the ability of segmenting the network into broadcast domains. The VLAN is needed to be
COMPUTING TECHNOLOGIES
and thus the agents needs to put more effort for gathering information for accessing the system
components. Thus, the implementation of the VLAN increases the security, flexibility and the
mobility of the user and helps in development of an efficient network for speedfix.co.uk. The
users of the network can be assigned with a specific VLAN would be always connected to that
VLAN irrespective of the location (Owada et al. 2019). The use of the VLAN concept also helps
in creating an efficient design for the wireless network and eliminates the security constraints.
The switches that are used in the network operates on IEEE 802.1D standard at the
second layer (data link) of the OSI model. The OSI model is used as the guideline for the
manufacturers to build the interface along with other network technology. Address resolution
protocol is needed for enabling communication with the network device that is attached. An IP
address is needed to be assigned to each of the network device with a network identifier for
broadcasting the packets and getting response from the targeted device with the destination IP
address (Fujikawa et al. 2017). The switch receives the broadcast message and broadcasts to the
port expect from the port where it has received the message. The delivery of the pack can
become an issue since the broadcast of the message generates unnecessary network traffic and
causes a degradation in the network performance. An issue is also faced in the network visibility
because it cannot identify the authorization of a requesting device for establishing connection
with the targeted device. If the device exists in the network with the targeted IP address, it picks
the broadcast message and processes the message (Wong and Wan 2017). Using the MAC
address of the source present in the broadcast message a response is sent to requesting device
including the MAC address of the target.
For reducing the network traffic 802.1Q compatible switches are needed to be used since
it has the ability of segmenting the network into broadcast domains. The VLAN is needed to be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
COMPUTING TECHNOLOGIES
assigned to the switchport for allowing access of the network device to communicate using the
VLAN (Mathov et al. 2019). The network devices that are connected with the specific switch
port can communicate with the device that are also assigned with the same VLAN but are
isolated from the ports that are not assigned with the same VLAN.
Application and Analysis
There are different network components that are used for the expansion of the network
topology and the protocols that are used for the configuration of the network is needed to be
identified for enabling operation following the requirement of the organization. The features,
purpose and functionality of the network components are needed to be evaluated for its
application (Yokotani and Kawai 2019). A wide range of network devices are available and can
be used for the configuration of the modern network. The working of the different network
devices that are needed to be used for the development of the network is given below:
Switches
Switches are used as a multiport device for improvement of network efficiency and it helps
in maintaining the limited routing info about the nodes installed in the inner network. It also
allows connection between the system and the strands of the local area network are connected
with the help of switches. The switch can be subject to denial of service attacks and thus flood
guards are needed to be used for prevention of malicious traffic which can halt the switch
(Gheisari et al. 2018). Switch port security is needed to be enforced and the unused ports are
needed to be disabled with the use of DHCP snooping, MAC address filtering and ARP
inspection.
Switch Ports
COMPUTING TECHNOLOGIES
assigned to the switchport for allowing access of the network device to communicate using the
VLAN (Mathov et al. 2019). The network devices that are connected with the specific switch
port can communicate with the device that are also assigned with the same VLAN but are
isolated from the ports that are not assigned with the same VLAN.
Application and Analysis
There are different network components that are used for the expansion of the network
topology and the protocols that are used for the configuration of the network is needed to be
identified for enabling operation following the requirement of the organization. The features,
purpose and functionality of the network components are needed to be evaluated for its
application (Yokotani and Kawai 2019). A wide range of network devices are available and can
be used for the configuration of the modern network. The working of the different network
devices that are needed to be used for the development of the network is given below:
Switches
Switches are used as a multiport device for improvement of network efficiency and it helps
in maintaining the limited routing info about the nodes installed in the inner network. It also
allows connection between the system and the strands of the local area network are connected
with the help of switches. The switch can be subject to denial of service attacks and thus flood
guards are needed to be used for prevention of malicious traffic which can halt the switch
(Gheisari et al. 2018). Switch port security is needed to be enforced and the unused ports are
needed to be disabled with the use of DHCP snooping, MAC address filtering and ARP
inspection.
Switch Ports

5
COMPUTING TECHNOLOGIES
Cables used for connecting switches and routers
Rack mounts, freestanding devices and stackable
Managed switch
Routers
It transmits the data packets to the destination by creating a path with the use of
interconnected network devices that uses different network topologies. The information of the
network are stored in the routers and it is needed to be configured with different protocols such
that packet filtering and access control list. Routers can be used with channel service for
translating LAN to WAN framing. Router can be used for dividing the network into multiple sub
network and zones can be created for independent operation (Fujikawa et al. 2018). The
communication is established by maintaining tables of the local address and the destination
address. The routers acts as the first line of defense and it is needed to be configured such that it
can only pass the data traffic authorized by the administrator of the network.
Routing and routable protocols
Dedicated hardware v/s server based routers
Network interface cards
The network interface card may be for connecting the wireless network or the Ethernet
and it has the MAC address that is used for identifying the source address and enabling
transmission of data packet in the network. The MAC address of NIC are unique and it can easily
distinguish the client connected in the network.
Wireless access points
COMPUTING TECHNOLOGIES
Cables used for connecting switches and routers
Rack mounts, freestanding devices and stackable
Managed switch
Routers
It transmits the data packets to the destination by creating a path with the use of
interconnected network devices that uses different network topologies. The information of the
network are stored in the routers and it is needed to be configured with different protocols such
that packet filtering and access control list. Routers can be used with channel service for
translating LAN to WAN framing. Router can be used for dividing the network into multiple sub
network and zones can be created for independent operation (Fujikawa et al. 2018). The
communication is established by maintaining tables of the local address and the destination
address. The routers acts as the first line of defense and it is needed to be configured such that it
can only pass the data traffic authorized by the administrator of the network.
Routing and routable protocols
Dedicated hardware v/s server based routers
Network interface cards
The network interface card may be for connecting the wireless network or the Ethernet
and it has the MAC address that is used for identifying the source address and enabling
transmission of data packet in the network. The MAC address of NIC are unique and it can easily
distinguish the client connected in the network.
Wireless access points
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
COMPUTING TECHNOLOGIES
It has a transmitter and receiver for the development of a wireless LAN and this are
separate network devices with built in antenna, adapter and transmitter. The wireless
infrastructure mode is used by the access point for creating the connection between the wired
network and wireless network (Sinh et al. 2017). The size of the network is needed to be
evaluated the number of access point needed to be installed is analyzed such that full coverage is
provided. Additional access point are installed in the network such that range of the wireless
network can be expanded (Sinh et al. 2018). Transmission range is limited for the wireless
access point and the Aps are needed to be placed such it is far away from interference and the
client can obtain signal usable and the data processing speed is efficient. The wireless standard is
depended for the coverage area, environmental condition and obstruction between the access
point and client. High end access point is needed to be installed with high powered antenna such
and firewall capability for securing the network.
There are different network models used for enabling data communication in the network
but all the network provide the basic functionality for transferring messages between the sender
and receiver. The network can utilize different hardware and software for providing different
functionality but the hardware and software need to work unitedly for transferring messages
successfully (Sita et al. 2019). The entire communication set is needed to be broken into
different layers for defining separately. The network layers can be defined in multiple ways and
two of the important network models such as: OSI and internet model.
The open system interconnection reference model is used in the commercial network and
developed using non standardized technologies. This model has 7 layers that describes the
communication between computers to computer. The software installed in the computers
operates on each of the layer and perform the function needed by those layers (Okafor et al.
COMPUTING TECHNOLOGIES
It has a transmitter and receiver for the development of a wireless LAN and this are
separate network devices with built in antenna, adapter and transmitter. The wireless
infrastructure mode is used by the access point for creating the connection between the wired
network and wireless network (Sinh et al. 2017). The size of the network is needed to be
evaluated the number of access point needed to be installed is analyzed such that full coverage is
provided. Additional access point are installed in the network such that range of the wireless
network can be expanded (Sinh et al. 2018). Transmission range is limited for the wireless
access point and the Aps are needed to be placed such it is far away from interference and the
client can obtain signal usable and the data processing speed is efficient. The wireless standard is
depended for the coverage area, environmental condition and obstruction between the access
point and client. High end access point is needed to be installed with high powered antenna such
and firewall capability for securing the network.
There are different network models used for enabling data communication in the network
but all the network provide the basic functionality for transferring messages between the sender
and receiver. The network can utilize different hardware and software for providing different
functionality but the hardware and software need to work unitedly for transferring messages
successfully (Sita et al. 2019). The entire communication set is needed to be broken into
different layers for defining separately. The network layers can be defined in multiple ways and
two of the important network models such as: OSI and internet model.
The open system interconnection reference model is used in the commercial network and
developed using non standardized technologies. This model has 7 layers that describes the
communication between computers to computer. The software installed in the computers
operates on each of the layer and perform the function needed by those layers (Okafor et al.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
COMPUTING TECHNOLOGIES
2017). Each of the layer uses a protocol or formal language that sets a rule and define the
working of the layer and defining the set of messages for working of the software.
Evaluation and Judgement
The reliability of the network is needed to be consistent such that probability of
correctness is higher and the network can meet all the telecommunication needs of
speedfix.co.uk. There are different approaches used for evaluation and optimizing the reliability
of the network design (Goutam, Enck and Reaves 2019). Redundant link and shortest path is
maintained for connecting the devices and deliver the data packets in short time interval.
Separate switch is assigned for each of the department such that outrage of a switch cannot affect
the whole network. Centralized management and configuration is used for the devices such that
faults in the setup can be troubleshoot easily and the network reliability, availability is higher
(Yokotani 2019). A failover plan is needed to be created and backup of the server is needed to be
created regularly. Redundant framework is needed to be used for the network device such that
one of the device fails the data packet can reach the target address using the secondary device
available.
Different software tools are needed to be used for the evaluation of the reliability and
optimizing it for reducing the failure rate and improve the efficiency of the network. An
estimation is needed to be made optimizing the concept of design and accelerating the
verification and reliability in network performance (Do et al. 2018). The placement of the
wireless access point is needed to be analyzed such that it can cover the major area of the office
and wireless devices can be connected with the network. Wireless connection is also used for the
IoT devices and it is needed to be secured with WPA2 passphrase such that unauthorized access
is restricted.
COMPUTING TECHNOLOGIES
2017). Each of the layer uses a protocol or formal language that sets a rule and define the
working of the layer and defining the set of messages for working of the software.
Evaluation and Judgement
The reliability of the network is needed to be consistent such that probability of
correctness is higher and the network can meet all the telecommunication needs of
speedfix.co.uk. There are different approaches used for evaluation and optimizing the reliability
of the network design (Goutam, Enck and Reaves 2019). Redundant link and shortest path is
maintained for connecting the devices and deliver the data packets in short time interval.
Separate switch is assigned for each of the department such that outrage of a switch cannot affect
the whole network. Centralized management and configuration is used for the devices such that
faults in the setup can be troubleshoot easily and the network reliability, availability is higher
(Yokotani 2019). A failover plan is needed to be created and backup of the server is needed to be
created regularly. Redundant framework is needed to be used for the network device such that
one of the device fails the data packet can reach the target address using the secondary device
available.
Different software tools are needed to be used for the evaluation of the reliability and
optimizing it for reducing the failure rate and improve the efficiency of the network. An
estimation is needed to be made optimizing the concept of design and accelerating the
verification and reliability in network performance (Do et al. 2018). The placement of the
wireless access point is needed to be analyzed such that it can cover the major area of the office
and wireless devices can be connected with the network. Wireless connection is also used for the
IoT devices and it is needed to be secured with WPA2 passphrase such that unauthorized access
is restricted.
8
COMPUTING TECHNOLOGIES
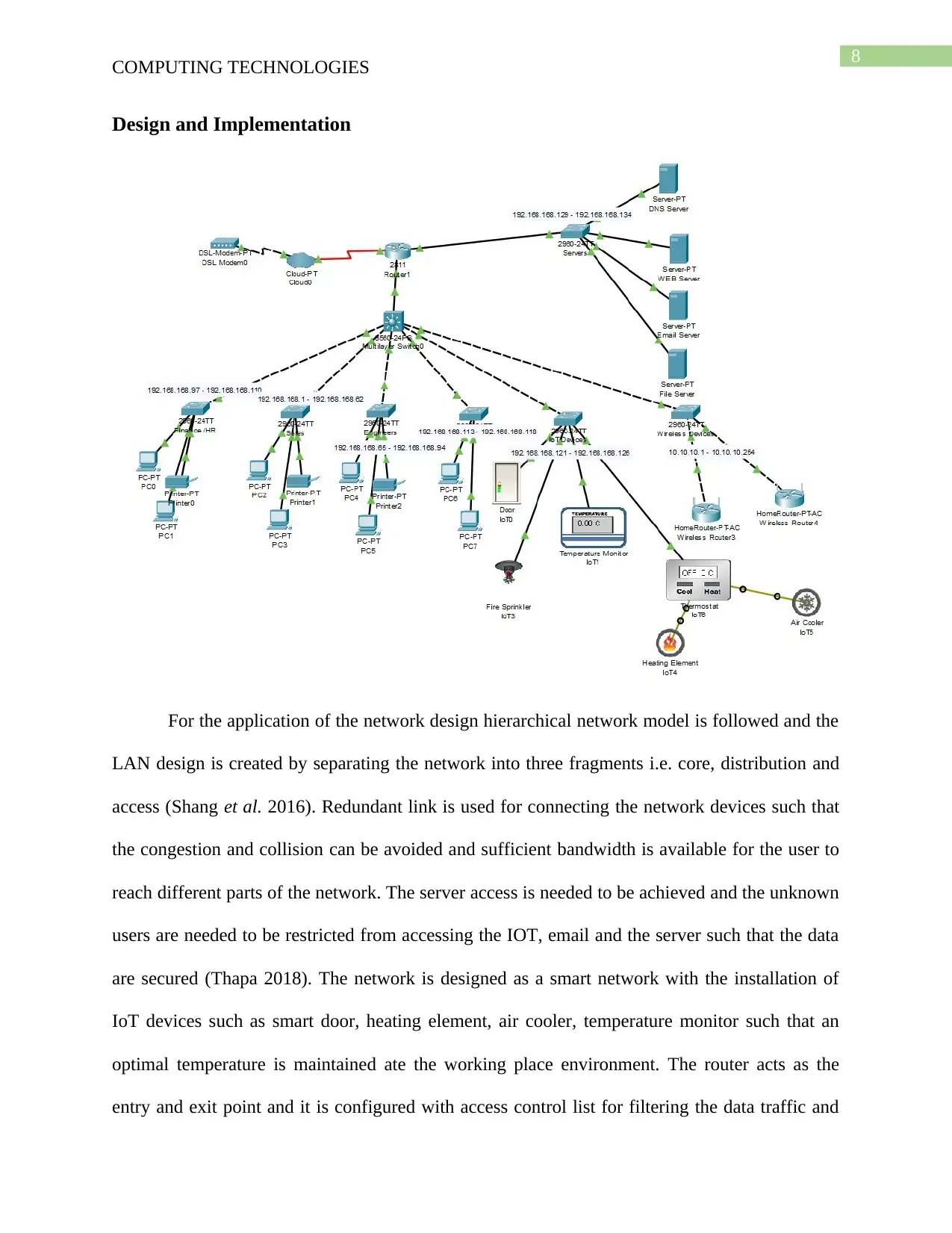
Design and Implementation
For the application of the network design hierarchical network model is followed and the
LAN design is created by separating the network into three fragments i.e. core, distribution and
access (Shang et al. 2016). Redundant link is used for connecting the network devices such that
the congestion and collision can be avoided and sufficient bandwidth is available for the user to
reach different parts of the network. The server access is needed to be achieved and the unknown
users are needed to be restricted from accessing the IOT, email and the server such that the data
are secured (Thapa 2018). The network is designed as a smart network with the installation of
IoT devices such as smart door, heating element, air cooler, temperature monitor such that an
optimal temperature is maintained ate the working place environment. The router acts as the
entry and exit point and it is configured with access control list for filtering the data traffic and
COMPUTING TECHNOLOGIES
Design and Implementation
For the application of the network design hierarchical network model is followed and the
LAN design is created by separating the network into three fragments i.e. core, distribution and
access (Shang et al. 2016). Redundant link is used for connecting the network devices such that
the congestion and collision can be avoided and sufficient bandwidth is available for the user to
reach different parts of the network. The server access is needed to be achieved and the unknown
users are needed to be restricted from accessing the IOT, email and the server such that the data
are secured (Thapa 2018). The network is designed as a smart network with the installation of
IoT devices such as smart door, heating element, air cooler, temperature monitor such that an
optimal temperature is maintained ate the working place environment. The router acts as the
entry and exit point and it is configured with access control list for filtering the data traffic and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
COMPUTING TECHNOLOGIES
secure the network. The multilayer switch 1 is configured as a VTP server and it contains all the
VLAN configuration such that an integrated control can be applied in the network and it can be
managed easily.
The following is the IP addressing plan that is followed for the configuration of VLAN
and fast Ethernet interface.
Major IP Address used for the local area network – 192.168.168.0/24
Major IP address used for the wireless network – 10.10.10.0/24
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Financ
e and
HR
11 14 192.168.168
.96
/28 255.255.255
.240
192.168.168
.97 -
192.168.168
.110
192.168.168
.111
Sales 38 62 192.168.168
.0
/26 255.255.255
.192
192.168.168
.1 -
192.168.168
.62
192.168.168
.63
Engine
ers
20 30 192.168.168
.64
/27 255.255.255
.224
192.168.168
.65 -
192.168.168
192.168.168
.95
COMPUTING TECHNOLOGIES
secure the network. The multilayer switch 1 is configured as a VTP server and it contains all the
VLAN configuration such that an integrated control can be applied in the network and it can be
managed easily.
The following is the IP addressing plan that is followed for the configuration of VLAN
and fast Ethernet interface.
Major IP Address used for the local area network – 192.168.168.0/24
Major IP address used for the wireless network – 10.10.10.0/24
Subnet
Name
Need
ed
Size
Allocat
ed Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Financ
e and
HR
11 14 192.168.168
.96
/28 255.255.255
.240
192.168.168
.97 -
192.168.168
.110
192.168.168
.111
Sales 38 62 192.168.168
.0
/26 255.255.255
.192
192.168.168
.1 -
192.168.168
.62
192.168.168
.63
Engine
ers
20 30 192.168.168
.64
/27 255.255.255
.224
192.168.168
.65 -
192.168.168
192.168.168
.95
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
COMPUTING TECHNOLOGIES
.94
Admin
s
5 6 192.168.168
.112
/29 255.255.255
.248
192.168.168
.113 -
192.168.168
.118
192.168.168
.119
Wireles
s
Devices
254 254 10.10.10.0 /24
255.255.255
.0
10.10.10.1 -
10.10.10.25
4
10.10.10.25
5
Server 4 6 192.168.168
.128
/29 255.255.255
.248
192.168.168
.129 -
192.168.168
.134
192.168.168
.135
IoT 5 6 192.168.168
.120
/29 255.255.255
.248
192.168.168
.121 -
192.168.168
.126
192.168.168
.127
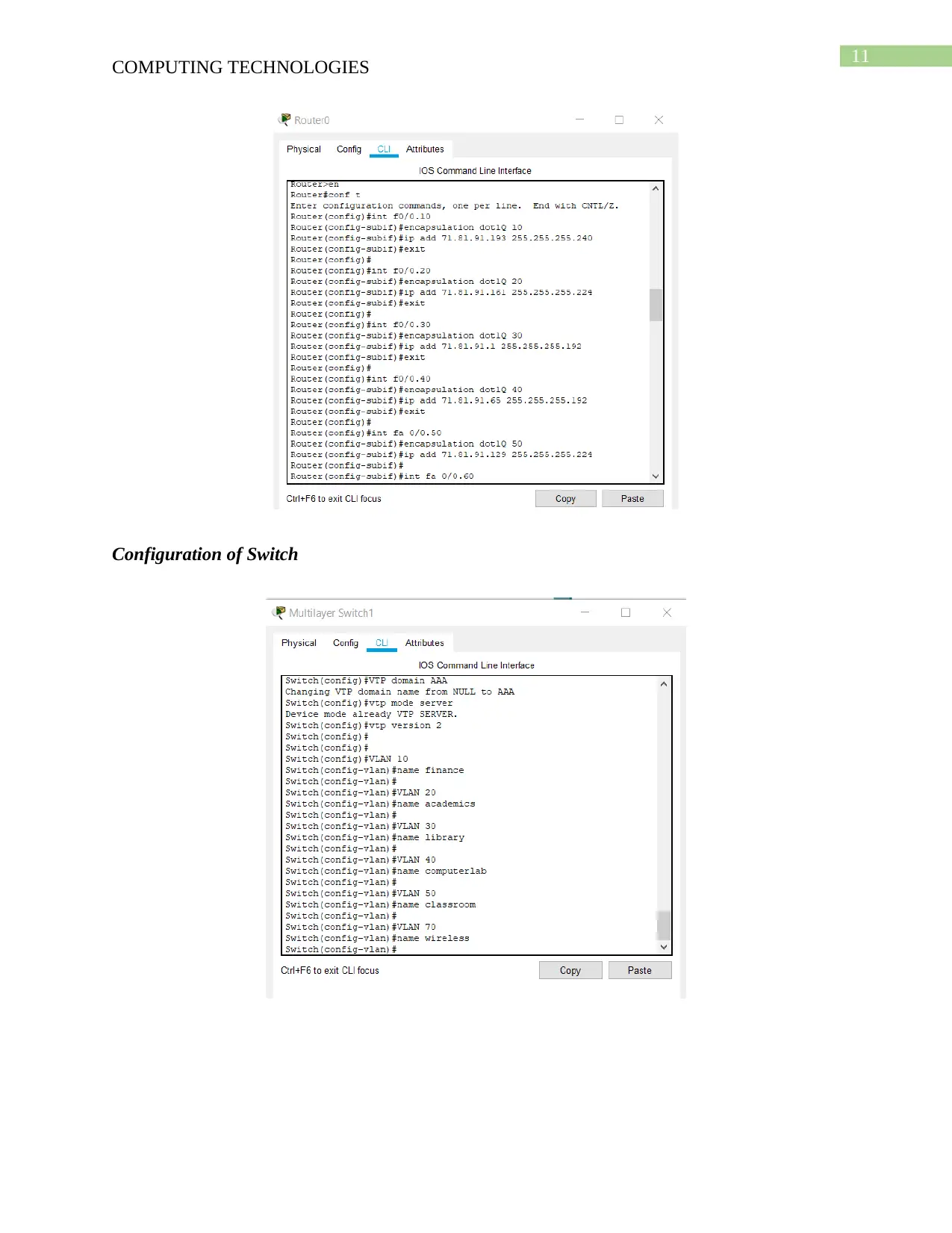
Configuration of Router
COMPUTING TECHNOLOGIES
.94
Admin
s
5 6 192.168.168
.112
/29 255.255.255
.248
192.168.168
.113 -
192.168.168
.118
192.168.168
.119
Wireles
s
Devices
254 254 10.10.10.0 /24
255.255.255
.0
10.10.10.1 -
10.10.10.25
4
10.10.10.25
5
Server 4 6 192.168.168
.128
/29 255.255.255
.248
192.168.168
.129 -
192.168.168
.134
192.168.168
.135
IoT 5 6 192.168.168
.120
/29 255.255.255
.248
192.168.168
.121 -
192.168.168
.126
192.168.168
.127
Configuration of Router
11
COMPUTING TECHNOLOGIES
Configuration of Switch
COMPUTING TECHNOLOGIES
Configuration of Switch
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





