Cyber Security Countermeasures
VerifiedAdded on 2023/03/17
|13
|3136
|67
AI Summary
This report discusses the importance of cyber security countermeasures in organizations, particularly for those moving towards online platforms. It identifies critical issues faced by a company and provides solutions to address them, including the use of cloud-based security measures. The report also compares cloud-based approaches with traditional ones and provides a breakdown of the cost for implementing the proposed countermeasures.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: CYBER SECURITY COUNTERMEASURES
Cyber Security countermeasures
Name of the student:
Name of the university:
Author note:
Cyber Security countermeasures
Name of the student:
Name of the university:
Author note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1CYBER SECURITY COUNTERMEASURES
Table of Contents
Introduction:...............................................................................................................................2
Discussion:.................................................................................................................................3
Current cyber security scenario in the company:...................................................................3
5 critical cyber security issues which need immediate attention:..........................................4
Solutions to address the identified issues:..............................................................................5
Comparison with alternative approaches:..............................................................................7
Breakdown structure of the cost for addressing the issues:.......................................................7
Conclusion:................................................................................................................................7
References:.................................................................................................................................8
Table of Contents
Introduction:...............................................................................................................................2
Discussion:.................................................................................................................................3
Current cyber security scenario in the company:...................................................................3
5 critical cyber security issues which need immediate attention:..........................................4
Solutions to address the identified issues:..............................................................................5
Comparison with alternative approaches:..............................................................................7
Breakdown structure of the cost for addressing the issues:.......................................................7
Conclusion:................................................................................................................................7
References:.................................................................................................................................8

2CYBER SECURITY COUNTERMEASURES
Introduction:
In this modern world of cyber advancements, more and more cyber risks are emerging
with the growth in the technology. Organisations regardless of their sizes are tending to move
towards online platform and as a result of which are more vulnerable towards facing cyber
risks and threats. It is important for companies to stay updated about the latest security
policies and countermeasures in order to prevent any major data loss from their systems or
databases. Cyber security is gradually changing its face with the new types of cyber attacks
that are taking place at every moment. A cyber ttack is referred to as the term of deliberately
attacking and exploiting the computer systems within the targeted organization causing loss
in the credential data that are much critical for the company’s survival. For every
organisation it is needed to perform a cyber risk assessment before moving its business to the
online platform as while in online platform the organization’s data assets would be at the
verge of more inevitable risks (Elgazzar, Hassanein & Martin, 2014). Cyber risk assessment
within organisation helps the company to point out the importabt issues that are faced during
the time of operation and also helps in identifying proper countermeasures to combat the
issues. The following report is prepared so as to reflect the major issues that are identified
within the organisation of Arrow and based on its effective countermeasures are hence
recommended.
Overview of the company:
The company of Arrow is a small company mainly known for its account related
work. The company resides in Miami, Florida and currently employs about five employees
which the company plans to extend it to at least ten. The company of Arrow is reported to
have made about progressive move by taking initiative to move its business towards the
online platform. However, with the advancement in its business, the company is facing a
Introduction:
In this modern world of cyber advancements, more and more cyber risks are emerging
with the growth in the technology. Organisations regardless of their sizes are tending to move
towards online platform and as a result of which are more vulnerable towards facing cyber
risks and threats. It is important for companies to stay updated about the latest security
policies and countermeasures in order to prevent any major data loss from their systems or
databases. Cyber security is gradually changing its face with the new types of cyber attacks
that are taking place at every moment. A cyber ttack is referred to as the term of deliberately
attacking and exploiting the computer systems within the targeted organization causing loss
in the credential data that are much critical for the company’s survival. For every
organisation it is needed to perform a cyber risk assessment before moving its business to the
online platform as while in online platform the organization’s data assets would be at the
verge of more inevitable risks (Elgazzar, Hassanein & Martin, 2014). Cyber risk assessment
within organisation helps the company to point out the importabt issues that are faced during
the time of operation and also helps in identifying proper countermeasures to combat the
issues. The following report is prepared so as to reflect the major issues that are identified
within the organisation of Arrow and based on its effective countermeasures are hence
recommended.
Overview of the company:
The company of Arrow is a small company mainly known for its account related
work. The company resides in Miami, Florida and currently employs about five employees
which the company plans to extend it to at least ten. The company of Arrow is reported to
have made about progressive move by taking initiative to move its business towards the
online platform. However, with the advancement in its business, the company is facing a

3CYBER SECURITY COUNTERMEASURES
number of security issues and thus it has become necessary to perform a cyber risk
assessment for the company to identify the countermeasures for the threats.
Discussion:
Current cyber security scenario in the company:
As reported, the company of Arrow is facing a number of cyber security risks associated
with their data assets. The current situation of the cyber systems within the company is as
follows:
1. First of all, the company of Arrow lacks in having any major security policy in place.
2. The majority of the computers or laptops that are used within the company do not
have any security software installed within them.
3. The company uses the ADSL to access its internet via the D-Link DSL wireless
router. The ADSL type of internet access is known to be the riskier one as the whole
system may get disrupted if any how the network gets attacked. Another issue with
the company is that the in order to store its data as a backup, the company uses the Q
Nap TSS-412 NAS.
4. All the confidential data that are used within the company’s database systems are
transferred via email which is no way a secured method to transfer the confidential
files of the company (Madzima, Moyo & Abdullah, 2014).
5. Apart from these type of cyber issues within the company, another issue that exist is
that the server that the organisation uses for its business process is not that much safe.
As the company used the windows 2000 server before in its business but now due to
some major power cut problem, the server is not yet in a working mode (Vaniea &
Rashidi, 2016). This is a major drawback for the company and in some cases, it may
also lead to the failure to mitigate some major cyber issues like the one which the
number of security issues and thus it has become necessary to perform a cyber risk
assessment for the company to identify the countermeasures for the threats.
Discussion:
Current cyber security scenario in the company:
As reported, the company of Arrow is facing a number of cyber security risks associated
with their data assets. The current situation of the cyber systems within the company is as
follows:
1. First of all, the company of Arrow lacks in having any major security policy in place.
2. The majority of the computers or laptops that are used within the company do not
have any security software installed within them.
3. The company uses the ADSL to access its internet via the D-Link DSL wireless
router. The ADSL type of internet access is known to be the riskier one as the whole
system may get disrupted if any how the network gets attacked. Another issue with
the company is that the in order to store its data as a backup, the company uses the Q
Nap TSS-412 NAS.
4. All the confidential data that are used within the company’s database systems are
transferred via email which is no way a secured method to transfer the confidential
files of the company (Madzima, Moyo & Abdullah, 2014).
5. Apart from these type of cyber issues within the company, another issue that exist is
that the server that the organisation uses for its business process is not that much safe.
As the company used the windows 2000 server before in its business but now due to
some major power cut problem, the server is not yet in a working mode (Vaniea &
Rashidi, 2016). This is a major drawback for the company and in some cases, it may
also lead to the failure to mitigate some major cyber issues like the one which the
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4CYBER SECURITY COUNTERMEASURES
company faced in the year 2018 where the organisation has to pay the ransomware as
demanded by the attacker (Richardson & North, 2017).
6. Another issue that is faced within the company is that the employees who are working
for the company do not have any type of IT expertise and thus lacks the skills that are
required in order to mitigate the cyber issue in emergency solutions. As a result of this
issues the employees remains unaware of the risk factors while accessing others file
and using their accounts (Liao et al., 2016). This type of practice may lead to insider’s
attack within the company.
It is noted that all these cyber issues started taking place after one of the employees in the
company inserted an USB device which was found from the parking area, in one of the
computer systems of the company and from that time the computers are known to have their
own mind.
5 critical cyber security issues which need immediate attention:
As per the issues that are mentioned it has become vital for the company to provide and
implement countermeasures for the issues and accordingly, 5 major issues are identified
within the company which are as follows:
1. Information misuse: The employees within the company of Arrow lacks any cyber
security knowledge and as a result of which the employees misuses the information
within the company. Also, the transferable mode of the information within the
company are not that much secured. So overall the company needs to implement
security policies within the organisation and make employees abide by those as this
issue is a serious one and needs immediate attention.
2. Information privacy issue: As per report, the company uses the latest update of
Microsoft within their systems which is known to have some patching issues within it.
company faced in the year 2018 where the organisation has to pay the ransomware as
demanded by the attacker (Richardson & North, 2017).
6. Another issue that is faced within the company is that the employees who are working
for the company do not have any type of IT expertise and thus lacks the skills that are
required in order to mitigate the cyber issue in emergency solutions. As a result of this
issues the employees remains unaware of the risk factors while accessing others file
and using their accounts (Liao et al., 2016). This type of practice may lead to insider’s
attack within the company.
It is noted that all these cyber issues started taking place after one of the employees in the
company inserted an USB device which was found from the parking area, in one of the
computer systems of the company and from that time the computers are known to have their
own mind.
5 critical cyber security issues which need immediate attention:
As per the issues that are mentioned it has become vital for the company to provide and
implement countermeasures for the issues and accordingly, 5 major issues are identified
within the company which are as follows:
1. Information misuse: The employees within the company of Arrow lacks any cyber
security knowledge and as a result of which the employees misuses the information
within the company. Also, the transferable mode of the information within the
company are not that much secured. So overall the company needs to implement
security policies within the organisation and make employees abide by those as this
issue is a serious one and needs immediate attention.
2. Information privacy issue: As per report, the company uses the latest update of
Microsoft within their systems which is known to have some patching issues within it.

5CYBER SECURITY COUNTERMEASURES
As a result of this the system where the update is installed are attacked with mew bugs
causing malicious attack within the system.
3. Compromise of data within the organisation: The computer system within the
company of Arrow has no major software security and also the important credentials
of the company gets transferred via email which is not a secured method for
information transaction and in any times the data within the company may get leaked
causing disruption of the whole business. Here the business of Arrow company needs
to implement some kind of cryptographic measures to secure its data.
4. Unsecured accessing of network: As the company uses the D-Link ADSL network to
access its internet hence the company is at some point of risk to cyber-attack. The
ADSL networks are known to have some major flaws as it allows connection of
remote devices within its network (Jaiswal, Nath & Kumar, 2014). Moving to an
online platform needs much more secured network access and thus the company
needs to find some alternatives in this respect.
5. Issues with the use of information assets within the organisation ethically and legally:
The organisation of Arrow faces major issues related to cyber security and also lacks
in following ethical and legal standards while accessing, using or transferring
information within the company.
Solutions to address the identified issues:
For any organisation it is very much essential to put into effective solutions to mitigate
any cyber issues within the organisation (Chang, Kuo & Ramachandran, 2016). For the
company of Arrow, it is very much essential to implement mitigating measures immediately
as the business is focusing towards moving its business towards the online business platform.
As a result of this the system where the update is installed are attacked with mew bugs
causing malicious attack within the system.
3. Compromise of data within the organisation: The computer system within the
company of Arrow has no major software security and also the important credentials
of the company gets transferred via email which is not a secured method for
information transaction and in any times the data within the company may get leaked
causing disruption of the whole business. Here the business of Arrow company needs
to implement some kind of cryptographic measures to secure its data.
4. Unsecured accessing of network: As the company uses the D-Link ADSL network to
access its internet hence the company is at some point of risk to cyber-attack. The
ADSL networks are known to have some major flaws as it allows connection of
remote devices within its network (Jaiswal, Nath & Kumar, 2014). Moving to an
online platform needs much more secured network access and thus the company
needs to find some alternatives in this respect.
5. Issues with the use of information assets within the organisation ethically and legally:
The organisation of Arrow faces major issues related to cyber security and also lacks
in following ethical and legal standards while accessing, using or transferring
information within the company.
Solutions to address the identified issues:
For any organisation it is very much essential to put into effective solutions to mitigate
any cyber issues within the organisation (Chang, Kuo & Ramachandran, 2016). For the
company of Arrow, it is very much essential to implement mitigating measures immediately
as the business is focusing towards moving its business towards the online business platform.

6CYBER SECURITY COUNTERMEASURES
The basic steps that needs to be adopted by the company before moving to the online
platform includes the following:
1. Classifying its information assets: Information assets are important [part of any
business and forms the backbone of the entire business process and thus for the
company of Arrow it is essentially important to identify its information assets and
classify them under Top secret, secret and Confidential information classes. This
classification of information will help the company s identifying its information
priority and thus will also help the organisation to transfer them accordingly.
2. Another important step that needs to be taken is to adopt preventive measures so as to
ensure that no data is lost. There ae wide range of DLP present which helps in
mitigating the issues.
3. Another utmost security measure that needs to be taken by the company of Arrow
includes adopting of hardware security in order to overcome the disadvantages of
disconnections between the objectives of the business with that of the IT technologies
with advanced security measures (Kalaiprasath, Elankavi & Udayakumar, 2017).
As the company is planning to move its business towards the online platform, hence it
is very much required for the organisation to implement some solution that will serve
their business purpose and also provide security measures to the business (Ali, Khan &
Vasilakos, 2015). In this context, the organization may take help of some cloud service
providers in order to implement cloud-based solutions aligning with the business
(Ibrahim, Hamlyn-Harris & Grundy, 2016). As with the advancement in business, the
company of Arrow will have to face more peak in traffics along with work loads and all
these things can be well balanced in the cloud platform. Also, the security features of
cloud are well advanced in order to mitigate all the identified issues within the
organisation (Yousafzai, Chang, Gani & Noor, 2016).
The basic steps that needs to be adopted by the company before moving to the online
platform includes the following:
1. Classifying its information assets: Information assets are important [part of any
business and forms the backbone of the entire business process and thus for the
company of Arrow it is essentially important to identify its information assets and
classify them under Top secret, secret and Confidential information classes. This
classification of information will help the company s identifying its information
priority and thus will also help the organisation to transfer them accordingly.
2. Another important step that needs to be taken is to adopt preventive measures so as to
ensure that no data is lost. There ae wide range of DLP present which helps in
mitigating the issues.
3. Another utmost security measure that needs to be taken by the company of Arrow
includes adopting of hardware security in order to overcome the disadvantages of
disconnections between the objectives of the business with that of the IT technologies
with advanced security measures (Kalaiprasath, Elankavi & Udayakumar, 2017).
As the company is planning to move its business towards the online platform, hence it
is very much required for the organisation to implement some solution that will serve
their business purpose and also provide security measures to the business (Ali, Khan &
Vasilakos, 2015). In this context, the organization may take help of some cloud service
providers in order to implement cloud-based solutions aligning with the business
(Ibrahim, Hamlyn-Harris & Grundy, 2016). As with the advancement in business, the
company of Arrow will have to face more peak in traffics along with work loads and all
these things can be well balanced in the cloud platform. Also, the security features of
cloud are well advanced in order to mitigate all the identified issues within the
organisation (Yousafzai, Chang, Gani & Noor, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7CYBER SECURITY COUNTERMEASURES
The list of security features that are provide by cloud-based platforms includes:
1. Cloud directory services: The cloud directory services will help the company of
Arrow to mitigate the issue that they are facing due to the lack of the Windows 2000
server within their systems by allowing the systems with more advanced security
features that will help in mitigating the security issues within the company (Trihinas,
Pallis & Dikaiakos, 2015).
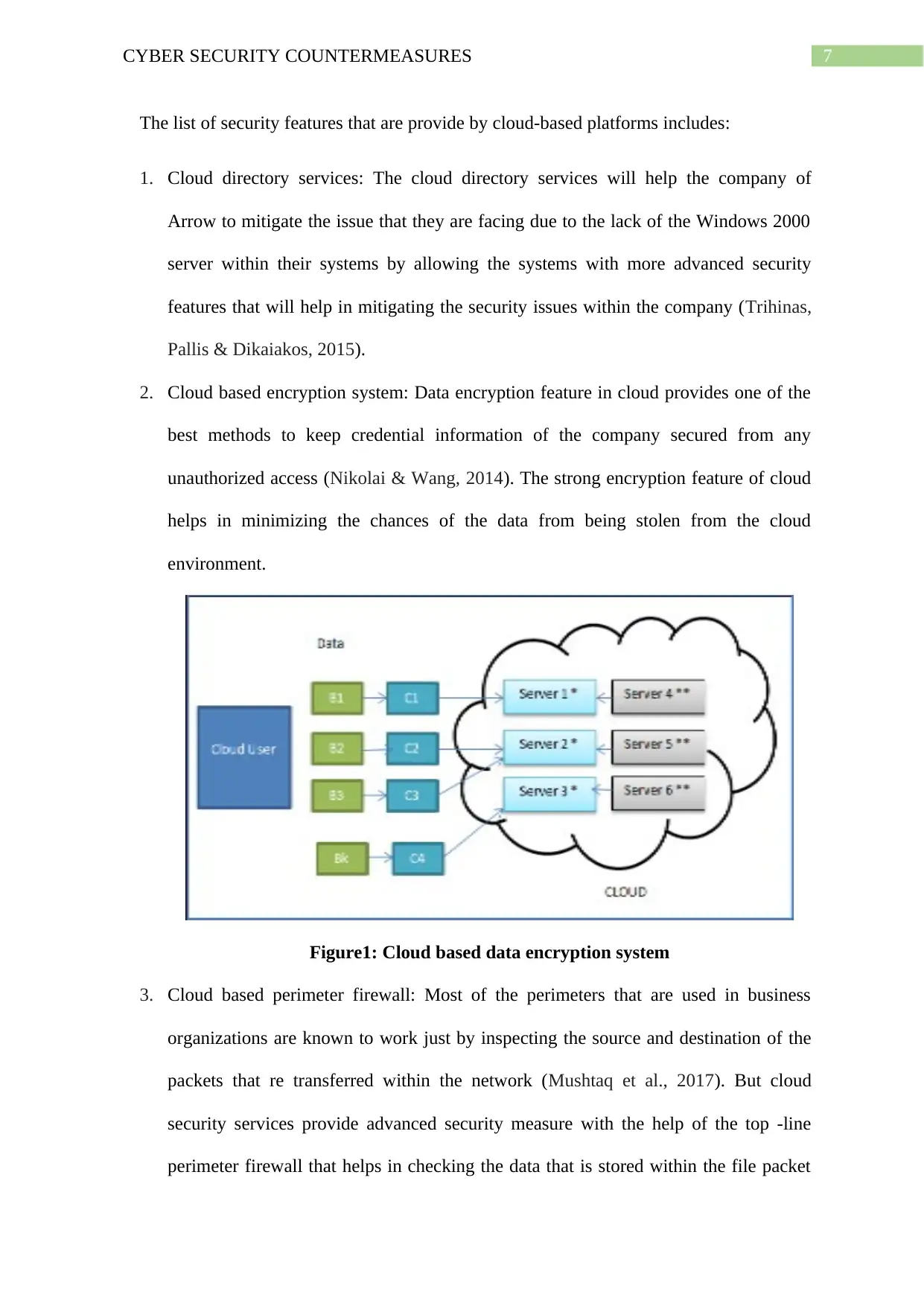
2. Cloud based encryption system: Data encryption feature in cloud provides one of the
best methods to keep credential information of the company secured from any
unauthorized access (Nikolai & Wang, 2014). The strong encryption feature of cloud
helps in minimizing the chances of the data from being stolen from the cloud
environment.
Figure1: Cloud based data encryption system
3. Cloud based perimeter firewall: Most of the perimeters that are used in business
organizations are known to work just by inspecting the source and destination of the
packets that re transferred within the network (Mushtaq et al., 2017). But cloud
security services provide advanced security measure with the help of the top -line
perimeter firewall that helps in checking the data that is stored within the file packet
The list of security features that are provide by cloud-based platforms includes:
1. Cloud directory services: The cloud directory services will help the company of
Arrow to mitigate the issue that they are facing due to the lack of the Windows 2000
server within their systems by allowing the systems with more advanced security
features that will help in mitigating the security issues within the company (Trihinas,
Pallis & Dikaiakos, 2015).
2. Cloud based encryption system: Data encryption feature in cloud provides one of the
best methods to keep credential information of the company secured from any
unauthorized access (Nikolai & Wang, 2014). The strong encryption feature of cloud
helps in minimizing the chances of the data from being stolen from the cloud
environment.
Figure1: Cloud based data encryption system
3. Cloud based perimeter firewall: Most of the perimeters that are used in business
organizations are known to work just by inspecting the source and destination of the
packets that re transferred within the network (Mushtaq et al., 2017). But cloud
security services provide advanced security measure with the help of the top -line
perimeter firewall that helps in checking the data that is stored within the file packet
8CYBER SECURITY COUNTERMEASURES
and examines each detail of it including the file type, source, destination, as well as
integrity.
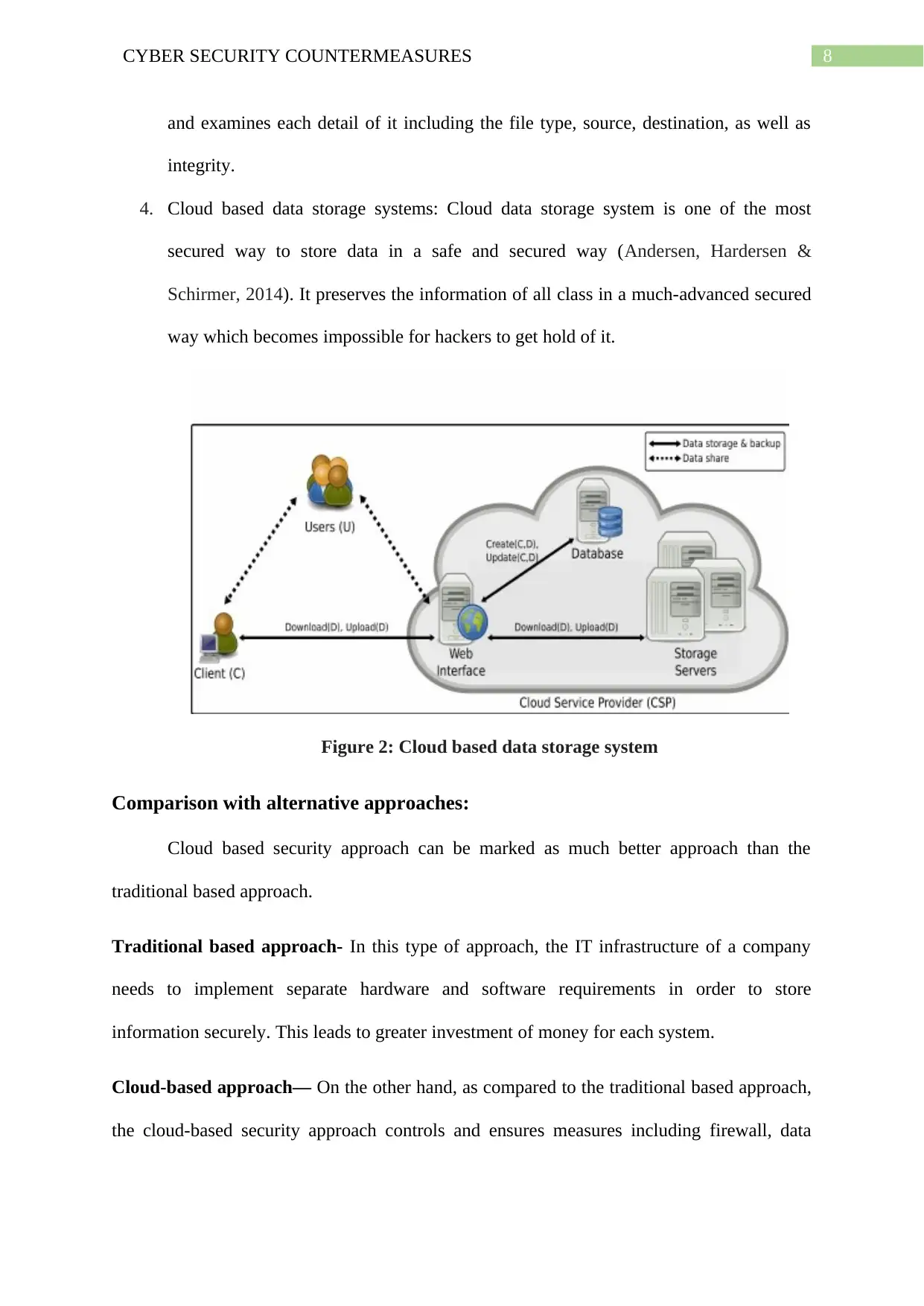
4. Cloud based data storage systems: Cloud data storage system is one of the most
secured way to store data in a safe and secured way (Andersen, Hardersen &
Schirmer, 2014). It preserves the information of all class in a much-advanced secured
way which becomes impossible for hackers to get hold of it.
Figure 2: Cloud based data storage system
Comparison with alternative approaches:
Cloud based security approach can be marked as much better approach than the
traditional based approach.
Traditional based approach- In this type of approach, the IT infrastructure of a company
needs to implement separate hardware and software requirements in order to store
information securely. This leads to greater investment of money for each system.
Cloud-based approach— On the other hand, as compared to the traditional based approach,
the cloud-based security approach controls and ensures measures including firewall, data
and examines each detail of it including the file type, source, destination, as well as
integrity.
4. Cloud based data storage systems: Cloud data storage system is one of the most
secured way to store data in a safe and secured way (Andersen, Hardersen &
Schirmer, 2014). It preserves the information of all class in a much-advanced secured
way which becomes impossible for hackers to get hold of it.
Figure 2: Cloud based data storage system
Comparison with alternative approaches:
Cloud based security approach can be marked as much better approach than the
traditional based approach.
Traditional based approach- In this type of approach, the IT infrastructure of a company
needs to implement separate hardware and software requirements in order to store
information securely. This leads to greater investment of money for each system.
Cloud-based approach— On the other hand, as compared to the traditional based approach,
the cloud-based security approach controls and ensures measures including firewall, data
9CYBER SECURITY COUNTERMEASURES
encryption and many more (Ali, Khan & Vasilakos, 2015). Moreover, it also enables layered
authorization while accessing any particular network.
Breakdown structure of the cost for addressing the issues:
Proposed countermeasures Cost to implement
Cloud IAM service Approximately around $ 5000
Cloud security services Approximately around $3 to $10 per month
Top line perimeter firewall Around $100
Cloud based data encryption $10000
Conclusion:
Thus, from the above presented report it can be concluded that for business of all size
it’s essentially important to implement effective countermeasures so as to mitigate any issue
that is faced within the organization. For business like Arrow company who tends to move
towards the online business it is essentially important that they should mitigate the security
issues as lot of cyber issues are found in the online platform. Here in plays the vital roe of
cloud security services as it offers the all possible solutions to online business platforms
while helping them to progress in their business. Besides all these security solutions it is also
the responsibility of the employees to get aware of the security risks and should be trained
accordingly to provide mitigating measures to countermeasure the issues in future.
encryption and many more (Ali, Khan & Vasilakos, 2015). Moreover, it also enables layered
authorization while accessing any particular network.
Breakdown structure of the cost for addressing the issues:
Proposed countermeasures Cost to implement
Cloud IAM service Approximately around $ 5000
Cloud security services Approximately around $3 to $10 per month
Top line perimeter firewall Around $100
Cloud based data encryption $10000
Conclusion:
Thus, from the above presented report it can be concluded that for business of all size
it’s essentially important to implement effective countermeasures so as to mitigate any issue
that is faced within the organization. For business like Arrow company who tends to move
towards the online business it is essentially important that they should mitigate the security
issues as lot of cyber issues are found in the online platform. Here in plays the vital roe of
cloud security services as it offers the all possible solutions to online business platforms
while helping them to progress in their business. Besides all these security solutions it is also
the responsibility of the employees to get aware of the security risks and should be trained
accordingly to provide mitigating measures to countermeasure the issues in future.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10CYBER SECURITY COUNTERMEASURES
References:
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
http://dx.doi.org/10.1016/j.ins.2015.01.025 0020-0255/ 2015
Andersen, A., Hardersen, T., & Schirmer, N. (2014). Privacy for cloud storage. In ISSE 2014
Securing Electronic Business Processes (pp. 211-219). Springer Vieweg, Wiesbaden.
https://doi.org/10.1007/978-3-658-06708-3_17
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41. https://eprints.soton.ac.uk/382704/1/CCAF_VC_openstack_accepted.pdf
Chen, H. C., & Lee, P. P. (2014). Enabling data integrity protection in regenerating-coding-
based cloud storage: Theory and implementation. IEEE transactions on parallel and
distributed systems, 25(2), 407-416.
http://lansainformatics.com/wp-content/plugins/project-mgt/file/upload/pdf/
3610Enabling-Data-Integrity-Protection-in-Regenerating-Coding-Based-Cloud-
Storage-Theory-and-Implementation-pdf.pdf
Elgazzar, K., Hassanein, H. S., & Martin, P. (2014). Daas: Cloud-based mobile web service
discovery. Pervasive and Mobile Computing, 13, 67-84.
http://dx.doi.org/10.1016/j.pmcj.2013.10.015
Ibrahim, A. S., Hamlyn-Harris, J., & Grundy, J. (2016). Emerging security challenges of
cloud virtual infrastructure. arXiv preprint arXiv:1612.09059.
https://arxiv.org/ftp/arxiv/papers/1612/1612.09059.pdf
References:
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
http://dx.doi.org/10.1016/j.ins.2015.01.025 0020-0255/ 2015
Andersen, A., Hardersen, T., & Schirmer, N. (2014). Privacy for cloud storage. In ISSE 2014
Securing Electronic Business Processes (pp. 211-219). Springer Vieweg, Wiesbaden.
https://doi.org/10.1007/978-3-658-06708-3_17
Chang, V., Kuo, Y. H., & Ramachandran, M. (2016). Cloud computing adoption framework:
A security framework for business clouds. Future Generation Computer Systems, 57,
24-41. https://eprints.soton.ac.uk/382704/1/CCAF_VC_openstack_accepted.pdf
Chen, H. C., & Lee, P. P. (2014). Enabling data integrity protection in regenerating-coding-
based cloud storage: Theory and implementation. IEEE transactions on parallel and
distributed systems, 25(2), 407-416.
http://lansainformatics.com/wp-content/plugins/project-mgt/file/upload/pdf/
3610Enabling-Data-Integrity-Protection-in-Regenerating-Coding-Based-Cloud-
Storage-Theory-and-Implementation-pdf.pdf
Elgazzar, K., Hassanein, H. S., & Martin, P. (2014). Daas: Cloud-based mobile web service
discovery. Pervasive and Mobile Computing, 13, 67-84.
http://dx.doi.org/10.1016/j.pmcj.2013.10.015
Ibrahim, A. S., Hamlyn-Harris, J., & Grundy, J. (2016). Emerging security challenges of
cloud virtual infrastructure. arXiv preprint arXiv:1612.09059.
https://arxiv.org/ftp/arxiv/papers/1612/1612.09059.pdf

11CYBER SECURITY COUNTERMEASURES
Jaiswal, C., Nath, M., & Kumar, V. (2014). Location-based security framework for cloud
perimeters. IEEE Cloud Computing, 1(3), 56-64.
https://par.nsf.gov/servlets/purl/10021619
Kalaiprasath, R., Elankavi, R., & Udayakumar, D. R. (2017). Cloud. Security and
Compliance-A Semantic Approach in End to End Security. International Journal Of
Mechanical Engineering And Technology (Ijmet), 8(5), 987-994.
https://www.researchgate.net/profile/Kalaiprasath_r/publication/319456516_A_new_
approach_for_cloud_data_security_From_single_to_Cloud-of-Clouds/links/
5ae16003aca272fdaf8d9601/A-new-approach-for-cloud-data-security-From-single-to-
Cloud-of-Clouds.pdf
Liao, X., Liu, C., McCoy, D., Shi, E., Hao, S., & Beyah, R. (2016, April). Characterizing
long-tail SEO spam on cloud web hosting services. In Proceedings of the 25th
International Conference on World Wide Web (pp. 321-332). International World
Wide Web Conferences Steering Committee.
https://doi.org/10.1145/2872427.2883008
Madzima, K., Moyo, M., & Abdullah, H. (2014, August). Is bring your own device an
institutional information security risk for small-scale business organisations? In 2014
Information Security for South Africa (pp. 1-8). IEEE.
https://digifors.cs.up.ac.za/issa/2014/Proceedings/Full/54_Paper.pdf
Mushtaq, M. F., Akram, U., Khan, I., Khan, S. N., Shahzad, A., & Ullah, A. (2017). Cloud
computing environment and security challenges: A review. International Journal of
Advanced Computer Science and Application, 8(10), 183-195.
https://www.researchgate.net/profile/Muhammad_Mushtaq31/publication/
320802850_Cloud_Computing_Environment_and_Security_Challenges_A_Review/
Jaiswal, C., Nath, M., & Kumar, V. (2014). Location-based security framework for cloud
perimeters. IEEE Cloud Computing, 1(3), 56-64.
https://par.nsf.gov/servlets/purl/10021619
Kalaiprasath, R., Elankavi, R., & Udayakumar, D. R. (2017). Cloud. Security and
Compliance-A Semantic Approach in End to End Security. International Journal Of
Mechanical Engineering And Technology (Ijmet), 8(5), 987-994.
https://www.researchgate.net/profile/Kalaiprasath_r/publication/319456516_A_new_
approach_for_cloud_data_security_From_single_to_Cloud-of-Clouds/links/
5ae16003aca272fdaf8d9601/A-new-approach-for-cloud-data-security-From-single-to-
Cloud-of-Clouds.pdf
Liao, X., Liu, C., McCoy, D., Shi, E., Hao, S., & Beyah, R. (2016, April). Characterizing
long-tail SEO spam on cloud web hosting services. In Proceedings of the 25th
International Conference on World Wide Web (pp. 321-332). International World
Wide Web Conferences Steering Committee.
https://doi.org/10.1145/2872427.2883008
Madzima, K., Moyo, M., & Abdullah, H. (2014, August). Is bring your own device an
institutional information security risk for small-scale business organisations? In 2014
Information Security for South Africa (pp. 1-8). IEEE.
https://digifors.cs.up.ac.za/issa/2014/Proceedings/Full/54_Paper.pdf
Mushtaq, M. F., Akram, U., Khan, I., Khan, S. N., Shahzad, A., & Ullah, A. (2017). Cloud
computing environment and security challenges: A review. International Journal of
Advanced Computer Science and Application, 8(10), 183-195.
https://www.researchgate.net/profile/Muhammad_Mushtaq31/publication/
320802850_Cloud_Computing_Environment_and_Security_Challenges_A_Review/

12CYBER SECURITY COUNTERMEASURES
links/59fc20da458515d07062864c/Cloud-Computing-Environment-and-Security-
Challenges-A-Review.pdf
Nikolai, J., & Wang, Y. (2014, February). Hypervisor-based cloud intrusion detection
system. In 2014 International Conference on Computing, Networking and
Communications (ICNC) (pp. 989-993). IEEE.
https://www.researchgate.net/profile/Jason_Nikolai/publication/269311687_Hypervis
or-based_cloud_intrusion_detection_system/links/590c1efaaca272db9ca56a3c/
Hypervisor-based-cloud-intrusion-detection-system.pdf
Richardson, R., & North, M. M. (2017). Ransomware: Evolution, mitigation and
prevention. International Management Review, 13(1), 10.
https://digitalcommons.kennesaw.edu/cgi/viewcontent.cgi?
article=5312&context=facpubs
Trihinas, D., Pallis, G., & Dikaiakos, M. (2015). Monitoring elastically adaptive multi-cloud
services. IEEE Transactions on Cloud Computing.
http://linc.ucy.ac.cy/publications/pdfs/dtrihinas_jcatascopia_tcc_dec2015.pdf
Vaniea, K., & Rashidi, Y. (2016, May). Tales of software updates: The process of updating
software. In Proceedings of the 2016 chi conference on human factors in computing
systems (pp. 3215-3226). ACM. DOI: 10.1145/2858036.2858303
Yousafzai, A., Chang, V., Gani, A., & Noor, R. M. (2016). Directory-based incentive
management services for ad-hoc mobile clouds. International Journal of Information
Management, 36(6), 900-906. https://eprints.soton.ac.uk/395487/1/IJIM_DIMS.pdf
links/59fc20da458515d07062864c/Cloud-Computing-Environment-and-Security-
Challenges-A-Review.pdf
Nikolai, J., & Wang, Y. (2014, February). Hypervisor-based cloud intrusion detection
system. In 2014 International Conference on Computing, Networking and
Communications (ICNC) (pp. 989-993). IEEE.
https://www.researchgate.net/profile/Jason_Nikolai/publication/269311687_Hypervis
or-based_cloud_intrusion_detection_system/links/590c1efaaca272db9ca56a3c/
Hypervisor-based-cloud-intrusion-detection-system.pdf
Richardson, R., & North, M. M. (2017). Ransomware: Evolution, mitigation and
prevention. International Management Review, 13(1), 10.
https://digitalcommons.kennesaw.edu/cgi/viewcontent.cgi?
article=5312&context=facpubs
Trihinas, D., Pallis, G., & Dikaiakos, M. (2015). Monitoring elastically adaptive multi-cloud
services. IEEE Transactions on Cloud Computing.
http://linc.ucy.ac.cy/publications/pdfs/dtrihinas_jcatascopia_tcc_dec2015.pdf
Vaniea, K., & Rashidi, Y. (2016, May). Tales of software updates: The process of updating
software. In Proceedings of the 2016 chi conference on human factors in computing
systems (pp. 3215-3226). ACM. DOI: 10.1145/2858036.2858303
Yousafzai, A., Chang, V., Gani, A., & Noor, R. M. (2016). Directory-based incentive
management services for ad-hoc mobile clouds. International Journal of Information
Management, 36(6), 900-906. https://eprints.soton.ac.uk/395487/1/IJIM_DIMS.pdf
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





