Cyber Operations: Principles, Analysis, and Modern Environment
VerifiedAdded on 2023/01/18
|15
|3196
|38
Report
AI Summary
This report provides an in-depth analysis of cyber operations, focusing on cyber maneuver principles, and the distinctions between offensive and defensive strategies. It examines cyber operations within the modern information environment, emphasizing the application of offensive and defensive techniques in cyberspace. The report also delves into the understanding of computer security principles from a system perspective, exploring concepts like discretionary access control and security regulations. Furthermore, it includes a practical analysis of network traffic using Wireshark, demonstrating how to capture and interpret network packets to identify potential security threats and network issues. The analysis covers color coding and error identification within the packet data to provide a comprehensive understanding of network security and cyber operations.

CYBER OPERATIONS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................3
TASK 2............................................................................................................................................3
Paper critique..........................................................................................................................3
Explain the cyber maneuver principles and the offensive and defensive operations.............4
Cyber operations in the modern environment........................................................................6
TASK 3............................................................................................................................................7
Understand principles in computer security from system perspectives.................................7
Packet analysis........................................................................................................................7
CONCLUSION..............................................................................................................................14
REFERENCES..............................................................................................................................15
INTRODUCTION...........................................................................................................................3
TASK 2............................................................................................................................................3
Paper critique..........................................................................................................................3
Explain the cyber maneuver principles and the offensive and defensive operations.............4
Cyber operations in the modern environment........................................................................6
TASK 3............................................................................................................................................7
Understand principles in computer security from system perspectives.................................7
Packet analysis........................................................................................................................7
CONCLUSION..............................................................................................................................14
REFERENCES..............................................................................................................................15

INTRODUCTION
Cyber operations are based on the activities that performed within network system which
mainly focused on the assuring critical department of defence mission. It is delivered the solution
which enable intelligence and business operations. It also implemented cyberwarfare technology
that mainly attack nation and also causes the comparable harm to actual warfare. This report is
based on the Wireshark tool that used as an open source packet analyser. It applicable for trouble
shooting, software and communication protocol and analysis. Network administrator is mainly
used for examine overall security problems, troubleshoot network issues and identifying
applications. This report will discuss about the Cyber manoeuvre in terms of modern information
environment that critically analyse about the principles which underpin defensive and offensive
operation in modern information system. Furthermore, it will discuss about the understanding of
advance principles in terms of compute security perspectives.
TASK 2
Paper critique
Deception and Maneuver Warfare Utilizing Cloud Resources
Through the paper critique we have analysed that the deception and the Maneuver
warfare had utilize the cloud resources. It is using the cloud computing resources and the SME
are operating it on the national and multinational level. Proactive operations are used by the
securing the digital assets and the including the deception strategy as well. On the other context
we think that the deception Maneuver warfare are utilized the cloud resources. These are using
the investment at the time of the Maneuver warfare and also it requires the power and storage as
well. All the knowledge is readily available but the information provided could be stolen by
anyone. It requires the high-tech security for securing the information.
Cyber operations are based on the activities that performed within network system which
mainly focused on the assuring critical department of defence mission. It is delivered the solution
which enable intelligence and business operations. It also implemented cyberwarfare technology
that mainly attack nation and also causes the comparable harm to actual warfare. This report is
based on the Wireshark tool that used as an open source packet analyser. It applicable for trouble
shooting, software and communication protocol and analysis. Network administrator is mainly
used for examine overall security problems, troubleshoot network issues and identifying
applications. This report will discuss about the Cyber manoeuvre in terms of modern information
environment that critically analyse about the principles which underpin defensive and offensive
operation in modern information system. Furthermore, it will discuss about the understanding of
advance principles in terms of compute security perspectives.
TASK 2
Paper critique
Deception and Maneuver Warfare Utilizing Cloud Resources
Through the paper critique we have analysed that the deception and the Maneuver
warfare had utilize the cloud resources. It is using the cloud computing resources and the SME
are operating it on the national and multinational level. Proactive operations are used by the
securing the digital assets and the including the deception strategy as well. On the other context
we think that the deception Maneuver warfare are utilized the cloud resources. These are using
the investment at the time of the Maneuver warfare and also it requires the power and storage as
well. All the knowledge is readily available but the information provided could be stolen by
anyone. It requires the high-tech security for securing the information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Explain the cyber maneuver principles and the offensive and defensive operations
The cyber operations include the computer programs and the ways which create the effect
on the cyber space. Cyber maneuver is the concept used in wars for destroying the enemy. The
process in which the employees move towards the enemy and also include the military support to
achieve the objective. The cyber maneuver consists of the speed which runs at the speed of the
machine and also speed responses to the human speed of the decision-making. In these processes
the military would reach the enemy without any loss. Due to emerging of the new technologies
and legal factors the cyber operations are running effectively. Operation in the cyber space is the
is depends upon the technology and the technical capabilities of the country. Traditional
maneuver warfare consists of the military forces which would also include the situation of the
war at the at time.
Cyber maneuver principles
cyber space maneuver is cyber operation which are organized for fight in growth the
enemy at the time of the war and also the to protect the information which is stored in the
computers. It includes the cyber space domain which is globally connecting all the computer
networks. The electromagnet spectrum is used for storing the information and also transmit and
modify the data of the networks as well. Cyber space actions are running at the speed of the
machine and target would be set for different attackers (Shan, Neamtiu, Qian and Torrier 2015).
Traditional maneuver involves the movement of the military forces and the also it would
support the fires in the war fighting situations. Due to the lack of the forces the maneuver war
fare would use the cyber security and cyber space maneuver for attacking and defensing at the
time of the war. Military forces consist of the computers and the software and the operations
which would run on the computers. At the time of the war the cyber operation are run according
to the conditions the attack would be offensive or defensive.
Offensive operation
offensive cyber space maneuver operations are done to obtain the denial, disruption and
destruction of the target thorough the help of the cyber space operations (Steiner 2017). These
offensive techniques are categorized on the basis of the exploitive, positional and categorized as
well. Offensive cyber maneuver is divided into the three parts and are described below:
The cyber operations include the computer programs and the ways which create the effect
on the cyber space. Cyber maneuver is the concept used in wars for destroying the enemy. The
process in which the employees move towards the enemy and also include the military support to
achieve the objective. The cyber maneuver consists of the speed which runs at the speed of the
machine and also speed responses to the human speed of the decision-making. In these processes
the military would reach the enemy without any loss. Due to emerging of the new technologies
and legal factors the cyber operations are running effectively. Operation in the cyber space is the
is depends upon the technology and the technical capabilities of the country. Traditional
maneuver warfare consists of the military forces which would also include the situation of the
war at the at time.
Cyber maneuver principles
cyber space maneuver is cyber operation which are organized for fight in growth the
enemy at the time of the war and also the to protect the information which is stored in the
computers. It includes the cyber space domain which is globally connecting all the computer
networks. The electromagnet spectrum is used for storing the information and also transmit and
modify the data of the networks as well. Cyber space actions are running at the speed of the
machine and target would be set for different attackers (Shan, Neamtiu, Qian and Torrier 2015).
Traditional maneuver involves the movement of the military forces and the also it would
support the fires in the war fighting situations. Due to the lack of the forces the maneuver war
fare would use the cyber security and cyber space maneuver for attacking and defensing at the
time of the war. Military forces consist of the computers and the software and the operations
which would run on the computers. At the time of the war the cyber operation are run according
to the conditions the attack would be offensive or defensive.
Offensive operation
offensive cyber space maneuver operations are done to obtain the denial, disruption and
destruction of the target thorough the help of the cyber space operations (Steiner 2017). These
offensive techniques are categorized on the basis of the exploitive, positional and categorized as
well. Offensive cyber maneuver is divided into the three parts and are described below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Exploitive maneuver
Through the use of the exploitive maneuver the military would capture the information of
the enemy and also gain the strategies of the enemies and as well. The information captured is
used against the enemy at the time of the war. Key information is used by the military and the
report are made for destroying the enemy.
Positional maneuver
In the positional maneuver the military would be using the physical nodes of the
information to follow the operations of the enemy. In order to control the enemy the cyber
operation would be arranged and the computers would capture all the logical nodes of the enemy
which would help us to follow the enemy and the strategies as well (Schmitt 2017).
Influencing maneuver
The cyber operation is used by the military for the taking any decisions about the enemy
at the time of the war. In the influencing power the enemy is influenced by the actions and also
the enemy would forcefully approve the decisions of the military or in the indirect way.
Kinetic maneuver operations are producing the similar effects which are giving the effect
on the cyber space, and they do not have the analog signal as well. For example- if the enemy
has distributed the denial attacks and it would raise the problem because of the no analog signals.
The military is using the cyber security at the time of the war for protecting our data and also to
track the enemy at every step. Due to tracking the military would track the strategies of the
enemy.
Defensive operations
The defensive cyber maneuver includes the cyber space action which are done in the
traditional manner and it would also build the secure network. The defensive operation is also
categorized in
Perimeter defense
In order to control the enemy the cyber maneuver is used and it would also create the
hard and the defensive to protect the interior systems in which the information is stored (Gioe
2016). The interior systems consist of the strategies and the information so these must have the
hard and strong interior systems which cannot be controlled by anyone. The information
protector must be offensive maneuver which would be protecting the information.
Through the use of the exploitive maneuver the military would capture the information of
the enemy and also gain the strategies of the enemies and as well. The information captured is
used against the enemy at the time of the war. Key information is used by the military and the
report are made for destroying the enemy.
Positional maneuver
In the positional maneuver the military would be using the physical nodes of the
information to follow the operations of the enemy. In order to control the enemy the cyber
operation would be arranged and the computers would capture all the logical nodes of the enemy
which would help us to follow the enemy and the strategies as well (Schmitt 2017).
Influencing maneuver
The cyber operation is used by the military for the taking any decisions about the enemy
at the time of the war. In the influencing power the enemy is influenced by the actions and also
the enemy would forcefully approve the decisions of the military or in the indirect way.
Kinetic maneuver operations are producing the similar effects which are giving the effect
on the cyber space, and they do not have the analog signal as well. For example- if the enemy
has distributed the denial attacks and it would raise the problem because of the no analog signals.
The military is using the cyber security at the time of the war for protecting our data and also to
track the enemy at every step. Due to tracking the military would track the strategies of the
enemy.
Defensive operations
The defensive cyber maneuver includes the cyber space action which are done in the
traditional manner and it would also build the secure network. The defensive operation is also
categorized in
Perimeter defense
In order to control the enemy the cyber maneuver is used and it would also create the
hard and the defensive to protect the interior systems in which the information is stored (Gioe
2016). The interior systems consist of the strategies and the information so these must have the
hard and strong interior systems which cannot be controlled by anyone. The information
protector must be offensive maneuver which would be protecting the information.

Deceptive defense
Deceptive defense is used by the attacker and also action of them would assist the
attacker to find the strategies and methods. It would also assist the defender to gain the initiative
and also the waste resources.
Moving target defense
In order to keep an eye on the enemy the target are moved easily in the defensive cyber
maneuver (Brantly, 2017). Cyber operations would include the technical methods for shifting the
targets systems. Through the help of these the manure the attacker is finds hard to trace the
target. The method is quote complex and also the attacker would find the problem. Moving the
target is only method which is quite similar to the traditional methods of the cyber space
maneuver. Due to use of the technology in the cyber operation the defensive techniques has also
been improved with the time and the technology.
Cyber operations in the modern environment
In the modern era the cyber operations are the part of the information warfare operations
and the information is controlled form the information environment. Cyber operations include
the mission area and the cyber operations include the defense mission and the cyber warfare
operations as well. It includes the intelligence and military operations and also cyber space
operations as well. Cyber warfare operations are the part of the cyber operations. In the offensive
or the defensive maneuver the cyber space would mark the target to attack. In the modern era the
cyber operations are handled through the electronic media and the computers systems.
Traditional methods of the maneuver include the target, facilities, equipment and the companies
which are supporting the conditions or would help in the situation. The military forces attack and
defend themselves form the attackers but in the cyber space operations the server farm is
destroyed and the and data in computers an or the soft wares is manipulated accordingly. Power
projects platforms and the weapons which would be used in the war are no physical assets, in the
cyber operation the capabilities and the technology is tested which would be protecting the
information of the customers.
Deceptive defense is used by the attacker and also action of them would assist the
attacker to find the strategies and methods. It would also assist the defender to gain the initiative
and also the waste resources.
Moving target defense
In order to keep an eye on the enemy the target are moved easily in the defensive cyber
maneuver (Brantly, 2017). Cyber operations would include the technical methods for shifting the
targets systems. Through the help of these the manure the attacker is finds hard to trace the
target. The method is quote complex and also the attacker would find the problem. Moving the
target is only method which is quite similar to the traditional methods of the cyber space
maneuver. Due to use of the technology in the cyber operation the defensive techniques has also
been improved with the time and the technology.
Cyber operations in the modern environment
In the modern era the cyber operations are the part of the information warfare operations
and the information is controlled form the information environment. Cyber operations include
the mission area and the cyber operations include the defense mission and the cyber warfare
operations as well. It includes the intelligence and military operations and also cyber space
operations as well. Cyber warfare operations are the part of the cyber operations. In the offensive
or the defensive maneuver the cyber space would mark the target to attack. In the modern era the
cyber operations are handled through the electronic media and the computers systems.
Traditional methods of the maneuver include the target, facilities, equipment and the companies
which are supporting the conditions or would help in the situation. The military forces attack and
defend themselves form the attackers but in the cyber space operations the server farm is
destroyed and the and data in computers an or the soft wares is manipulated accordingly. Power
projects platforms and the weapons which would be used in the war are no physical assets, in the
cyber operation the capabilities and the technology is tested which would be protecting the
information of the customers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

TASK 3
Understand principles in computer security from system perspectives.
Computer security is based on the process for maintaining protection which are affordable to
automated information system. in order to understand persevering objective that maintain
confidentiality, integrity and availability of data system resources (Bagyalakshmi and et.al.,
2018). There are common principles applicable in computer security from perspective for overall
network system. At the time of data transmission from source to destination which requires
proper security aspects for reducing risk of attack and threat within network.
It will be used the Discretionary access control procedures, which based on the determine
requestor and also access rules for stating different requestors. They must allow to protect
resources that used in the network protection.
It also set up the rules and practices which may specify proper regulation where how
overall system or business provide security services of their network system. in this way,
it can easily protect sensitive information and system resources in proper manner.
A protection due to violation in terms of security, it exits when there are some different
circumstances, action, capability and event that could occurs data breach. In this way, it is
becoming possible to hold all security concept in term of privacy and security.
Packet analysis
Wireshark is based on the network analysis platform or tool which easily captured packet
in real time and also display them of readable format for human being (Jawaharan, Mohan and
Gurusamy, 2018). This type of tool is mainly including colour coding, filters and other type of
features that can identify the depth network traffic. It is best process for inspection of individual
packets.
Understand principles in computer security from system perspectives.
Computer security is based on the process for maintaining protection which are affordable to
automated information system. in order to understand persevering objective that maintain
confidentiality, integrity and availability of data system resources (Bagyalakshmi and et.al.,
2018). There are common principles applicable in computer security from perspective for overall
network system. At the time of data transmission from source to destination which requires
proper security aspects for reducing risk of attack and threat within network.
It will be used the Discretionary access control procedures, which based on the determine
requestor and also access rules for stating different requestors. They must allow to protect
resources that used in the network protection.
It also set up the rules and practices which may specify proper regulation where how
overall system or business provide security services of their network system. in this way,
it can easily protect sensitive information and system resources in proper manner.
A protection due to violation in terms of security, it exits when there are some different
circumstances, action, capability and event that could occurs data breach. In this way, it is
becoming possible to hold all security concept in term of privacy and security.
Packet analysis
Wireshark is based on the network analysis platform or tool which easily captured packet
in real time and also display them of readable format for human being (Jawaharan, Mohan and
Gurusamy, 2018). This type of tool is mainly including colour coding, filters and other type of
features that can identify the depth network traffic. It is best process for inspection of individual
packets.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
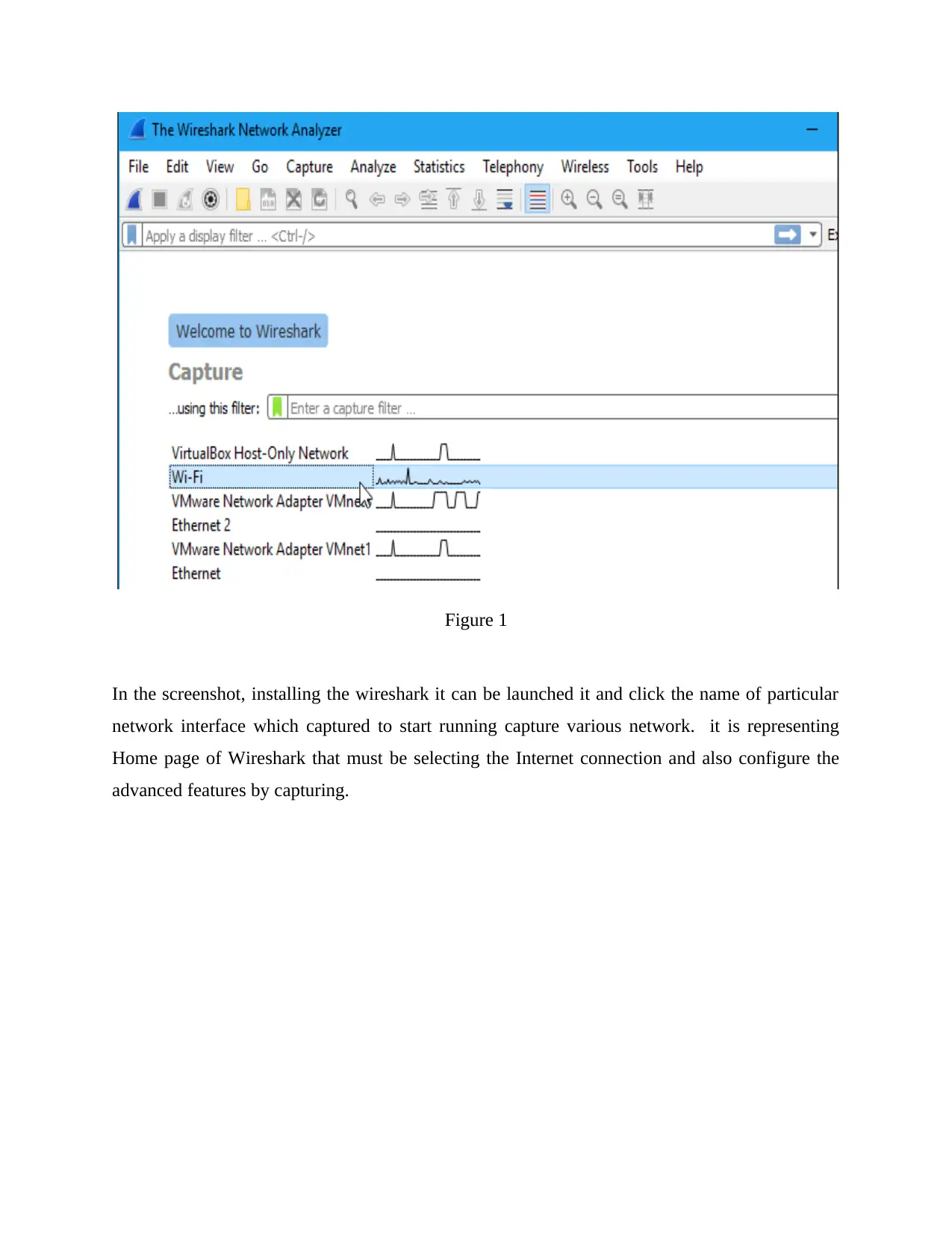
Figure 1
In the screenshot, installing the wireshark it can be launched it and click the name of particular
network interface which captured to start running capture various network. it is representing
Home page of Wireshark that must be selecting the Internet connection and also configure the
advanced features by capturing.
In the screenshot, installing the wireshark it can be launched it and click the name of particular
network interface which captured to start running capture various network. it is representing
Home page of Wireshark that must be selecting the Internet connection and also configure the
advanced features by capturing.
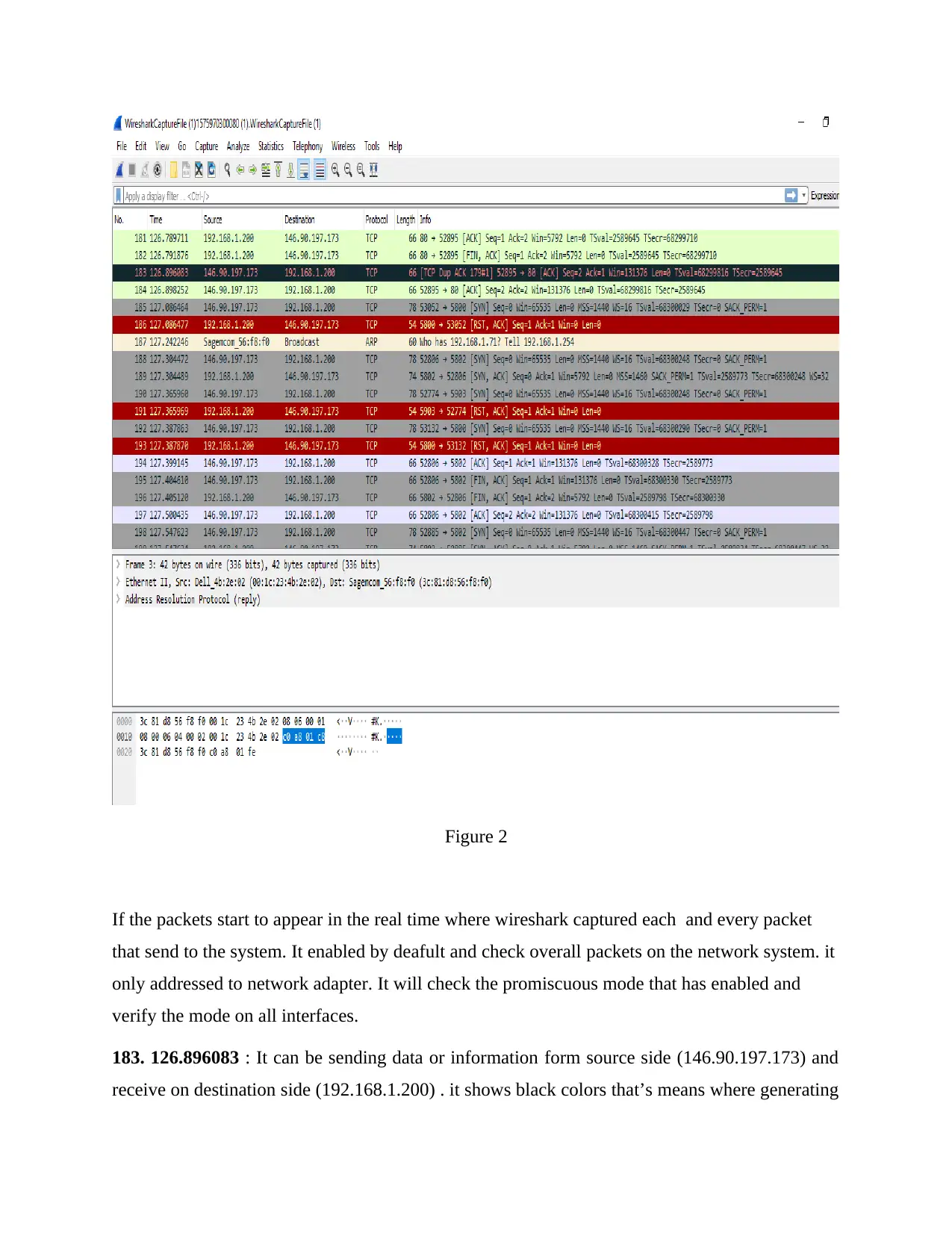
Figure 2
If the packets start to appear in the real time where wireshark captured each and every packet
that send to the system. It enabled by deafult and check overall packets on the network system. it
only addressed to network adapter. It will check the promiscuous mode that has enabled and
verify the mode on all interfaces.
183. 126.896083 : It can be sending data or information form source side (146.90.197.173) and
receive on destination side (192.168.1.200) . it shows black colors that’s means where generating
If the packets start to appear in the real time where wireshark captured each and every packet
that send to the system. It enabled by deafult and check overall packets on the network system. it
only addressed to network adapter. It will check the promiscuous mode that has enabled and
verify the mode on all interfaces.
183. 126.896083 : It can be sending data or information form source side (146.90.197.173) and
receive on destination side (192.168.1.200) . it shows black colors that’s means where generating
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

errors during data transmission and cannot be received in accurate destination. In this way, it can
be concluded that it could have been delivered out of order. On the other hand, it also
representing the red colour which means that generate threat due to attack in network system.
186.127.08644 : It has to be sending data from source to destination so as determine in network
packet analysis. Source is (192.168.1.200) and destination is (146.90.197.173). it mainly uses for
identifying the overall errors during data transmission. It has a chances of data loss within
network system.
Color coding:
After analysing, it can be found that there are large number of data packet transferred within
one network. it also highlighted in the different color format. Wireshark is mainly used the color
that help for identidying traffic type (Bock, 2019). By defualt the Purple color is represents TCP
traffic and blue color shows UBP traffic. On the other hand, black idetifies packet with errors.
Red color: It is mainly representing threat of network system during data transmission
from source to destination.
Dark blue color: it is mainly representing the DNS traffic. If it will show that colors
means data traffic increases in siganl tranmission.
Lighcolor: it is representing the UDP traffic where becoming tought for managing traffic
devel of UDP in data traffic within network system.
Black Color: it can be represented as an error in the data tranmission where singals has
not be reached to their destination (Bhandari and et.al., 2018).
be concluded that it could have been delivered out of order. On the other hand, it also
representing the red colour which means that generate threat due to attack in network system.
186.127.08644 : It has to be sending data from source to destination so as determine in network
packet analysis. Source is (192.168.1.200) and destination is (146.90.197.173). it mainly uses for
identifying the overall errors during data transmission. It has a chances of data loss within
network system.
Color coding:
After analysing, it can be found that there are large number of data packet transferred within
one network. it also highlighted in the different color format. Wireshark is mainly used the color
that help for identidying traffic type (Bock, 2019). By defualt the Purple color is represents TCP
traffic and blue color shows UBP traffic. On the other hand, black idetifies packet with errors.
Red color: It is mainly representing threat of network system during data transmission
from source to destination.
Dark blue color: it is mainly representing the DNS traffic. If it will show that colors
means data traffic increases in siganl tranmission.
Lighcolor: it is representing the UDP traffic where becoming tought for managing traffic
devel of UDP in data traffic within network system.
Black Color: it can be represented as an error in the data tranmission where singals has
not be reached to their destination (Bhandari and et.al., 2018).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Attack explanation
Wireshark software is mainly captured the network traffic and also displayed colour coded
chart as per traffic. It also making it become convenient for administrator to easily identify or
detect network attacks. If there will be used to determine hacking attempts on the network
system. there will be examining the colour coded result or outcomes (Holkovič, Ryšavý and
Dudek, 2019). As per capture analysis, Red color shows that must indicate the required for
immediate attention otherwise it will generate threat to network system. it also investigates about
the potential threat of system by using Wireshark tool.
In above Figure-2, it can be identified that red color shows because of threat and sometimes,
it may indicate Denial of service attacks and other hacking activities occurred. DoS attacks are
the most problematic situation because its servers from IP addresses, causes of overall server
performance which directly hits entire server. It will get chances of crashes.
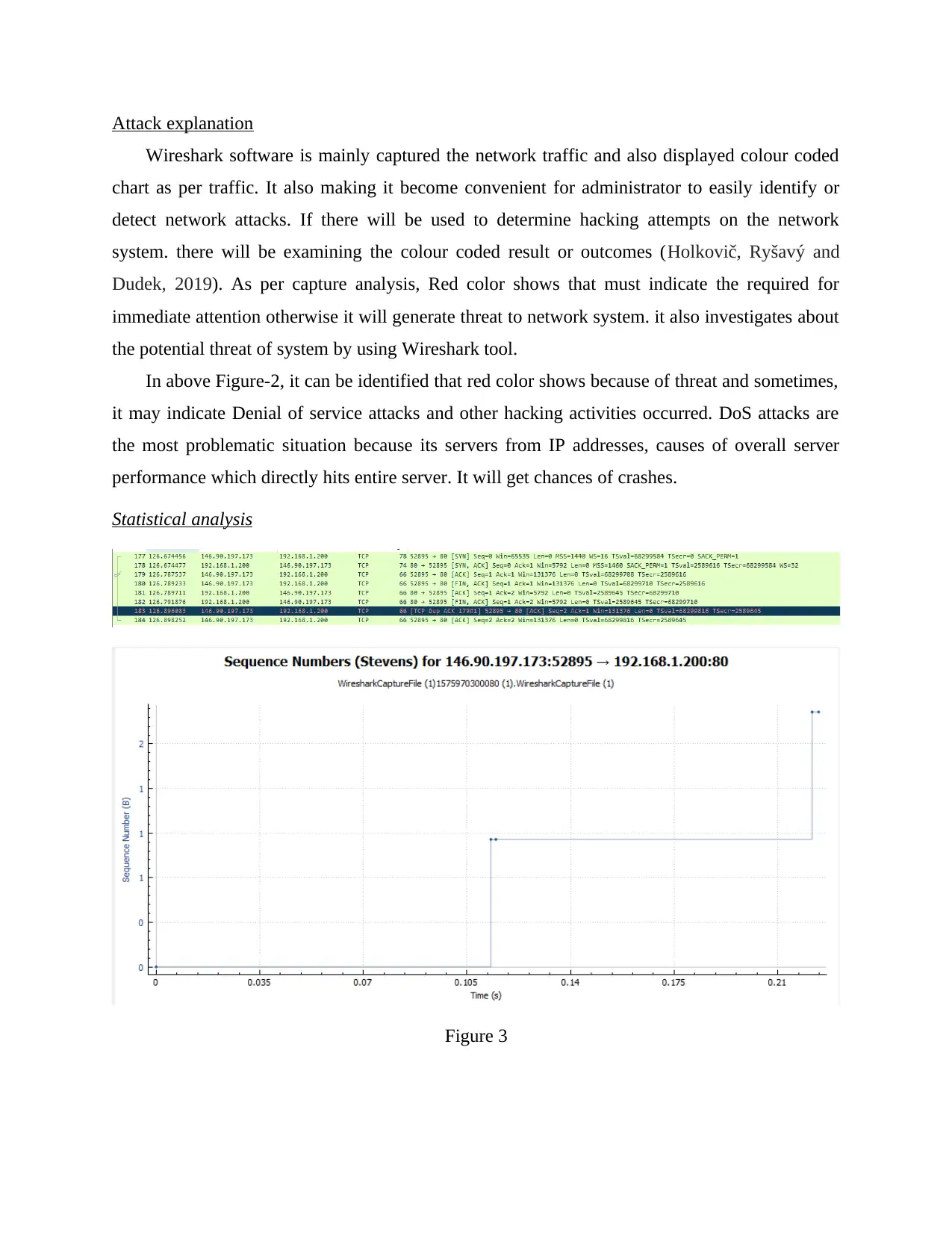
Statistical analysis
Figure 3
Wireshark software is mainly captured the network traffic and also displayed colour coded
chart as per traffic. It also making it become convenient for administrator to easily identify or
detect network attacks. If there will be used to determine hacking attempts on the network
system. there will be examining the colour coded result or outcomes (Holkovič, Ryšavý and
Dudek, 2019). As per capture analysis, Red color shows that must indicate the required for
immediate attention otherwise it will generate threat to network system. it also investigates about
the potential threat of system by using Wireshark tool.
In above Figure-2, it can be identified that red color shows because of threat and sometimes,
it may indicate Denial of service attacks and other hacking activities occurred. DoS attacks are
the most problematic situation because its servers from IP addresses, causes of overall server
performance which directly hits entire server. It will get chances of crashes.
Statistical analysis
Figure 3
In this graph, it mainly shows sequence number graph where packet will receive from sources
and increasing sequence number but cannot reached to the actual destination. At initial level, the
sequence number remain constant from time interval 0.0105 and after it will increase size of
number. This process will continue running but not reached to their destination.
Sequence Number: 146.90.197.173.52895 -> 192.168.1.200:80
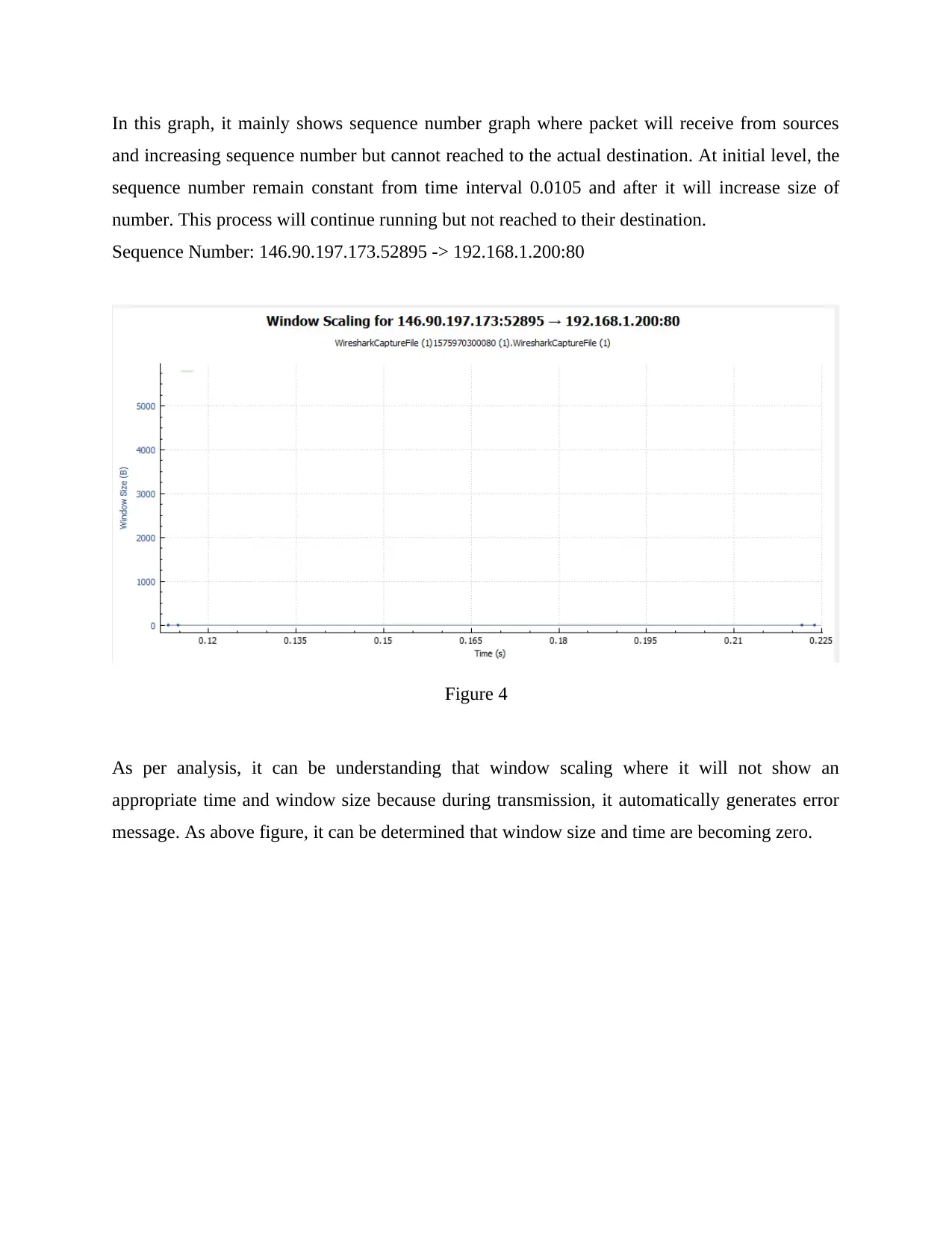
Figure 4
As per analysis, it can be understanding that window scaling where it will not show an
appropriate time and window size because during transmission, it automatically generates error
message. As above figure, it can be determined that window size and time are becoming zero.
and increasing sequence number but cannot reached to the actual destination. At initial level, the
sequence number remain constant from time interval 0.0105 and after it will increase size of
number. This process will continue running but not reached to their destination.
Sequence Number: 146.90.197.173.52895 -> 192.168.1.200:80
Figure 4
As per analysis, it can be understanding that window scaling where it will not show an
appropriate time and window size because during transmission, it automatically generates error
message. As above figure, it can be determined that window size and time are becoming zero.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





