ITC595 Report: Cryptographic Techniques Using Biometric Authentication
VerifiedAdded on 2021/05/31
|4
|3757
|59
Report
AI Summary
This ITC595 research project report explores the security challenges and threats associated with cryptographic techniques that utilize biometric authentication. The study investigates the use of fingerprint-based authentication, encryption, and digital watermarking, including the application of ECC for secure communication. The report provides a literature review, discusses the research problem of improving the performance of cryptographic technology, and highlights the need for robust authentication mechanisms. It examines various protocols, including symmetric and public key cryptography, and emphasizes the importance of addressing key distribution problems. The research presents an experimental analysis using MATLAB R2019B, including comparative studies and block diagrams to illustrate the cryptographic process. The report also addresses the challenges associated with biometric encryption, such as the need for improved image acquisition methods and resilient algorithms. The conclusion summarizes the identified gaps and suggests directions for future research, aiming to enhance the overall security and accuracy of biometric authentication in cryptographic systems.

ITC595 Research Project (Cryptographic Technique
using Biometric Authentication)
A. Author
ITC595 MIT, School of Computing & Mathematics, Charles Sturt University
author@first-third.edu.au
ABSTRACT – This report discusses about the security issues
and threats faced in the cryptographic technology through the use
of biometric authentication and highlight the challenges that has
come across during the research of the whole process in the
individual projects. In the review part, the critical issues
addressed in the current literature will be discussed and the issue
that are not addressed will be highlighted. In the final conclusion
future research will be summarized based on the gaps that were
identified.
Keywords— privacy, security, cryptography, authentication,
biometric
INTRODUCTION
With the use of cryptography various transaction are done to
make the information secure through the internet. The process
of encryption is used to encrypt the plain text into cipher text.
At the receiver’s end, the sender will send the encrypted text
with the information or the key. The receiver then decrypts the
encrypted key by using the information or the key. This paper
contains the concept of cryptography where different algorithm
exists for encryption or decryption. Thus, with the use of
encryption algorithm, the plain text would be encrypted and a
text of information would be achieved. The fingerprint image
of the sender’s would be the key information. At the receiver’s
end the encrypted text with the key will be receive and get the
information from the key with the use of senders Database
fingerprint images. The receiver would then match the
fingerprint geometry of the sender’s with the key. If both the
key matches, then it is easier to derive the information from the
key. In the next step, the encrypted text would be decrypted
through the information that has been achieve. Thus, the whole
process of cryptography is through a binary conversion that
means both the encryption and decryption process uses the
binary form for conversion. Cryptographic technique is
applicable to all data transmission for binary conversion. The
binary conversion is applied on image, text, multimedia data
and lot more that are converted to binary form. In the
cryptographic technique, with the key generation, the recent
fingerprint geometry of the senders would be combined with
the information. Moreover, the sender’s Database fingerprint
geometry which is the collection of fingerprint image of the
sender’s available at the receiver’s side that helps in deriving
the key information. The research paper concentrate on the
performance enhancement of the cryptographic technique using
biometric authentication that has develop a key protocol using
the ECC and design the robust watermark with embedded and
extraction algorithm to achieve a secure communication and
better authentication. The problem definition will be
highlighted and adopt a methodology for the problem.
A. Research Problem
The use of cryptographic technique in the biometric
authentication need some improvement in the performance that
has been undertaken in the research problem for data
transaction with biometric authentication and secure
communication. There are various protocols for development
of authentication that enhance the performance of the technique
used such as symmetric and public key cryptography. Digital
watermarking and cryptography both mechanism are used
traditionally to authenticate the genuine user and secure their
information.
The traditional cryptographic technique uses more than one
key and convert the plain text to the cipher text at the sender
end. In reverse, at the receivers’ end, the plain text will retrieve
back through the use of decryption key. The conversion is
infeasible in the absence of correct decryption keys when both
the cost and time is considered. Thus, when the intruder obtains
the cipher text, it would not be able to extract any useful
information from the text as it is secure. The biggest drawback
of the scheme of information secure, which is a traditional
cryptography, is the illegal way of sharing the key between the
sender and the receiver. This is the key problem of distribution.
The above problem can be rectified by deriving the
cryptographic keys with the use of biometric features. Through
a genuine user the keys have been introduce with the use of
biometric features. It increases the security of information and
decrease the possible illegal utilization.
The research problem is for the improvement of
performance of cryptographic technology using the biometric
technique. This can be achieved by
Integrating conventional biometrics and cryptography that is
design to have a strong authentication mechanism.
Combining digital watermarking technique with
cryptography is design to have a secure communication
LITEERATURE REVIEW
Based on the recent research on cryptographic technique, the
author has derived a string from the typing pattern of the user’s
and has combined the password forming a hard password. Each
feature of the key-stroke is discretised in a single bit. The bits
are then concatenated that has formed by a short string. In one
of the paper of the author, a reliable implementation has
proposed based on the voice of biometrics with the use of
discretization methodology. The report contains an
improvement in the performance. The biometric key entropy
increase from 12 bits to 46 bits and false rejection rate falls
from 48.4 % to 20 %.
Another author had use handwritten signatures to define the
features of forty-three signature that was extracted from some
dynamic information like the pressure, velocity, azimuth, and
altitude. Each feature has been quantizing to a bit by using a
feature coding that has concatenated to binary string. The 40-
bit key entropy was achieved with a rejection rate of 28%.
using Biometric Authentication)
A. Author
ITC595 MIT, School of Computing & Mathematics, Charles Sturt University
author@first-third.edu.au
ABSTRACT – This report discusses about the security issues
and threats faced in the cryptographic technology through the use
of biometric authentication and highlight the challenges that has
come across during the research of the whole process in the
individual projects. In the review part, the critical issues
addressed in the current literature will be discussed and the issue
that are not addressed will be highlighted. In the final conclusion
future research will be summarized based on the gaps that were
identified.
Keywords— privacy, security, cryptography, authentication,
biometric
INTRODUCTION
With the use of cryptography various transaction are done to
make the information secure through the internet. The process
of encryption is used to encrypt the plain text into cipher text.
At the receiver’s end, the sender will send the encrypted text
with the information or the key. The receiver then decrypts the
encrypted key by using the information or the key. This paper
contains the concept of cryptography where different algorithm
exists for encryption or decryption. Thus, with the use of
encryption algorithm, the plain text would be encrypted and a
text of information would be achieved. The fingerprint image
of the sender’s would be the key information. At the receiver’s
end the encrypted text with the key will be receive and get the
information from the key with the use of senders Database
fingerprint images. The receiver would then match the
fingerprint geometry of the sender’s with the key. If both the
key matches, then it is easier to derive the information from the
key. In the next step, the encrypted text would be decrypted
through the information that has been achieve. Thus, the whole
process of cryptography is through a binary conversion that
means both the encryption and decryption process uses the
binary form for conversion. Cryptographic technique is
applicable to all data transmission for binary conversion. The
binary conversion is applied on image, text, multimedia data
and lot more that are converted to binary form. In the
cryptographic technique, with the key generation, the recent
fingerprint geometry of the senders would be combined with
the information. Moreover, the sender’s Database fingerprint
geometry which is the collection of fingerprint image of the
sender’s available at the receiver’s side that helps in deriving
the key information. The research paper concentrate on the
performance enhancement of the cryptographic technique using
biometric authentication that has develop a key protocol using
the ECC and design the robust watermark with embedded and
extraction algorithm to achieve a secure communication and
better authentication. The problem definition will be
highlighted and adopt a methodology for the problem.
A. Research Problem
The use of cryptographic technique in the biometric
authentication need some improvement in the performance that
has been undertaken in the research problem for data
transaction with biometric authentication and secure
communication. There are various protocols for development
of authentication that enhance the performance of the technique
used such as symmetric and public key cryptography. Digital
watermarking and cryptography both mechanism are used
traditionally to authenticate the genuine user and secure their
information.
The traditional cryptographic technique uses more than one
key and convert the plain text to the cipher text at the sender
end. In reverse, at the receivers’ end, the plain text will retrieve
back through the use of decryption key. The conversion is
infeasible in the absence of correct decryption keys when both
the cost and time is considered. Thus, when the intruder obtains
the cipher text, it would not be able to extract any useful
information from the text as it is secure. The biggest drawback
of the scheme of information secure, which is a traditional
cryptography, is the illegal way of sharing the key between the
sender and the receiver. This is the key problem of distribution.
The above problem can be rectified by deriving the
cryptographic keys with the use of biometric features. Through
a genuine user the keys have been introduce with the use of
biometric features. It increases the security of information and
decrease the possible illegal utilization.
The research problem is for the improvement of
performance of cryptographic technology using the biometric
technique. This can be achieved by
Integrating conventional biometrics and cryptography that is
design to have a strong authentication mechanism.
Combining digital watermarking technique with
cryptography is design to have a secure communication
LITEERATURE REVIEW
Based on the recent research on cryptographic technique, the
author has derived a string from the typing pattern of the user’s
and has combined the password forming a hard password. Each
feature of the key-stroke is discretised in a single bit. The bits
are then concatenated that has formed by a short string. In one
of the paper of the author, a reliable implementation has
proposed based on the voice of biometrics with the use of
discretization methodology. The report contains an
improvement in the performance. The biometric key entropy
increase from 12 bits to 46 bits and false rejection rate falls
from 48.4 % to 20 %.
Another author had use handwritten signatures to define the
features of forty-three signature that was extracted from some
dynamic information like the pressure, velocity, azimuth, and
altitude. Each feature has been quantizing to a bit by using a
feature coding that has concatenated to binary string. The 40-
bit key entropy was achieved with a rejection rate of 28%.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

In the criminal cases, fingerprints are among the reliable
biometrics. The author has reported fingerprint as the
biometric-key system and the technology was first
commercialize into a product called as Bioscrypt. From the
fingerprint image the phase information is extracted using
Fourier transform and majority coding is applied that reduces
the feature of variation.
The use of biometric data in accessing the individual devices
increases the limitations of using the password based
mechanism. Biometric data can be stolen and use in malicious
ways. With experience and history, it is clear that extensive use
of something can be monetized and misuse by the criminals.
Numerous efforts were made in the past few years for a
number of research in integrating the biometric authentication
into the cryptography technique. In one of the research, the
author proposed a key binding algorithm in the system
matching an optical correlation-based fingerprint matching
system. In this algorithm, a cryptographic key is bind with the
users’ fingerprint images during the enrollment. The key could
be retrieve only when the authentication is successful. From the
literature review, the encryption and watermarking techniques
can be achieved. In the encryption technique, security is not
provided for the decrypted data. While in watermarking
technique, information is embedded into the host data in order
to achieve security for the decrypted data. The main problem
with the watermarking technique is the tracking mechanism
that can identify the biometric data. Therefore, with the use of
hybrid methodology, both the watermarking and encryption
techniques have the advantage of designing a secure and better
authentication system. Biometric need to be coupled to a
system that provide an identity. Such systems are vulnerable to
traditional security threats and new ones. For a biometric
vendor it is impossible or infeasible to claim and recreate the
enrolled image. The reason for this is because of the record
feature of the templates such as minutiae that are not an image
proprietary. With the use of small portion of the image
template are calculated. The image appears much bigger than
the template. The storage format of biometric has a proprietary
nature that makes infeasible to hack the template.
Davida proposed an iris biometric algorithm that has a
binary representation for the texture of iris Code having a
length of 2048 bits. The Hamming distance is compute by the
biometric matcher between the database template and the input
that represents and compare the threshold in order to identify
whether the samples of biometric is of the same person or not.
Is has been assume by the author that IrisCode can have 10% of
different sample of iris from 2048 bits and also it differs of 45
% of 2048 bits. According to Lifang Wu, developing a
cryptographic technology using biometric authentication is also
based on face biometrics. At the encryption 128-bit binary
vector was achieved through threshold. From the face image
the author has initially obtained the 128-dmensional for the
feature of Principle Component Analysis. With the use of
Reed-Solomon algorithm, error correction code is produced.
Monrose had proposed a method that has made the password
more secure with the combination of keystroke biometric
password. The inspiration came from the password ‘salting’
concept where user password is salted and prepending with 8-
bit number that is random. Thus, it resulted in Harding the
password. The week point of this technique is that it could
handle only 15 bits password entropy to make them more
secure. Integrating biometric authentication in cryptographic
technique is the potential solution to overcome little changes
between different acquirement that have generated a reliable
key. A technique has been developed by Sashank Singhvi that
has exploits features dependent on entropy with the process of
extraction, integrating with error correcting code of Reed
Solomon. Monrose on the other hand, made some
modifications of the original scheme that were applied to
biometric voice. Through this, the cryptography keys are
generated eventually till 60 bits, which is anyhow was higher
than the 15 bits that were achieve in their work earlier. Tuyls
had assume a noise-free template for a biometric identifier for
the purpose of enrollment of the secret and generate the helper
data.
A survey being conducted on the research of cryptographic
technique which is the symmetric and asymmetric
cryptography and their associated problem. During the survey
it was found that the popularity of the ECC system is
increasing to secure the data and communication with the use
of PKC. The public key cryptography implements the key size
of ECC to devices like smart cards and RFID. When
cryptographic algorithm is incorporated with biometric
technologies it strengthens the performance. Thus, with the use
of ECC parameters through fingerprint, a new agreement
protocol is designed that can robust the session key agreement
protocol and iris the purpose of authentication. With the use of
MATLAB R2019B version, experimental research was carried
out to simulate the protocol for the same reason. When the
protocol was run a thorough analysis were made with the use of
sample database that contain 750 each images of iris and
fingerprint. The age group of 20-50 of both male and female
whose fingerprints are collected and from MMU1 and MMU2
of public database, the iris images are collected. All those
results are projected in the table form as shown in figure 1.
Certain challenges have come across with the Biometric
Encryption. If considered technologically, Biometric
Encryption is more difficult compare to standard biometric.
The scheme of Biometric mostly work in ‘blind, mode. There is
consequent section to advance Biometric Encryption for a
prototype making and testing. Generally, a standard biometric
is chosen for low variability, high entropy, alignment and
acceptance of the public. At present, the foremost encryption of
biometric is the iris then comes the fingerprints and face. It has
become important to improve the image acquisition method.
Against the attacks biometric encryption has created resilient. It
is better to improve the Biometric Encryption algorithm for the
overall security and accuracy of Biometric algorithms.
Development with standard biometrics that has advances
within the algorithm and applied ECC to Biometric Encryption.
B. Figures and Tables
biometrics. The author has reported fingerprint as the
biometric-key system and the technology was first
commercialize into a product called as Bioscrypt. From the
fingerprint image the phase information is extracted using
Fourier transform and majority coding is applied that reduces
the feature of variation.
The use of biometric data in accessing the individual devices
increases the limitations of using the password based
mechanism. Biometric data can be stolen and use in malicious
ways. With experience and history, it is clear that extensive use
of something can be monetized and misuse by the criminals.
Numerous efforts were made in the past few years for a
number of research in integrating the biometric authentication
into the cryptography technique. In one of the research, the
author proposed a key binding algorithm in the system
matching an optical correlation-based fingerprint matching
system. In this algorithm, a cryptographic key is bind with the
users’ fingerprint images during the enrollment. The key could
be retrieve only when the authentication is successful. From the
literature review, the encryption and watermarking techniques
can be achieved. In the encryption technique, security is not
provided for the decrypted data. While in watermarking
technique, information is embedded into the host data in order
to achieve security for the decrypted data. The main problem
with the watermarking technique is the tracking mechanism
that can identify the biometric data. Therefore, with the use of
hybrid methodology, both the watermarking and encryption
techniques have the advantage of designing a secure and better
authentication system. Biometric need to be coupled to a
system that provide an identity. Such systems are vulnerable to
traditional security threats and new ones. For a biometric
vendor it is impossible or infeasible to claim and recreate the
enrolled image. The reason for this is because of the record
feature of the templates such as minutiae that are not an image
proprietary. With the use of small portion of the image
template are calculated. The image appears much bigger than
the template. The storage format of biometric has a proprietary
nature that makes infeasible to hack the template.
Davida proposed an iris biometric algorithm that has a
binary representation for the texture of iris Code having a
length of 2048 bits. The Hamming distance is compute by the
biometric matcher between the database template and the input
that represents and compare the threshold in order to identify
whether the samples of biometric is of the same person or not.
Is has been assume by the author that IrisCode can have 10% of
different sample of iris from 2048 bits and also it differs of 45
% of 2048 bits. According to Lifang Wu, developing a
cryptographic technology using biometric authentication is also
based on face biometrics. At the encryption 128-bit binary
vector was achieved through threshold. From the face image
the author has initially obtained the 128-dmensional for the
feature of Principle Component Analysis. With the use of
Reed-Solomon algorithm, error correction code is produced.
Monrose had proposed a method that has made the password
more secure with the combination of keystroke biometric
password. The inspiration came from the password ‘salting’
concept where user password is salted and prepending with 8-
bit number that is random. Thus, it resulted in Harding the
password. The week point of this technique is that it could
handle only 15 bits password entropy to make them more
secure. Integrating biometric authentication in cryptographic
technique is the potential solution to overcome little changes
between different acquirement that have generated a reliable
key. A technique has been developed by Sashank Singhvi that
has exploits features dependent on entropy with the process of
extraction, integrating with error correcting code of Reed
Solomon. Monrose on the other hand, made some
modifications of the original scheme that were applied to
biometric voice. Through this, the cryptography keys are
generated eventually till 60 bits, which is anyhow was higher
than the 15 bits that were achieve in their work earlier. Tuyls
had assume a noise-free template for a biometric identifier for
the purpose of enrollment of the secret and generate the helper
data.
A survey being conducted on the research of cryptographic
technique which is the symmetric and asymmetric
cryptography and their associated problem. During the survey
it was found that the popularity of the ECC system is
increasing to secure the data and communication with the use
of PKC. The public key cryptography implements the key size
of ECC to devices like smart cards and RFID. When
cryptographic algorithm is incorporated with biometric
technologies it strengthens the performance. Thus, with the use
of ECC parameters through fingerprint, a new agreement
protocol is designed that can robust the session key agreement
protocol and iris the purpose of authentication. With the use of
MATLAB R2019B version, experimental research was carried
out to simulate the protocol for the same reason. When the
protocol was run a thorough analysis were made with the use of
sample database that contain 750 each images of iris and
fingerprint. The age group of 20-50 of both male and female
whose fingerprints are collected and from MMU1 and MMU2
of public database, the iris images are collected. All those
results are projected in the table form as shown in figure 1.
Certain challenges have come across with the Biometric
Encryption. If considered technologically, Biometric
Encryption is more difficult compare to standard biometric.
The scheme of Biometric mostly work in ‘blind, mode. There is
consequent section to advance Biometric Encryption for a
prototype making and testing. Generally, a standard biometric
is chosen for low variability, high entropy, alignment and
acceptance of the public. At present, the foremost encryption of
biometric is the iris then comes the fingerprints and face. It has
become important to improve the image acquisition method.
Against the attacks biometric encryption has created resilient. It
is better to improve the Biometric Encryption algorithm for the
overall security and accuracy of Biometric algorithms.
Development with standard biometrics that has advances
within the algorithm and applied ECC to Biometric Encryption.
B. Figures and Tables
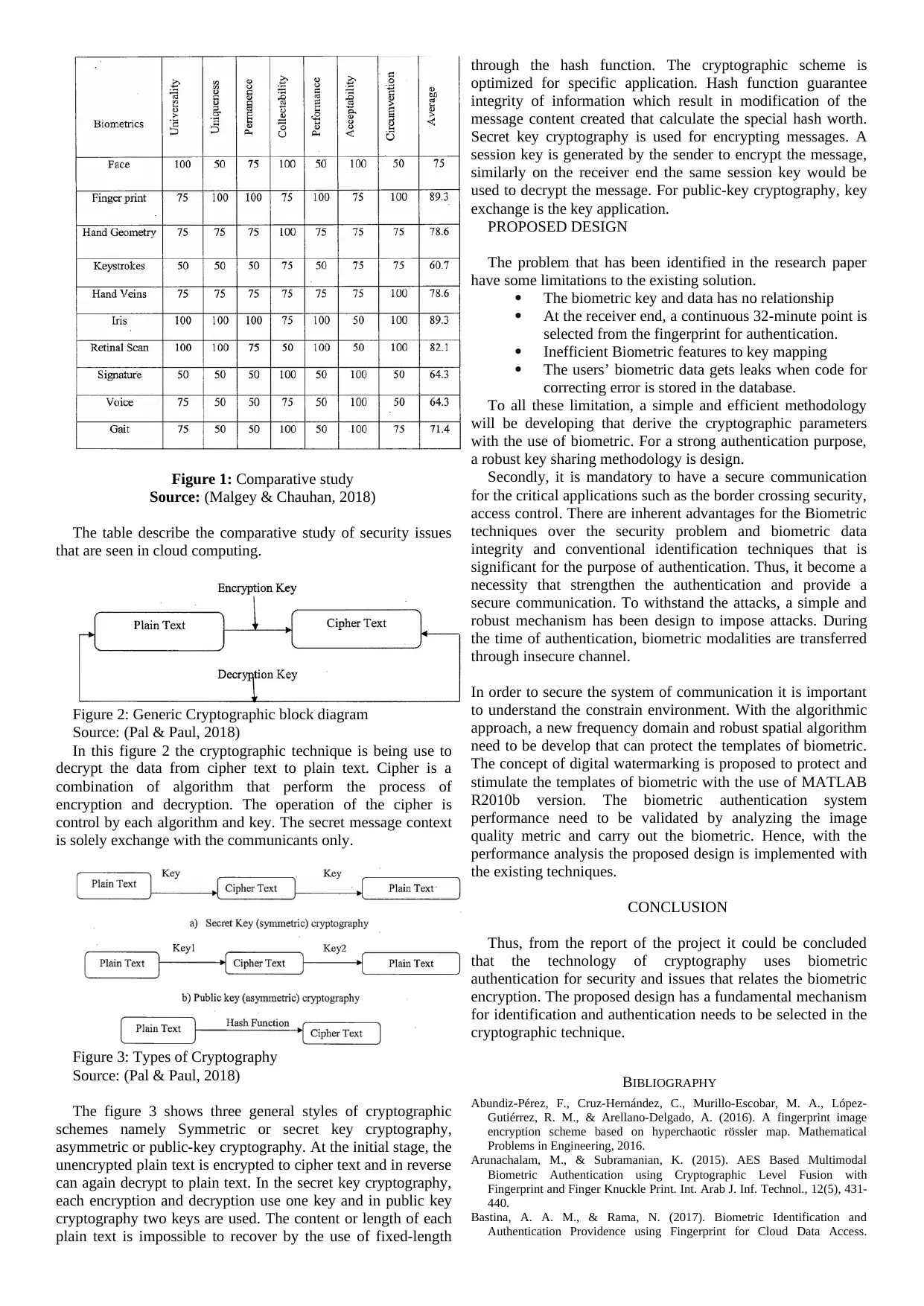
Figure 1: Comparative study
Source: (Malgey & Chauhan, 2018)
The table describe the comparative study of security issues
that are seen in cloud computing.
Figure 2: Generic Cryptographic block diagram
Source: (Pal & Paul, 2018)
In this figure 2 the cryptographic technique is being use to
decrypt the data from cipher text to plain text. Cipher is a
combination of algorithm that perform the process of
encryption and decryption. The operation of the cipher is
control by each algorithm and key. The secret message context
is solely exchange with the communicants only.
Figure 3: Types of Cryptography
Source: (Pal & Paul, 2018)
The figure 3 shows three general styles of cryptographic
schemes namely Symmetric or secret key cryptography,
asymmetric or public-key cryptography. At the initial stage, the
unencrypted plain text is encrypted to cipher text and in reverse
can again decrypt to plain text. In the secret key cryptography,
each encryption and decryption use one key and in public key
cryptography two keys are used. The content or length of each
plain text is impossible to recover by the use of fixed-length
through the hash function. The cryptographic scheme is
optimized for specific application. Hash function guarantee
integrity of information which result in modification of the
message content created that calculate the special hash worth.
Secret key cryptography is used for encrypting messages. A
session key is generated by the sender to encrypt the message,
similarly on the receiver end the same session key would be
used to decrypt the message. For public-key cryptography, key
exchange is the key application.
PROPOSED DESIGN
The problem that has been identified in the research paper
have some limitations to the existing solution.
The biometric key and data has no relationship
At the receiver end, a continuous 32-minute point is
selected from the fingerprint for authentication.
Inefficient Biometric features to key mapping
The users’ biometric data gets leaks when code for
correcting error is stored in the database.
To all these limitation, a simple and efficient methodology
will be developing that derive the cryptographic parameters
with the use of biometric. For a strong authentication purpose,
a robust key sharing methodology is design.
Secondly, it is mandatory to have a secure communication
for the critical applications such as the border crossing security,
access control. There are inherent advantages for the Biometric
techniques over the security problem and biometric data
integrity and conventional identification techniques that is
significant for the purpose of authentication. Thus, it become a
necessity that strengthen the authentication and provide a
secure communication. To withstand the attacks, a simple and
robust mechanism has been design to impose attacks. During
the time of authentication, biometric modalities are transferred
through insecure channel.
In order to secure the system of communication it is important
to understand the constrain environment. With the algorithmic
approach, a new frequency domain and robust spatial algorithm
need to be develop that can protect the templates of biometric.
The concept of digital watermarking is proposed to protect and
stimulate the templates of biometric with the use of MATLAB
R2010b version. The biometric authentication system
performance need to be validated by analyzing the image
quality metric and carry out the biometric. Hence, with the
performance analysis the proposed design is implemented with
the existing techniques.
CONCLUSION
Thus, from the report of the project it could be concluded
that the technology of cryptography uses biometric
authentication for security and issues that relates the biometric
encryption. The proposed design has a fundamental mechanism
for identification and authentication needs to be selected in the
cryptographic technique.
BIBLIOGRAPHY
Abundiz-Pérez, F., Cruz-Hernández, C., Murillo-Escobar, M. A., López-
Gutiérrez, R. M., & Arellano-Delgado, A. (2016). A fingerprint image
encryption scheme based on hyperchaotic rössler map. Mathematical
Problems in Engineering, 2016.
Arunachalam, M., & Subramanian, K. (2015). AES Based Multimodal
Biometric Authentication using Cryptographic Level Fusion with
Fingerprint and Finger Knuckle Print. Int. Arab J. Inf. Technol., 12(5), 431-
440.
Bastina, A. A. M., & Rama, N. (2017). Biometric Identification and
Authentication Providence using Fingerprint for Cloud Data Access.
Source: (Malgey & Chauhan, 2018)
The table describe the comparative study of security issues
that are seen in cloud computing.
Figure 2: Generic Cryptographic block diagram
Source: (Pal & Paul, 2018)
In this figure 2 the cryptographic technique is being use to
decrypt the data from cipher text to plain text. Cipher is a
combination of algorithm that perform the process of
encryption and decryption. The operation of the cipher is
control by each algorithm and key. The secret message context
is solely exchange with the communicants only.
Figure 3: Types of Cryptography
Source: (Pal & Paul, 2018)
The figure 3 shows three general styles of cryptographic
schemes namely Symmetric or secret key cryptography,
asymmetric or public-key cryptography. At the initial stage, the
unencrypted plain text is encrypted to cipher text and in reverse
can again decrypt to plain text. In the secret key cryptography,
each encryption and decryption use one key and in public key
cryptography two keys are used. The content or length of each
plain text is impossible to recover by the use of fixed-length
through the hash function. The cryptographic scheme is
optimized for specific application. Hash function guarantee
integrity of information which result in modification of the
message content created that calculate the special hash worth.
Secret key cryptography is used for encrypting messages. A
session key is generated by the sender to encrypt the message,
similarly on the receiver end the same session key would be
used to decrypt the message. For public-key cryptography, key
exchange is the key application.
PROPOSED DESIGN
The problem that has been identified in the research paper
have some limitations to the existing solution.
The biometric key and data has no relationship
At the receiver end, a continuous 32-minute point is
selected from the fingerprint for authentication.
Inefficient Biometric features to key mapping
The users’ biometric data gets leaks when code for
correcting error is stored in the database.
To all these limitation, a simple and efficient methodology
will be developing that derive the cryptographic parameters
with the use of biometric. For a strong authentication purpose,
a robust key sharing methodology is design.
Secondly, it is mandatory to have a secure communication
for the critical applications such as the border crossing security,
access control. There are inherent advantages for the Biometric
techniques over the security problem and biometric data
integrity and conventional identification techniques that is
significant for the purpose of authentication. Thus, it become a
necessity that strengthen the authentication and provide a
secure communication. To withstand the attacks, a simple and
robust mechanism has been design to impose attacks. During
the time of authentication, biometric modalities are transferred
through insecure channel.
In order to secure the system of communication it is important
to understand the constrain environment. With the algorithmic
approach, a new frequency domain and robust spatial algorithm
need to be develop that can protect the templates of biometric.
The concept of digital watermarking is proposed to protect and
stimulate the templates of biometric with the use of MATLAB
R2010b version. The biometric authentication system
performance need to be validated by analyzing the image
quality metric and carry out the biometric. Hence, with the
performance analysis the proposed design is implemented with
the existing techniques.
CONCLUSION
Thus, from the report of the project it could be concluded
that the technology of cryptography uses biometric
authentication for security and issues that relates the biometric
encryption. The proposed design has a fundamental mechanism
for identification and authentication needs to be selected in the
cryptographic technique.
BIBLIOGRAPHY
Abundiz-Pérez, F., Cruz-Hernández, C., Murillo-Escobar, M. A., López-
Gutiérrez, R. M., & Arellano-Delgado, A. (2016). A fingerprint image
encryption scheme based on hyperchaotic rössler map. Mathematical
Problems in Engineering, 2016.
Arunachalam, M., & Subramanian, K. (2015). AES Based Multimodal
Biometric Authentication using Cryptographic Level Fusion with
Fingerprint and Finger Knuckle Print. Int. Arab J. Inf. Technol., 12(5), 431-
440.
Bastina, A. A. M., & Rama, N. (2017). Biometric Identification and
Authentication Providence using Fingerprint for Cloud Data Access.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

International Journal of Electrical and Computer Engineering (IJECE), 7(1),
408-416.
Bellare, M., Paterson, K. G., & Rogaway, P. (2014, August). Security of
symmetric encryption against mass surveillance. In International
Cryptology Conference (pp. 1-19). Springer, Berlin, Heidelberg.
Chandra, S., Mandal, B., Alam, S. S., & Bhattacharyya, S. (2015). Content
based double encryption algorithm using symmetric key cryptography.
Procedia Computer Science, 57, 1228-1234.
Chen, C., Anada, H., Kawamoto, J., & Sakurai, K. (2016). A Hybrid
Encryption Scheme with Key-cloning Protection: User/Terminal Double
Authentication via Attributes and Fingerprints. J. Internet Serv. Inf. Secur.,
6(2), 23-36.
Durairajan, M. S., & Saravanan, R. (2014). Biometrics based key generation
using Diffie Hellman Key Exchange for enhanced security Mechanism.
International Journal of ChemTech Research, 6(9), 4359-4365.
Ferrag, M. A., Maglaras, L., Derhab, A., Vasilakos, A. V., Rallis, S., &
Janicke, H. (2018). Authentication schemes for Smart Mobile Devices:
Threat Models, Countermeasures, and Open Research Issues. arXiv preprint
arXiv:1803.10281.
Gobi, M., & Kannan, D. (2015). A secured public key cryptosystem for
biometric encryption. International Journal of Computer Science and
Network Security (IJCSNS), 15(1), 49.
Khan, S. H., Akbar, M. A., Shahzad, F., Farooq, M., & Khan, Z. (2015). Secure
biometric template generation for multi-factor authentication. Pattern
Recognition, 48(2), 458-472.
Kumari, D., & Sharma, R. (2016). Analysis of Biometric Authentication
system-Security, Issues and Working using Visual Cryptography.
International Journal of Advanced Research in Computer Science, 7(1).
Mahto, D., & Yadav, D. K. (2015, February). Enhancing security of one-time
password using Elliptic Curve Cryptography with biometrics for e-
commerce applications. In Computer, Communication, Control and
Information Technology (C3IT), 2015 Third International Conference on
(pp. 1-6). IEEE.
Pal, S., & Paul, P. (2018). Cryptographic Technique Using Biometric
Authentication. Retrieved from
http://shodhganga.inflibnet.ac.in/bitstream/10603/124002/9/09_cha
pter%201.pdf
Parmar, P. V., Padhar, S. B., Patel, S. N., Bhatt, N. I., & Jhaveri, R. H. (2014).
Survey of various homomorphic encryption algorithms and schemes.
International Journal of Computer Applications, 91(8).
Premarathne, U., Abuadbba, A., Alabdulatif, A., Khalil, I., Tari, Z., Zomaya,
A., & Buyya, R. (2016). Hybrid cryptographic access control for cloud-
based EHR systems. IEEE Cloud Computing, 3(4), 58-64.
Šeděnka, J., Govindarajan, S., Gasti, P., & Balagani, K. S. (2015). Secure
outsourced biometric authentication with performance evaluation on
smartphones. IEEE Transactions on Information Forensics and Security,
10(2), 384-396.
Selvarani, P., & Malarvizhi, N. (2016). Data Security in Cloud using Multi
Modal Biocryptographic Authentication. Indian Journal of Science and
Technology, 9(34).
Sudhan, S. K. H. H., & Kumar, S. S. (2015). An innovative proposal for secure
cloud authentication using encrypted biometric authentication scheme.
Indian Journal of Science and Technology, 8(35).
Syta, E., Fischer, M. J., Wolinsky, D., Silberschatz, A., Gallegos-García, G., &
Ford, B. (2015, July). Private eyes: Secure remote biometric authentication.
In e-Business and Telecommunications (ICETE), 2015 12th International
Joint Conference on (Vol. 4, pp. 243-250). IEEE.
Toli, C. A., & Preneel, B. (2017, October). Privacy-Preserving Biometric
Authentication Model for e-Finance Applications. In 4rth International
Conference on Information Systems Security and Privacy, ICISSP 2018
(pp. 1-8).
Yadav, D., Malwe, D., Rao, K. S., Kumari, P., Yadav, P., & Deshmukh, P.
(2017). Intensify the security of one-time password using elliptic curve
cryptography with fingerprint for e-commerce application. International
Journal of Engineering Science, 5480.
Zhu, H. F., Jiang, M., Hao, X., & Zhang, Y. (2015). Robust biometrics-based
key agreement scheme with smart cards towards a new architecture. Journal
of Information Hiding and Multimedia Signal Processing, 6(1), 81-98.
408-416.
Bellare, M., Paterson, K. G., & Rogaway, P. (2014, August). Security of
symmetric encryption against mass surveillance. In International
Cryptology Conference (pp. 1-19). Springer, Berlin, Heidelberg.
Chandra, S., Mandal, B., Alam, S. S., & Bhattacharyya, S. (2015). Content
based double encryption algorithm using symmetric key cryptography.
Procedia Computer Science, 57, 1228-1234.
Chen, C., Anada, H., Kawamoto, J., & Sakurai, K. (2016). A Hybrid
Encryption Scheme with Key-cloning Protection: User/Terminal Double
Authentication via Attributes and Fingerprints. J. Internet Serv. Inf. Secur.,
6(2), 23-36.
Durairajan, M. S., & Saravanan, R. (2014). Biometrics based key generation
using Diffie Hellman Key Exchange for enhanced security Mechanism.
International Journal of ChemTech Research, 6(9), 4359-4365.
Ferrag, M. A., Maglaras, L., Derhab, A., Vasilakos, A. V., Rallis, S., &
Janicke, H. (2018). Authentication schemes for Smart Mobile Devices:
Threat Models, Countermeasures, and Open Research Issues. arXiv preprint
arXiv:1803.10281.
Gobi, M., & Kannan, D. (2015). A secured public key cryptosystem for
biometric encryption. International Journal of Computer Science and
Network Security (IJCSNS), 15(1), 49.
Khan, S. H., Akbar, M. A., Shahzad, F., Farooq, M., & Khan, Z. (2015). Secure
biometric template generation for multi-factor authentication. Pattern
Recognition, 48(2), 458-472.
Kumari, D., & Sharma, R. (2016). Analysis of Biometric Authentication
system-Security, Issues and Working using Visual Cryptography.
International Journal of Advanced Research in Computer Science, 7(1).
Mahto, D., & Yadav, D. K. (2015, February). Enhancing security of one-time
password using Elliptic Curve Cryptography with biometrics for e-
commerce applications. In Computer, Communication, Control and
Information Technology (C3IT), 2015 Third International Conference on
(pp. 1-6). IEEE.
Pal, S., & Paul, P. (2018). Cryptographic Technique Using Biometric
Authentication. Retrieved from
http://shodhganga.inflibnet.ac.in/bitstream/10603/124002/9/09_cha
pter%201.pdf
Parmar, P. V., Padhar, S. B., Patel, S. N., Bhatt, N. I., & Jhaveri, R. H. (2014).
Survey of various homomorphic encryption algorithms and schemes.
International Journal of Computer Applications, 91(8).
Premarathne, U., Abuadbba, A., Alabdulatif, A., Khalil, I., Tari, Z., Zomaya,
A., & Buyya, R. (2016). Hybrid cryptographic access control for cloud-
based EHR systems. IEEE Cloud Computing, 3(4), 58-64.
Šeděnka, J., Govindarajan, S., Gasti, P., & Balagani, K. S. (2015). Secure
outsourced biometric authentication with performance evaluation on
smartphones. IEEE Transactions on Information Forensics and Security,
10(2), 384-396.
Selvarani, P., & Malarvizhi, N. (2016). Data Security in Cloud using Multi
Modal Biocryptographic Authentication. Indian Journal of Science and
Technology, 9(34).
Sudhan, S. K. H. H., & Kumar, S. S. (2015). An innovative proposal for secure
cloud authentication using encrypted biometric authentication scheme.
Indian Journal of Science and Technology, 8(35).
Syta, E., Fischer, M. J., Wolinsky, D., Silberschatz, A., Gallegos-García, G., &
Ford, B. (2015, July). Private eyes: Secure remote biometric authentication.
In e-Business and Telecommunications (ICETE), 2015 12th International
Joint Conference on (Vol. 4, pp. 243-250). IEEE.
Toli, C. A., & Preneel, B. (2017, October). Privacy-Preserving Biometric
Authentication Model for e-Finance Applications. In 4rth International
Conference on Information Systems Security and Privacy, ICISSP 2018
(pp. 1-8).
Yadav, D., Malwe, D., Rao, K. S., Kumari, P., Yadav, P., & Deshmukh, P.
(2017). Intensify the security of one-time password using elliptic curve
cryptography with fingerprint for e-commerce application. International
Journal of Engineering Science, 5480.
Zhu, H. F., Jiang, M., Hao, X., & Zhang, Y. (2015). Robust biometrics-based
key agreement scheme with smart cards towards a new architecture. Journal
of Information Hiding and Multimedia Signal Processing, 6(1), 81-98.
1 out of 4
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


