Cryptography Techniques for Network Security: A Research Project
VerifiedAdded on 2024/05/21
|5
|3935
|215
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

ITC595 Research Project
Cryptographic Technique
A. Abdul
ITC595 MIT, School of Computing & Mathematics, Charles Sturt University
author@first-third.edu.au
ABSTRACT – This paper aims to research over cryptography. One
of the major problems all industries facing today is the leakage of
data. The attackers get their hands on the precious data and might
misuse it. We need to look into possible solution so that the data
does not reach in wrong hands. In this paper, we have described
certain cryptography techniques, to store data in an encrypted
form. Techniques like ciphering, MAC, Hash Function, SHA are
described in detail to get a gist of the topic.
Keywords— Cryptography; secret key; Authentication;
Confidentiality
INTRODUCTION
In the recent years, the networks trespassers have
expanded their technical knowledge, advanced superior
packages and feature determined out new approaches to take
advantage of community vulnerabilities. The activities of such
intruders can create a stampede for the companies as the
intruders can easily have access to the confidential
information of an organization. It can also harm a person
personally as an attacker can come to know the account’s
number and password and can easily misuse it according to his
own advantage. All these issues have raised the demand for
network security. Network security can be divided into four
categories: confidentiality, authentication, non-repudiation,
and integrity.
Confidentiality – Confidentiality refers to keeping the
information out of unauthorized people.
Authentication – Authentication refers to knowing whom you
are talking to before revealing sensitive information.
Nonrepudiation – Nonrepudiation deals with the digital
signature so that the other party cannot deny the authenticity
of the message (Baortaz, 2005).
Integrity – Integrity refers to ensuring that the content of the
message is not altered while sending and receiving the
message.
Figure 1 Encryption technology
For these reasons, cryptography has become an essential part
of computers and communication networks. Cryptography
protects everything from business emails to internet shopping
to electronic bank transactions.
Cryptography is the process of encrypting a plain text
(readable) into a ciphertext (non-readable) (Deffie, 1976).
Cryptography involves certain mathematical techniques to
avoid eavesdropping. The boom in the use of cryptography
can be dated back to 20th century when wireless
communication was introduced in the communication
networks. Until the early 1990s, only governmental, military
and financial data were protected by encryption. But now
things as simple as chat applications are well encrypted. There
are several ways to encrypt the valuable information like a
block cipher, stream cipher, MAC (Message Authentication
Codes), Hash Functions, Public key, Private Key, Digital
Signatures etc.
A. Research Problem
The major issue is discussed in the research report is about
to network source. To resolve this issue, the authentication
and confidentiality technique is used. This research paper is
based on the security issues which can be solved by the
cryptographic technology (Sharma, 2015).
B. Research Justification
This research aims to solve the security issues with
identifying the network issues. Research is being performed
after reviewing the research article to find the best technology
with the best result. With this research, provide the
knowledge of the cryptography technology with their
functionality.
Figure 2 Cryptography technique
TABLE I: COMPARISON OF ALGORITHM
S.
no.
Comparison
Cryptography Size Generation time
1
Cryptographic Technique
A. Abdul
ITC595 MIT, School of Computing & Mathematics, Charles Sturt University
author@first-third.edu.au
ABSTRACT – This paper aims to research over cryptography. One
of the major problems all industries facing today is the leakage of
data. The attackers get their hands on the precious data and might
misuse it. We need to look into possible solution so that the data
does not reach in wrong hands. In this paper, we have described
certain cryptography techniques, to store data in an encrypted
form. Techniques like ciphering, MAC, Hash Function, SHA are
described in detail to get a gist of the topic.
Keywords— Cryptography; secret key; Authentication;
Confidentiality
INTRODUCTION
In the recent years, the networks trespassers have
expanded their technical knowledge, advanced superior
packages and feature determined out new approaches to take
advantage of community vulnerabilities. The activities of such
intruders can create a stampede for the companies as the
intruders can easily have access to the confidential
information of an organization. It can also harm a person
personally as an attacker can come to know the account’s
number and password and can easily misuse it according to his
own advantage. All these issues have raised the demand for
network security. Network security can be divided into four
categories: confidentiality, authentication, non-repudiation,
and integrity.
Confidentiality – Confidentiality refers to keeping the
information out of unauthorized people.
Authentication – Authentication refers to knowing whom you
are talking to before revealing sensitive information.
Nonrepudiation – Nonrepudiation deals with the digital
signature so that the other party cannot deny the authenticity
of the message (Baortaz, 2005).
Integrity – Integrity refers to ensuring that the content of the
message is not altered while sending and receiving the
message.
Figure 1 Encryption technology
For these reasons, cryptography has become an essential part
of computers and communication networks. Cryptography
protects everything from business emails to internet shopping
to electronic bank transactions.
Cryptography is the process of encrypting a plain text
(readable) into a ciphertext (non-readable) (Deffie, 1976).
Cryptography involves certain mathematical techniques to
avoid eavesdropping. The boom in the use of cryptography
can be dated back to 20th century when wireless
communication was introduced in the communication
networks. Until the early 1990s, only governmental, military
and financial data were protected by encryption. But now
things as simple as chat applications are well encrypted. There
are several ways to encrypt the valuable information like a
block cipher, stream cipher, MAC (Message Authentication
Codes), Hash Functions, Public key, Private Key, Digital
Signatures etc.
A. Research Problem
The major issue is discussed in the research report is about
to network source. To resolve this issue, the authentication
and confidentiality technique is used. This research paper is
based on the security issues which can be solved by the
cryptographic technology (Sharma, 2015).
B. Research Justification
This research aims to solve the security issues with
identifying the network issues. Research is being performed
after reviewing the research article to find the best technology
with the best result. With this research, provide the
knowledge of the cryptography technology with their
functionality.
Figure 2 Cryptography technique
TABLE I: COMPARISON OF ALGORITHM
S.
no.
Comparison
Cryptography Size Generation time
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
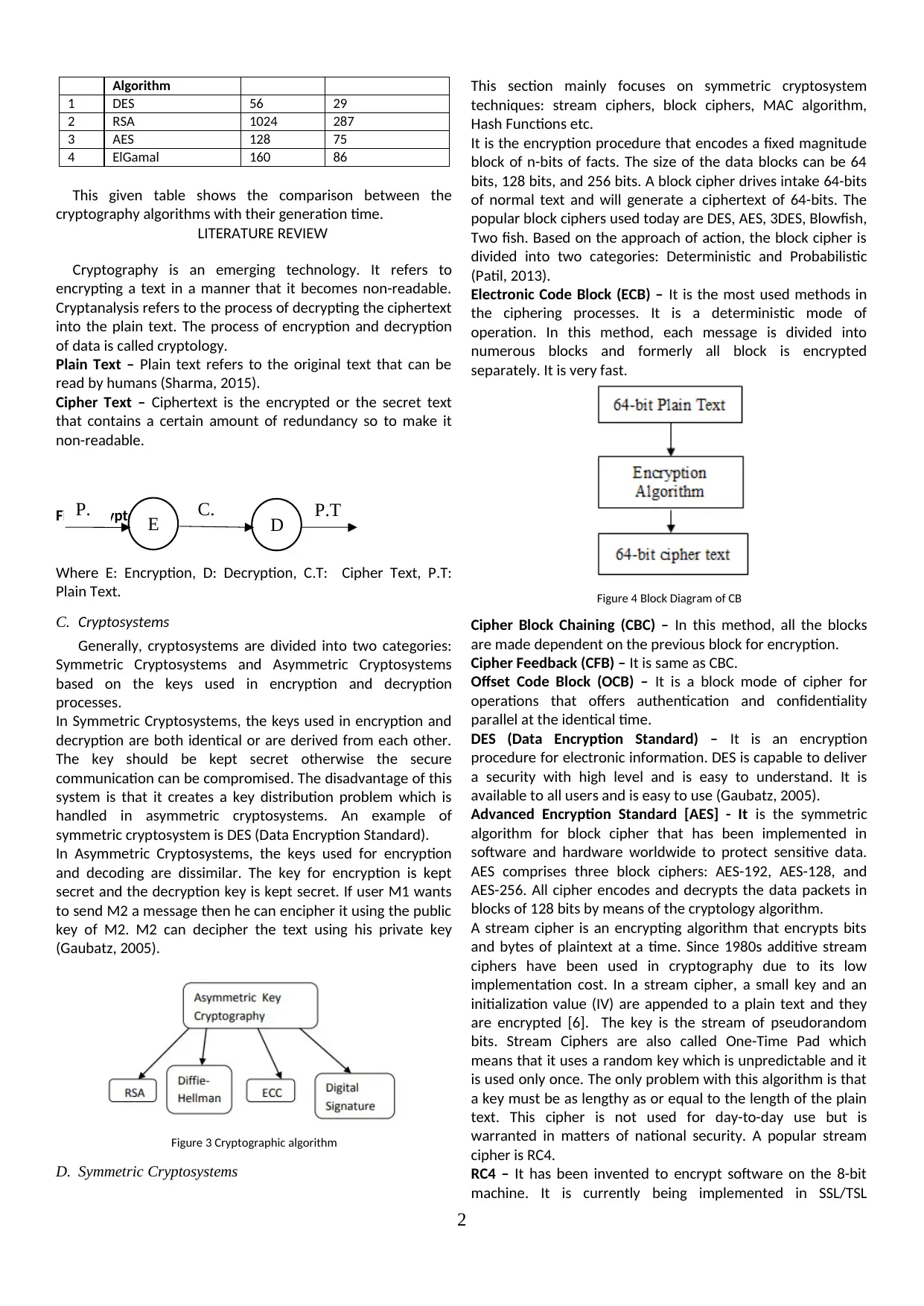
Algorithm
1 DES 56 29
2 RSA 1024 287
3 AES 128 75
4 ElGamal 160 86
This given table shows the comparison between the
cryptography algorithms with their generation time.
LITERATURE REVIEW
Cryptography is an emerging technology. It refers to
encrypting a text in a manner that it becomes non-readable.
Cryptanalysis refers to the process of decrypting the ciphertext
into the plain text. The process of encryption and decryption
of data is called cryptology.
Plain Text – Plain text refers to the original text that can be
read by humans (Sharma, 2015).
Cipher Text – Ciphertext is the encrypted or the secret text
that contains a certain amount of redundancy so to make it
non-readable.
Fig 1: Cryptology
Where E: Encryption, D: Decryption, C.T: Cipher Text, P.T:
Plain Text.
C. Cryptosystems
Generally, cryptosystems are divided into two categories:
Symmetric Cryptosystems and Asymmetric Cryptosystems
based on the keys used in encryption and decryption
processes.
In Symmetric Cryptosystems, the keys used in encryption and
decryption are both identical or are derived from each other.
The key should be kept secret otherwise the secure
communication can be compromised. The disadvantage of this
system is that it creates a key distribution problem which is
handled in asymmetric cryptosystems. An example of
symmetric cryptosystem is DES (Data Encryption Standard).
In Asymmetric Cryptosystems, the keys used for encryption
and decoding are dissimilar. The key for encryption is kept
secret and the decryption key is kept secret. If user M1 wants
to send M2 a message then he can encipher it using the public
key of M2. M2 can decipher the text using his private key
(Gaubatz, 2005).
Figure 3 Cryptographic algorithm
D. Symmetric Cryptosystems
This section mainly focuses on symmetric cryptosystem
techniques: stream ciphers, block ciphers, MAC algorithm,
Hash Functions etc.
It is the encryption procedure that encodes a fixed magnitude
block of n-bits of facts. The size of the data blocks can be 64
bits, 128 bits, and 256 bits. A block cipher drives intake 64-bits
of normal text and will generate a ciphertext of 64-bits. The
popular block ciphers used today are DES, AES, 3DES, Blowfish,
Two fish. Based on the approach of action, the block cipher is
divided into two categories: Deterministic and Probabilistic
(Patil, 2013).
Electronic Code Block (ECB) – It is the most used methods in
the ciphering processes. It is a deterministic mode of
operation. In this method, each message is divided into
numerous blocks and formerly all block is encrypted
separately. It is very fast.
Figure 4 Block Diagram of CB
Cipher Block Chaining (CBC) – In this method, all the blocks
are made dependent on the previous block for encryption.
Cipher Feedback (CFB) – It is same as CBC.
Offset Code Block (OCB) – It is a block mode of cipher for
operations that offers authentication and confidentiality
parallel at the identical time.
DES (Data Encryption Standard) – It is an encryption
procedure for electronic information. DES is capable to deliver
a security with high level and is easy to understand. It is
available to all users and is easy to use (Gaubatz, 2005).
Advanced Encryption Standard [AES] - It is the symmetric
algorithm for block cipher that has been implemented in
software and hardware worldwide to protect sensitive data.
AES comprises three block ciphers: AES-192, AES-128, and
AES-256. All cipher encodes and decrypts the data packets in
blocks of 128 bits by means of the cryptology algorithm.
A stream cipher is an encrypting algorithm that encrypts bits
and bytes of plaintext at a time. Since 1980s additive stream
ciphers have been used in cryptography due to its low
implementation cost. In a stream cipher, a small key and an
initialization value (IV) are appended to a plain text and they
are encrypted [6]. The key is the stream of pseudorandom
bits. Stream Ciphers are also called One-Time Pad which
means that it uses a random key which is unpredictable and it
is used only once. The only problem with this algorithm is that
a key must be as lengthy as or equal to the length of the plain
text. This cipher is not used for day-to-day use but is
warranted in matters of national security. A popular stream
cipher is RC4.
RC4 – It has been invented to encrypt software on the 8-bit
machine. It is currently being implemented in SSL/TSL
2
E D
P. C. P.T
1 DES 56 29
2 RSA 1024 287
3 AES 128 75
4 ElGamal 160 86
This given table shows the comparison between the
cryptography algorithms with their generation time.
LITERATURE REVIEW
Cryptography is an emerging technology. It refers to
encrypting a text in a manner that it becomes non-readable.
Cryptanalysis refers to the process of decrypting the ciphertext
into the plain text. The process of encryption and decryption
of data is called cryptology.
Plain Text – Plain text refers to the original text that can be
read by humans (Sharma, 2015).
Cipher Text – Ciphertext is the encrypted or the secret text
that contains a certain amount of redundancy so to make it
non-readable.
Fig 1: Cryptology
Where E: Encryption, D: Decryption, C.T: Cipher Text, P.T:
Plain Text.
C. Cryptosystems
Generally, cryptosystems are divided into two categories:
Symmetric Cryptosystems and Asymmetric Cryptosystems
based on the keys used in encryption and decryption
processes.
In Symmetric Cryptosystems, the keys used in encryption and
decryption are both identical or are derived from each other.
The key should be kept secret otherwise the secure
communication can be compromised. The disadvantage of this
system is that it creates a key distribution problem which is
handled in asymmetric cryptosystems. An example of
symmetric cryptosystem is DES (Data Encryption Standard).
In Asymmetric Cryptosystems, the keys used for encryption
and decoding are dissimilar. The key for encryption is kept
secret and the decryption key is kept secret. If user M1 wants
to send M2 a message then he can encipher it using the public
key of M2. M2 can decipher the text using his private key
(Gaubatz, 2005).
Figure 3 Cryptographic algorithm
D. Symmetric Cryptosystems
This section mainly focuses on symmetric cryptosystem
techniques: stream ciphers, block ciphers, MAC algorithm,
Hash Functions etc.
It is the encryption procedure that encodes a fixed magnitude
block of n-bits of facts. The size of the data blocks can be 64
bits, 128 bits, and 256 bits. A block cipher drives intake 64-bits
of normal text and will generate a ciphertext of 64-bits. The
popular block ciphers used today are DES, AES, 3DES, Blowfish,
Two fish. Based on the approach of action, the block cipher is
divided into two categories: Deterministic and Probabilistic
(Patil, 2013).
Electronic Code Block (ECB) – It is the most used methods in
the ciphering processes. It is a deterministic mode of
operation. In this method, each message is divided into
numerous blocks and formerly all block is encrypted
separately. It is very fast.
Figure 4 Block Diagram of CB
Cipher Block Chaining (CBC) – In this method, all the blocks
are made dependent on the previous block for encryption.
Cipher Feedback (CFB) – It is same as CBC.
Offset Code Block (OCB) – It is a block mode of cipher for
operations that offers authentication and confidentiality
parallel at the identical time.
DES (Data Encryption Standard) – It is an encryption
procedure for electronic information. DES is capable to deliver
a security with high level and is easy to understand. It is
available to all users and is easy to use (Gaubatz, 2005).
Advanced Encryption Standard [AES] - It is the symmetric
algorithm for block cipher that has been implemented in
software and hardware worldwide to protect sensitive data.
AES comprises three block ciphers: AES-192, AES-128, and
AES-256. All cipher encodes and decrypts the data packets in
blocks of 128 bits by means of the cryptology algorithm.
A stream cipher is an encrypting algorithm that encrypts bits
and bytes of plaintext at a time. Since 1980s additive stream
ciphers have been used in cryptography due to its low
implementation cost. In a stream cipher, a small key and an
initialization value (IV) are appended to a plain text and they
are encrypted [6]. The key is the stream of pseudorandom
bits. Stream Ciphers are also called One-Time Pad which
means that it uses a random key which is unpredictable and it
is used only once. The only problem with this algorithm is that
a key must be as lengthy as or equal to the length of the plain
text. This cipher is not used for day-to-day use but is
warranted in matters of national security. A popular stream
cipher is RC4.
RC4 – It has been invented to encrypt software on the 8-bit
machine. It is currently being implemented in SSL/TSL
2
E D
P. C. P.T
protocols. This algorithm has many pitfalls still it is able to stop
and restrain key recovery attacks.
In last 20 years, many stream ciphers ensure developed that
can operate on 32-bit and 64bit processors. MUGI and SNOW
are two new stream ciphers that are included in ISO.
2.2.3 MAC (Message Authentication Code)
Message Authentication Codes are utilized for authentication
purpose between parties, sharing a key. They are used in
communication networks as they are more efficient in
performance than any other encryption process.
User M1 wants to send M2 a text. He encodes the message by
means of a secret key which knows to M2. M2 will receive the
message and will decrypt it using the key (Sharma, 2015).
Figure 5 MAC Process
In the constrained environment is like cellular phones where
complex computation is not possible due to non-availability of
the resources. The cellular environment can capacitate less
power consumption otherwise the battery can run out. In this
context nested MAC or HMAC (Hash MAC) is used for security
purposes. HMAC is widely used for wireless communication
environment (Gaubatz, 2005)
Implementation of HMAC:
1. Divide the message to be input into blocks of n-bits.
2. A key K, which should be equal to the length of b
(length of the message), is XORed with a constant
called i-pad.
3. The output received from above step is then
appended to the message.
4. Apply the hash function to the output received from
the above step.
5. Now, the key K is XORed with another constant I-pad.
6. This output is then appended to the result received in
step 4.
7. Apply a hash function to the above string.
8. Select the leftmost t bytes of the above result as the
MAC.
The most standard MAC used aimed at the monetary
transaction is the CBC-MAC.
CBC-MAC – The CBC-MAC is grounded on an n-bit block
cipher. In this, the plain text is appended with the multiple of
the length of the plaintext and then the output is separated
into t n-bit blocks ranging from x1 to tx.
C1: Ek (x0)
Ci: Ek (xi ⨁ ci-1), 1< i <=t
Where ⨁ denotes the exclusive-or bitwise operator.
2.2.4. Hash Function
A hash function produces an output of fixed size and the input
can be of varying size. It is very easy to calculate the hash. The
result generated by the hash function is called as digest it is
typically of the formula:
h ( x )= y
Where x ϵ Z and y ϵ Zn
Properties of a hash function:
We have seen that the hash function tends to decrease the
input given that means that we can find two or more inputs
for the same output.
Preimage Resistance – It means that if we have a
message digest y, then it is not possible to find x like
that h(x) = y.
Weak Collision Resistance – If we are given two
values, x and y then it is computationally not possible
to find x’ ≠ x such that h(x) = h (x’).
Collision Resistance – It means that it is
computationally not possible to find x and x’ where x
≠ x’ such that h(x) = h (x’). Here, we can choose the
messages so it is called as strong resistance (Sharma,
2015).
2.3. Asymmetric Cryptosystems
In asymmetric cryptosystems, two keys are used, one is the
key for public and another one is the private key. Both these
keys are mathematically linked to one another. If user M1
desires to conduct a message to M2, he will encrypt it using
M2’s public key. On receiving the message, M2 will decrypt it
using his private key (Diffie, 1976).
Fig 5: Asymmetric or public key cryptosystems
Where M1: user 1, M2: User 2, E: Encryption, D: Decryption.
One such public-key algorithm is RSA. RSA is grounded at the
difference among the convenience of locating two massive
prime numbers and the difficulty of factoring huge prime
numbers. The attacks that can be performed on RSA are
Forward Search Attack and Common Modulus Attack (Jasuja,
2015).
Steps to implement RSA:
1. Choice two large prime digits p & q.
2. Compute n = p*q;
3. Compute Φ = (p-1)(q-1)
4. Select an integer e, 1<e< Φ, such that gcd (e, Φ) =
1.
5. Compute the secret component d, 1<d< Φ, such
that ed = 1.
6. The public key is (n, e) and the private key (d, p, q).
All these values are kept secret.
3
and restrain key recovery attacks.
In last 20 years, many stream ciphers ensure developed that
can operate on 32-bit and 64bit processors. MUGI and SNOW
are two new stream ciphers that are included in ISO.
2.2.3 MAC (Message Authentication Code)
Message Authentication Codes are utilized for authentication
purpose between parties, sharing a key. They are used in
communication networks as they are more efficient in
performance than any other encryption process.
User M1 wants to send M2 a text. He encodes the message by
means of a secret key which knows to M2. M2 will receive the
message and will decrypt it using the key (Sharma, 2015).
Figure 5 MAC Process
In the constrained environment is like cellular phones where
complex computation is not possible due to non-availability of
the resources. The cellular environment can capacitate less
power consumption otherwise the battery can run out. In this
context nested MAC or HMAC (Hash MAC) is used for security
purposes. HMAC is widely used for wireless communication
environment (Gaubatz, 2005)
Implementation of HMAC:
1. Divide the message to be input into blocks of n-bits.
2. A key K, which should be equal to the length of b
(length of the message), is XORed with a constant
called i-pad.
3. The output received from above step is then
appended to the message.
4. Apply the hash function to the output received from
the above step.
5. Now, the key K is XORed with another constant I-pad.
6. This output is then appended to the result received in
step 4.
7. Apply a hash function to the above string.
8. Select the leftmost t bytes of the above result as the
MAC.
The most standard MAC used aimed at the monetary
transaction is the CBC-MAC.
CBC-MAC – The CBC-MAC is grounded on an n-bit block
cipher. In this, the plain text is appended with the multiple of
the length of the plaintext and then the output is separated
into t n-bit blocks ranging from x1 to tx.
C1: Ek (x0)
Ci: Ek (xi ⨁ ci-1), 1< i <=t
Where ⨁ denotes the exclusive-or bitwise operator.
2.2.4. Hash Function
A hash function produces an output of fixed size and the input
can be of varying size. It is very easy to calculate the hash. The
result generated by the hash function is called as digest it is
typically of the formula:
h ( x )= y
Where x ϵ Z and y ϵ Zn
Properties of a hash function:
We have seen that the hash function tends to decrease the
input given that means that we can find two or more inputs
for the same output.
Preimage Resistance – It means that if we have a
message digest y, then it is not possible to find x like
that h(x) = y.
Weak Collision Resistance – If we are given two
values, x and y then it is computationally not possible
to find x’ ≠ x such that h(x) = h (x’).
Collision Resistance – It means that it is
computationally not possible to find x and x’ where x
≠ x’ such that h(x) = h (x’). Here, we can choose the
messages so it is called as strong resistance (Sharma,
2015).
2.3. Asymmetric Cryptosystems
In asymmetric cryptosystems, two keys are used, one is the
key for public and another one is the private key. Both these
keys are mathematically linked to one another. If user M1
desires to conduct a message to M2, he will encrypt it using
M2’s public key. On receiving the message, M2 will decrypt it
using his private key (Diffie, 1976).
Fig 5: Asymmetric or public key cryptosystems
Where M1: user 1, M2: User 2, E: Encryption, D: Decryption.
One such public-key algorithm is RSA. RSA is grounded at the
difference among the convenience of locating two massive
prime numbers and the difficulty of factoring huge prime
numbers. The attacks that can be performed on RSA are
Forward Search Attack and Common Modulus Attack (Jasuja,
2015).
Steps to implement RSA:
1. Choice two large prime digits p & q.
2. Compute n = p*q;
3. Compute Φ = (p-1)(q-1)
4. Select an integer e, 1<e< Φ, such that gcd (e, Φ) =
1.
5. Compute the secret component d, 1<d< Φ, such
that ed = 1.
6. The public key is (n, e) and the private key (d, p, q).
All these values are kept secret.
3

Digital Signature – Digital Signature is a method to encrypt
messages such as documents, contracts, and information
which will be transferred using data exchanging and data
encrypting protocols. In this process, an abstract is created
which is a signature or a seal which can be used by the
receiver to verify the sender (Jasuja, 2015).
2.4. MD5 (Message Digest)
The MD5 hashing algorithm is a one-way algorithm
which produces an output of fixed length by taking the
input of any length. It was originally developed to
authenticate digital signatures. But now its value has
depreciated to such extent that now it is only used as a
checksum for data integrity and data corruption. It is no
longer considered reliable because some techniques
have been detected which are easily capable of
generating MD5 collisions.
MD5 hashing algorithm works on data blocks of 512
bits, which are further divided into 16 words of 32 bits
each. The process works in multiple stages. In each
stage, 512-bit block is processed taking along the result
obtained in the previous stage.
In the primary stage, the message process esteem is
introduced utilizing the hexadecimal numerical
qualities.
Each stage incorporates four message process passes
which control the qualities in the square. The last
esteem processed from the last square is considered as
the message process. The point of MD5 is to deliver a
yield that looks irregular.
To be viewed as secure, the hash work needs to meet
these two prerequisites: it ought to be difficult to make
a message coordinating a particular hash esteem and it
ought to be difficult to make two messages that make a
similar hash esteem (Jasuja, 2015).
Steps in MD5:
1. Attach the padding bits: The text is padded so that
its size converts 64 bits fewer than the multiple of
512. In padding, first one bit “1” is appended to the
text and then the “0s” are appended till the
measurement becomes 64 bits which is less than
the several of 512.
2. Append the length: The size of the text is counted
and is transformed to binary. It is then appended to
the output in step 1. These are the remaining 64
bits.
3. Initializing MD buffer: A 4-word buffer – A, B, C, and
D are utilized with compute the message digest
(MD). AB, C, and D are 32-bit registers.
4. Process the Message: Here, four supporting
functions are definite. These functions take in 32-
bit expression input and yield a 32-bit word output
(Patil, 2013).
2.5. SHA(Secure Hash Algorithm)
The Secure Hash Algorithms are the series of cryptographic
hash utilities. Few of the popular SHA are SHA-1, SHA-2, and
SHA-5. SHA is better than MD5 as it is strongly encrypted in
response to the hackers attack. A very common application of
SHA is encrypting passwords. This is very helpful in the case
any hacker tries to attack the database as now he will only find
the random hashed values rather than the actual password.
These algorithms are also used in security applications such as
TLS, SSL<, IPsec, MIME etc.
3. Network Security Threats
For any organization, it’s IT structure is an asset as it is
the essential part of which all the employees depend
upon to do their job. Nowadays, an IT infrastructure has
made productive work and profit-making fast and
reliable. But the question arises here: Is this
infrastructure really safe? Is there any threat to it? If
there is any threat, what can it be? (Patil, 2013)
IT security is very important as it can prevent many
threats which can harm organizations valuable
information. Not only the data of the company is leaked
but also the formula of success of that company falls into
the wrong hands which can devastate the company.
In 2017, Tesco Bank faced a cyber raid on one of its
customer’s accounts.
Types of security risks to organizations are:
Hackers – Organizations are targeted by hackers for
financial gains. A hacker is a person who has technical
skills to overcome any computer security (Jasuja, 2015).
Viruses – Virus is a computer program that replicates and
executes itself and intervenes in the process a computer
operates. It is costly and dangerous.
Spyware – It is harmful software that spies the user
without his knowledge or permission. If a criminal is able
to install a spyware on an organization’s system then he
can monitor all the activities of the device.
Adware – The unwanted advertisements appearing on
the screen are mostly infected by adware. A person may
download this adware by mistake. It can retrieve your
information without your knowledge.
Phishing – Phishing can be done by sending packets to
the internal user by tricking the packet filter using the
exact IP address as of the internal user so that sensitive
and critical information like username and password can
be retrieved of an organization’s system.
Worms – This malicious software reproduces itself in
massive quantity momentarily. It can degrade your
network performance and can be used to launch other
malicious software through your system (Patil, 2013).
Spam – Spams are the junk emails, which may contain
harmful links. It can also take over your system and
generate and distribute more spams. These can overload
your mail server and may also clog an organization’s
server.
Botnets – A botnet involves many computers, connected
to the internet which runs and controls one or more bots.
Deployed by a botmaster, this security threat, commands
4
messages such as documents, contracts, and information
which will be transferred using data exchanging and data
encrypting protocols. In this process, an abstract is created
which is a signature or a seal which can be used by the
receiver to verify the sender (Jasuja, 2015).
2.4. MD5 (Message Digest)
The MD5 hashing algorithm is a one-way algorithm
which produces an output of fixed length by taking the
input of any length. It was originally developed to
authenticate digital signatures. But now its value has
depreciated to such extent that now it is only used as a
checksum for data integrity and data corruption. It is no
longer considered reliable because some techniques
have been detected which are easily capable of
generating MD5 collisions.
MD5 hashing algorithm works on data blocks of 512
bits, which are further divided into 16 words of 32 bits
each. The process works in multiple stages. In each
stage, 512-bit block is processed taking along the result
obtained in the previous stage.
In the primary stage, the message process esteem is
introduced utilizing the hexadecimal numerical
qualities.
Each stage incorporates four message process passes
which control the qualities in the square. The last
esteem processed from the last square is considered as
the message process. The point of MD5 is to deliver a
yield that looks irregular.
To be viewed as secure, the hash work needs to meet
these two prerequisites: it ought to be difficult to make
a message coordinating a particular hash esteem and it
ought to be difficult to make two messages that make a
similar hash esteem (Jasuja, 2015).
Steps in MD5:
1. Attach the padding bits: The text is padded so that
its size converts 64 bits fewer than the multiple of
512. In padding, first one bit “1” is appended to the
text and then the “0s” are appended till the
measurement becomes 64 bits which is less than
the several of 512.
2. Append the length: The size of the text is counted
and is transformed to binary. It is then appended to
the output in step 1. These are the remaining 64
bits.
3. Initializing MD buffer: A 4-word buffer – A, B, C, and
D are utilized with compute the message digest
(MD). AB, C, and D are 32-bit registers.
4. Process the Message: Here, four supporting
functions are definite. These functions take in 32-
bit expression input and yield a 32-bit word output
(Patil, 2013).
2.5. SHA(Secure Hash Algorithm)
The Secure Hash Algorithms are the series of cryptographic
hash utilities. Few of the popular SHA are SHA-1, SHA-2, and
SHA-5. SHA is better than MD5 as it is strongly encrypted in
response to the hackers attack. A very common application of
SHA is encrypting passwords. This is very helpful in the case
any hacker tries to attack the database as now he will only find
the random hashed values rather than the actual password.
These algorithms are also used in security applications such as
TLS, SSL<, IPsec, MIME etc.
3. Network Security Threats
For any organization, it’s IT structure is an asset as it is
the essential part of which all the employees depend
upon to do their job. Nowadays, an IT infrastructure has
made productive work and profit-making fast and
reliable. But the question arises here: Is this
infrastructure really safe? Is there any threat to it? If
there is any threat, what can it be? (Patil, 2013)
IT security is very important as it can prevent many
threats which can harm organizations valuable
information. Not only the data of the company is leaked
but also the formula of success of that company falls into
the wrong hands which can devastate the company.
In 2017, Tesco Bank faced a cyber raid on one of its
customer’s accounts.
Types of security risks to organizations are:
Hackers – Organizations are targeted by hackers for
financial gains. A hacker is a person who has technical
skills to overcome any computer security (Jasuja, 2015).
Viruses – Virus is a computer program that replicates and
executes itself and intervenes in the process a computer
operates. It is costly and dangerous.
Spyware – It is harmful software that spies the user
without his knowledge or permission. If a criminal is able
to install a spyware on an organization’s system then he
can monitor all the activities of the device.
Adware – The unwanted advertisements appearing on
the screen are mostly infected by adware. A person may
download this adware by mistake. It can retrieve your
information without your knowledge.
Phishing – Phishing can be done by sending packets to
the internal user by tricking the packet filter using the
exact IP address as of the internal user so that sensitive
and critical information like username and password can
be retrieved of an organization’s system.
Worms – This malicious software reproduces itself in
massive quantity momentarily. It can degrade your
network performance and can be used to launch other
malicious software through your system (Patil, 2013).
Spam – Spams are the junk emails, which may contain
harmful links. It can also take over your system and
generate and distribute more spams. These can overload
your mail server and may also clog an organization’s
server.
Botnets – A botnet involves many computers, connected
to the internet which runs and controls one or more bots.
Deployed by a botmaster, this security threat, commands
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

other bots to run and perform malicious activities over
the internet. These are sometimes called “zombie army”.
Rootkits – It is a collection of software, which are
malicious that can access a computer that is not allowed.
It provides access to a malicious program up to
administrative-level. It first gains access to the user-level
and then it could crack the password of administrative-
level.
DOS (Denial-of-Service) Attacks – In this kind of an
attack, the attacker makes the company’s resources
unavailable to it. These are mostly done for blackmailing
and ransom. The most famous kind of DOS attack is DDOS
(Distributed Denial-of-Service) attack, which involves
swamping your server with traffic and request so that the
server gets filled and shut down (Sharma, 2015).
PROPOSED DESIGN
In the proposed design, the network security issue has been
resolved. The private conversation between M1 and M2 could
have been listened by the attacker who might get into the
network and get to know the private information. But now, by
encrypting the text using the above-described algorithms,
confidentiality can be achieved. Also by using the public and
private key, we have also achieved authentication as the data
has been signed by the sender.
CONCLUSION
We have successfully found the solution for network
security issues using cryptographic techniques. There are
many techniques to encrypt the text like a stream cipher,
block cipher, MAC, SHA, RSA. In this paper, we have also seen
the detailed description of some of the algorithms which can
be directly realized in the programming languages. The
research in the area of cryptography is increasing which is
giving better solutions for securing our data.
REFERENCES
[1] Sharma, R., & Bollavarapu, S. (2015). Data Security using Compression
and Cryptography Techniques. International Journal of Computer
Applications, 117(14).
[2] Patil, M., & Sahu, V. (2013). A Survey of Compression and Encryption
technique for SMS. International Journal of Advancements in Research &
Technology, 2(5).
[3] Jasuja, B., & Pandya, A. (2015). Crypto-Compression System: An
Integrated Approach using Stream Cipher Cryptography and Entropy
Encoding. International Journal of Computer Applications, 116(21).
[4] Diffie, W., & Hellman, M. (1976). New directions in cryptography. IEEE
Transactions on Information Theory, 22(6), 644-654.
[5] Gaubatz, G., Kaps, J. P., Ozturk, E., & Sunar, B. (2005, March). State of
the art in ultra-low power public key cryptography for wireless sensor
networks. In Pervasive Computing and Communications Workshops,
2005. PerCom 2005 Workshops. Third IEEE International Conference
on (pp. 146-150). IEEE.
5
the internet. These are sometimes called “zombie army”.
Rootkits – It is a collection of software, which are
malicious that can access a computer that is not allowed.
It provides access to a malicious program up to
administrative-level. It first gains access to the user-level
and then it could crack the password of administrative-
level.
DOS (Denial-of-Service) Attacks – In this kind of an
attack, the attacker makes the company’s resources
unavailable to it. These are mostly done for blackmailing
and ransom. The most famous kind of DOS attack is DDOS
(Distributed Denial-of-Service) attack, which involves
swamping your server with traffic and request so that the
server gets filled and shut down (Sharma, 2015).
PROPOSED DESIGN
In the proposed design, the network security issue has been
resolved. The private conversation between M1 and M2 could
have been listened by the attacker who might get into the
network and get to know the private information. But now, by
encrypting the text using the above-described algorithms,
confidentiality can be achieved. Also by using the public and
private key, we have also achieved authentication as the data
has been signed by the sender.
CONCLUSION
We have successfully found the solution for network
security issues using cryptographic techniques. There are
many techniques to encrypt the text like a stream cipher,
block cipher, MAC, SHA, RSA. In this paper, we have also seen
the detailed description of some of the algorithms which can
be directly realized in the programming languages. The
research in the area of cryptography is increasing which is
giving better solutions for securing our data.
REFERENCES
[1] Sharma, R., & Bollavarapu, S. (2015). Data Security using Compression
and Cryptography Techniques. International Journal of Computer
Applications, 117(14).
[2] Patil, M., & Sahu, V. (2013). A Survey of Compression and Encryption
technique for SMS. International Journal of Advancements in Research &
Technology, 2(5).
[3] Jasuja, B., & Pandya, A. (2015). Crypto-Compression System: An
Integrated Approach using Stream Cipher Cryptography and Entropy
Encoding. International Journal of Computer Applications, 116(21).
[4] Diffie, W., & Hellman, M. (1976). New directions in cryptography. IEEE
Transactions on Information Theory, 22(6), 644-654.
[5] Gaubatz, G., Kaps, J. P., Ozturk, E., & Sunar, B. (2005, March). State of
the art in ultra-low power public key cryptography for wireless sensor
networks. In Pervasive Computing and Communications Workshops,
2005. PerCom 2005 Workshops. Third IEEE International Conference
on (pp. 146-150). IEEE.
5
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





