Corporate Insider Threat Detection - Research Proposal
VerifiedAdded on 2023/04/23
|15
|3361
|223
AI Summary
This research proposal focuses on the detection of corporate insider threats using behavioral techniques such as biometric, communication, and cyber behavior. The study analyzes the potential risk indicators in determining a corporate insider and proposes algorithms for threat detection. The research methodology includes a case scenario and hypothesis testing.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Corporate insider
threat detection
Research Proposal
Institutional affiliation
GEN 690
MATERIAL ENGINEERING PROJECT
Student name
Student ID number
2019
threat detection
Research Proposal
Institutional affiliation
GEN 690
MATERIAL ENGINEERING PROJECT
Student name
Student ID number
2019
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
INTRODUCTION.......................................................................................................................................3
LITERATURE REVIEW............................................................................................................................5
RESEARCH METHODOLOGY................................................................................................................8
RESULTS..................................................................................................................................................11
CONCLUSION.........................................................................................................................................12
REFERENCES..........................................................................................................................................13
1
INTRODUCTION.......................................................................................................................................3
LITERATURE REVIEW............................................................................................................................5
RESEARCH METHODOLOGY................................................................................................................8
RESULTS..................................................................................................................................................11
CONCLUSION.........................................................................................................................................12
REFERENCES..........................................................................................................................................13
1

ABSTRACT
There are a number of factors to consider as potential risk indicators in determining a
corporate insider. Corporate insiders tend to attempt to bypass security controls and protocols
especially if they do not have security clearance in a certain level or they may have unjustified
work pattern. Some indicators are such as unjustified work patterns, chronic violation of
information security policies, emotional expression of conflicted loyalty to the organization and
a competitor, disgruntled employees, use of unauthorized digital external storage devices, failure
to report foreign contacts, and insensitive access to data on terminal of employment.
One of the key methods in the classification of detection mechanisms has to do with the
employee behavior and identification of anomalies and inconsistencies in the operations. The
experimental data was created based on the synthetic datasets that were conducted for the
isolation of the detection system. The datasets are obtained from transactional activities carried
out in the information system to attack data based on the log files.
The insider threat is commonly caused by biometric, communication, and cyber behavior
as compared to the psychosocial behavior. The data obtained from the information security
system is evaluated using the algorithms and the potential risks that may overcome the system
and cause it loop holes.
2
There are a number of factors to consider as potential risk indicators in determining a
corporate insider. Corporate insiders tend to attempt to bypass security controls and protocols
especially if they do not have security clearance in a certain level or they may have unjustified
work pattern. Some indicators are such as unjustified work patterns, chronic violation of
information security policies, emotional expression of conflicted loyalty to the organization and
a competitor, disgruntled employees, use of unauthorized digital external storage devices, failure
to report foreign contacts, and insensitive access to data on terminal of employment.
One of the key methods in the classification of detection mechanisms has to do with the
employee behavior and identification of anomalies and inconsistencies in the operations. The
experimental data was created based on the synthetic datasets that were conducted for the
isolation of the detection system. The datasets are obtained from transactional activities carried
out in the information system to attack data based on the log files.
The insider threat is commonly caused by biometric, communication, and cyber behavior
as compared to the psychosocial behavior. The data obtained from the information security
system is evaluated using the algorithms and the potential risks that may overcome the system
and cause it loop holes.
2

INTRODUCTION
The corporate insiders are comprised of the authorized people who use their access
credentials to perform unauthorized tasks. These people have legitimate access to the corporate
resources and the organization has attached a level of trust to their access credentials based on
the security levels as defined in the information security policies in the organization. There are
inadvertent or malicious insiders in the corporate insider category. Several incidences have been
recorded in the past such as the infamous Wiki-Leaks that hit the US during the year 2013. The
Wiki-Leaks incidence saw thousands of classified government documents and information from
emails to reports, disclosed to the public. Such incidences force organizations, both private and
public, to re-evaluate their information policy documents to determine if there are any loop holes
in their information security system. A corporate insider threat is bound to have a larger effect on
the organization as the insider has authorized access to the company’s resources (Cappelli,
Moore, Trzeciak, 2005).
Based on previous research, the incidence of employee financial hardships are
encountered during economic downturns. Sometimes the increased use of technology in
communication within an organization may ease theft in an organization. Some reports have
shown that the insider threat is quite more expensive and damaging as corporates are bound to
spend up to $412,000 per threat incident annually. The more the incidences, the higher the loss
the organization is bound to incur. There are a number of factors to consider as potential risk
indicators in determining a corporate insider. Corporate insiders tend to attempt to bypass
security controls and protocols especially if they do not have security clearance in a certain level
or they may have unjustified work pattern (Legg, et al., 2013 p. 25 ). Some indicators are such as
unjustified work patterns, chronic violation of information security policies, emotional
3
The corporate insiders are comprised of the authorized people who use their access
credentials to perform unauthorized tasks. These people have legitimate access to the corporate
resources and the organization has attached a level of trust to their access credentials based on
the security levels as defined in the information security policies in the organization. There are
inadvertent or malicious insiders in the corporate insider category. Several incidences have been
recorded in the past such as the infamous Wiki-Leaks that hit the US during the year 2013. The
Wiki-Leaks incidence saw thousands of classified government documents and information from
emails to reports, disclosed to the public. Such incidences force organizations, both private and
public, to re-evaluate their information policy documents to determine if there are any loop holes
in their information security system. A corporate insider threat is bound to have a larger effect on
the organization as the insider has authorized access to the company’s resources (Cappelli,
Moore, Trzeciak, 2005).
Based on previous research, the incidence of employee financial hardships are
encountered during economic downturns. Sometimes the increased use of technology in
communication within an organization may ease theft in an organization. Some reports have
shown that the insider threat is quite more expensive and damaging as corporates are bound to
spend up to $412,000 per threat incident annually. The more the incidences, the higher the loss
the organization is bound to incur. There are a number of factors to consider as potential risk
indicators in determining a corporate insider. Corporate insiders tend to attempt to bypass
security controls and protocols especially if they do not have security clearance in a certain level
or they may have unjustified work pattern (Legg, et al., 2013 p. 25 ). Some indicators are such as
unjustified work patterns, chronic violation of information security policies, emotional
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

expression of conflicted loyalty to the organization and a competitor, disgruntled employees, use
of unauthorized digital external storage devices, failure to report foreign contacts, and insensitive
access to data on terminal of employment (Bishop, et al., 2014). The following pie charts
illustrate the types of insider acts alongside their primary motivation,
It is important to know that the corporate insider threat is not categorized as hacking or
under cyber security as the detection of corporate insiders focuses on the behavioral techniques.
Based on several research and statistics, the corporate insider threats are mainly carried out by
authorized staff members and smaller percentages of the acts are carried out by contractors and
temporary staff (CPNI). The corporate staff exploits corporate weaknesses such as poor
management practices, auditing functions, improper protective security controls and culture,
employment and HR screening, threat awareness at management level, and inadequate corporate
governance (Greitzer, et al., 2011, p. 32). Currently, corporate are quite cautious and they do all
that is necessary to protect their resources especially information, data, and hardware resources
by implementing insider threat detection programs and policies.
4
of unauthorized digital external storage devices, failure to report foreign contacts, and insensitive
access to data on terminal of employment (Bishop, et al., 2014). The following pie charts
illustrate the types of insider acts alongside their primary motivation,
It is important to know that the corporate insider threat is not categorized as hacking or
under cyber security as the detection of corporate insiders focuses on the behavioral techniques.
Based on several research and statistics, the corporate insider threats are mainly carried out by
authorized staff members and smaller percentages of the acts are carried out by contractors and
temporary staff (CPNI). The corporate staff exploits corporate weaknesses such as poor
management practices, auditing functions, improper protective security controls and culture,
employment and HR screening, threat awareness at management level, and inadequate corporate
governance (Greitzer, et al., 2011, p. 32). Currently, corporate are quite cautious and they do all
that is necessary to protect their resources especially information, data, and hardware resources
by implementing insider threat detection programs and policies.
4

LITERATURE REVIEW
During economic crisis, people tend to find ways to make ends meet. Corporate insiders
are considered to be quite active during such periods. These are the individuals who have access
to corporate hardware, software, and firmware. They may have authorized or non-authorized
access to the proprietary information and equipment in a given organization by using their
personal accounts or hacked accounts. Some of the common resources that the corporate insiders
get access to are computers, network rooms and other intangible resources such as the email
accounts, user accounts, and the human resource in an organization. Most of the corporate
insiders are either disgruntled employees or victims of turf financial times or economic recess.
The main point is that these corporate insiders always have motive to have unauthorized access
to proprietary organization materials and leak them to unauthorized users (Kammueller, et al.,
2014, p.68).
There are several research papers done to determine the type of behavior of an insider.
Most of the research work done in the information security and corporate data security entails the
threat prevention and detection. The threat prevention has to do with enforcement of good
policies, procedures, and practices where one can manage and monitor the flow of information,
the utilization of corporate resources, the resource management and role allocation strategies as
well as the honeypots. To prevent insider threats, an organization formulates and enforces good
information security policies, procedures, and practices. To mitigate the incidences of insider
threats, organizations implement secure backup and recovery processes and perform periodic
information audits on cyber activities. Bertacchini, et al., did a survey that sought to analyze the
use of UNIX commands on an information system to detect insider threats. The most plausible
5
During economic crisis, people tend to find ways to make ends meet. Corporate insiders
are considered to be quite active during such periods. These are the individuals who have access
to corporate hardware, software, and firmware. They may have authorized or non-authorized
access to the proprietary information and equipment in a given organization by using their
personal accounts or hacked accounts. Some of the common resources that the corporate insiders
get access to are computers, network rooms and other intangible resources such as the email
accounts, user accounts, and the human resource in an organization. Most of the corporate
insiders are either disgruntled employees or victims of turf financial times or economic recess.
The main point is that these corporate insiders always have motive to have unauthorized access
to proprietary organization materials and leak them to unauthorized users (Kammueller, et al.,
2014, p.68).
There are several research papers done to determine the type of behavior of an insider.
Most of the research work done in the information security and corporate data security entails the
threat prevention and detection. The threat prevention has to do with enforcement of good
policies, procedures, and practices where one can manage and monitor the flow of information,
the utilization of corporate resources, the resource management and role allocation strategies as
well as the honeypots. To prevent insider threats, an organization formulates and enforces good
information security policies, procedures, and practices. To mitigate the incidences of insider
threats, organizations implement secure backup and recovery processes and perform periodic
information audits on cyber activities. Bertacchini, et al., did a survey that sought to analyze the
use of UNIX commands on an information system to detect insider threats. The most plausible
5

detection method for the insider threats is the behavioral techniques. It has to do with biometric,
printing, login, online communication and other psychosocial behavior on systems.
One of the key methods in the classification of detection mechanisms has to do with the
employee behavior and identification of anomalies and inconsistencies in the operations. The
communication behavior is focused on as it determines the information theft. Under
communication, there are biometric, cyber, psychosocial, and communication behavior that is
analyzed in the determination of corporate insider threats. The organization seeks to detect the
threat based on the security levels defined in the information security policies. The information
auditors and forensic officers may search through reports and system logs to detect malicious
insider behavior (Ogiela, et al., 2012, p.42).
Biometric behavior is used in recognizing a given user. The employee’s behavior can be
studied from the biometric information obtained and inconsistencies in the implementation or
testing of biometric information can be recorded in system log files. The system records the
masqueraders and any person willing to do malicious activities (Spitzner, 2003, p.175).
Cyber behavior observes the staff users activities while using corporate resources such as
printing, web searches, external devices use, login attempts, serial file search attempts. The
activities and the cyber actions are used to detect anomalies in the use of corporate resources.
The cyber activities detect information but detecting the actors behind the activities recorded
requires an involvement with the biometric information. It helps distinguish information over
different environments. Further, the threat prevention and detection systems implemented in the
organizations to determine the anomalies in the cyber behavior. It focuses on UNIX commands
and determines what the staff has been doing on the company system (Magklaras, 2002, p.68).
6
printing, login, online communication and other psychosocial behavior on systems.
One of the key methods in the classification of detection mechanisms has to do with the
employee behavior and identification of anomalies and inconsistencies in the operations. The
communication behavior is focused on as it determines the information theft. Under
communication, there are biometric, cyber, psychosocial, and communication behavior that is
analyzed in the determination of corporate insider threats. The organization seeks to detect the
threat based on the security levels defined in the information security policies. The information
auditors and forensic officers may search through reports and system logs to detect malicious
insider behavior (Ogiela, et al., 2012, p.42).
Biometric behavior is used in recognizing a given user. The employee’s behavior can be
studied from the biometric information obtained and inconsistencies in the implementation or
testing of biometric information can be recorded in system log files. The system records the
masqueraders and any person willing to do malicious activities (Spitzner, 2003, p.175).
Cyber behavior observes the staff users activities while using corporate resources such as
printing, web searches, external devices use, login attempts, serial file search attempts. The
activities and the cyber actions are used to detect anomalies in the use of corporate resources.
The cyber activities detect information but detecting the actors behind the activities recorded
requires an involvement with the biometric information. It helps distinguish information over
different environments. Further, the threat prevention and detection systems implemented in the
organizations to determine the anomalies in the cyber behavior. It focuses on UNIX commands
and determines what the staff has been doing on the company system (Magklaras, 2002, p.68).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Psychosocial behavior focuses on actors who wish to sabotage corporate resources. These
actors may be disgruntled employees who may perform sophisticated cyber-attacks. Some of the
attacks include spoofing, denial of service attacks, and account espionage. The actors tend to
have conflict with supervisors and their fellow colleagues. The actors have cases of anomalies in
their social behavior. The information security policy requires that the psychosocial behavior is
collected on periodic basis.
Communication behavior determines the characteristics for the communication and
employees in different departments. The information is obtained from the communication
methods used in an organization such as email accounts, instant messaging applications, file
sharing applications, and telephone conversations and messages. The information is collected
and stored for forensic, insider threat, and quality checks. The system uses threat detection and
prevention systems that can search through system logs to detect flagged words or activities that
are highlighted as threats. However, the logging data may contain a lot of data which may be too
much to interpret. The user activity recording is important and it is instantly understood by the
auditors and the irrefutable evidence of user actions (Myers, et al., 2009, p 46).
7
actors may be disgruntled employees who may perform sophisticated cyber-attacks. Some of the
attacks include spoofing, denial of service attacks, and account espionage. The actors tend to
have conflict with supervisors and their fellow colleagues. The actors have cases of anomalies in
their social behavior. The information security policy requires that the psychosocial behavior is
collected on periodic basis.
Communication behavior determines the characteristics for the communication and
employees in different departments. The information is obtained from the communication
methods used in an organization such as email accounts, instant messaging applications, file
sharing applications, and telephone conversations and messages. The information is collected
and stored for forensic, insider threat, and quality checks. The system uses threat detection and
prevention systems that can search through system logs to detect flagged words or activities that
are highlighted as threats. However, the logging data may contain a lot of data which may be too
much to interpret. The user activity recording is important and it is instantly understood by the
auditors and the irrefutable evidence of user actions (Myers, et al., 2009, p 46).
7

RESEARCH METHODOLOGY
System Requirements Analysis
(i) The system should determine an insider threat score and alert the administrator when
the threat level is too high.
(ii) The system requires distinguishing the insider threat before obtaining a score for the
sabotage, data fraud, and intellectual property theft.
(iii) The system requires determining the new and anticipating potential threats that may
not have been captured in the information security policy.
Study Design
Some of the techniques that are useful in accomplishing the research work are as
discussed in this section. A case scenario is adopted in a given organization. The main tasks
include reviewing the current information security policy. The data collection techniques will be
implemented so as to determine the security constraints, loopholes, and UNIX commands which
raises an alarm. The following datasets are analyzed in the research study to determine the
insider threats for a given security system.
Behavior types Availability in the system
UNIX Commands 1. Public
2. On request
System Level 1. Private
2. On Request
Cyber 1. Private
2. On Request
8
System Requirements Analysis
(i) The system should determine an insider threat score and alert the administrator when
the threat level is too high.
(ii) The system requires distinguishing the insider threat before obtaining a score for the
sabotage, data fraud, and intellectual property theft.
(iii) The system requires determining the new and anticipating potential threats that may
not have been captured in the information security policy.
Study Design
Some of the techniques that are useful in accomplishing the research work are as
discussed in this section. A case scenario is adopted in a given organization. The main tasks
include reviewing the current information security policy. The data collection techniques will be
implemented so as to determine the security constraints, loopholes, and UNIX commands which
raises an alarm. The following datasets are analyzed in the research study to determine the
insider threats for a given security system.
Behavior types Availability in the system
UNIX Commands 1. Public
2. On request
System Level 1. Private
2. On Request
Cyber 1. Private
2. On Request
8
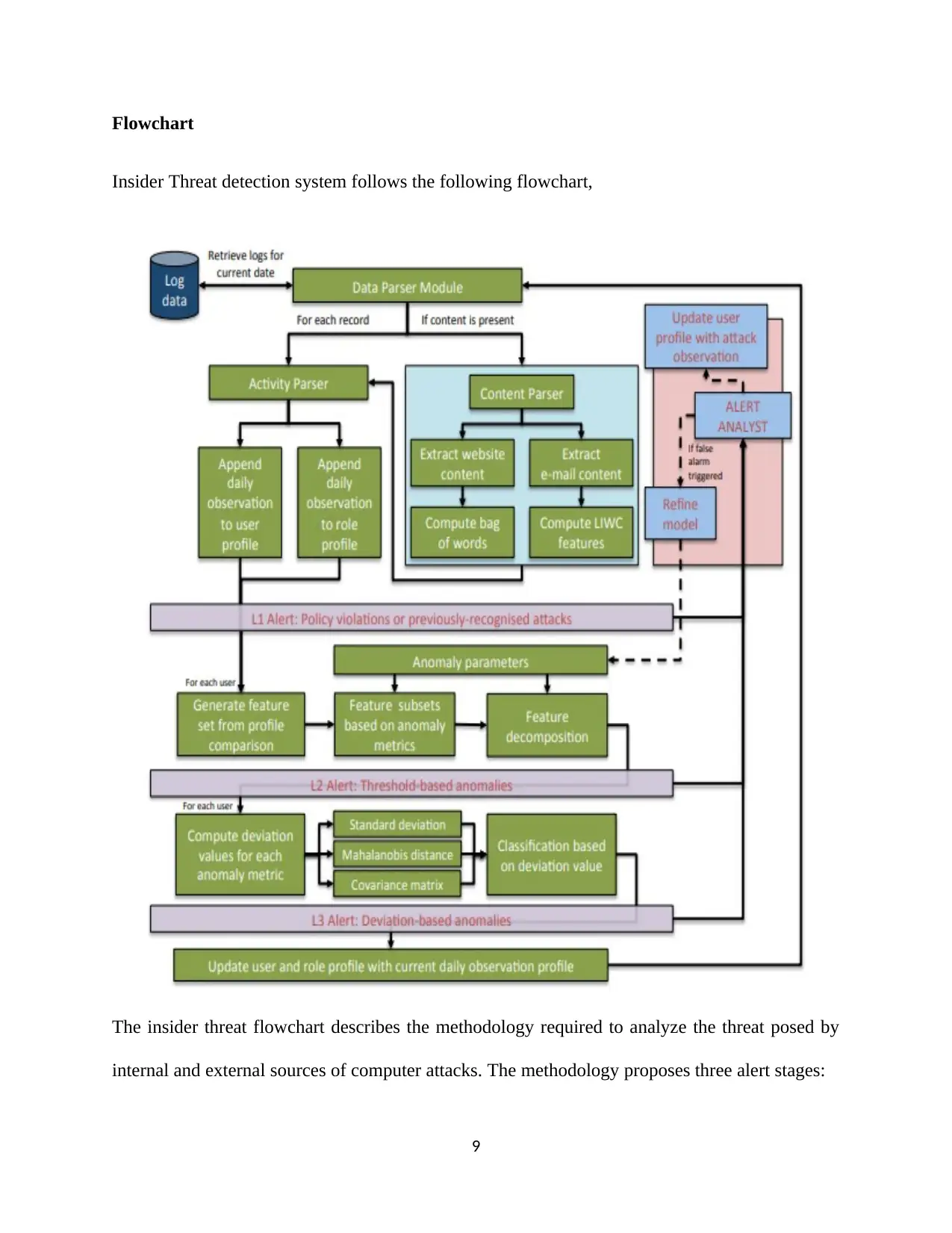
Flowchart
Insider Threat detection system follows the following flowchart,
The insider threat flowchart describes the methodology required to analyze the threat posed by
internal and external sources of computer attacks. The methodology proposes three alert stages:
9
Insider Threat detection system follows the following flowchart,
The insider threat flowchart describes the methodology required to analyze the threat posed by
internal and external sources of computer attacks. The methodology proposes three alert stages:
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
(i) Policy violation or previously recognized attacks
(ii) Threshold-based anomalies
(iii) Deviation-based anomalies
The three alerts are actioned once the anomalies or attacks are detected in the system. When the
network system or database storage network system determines an attack a data parser module
retrieves logs of the attack from the log file. The user profile is able to append the log file before
it is passed to the content parser. An analyst checks the information and updates the user profile
with the information once they are alerted. Further, the system is analyzed for any form of policy
violations or other known attacks with the anomaly metrics. The user roles defined in the
security policy are constantly updated in the daily observation profile.
Some of the algorithms that need to be implemented in the system and the synthesis of
data may include the following case scenario,
Case Scenario Algorithm
Guild leaving the online gaming platform during a session Random Forest
Personal interaction with colleagues and their interpersonal
relations at the workplace
Bayesian Network
Human Resource Management evaluation of the staff behavior Bayesian Network
Communication on social media platforms using corporate
resources. For instance, YouTube Comments
Naïve Bayes
Support Vector Machine
Logistic regression
The experimental data was created based on the synthetic datasets that were conducted
for the isolation of the detection system. The datasets are obtained from transactional activities
10
(ii) Threshold-based anomalies
(iii) Deviation-based anomalies
The three alerts are actioned once the anomalies or attacks are detected in the system. When the
network system or database storage network system determines an attack a data parser module
retrieves logs of the attack from the log file. The user profile is able to append the log file before
it is passed to the content parser. An analyst checks the information and updates the user profile
with the information once they are alerted. Further, the system is analyzed for any form of policy
violations or other known attacks with the anomaly metrics. The user roles defined in the
security policy are constantly updated in the daily observation profile.
Some of the algorithms that need to be implemented in the system and the synthesis of
data may include the following case scenario,
Case Scenario Algorithm
Guild leaving the online gaming platform during a session Random Forest
Personal interaction with colleagues and their interpersonal
relations at the workplace
Bayesian Network
Human Resource Management evaluation of the staff behavior Bayesian Network
Communication on social media platforms using corporate
resources. For instance, YouTube Comments
Naïve Bayes
Support Vector Machine
Logistic regression
The experimental data was created based on the synthetic datasets that were conducted
for the isolation of the detection system. The datasets are obtained from transactional activities
10

carried out in the information system to attack data based on the log files. The information
security policy determines an employee’s role in the organization to determine the,
(i) Log-in attempts
(ii) HTTP requests
(iii) Email contacts
(iv) Email communication and IM interactions
Hypothesis
H0: The Information security policy is sufficient for the management of the insider threat system
analysis.
H1: The insider threat is commonly caused by biometric, communication, and cyber behavior as
compared to the psychosocial behavior.
RESULTS
These algorithms form part of a larger information security threat detection system that
are implemented to determine the insider threat. Data is obtained from the system log which
contains data over a period of time. The study was conducted on 5 insiders with information
security clearance levels 2 and 3. The table below illustrates the alerts obtained from the threat
detection system,
# L2 alerts
(ϭ<0.1)
L2 alerts
(ϭ<0.2)
L2 alerts
(ϭ<0.3)
L3 alerts
(ϭ<1.0)
L3 alerts
(ϭ<2.0)
L2 anomaly
vectors
L3 anomaly
vectors
1 915 415 352 276 75 n/a n/a
2 3015 92 88 68 24 Logon, logon
duration
Insert, file,
hourly, user,
total
3 904 553 474 287 82 User, new,
this
New, email
4 1572 125 89 977 276 Logon, logon User, file, total
11
security policy determines an employee’s role in the organization to determine the,
(i) Log-in attempts
(ii) HTTP requests
(iii) Email contacts
(iv) Email communication and IM interactions
Hypothesis
H0: The Information security policy is sufficient for the management of the insider threat system
analysis.
H1: The insider threat is commonly caused by biometric, communication, and cyber behavior as
compared to the psychosocial behavior.
RESULTS
These algorithms form part of a larger information security threat detection system that
are implemented to determine the insider threat. Data is obtained from the system log which
contains data over a period of time. The study was conducted on 5 insiders with information
security clearance levels 2 and 3. The table below illustrates the alerts obtained from the threat
detection system,
# L2 alerts
(ϭ<0.1)
L2 alerts
(ϭ<0.2)
L2 alerts
(ϭ<0.3)
L3 alerts
(ϭ<1.0)
L3 alerts
(ϭ<2.0)
L2 anomaly
vectors
L3 anomaly
vectors
1 915 415 352 276 75 n/a n/a
2 3015 92 88 68 24 Logon, logon
duration
Insert, file,
hourly, user,
total
3 904 553 474 287 82 User, new,
this
New, email
4 1572 125 89 977 276 Logon, logon User, file, total
11
duration
5 1645 610 526 452 73 n/a New, number,
user, role,
total, hourly
The table above describes the experiment performed on the network that shows tests carried out
when different attacks were posted on the system. The different alerts and warnings labelled L1,
L2, and L3 based on the flowchart were analyzed from the log files. The table indicates the
number of times the alert was detected. Five tests were carried for different attacks some based
on threshold based anomalies, deviation-based anomalies, and policy violations or previously
recognized attacks.
DISCUSSION
Some of the useful behavior captured from the system is the search behavior, UNIX
commands, system level behavior, and print, browse and search activities, upload and download
on the information system, communication and social media interactions on the corporate
resources. The proposal discusses the algorithms that are implemented in the system to determine
the evaluation of the information security system. The data obtained from the information
security system is evaluated using the algorithms and the potential risks that may overcome the
system and cause it loop holes. The research on the insider threat is not an isolated issue in the
information security system rather it performs the detection of security flaws based on the insider
or the actor’s behavior while using the corporate resources. The system attacks are caused by the
biometric interactions on the system, the communication and interaction on social media using
the corporate resources.
12
5 1645 610 526 452 73 n/a New, number,
user, role,
total, hourly
The table above describes the experiment performed on the network that shows tests carried out
when different attacks were posted on the system. The different alerts and warnings labelled L1,
L2, and L3 based on the flowchart were analyzed from the log files. The table indicates the
number of times the alert was detected. Five tests were carried for different attacks some based
on threshold based anomalies, deviation-based anomalies, and policy violations or previously
recognized attacks.
DISCUSSION
Some of the useful behavior captured from the system is the search behavior, UNIX
commands, system level behavior, and print, browse and search activities, upload and download
on the information system, communication and social media interactions on the corporate
resources. The proposal discusses the algorithms that are implemented in the system to determine
the evaluation of the information security system. The data obtained from the information
security system is evaluated using the algorithms and the potential risks that may overcome the
system and cause it loop holes. The research on the insider threat is not an isolated issue in the
information security system rather it performs the detection of security flaws based on the insider
or the actor’s behavior while using the corporate resources. The system attacks are caused by the
biometric interactions on the system, the communication and interaction on social media using
the corporate resources.
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CONCLUSION
In a nutshell, the research proposal has surveyed the potential insider threats and risk
indicators. The paper compares the different behavioral analysis such as the psychosocial, cyber,
biometric, and communication that may cause potential threat in a corporate. Having categorized
the insider threats and assigned them scores based on the occurrence, the threats are seen are
evaluated and provided for the data behavior. The proposal is given such that malicious threats
can be detected on the system. The information obtained to form the case scenarios is obtained
on the basis of the information security policy. The policy acts as a guide and the system data
collection methods are implemented in the organization. The information is evaluated using the
common statistical techniques and it enables the researcher make relevant deductions on the
systems. The information obtained from the analysis is used to improve the current information
security policy.
REFERENCES
D. M. Cappelli, A. P. Moore, and R. F. Trzeciak. The CERT Guide to Insider Threats: How to
Prevent, Detect, and Respond to Information Technology Crimes. Addison-Wesley
Professional, 1st edition, 2012. I. Jolliffe. Principal component analysis. Wiley Online
Library, 2005.
13
In a nutshell, the research proposal has surveyed the potential insider threats and risk
indicators. The paper compares the different behavioral analysis such as the psychosocial, cyber,
biometric, and communication that may cause potential threat in a corporate. Having categorized
the insider threats and assigned them scores based on the occurrence, the threats are seen are
evaluated and provided for the data behavior. The proposal is given such that malicious threats
can be detected on the system. The information obtained to form the case scenarios is obtained
on the basis of the information security policy. The policy acts as a guide and the system data
collection methods are implemented in the organization. The information is evaluated using the
common statistical techniques and it enables the researcher make relevant deductions on the
systems. The information obtained from the analysis is used to improve the current information
security policy.
REFERENCES
D. M. Cappelli, A. P. Moore, and R. F. Trzeciak. The CERT Guide to Insider Threats: How to
Prevent, Detect, and Respond to Information Technology Crimes. Addison-Wesley
Professional, 1st edition, 2012. I. Jolliffe. Principal component analysis. Wiley Online
Library, 2005.
13

P. A. Legg, N. Moffat, J. R. C. Nurse, J. Happa, I. Agrafiotis, M. Goldsmith, and S. Creese.
Towards a conceptual model and reasoning structure for insider threat detection. Journal
of Wireless Mobile Networks, Ubiquitous Computing and Dependable Applications,
4(4):20–37, 2013.
M. Bishop, B. Simidchieva, H. Conboy, H. Phan, L. Osterwell, L. Clarke, G. Avrunin, and S.
Peisert. Insider threat detection by process analysis. In IEEE Security and Privacy
Workshops (SPW). IEEE, 2014.
M. Bishop, S. Engle, S. Peisert, S. Whalen, and C. Gates. We have met the enemy and he is us.
In Proc. of the 2008 workshop on New security paradigms (NSPW’08), Lake Tahoe,
California, USA, pages 1–12. ACM, September 2008.
F. L. Greitzer and R. E. Hohimer. Modeling human behavior to anticipate insider attacks.
Journal of Strategic Security, 4(2):25–48, 2011.
J. R. C Nurse, O. Buckley, P. A. Legg, M. Goldsmith, S. Creese, G. R. T. Wright, and M.
Whitty. Understanding insider threat: A framework for characterising attacks. In IEEE
Security and Privacy Workshops (SPW). IEEE, 2014.
F. Kammueller and C. W. Probst. Invalidating policies using structural information. Journal of
Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications,
5(2):59–79.
M. R. Ogiela and U. Ogiela. Linguistic protocols for secure information management and
sharing. Computers & Mathematics with Applications, 63(2):564–572, January 2012.
L. Spitzner. Honeypots: catching the insider threat. In Proc. of the 19th IEEE Computer Security
Applications Conference (ACSAC’03), Las Vegas, Nevada, USA, pages 170–179. IEEE,
December 2003.
G. B. Magklaras and S. M. Furnell. Insider threat prediction tool: Evaluating the probability of
IT misuse. Computers and Security, 21(1):62–73, 2002.
J. Myers, M. R. Grimaila, and R. F. Mills. Towards insider threat detection using web server
logs. In Proceedings of the 5th Annual Workshop on Cyber Security and Information
Intelligence Research: Cyber Security and Information Intelligence Challenges and
Strategies, CSIIRW ’09, pages 54:1–54:4, New York, NY, USA, 2009. ACM.
14
Towards a conceptual model and reasoning structure for insider threat detection. Journal
of Wireless Mobile Networks, Ubiquitous Computing and Dependable Applications,
4(4):20–37, 2013.
M. Bishop, B. Simidchieva, H. Conboy, H. Phan, L. Osterwell, L. Clarke, G. Avrunin, and S.
Peisert. Insider threat detection by process analysis. In IEEE Security and Privacy
Workshops (SPW). IEEE, 2014.
M. Bishop, S. Engle, S. Peisert, S. Whalen, and C. Gates. We have met the enemy and he is us.
In Proc. of the 2008 workshop on New security paradigms (NSPW’08), Lake Tahoe,
California, USA, pages 1–12. ACM, September 2008.
F. L. Greitzer and R. E. Hohimer. Modeling human behavior to anticipate insider attacks.
Journal of Strategic Security, 4(2):25–48, 2011.
J. R. C Nurse, O. Buckley, P. A. Legg, M. Goldsmith, S. Creese, G. R. T. Wright, and M.
Whitty. Understanding insider threat: A framework for characterising attacks. In IEEE
Security and Privacy Workshops (SPW). IEEE, 2014.
F. Kammueller and C. W. Probst. Invalidating policies using structural information. Journal of
Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications,
5(2):59–79.
M. R. Ogiela and U. Ogiela. Linguistic protocols for secure information management and
sharing. Computers & Mathematics with Applications, 63(2):564–572, January 2012.
L. Spitzner. Honeypots: catching the insider threat. In Proc. of the 19th IEEE Computer Security
Applications Conference (ACSAC’03), Las Vegas, Nevada, USA, pages 170–179. IEEE,
December 2003.
G. B. Magklaras and S. M. Furnell. Insider threat prediction tool: Evaluating the probability of
IT misuse. Computers and Security, 21(1):62–73, 2002.
J. Myers, M. R. Grimaila, and R. F. Mills. Towards insider threat detection using web server
logs. In Proceedings of the 5th Annual Workshop on Cyber Security and Information
Intelligence Research: Cyber Security and Information Intelligence Challenges and
Strategies, CSIIRW ’09, pages 54:1–54:4, New York, NY, USA, 2009. ACM.
14
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





