Cryptography and Encryption: Playfair Cipher and Transposition Methods
VerifiedAdded on 2023/04/23
|20
|3498
|416
Homework Assignment
AI Summary
This assignment delves into various cryptography techniques, providing solutions for encryption and decryption problems. It covers Caesar ciphers, including finding cipher text with a given shift and deciphering plain text from cipher text. The assignment also explores substitution ciphers using key phrases and reversed alphabets, along with Playfair ciphers using 'KEDLESTON ROAD' as the key phrase and Vigenère ciphers with 'ATHENS' as the keyword. Furthermore, it demonstrates simple transposition ciphers using a four-digit key to encipher messages, and includes matrix addition problems. The document also covers binary addition and conversion between decimal and binary numbers. Finally, it includes exercises on Caesar ciphers, transposition ciphers, Playfair squares and Vigenere autokey method, providing a comprehensive overview of fundamental cryptographic methods.

Running head: CRYPTOGRAPHY
CRYPTOGRAPHY
Name of the Student
Name of the University
Author Note
CRYPTOGRAPHY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CRYPTOGRAPHY 1
Cryptography Tutorial 1 2019
1)
a)
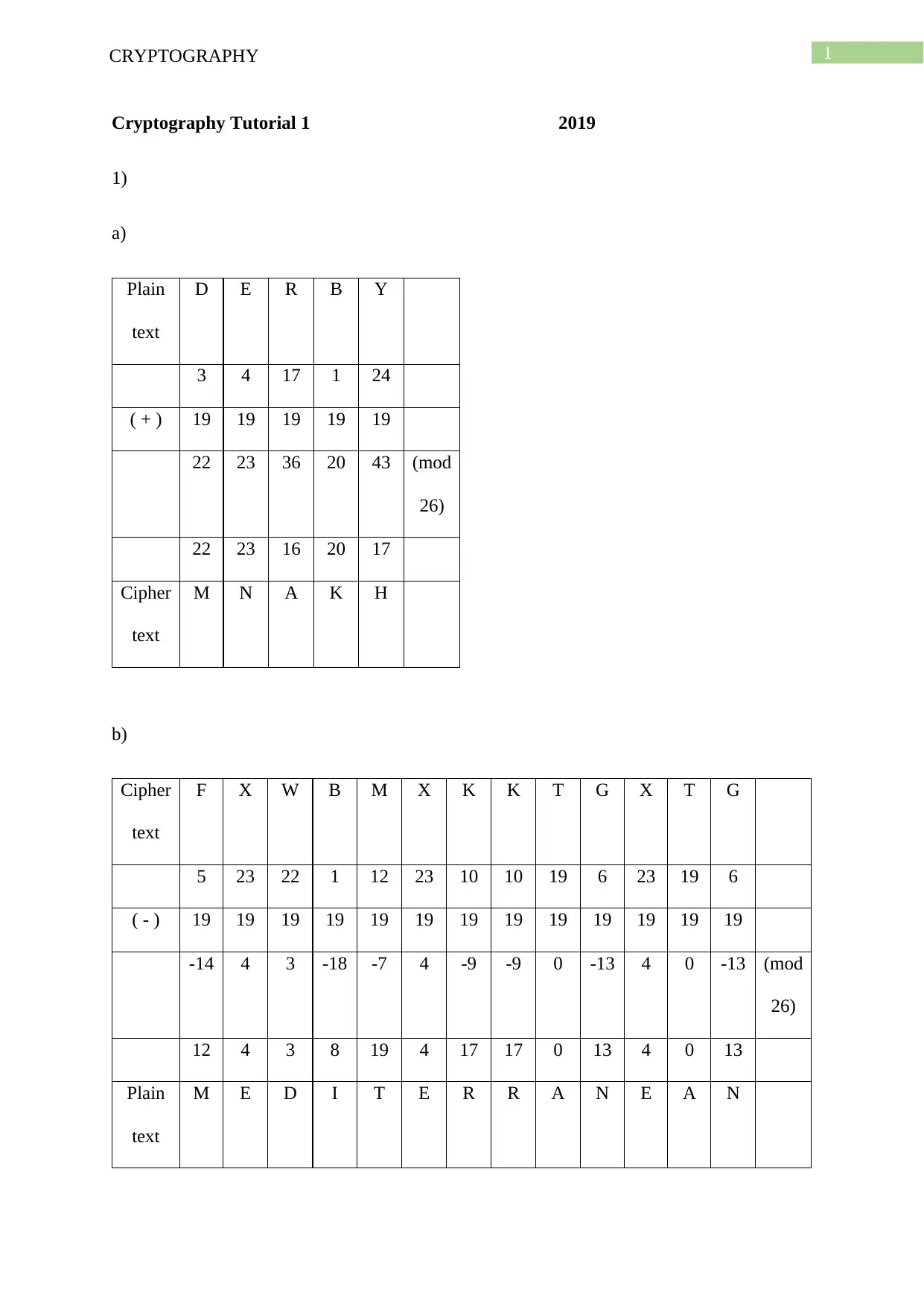
Plain
text
D E R B Y
3 4 17 1 24
( + ) 19 19 19 19 19
22 23 36 20 43 (mod
26)
22 23 16 20 17
Cipher
text
M N A K H
b)
Cipher
text
F X W B M X K K T G X T G
5 23 22 1 12 23 10 10 19 6 23 19 6
( - ) 19 19 19 19 19 19 19 19 19 19 19 19 19
-14 4 3 -18 -7 4 -9 -9 0 -13 4 0 -13 (mod
26)
12 4 3 8 19 4 17 17 0 13 4 0 13
Plain
text
M E D I T E R R A N E A N
Cryptography Tutorial 1 2019
1)
a)
Plain
text
D E R B Y
3 4 17 1 24
( + ) 19 19 19 19 19
22 23 36 20 43 (mod
26)
22 23 16 20 17
Cipher
text
M N A K H
b)
Cipher
text
F X W B M X K K T G X T G
5 23 22 1 12 23 10 10 19 6 23 19 6
( - ) 19 19 19 19 19 19 19 19 19 19 19 19 19
-14 4 3 -18 -7 4 -9 -9 0 -13 4 0 -13 (mod
26)
12 4 3 8 19 4 17 17 0 13 4 0 13
Plain
text
M E D I T E R R A N E A N
2CRYPTOGRAPHY
2)
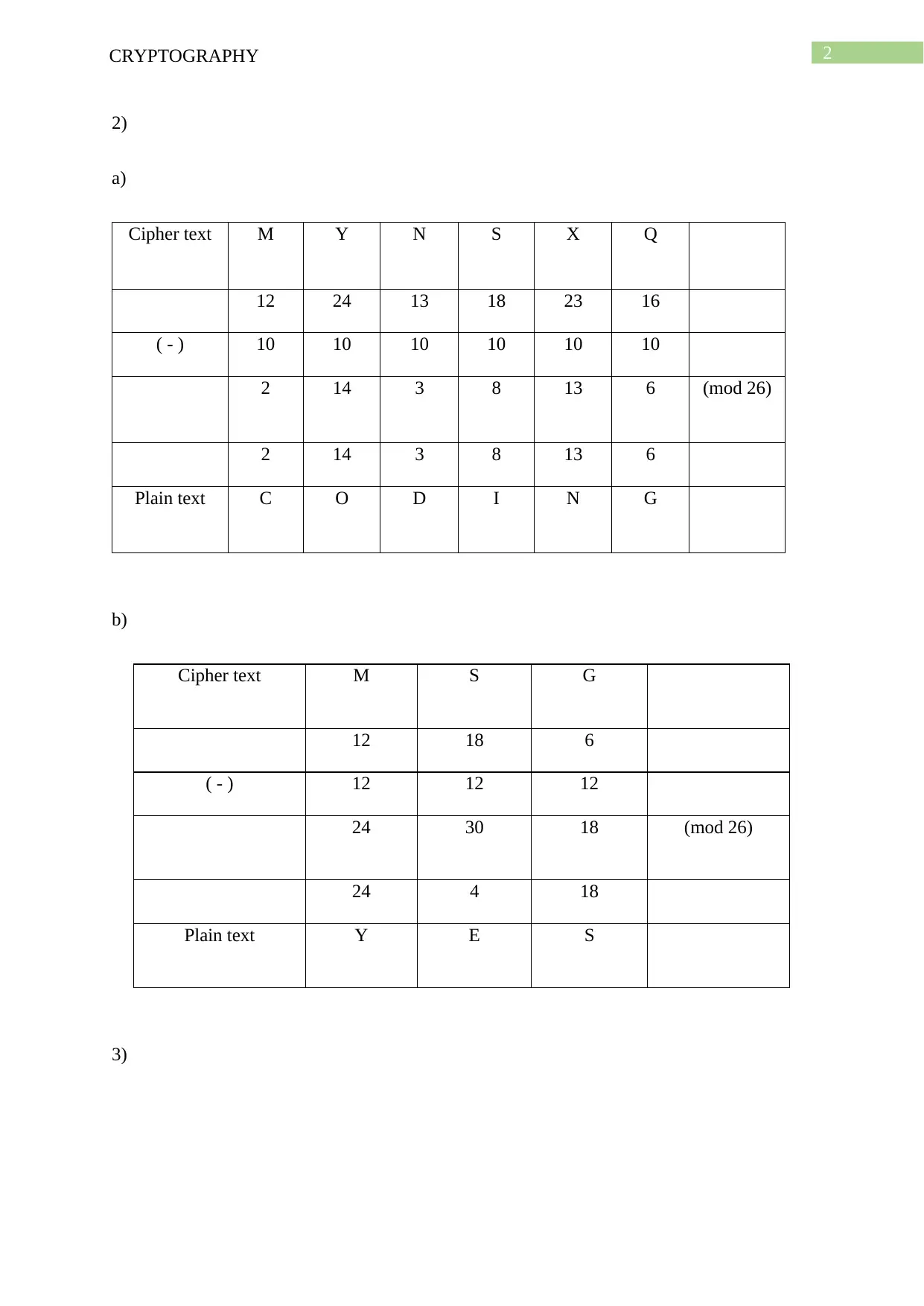
a)
Cipher text M Y N S X Q
12 24 13 18 23 16
( - ) 10 10 10 10 10 10
2 14 3 8 13 6 (mod 26)
2 14 3 8 13 6
Plain text C O D I N G
b)
Cipher text M S G
12 18 6
( - ) 12 12 12
24 30 18 (mod 26)
24 4 18
Plain text Y E S
3)
2)
a)
Cipher text M Y N S X Q
12 24 13 18 23 16
( - ) 10 10 10 10 10 10
2 14 3 8 13 6 (mod 26)
2 14 3 8 13 6
Plain text C O D I N G
b)
Cipher text M S G
12 18 6
( - ) 12 12 12
24 30 18 (mod 26)
24 4 18
Plain text Y E S
3)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3CRYPTOGRAPHY
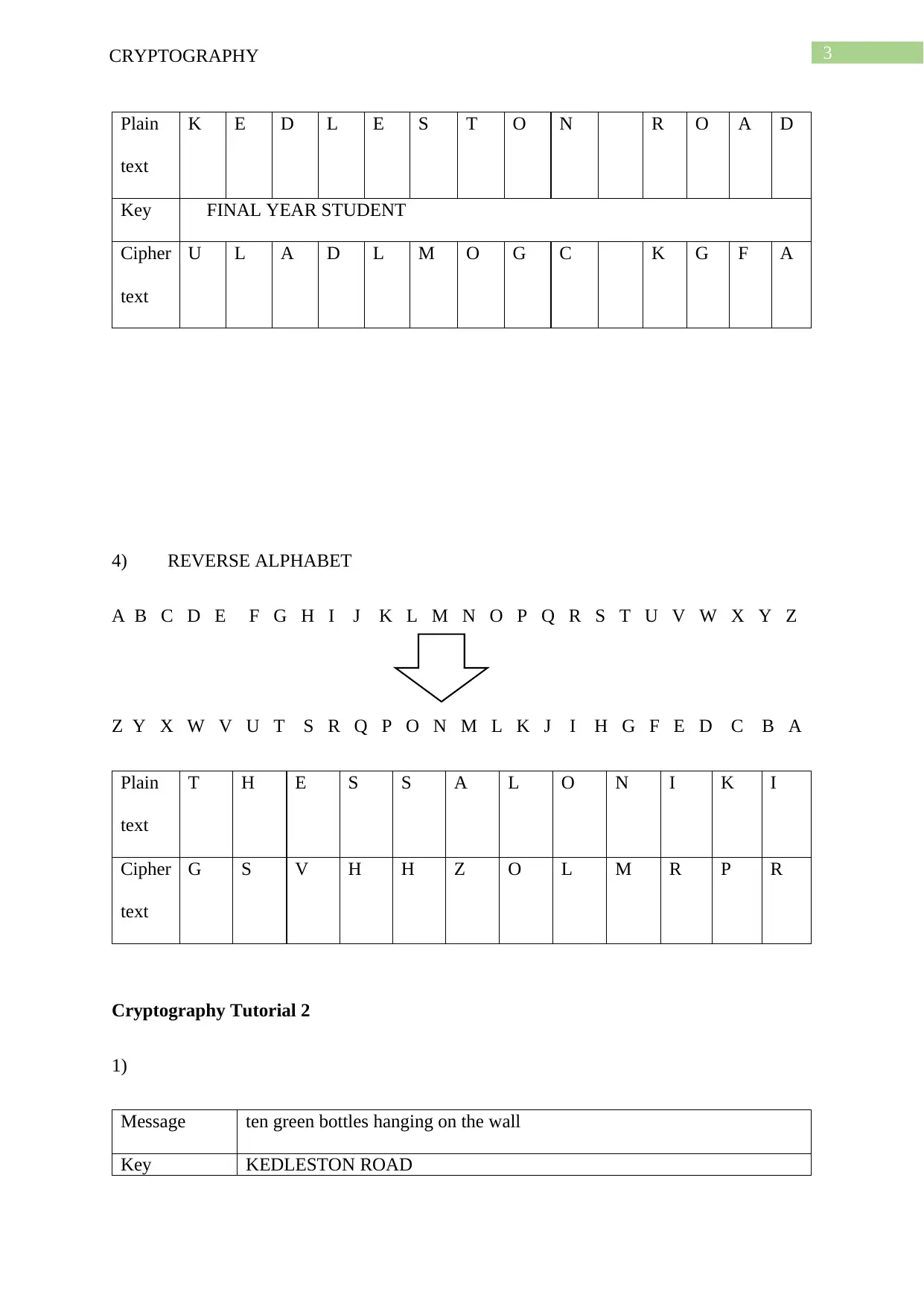
Plain
text
K E D L E S T O N R O A D
Key FINAL YEAR STUDENT
Cipher
text
U L A D L M O G C K G F A
4) REVERSE ALPHABET
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Z Y X W V U T S R Q P O N M L K J I H G F E D C B A
Plain
text
T H E S S A L O N I K I
Cipher
text
G S V H H Z O L M R P R
Cryptography Tutorial 2
1)
Message ten green bottles hanging on the wall
Key KEDLESTON ROAD
Plain
text
K E D L E S T O N R O A D
Key FINAL YEAR STUDENT
Cipher
text
U L A D L M O G C K G F A
4) REVERSE ALPHABET
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Z Y X W V U T S R Q P O N M L K J I H G F E D C B A
Plain
text
T H E S S A L O N I K I
Cipher
text
G S V H H Z O L M R P R
Cryptography Tutorial 2
1)
Message ten green bottles hanging on the wall
Key KEDLESTON ROAD
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CRYPTOGRAPHY
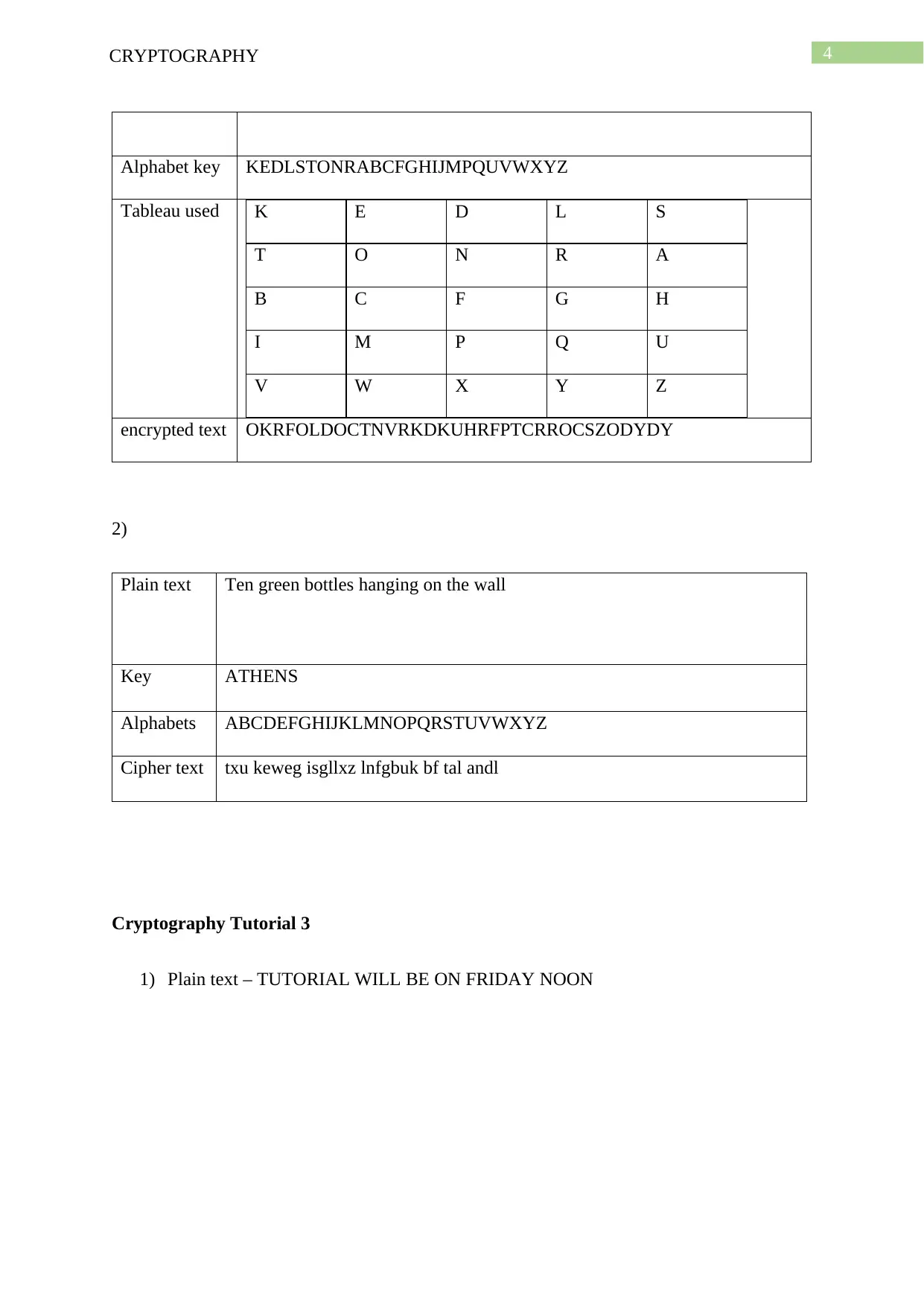
Alphabet key KEDLSTONRABCFGHIJMPQUVWXYZ
Tableau used K E D L S
T O N R A
B C F G H
I M P Q U
V W X Y Z
encrypted text OKRFOLDOCTNVRKDKUHRFPTCRROCSZODYDY
2)
Plain text Ten green bottles hanging on the wall
Key ATHENS
Alphabets ABCDEFGHIJKLMNOPQRSTUVWXYZ
Cipher text txu keweg isgllxz lnfgbuk bf tal andl
Cryptography Tutorial 3
1) Plain text – TUTORIAL WILL BE ON FRIDAY NOON
Alphabet key KEDLSTONRABCFGHIJMPQUVWXYZ
Tableau used K E D L S
T O N R A
B C F G H
I M P Q U
V W X Y Z
encrypted text OKRFOLDOCTNVRKDKUHRFPTCRROCSZODYDY
2)
Plain text Ten green bottles hanging on the wall
Key ATHENS
Alphabets ABCDEFGHIJKLMNOPQRSTUVWXYZ
Cipher text txu keweg isgllxz lnfgbuk bf tal andl
Cryptography Tutorial 3
1) Plain text – TUTORIAL WILL BE ON FRIDAY NOON
5CRYPTOGRAPHY
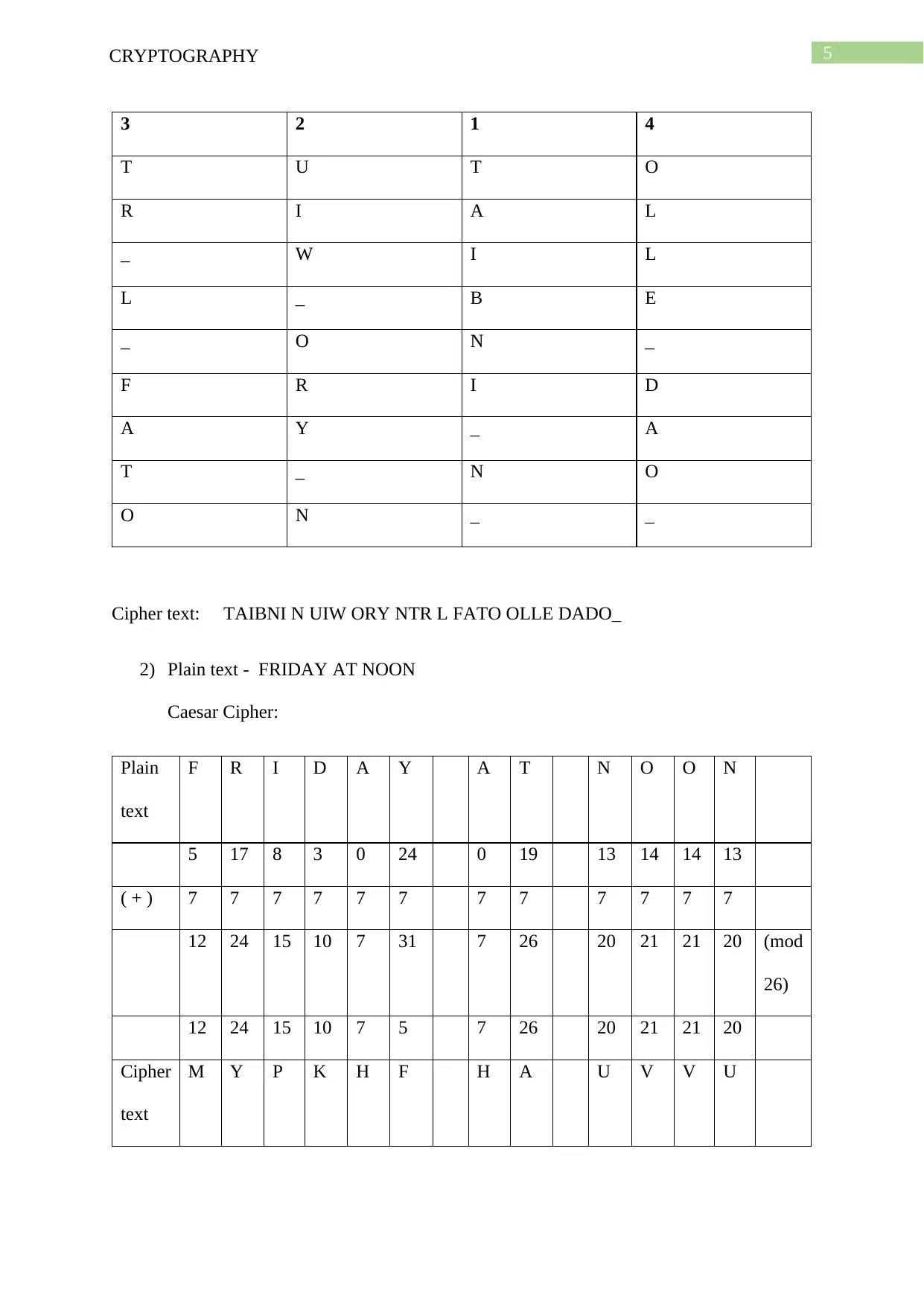
3 2 1 4
T U T O
R I A L
_ W I L
L _ B E
_ O N _
F R I D
A Y _ A
T _ N O
O N _ _
Cipher text: TAIBNI N UIW ORY NTR L FATO OLLE DADO_
2) Plain text - FRIDAY AT NOON
Caesar Cipher:
Plain
text
F R I D A Y A T N O O N
5 17 8 3 0 24 0 19 13 14 14 13
( + ) 7 7 7 7 7 7 7 7 7 7 7 7
12 24 15 10 7 31 7 26 20 21 21 20 (mod
26)
12 24 15 10 7 5 7 26 20 21 21 20
Cipher
text
M Y P K H F H A U V V U
3 2 1 4
T U T O
R I A L
_ W I L
L _ B E
_ O N _
F R I D
A Y _ A
T _ N O
O N _ _
Cipher text: TAIBNI N UIW ORY NTR L FATO OLLE DADO_
2) Plain text - FRIDAY AT NOON
Caesar Cipher:
Plain
text
F R I D A Y A T N O O N
5 17 8 3 0 24 0 19 13 14 14 13
( + ) 7 7 7 7 7 7 7 7 7 7 7 7
12 24 15 10 7 31 7 26 20 21 21 20 (mod
26)
12 24 15 10 7 5 7 26 20 21 21 20
Cipher
text
M Y P K H F H A U V V U
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CRYPTOGRAPHY
Transposition cipher:
1 2 3 4 5
F R I D A
Y _ A T _
N O O N _
Key- 52341
Cipher text: ARIDF___ATY_OONN
1) MATRIX ADDITION:
i. AG - Addition is not possible because dimension of A is 1*6 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
ii. AB - Addition is not possible because dimension of A is 1*6 and for B is 3*1 and
in matrix addition it is not possible to add two matrix with different dimension.
iii. GA- Addition is not possible because dimension of A is 1*6 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
iv. GB - Addition is not possible because dimension of B is 3*1 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
v. CG - Addition is not possible because dimension of C is 1*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
vi. GC - Addition is not possible because dimension of C is 1*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
vii. DG - Addition is not possible because dimension of D is 3*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
Transposition cipher:
1 2 3 4 5
F R I D A
Y _ A T _
N O O N _
Key- 52341
Cipher text: ARIDF___ATY_OONN
1) MATRIX ADDITION:
i. AG - Addition is not possible because dimension of A is 1*6 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
ii. AB - Addition is not possible because dimension of A is 1*6 and for B is 3*1 and
in matrix addition it is not possible to add two matrix with different dimension.
iii. GA- Addition is not possible because dimension of A is 1*6 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
iv. GB - Addition is not possible because dimension of B is 3*1 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
v. CG - Addition is not possible because dimension of C is 1*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
vi. GC - Addition is not possible because dimension of C is 1*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
vii. DG - Addition is not possible because dimension of D is 3*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CRYPTOGRAPHY
viii. GD - Addition is not possible because dimension of D is 3*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
ix. EG - Addition is not possible because dimension of E is 1*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
x. EF –
E = [0 0 1] F = [0 1 0]
EF = [ 0+0 0+1 1+0 ] = [ 0 1 1 ]
2)
i. 1010+0111 = 10001
ii. 100+001 = 101
iii.
Decimal Binary
0 0000
1 0001
2 0010
3 0011
4 0100
5 0101
6 0110
7 0111
iv. 1010+1011+0000 = 10101
3)
viii. GD - Addition is not possible because dimension of D is 3*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
ix. EG - Addition is not possible because dimension of E is 1*3 and for G is 3*6 and
in matrix addition it is not possible to add two matrix with different dimension.
x. EF –
E = [0 0 1] F = [0 1 0]
EF = [ 0+0 0+1 1+0 ] = [ 0 1 1 ]
2)
i. 1010+0111 = 10001
ii. 100+001 = 101
iii.
Decimal Binary
0 0000
1 0001
2 0010
3 0011
4 0100
5 0101
6 0110
7 0111
iv. 1010+1011+0000 = 10101
3)
8CRYPTOGRAPHY
i. 0101+1110 = 1011
ii. 0001+1011 = 1010
iii. 000111001+111010101 = 111101100
iv. 01010101+01010101 = 0
CRYPTOGRAPHY EXERCISES:
Exercise 1:
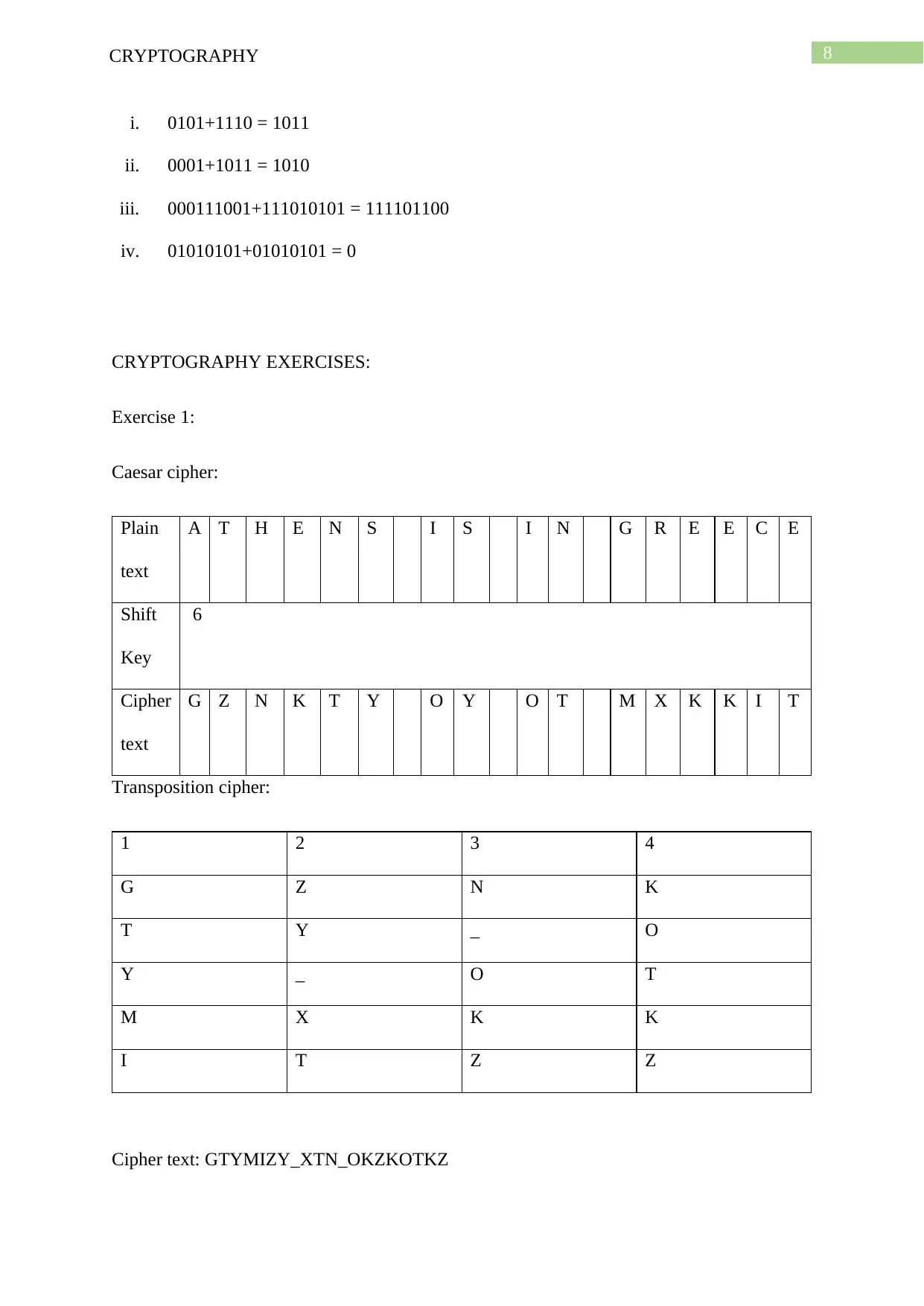
Caesar cipher:
Plain
text
A T H E N S I S I N G R E E C E
Shift
Key
6
Cipher
text
G Z N K T Y O Y O T M X K K I T
Transposition cipher:
1 2 3 4
G Z N K
T Y _ O
Y _ O T
M X K K
I T Z Z
Cipher text: GTYMIZY_XTN_OKZKOTKZ
i. 0101+1110 = 1011
ii. 0001+1011 = 1010
iii. 000111001+111010101 = 111101100
iv. 01010101+01010101 = 0
CRYPTOGRAPHY EXERCISES:
Exercise 1:
Caesar cipher:
Plain
text
A T H E N S I S I N G R E E C E
Shift
Key
6
Cipher
text
G Z N K T Y O Y O T M X K K I T
Transposition cipher:
1 2 3 4
G Z N K
T Y _ O
Y _ O T
M X K K
I T Z Z
Cipher text: GTYMIZY_XTN_OKZKOTKZ
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9CRYPTOGRAPHY
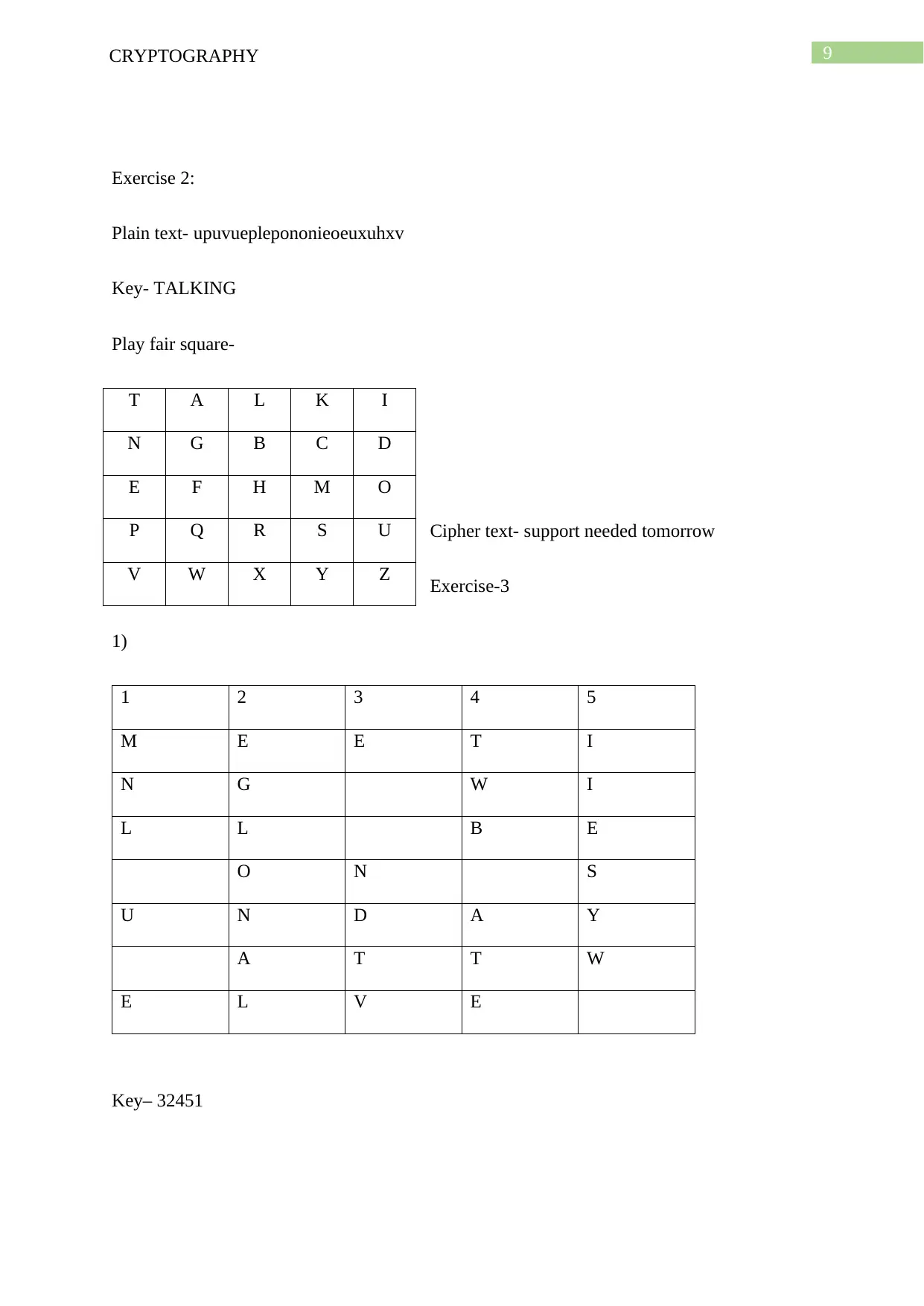
Exercise 2:
Plain text- upuvueplepononieoeuxuhxv
Key- TALKING
Play fair square-
Cipher text- support needed tomorrow
Exercise-3
1)
1 2 3 4 5
M E E T I
N G W I
L L B E
O N S
U N D A Y
A T T W
E L V E
Key– 32451
T A L K I
N G B C D
E F H M O
P Q R S U
V W X Y Z
Exercise 2:
Plain text- upuvueplepononieoeuxuhxv
Key- TALKING
Play fair square-
Cipher text- support needed tomorrow
Exercise-3
1)
1 2 3 4 5
M E E T I
N G W I
L L B E
O N S
U N D A Y
A T T W
E L V E
Key– 32451
T A L K I
N G B C D
E F H M O
P Q R S U
V W X Y Z
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CRYPTOGRAPHY
3 2 4 5 1
E E T I M
G W I N
L B E L
N O S
D N A Y U
T A T W
V L E E
Cipher text- EETIM GWIN S DNAYUTA T LEVEW
2).
1 2 3 4 5 6
P E I T G H
C N I P P E
S R U H B E
T I U S T T
N O E E S S
O B L Y F M
A E C O H R
T T E L R E
3 2 4 5 1
E E T I M
G W I N
L B E L
N O S
D N A Y U
T A T W
V L E E
Cipher text- EETIM GWIN S DNAYUTA T LEVEW
2).
1 2 3 4 5 6
P E I T G H
C N I P P E
S R U H B E
T I U S T T
N O E E S S
O B L Y F M
A E C O H R
T T E L R E

11CRYPTOGRAPHY
Order applied- 4 6 2 1 3 5
4 6 2 1 3 5
T H E P I G
P E N C I P
H E R S U B
S T I T U T
E S O N E S
Y M B O L F
O R E A C H
L E T T E R
Plain text- THE PIG PEN CIPHER SUBSTITUTES ONE SYMBOL FOR EACH LETTER
Exercise 4:
Vigenere autokey method:
In autokey method, the term autokey means the key that is depending on the actual
plaintext. Actually this is extension of the vigenere cipher, makes the cipher text harder to
break. In this method, the passphrase is used only once and the clear text is used to encrypt or
decrypt the text instead of using that repeatedly.
Plain text: cryptography is fab
Key: S
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
A A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Order applied- 4 6 2 1 3 5
4 6 2 1 3 5
T H E P I G
P E N C I P
H E R S U B
S T I T U T
E S O N E S
Y M B O L F
O R E A C H
L E T T E R
Plain text- THE PIG PEN CIPHER SUBSTITUTES ONE SYMBOL FOR EACH LETTER
Exercise 4:
Vigenere autokey method:
In autokey method, the term autokey means the key that is depending on the actual
plaintext. Actually this is extension of the vigenere cipher, makes the cipher text harder to
break. In this method, the passphrase is used only once and the clear text is used to encrypt or
decrypt the text instead of using that repeatedly.
Plain text: cryptography is fab
Key: S
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
A A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





