CSC8419 Assignment: Cryptography, MD5, Secret Communication, SSL
VerifiedAdded on 2024/05/29
|13
|1547
|169
Practical Assignment
AI Summary
This assignment solution for CSC8419 Cryptography and Security explores various aspects of cryptographic techniques. It includes verifying a Debian DVD ISO image file using the MD5 algorithm, detailing the steps for image creation and signature verification. The solution further elucidates a secret communication process between a student and teacher using public and private keys for secure exchange. Additionally, it delves into generating digital certificates using OpenSSL, covering private key creation, public key generation, and certificate verification. The document references academic sources to support its explanations and conclusions, providing a comprehensive overview of cryptography and security principles.

CSC8419
Assignment 1
Cryptography and Security
Student Name:
Student Number:
0
Assignment 1
Cryptography and Security
Student Name:
Student Number:
0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1..........................................................................................................................................................2
Task 2..........................................................................................................................................................4
Task 4..........................................................................................................................................................8
Introduction.............................................................................................................................................8
Background.............................................................................................................................................8
Conclusion...............................................................................................................................................9
Reference:.................................................................................................................................................10
List of Figure
Figure 1: ISO image file extracted through MD5 Algorithm step 1..............................................................2
Figure 2: ISO image file extracted through MD5 Algorithm step 2..............................................................2
Figure 3: ISO image file extracted through MD5 Algorithm step 3.............................................................2
Figure 4: : ISO image file extracted through MD5 Algorithm step...............................................................3
Figure 5: ID of finger print...........................................................................................................................3
Figure 6: ISO image file extracted through MD5 Algorithm step 5..............................................................3
Figure 7: Secret communication Phase 1.....................................................................................................4
Figure 8: Secret communication Phase 2.....................................................................................................5
Figure 9: Secret communication Phase 3.....................................................................................................6
Figure 10: Secret communication phase 4...................................................................................................6
1
Task 1..........................................................................................................................................................2
Task 2..........................................................................................................................................................4
Task 4..........................................................................................................................................................8
Introduction.............................................................................................................................................8
Background.............................................................................................................................................8
Conclusion...............................................................................................................................................9
Reference:.................................................................................................................................................10
List of Figure
Figure 1: ISO image file extracted through MD5 Algorithm step 1..............................................................2
Figure 2: ISO image file extracted through MD5 Algorithm step 2..............................................................2
Figure 3: ISO image file extracted through MD5 Algorithm step 3.............................................................2
Figure 4: : ISO image file extracted through MD5 Algorithm step...............................................................3
Figure 5: ID of finger print...........................................................................................................................3
Figure 6: ISO image file extracted through MD5 Algorithm step 5..............................................................3
Figure 7: Secret communication Phase 1.....................................................................................................4
Figure 8: Secret communication Phase 2.....................................................................................................5
Figure 9: Secret communication Phase 3.....................................................................................................6
Figure 10: Secret communication phase 4...................................................................................................6
1

Task 1
Debian DVD ISO image file can be download from the HTTP server such as Debian server. The image
file is downloading from the https://goo.gl/8CNeyc. SHA-1 and the MD5 algorithm can be used for
verification process. I have used MD5 algorithms. This algorithm used encrypted the signature for the
verification. Following steps are used to the creation of ISO image such as
1. It designs the directory files which saved all files single place and confirmation locations of files
are correct.
Figure 1: ISO image file extracted through MD5 Algorithm step 1
2. After that, there is used GNU Privacy Guard for the encrypted signature verification that is
created with the help of an MD5 algorithm.
Figure 2: ISO image file extracted through MD5 Algorithm step 2
In this process, the public key is not created. So there are used gpg commands and extracted
an ID such as ID = ‘6294BE9B’. With the help of ID, gpg commands extracted the public
key.
3. The public key is download form Debian keyring sever with the help of id = ‘6294BE9B’
2
Debian DVD ISO image file can be download from the HTTP server such as Debian server. The image
file is downloading from the https://goo.gl/8CNeyc. SHA-1 and the MD5 algorithm can be used for
verification process. I have used MD5 algorithms. This algorithm used encrypted the signature for the
verification. Following steps are used to the creation of ISO image such as
1. It designs the directory files which saved all files single place and confirmation locations of files
are correct.
Figure 1: ISO image file extracted through MD5 Algorithm step 1
2. After that, there is used GNU Privacy Guard for the encrypted signature verification that is
created with the help of an MD5 algorithm.
Figure 2: ISO image file extracted through MD5 Algorithm step 2
In this process, the public key is not created. So there are used gpg commands and extracted
an ID such as ID = ‘6294BE9B’. With the help of ID, gpg commands extracted the public
key.
3. The public key is download form Debian keyring sever with the help of id = ‘6294BE9B’
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 3: ISO image file extracted through MD5 Algorithm step 3
4. There are performed the verification process MD5 algorithm files.
Figure 4: ISO image file extracted through MD5 Algorithm step
There are created Good signature with the help of Debian CD signing key. There are also created the
fingerprint with the help of DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B key and compared
the SHS-1 fingerprint with the key fingerprint.
Figure 5: ID of fingerprint
5. After that, there is performed ISO image verification process with image content and the testing
process performed through checksum files
3
4. There are performed the verification process MD5 algorithm files.
Figure 4: ISO image file extracted through MD5 Algorithm step
There are created Good signature with the help of Debian CD signing key. There are also created the
fingerprint with the help of DF9B 9C49 EAA9 2984 3258 9D76 DA87 E80D 6294 BE9B key and compared
the SHS-1 fingerprint with the key fingerprint.
Figure 5: ID of fingerprint
5. After that, there is performed ISO image verification process with image content and the testing
process performed through checksum files
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 6: ISO image file extracted through MD5 Algorithm step 5
4
4

Task 2
Here, explained the secret communication process between student and teacher. Secret communication
uses the public and private key.
1. Text and encoded format are used to the representation of the global public parameter
Figure 7: Secret communication Phase 1
2. The public key and private key are used for Public parameters generation.
5
Here, explained the secret communication process between student and teacher. Secret communication
uses the public and private key.
1. Text and encoded format are used to the representation of the global public parameter
Figure 7: Secret communication Phase 1
2. The public key and private key are used for Public parameters generation.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 8: Secret communication Phase 2
3. There are retrieved the public key
6
3. There are retrieved the public key
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
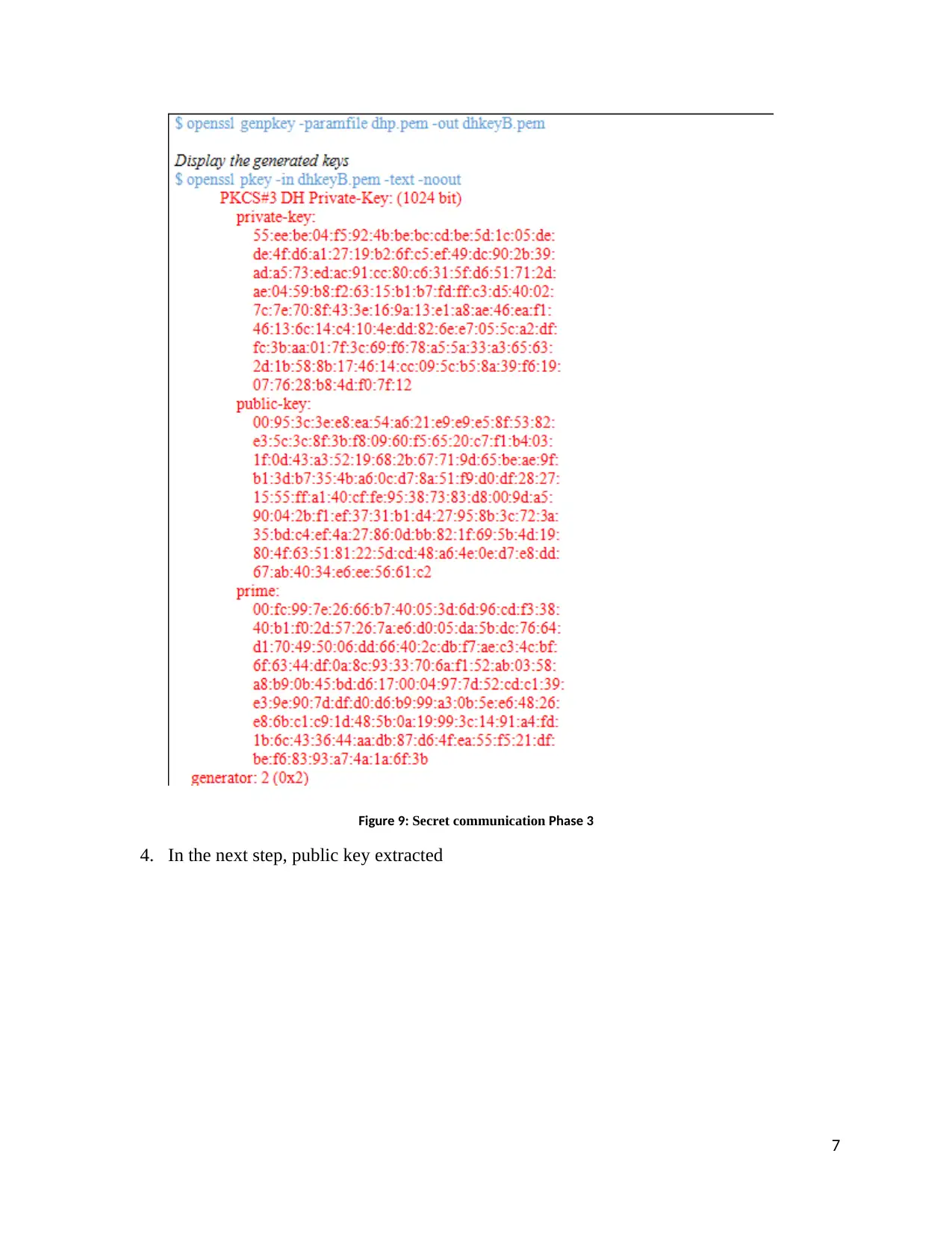
Figure 9: Secret communication Phase 3
4. In the next step, public key extracted
7
4. In the next step, public key extracted
7

Figure 10: Secret communication phase 4
5. After that, the teacher shared their secret key through their public key and private key. In
the end, student side generated a secret key and match both side secret key if both are
same then teacher secret key is right.
8
5. After that, the teacher shared their secret key through their public key and private key. In
the end, student side generated a secret key and match both side secret key if both are
same then teacher secret key is right.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 4
Introduction
Open SSL is a command line apparatus that are used in the HTTPS (HTTP over TLS) PKI (Public Key
Infrastructure) task. Creation of the private keys, certificate format conversion, and certificate signing
requests are the example of the Open SSL commands ((Armknecht, Gasmi, Sadeghi, Stewin, Unger,
Ramunno, and Vernizzi, 2008,). A digital certificate is an electronic password that works on
authentication process for user or system allow on the website. Certification authorities are used for
message passing process. It sent and received the data on the network in the packet format. Public key
certificates and identity certificate is also known as a digital certificate ( Debry, International Business
Machines Corp, 2001). Open SSL is an open cryptography library that is implemented on the Transport
layer security (TLS) and Secure sockets layer (SSL). Both layers worked as protocols in the network. The
report will be explained about generate the digital certificate so there are explained such steps for the
digital certificate creation.
Background
A digital certificate is created with the help of the private key, self-signed certificate, and certificate
signing request (CSR). Here, explained the steps which are needs for the generation of digital certificate
process.
Produce Private Key: First of all, there are created the private key through the certificate signing request
(CSR) and Rivest-Shamir-Adleman algorithm (RSA). The private key may be created in the PEM format
because SAS use the PEM format during the execution of the UNIX operating system. After that, there
are sent a request for the digital certificate on servers.
Public key Generation: the Public key is Generated through Certification authority (CA) and the server
it is an optional step because there are created some challenges during the public key Generation such as
It needs a number of commands in the right order if any change the order of commands, there
is not created the Public key
During the Public key Generation, it shows the sensitive information (Viega, Messier, and
Chandra, 2002).
9
Introduction
Open SSL is a command line apparatus that are used in the HTTPS (HTTP over TLS) PKI (Public Key
Infrastructure) task. Creation of the private keys, certificate format conversion, and certificate signing
requests are the example of the Open SSL commands ((Armknecht, Gasmi, Sadeghi, Stewin, Unger,
Ramunno, and Vernizzi, 2008,). A digital certificate is an electronic password that works on
authentication process for user or system allow on the website. Certification authorities are used for
message passing process. It sent and received the data on the network in the packet format. Public key
certificates and identity certificate is also known as a digital certificate ( Debry, International Business
Machines Corp, 2001). Open SSL is an open cryptography library that is implemented on the Transport
layer security (TLS) and Secure sockets layer (SSL). Both layers worked as protocols in the network. The
report will be explained about generate the digital certificate so there are explained such steps for the
digital certificate creation.
Background
A digital certificate is created with the help of the private key, self-signed certificate, and certificate
signing request (CSR). Here, explained the steps which are needs for the generation of digital certificate
process.
Produce Private Key: First of all, there are created the private key through the certificate signing request
(CSR) and Rivest-Shamir-Adleman algorithm (RSA). The private key may be created in the PEM format
because SAS use the PEM format during the execution of the UNIX operating system. After that, there
are sent a request for the digital certificate on servers.
Public key Generation: the Public key is Generated through Certification authority (CA) and the server
it is an optional step because there are created some challenges during the public key Generation such as
It needs a number of commands in the right order if any change the order of commands, there
is not created the Public key
During the Public key Generation, it shows the sensitive information (Viega, Messier, and
Chandra, 2002).
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Private Key File needs the Security: Network is secured through with the help of password which
prevents unauthorized access to the Private Key File. It accesses the only password. Security is provided
Private Key File after the private key creation I the network (Bellare, and Yee, 2003).
Digital certificate Checking process: In this process, user check the Digital certificate with the help of
following command such as
OpenSSL > 509 – text –in filename. Pem
Creation of the certificate: There is created a certificate through the PEM format. It is created for user
and server for the authentication process. OpenSSL is recognized for the trusted Certification authority.
This process is known as a chain of trust.
Verification of the certificate: In this steps, the certificates are Verified with a chain of trust through
OpenSSL. Digital certificates are exchanged between the client and servers. During the exchange process,
there are need a valid certificate for the server which helps the creation of trust chain (Liu, Au, and
Susilo, 2007).
OpenSSL Exist: There type the quit command to end process and exist from sever.
10
prevents unauthorized access to the Private Key File. It accesses the only password. Security is provided
Private Key File after the private key creation I the network (Bellare, and Yee, 2003).
Digital certificate Checking process: In this process, user check the Digital certificate with the help of
following command such as
OpenSSL > 509 – text –in filename. Pem
Creation of the certificate: There is created a certificate through the PEM format. It is created for user
and server for the authentication process. OpenSSL is recognized for the trusted Certification authority.
This process is known as a chain of trust.
Verification of the certificate: In this steps, the certificates are Verified with a chain of trust through
OpenSSL. Digital certificates are exchanged between the client and servers. During the exchange process,
there are need a valid certificate for the server which helps the creation of trust chain (Liu, Au, and
Susilo, 2007).
OpenSSL Exist: There type the quit command to end process and exist from sever.
10

Conclusion
OpenSSL is a library which is used in the digital certificate creation. There are used such steps to the
creation of digital certificates like Produce Private Key and Public key for the digital certificate. The
second steps, it removed the passphrase. A digital certificate is created through self-signed so there are
installed the private key and created a valid certificate through the trust chain. Final steps restart the
apache system for the testing process. A digital certificate is created with the help of a private key, public
key, and CSR.
11
OpenSSL is a library which is used in the digital certificate creation. There are used such steps to the
creation of digital certificates like Produce Private Key and Public key for the digital certificate. The
second steps, it removed the passphrase. A digital certificate is created through self-signed so there are
installed the private key and created a valid certificate through the trust chain. Final steps restart the
apache system for the testing process. A digital certificate is created with the help of a private key, public
key, and CSR.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





