Comprehensive Analysis of Computer Networks: OSI Model & Protocols
VerifiedAdded on 2023/04/20
|24
|3023
|327
Homework Assignment
AI Summary
This assignment solution provides a comprehensive overview of computer networks, starting with an explanation of the OSI model and the functions of each layer. It delves into TCP/IP protocols, including the 3-way handshake and connection closing mechanisms, highlighting TCP's reliability features such as sequencing, acknowledgements, flow control, and error control. The document also discusses network addressing, subnet masks, and the differences between TCP and UDP, including their applications. Routing protocols like RIP and OSPF are compared, and IPv4 characteristics are outlined. Error detection methods, such as parity checks and Frame Check Sequence (FCS), are explained, along with useful network commands like ping, tracert, and route print. The assignment concludes with a discussion on network devices like bridges and switches, and the benefits of smaller LANs. This document is useful for students looking for past papers and solved assignments.
Running Head: COMPUTER NETWORKS 0 | P a g e
Computer Networks
Individual Task
Student name
Computer Networks
Individual Task
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer Networks 1 | P a g e
1.a Open Systems Interconnect (OSI) model is having seven layers, which are application,
session, presentation, transport, network, data link and physical layer. Host A is sending a
request to the Hub-B for accessing a webpage form the Server F. Host A and Hub B are
connected with physical layer technology, which is Ethernet. Hub-B accepts the request at
physical layer, and forwards it to the Router-C. therefore, these devices are at different layers of
the OSI model, such as Hub-B is at data link layer, Router-C is ate Network Layer, Router-D at
Network Layer, Switch-E at data link layer.
1.b Message size is 2000 bytes. Header size is 200 bytes for each layer. Therefore, total header
size is 1200 bytes. Total size of header and message is 3200 bytes.
So, (1200/3200)*100 = 37.5 %
1.a Open Systems Interconnect (OSI) model is having seven layers, which are application,
session, presentation, transport, network, data link and physical layer. Host A is sending a
request to the Hub-B for accessing a webpage form the Server F. Host A and Hub B are
connected with physical layer technology, which is Ethernet. Hub-B accepts the request at
physical layer, and forwards it to the Router-C. therefore, these devices are at different layers of
the OSI model, such as Hub-B is at data link layer, Router-C is ate Network Layer, Router-D at
Network Layer, Switch-E at data link layer.
1.b Message size is 2000 bytes. Header size is 200 bytes for each layer. Therefore, total header
size is 1200 bytes. Total size of header and message is 3200 bytes.
So, (1200/3200)*100 = 37.5 %

Computer Networks 2 | P a g e
1.c Encapsulation is process in which message is added some bytes for information about the
data and protocols for the understanding the control and data flow. Each layer is having
separated work, such as network layer is used for the node-to-node delivery of the packet.
Therefore, each layer is adding the header in the main message for understand about the packet.
It is like postal services.
1.d client-server model is having a centralized computer, which manage all the other systems.
Client-server model is stable, as it is responding clients for their request. Client-server model is
more scalable, as new client is easily added in the system. Security is high in the Client server
model as it is having access controls for each client separated. Performance of client-server
model is high, as server is dedicated for all the clients. Backup feature is so important for the
safety of the data. It is better in the client-server network model.
1. e a network is required proper addressing of the computer systems. Computer systems are
connected than they are required IP addresses for each system. So, according to choose address
for networking, such as 192.168.10.1 for group of 254 computer systems with a subnet mask,
which is 255.255.255.0. It is also possible by the DHCP.
1.c Encapsulation is process in which message is added some bytes for information about the
data and protocols for the understanding the control and data flow. Each layer is having
separated work, such as network layer is used for the node-to-node delivery of the packet.
Therefore, each layer is adding the header in the main message for understand about the packet.
It is like postal services.
1.d client-server model is having a centralized computer, which manage all the other systems.
Client-server model is stable, as it is responding clients for their request. Client-server model is
more scalable, as new client is easily added in the system. Security is high in the Client server
model as it is having access controls for each client separated. Performance of client-server
model is high, as server is dedicated for all the clients. Backup feature is so important for the
safety of the data. It is better in the client-server network model.
1. e a network is required proper addressing of the computer systems. Computer systems are
connected than they are required IP addresses for each system. So, according to choose address
for networking, such as 192.168.10.1 for group of 254 computer systems with a subnet mask,
which is 255.255.255.0. It is also possible by the DHCP.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Computer Networks 3 | P a g e
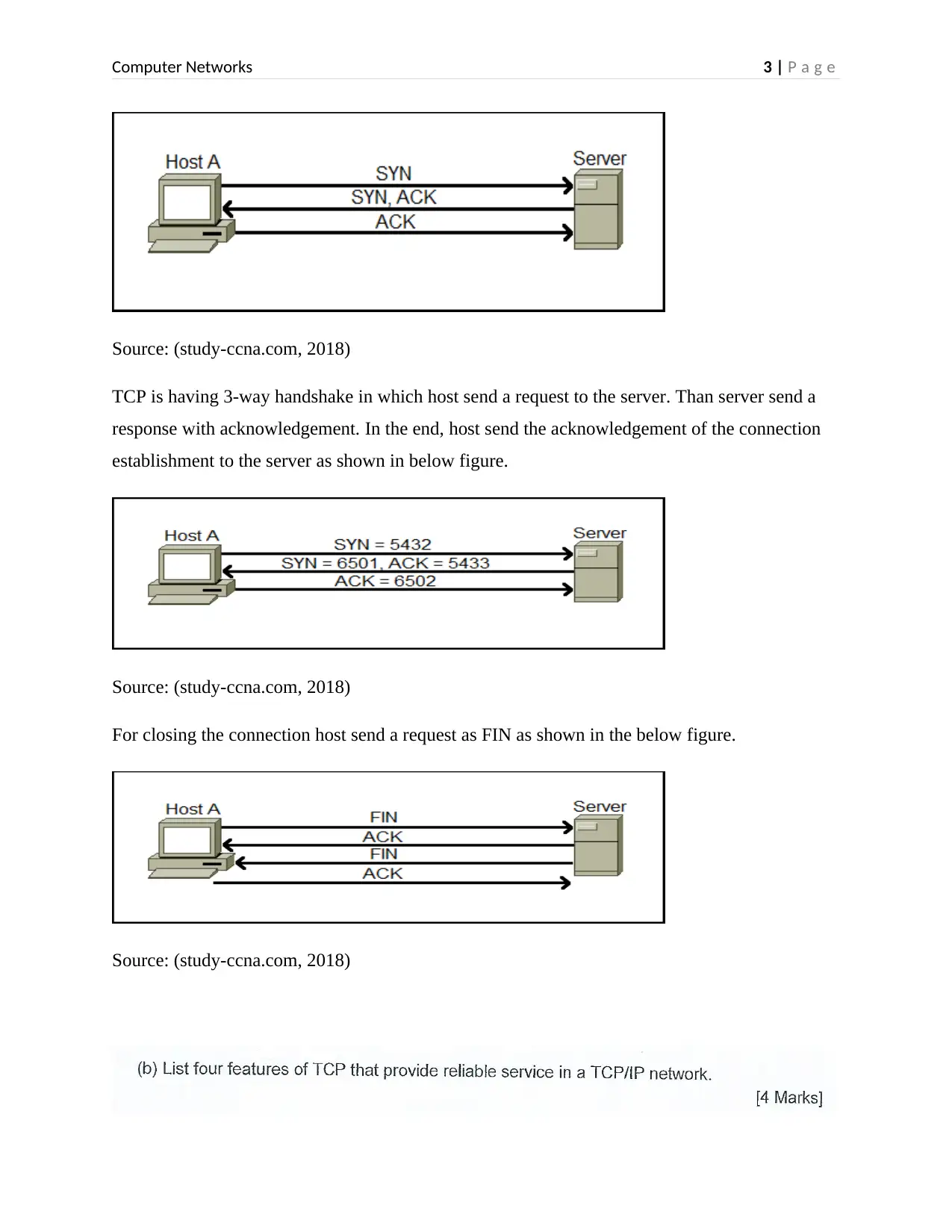
Source: (study-ccna.com, 2018)
TCP is having 3-way handshake in which host send a request to the server. Than server send a
response with acknowledgement. In the end, host send the acknowledgement of the connection
establishment to the server as shown in below figure.
Source: (study-ccna.com, 2018)
For closing the connection host send a request as FIN as shown in the below figure.
Source: (study-ccna.com, 2018)
Source: (study-ccna.com, 2018)
TCP is having 3-way handshake in which host send a request to the server. Than server send a
response with acknowledgement. In the end, host send the acknowledgement of the connection
establishment to the server as shown in below figure.
Source: (study-ccna.com, 2018)
For closing the connection host send a request as FIN as shown in the below figure.
Source: (study-ccna.com, 2018)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer Networks 4 | P a g e
2.b TCP is reliable protocol as it is taking acknowledgement of the packet. Few features make it
more reliable. TCP is providing reliable data transfer. It uses sequence number for the segments.
It provides flow control and error control, which makes it more reliable. It is having connection-
oriented service. TCP is more flexible than other protocols. It is sending data in the ordered way.
It retransmits the lost packets. It is also discarding duplicate packets.
1. TCP is reliable protocol and UDP is unreliable protocol
2. TCP is having sequencing of segments and acknowledgements but UDP is not having it.
2.d i Data in the first segment is 1910-1010 = 900
2.d ii Acknowledgement number is 1010
2.d.iii The value of rwnd = 3500-1000 = 2500.
Host B can receive only 2500 bytes of data before overflowing its buffer. Host B advertises this
value in its next segment to A.
2.b TCP is reliable protocol as it is taking acknowledgement of the packet. Few features make it
more reliable. TCP is providing reliable data transfer. It uses sequence number for the segments.
It provides flow control and error control, which makes it more reliable. It is having connection-
oriented service. TCP is more flexible than other protocols. It is sending data in the ordered way.
It retransmits the lost packets. It is also discarding duplicate packets.
1. TCP is reliable protocol and UDP is unreliable protocol
2. TCP is having sequencing of segments and acknowledgements but UDP is not having it.
2.d i Data in the first segment is 1910-1010 = 900
2.d ii Acknowledgement number is 1010
2.d.iii The value of rwnd = 3500-1000 = 2500.
Host B can receive only 2500 bytes of data before overflowing its buffer. Host B advertises this
value in its next segment to A.
Computer Networks 5 | P a g e
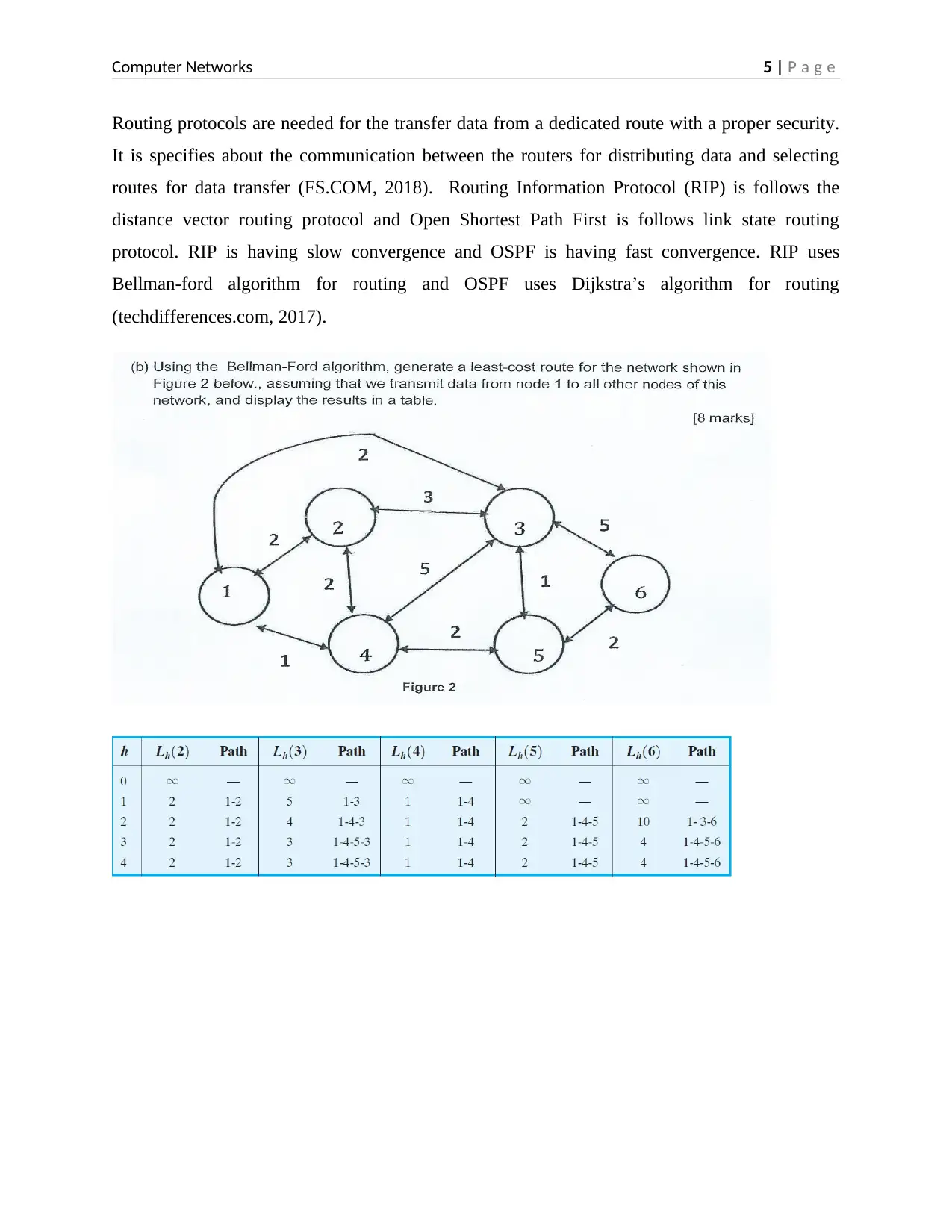
Routing protocols are needed for the transfer data from a dedicated route with a proper security.
It is specifies about the communication between the routers for distributing data and selecting
routes for data transfer (FS.COM, 2018). Routing Information Protocol (RIP) is follows the
distance vector routing protocol and Open Shortest Path First is follows link state routing
protocol. RIP is having slow convergence and OSPF is having fast convergence. RIP uses
Bellman-ford algorithm for routing and OSPF uses Dijkstra’s algorithm for routing
(techdifferences.com, 2017).
Routing protocols are needed for the transfer data from a dedicated route with a proper security.
It is specifies about the communication between the routers for distributing data and selecting
routes for data transfer (FS.COM, 2018). Routing Information Protocol (RIP) is follows the
distance vector routing protocol and Open Shortest Path First is follows link state routing
protocol. RIP is having slow convergence and OSPF is having fast convergence. RIP uses
Bellman-ford algorithm for routing and OSPF uses Dijkstra’s algorithm for routing
(techdifferences.com, 2017).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Computer Networks 6 | P a g e
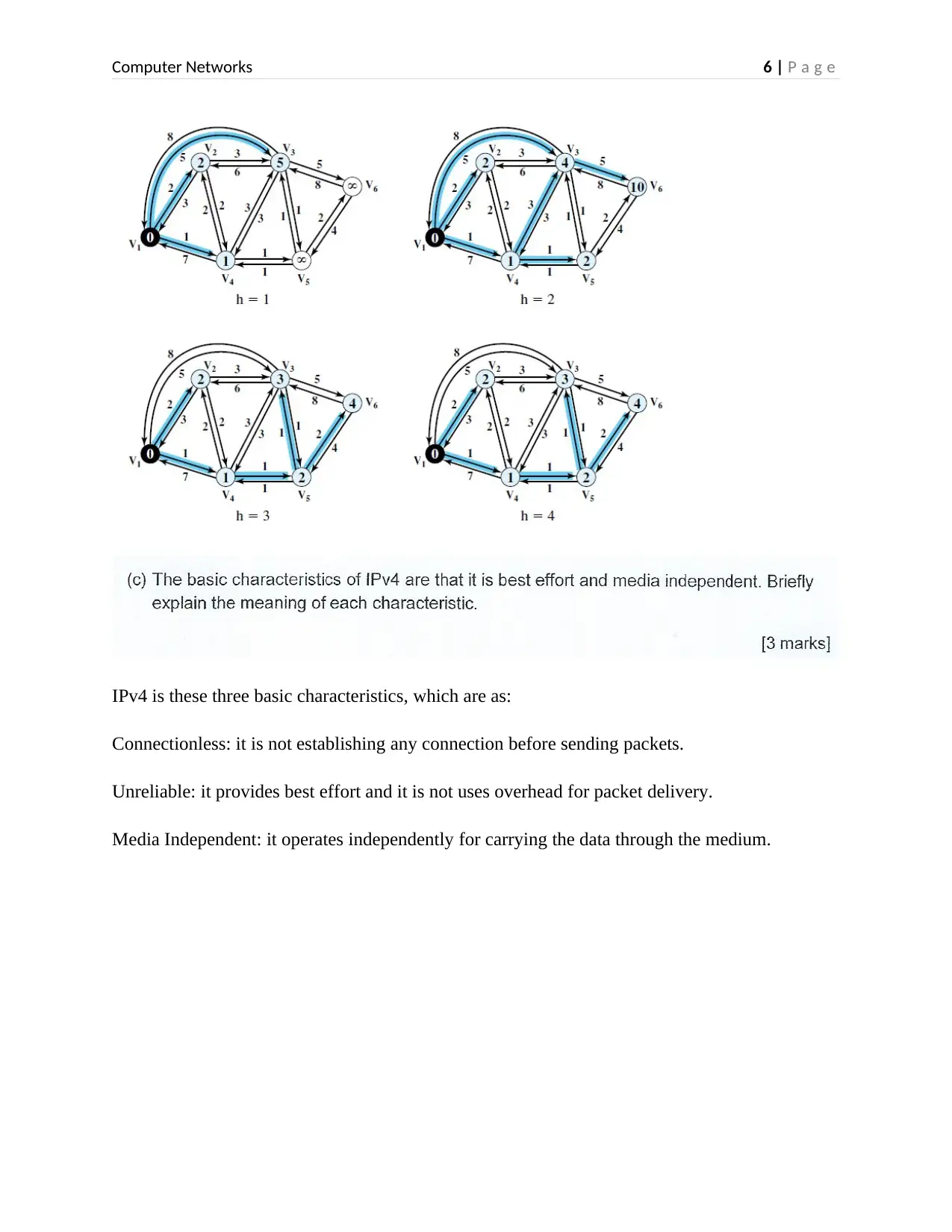
IPv4 is these three basic characteristics, which are as:
Connectionless: it is not establishing any connection before sending packets.
Unreliable: it provides best effort and it is not uses overhead for packet delivery.
Media Independent: it operates independently for carrying the data through the medium.
IPv4 is these three basic characteristics, which are as:
Connectionless: it is not establishing any connection before sending packets.
Unreliable: it provides best effort and it is not uses overhead for packet delivery.
Media Independent: it operates independently for carrying the data through the medium.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer Networks 7 | P a g e
Time to live is 8-bit field in the IPv4 version. It indicates the maximum number of hops in the
network, where datagram can take reach. If, value of time-to-live is equal to zero than packet is
discarded from the network. It is used for avoiding looping.
Type of service is 8 bits field in the IPv4 version. It is used for the Quality of Services (QoS).
i. Address class is C
ii. Subnet mask is 255.255.255.224
iii. 3 bits used for the managing the network from the host-id
Time to live is 8-bit field in the IPv4 version. It indicates the maximum number of hops in the
network, where datagram can take reach. If, value of time-to-live is equal to zero than packet is
discarded from the network. It is used for avoiding looping.
Type of service is 8 bits field in the IPv4 version. It is used for the Quality of Services (QoS).
i. Address class is C
ii. Subnet mask is 255.255.255.224
iii. 3 bits used for the managing the network from the host-id

Computer Networks 8 | P a g e
iv. These are following ranges of the IP addresses for the desired network:
All networks are having 30 hosts.
v. Total number of subnet hosts are 8
vi. Number of usable hosts are 30
vii. 192.168.10.1 - 192.168.10.30
Smaller LAN are more efficient comparatively a larger LAN in an organization. It is also helpful
for the extending the network. Smaller LAN’s are having less congestion. It is helpful to short
out the isolated network problems. Implementation of security is better in the smaller LAN.
iv. These are following ranges of the IP addresses for the desired network:
All networks are having 30 hosts.
v. Total number of subnet hosts are 8
vi. Number of usable hosts are 30
vii. 192.168.10.1 - 192.168.10.30
Smaller LAN are more efficient comparatively a larger LAN in an organization. It is also helpful
for the extending the network. Smaller LAN’s are having less congestion. It is helpful to short
out the isolated network problems. Implementation of security is better in the smaller LAN.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computer Networks 9 | P a g e
i. _ _ 1 _ 0 1 1 _ 0 1 0
Position 1 is having number of one’s in even number at the position 1,3,5,7,9,11, so it is 0
parity
Position 2 is having number of one’s in odd number at the position 2, 3,6,7,10,11 so it is
1 parity
Position 4 is having number of one’s in even at the position 4,5,6,7 so it is having 0 as
parity
Position 8 is having number of one’s in odd number at the position 8, 9,10,11,12 so it is 1
parity
ii. Bit stream transmitted to the channel is 01100111010.
iii. It is a good method for the one-bit error check code and it is based on the even and odd
parity.
iv. It is one-bit error correcting code so if number of bits change more than one than it is
failed to discover the error at the destination.
Frame check Sequence (FCS) is used for the error detection. There are different methods for the
error correction in the frame, such as hamming code, Cyclic Redundancy Check (CRC). There
are different standard for checking of the frame and data in the frame, such as CRC-32.
There is a different command according to the operating system. As an example, in windows arp
–a is a command to locate MAC address of the device. These are the steps for finding MAC
address (Mitchell, 2018).
First, ping the system by using ping command.
i. _ _ 1 _ 0 1 1 _ 0 1 0
Position 1 is having number of one’s in even number at the position 1,3,5,7,9,11, so it is 0
parity
Position 2 is having number of one’s in odd number at the position 2, 3,6,7,10,11 so it is
1 parity
Position 4 is having number of one’s in even at the position 4,5,6,7 so it is having 0 as
parity
Position 8 is having number of one’s in odd number at the position 8, 9,10,11,12 so it is 1
parity
ii. Bit stream transmitted to the channel is 01100111010.
iii. It is a good method for the one-bit error check code and it is based on the even and odd
parity.
iv. It is one-bit error correcting code so if number of bits change more than one than it is
failed to discover the error at the destination.
Frame check Sequence (FCS) is used for the error detection. There are different methods for the
error correction in the frame, such as hamming code, Cyclic Redundancy Check (CRC). There
are different standard for checking of the frame and data in the frame, such as CRC-32.
There is a different command according to the operating system. As an example, in windows arp
–a is a command to locate MAC address of the device. These are the steps for finding MAC
address (Mitchell, 2018).
First, ping the system by using ping command.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer Networks 10 | P a g e
Source: Author
i. Ping is a command for checking availability of the destination computer system. It is
used for checking communication path between the different systems in a network
(Fisher , 2018).
ii. tracert is a command for the finding path of a packet by which it transfers from source to
destination.
iii. route print command is used to view and manipulate the IP routing table.
Source: Author
i. Ping is a command for checking availability of the destination computer system. It is
used for checking communication path between the different systems in a network
(Fisher , 2018).
ii. tracert is a command for the finding path of a packet by which it transfers from source to
destination.
iii. route print command is used to view and manipulate the IP routing table.
Computer Networks 11 | P a g e
i. Bridge is the best device to connecting LAN of different buildings. Bridge is having a
good quality to forwarding of the packet in a selective manner.
ii. Switches are the best way to linking LAN segments in a building to control broadcast
traffic.
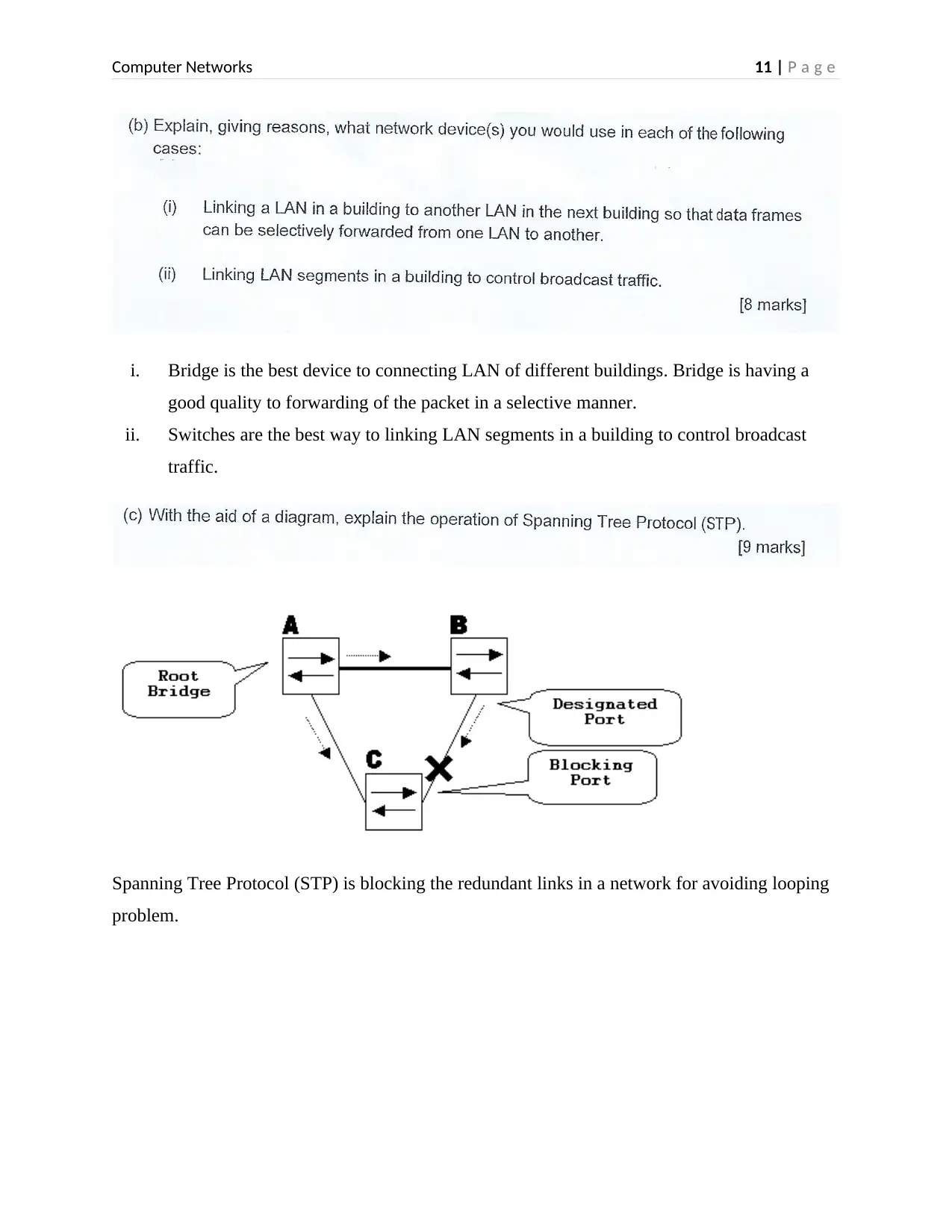
Spanning Tree Protocol (STP) is blocking the redundant links in a network for avoiding looping
problem.
i. Bridge is the best device to connecting LAN of different buildings. Bridge is having a
good quality to forwarding of the packet in a selective manner.
ii. Switches are the best way to linking LAN segments in a building to control broadcast
traffic.
Spanning Tree Protocol (STP) is blocking the redundant links in a network for avoiding looping
problem.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 24
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





