Analysis of Staysure.co.uk Ltd Cyber Breach: Security and Psychology
VerifiedAdded on 2023/04/22
|22
|5741
|160
Report
AI Summary
This report provides a detailed analysis of the cyber breach at Staysure.co.uk Ltd, a financial and insurance services company. It summarizes the case, highlighting the compromise of over 100,000 customer credit card details due to software vulnerabilities and inadequate security measures. The report includes a high-level security architecture diagram, a risk assessment covering assets, threats, and vulnerabilities, and recommendations for preventing future breaches. It also explores the psychological motivations behind potential insider attacks and proposes a security assurance architecture with relevant information security policies to enhance system protection. The analysis aims to improve the integrity, accessibility, and confidentiality of Staysure's data and systems.

Running head: CYBER BREACH
CYBER BREACH
Name of student
Name of university
Author’s note:
CYBER BREACH
Name of student
Name of university
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CYBER BREACH
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Stage 1........................................................................................................................2
Task 1: Summary...................................................................................................2
Task 2: Security architecture..................................................................................4
Stage 2: Threat analysis and threat assessment..........................................................4
Task 3: Risk analysis and threat assessment..........................................................4
Task 4: Recommendations.....................................................................................7
Stage 3: Psychological motivations........................................................................10
Task 5: Psychological motivations for insider attack..........................................10
Stage 4: Security architecture...................................................................................12
Task 6: Design of security assurance architecture...............................................12
Task 7: Security policies......................................................................................14
Conclusion....................................................................................................................16
References....................................................................................................................17
CYBER BREACH
Table of Contents
Introduction....................................................................................................................2
Discussion......................................................................................................................2
Stage 1........................................................................................................................2
Task 1: Summary...................................................................................................2
Task 2: Security architecture..................................................................................4
Stage 2: Threat analysis and threat assessment..........................................................4
Task 3: Risk analysis and threat assessment..........................................................4
Task 4: Recommendations.....................................................................................7
Stage 3: Psychological motivations........................................................................10
Task 5: Psychological motivations for insider attack..........................................10
Stage 4: Security architecture...................................................................................12
Task 6: Design of security assurance architecture...............................................12
Task 7: Security policies......................................................................................14
Conclusion....................................................................................................................16
References....................................................................................................................17

2
CYBER BREACH
Introduction
This report aims to discuss the issue of cyber breach at Staysure.co.uk Ltd. A detailed
case articulation is provided in this report. The summary of the case study from the open
source is provided in this report. A high level security diagram is provided in this report for
the company. A risk assessment of the architecture and the system is carried out that covers
all the assets, vulnerabilities, threat actors, and the threat sources. A short recommendation is
provided for preventing the breach. The psychological motivations that could be used for
explaining the attack is discussed in this report. A security assurance architecture is provided
that could have prevented the data breach with explanation of the components and the
architectures. A set of information security policies that covers the system for including the
overall security policies is provided in this report.
Discussion
Stage 1
Task 1: Summary
Staysure.co.uk Ltd has the speciality in the financial and insurance services in Europe
and UK. It was designed in 2004 for providing the travel insurance and then expanded further
for providing motor, home, health, and life insurance along with several other insurance
products. In the month of October, 2013 Staysure.co.uk faced a serious security breach
wherein over 100,000 live details of credit card along with the other personal details of
customers were compromised. The security breach almost affected 7% of customers who had
bought insurance from the Staysure prior May 2012. Prior May 2012, the card numbers of the
customers were stored by the company along CVV numbers and several other personal
details like the name and address of the customers. The encryption of the card details was
done but the entry of the CVV numbers in the database were not done according to the rules
CYBER BREACH
Introduction
This report aims to discuss the issue of cyber breach at Staysure.co.uk Ltd. A detailed
case articulation is provided in this report. The summary of the case study from the open
source is provided in this report. A high level security diagram is provided in this report for
the company. A risk assessment of the architecture and the system is carried out that covers
all the assets, vulnerabilities, threat actors, and the threat sources. A short recommendation is
provided for preventing the breach. The psychological motivations that could be used for
explaining the attack is discussed in this report. A security assurance architecture is provided
that could have prevented the data breach with explanation of the components and the
architectures. A set of information security policies that covers the system for including the
overall security policies is provided in this report.
Discussion
Stage 1
Task 1: Summary
Staysure.co.uk Ltd has the speciality in the financial and insurance services in Europe
and UK. It was designed in 2004 for providing the travel insurance and then expanded further
for providing motor, home, health, and life insurance along with several other insurance
products. In the month of October, 2013 Staysure.co.uk faced a serious security breach
wherein over 100,000 live details of credit card along with the other personal details of
customers were compromised. The security breach almost affected 7% of customers who had
bought insurance from the Staysure prior May 2012. Prior May 2012, the card numbers of the
customers were stored by the company along CVV numbers and several other personal
details like the name and address of the customers. The encryption of the card details was
done but the entry of the CVV numbers in the database were not done according to the rules
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CYBER BREACH
of the industry. The CEO of the company claimed that the storing of the details was done for
helping the customers in the process of renewal. Post May 2012, the details storing was
ceased by the company. The server where the website server was based had a vulnerability of
software and even though the publishing of the software patch was done in the between 2010
and 2013, the controller of data failed in updating the software both the times due to lack of
the formal process for review and applying the updates of software. The failure of updating
the security flaws and the database software in IT security system created significant
vulnerability to the cyber attack. The flaws in the JBoss application web server were
exploited among October 2013. The vulnerability was used by the attacker in the application
server for injecting the malicious JavaScript code called the JSPSpy on the website of the
firm. Using JSPSpy, the attackers were able to remotely view and then perform the
modification on the source code of the website and then query on the database that contains
all the details of customers. It also allows the attackers to open a command shell that allows
them to remotely execute the privileged commands of operating system. The attackers
particularly downloaded after they targeted the details of payment card. Although, encryption
was done to the card numbers, the attackers were able in identifying the keys that were used
in the encryption and then could decryption was performed for the card numbers. During the
time of attack, the database included almost 110, 096 live details of cards, that posed a threat
of being exposed and then used for the fraudulent transactions. The knowledge of the attack
was gained by the company on 14th November 2013 and then immediately hiring of
independent experts of forensic data was done and wrote to over 93, 389 customers for
providing them with the knowledge of the attack. Free access to the Data patrol was provided
to the affected customers by the company that is the monitoring service of the identity fraud.
CYBER BREACH
of the industry. The CEO of the company claimed that the storing of the details was done for
helping the customers in the process of renewal. Post May 2012, the details storing was
ceased by the company. The server where the website server was based had a vulnerability of
software and even though the publishing of the software patch was done in the between 2010
and 2013, the controller of data failed in updating the software both the times due to lack of
the formal process for review and applying the updates of software. The failure of updating
the security flaws and the database software in IT security system created significant
vulnerability to the cyber attack. The flaws in the JBoss application web server were
exploited among October 2013. The vulnerability was used by the attacker in the application
server for injecting the malicious JavaScript code called the JSPSpy on the website of the
firm. Using JSPSpy, the attackers were able to remotely view and then perform the
modification on the source code of the website and then query on the database that contains
all the details of customers. It also allows the attackers to open a command shell that allows
them to remotely execute the privileged commands of operating system. The attackers
particularly downloaded after they targeted the details of payment card. Although, encryption
was done to the card numbers, the attackers were able in identifying the keys that were used
in the encryption and then could decryption was performed for the card numbers. During the
time of attack, the database included almost 110, 096 live details of cards, that posed a threat
of being exposed and then used for the fraudulent transactions. The knowledge of the attack
was gained by the company on 14th November 2013 and then immediately hiring of
independent experts of forensic data was done and wrote to over 93, 389 customers for
providing them with the knowledge of the attack. Free access to the Data patrol was provided
to the affected customers by the company that is the monitoring service of the identity fraud.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
CYBER BREACH
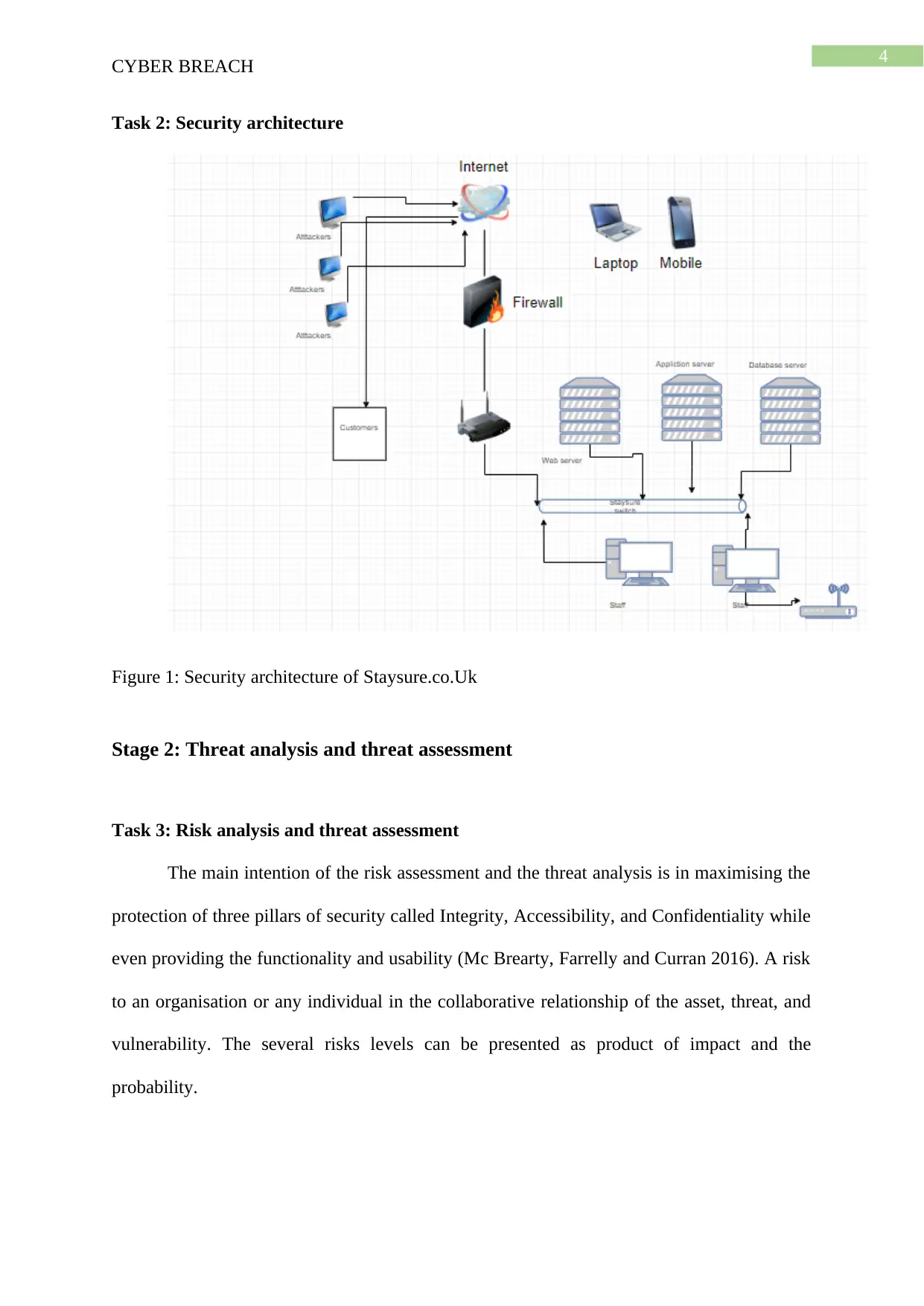
Task 2: Security architecture
Figure 1: Security architecture of Staysure.co.Uk
Stage 2: Threat analysis and threat assessment
Task 3: Risk analysis and threat assessment
The main intention of the risk assessment and the threat analysis is in maximising the
protection of three pillars of security called Integrity, Accessibility, and Confidentiality while
even providing the functionality and usability (Mc Brearty, Farrelly and Curran 2016). A risk
to an organisation or any individual in the collaborative relationship of the asset, threat, and
vulnerability. The several risks levels can be presented as product of impact and the
probability.
CYBER BREACH
Task 2: Security architecture
Figure 1: Security architecture of Staysure.co.Uk
Stage 2: Threat analysis and threat assessment
Task 3: Risk analysis and threat assessment
The main intention of the risk assessment and the threat analysis is in maximising the
protection of three pillars of security called Integrity, Accessibility, and Confidentiality while
even providing the functionality and usability (Mc Brearty, Farrelly and Curran 2016). A risk
to an organisation or any individual in the collaborative relationship of the asset, threat, and
vulnerability. The several risks levels can be presented as product of impact and the
probability.

5
CYBER BREACH
Quantative Qualitative Description
5 High Any high risk can take place often and it
can have a significant effect on
organisation. Various measures would be
required for the mitigation of any high
level risk.
4 Medium Any medium risk could occur with the
higher probability but it might not persist.
If this occurs the organisations could have
any significant or severe effect.
3 Medium Any medium risk would likely to occur in
many situations and if any medium level
attack occurs it might have the moderate
to severe effect on organisation.
2 Low
medium
Any low medium risk could be considered
when any organisation would have any
moderate or minor impact as the result of
any attack.
1 Low
medium
Any low medium risk could be considered
to be low when likelihood of any attack on
any entity is low and impact of the attack
on entity is minor or negligible.
CYBER BREACH
Quantative Qualitative Description
5 High Any high risk can take place often and it
can have a significant effect on
organisation. Various measures would be
required for the mitigation of any high
level risk.
4 Medium Any medium risk could occur with the
higher probability but it might not persist.
If this occurs the organisations could have
any significant or severe effect.
3 Medium Any medium risk would likely to occur in
many situations and if any medium level
attack occurs it might have the moderate
to severe effect on organisation.
2 Low
medium
Any low medium risk could be considered
when any organisation would have any
moderate or minor impact as the result of
any attack.
1 Low
medium
Any low medium risk could be considered
to be low when likelihood of any attack on
any entity is low and impact of the attack
on entity is minor or negligible.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CYBER BREACH
This figure shows the risk matrix that represents various risk levels. Any vulnerability
is the weakness in system, which can be exploited by any attacked or it can be unintentionally
triggered by any person in any organisation. The likelihood is possibility, which any
vulnerability would be advantageous or any vulnerability would be triggered by anyone
unintentionally. The likelihood is connected to the intent of the attacker, the ability of the
attacker and the target of the attacker. If any certain vulnerability would be exploited, impact
on any organisation could be expressed in the terms like the minor, moderate, negligible,
significant, severe.
This table below displays the risk assessment architecture for the Staysure.co.Uk. This
firm had various flaws in the security in system that the attackers used for gaining the access
to the information of the customer.
Asset Threat Vulnerability Threat Actor Consequence
s
Likelihood
Customer
personal
details
Can be
accessed and
manipulated
No security
procedure
was
implemented
in the
database as
the data is
Any person
or hacker in
the
organisations
Gaining the
access to the
database with
getting the
access to
webserver or
the SQL
The personal
details of the
employees
like the
name, phone
address
could be
CYBER BREACH
This figure shows the risk matrix that represents various risk levels. Any vulnerability
is the weakness in system, which can be exploited by any attacked or it can be unintentionally
triggered by any person in any organisation. The likelihood is possibility, which any
vulnerability would be advantageous or any vulnerability would be triggered by anyone
unintentionally. The likelihood is connected to the intent of the attacker, the ability of the
attacker and the target of the attacker. If any certain vulnerability would be exploited, impact
on any organisation could be expressed in the terms like the minor, moderate, negligible,
significant, severe.
This table below displays the risk assessment architecture for the Staysure.co.Uk. This
firm had various flaws in the security in system that the attackers used for gaining the access
to the information of the customer.
Asset Threat Vulnerability Threat Actor Consequence
s
Likelihood
Customer
personal
details
Can be
accessed and
manipulated
No security
procedure
was
implemented
in the
database as
the data is
Any person
or hacker in
the
organisations
Gaining the
access to the
database with
getting the
access to
webserver or
the SQL
The personal
details of the
employees
like the
name, phone
address
could be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CYBER BREACH
hugely
accessible
injections accessed,
used or
modified
Company
website
The website
source code
could be
modified
and then
malicious
code could
be injected
and then
made to
execute on
browser
The cross
site scripting
could be
performed
on website if
the security
measures are
not properly
handled
while the
development
of the
website.
Insider or
any hacker
Web pages The
injection of
the
malicious
code in the
web pages
could be
done and
therefore
allowing the
access to
web server
and database
Controller
system of
data
Lack of the
intrusion
detection
system
Any system
without the
proper
security
measures
could be
simply
penetrated
Insider or
any hacker
who is
attempting in
getting the
unauthorised
access
Any backdoor
that is created
in the web
server
Gaining
access to
data
controllers
allows threat
actor in
executing
the
privileged
commands
of operating
system
Details of
financial
card
Incorrect
storage of
the financial
details
The
unencrypted
details that
are stored in
the database
Insider or
any hacker
who are
attempting to
obtain
unauthorised
access
The source
code of the
website could
be exploited
for the
querying the
database
The card
details could
be used for
making the
fraudulent
transaction
and the
cloning
Task 4: Recommendations
Commonly, the data breaches could happen due to the hackers obtaining the access to
information or else lose any device that has the unencrypted information. Some of the
methods of preventing the breaches to the website are:
CYBER BREACH
hugely
accessible
injections accessed,
used or
modified
Company
website
The website
source code
could be
modified
and then
malicious
code could
be injected
and then
made to
execute on
browser
The cross
site scripting
could be
performed
on website if
the security
measures are
not properly
handled
while the
development
of the
website.
Insider or
any hacker
Web pages The
injection of
the
malicious
code in the
web pages
could be
done and
therefore
allowing the
access to
web server
and database
Controller
system of
data
Lack of the
intrusion
detection
system
Any system
without the
proper
security
measures
could be
simply
penetrated
Insider or
any hacker
who is
attempting in
getting the
unauthorised
access
Any backdoor
that is created
in the web
server
Gaining
access to
data
controllers
allows threat
actor in
executing
the
privileged
commands
of operating
system
Details of
financial
card
Incorrect
storage of
the financial
details
The
unencrypted
details that
are stored in
the database
Insider or
any hacker
who are
attempting to
obtain
unauthorised
access
The source
code of the
website could
be exploited
for the
querying the
database
The card
details could
be used for
making the
fraudulent
transaction
and the
cloning
Task 4: Recommendations
Commonly, the data breaches could happen due to the hackers obtaining the access to
information or else lose any device that has the unencrypted information. Some of the
methods of preventing the breaches to the website are:

8
CYBER BREACH
Protection of the information: The sensitive information should be protected
whenever the storing has been done or accessed (Black 2013).
Reduction of the data transfer: Strict ban must be implemented on the transfer of the
data from one device to any another external device (Gao, Zhong and Mei 2015). The loss of
the removable media would put data on disk under severe risk.
Restriction of the download: Media that would serve as the allegiance to hackers must
be placed with restriction in downloading (Laube and Böhme 2016). It could significantly
reduce the transferring risk of the downloadable media to any external source.
Shredding of the files: organisation must shred the files and the folder prior disposing
any equipment of storage (Ahmed and Hossain 2014). There are several applications that can
retrieve the information after executing the formatting.
Ban on the unencrypted device: The organisation must implement ban on device that
have been unencrypted. The portable devices and the laptops which are unencrypted are
vulnerable to the attack.
Securing transfer: The exploitation of the secure courier services and the packaging
that is tamper proof during the bulk data transportation would help in the preventing any
breach (Wang et al. 2013).
Strong password: password for access should be unpredictable and immensely
difficult to hack. The change of the password in regular intervals.
Automation of the security: the automating system which regularly checks the settings
of the password, firewall and the server configuration may bring the reduction of the risk in
sensitive information (Hovav and Gray 2014).
CYBER BREACH
Protection of the information: The sensitive information should be protected
whenever the storing has been done or accessed (Black 2013).
Reduction of the data transfer: Strict ban must be implemented on the transfer of the
data from one device to any another external device (Gao, Zhong and Mei 2015). The loss of
the removable media would put data on disk under severe risk.
Restriction of the download: Media that would serve as the allegiance to hackers must
be placed with restriction in downloading (Laube and Böhme 2016). It could significantly
reduce the transferring risk of the downloadable media to any external source.
Shredding of the files: organisation must shred the files and the folder prior disposing
any equipment of storage (Ahmed and Hossain 2014). There are several applications that can
retrieve the information after executing the formatting.
Ban on the unencrypted device: The organisation must implement ban on device that
have been unencrypted. The portable devices and the laptops which are unencrypted are
vulnerable to the attack.
Securing transfer: The exploitation of the secure courier services and the packaging
that is tamper proof during the bulk data transportation would help in the preventing any
breach (Wang et al. 2013).
Strong password: password for access should be unpredictable and immensely
difficult to hack. The change of the password in regular intervals.
Automation of the security: the automating system which regularly checks the settings
of the password, firewall and the server configuration may bring the reduction of the risk in
sensitive information (Hovav and Gray 2014).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CYBER BREACH
Identification of the threats: the team of security must have the capability of
identifying the suspicious activity on the network and it should be prepared in case there is
any attack from network.
Monitoring the leakage of data: The periodic checking of the controls of security
would allows the team of security in having the control on network (Serwadda and Phoha
2013). The constant check on the contents of the internet for locating whether any private
data is accessible for the viewing to the public is also a good practise of monitoring the data
Tracking the data: the tracking of the data motion in the network of the organisation
would prevent the unintentional use of the sensitive information (Lee, Geng and Raghunathan
2013).
Defining the accessibility: Outlining the accessibility to the people who are currently
working on the sensitive data of the company would help in reducing the risk of the malicious
users.
Training of security measures: Offering the training of the security and privacy to all
the clients, employees and any other connected to the data activities would help in reducing
the awareness regarding the data breaches (Liu et al. 2015).
Stopping incursion: by shutting down the avenues to the warehouse of the company
would prevent any incursion by any hacker. The solutions of production, security, and
production should be complained for preventing the targeted attacks (Amin, Maitra and Rana
2013).
Response to any breach: possessing any response for any kind of breaches would help
in triggering the swift response to any data breaches and assist in harm reduction. This plan
could possess the steps involved notifications of any concerned staff or agency who could
handle the breach (Chou 2013).
CYBER BREACH
Identification of the threats: the team of security must have the capability of
identifying the suspicious activity on the network and it should be prepared in case there is
any attack from network.
Monitoring the leakage of data: The periodic checking of the controls of security
would allows the team of security in having the control on network (Serwadda and Phoha
2013). The constant check on the contents of the internet for locating whether any private
data is accessible for the viewing to the public is also a good practise of monitoring the data
Tracking the data: the tracking of the data motion in the network of the organisation
would prevent the unintentional use of the sensitive information (Lee, Geng and Raghunathan
2013).
Defining the accessibility: Outlining the accessibility to the people who are currently
working on the sensitive data of the company would help in reducing the risk of the malicious
users.
Training of security measures: Offering the training of the security and privacy to all
the clients, employees and any other connected to the data activities would help in reducing
the awareness regarding the data breaches (Liu et al. 2015).
Stopping incursion: by shutting down the avenues to the warehouse of the company
would prevent any incursion by any hacker. The solutions of production, security, and
production should be complained for preventing the targeted attacks (Amin, Maitra and Rana
2013).
Response to any breach: possessing any response for any kind of breaches would help
in triggering the swift response to any data breaches and assist in harm reduction. This plan
could possess the steps involved notifications of any concerned staff or agency who could
handle the breach (Chou 2013).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CYBER BREACH
Stage 3: Psychological motivations
Task 5: Psychological motivations for insider attack
It has been observed that the motivation is the major factor that leads to the insider
threats. These motivations includes the stress, greed, espionage and revenge (Gordon et al.
2015). The motivation of the insider attack could be grouped into three major categories,
which are financial gain, sabotage, and the business gain. It has been discovered that in the
recent times, the major reason for the insider attacks is the financial, which is the intention of
the attacker to sell the data and information of the organisation that exists in database
(Crossler et al. 2013). Frequently, the insiders intentionally misuse the system for gaining the
sensitive data for the business or financial gains. Whether motivation is accidental or
deliberate, this represents the significant risk of the inappropriate activity of the user
(Soomro, Shah and Ahmed 2016). The motivation of the malicious insider could include the
intent of gaining personal financial data or insider might have been recruited by any
competitive organisations, which financially rewards the insider for the breach. The
opportunity could be an important motivational factor, the methods by which the availability
of the opportunity could motivate the employees in abusing the organisations (Huang, Behara
and Goo 2014). Most of the insider breaches in the banking and the finance sector is
motivated by the personal gains, instead of any desire of sabotaging the information or the
infrastructure of the organisations. The insiders stole the information for selling it and then
modified the data for achieving the financial gains for their own. Another motivation for the
insider breaches is the business advantages (Romanosky, Hoffman and Acquisti 2014). In
these cases, the malicious insiders stole the intellectual property for gaining any business
advantage. In some situations, the insiders stole information for gaining any direct advantage
at any new job or for implementing any new competing business. If insiders consist of the
motive for harming the organisation and having the physical or logical access either
CYBER BREACH
Stage 3: Psychological motivations
Task 5: Psychological motivations for insider attack
It has been observed that the motivation is the major factor that leads to the insider
threats. These motivations includes the stress, greed, espionage and revenge (Gordon et al.
2015). The motivation of the insider attack could be grouped into three major categories,
which are financial gain, sabotage, and the business gain. It has been discovered that in the
recent times, the major reason for the insider attacks is the financial, which is the intention of
the attacker to sell the data and information of the organisation that exists in database
(Crossler et al. 2013). Frequently, the insiders intentionally misuse the system for gaining the
sensitive data for the business or financial gains. Whether motivation is accidental or
deliberate, this represents the significant risk of the inappropriate activity of the user
(Soomro, Shah and Ahmed 2016). The motivation of the malicious insider could include the
intent of gaining personal financial data or insider might have been recruited by any
competitive organisations, which financially rewards the insider for the breach. The
opportunity could be an important motivational factor, the methods by which the availability
of the opportunity could motivate the employees in abusing the organisations (Huang, Behara
and Goo 2014). Most of the insider breaches in the banking and the finance sector is
motivated by the personal gains, instead of any desire of sabotaging the information or the
infrastructure of the organisations. The insiders stole the information for selling it and then
modified the data for achieving the financial gains for their own. Another motivation for the
insider breaches is the business advantages (Romanosky, Hoffman and Acquisti 2014). In
these cases, the malicious insiders stole the intellectual property for gaining any business
advantage. In some situations, the insiders stole information for gaining any direct advantage
at any new job or for implementing any new competing business. If insiders consist of the
motive for harming the organisation and having the physical or logical access either

11
CYBER BREACH
unauthorised or authorised, and are familiar with environment of workplace, they could
represent any serious threat to organisation (Wang et al. 2013). The malicious insider threats
can be categorised as the emotions based, financially based, and politically based. The
emotions based are the threats that are caused when any insider is depressed, frustrated, angry
or bored on the basis on any situation that involves any organisation or any workplace, there
is a high probability that the people might act out maliciously (Lafuente 2015). The
financially based insider threats are commonly motivated by the intent of gaining extra
money by any individual. If any employee is suffering from any kind of hardship financially,
or they are intending to improve the financial situations then it raises the chances of
exploiting the opportunity of insider breaches for gaining money. The unintentional insider
threats can be caused due to the lack in the knowledge or understanding, convenience, or
misplaced technology (Arlitsch and Edelman 2014). The lack of the knowledge regarding any
particular aspect if the policies of cybersecurity are increasingly technical and robust. The
aspect of Work on-the-go immensely more common every year. Moreover increased threat of
the prying eyes that are attempting in gaining access in these protected devices, it provides
any opportunity for the insiders in accidentally misplace the equipment, creating it a huge
risk (Ritter et al. 2015).
CYBER BREACH
unauthorised or authorised, and are familiar with environment of workplace, they could
represent any serious threat to organisation (Wang et al. 2013). The malicious insider threats
can be categorised as the emotions based, financially based, and politically based. The
emotions based are the threats that are caused when any insider is depressed, frustrated, angry
or bored on the basis on any situation that involves any organisation or any workplace, there
is a high probability that the people might act out maliciously (Lafuente 2015). The
financially based insider threats are commonly motivated by the intent of gaining extra
money by any individual. If any employee is suffering from any kind of hardship financially,
or they are intending to improve the financial situations then it raises the chances of
exploiting the opportunity of insider breaches for gaining money. The unintentional insider
threats can be caused due to the lack in the knowledge or understanding, convenience, or
misplaced technology (Arlitsch and Edelman 2014). The lack of the knowledge regarding any
particular aspect if the policies of cybersecurity are increasingly technical and robust. The
aspect of Work on-the-go immensely more common every year. Moreover increased threat of
the prying eyes that are attempting in gaining access in these protected devices, it provides
any opportunity for the insiders in accidentally misplace the equipment, creating it a huge
risk (Ritter et al. 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




