CSC8419 Cryptography and Security: Debian ISO Verification & Report
VerifiedAdded on 2024/05/29
|14
|1535
|160
Report
AI Summary
This report provides a detailed analysis of cryptography and security concepts, focusing on the verification of a Debian DVD ISO image and key exchange methods. The report outlines the steps taken to verify the integrity and authenticity of the Debian ISO image using GNU Privacy Guard and checksum comparisons. Additionally, it explores the process of extracting public and private keys for shared secret key generation. The report also includes an abstract that discusses the importance of data security and the use of block cipher algorithms like DES (Data Encryption Standard) and AES (Advanced Encryption Standard). It further elaborates on the operations, strengths, weaknesses, applications, and future possibilities of both DES and AES algorithms, concluding that AES offers better encryption and security due to its wider range of key sizes.

CSC8419 - CRYPTOGRAPHY AND SECURITY - ASSIGNMENT 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task 1...............................................................................................................................................2
Task 2...............................................................................................................................................5
Task 3...............................................................................................................................................9
Task 4.............................................................................................................................................10
References......................................................................................................................................13
1
Task 1...............................................................................................................................................2
Task 2...............................................................................................................................................5
Task 3...............................................................................................................................................9
Task 4.............................................................................................................................................10
References......................................................................................................................................13
1

Task 1
Verification of the Debian DVD ISO image
For the verification, the entire files have been downloaded from the website:
https://goo.gl/8CNeyc . In order to check the completeness of the ISO images including its
signature files for SHA-1, the following steps are done.
In the first step, entire files are documented in the directory so that every file should be at
the proper place
Now go for the check for correct signature with the help of GNU Privacy Guard. This
check is for SHA-1.
As the command will run for the first time, there is no availability of the public key on
the system. This command will let the result as ID= ‘6294BE9B’. This ID will help in
retrieving the public key as explained in the step below.
Now, from the Debian key server, download the public key by using the ID ‘6294BE9B’
2
Verification of the Debian DVD ISO image
For the verification, the entire files have been downloaded from the website:
https://goo.gl/8CNeyc . In order to check the completeness of the ISO images including its
signature files for SHA-1, the following steps are done.
In the first step, entire files are documented in the directory so that every file should be at
the proper place
Now go for the check for correct signature with the help of GNU Privacy Guard. This
check is for SHA-1.
As the command will run for the first time, there is no availability of the public key on
the system. This command will let the result as ID= ‘6294BE9B’. This ID will help in
retrieving the public key as explained in the step below.
Now, from the Debian key server, download the public key by using the ID ‘6294BE9B’
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

In this step, the verification is done on both the checksum files by comparing the
signature files
In order to confirm the authenticity of the image of Debian DVD, a statement is appeared
as “Good signature from "Debian CD signing key <debian-cd@lists.debian.org>”. For
the comparison of the listed key in the link: https://www.debian.org/CD/verify, the
generated fingerprint key is used and the key is DF9B 9C49 EAA9 2984 3258 9D76
DA87 E80D 6294 BE9B which matches to the listed fingerprint keys.
3
signature files
In order to confirm the authenticity of the image of Debian DVD, a statement is appeared
as “Good signature from "Debian CD signing key <debian-cd@lists.debian.org>”. For
the comparison of the listed key in the link: https://www.debian.org/CD/verify, the
generated fingerprint key is used and the key is DF9B 9C49 EAA9 2984 3258 9D76
DA87 E80D 6294 BE9B which matches to the listed fingerprint keys.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
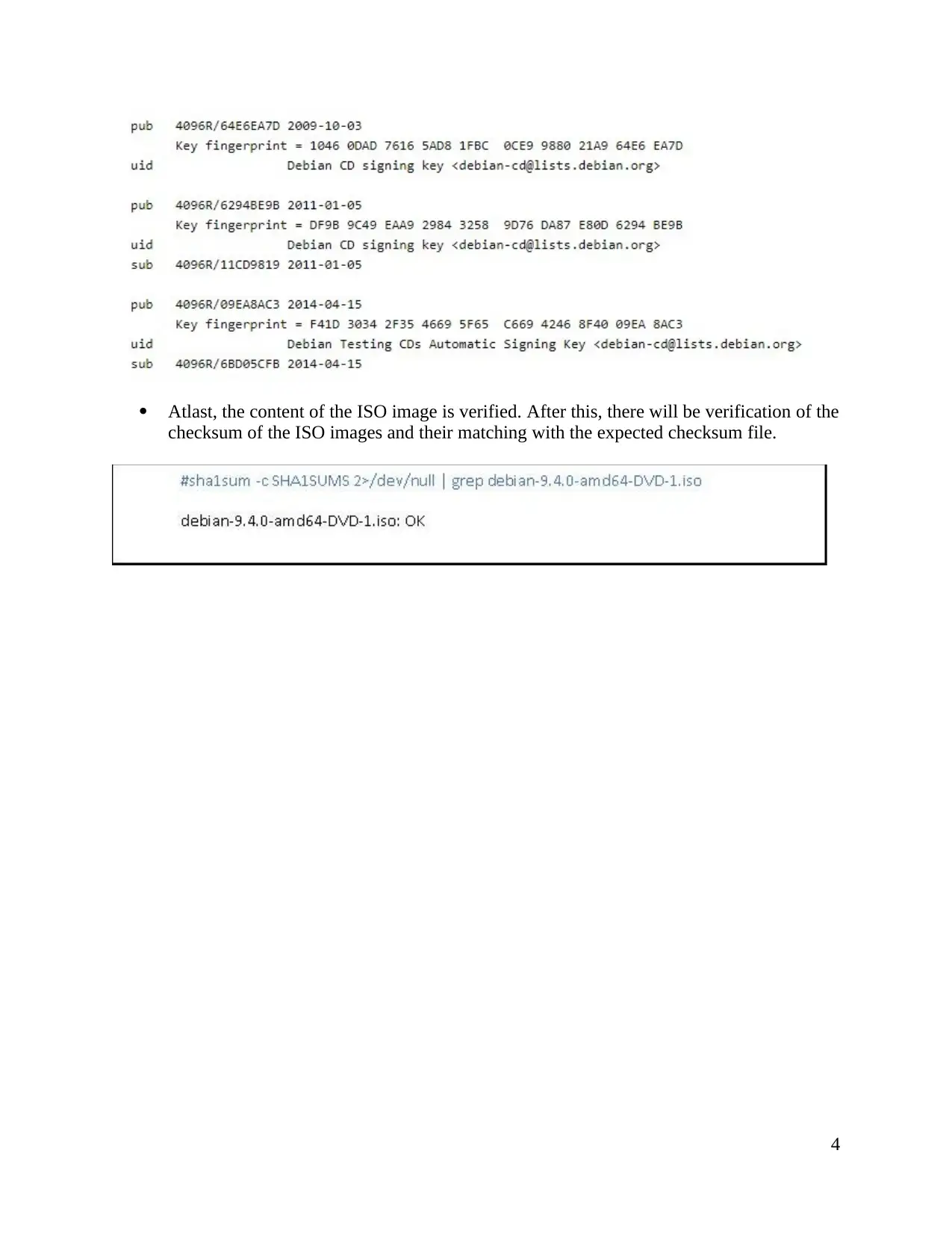
Atlast, the content of the ISO image is verified. After this, there will be verification of the
checksum of the ISO images and their matching with the expected checksum file.
4
checksum of the ISO images and their matching with the expected checksum file.
4
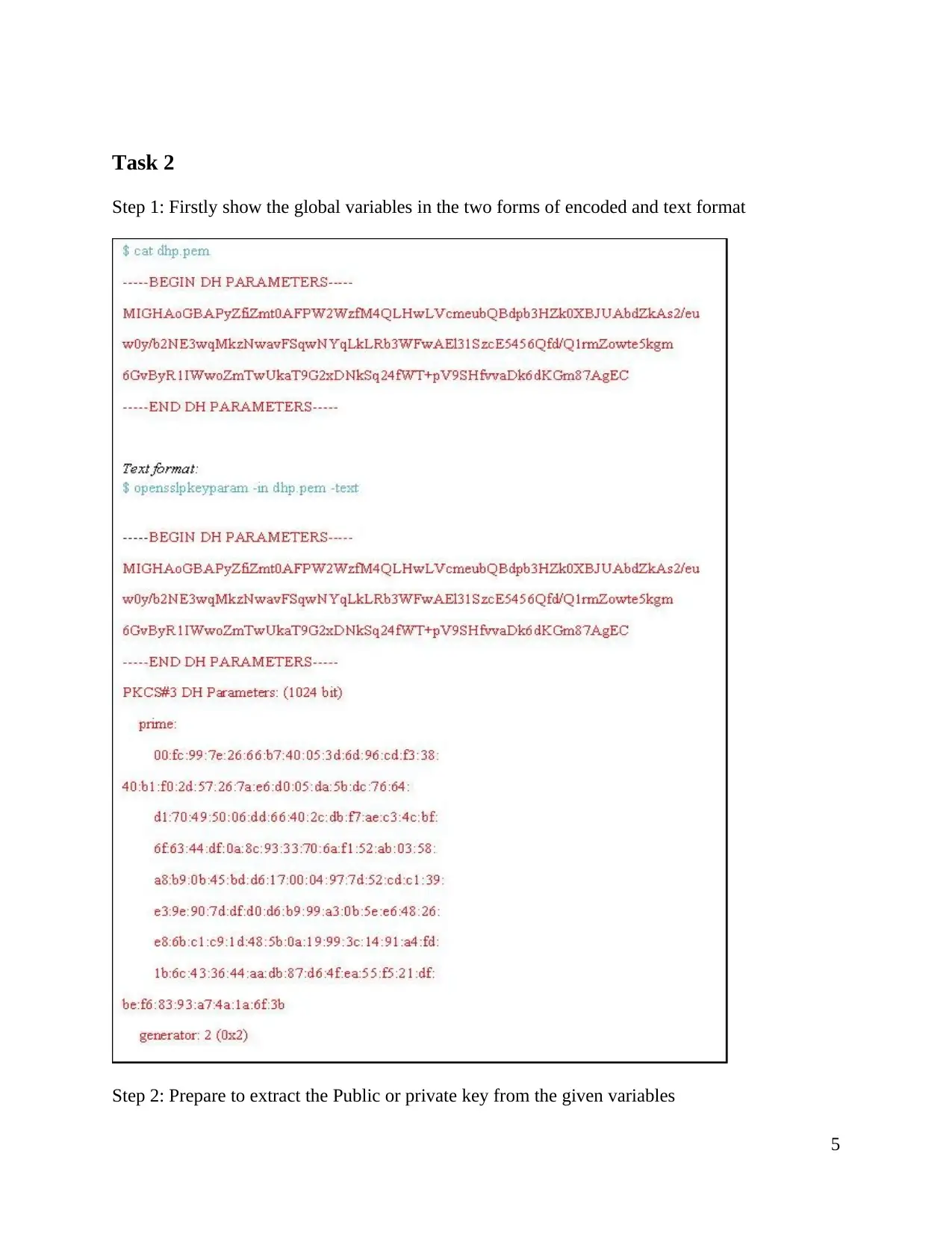
Task 2
Step 1: Firstly show the global variables in the two forms of encoded and text format
Step 2: Prepare to extract the Public or private key from the given variables
5
Step 1: Firstly show the global variables in the two forms of encoded and text format
Step 2: Prepare to extract the Public or private key from the given variables
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Step 3: In this step, the public key is extracted
6
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Step 4: From the instructor, the private key and public key is retrieved and these keys can be
used for the generation of the shared secret key
7
used for the generation of the shared secret key
7
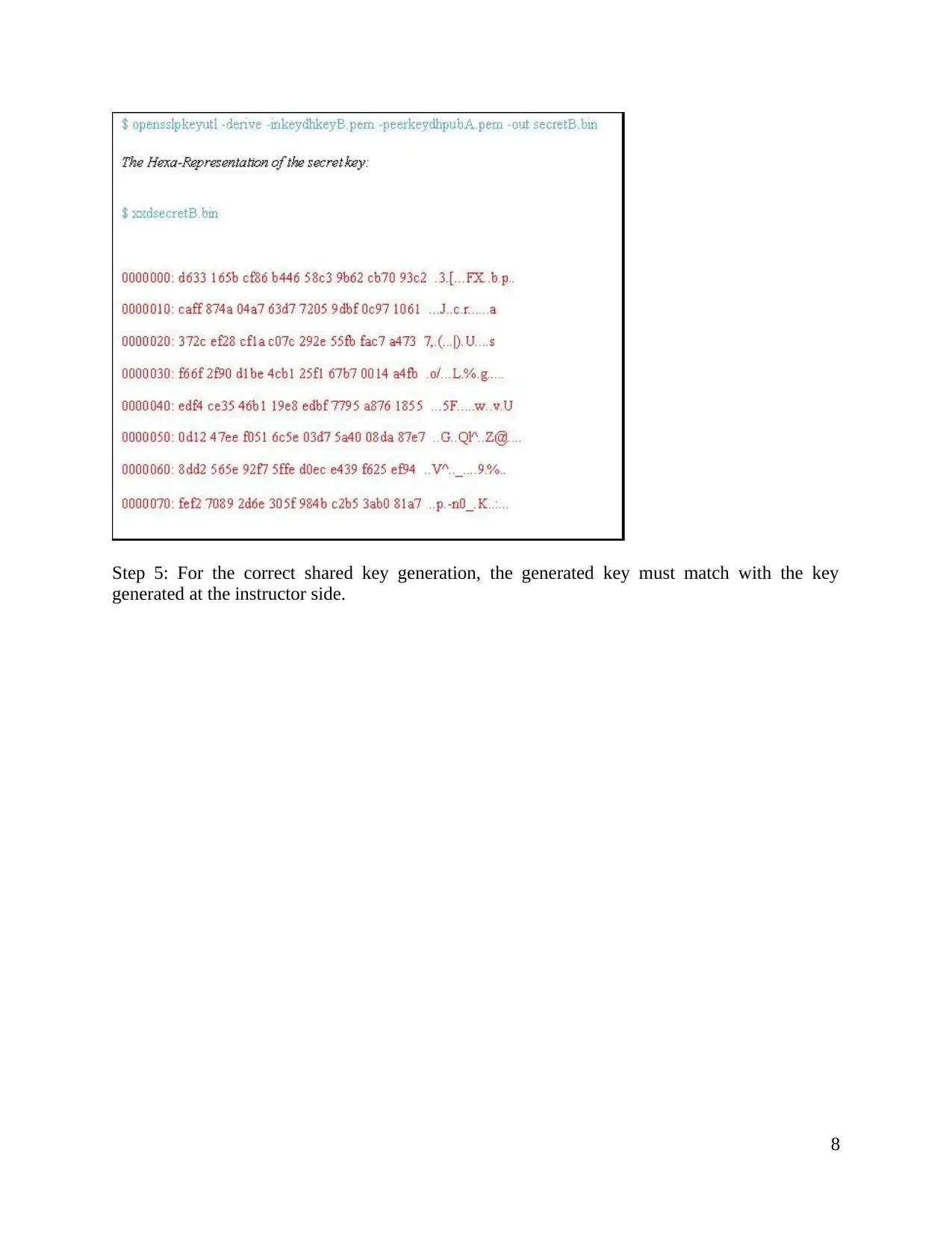
Step 5: For the correct shared key generation, the generated key must match with the key
generated at the instructor side.
8
generated at the instructor side.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 3
9
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Task 4
Abstract
Technology becomes advanced to a higher level where different aspects of the data and the
network are considered. One such aspect is the security of the data which is being transferred
from the sender to the receiver from any points of the world. Some of the data is confidential
which must be secured from all the threats and for this, there are several types of
mechanismsavailable for the security. One such method is cryptography and with this data can
be converted into another form which can be understood by only the sender and receiver. This is
done using some block cipher algorithms and the main algorithms which are used most popularly
are DES and AES (Rock and Nyberg, 2013).
Introduction
Most popularly used algorithms of symmetric key block cipher are AES and DES. These
algorithms are widely used to encrypt and decrypt the data which is being transferred on a non-
secured network channel. This report includes a brief discussion on both these algorithms.
DES (Data Encryption Standard) and its operation
Data Encryption Standard is a type of algorithm which protects the data available in electronic
format. The data is firstly converted into the gibberish language known as ciphertext and during
decrypting the cipher text is converted into the original data. It takes an input data of 64 bits and
having output data of similar size. There are four types of round that are followed during each
round of conversion and they are a permutation, shifting, substitution box and instantiations
(Simmons, 2016).
Figure 1: DES
Source:
Strengths of DES
Secret key of 64 bits is converted into the output of the same size
In case, if the key is expanded to a larger size then the extra can be used in the later
operations
10
Abstract
Technology becomes advanced to a higher level where different aspects of the data and the
network are considered. One such aspect is the security of the data which is being transferred
from the sender to the receiver from any points of the world. Some of the data is confidential
which must be secured from all the threats and for this, there are several types of
mechanismsavailable for the security. One such method is cryptography and with this data can
be converted into another form which can be understood by only the sender and receiver. This is
done using some block cipher algorithms and the main algorithms which are used most popularly
are DES and AES (Rock and Nyberg, 2013).
Introduction
Most popularly used algorithms of symmetric key block cipher are AES and DES. These
algorithms are widely used to encrypt and decrypt the data which is being transferred on a non-
secured network channel. This report includes a brief discussion on both these algorithms.
DES (Data Encryption Standard) and its operation
Data Encryption Standard is a type of algorithm which protects the data available in electronic
format. The data is firstly converted into the gibberish language known as ciphertext and during
decrypting the cipher text is converted into the original data. It takes an input data of 64 bits and
having output data of similar size. There are four types of round that are followed during each
round of conversion and they are a permutation, shifting, substitution box and instantiations
(Simmons, 2016).
Figure 1: DES
Source:
Strengths of DES
Secret key of 64 bits is converted into the output of the same size
In case, if the key is expanded to a larger size then the extra can be used in the later
operations
10

This algorithm is difficult to break
Difficult to crack the codes
Weakness of DES
Keys used are less scalable to the software implementation
Security aspects are limited toa change in security protocols(Oukili and Bri, 2017).
Application of DES and its future possibilities
Financial transactions
Increases speed of the ATM’s functioning
Mostly used in routers and servers
DES is used in most of the sectors and provided high specific security to the data during its
transfer. It allows the high encryption level as there isthe availability of higher versions of DES
in the security field such 3-DES. However, computing resources such as bandwidth and memory
are limited in case of DES (Khiabani, Wei, Yuan and Wang, 2012).
AES (Advanced Encryption Standard) and its operation
AES is another form of cipher encryption and decryption standard in terms of symmetric keys. In
this blocks of plaintext are converted into the cipher coding and this can be done by using keys
of sizes 128 bits, 192 bits and 256 bits. There are specific rounds decided by the size of keys
such as there are 10 rounds for the 128 bit and so on. in each round, there are four types of
transformation that take place during one round and they are sub-bytes, rows shifting, column
mixing and add round key(Kumar and Farik, 2017).
Strengths of AES
Easy implementation of the domain hardware
Size of the keys are available in a wider range
Breaking of the algorithm applied to the data is difficult
High range of applications
Weakness of AES
Easily understandable design of the algorithm
Implementation of this algorithm on software is hard
Similar algorithms are used in all blocks which leads to more risk (De and Bhaumik,
2014)
Application of AES and its future possibilities
In almost all data transactions
E-commerce
Electronic banking
Confidential email transfer
11
Difficult to crack the codes
Weakness of DES
Keys used are less scalable to the software implementation
Security aspects are limited toa change in security protocols(Oukili and Bri, 2017).
Application of DES and its future possibilities
Financial transactions
Increases speed of the ATM’s functioning
Mostly used in routers and servers
DES is used in most of the sectors and provided high specific security to the data during its
transfer. It allows the high encryption level as there isthe availability of higher versions of DES
in the security field such 3-DES. However, computing resources such as bandwidth and memory
are limited in case of DES (Khiabani, Wei, Yuan and Wang, 2012).
AES (Advanced Encryption Standard) and its operation
AES is another form of cipher encryption and decryption standard in terms of symmetric keys. In
this blocks of plaintext are converted into the cipher coding and this can be done by using keys
of sizes 128 bits, 192 bits and 256 bits. There are specific rounds decided by the size of keys
such as there are 10 rounds for the 128 bit and so on. in each round, there are four types of
transformation that take place during one round and they are sub-bytes, rows shifting, column
mixing and add round key(Kumar and Farik, 2017).
Strengths of AES
Easy implementation of the domain hardware
Size of the keys are available in a wider range
Breaking of the algorithm applied to the data is difficult
High range of applications
Weakness of AES
Easily understandable design of the algorithm
Implementation of this algorithm on software is hard
Similar algorithms are used in all blocks which leads to more risk (De and Bhaumik,
2014)
Application of AES and its future possibilities
In almost all data transactions
E-commerce
Electronic banking
Confidential email transfer
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





