Cyber Security Threats Landscape
VerifiedAdded on 2020/04/01
|15
|3318
|119
AI Summary
This assignment requires you to delve into the evolving landscape of cybersecurity threats. You'll examine various threat categories, understand the motivations behind cyberattacks, analyze their potential impacts on individuals and organizations, and propose effective mitigation strategies. The analysis should draw upon relevant research papers and industry reports provided.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CHALLENGES FOR CYBER SECURITY IN BUSINESSES
Name
Institutional Affiliation
Date
1
Name
Institutional Affiliation
Date
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

CHALLENGES FOR CYBER SECURITY IN BUSINESSES
EXECUTIVE SUMMARY
This is a report on the research of the topic “challenges affecting cyber security in business
organizations in Australia”. The report gives instructions about how the research was carried out
and the findings. It contains ten main sections which are: the introduction part, project objective,
project scope section, literature review section, the research questions section, research design
and methodology part, research limitations section, research plan section, conclusion part and
lastly the reference section. Every section of the report has important details about the report to
indicate its progress.
2
EXECUTIVE SUMMARY
This is a report on the research of the topic “challenges affecting cyber security in business
organizations in Australia”. The report gives instructions about how the research was carried out
and the findings. It contains ten main sections which are: the introduction part, project objective,
project scope section, literature review section, the research questions section, research design
and methodology part, research limitations section, research plan section, conclusion part and
lastly the reference section. Every section of the report has important details about the report to
indicate its progress.
2

Table of Contents
INTRODUCTION.....................................................................................................................................1
RESEARCH AIM AND OBJECTIVE....................................................................................................2
PROJECT SCOPE....................................................................................................................................2
RESEARCH JUSTIFICATION...............................................................................................................2
LITERATURE REVIEW.........................................................................................................................3
Types of Cyber security Risks..............................................................................................................3
Cyber Thefts........................................................................................................................................3
Cyber Espionage..................................................................................................................................4
Internet of Things................................................................................................................................4
RESEARCH QUESTIONS AND HYPOTHESIS...................................................................................5
Primary Question..................................................................................................................................5
Secondary Question...............................................................................................................................5
RESEARCH DESIGN AND METHODOLOGY....................................................................................5
Qualitative Research Method...............................................................................................................5
Research Method Validity....................................................................................................................6
Sampling method...................................................................................................................................6
Data Collection Method........................................................................................................................6
RESEARCH LIMITATIONS...................................................................................................................6
RESEARCH PLAN...................................................................................................................................7
CONCLUSION..........................................................................................................................................7
REFERENCES..........................................................................................................................................8
3
INTRODUCTION.....................................................................................................................................1
RESEARCH AIM AND OBJECTIVE....................................................................................................2
PROJECT SCOPE....................................................................................................................................2
RESEARCH JUSTIFICATION...............................................................................................................2
LITERATURE REVIEW.........................................................................................................................3
Types of Cyber security Risks..............................................................................................................3
Cyber Thefts........................................................................................................................................3
Cyber Espionage..................................................................................................................................4
Internet of Things................................................................................................................................4
RESEARCH QUESTIONS AND HYPOTHESIS...................................................................................5
Primary Question..................................................................................................................................5
Secondary Question...............................................................................................................................5
RESEARCH DESIGN AND METHODOLOGY....................................................................................5
Qualitative Research Method...............................................................................................................5
Research Method Validity....................................................................................................................6
Sampling method...................................................................................................................................6
Data Collection Method........................................................................................................................6
RESEARCH LIMITATIONS...................................................................................................................6
RESEARCH PLAN...................................................................................................................................7
CONCLUSION..........................................................................................................................................7
REFERENCES..........................................................................................................................................8
3

INTRODUCTION
Cyber security is a technological process and practices that is designed to protect computers and
its components from theft or damage. It is responsible for protecting the computers software and
hardware devices, computer networks and programs as well as computer data from being
damaged by unauthorized personnel. Therefore, cyber security are the measures that are
implemented with the aim of protecting computer data and components (Choo, 2014). Over the
last decades, business organizations have been depending highly on computers and technology to
conduct their operations. A large number of businesses are now using computers and other
technological improved equipment to carry out their operations on finances, administering,
procurement and purchases, sales and marketing to name a few (Kostyuk, 2014). However, over
the recent years, there has been an increase in cyber security breach and attack. This has led to
theft and damage of business information and any data that is stored in the computer software.
The main types of breaches or attacks include theft, unauthorized access to data and compromise
of the organizational data with an aim of selling the information to competitors, destroying or
damaging the businesses image, gaining a leverage for the business and for some people just fun
to breach cyber security.
RESEARCHAIM AND OBJECTIVE
Aim
The project’s main aim was to identify and analyze some of the common cyber security
challenges for businesses in Australia.
Objective
The main objective of the project was to discuss and evaluate the common cyber securities that
challenge business organizations in Australia
PROJECT SCOPE
The research was stated to only address the cyber security challenges affecting businesses in
Australia. The research was limited to include the business organizations that have used the
modern technology for many years, e.g. computers to store data and carry out most of their
4
Cyber security is a technological process and practices that is designed to protect computers and
its components from theft or damage. It is responsible for protecting the computers software and
hardware devices, computer networks and programs as well as computer data from being
damaged by unauthorized personnel. Therefore, cyber security are the measures that are
implemented with the aim of protecting computer data and components (Choo, 2014). Over the
last decades, business organizations have been depending highly on computers and technology to
conduct their operations. A large number of businesses are now using computers and other
technological improved equipment to carry out their operations on finances, administering,
procurement and purchases, sales and marketing to name a few (Kostyuk, 2014). However, over
the recent years, there has been an increase in cyber security breach and attack. This has led to
theft and damage of business information and any data that is stored in the computer software.
The main types of breaches or attacks include theft, unauthorized access to data and compromise
of the organizational data with an aim of selling the information to competitors, destroying or
damaging the businesses image, gaining a leverage for the business and for some people just fun
to breach cyber security.
RESEARCHAIM AND OBJECTIVE
Aim
The project’s main aim was to identify and analyze some of the common cyber security
challenges for businesses in Australia.
Objective
The main objective of the project was to discuss and evaluate the common cyber securities that
challenge business organizations in Australia
PROJECT SCOPE
The research was stated to only address the cyber security challenges affecting businesses in
Australia. The research was limited to include the business organizations that have used the
modern technology for many years, e.g. computers to store data and carry out most of their
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

business operations. This therefore relates to businesses like financial institutions (banks),
insurance companies and software developing businesses.
RESEARCH JUSTIFICATION
Cyber security threats and challenges are increasing with technology development and
improvement. On the other hand, technology around the world improves or advances on a daily
basis hence increasing and strengthening the world’s connection. This means an increase in
cyber breach and attacks which depend on the technology advancement (Babate et al, 2014).
Therefore, Cyber security can only be possible if the measures and the practices are modernized
and effective. In that case, this research is actually important to conduct. Through the research,
business organizations around Australia were able to identify and understand some of the most
cyber security threats that may occur during their business operations (Sen et al, 2013). In
addition to that, the businesses were able to acquire some professional advice on how such
threats can be avoided and prevented in case they have not experienced them. In the end, the
businesses got the opportunity to understand different methods of protecting their computer
appliances, software and hardware devices and any other information stored in such appliances.
Therefore, the research was certainly able produce some very crucial information about cyber
security in a business, types of cyber security breaches and attacks and methods of ensuring
strong cyber security for businesses. This research was extremely useful for business
organizations that were already facing some of the challenges. Or those that anticipated for such
threats.
LITERATURE REVIEW
Over the last decades, a large number of business organizations has been using the internet to
conduct most of their business operations- especially the international businesses. However, this
is common and popular in most developed countries than those that are developed (Elmaghraby
and Losavio, 2014). These businesses conducting their operations (marketing activities, sales
activities, advertising, procurement options, investment activities to name a few) by use of the
internet. Additionally, organizations have stored and displayed information about their
development and growth in the internet. The internet is a world-wide-web platform that offers a
good chance for businesses to use the computers and their software and hardware systems which
has proved to be a very effective and efficient way to conduct business operations (Losavio et al,
5
insurance companies and software developing businesses.
RESEARCH JUSTIFICATION
Cyber security threats and challenges are increasing with technology development and
improvement. On the other hand, technology around the world improves or advances on a daily
basis hence increasing and strengthening the world’s connection. This means an increase in
cyber breach and attacks which depend on the technology advancement (Babate et al, 2014).
Therefore, Cyber security can only be possible if the measures and the practices are modernized
and effective. In that case, this research is actually important to conduct. Through the research,
business organizations around Australia were able to identify and understand some of the most
cyber security threats that may occur during their business operations (Sen et al, 2013). In
addition to that, the businesses were able to acquire some professional advice on how such
threats can be avoided and prevented in case they have not experienced them. In the end, the
businesses got the opportunity to understand different methods of protecting their computer
appliances, software and hardware devices and any other information stored in such appliances.
Therefore, the research was certainly able produce some very crucial information about cyber
security in a business, types of cyber security breaches and attacks and methods of ensuring
strong cyber security for businesses. This research was extremely useful for business
organizations that were already facing some of the challenges. Or those that anticipated for such
threats.
LITERATURE REVIEW
Over the last decades, a large number of business organizations has been using the internet to
conduct most of their business operations- especially the international businesses. However, this
is common and popular in most developed countries than those that are developed (Elmaghraby
and Losavio, 2014). These businesses conducting their operations (marketing activities, sales
activities, advertising, procurement options, investment activities to name a few) by use of the
internet. Additionally, organizations have stored and displayed information about their
development and growth in the internet. The internet is a world-wide-web platform that offers a
good chance for businesses to use the computers and their software and hardware systems which
has proved to be a very effective and efficient way to conduct business operations (Losavio et al,
5

2015). Therefore, this being the main reason why business cyber security has received increased
threat levels, it has become more challenging to prevent or avoid these threats (Djambazova et al,
2011). Nowadays, the cyber security hacking experts have proven to be more sophisticated and
confident about what they do. It has been proven that the cyber security threats an espionage
attacks are increasing day in day out.
Types of Cyber security Risks
Cyber Thefts
Cyber thefts revolves around the stealing of organization information, especially financial
information. This is an act that a good number of business have been facing since computers or
internet started being used to conduct business operations. In most case, financial information is
stolen from companies that have stored their financial information in the electronic financial
system, especially in very large financial companies located in developed countries. The cyber
hackers get the chance acquire the information even when it is protected. On the other hand,
financial information is common with people who use credit or debit card for shopping or storing
their finances (Manley, 2015). When these cards are stolen, they are sold or used in the black
market which is recently a well-established and growing market for the cyber security hackers
and thieves. Additionally, businesses have recently been using online mobile payments or online
electronic money transfers and financial saving. This method offers new opportunity for the
cyber security hackers to access the accounts and steal the funds (Pramanik, 2013). Apparently,
many case have been reported especially by a large number of medium sized businesses that are
trying to keep with technology advancement but fail to secure their financial data effectively.
Cyber Espionage
This relates to the use of computers and the internet to access confidential information- illegally.
This is a practice that is becoming very common between governments, business organizations
(rivals or competitors), individuals, political groups and movements among others. Cyber
espionage is currently being used by many business organizations to acquire unauthorized
information which most of them aim to use for blackmail or to benefit themselves. In other
words, cyber espionage has become a better choice for businesses to undermine their rivals and
gain competitive advantage (Ijaz et al, 2016). Through cyber espionage, businesses can steal
6
threat levels, it has become more challenging to prevent or avoid these threats (Djambazova et al,
2011). Nowadays, the cyber security hacking experts have proven to be more sophisticated and
confident about what they do. It has been proven that the cyber security threats an espionage
attacks are increasing day in day out.
Types of Cyber security Risks
Cyber Thefts
Cyber thefts revolves around the stealing of organization information, especially financial
information. This is an act that a good number of business have been facing since computers or
internet started being used to conduct business operations. In most case, financial information is
stolen from companies that have stored their financial information in the electronic financial
system, especially in very large financial companies located in developed countries. The cyber
hackers get the chance acquire the information even when it is protected. On the other hand,
financial information is common with people who use credit or debit card for shopping or storing
their finances (Manley, 2015). When these cards are stolen, they are sold or used in the black
market which is recently a well-established and growing market for the cyber security hackers
and thieves. Additionally, businesses have recently been using online mobile payments or online
electronic money transfers and financial saving. This method offers new opportunity for the
cyber security hackers to access the accounts and steal the funds (Pramanik, 2013). Apparently,
many case have been reported especially by a large number of medium sized businesses that are
trying to keep with technology advancement but fail to secure their financial data effectively.
Cyber Espionage
This relates to the use of computers and the internet to access confidential information- illegally.
This is a practice that is becoming very common between governments, business organizations
(rivals or competitors), individuals, political groups and movements among others. Cyber
espionage is currently being used by many business organizations to acquire unauthorized
information which most of them aim to use for blackmail or to benefit themselves. In other
words, cyber espionage has become a better choice for businesses to undermine their rivals and
gain competitive advantage (Ijaz et al, 2016). Through cyber espionage, businesses can steal
6

funds, employee details, management details, management strategies information among other
things that should be secret in a business organization.
Internet of Things
As the technology improves, the internet capability and effectiveness increases. Modern
revolution has brought about the revolution of internet and its enablement towards devices.
Basically, it refers to the connection of physical electronic appliances that may need the internet
to access, e.g. cars and other home appliances (Pramanik, 2013). In addition to that, as far as the
interconnectivity of devices increases, the internet network will always offer opportunity for
businesses to access confidential information from each other (Abomhara, 2015). Therefore, this
means that businesses are now able to access the internet whenever they need it to conduct their
operations. For instance, the cars that transport funds from bank to another are connected with
the bank by the internet. This indicates a risk for these appliances to be compromised and be
misled or stolen. However, the IoT is facing serious risks, e.g. attacks. The products and
information in the IoT can be found by unauthorized persons and be stolen. This means that it is
not really a secure place or platform for businesses to be involved with.
Malware and Vectors Risks
Cyber criminals have now upgrades their techniques by attacking the internet and computer with
vectors that restrict access and usage of these devices, e.g. the malware. The malware is a
software that is designed to allow unauthorized access to the internet or other software
devices/appliances. It can be categorized into different categories, ransomware, viruses, worms,
spyware and Trojans (Mallinder and Drabwell, 2014). A ransomware is a malicious program that
interrupts an individual’s internet access and demand for payment for access to be granted
(Creeger, 2010). A virus is a form of code that is designed to cause damage to a computer
software appliance or internet and multiplies whenever the appliance is opened. Worms are used
to detect and search for weaknesses in computers and the internet. Attack vectors include
practices like social engineering, phishing, pharming and drive-by (Babate et al, 2014). They are
all meant to cause harm and destruction to a computer and internet operational processes.
Other types of risks and challenges include: computer sabotage, insider threats, insecure
passwords, tampering and clickjacking.
7
things that should be secret in a business organization.
Internet of Things
As the technology improves, the internet capability and effectiveness increases. Modern
revolution has brought about the revolution of internet and its enablement towards devices.
Basically, it refers to the connection of physical electronic appliances that may need the internet
to access, e.g. cars and other home appliances (Pramanik, 2013). In addition to that, as far as the
interconnectivity of devices increases, the internet network will always offer opportunity for
businesses to access confidential information from each other (Abomhara, 2015). Therefore, this
means that businesses are now able to access the internet whenever they need it to conduct their
operations. For instance, the cars that transport funds from bank to another are connected with
the bank by the internet. This indicates a risk for these appliances to be compromised and be
misled or stolen. However, the IoT is facing serious risks, e.g. attacks. The products and
information in the IoT can be found by unauthorized persons and be stolen. This means that it is
not really a secure place or platform for businesses to be involved with.
Malware and Vectors Risks
Cyber criminals have now upgrades their techniques by attacking the internet and computer with
vectors that restrict access and usage of these devices, e.g. the malware. The malware is a
software that is designed to allow unauthorized access to the internet or other software
devices/appliances. It can be categorized into different categories, ransomware, viruses, worms,
spyware and Trojans (Mallinder and Drabwell, 2014). A ransomware is a malicious program that
interrupts an individual’s internet access and demand for payment for access to be granted
(Creeger, 2010). A virus is a form of code that is designed to cause damage to a computer
software appliance or internet and multiplies whenever the appliance is opened. Worms are used
to detect and search for weaknesses in computers and the internet. Attack vectors include
practices like social engineering, phishing, pharming and drive-by (Babate et al, 2014). They are
all meant to cause harm and destruction to a computer and internet operational processes.
Other types of risks and challenges include: computer sabotage, insider threats, insecure
passwords, tampering and clickjacking.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RESEARCH QUESTIONS AND HYPOTHESIS
Primary Question
Which are the most common cyber security challenges or threats that are facing business
organizations over the last few years?
Secondary Question
What are some of the impacts on business organizations caused by cyber security risks and
challenges?
What solutions that can be implemented to avoid or prevent cyber security challenges for
businesses?
RESEARCH DESIGN AND METHODOLOGY
Qualitative Research Method
This method is used to focus on a wide range of educational areas that uses unstructured data
collection methods like observations, interviews and surveys. The research method tries to help
the researcher understand the meaning of theories of life (Hurt and McLaughlin, 2012). This
means that the method is used to create and build reasonable and realistic relationship and
understanding between the research and researcher. This method played an important role in in
ensuring the completion of the research. The steps that were used in deciding on the qualitative
method are (Chenail, 2011 and Chenail et al, 2014)): the research questions were carefully
analyzed, the literature review was evaluated and much consideration put on it, the sample size
was also carefully considered and then the decision on the method was made.
Research Method Validity
The method is valid for this research because of the fact that the research only tries to understand
the theoretical background on the challenges facing business organization as a result of cyber
security. These challenges can certainly not be measured therefore quantitative research
methodology is not valid or relevant for this research. Qualitative methodology can only help
understand the factual aspects of life like emotions, theories and other aspects that are not
quantitative.
8
Primary Question
Which are the most common cyber security challenges or threats that are facing business
organizations over the last few years?
Secondary Question
What are some of the impacts on business organizations caused by cyber security risks and
challenges?
What solutions that can be implemented to avoid or prevent cyber security challenges for
businesses?
RESEARCH DESIGN AND METHODOLOGY
Qualitative Research Method
This method is used to focus on a wide range of educational areas that uses unstructured data
collection methods like observations, interviews and surveys. The research method tries to help
the researcher understand the meaning of theories of life (Hurt and McLaughlin, 2012). This
means that the method is used to create and build reasonable and realistic relationship and
understanding between the research and researcher. This method played an important role in in
ensuring the completion of the research. The steps that were used in deciding on the qualitative
method are (Chenail, 2011 and Chenail et al, 2014)): the research questions were carefully
analyzed, the literature review was evaluated and much consideration put on it, the sample size
was also carefully considered and then the decision on the method was made.
Research Method Validity
The method is valid for this research because of the fact that the research only tries to understand
the theoretical background on the challenges facing business organization as a result of cyber
security. These challenges can certainly not be measured therefore quantitative research
methodology is not valid or relevant for this research. Qualitative methodology can only help
understand the factual aspects of life like emotions, theories and other aspects that are not
quantitative.
8

Sampling method
Random sampling method was to be used to determine the type of respondents. The businesses
that were prone to the use of cyber security to conduct their business operations were grouped
together and specific organizations picked randomly. However, the businesses were only those
that were currently using cyber security, those that had experience in using cyber security and
those that were planning to start using the cyber security processes. Additionally, the businesses
included just those that were located in Australia. This was the criteria that ended up determining
the sample size.
Data Collection Method
The research data was collected by use of questionnaires, interviews and physical observation.
The questionnaires contained unstructured questions whereby each respondent had the
opportunity to answer the questions in whatever method they would like.
RESEARCH LIMITATIONS
In every research there are some limitations that hinder the research from being complete or
completely successful. The following are some of the limitations that were involved during the
research process:
Lack of funds. During the research, the researchers were supposed to travel to different cities and
towns to observe certain specific businesses as they used cyber security to conduct business
operations. Due to this, the cost of the research was too much.
Failure of the respondents to cooperate and reply the questions on the questionnaire.
Respondents failed to give their answers correctly which led to misleading data and information
in the end
Some businesses were not ready to share some of their common challenges. Some of them
wanted their challenges and problems to stay secret and hidden because of the fear of it being
shared with the organization’s rivals or competitors.
9
Random sampling method was to be used to determine the type of respondents. The businesses
that were prone to the use of cyber security to conduct their business operations were grouped
together and specific organizations picked randomly. However, the businesses were only those
that were currently using cyber security, those that had experience in using cyber security and
those that were planning to start using the cyber security processes. Additionally, the businesses
included just those that were located in Australia. This was the criteria that ended up determining
the sample size.
Data Collection Method
The research data was collected by use of questionnaires, interviews and physical observation.
The questionnaires contained unstructured questions whereby each respondent had the
opportunity to answer the questions in whatever method they would like.
RESEARCH LIMITATIONS
In every research there are some limitations that hinder the research from being complete or
completely successful. The following are some of the limitations that were involved during the
research process:
Lack of funds. During the research, the researchers were supposed to travel to different cities and
towns to observe certain specific businesses as they used cyber security to conduct business
operations. Due to this, the cost of the research was too much.
Failure of the respondents to cooperate and reply the questions on the questionnaire.
Respondents failed to give their answers correctly which led to misleading data and information
in the end
Some businesses were not ready to share some of their common challenges. Some of them
wanted their challenges and problems to stay secret and hidden because of the fear of it being
shared with the organization’s rivals or competitors.
9

RESEARCH PLAN
Process of deciding on the topic for research-1st week of January 2017
Research topic introduction- 2nd week of January 2017
Research topic justification and research objectives- 3rd and 4th week of January 2017
Literature review- 1st to 3rd week of February 2017
Research methodology- 4th week February 2017 and 1st week March 2017
Data collection and data analysis- 2nd and 3rd week of March 2017
Research limitations and conclusion- 4th week of March 2017
10
Process of deciding on the topic for research-1st week of January 2017
Research topic introduction- 2nd week of January 2017
Research topic justification and research objectives- 3rd and 4th week of January 2017
Literature review- 1st to 3rd week of February 2017
Research methodology- 4th week February 2017 and 1st week March 2017
Data collection and data analysis- 2nd and 3rd week of March 2017
Research limitations and conclusion- 4th week of March 2017
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
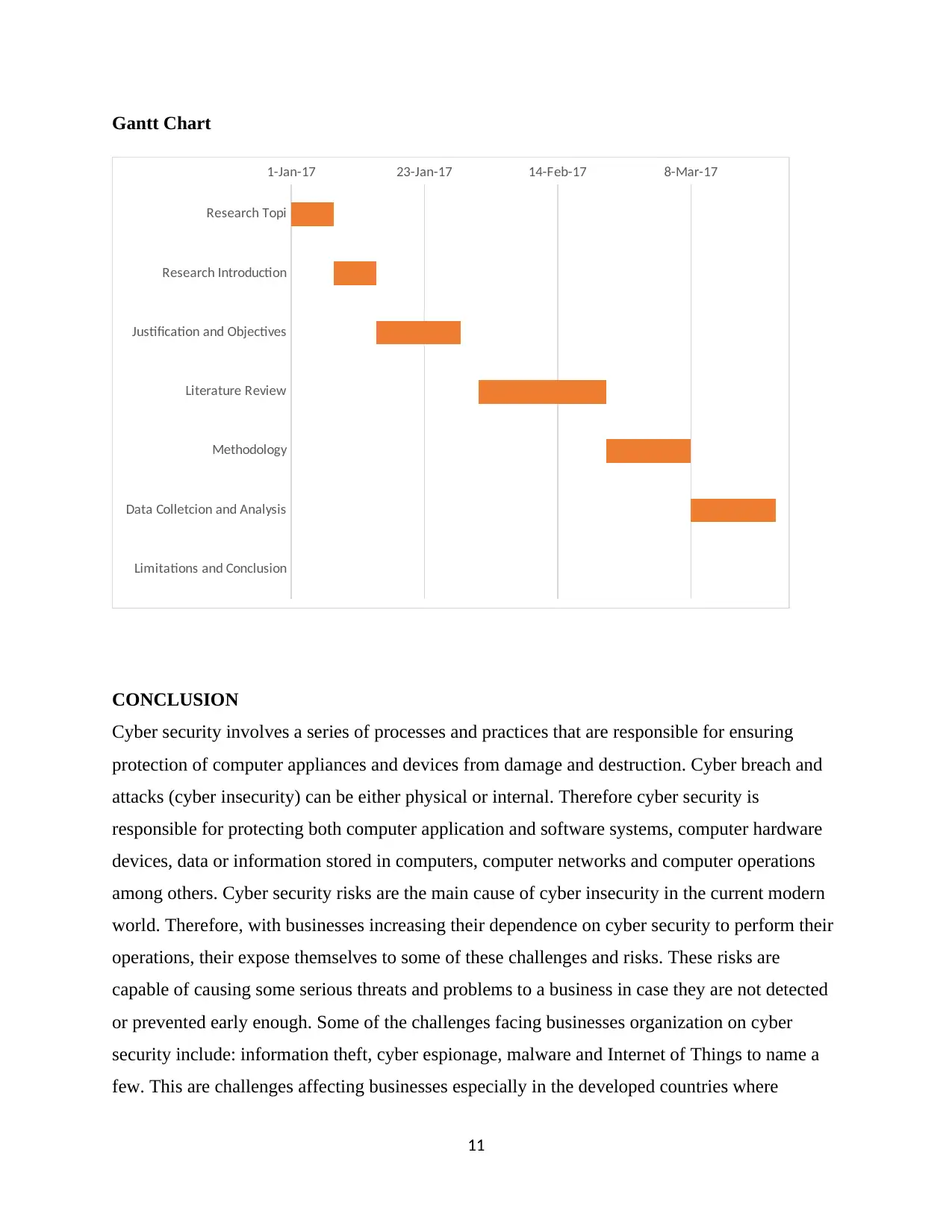
Gantt Chart
Research Topi
Research Introduction
Justification and Objectives
Literature Review
Methodology
Data Colletcion and Analysis
Limitations and Conclusion
1-Jan-17 23-Jan-17 14-Feb-17 8-Mar-17
CONCLUSION
Cyber security involves a series of processes and practices that are responsible for ensuring
protection of computer appliances and devices from damage and destruction. Cyber breach and
attacks (cyber insecurity) can be either physical or internal. Therefore cyber security is
responsible for protecting both computer application and software systems, computer hardware
devices, data or information stored in computers, computer networks and computer operations
among others. Cyber security risks are the main cause of cyber insecurity in the current modern
world. Therefore, with businesses increasing their dependence on cyber security to perform their
operations, their expose themselves to some of these challenges and risks. These risks are
capable of causing some serious threats and problems to a business in case they are not detected
or prevented early enough. Some of the challenges facing businesses organization on cyber
security include: information theft, cyber espionage, malware and Internet of Things to name a
few. This are challenges affecting businesses especially in the developed countries where
11
Research Topi
Research Introduction
Justification and Objectives
Literature Review
Methodology
Data Colletcion and Analysis
Limitations and Conclusion
1-Jan-17 23-Jan-17 14-Feb-17 8-Mar-17
CONCLUSION
Cyber security involves a series of processes and practices that are responsible for ensuring
protection of computer appliances and devices from damage and destruction. Cyber breach and
attacks (cyber insecurity) can be either physical or internal. Therefore cyber security is
responsible for protecting both computer application and software systems, computer hardware
devices, data or information stored in computers, computer networks and computer operations
among others. Cyber security risks are the main cause of cyber insecurity in the current modern
world. Therefore, with businesses increasing their dependence on cyber security to perform their
operations, their expose themselves to some of these challenges and risks. These risks are
capable of causing some serious threats and problems to a business in case they are not detected
or prevented early enough. Some of the challenges facing businesses organization on cyber
security include: information theft, cyber espionage, malware and Internet of Things to name a
few. This are challenges affecting businesses especially in the developed countries where
11
information technology improvement and development is very high, e.g. Australia. Therefore, it
is important for businesses to understand and analyze any cyber security need and use to ensure
that no threats and problems that accompany its use.
12
is important for businesses to understand and analyze any cyber security need and use to ensure
that no threats and problems that accompany its use.
12

13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Almadhoob, A. and Valverde, R., 2014. Cybercrime prevention in the kingdom of Bahrain via IT
security audit plans. Journal of Theoretical and Applied Information Technology, 65(1), pp.274-
292.
Babate, I.I., Musa, A., Kida, M. and Saidu, K., 2014. State of Cyber Security: Emerging Threats
Landscape.
Chenail, R.J., 2011. Ten steps for conceptualizing and conducting qualitative research studies in
a pragmatically curious manner. The Qualitative Report, 16(6), p.1713.
Chenail, R.J., Cooper, R. and Desir, C., 2010. Strategically Reviewing the Research Literature in
Qualitative Research. Journal of Ethnographic & Qualitative Research, 4(2).
Choo, K.K.R., 2014. A conceptual interdisciplinary plug-and-play cyber security framework.
In ICTs and the Millennium Development Goals (pp. 81-99). Springer US.
Creeger, M., 2010. CTO roundtable: malware defense. Communications of the ACM, 53(4),
pp.43-49.
Djambazova, E., Almgren, M., Dimitrov, K. and Jonsson, E., 2011. Emerging and future cyber
threats to critical systems. Open Research Problems in Network Security, pp.29-46.
Elmaghraby, A.S. and Losavio, M.M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research, 5(4), pp.491-497.
Hurt, R.L. and McLaughlin, E.J., 2012. An applied introduction to qualitative research methods
in academic advising. NACADA Journal, 32(1), pp.63-71.
Ijaz, S., Shah, M.A., Khan, A. and Ahmed, M., 2016. Smart cities: A survey on security
concerns. Int. J. Adv. Comput. Sci. Appl, 7, pp.612-625.
Kostyuk, N., 2014. International and domestic challenges to comprehensive national
cybersecurity: A case study of the Czech Republic. Journal of Strategic Security, 7(1), p.68.
14
Abomhara, M., 2015. Cyber security and the internet of things: vulnerabilities, threats, intruders
and attacks. Journal of Cyber Security and Mobility, 4(1), pp.65-88.
Almadhoob, A. and Valverde, R., 2014. Cybercrime prevention in the kingdom of Bahrain via IT
security audit plans. Journal of Theoretical and Applied Information Technology, 65(1), pp.274-
292.
Babate, I.I., Musa, A., Kida, M. and Saidu, K., 2014. State of Cyber Security: Emerging Threats
Landscape.
Chenail, R.J., 2011. Ten steps for conceptualizing and conducting qualitative research studies in
a pragmatically curious manner. The Qualitative Report, 16(6), p.1713.
Chenail, R.J., Cooper, R. and Desir, C., 2010. Strategically Reviewing the Research Literature in
Qualitative Research. Journal of Ethnographic & Qualitative Research, 4(2).
Choo, K.K.R., 2014. A conceptual interdisciplinary plug-and-play cyber security framework.
In ICTs and the Millennium Development Goals (pp. 81-99). Springer US.
Creeger, M., 2010. CTO roundtable: malware defense. Communications of the ACM, 53(4),
pp.43-49.
Djambazova, E., Almgren, M., Dimitrov, K. and Jonsson, E., 2011. Emerging and future cyber
threats to critical systems. Open Research Problems in Network Security, pp.29-46.
Elmaghraby, A.S. and Losavio, M.M., 2014. Cyber security challenges in Smart Cities: Safety,
security and privacy. Journal of advanced research, 5(4), pp.491-497.
Hurt, R.L. and McLaughlin, E.J., 2012. An applied introduction to qualitative research methods
in academic advising. NACADA Journal, 32(1), pp.63-71.
Ijaz, S., Shah, M.A., Khan, A. and Ahmed, M., 2016. Smart cities: A survey on security
concerns. Int. J. Adv. Comput. Sci. Appl, 7, pp.612-625.
Kostyuk, N., 2014. International and domestic challenges to comprehensive national
cybersecurity: A case study of the Czech Republic. Journal of Strategic Security, 7(1), p.68.
14

Losavio, M., Rogers, C. and Elmaghraby, A., 2015, September. Digital heritage from the Smart
City and the Internet of Things: History or stasis? In Digital Heritage, 2015 (Vol. 2, pp. 431-
434). IEEE.
Mallinder, J. and Drabwell, P., 2014. Cyber security: A critical examination of information
sharing versus data sensitivity issues for organisations at risk of cyber attack. Journal of business
continuity & emergency planning, 7(2), pp.103-111.
Manley, M., 2015. Cyberspace's Dynamic Duo: Forging a Cybersecurity Public-Private
Partnership. Journal of Strategic Security, 8(5), pp.85-98.
Pramanik, S., 2013, October. Threat motivation. In Emerging Technologies for a Smarter World
(CEWIT), 2013 10th International Conference and Expo on (pp. 1-5). IEEE.
Sen, M., Dutt, A., Agarwal, S. and Nath, A., 2013, April. Issues of privacy and security in the
role of software in smart cities. In Communication Systems and Network Technologies (CSNT),
2013 International Conference on (pp. 518-523). IEEE.
15
City and the Internet of Things: History or stasis? In Digital Heritage, 2015 (Vol. 2, pp. 431-
434). IEEE.
Mallinder, J. and Drabwell, P., 2014. Cyber security: A critical examination of information
sharing versus data sensitivity issues for organisations at risk of cyber attack. Journal of business
continuity & emergency planning, 7(2), pp.103-111.
Manley, M., 2015. Cyberspace's Dynamic Duo: Forging a Cybersecurity Public-Private
Partnership. Journal of Strategic Security, 8(5), pp.85-98.
Pramanik, S., 2013, October. Threat motivation. In Emerging Technologies for a Smarter World
(CEWIT), 2013 10th International Conference and Expo on (pp. 1-5). IEEE.
Sen, M., Dutt, A., Agarwal, S. and Nath, A., 2013, April. Issues of privacy and security in the
role of software in smart cities. In Communication Systems and Network Technologies (CSNT),
2013 International Conference on (pp. 518-523). IEEE.
15
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





