Data Communications Principles Assignment 2
VerifiedAdded on 2023/04/21
|7
|1926
|350
AI Summary
This document includes the routing tables for each node using minimum hop routing, explanation of how TCP connection is established and closed, summary of important aspects of cellular networks, comparison of medium access control technologies, overview of packet loss and recovery schemas in multimedia networking, and overview of RSVP and its reservation styles. It also explains how public key cryptography is used in digital signatures and encryption, along with a business application for each scenario.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.
CP5601 - 2018 SP53 JCUS
Data Communications Principles
Assignment 2
Submit your answers as a Word document to Assessment Task 3 in LearnJCU.
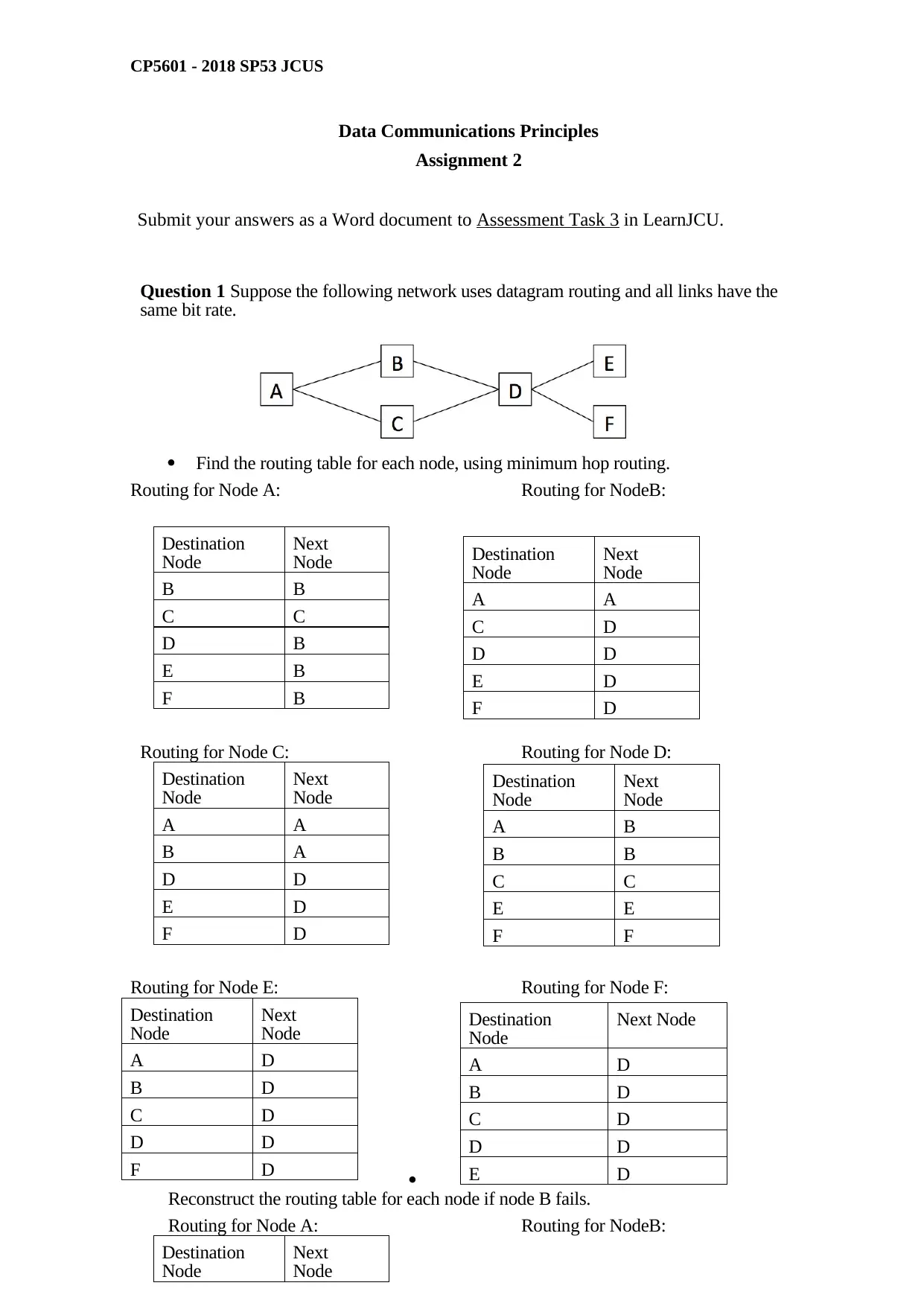
Question 1 Suppose the following network uses datagram routing and all links have the
same bit rate.
Find the routing table for each node, using minimum hop routing.
Routing for Node A: Routing for NodeB:
Destination
Node Next
Node
B B
C C
D B
E B
F B
Routing for Node C: Routing for Node D:
Destination
Node Next
Node
A A
B A
D D
E D
F D
Routing for Node E: Routing for Node F:
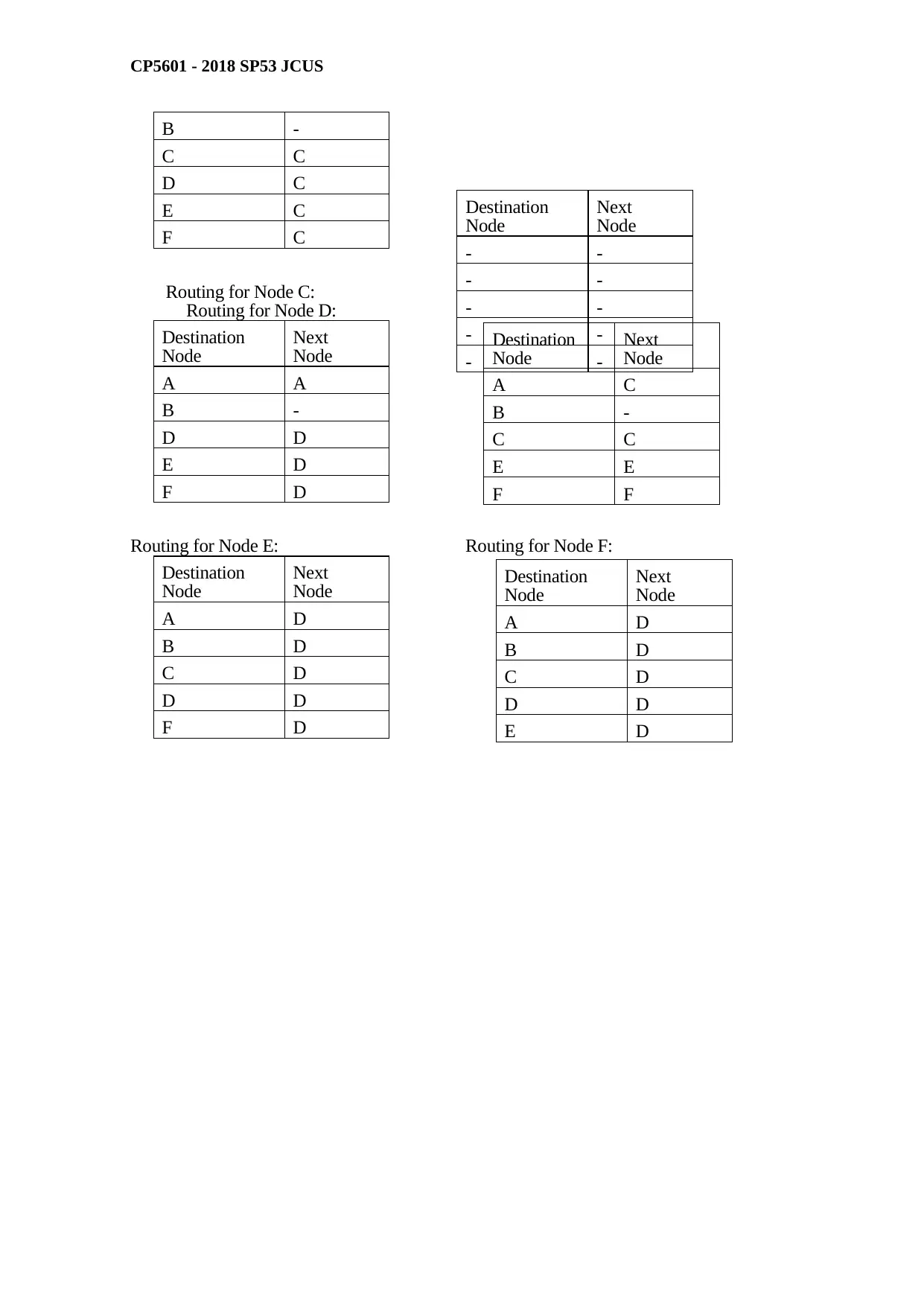
Reconstruct the routing table for each node if node B fails.
Routing for Node A: Routing for NodeB:
Destination
Node Next
Node
Destination
Node Next
Node
A A
C D
D D
E D
F D
Destination
Node Next
Node
A B
B B
C C
E E
F F
Destination
Node Next
Node
A D
B D
C D
D D
F D
Destination
Node Next Node
A D
B D
C D
D D
E D
Data Communications Principles
Assignment 2
Submit your answers as a Word document to Assessment Task 3 in LearnJCU.
Question 1 Suppose the following network uses datagram routing and all links have the
same bit rate.
Find the routing table for each node, using minimum hop routing.
Routing for Node A: Routing for NodeB:
Destination
Node Next
Node
B B
C C
D B
E B
F B
Routing for Node C: Routing for Node D:
Destination
Node Next
Node
A A
B A
D D
E D
F D
Routing for Node E: Routing for Node F:
Reconstruct the routing table for each node if node B fails.
Routing for Node A: Routing for NodeB:
Destination
Node Next
Node
Destination
Node Next
Node
A A
C D
D D
E D
F D
Destination
Node Next
Node
A B
B B
C C
E E
F F
Destination
Node Next
Node
A D
B D
C D
D D
F D
Destination
Node Next Node
A D
B D
C D
D D
E D
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
CP5601 - 2018 SP53 JCUS
B -
C C
D C
E C
F C
Routing for Node C:
Routing for Node D:
Destination
Node Next
Node
A A
B -
D D
E D
F D
Routing for Node E: Routing for Node F:
Destination
Node Next
Node
A D
B D
C D
D D
F D
Destination
Node Next
Node
- -
- -
- -
- -
- -
Destination
Node Next
Node
A C
B -
C C
E E
F F
Destination
Node Next
Node
A D
B D
C D
D D
E D
B -
C C
D C
E C
F C
Routing for Node C:
Routing for Node D:
Destination
Node Next
Node
A A
B -
D D
E D
F D
Routing for Node E: Routing for Node F:
Destination
Node Next
Node
A D
B D
C D
D D
F D
Destination
Node Next
Node
- -
- -
- -
- -
- -
Destination
Node Next
Node
A C
B -
C C
E E
F F
Destination
Node Next
Node
A D
B D
C D
D D
E D
CP5601 - 2018 SP53 JCUS
Question 2
Explain in detail how a TCP connection is established and closed.
What is TCP flow control and how it works?
You may use diagrams and examples in answers.
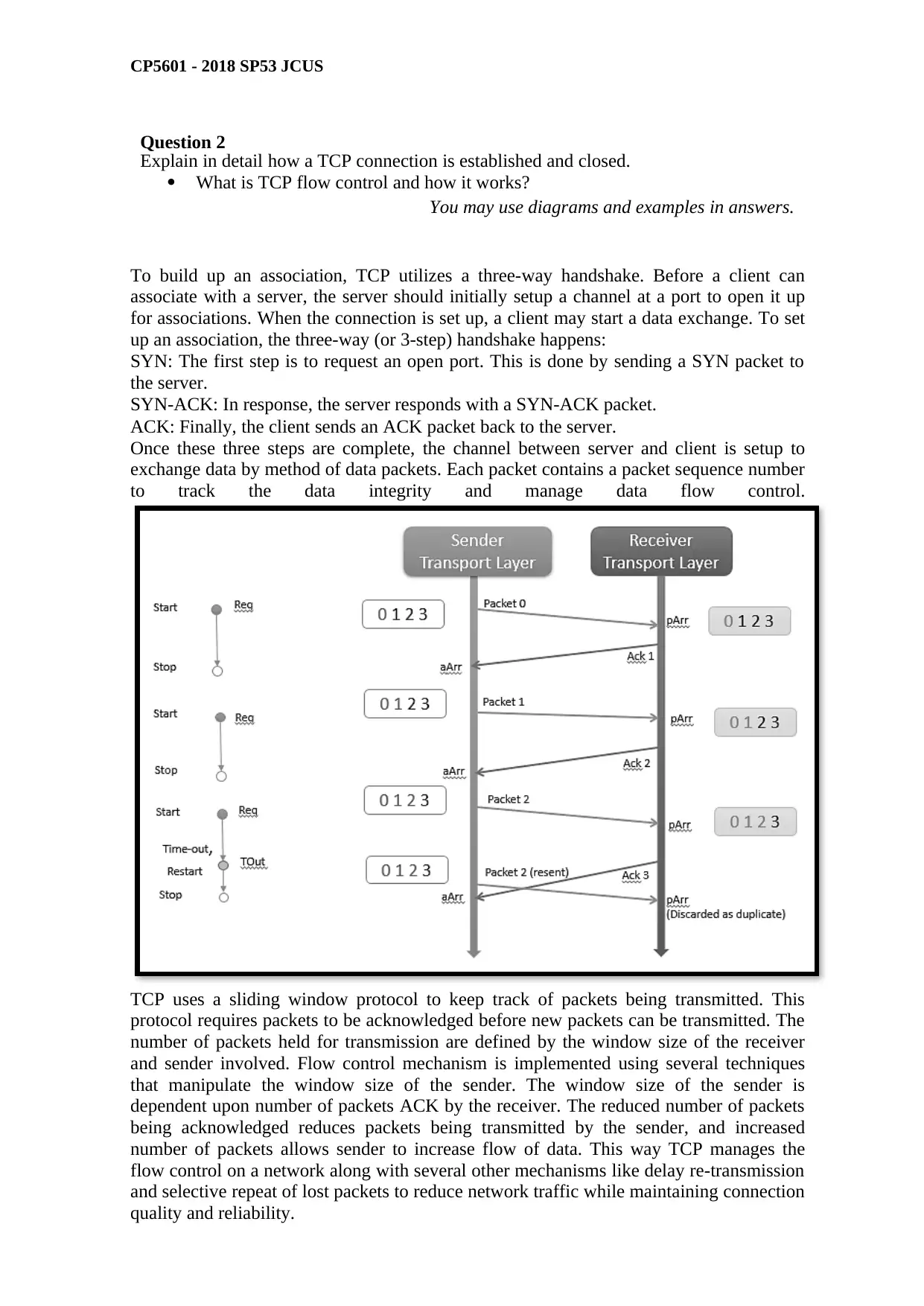
To build up an association, TCP utilizes a three-way handshake. Before a client can
associate with a server, the server should initially setup a channel at a port to open it up
for associations. When the connection is set up, a client may start a data exchange. To set
up an association, the three-way (or 3-step) handshake happens:
SYN: The first step is to request an open port. This is done by sending a SYN packet to
the server.
SYN-ACK: In response, the server responds with a SYN-ACK packet.
ACK: Finally, the client sends an ACK packet back to the server.
Once these three steps are complete, the channel between server and client is setup to
exchange data by method of data packets. Each packet contains a packet sequence number
to track the data integrity and manage data flow control.
TCP uses a sliding window protocol to keep track of packets being transmitted. This
protocol requires packets to be acknowledged before new packets can be transmitted. The
number of packets held for transmission are defined by the window size of the receiver
and sender involved. Flow control mechanism is implemented using several techniques
that manipulate the window size of the sender. The window size of the sender is
dependent upon number of packets ACK by the receiver. The reduced number of packets
being acknowledged reduces packets being transmitted by the sender, and increased
number of packets allows sender to increase flow of data. This way TCP manages the
flow control on a network along with several other mechanisms like delay re-transmission
and selective repeat of lost packets to reduce network traffic while maintaining connection
quality and reliability.
Question 2
Explain in detail how a TCP connection is established and closed.
What is TCP flow control and how it works?
You may use diagrams and examples in answers.
To build up an association, TCP utilizes a three-way handshake. Before a client can
associate with a server, the server should initially setup a channel at a port to open it up
for associations. When the connection is set up, a client may start a data exchange. To set
up an association, the three-way (or 3-step) handshake happens:
SYN: The first step is to request an open port. This is done by sending a SYN packet to
the server.
SYN-ACK: In response, the server responds with a SYN-ACK packet.
ACK: Finally, the client sends an ACK packet back to the server.
Once these three steps are complete, the channel between server and client is setup to
exchange data by method of data packets. Each packet contains a packet sequence number
to track the data integrity and manage data flow control.
TCP uses a sliding window protocol to keep track of packets being transmitted. This
protocol requires packets to be acknowledged before new packets can be transmitted. The
number of packets held for transmission are defined by the window size of the receiver
and sender involved. Flow control mechanism is implemented using several techniques
that manipulate the window size of the sender. The window size of the sender is
dependent upon number of packets ACK by the receiver. The reduced number of packets
being acknowledged reduces packets being transmitted by the sender, and increased
number of packets allows sender to increase flow of data. This way TCP manages the
flow control on a network along with several other mechanisms like delay re-transmission
and selective repeat of lost packets to reduce network traffic while maintaining connection
quality and reliability.

CP5601 - 2018 SP53 JCUS
Question 3
Study the Wikipedia on cellular network and summaries the important aspects.
The elements of cellular networks are:
1. Mobile Network: refers to PLMN (Public Land Mobile Network),
2. Wireless Channel: comprises of the spectrum or the Entire range of the carrier
frequencies used,
3. User Device: refers to the different devices used at the receivers’ end, each with
their own bandwidths and modulation schemes.
The principals involved in the working of cellular networks are:
1. Multiple Access
2. Duplexing
3. Cell sectorization
4. Signal to noise ratios
5. The capacity-coverage-quality tradeoff:
The higher the bit rate per user (quality), the lower the number of users a cell can serve
concurrently (capacity), due to sharing of cell resources. The higher the number of
supported users (capacity), the higher interference levels and hence the lower SINRs and
bit rates (quality). The higher the bit rate (quality) targeted for a cell edge user, the higher
its required SINR needs to be, and hence the nearer the cell edge (coverage) needs to be.
The higher the bit rate (quality) targeted for a cell edge user, the higher its required SINR
needs to be, and hence the nearer the cell edge (coverage) needs to be. The more remote a
cell edge user is (coverage), and hence the lower the correspondingly experienced SINR,
the higher the amount of resources (channel time, spectral bandwidth) the user needs to be
assigned to achieve a given bit rate, and hence the lower the number of users a cell can
serve concurrently (capacity). The bit rate is given by:
The following are the 3G technologies used in cellular networks:
1. GSM(global system for mobile)
2. GPRS(generalized packet radio service)
3. EDGE(enhanced data-rates for GSM evolution)
These are followed by:
4. UMTS(universal mobile Telecommunication System) which is 3G
5. HSDPA(high-speed downlink packet access): which is 3.5G
The technologies following the above are:
6. LTE(long-term evolution) which is 4G
7. LTE-Advanced which is 4.5G
This is followed by
8. 5G technology, which is deployed for use in 2020.
Each of the above technologies have their advantages and disadvantages than draw
the need for the coming of the more advanced further generations.
Question 3
Study the Wikipedia on cellular network and summaries the important aspects.
The elements of cellular networks are:
1. Mobile Network: refers to PLMN (Public Land Mobile Network),
2. Wireless Channel: comprises of the spectrum or the Entire range of the carrier
frequencies used,
3. User Device: refers to the different devices used at the receivers’ end, each with
their own bandwidths and modulation schemes.
The principals involved in the working of cellular networks are:
1. Multiple Access
2. Duplexing
3. Cell sectorization
4. Signal to noise ratios
5. The capacity-coverage-quality tradeoff:
The higher the bit rate per user (quality), the lower the number of users a cell can serve
concurrently (capacity), due to sharing of cell resources. The higher the number of
supported users (capacity), the higher interference levels and hence the lower SINRs and
bit rates (quality). The higher the bit rate (quality) targeted for a cell edge user, the higher
its required SINR needs to be, and hence the nearer the cell edge (coverage) needs to be.
The higher the bit rate (quality) targeted for a cell edge user, the higher its required SINR
needs to be, and hence the nearer the cell edge (coverage) needs to be. The more remote a
cell edge user is (coverage), and hence the lower the correspondingly experienced SINR,
the higher the amount of resources (channel time, spectral bandwidth) the user needs to be
assigned to achieve a given bit rate, and hence the lower the number of users a cell can
serve concurrently (capacity). The bit rate is given by:
The following are the 3G technologies used in cellular networks:
1. GSM(global system for mobile)
2. GPRS(generalized packet radio service)
3. EDGE(enhanced data-rates for GSM evolution)
These are followed by:
4. UMTS(universal mobile Telecommunication System) which is 3G
5. HSDPA(high-speed downlink packet access): which is 3.5G
The technologies following the above are:
6. LTE(long-term evolution) which is 4G
7. LTE-Advanced which is 4.5G
This is followed by
8. 5G technology, which is deployed for use in 2020.
Each of the above technologies have their advantages and disadvantages than draw
the need for the coming of the more advanced further generations.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
CP5601 - 2018 SP53 JCUS
Compare medium access control technologies FDMA, TDMA and CDMA
regards radio frequency, modulation, encoding and etc.
Obtaining input data from more than one source and transmitting it over a single channel
is called multiplexing. Depending upon bit rate of input data, the output channel should
have sufficient bandwidth to accommodate data from all input channels. In case the inputs
have burst nature of data, the buffers need to be added to smoothen out data flow rate. For
a signal, the multiplexing can happen either in time or in frequency domain.
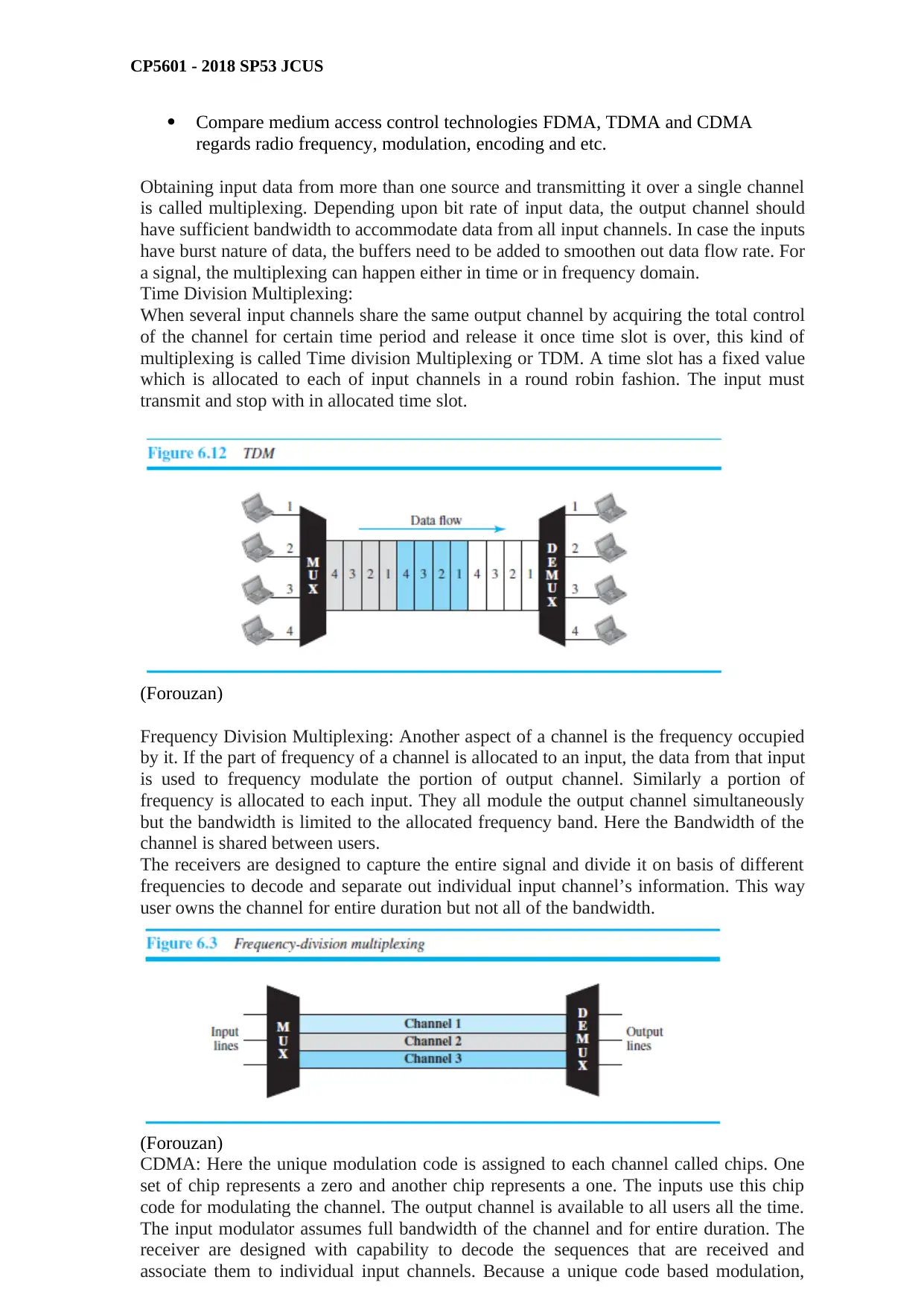
Time Division Multiplexing:
When several input channels share the same output channel by acquiring the total control
of the channel for certain time period and release it once time slot is over, this kind of
multiplexing is called Time division Multiplexing or TDM. A time slot has a fixed value
which is allocated to each of input channels in a round robin fashion. The input must
transmit and stop with in allocated time slot.
(Forouzan)
Frequency Division Multiplexing: Another aspect of a channel is the frequency occupied
by it. If the part of frequency of a channel is allocated to an input, the data from that input
is used to frequency modulate the portion of output channel. Similarly a portion of
frequency is allocated to each input. They all module the output channel simultaneously
but the bandwidth is limited to the allocated frequency band. Here the Bandwidth of the
channel is shared between users.
The receivers are designed to capture the entire signal and divide it on basis of different
frequencies to decode and separate out individual input channel’s information. This way
user owns the channel for entire duration but not all of the bandwidth.
(Forouzan)
CDMA: Here the unique modulation code is assigned to each channel called chips. One
set of chip represents a zero and another chip represents a one. The inputs use this chip
code for modulating the channel. The output channel is available to all users all the time.
The input modulator assumes full bandwidth of the channel and for entire duration. The
receiver are designed with capability to decode the sequences that are received and
associate them to individual input channels. Because a unique code based modulation,
Compare medium access control technologies FDMA, TDMA and CDMA
regards radio frequency, modulation, encoding and etc.
Obtaining input data from more than one source and transmitting it over a single channel
is called multiplexing. Depending upon bit rate of input data, the output channel should
have sufficient bandwidth to accommodate data from all input channels. In case the inputs
have burst nature of data, the buffers need to be added to smoothen out data flow rate. For
a signal, the multiplexing can happen either in time or in frequency domain.
Time Division Multiplexing:
When several input channels share the same output channel by acquiring the total control
of the channel for certain time period and release it once time slot is over, this kind of
multiplexing is called Time division Multiplexing or TDM. A time slot has a fixed value
which is allocated to each of input channels in a round robin fashion. The input must
transmit and stop with in allocated time slot.
(Forouzan)
Frequency Division Multiplexing: Another aspect of a channel is the frequency occupied
by it. If the part of frequency of a channel is allocated to an input, the data from that input
is used to frequency modulate the portion of output channel. Similarly a portion of
frequency is allocated to each input. They all module the output channel simultaneously
but the bandwidth is limited to the allocated frequency band. Here the Bandwidth of the
channel is shared between users.
The receivers are designed to capture the entire signal and divide it on basis of different
frequencies to decode and separate out individual input channel’s information. This way
user owns the channel for entire duration but not all of the bandwidth.
(Forouzan)
CDMA: Here the unique modulation code is assigned to each channel called chips. One
set of chip represents a zero and another chip represents a one. The inputs use this chip
code for modulating the channel. The output channel is available to all users all the time.
The input modulator assumes full bandwidth of the channel and for entire duration. The
receiver are designed with capability to decode the sequences that are received and
associate them to individual input channels. Because a unique code based modulation,
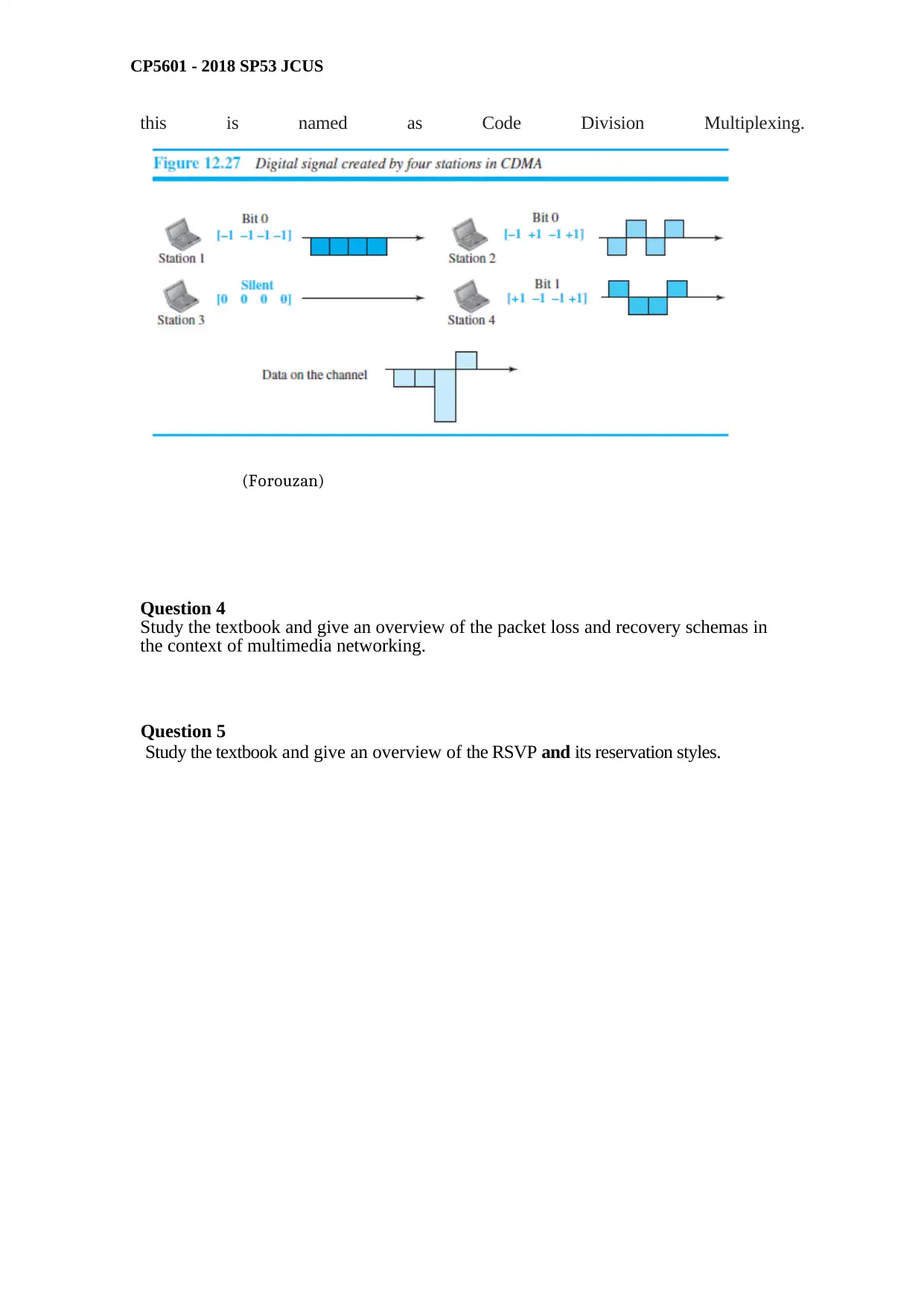
CP5601 - 2018 SP53 JCUS
this is named as Code Division Multiplexing.
(Forouzan)
Question 4
Study the textbook and give an overview of the packet loss and recovery schemas in
the context of multimedia networking.
Question 5
Study the textbook and give an overview of the RSVP and its reservation styles.
this is named as Code Division Multiplexing.
(Forouzan)
Question 4
Study the textbook and give an overview of the packet loss and recovery schemas in
the context of multimedia networking.
Question 5
Study the textbook and give an overview of the RSVP and its reservation styles.

CP5601 - 2018 SP53 JCUS
Question 6
Explain how public key cryptography is used in digital signatures and encryption. Give a
business application for each scenario.
Public key cryptography makes use of public/private keys and does not require a
secure channel for information to be exchanged between the communicators. Public
and private keys are hexadecimal numbers, the first of which can be shared with the
public but the account holder keeps the latter a secret. They are generated using
algorithms such as RSA (Rivest Shamir Adelman) and a related to each other
mathematically.
Digital signatures maintain the authenticity and integrity of any data exchanged on a
network. For creating a digital signature, a one-way hash of the data to be signed, is
created. This hash is then encrypted using a private key. The digital signature
ultimately comprises of the encrypted hash and the hashing algorithm used to encrypt
the one-way data hash.
Use of public-key cryptography with digital signatures and encryption:
1. First the digital signature of the message is created .
2. This message is then encrypted with the private key of the sender and the public
key of the receiver.
3. At the receiver’s side the receiver can decrypt the outer message using his private
key and then the public key of the sender is used to decrypt the inner message.
4. The receiver then runs the message with the hashing algorithm used by the sender
to ensure that nothing happened to the message while it was being sent to the
receiver, i.e. no eavesdropping occurred.
Application: Digital signatures are used to declare the budgets of a country’s govt., its
laws and bills.
Bibliography
Albertorio, A. (n.d.). Public Key Cryptography and Digital Signatures. Retrieved from
https://medium.com: https://medium.com/coinmonks/a-laymans-explanation-of-
public-key-cryptography-and-digital-signatures-1090d4bd072e
Forouzan, B. A. (n.d.). Data Communications and Networking. In B. A. Forouzan, Data
Communications and Networking. McGraw-Hill.
Question 6
Explain how public key cryptography is used in digital signatures and encryption. Give a
business application for each scenario.
Public key cryptography makes use of public/private keys and does not require a
secure channel for information to be exchanged between the communicators. Public
and private keys are hexadecimal numbers, the first of which can be shared with the
public but the account holder keeps the latter a secret. They are generated using
algorithms such as RSA (Rivest Shamir Adelman) and a related to each other
mathematically.
Digital signatures maintain the authenticity and integrity of any data exchanged on a
network. For creating a digital signature, a one-way hash of the data to be signed, is
created. This hash is then encrypted using a private key. The digital signature
ultimately comprises of the encrypted hash and the hashing algorithm used to encrypt
the one-way data hash.
Use of public-key cryptography with digital signatures and encryption:
1. First the digital signature of the message is created .
2. This message is then encrypted with the private key of the sender and the public
key of the receiver.
3. At the receiver’s side the receiver can decrypt the outer message using his private
key and then the public key of the sender is used to decrypt the inner message.
4. The receiver then runs the message with the hashing algorithm used by the sender
to ensure that nothing happened to the message while it was being sent to the
receiver, i.e. no eavesdropping occurred.
Application: Digital signatures are used to declare the budgets of a country’s govt., its
laws and bills.
Bibliography
Albertorio, A. (n.d.). Public Key Cryptography and Digital Signatures. Retrieved from
https://medium.com: https://medium.com/coinmonks/a-laymans-explanation-of-
public-key-cryptography-and-digital-signatures-1090d4bd072e
Forouzan, B. A. (n.d.). Data Communications and Networking. In B. A. Forouzan, Data
Communications and Networking. McGraw-Hill.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





