CYBER SECURITY Name: Student Id: Name of univeristy:.
VerifiedAdded on 2023/03/17
|8
|4621
|39
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

CYBER SECURITY
Name:
Student Id:
Name of univeristy:
1
Name:
Student Id:
Name of univeristy:
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Abstract— Cyber security threats are rapidly increasing day
by day. The number of cyber attacks has increased by multiple
times in the recent years. Organizations have vulnerabilities
in the network system which leads to the attack. The cyber
criminals look for weakness in the network system of the
company to enter the system. The attacks are generally done
to steal data and other confidential information from the
system to use it against the organization.
(Keywords—Cyber security, Cyber attacks, Vulnerabilities)
I. INTRODUCTION
Introduction
Technology has become the most reliable solution to every
worldly problem. IT services are used by both small and large
scale companies to serve their customers and solve major
issues. Every individual enterprise faces the risk of cyber
attacks and is constantly under threats from external factors.
None of the businesses are safe in the recent times. There are
too many threats out there in the open and each one is harmful
than the other. In the recent times system security threats and
challenges have increased considerably [1]. The challenges are
mostly connected to the healthcare and banking sectors. The
main motive of these attacks is to gain access of sensitive and
confidential information and use them against the company or
individuals. The perpetrators use the information to ask for
ransom to espionage and beyond. There are numerous
underlying motives for such attacks and they affect the general
public greatly [2]. Cyber crime has turned out to be a huge
business and the cyber criminals have discovered a sweet spot
for the attack. The attackers mostly launch the attack on small
and medium size enterprises. The attacks on the small and
medium size enterprises have increased gradually in the recent
years [3]. Organizations need to device strong network
security protocols to protect the organization from any kind of
external threat and malware attacks. The attackers mostly try
to access bank details of the users from the data base and
cause damage to the data. It is noticed that most SME’s are
not prepared stop and prevent such attacks. These small
medium size enterprises do not possess advanced cyber
security tools or apparatus to protect their organization [4].
The enterprises are highly vulnerable to system threats and
cyber attacks. The company needs to device plans for network
security. Network security can be defined as the purpose to
protect the integrity and the usability of both network and data
[5]. Attacks include malware attack, phishing attack, DDos
attacks, SQL injections, ransom ware and malware. Network
security includes software as well as hardware technologies.
The primary work of network security is to prevent numerous
threats, stop the entry of the attacks and finally curtail it from
spreading into the system. Network security merges several
defense layer into the network and at the edge [6]. Each layer
of the network implements controls and policies. The design
only allows authorized used to gain access to the resources
present in the network system. Malicious actors and third
party intruders are blocked from carrying out any kind of
threats and exploits. As digitization has completely
transformed the world, organizations are trying their best to
deliver services, meet customer demand and expectations.
Network security also helps you protect proprietary
information from the attack. Companies need to invest in
proper network security tools to protect the company’s assets
and sensitive data [7]. The initial blockage the attackers face is
the firewall. The stronger the firewall, better the security for
the company to prevent any future attacks. Recently attacks
have increased and a lot of companies are facing cyber attacks
annually. The problems with the attacks are that, each attack is
different from the other and the nature of the malware is
different. Certain malware can stay inside the system for
months or even years and stay completely undetected [8].
Later they unleash and cause tremendous harm to the
organization’s assets and data base. To prevent attacks
stringent cyber security policies and methods are implemented
[9].
II. TARGET STORE CORPORATION
Target Store Corporation is a retail giant in United States of
America. The company is a part of S&P 500 Index. The
company was founded in the year 1902 and over the years the
name of the company gradually changed. The company has
their headquarters at Minneapolis, United States. The
company slowly started expanding nationwide and developed
new stores under the brand name of Target. Initially the
company was named was Dayton Company from the name of
the founder. Later the parent company was renamed to Target
Store Corporation. As of the recent year, the company owns
numerous stores throughout the length and breadth of the
United States. The store format of Target Corporation includes
Super Market and flexible format target. The format of the
store helped the company to expand business and garner high
revenue.
Cyber attack: The Target Corporation faced a huge cyber
attack sometime between November and December in the year
2013. The network system of Target Corporation was breached
and it became a huge attack in the history of the company. The
attackers stole credit and debit card details of the customers
who used them in Target Corporation [20]. The attack started
sometime in the Thanks giving week and the malware stayed
undetected for several weeks. It is estimated that around a
hundred million customer data have been compromised. The
attack brought a loss of millions debit and credit card details,
and seventy million personal data and valuable information
have been stolen by the attack. The ordeal cost credit card
union nearly over $200 million for just reissuing cards [20] To
secure a massive chunk of data and connected devices is a
challenge in itself [16]. The challenge gets complex for the
retailers as they are connected and posses a vast network across
the country.
A. Vulnerabilities
The company Target Corporation tried out methods
to prevent the corporation from the attack of data infiltration
and malware. It was noticed that the company deployed a
reputable and well known malware and virus detection service
by day. The number of cyber attacks has increased by multiple
times in the recent years. Organizations have vulnerabilities
in the network system which leads to the attack. The cyber
criminals look for weakness in the network system of the
company to enter the system. The attacks are generally done
to steal data and other confidential information from the
system to use it against the organization.
(Keywords—Cyber security, Cyber attacks, Vulnerabilities)
I. INTRODUCTION
Introduction
Technology has become the most reliable solution to every
worldly problem. IT services are used by both small and large
scale companies to serve their customers and solve major
issues. Every individual enterprise faces the risk of cyber
attacks and is constantly under threats from external factors.
None of the businesses are safe in the recent times. There are
too many threats out there in the open and each one is harmful
than the other. In the recent times system security threats and
challenges have increased considerably [1]. The challenges are
mostly connected to the healthcare and banking sectors. The
main motive of these attacks is to gain access of sensitive and
confidential information and use them against the company or
individuals. The perpetrators use the information to ask for
ransom to espionage and beyond. There are numerous
underlying motives for such attacks and they affect the general
public greatly [2]. Cyber crime has turned out to be a huge
business and the cyber criminals have discovered a sweet spot
for the attack. The attackers mostly launch the attack on small
and medium size enterprises. The attacks on the small and
medium size enterprises have increased gradually in the recent
years [3]. Organizations need to device strong network
security protocols to protect the organization from any kind of
external threat and malware attacks. The attackers mostly try
to access bank details of the users from the data base and
cause damage to the data. It is noticed that most SME’s are
not prepared stop and prevent such attacks. These small
medium size enterprises do not possess advanced cyber
security tools or apparatus to protect their organization [4].
The enterprises are highly vulnerable to system threats and
cyber attacks. The company needs to device plans for network
security. Network security can be defined as the purpose to
protect the integrity and the usability of both network and data
[5]. Attacks include malware attack, phishing attack, DDos
attacks, SQL injections, ransom ware and malware. Network
security includes software as well as hardware technologies.
The primary work of network security is to prevent numerous
threats, stop the entry of the attacks and finally curtail it from
spreading into the system. Network security merges several
defense layer into the network and at the edge [6]. Each layer
of the network implements controls and policies. The design
only allows authorized used to gain access to the resources
present in the network system. Malicious actors and third
party intruders are blocked from carrying out any kind of
threats and exploits. As digitization has completely
transformed the world, organizations are trying their best to
deliver services, meet customer demand and expectations.
Network security also helps you protect proprietary
information from the attack. Companies need to invest in
proper network security tools to protect the company’s assets
and sensitive data [7]. The initial blockage the attackers face is
the firewall. The stronger the firewall, better the security for
the company to prevent any future attacks. Recently attacks
have increased and a lot of companies are facing cyber attacks
annually. The problems with the attacks are that, each attack is
different from the other and the nature of the malware is
different. Certain malware can stay inside the system for
months or even years and stay completely undetected [8].
Later they unleash and cause tremendous harm to the
organization’s assets and data base. To prevent attacks
stringent cyber security policies and methods are implemented
[9].
II. TARGET STORE CORPORATION
Target Store Corporation is a retail giant in United States of
America. The company is a part of S&P 500 Index. The
company was founded in the year 1902 and over the years the
name of the company gradually changed. The company has
their headquarters at Minneapolis, United States. The
company slowly started expanding nationwide and developed
new stores under the brand name of Target. Initially the
company was named was Dayton Company from the name of
the founder. Later the parent company was renamed to Target
Store Corporation. As of the recent year, the company owns
numerous stores throughout the length and breadth of the
United States. The store format of Target Corporation includes
Super Market and flexible format target. The format of the
store helped the company to expand business and garner high
revenue.
Cyber attack: The Target Corporation faced a huge cyber
attack sometime between November and December in the year
2013. The network system of Target Corporation was breached
and it became a huge attack in the history of the company. The
attackers stole credit and debit card details of the customers
who used them in Target Corporation [20]. The attack started
sometime in the Thanks giving week and the malware stayed
undetected for several weeks. It is estimated that around a
hundred million customer data have been compromised. The
attack brought a loss of millions debit and credit card details,
and seventy million personal data and valuable information
have been stolen by the attack. The ordeal cost credit card
union nearly over $200 million for just reissuing cards [20] To
secure a massive chunk of data and connected devices is a
challenge in itself [16]. The challenge gets complex for the
retailers as they are connected and posses a vast network across
the country.
A. Vulnerabilities
The company Target Corporation tried out methods
to prevent the corporation from the attack of data infiltration
and malware. It was noticed that the company deployed a
reputable and well known malware and virus detection service
that detects malware. The company ignored the multiple cyber
threats imposed on the corporation. The company
administrators who had little knowledge about the malware
detection service, turned off the software system. These
mistakes lead to the missing of the early detection of threats
by the company [15]. The question remains, that how the
corporation not recognize the breach and the way the malware
lied undetected in the network system of the company. There
were multiple flaws in the network system of Target
Corporation [16]. As the breach is observed and investigated,
it can be noticed that the effectiveness of the network system
of Target Corporation was not that strong to prevent such
attacks. Better software deployment was required and most
importantly the IT officials of the corporation should have
been more vigilant. The initial breach didn’t actually occur
inside Target Store Corporation. Instead, it occurred in a third
party vendor, Fazio Mechanical Services, the company
provides ventilation, heating and air-conditioning services
[15]. Then the attackers probed the Target Store Corporation
network, pinpointed the loop holes in the system to exploit the
database of the corporation [16]. Certain vulnerabilities were
used to gain access to the confidential and the sensitive data.
The rest were used to the bridge the gap and use it to transfer
data out of Target Store Corporation. The presence of the
weak segmentation of sensitive and non-sensitive data
network in Target Store Corporation aided the attackers to
gain complete access of the sale networks. The credit card
breach had a negative effect on the payment ecosystem as a
whole. Such breaches make the payment system vulnerable
and attacks become a regular and common entity.
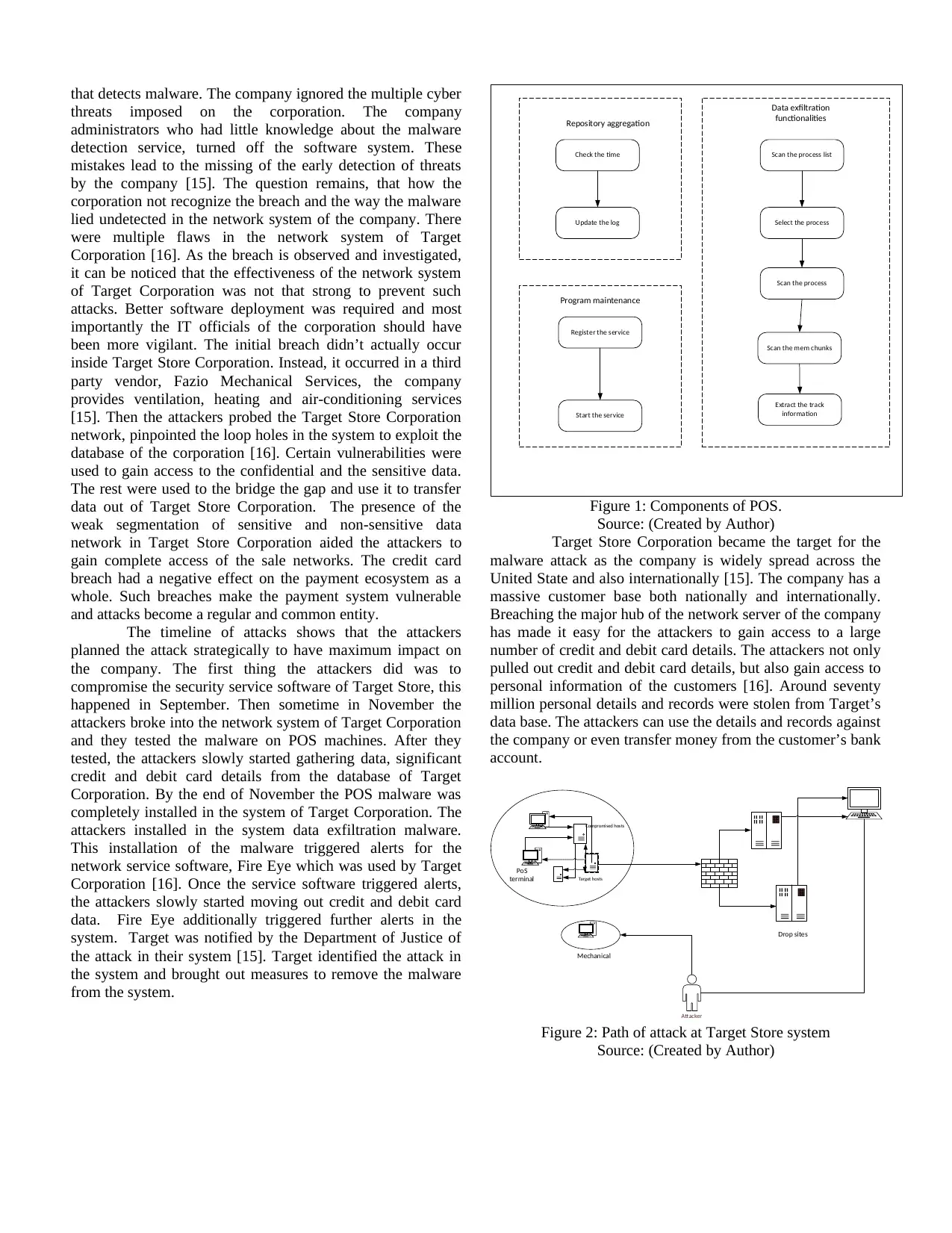
The timeline of attacks shows that the attackers
planned the attack strategically to have maximum impact on
the company. The first thing the attackers did was to
compromise the security service software of Target Store, this
happened in September. Then sometime in November the
attackers broke into the network system of Target Corporation
and they tested the malware on POS machines. After they
tested, the attackers slowly started gathering data, significant
credit and debit card details from the database of Target
Corporation. By the end of November the POS malware was
completely installed in the system of Target Corporation. The
attackers installed in the system data exfiltration malware.
This installation of the malware triggered alerts for the
network service software, Fire Eye which was used by Target
Corporation [16]. Once the service software triggered alerts,
the attackers slowly started moving out credit and debit card
data. Fire Eye additionally triggered further alerts in the
system. Target was notified by the Department of Justice of
the attack in their system [15]. Target identified the attack in
the system and brought out measures to remove the malware
from the system.
Check the time
Update the log
Repository aggregation
Program maintenance
Register the service
Start the service
Data exfiltration
functionalities
Scan the process list
Select the process
Scan the process
Scan the mem chunks
Extract the track
information
Figure 1: Components of POS.
Source: (Created by Author)
Target Store Corporation became the target for the
malware attack as the company is widely spread across the
United State and also internationally [15]. The company has a
massive customer base both nationally and internationally.
Breaching the major hub of the network server of the company
has made it easy for the attackers to gain access to a large
number of credit and debit card details. The attackers not only
pulled out credit and debit card details, but also gain access to
personal information of the customers [16]. Around seventy
million personal details and records were stolen from Target’s
data base. The attackers can use the details and records against
the company or even transfer money from the customer’s bank
account.
Compromised hosts
Target hosts
Mechanical
Attacker
PoS
terminal
Drop sites
Figure 2: Path of attack at Target Store system
Source: (Created by Author)
threats imposed on the corporation. The company
administrators who had little knowledge about the malware
detection service, turned off the software system. These
mistakes lead to the missing of the early detection of threats
by the company [15]. The question remains, that how the
corporation not recognize the breach and the way the malware
lied undetected in the network system of the company. There
were multiple flaws in the network system of Target
Corporation [16]. As the breach is observed and investigated,
it can be noticed that the effectiveness of the network system
of Target Corporation was not that strong to prevent such
attacks. Better software deployment was required and most
importantly the IT officials of the corporation should have
been more vigilant. The initial breach didn’t actually occur
inside Target Store Corporation. Instead, it occurred in a third
party vendor, Fazio Mechanical Services, the company
provides ventilation, heating and air-conditioning services
[15]. Then the attackers probed the Target Store Corporation
network, pinpointed the loop holes in the system to exploit the
database of the corporation [16]. Certain vulnerabilities were
used to gain access to the confidential and the sensitive data.
The rest were used to the bridge the gap and use it to transfer
data out of Target Store Corporation. The presence of the
weak segmentation of sensitive and non-sensitive data
network in Target Store Corporation aided the attackers to
gain complete access of the sale networks. The credit card
breach had a negative effect on the payment ecosystem as a
whole. Such breaches make the payment system vulnerable
and attacks become a regular and common entity.
The timeline of attacks shows that the attackers
planned the attack strategically to have maximum impact on
the company. The first thing the attackers did was to
compromise the security service software of Target Store, this
happened in September. Then sometime in November the
attackers broke into the network system of Target Corporation
and they tested the malware on POS machines. After they
tested, the attackers slowly started gathering data, significant
credit and debit card details from the database of Target
Corporation. By the end of November the POS malware was
completely installed in the system of Target Corporation. The
attackers installed in the system data exfiltration malware.
This installation of the malware triggered alerts for the
network service software, Fire Eye which was used by Target
Corporation [16]. Once the service software triggered alerts,
the attackers slowly started moving out credit and debit card
data. Fire Eye additionally triggered further alerts in the
system. Target was notified by the Department of Justice of
the attack in their system [15]. Target identified the attack in
the system and brought out measures to remove the malware
from the system.
Check the time
Update the log
Repository aggregation
Program maintenance
Register the service
Start the service
Data exfiltration
functionalities
Scan the process list
Select the process
Scan the process
Scan the mem chunks
Extract the track
information
Figure 1: Components of POS.
Source: (Created by Author)
Target Store Corporation became the target for the
malware attack as the company is widely spread across the
United State and also internationally [15]. The company has a
massive customer base both nationally and internationally.
Breaching the major hub of the network server of the company
has made it easy for the attackers to gain access to a large
number of credit and debit card details. The attackers not only
pulled out credit and debit card details, but also gain access to
personal information of the customers [16]. Around seventy
million personal details and records were stolen from Target’s
data base. The attackers can use the details and records against
the company or even transfer money from the customer’s bank
account.
Compromised hosts
Target hosts
Mechanical
Attacker
PoS
terminal
Drop sites
Figure 2: Path of attack at Target Store system
Source: (Created by Author)

B. Potential cyber security threats that the company can face
are:
Phishing: Cyber criminals try to gain access to secured
networks by using emails or social sites. The scammers use
convincing texts and messages to persuade the user to click on
the link the links which launches the attack. The cyber
criminals can access sensitive personal information and
confidential company data. The attackers can also download
the content on their server or computer[23].
Distributed Denial of Service (DDoS): DDoS attacks the
server of the organization directly. In this type of attack, the
server is flooded with requests from various sources. The
requests overwhelm the server to the extent that the server
slows down leading to the point of server crash. Once the
system crashes, it becomes impossible for the system to
perform effectively and use resources. To bring back the
server to life, the interactions are either blocked or canceled
[23].
Password attacks or Brute Force: The attackers tries to
secretly gain access of the network system by using programs
that helps to ascertain the working password [13].
Ransomware: This can lock the system down completely and
they encrypt the devices so that it cannot be used by anyone.
Ransomware is one of the most sophisticated and damaging
threats out there. The computer affected will remain blocked
until and unless a hefty ransom is paid on its behalf, but still it
does not ensure the unlocking of the network, as the attackers
can have the motive to escalate damage to the business [17].
C. Risk factor
Cyber Threats Impact on the organisation
Phishing Moderate
DDoS High
Brute Force High
Ransom ware Very High
Table 1:
Source: (Created by Author)
The company lacks proper firewall and network
system protection services. The main negative aspect of the
company is that the staffs of the company are not properly
trained. The company has poor network security and the
employees are not well trained. This leads to a lot of
mismanagement in the IT services of the company. Failure to
provide systematic update of the network service software can
lead to several vulnerabilities in the network system of the
company. The billing section of the company must have
secure software services and protocols to prevent phishing.
Network of the company should be well segmented to prevent
attacks and seepage of Trojans into the system. Poor network
segmentation leads to several vulnerabilities inside the system
and it becomes easier of the attackers to pinpoint the loopholes
to launch the attack from there [16]. Multiple firewall
installations in the network system and in the database of the
company can prevent further attacks. The company must
periodically run scans of the entire network system to
understand the health of the system. The company needs to
hire IT specialists to conduct regular checks in the system and
indentify malware threats [13]. The periodic checks will make
it easy for the IT professionals to detect any underlying
attacks. To identify undetected malwares in the network
system, the company should have stricter security policies
[14]. Periodic update of network security service software and
even installing new ones can be done to mitigate the
probability of future attacks. The company has to invest
heavily in network security plans and schemes [12]. To avoid
and prevent future breaches there is invest required to set up
walls and hire special IT officials to monitor the IT services
[21].
The steps required for security policy to secure the
organization’s network.
Running Network Security Audit ( asset
identification, firewall configuration, risk
assessment)
Monitor the network services
Moderate level of security
Inclusion of staff in the development of the
policy
Policy must conform to legal requirements
Awareness training to have informed
employees
Limit privileges to minimum- imposing POLP
(policy of least privilege)
Periodic software update
Reviewing cyber security tools
NIST Framework is used to understand the role of
security standards in improving network security. Since there
is a rapid advancement in technology and the cyber security
landscape is constantly evolving, the roadmap highlights the
relevant areas of development in the Framework [21]. The
focused areas include:
Cyber attack lifecycle;
Measuring Cyber security;
Secure Software Development;
Internet of Things (IoT);
Small business resource and awareness;
Referencing Techniques;
are:
Phishing: Cyber criminals try to gain access to secured
networks by using emails or social sites. The scammers use
convincing texts and messages to persuade the user to click on
the link the links which launches the attack. The cyber
criminals can access sensitive personal information and
confidential company data. The attackers can also download
the content on their server or computer[23].
Distributed Denial of Service (DDoS): DDoS attacks the
server of the organization directly. In this type of attack, the
server is flooded with requests from various sources. The
requests overwhelm the server to the extent that the server
slows down leading to the point of server crash. Once the
system crashes, it becomes impossible for the system to
perform effectively and use resources. To bring back the
server to life, the interactions are either blocked or canceled
[23].
Password attacks or Brute Force: The attackers tries to
secretly gain access of the network system by using programs
that helps to ascertain the working password [13].
Ransomware: This can lock the system down completely and
they encrypt the devices so that it cannot be used by anyone.
Ransomware is one of the most sophisticated and damaging
threats out there. The computer affected will remain blocked
until and unless a hefty ransom is paid on its behalf, but still it
does not ensure the unlocking of the network, as the attackers
can have the motive to escalate damage to the business [17].
C. Risk factor
Cyber Threats Impact on the organisation
Phishing Moderate
DDoS High
Brute Force High
Ransom ware Very High
Table 1:
Source: (Created by Author)
The company lacks proper firewall and network
system protection services. The main negative aspect of the
company is that the staffs of the company are not properly
trained. The company has poor network security and the
employees are not well trained. This leads to a lot of
mismanagement in the IT services of the company. Failure to
provide systematic update of the network service software can
lead to several vulnerabilities in the network system of the
company. The billing section of the company must have
secure software services and protocols to prevent phishing.
Network of the company should be well segmented to prevent
attacks and seepage of Trojans into the system. Poor network
segmentation leads to several vulnerabilities inside the system
and it becomes easier of the attackers to pinpoint the loopholes
to launch the attack from there [16]. Multiple firewall
installations in the network system and in the database of the
company can prevent further attacks. The company must
periodically run scans of the entire network system to
understand the health of the system. The company needs to
hire IT specialists to conduct regular checks in the system and
indentify malware threats [13]. The periodic checks will make
it easy for the IT professionals to detect any underlying
attacks. To identify undetected malwares in the network
system, the company should have stricter security policies
[14]. Periodic update of network security service software and
even installing new ones can be done to mitigate the
probability of future attacks. The company has to invest
heavily in network security plans and schemes [12]. To avoid
and prevent future breaches there is invest required to set up
walls and hire special IT officials to monitor the IT services
[21].
The steps required for security policy to secure the
organization’s network.
Running Network Security Audit ( asset
identification, firewall configuration, risk
assessment)
Monitor the network services
Moderate level of security
Inclusion of staff in the development of the
policy
Policy must conform to legal requirements
Awareness training to have informed
employees
Limit privileges to minimum- imposing POLP
(policy of least privilege)
Periodic software update
Reviewing cyber security tools
NIST Framework is used to understand the role of
security standards in improving network security. Since there
is a rapid advancement in technology and the cyber security
landscape is constantly evolving, the roadmap highlights the
relevant areas of development in the Framework [21]. The
focused areas include:
Cyber attack lifecycle;
Measuring Cyber security;
Secure Software Development;
Internet of Things (IoT);
Small business resource and awareness;
Referencing Techniques;
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Enterprise and Governance Risk Management.
To address the growing need for cyber security
measurement which is strictly aligned to the organizational
decisions and objectives and supports the same, Measuring
Cyber security is added as a Roadmap item. Referencing items
are additionally added to make the Framework stakeholders
understand the future intent of references of the Core and also
the general methodology and process of relating one to the
other [21]. A continuous focus is important on cyber security
in relation to both large scale companies and small scale ones.
Stakeholder focus on governance board, organizational
governance and enterprise risk management necessitates a
specific topic. Identity and Access Management to account for
a broader range of important technical topics including
authorization and identity proofing. Confidence Mechanisms
to reflect a broader range of activities that instill digital trust
[19]. The idea is to protect and spread awareness of different
polices to reduce cyber attacks and strengthen cyber security
policies.
D. CISCO SAFE Model
The model includes the following [22]:
1. Capability phase: Use cases or business flows are
defined in this particular phase. Using them as the foundation,
security capabilities appertain to address risks, threats and
policies.
2. Architecture phase: Logical security architecture is
defined using the security capabilities that were identified in
the business flows.
3. Design Phase: Putting in use the security architecture,
a particular design is developed to implement the security
capabilities required which is complete with configuration,
product list, cost and services.
SAFE is use to bridge the wide gap between technical and
business spectators by providing a communal security-centric
language for business concerns and technical solutions.
Business can visualize the required security and also account
the gap [18].
Business Flows include three categories:
Internal: This is the flow of work that the
employees perform inside the network of the
company.
Customers: Includes multiple services like
customer information and website portals.
Third Party: They are mostly vendors, partners,
service providers or guests.
Policy, risks, and threats affect each of them, requiring
security capabilities for protection.
Functional Controls: Common security controls which are
derived from the technical aspects of business flow
Secure Remote Access For third party customers or
partners and employees who are
extrinsic to the company’s
network.
Secure Applications Securing of the applications for
protection
Secure Access Third parties, employees,
customers and devices that
securely accessing network
system.
Secure Communications Video communication, email and
voice connect potential threats
and should be secured.
Secure East/West Traffic Data that securely moves between
internal or external resources.
Secure Web Access Web access controls enforce
usage policy and help prevent
network infection.
Table 2:
Source: (Created by Author)
III. LITERATURE REVIEW
Technology is advancing every hour in the day.
Technology brings in major benefits as well as invites threats
and attacks along with it. Smart grid is power system with ICT
power equipment which is layered massively [24]. Smart grids
integral components are electronic devices, smart meters and
sensors (new generation). Recently, the deployment of the
devices at several dissimilar layers and integration of it invites
cyber threats. The sub systems of the grid are mostly affected
by cyber threats and face cyber attacks [24]. The cyber
security vulnerabilities become even more evident due to the
existing superannuated cyber infrastructure. Cyber security
threats are constantly increasing and it becomes easy to attack
such grids.
Introduction of technology in the world has opened
several windows of opportunities and development. Internet of
things (IoT) is an advanced application of information
technology. IoT connects every smart devices to a single
network and all the device can be accessed simultaneously
[25]. Internet of Things (IoT) is quickly evolving into Internet
of Everything. The new ecosystem connects wireless
networks, analytical data, cloud computing and other
interactive technologies which includes smart devices. The
objects or the devices are embedded with network
connectivity and an identifier is used to enhance device to
device interactions. Advent of IoT has brought in smart
applications and solutions to complex problems. IoT is
advantageous, but the technology faces severe cyber threats
and risk. Since the technology connects multiple devices to a
single hub, it makes it vulnerable to cyber attacks [25]. The
attackers can easily enter through one of the many devices
connected in the network system and damage the working of
the application. The attack can result into data loss and
damage to property. These security concerns need to be
To address the growing need for cyber security
measurement which is strictly aligned to the organizational
decisions and objectives and supports the same, Measuring
Cyber security is added as a Roadmap item. Referencing items
are additionally added to make the Framework stakeholders
understand the future intent of references of the Core and also
the general methodology and process of relating one to the
other [21]. A continuous focus is important on cyber security
in relation to both large scale companies and small scale ones.
Stakeholder focus on governance board, organizational
governance and enterprise risk management necessitates a
specific topic. Identity and Access Management to account for
a broader range of important technical topics including
authorization and identity proofing. Confidence Mechanisms
to reflect a broader range of activities that instill digital trust
[19]. The idea is to protect and spread awareness of different
polices to reduce cyber attacks and strengthen cyber security
policies.
D. CISCO SAFE Model
The model includes the following [22]:
1. Capability phase: Use cases or business flows are
defined in this particular phase. Using them as the foundation,
security capabilities appertain to address risks, threats and
policies.
2. Architecture phase: Logical security architecture is
defined using the security capabilities that were identified in
the business flows.
3. Design Phase: Putting in use the security architecture,
a particular design is developed to implement the security
capabilities required which is complete with configuration,
product list, cost and services.
SAFE is use to bridge the wide gap between technical and
business spectators by providing a communal security-centric
language for business concerns and technical solutions.
Business can visualize the required security and also account
the gap [18].
Business Flows include three categories:
Internal: This is the flow of work that the
employees perform inside the network of the
company.
Customers: Includes multiple services like
customer information and website portals.
Third Party: They are mostly vendors, partners,
service providers or guests.
Policy, risks, and threats affect each of them, requiring
security capabilities for protection.
Functional Controls: Common security controls which are
derived from the technical aspects of business flow
Secure Remote Access For third party customers or
partners and employees who are
extrinsic to the company’s
network.
Secure Applications Securing of the applications for
protection
Secure Access Third parties, employees,
customers and devices that
securely accessing network
system.
Secure Communications Video communication, email and
voice connect potential threats
and should be secured.
Secure East/West Traffic Data that securely moves between
internal or external resources.
Secure Web Access Web access controls enforce
usage policy and help prevent
network infection.
Table 2:
Source: (Created by Author)
III. LITERATURE REVIEW
Technology is advancing every hour in the day.
Technology brings in major benefits as well as invites threats
and attacks along with it. Smart grid is power system with ICT
power equipment which is layered massively [24]. Smart grids
integral components are electronic devices, smart meters and
sensors (new generation). Recently, the deployment of the
devices at several dissimilar layers and integration of it invites
cyber threats. The sub systems of the grid are mostly affected
by cyber threats and face cyber attacks [24]. The cyber
security vulnerabilities become even more evident due to the
existing superannuated cyber infrastructure. Cyber security
threats are constantly increasing and it becomes easy to attack
such grids.
Introduction of technology in the world has opened
several windows of opportunities and development. Internet of
things (IoT) is an advanced application of information
technology. IoT connects every smart devices to a single
network and all the device can be accessed simultaneously
[25]. Internet of Things (IoT) is quickly evolving into Internet
of Everything. The new ecosystem connects wireless
networks, analytical data, cloud computing and other
interactive technologies which includes smart devices. The
objects or the devices are embedded with network
connectivity and an identifier is used to enhance device to
device interactions. Advent of IoT has brought in smart
applications and solutions to complex problems. IoT is
advantageous, but the technology faces severe cyber threats
and risk. Since the technology connects multiple devices to a
single hub, it makes it vulnerable to cyber attacks [25]. The
attackers can easily enter through one of the many devices
connected in the network system and damage the working of
the application. The attack can result into data loss and
damage to property. These security concerns need to be

addressed in order to ensure user confidence so as to promote
wide acceptance and reap the potentials of IoT [25].
IV. CONCLUSION
In this contemporary with technology spreading its
wings like never before, cyber security has become a major
concern. Cyber attacks have drastically increased tenfold in
the past few years. Large scale business firms, organizations,
government firms and even small and medium sized enterprise
have become vulnerable to cyber attacks. There are several
kinds of several attacks and the attacks wreck havoc in the
server system of the company or organisation. Organizations
lose confidential data which are sometimes used against the
company. A hefty price is paid for the aftermath of the attacks.
Organizations are investing hugely to provide better protection
to the network system.
REFERENCES
[1]B. Gupta, D.P. Agrawal, and S. Yamaguchi,
eds. Handbook of research on modern cryptographic solutions
for computer and cyber security. IGI global, 2016.
[2]L. Amini, M. Christodorescu, M.A. Cohen, S.
Parthasarathy, J. Rao, R. Sailer, D.L. Schales, W.Z. Venema,
and O. Verscheure, International Business Machines
Corp. Adaptive cyber-security analytics. U.S. Patent
9,032,521, 2015.
[3] M. Carr. Public–private partnerships in national cyber-
security strategies. International Affairs, 92(1), pp.43-62,
2016.
[4] W. Knowles, D. Prince, D. Hutchison, J.F.P. Disso, and
K. Jones. A survey of cyber security management in industrial
control systems. International journal of critical
infrastructure protection, 9, pp.52-80, 2015.
[5]A. Essa, T. Al-Shoura, A. Al Nabulsi, A.R. Al-Ali, and
F. Aloul. Cyber Physical Sensors System Security: Threats,
Vulnerabilities, and Solutions. In 2018 2nd International
Conference on Smart Grid and Smart Cities (ICSGSC) (pp.
62-67). IEEE, 2018.
[6]B. Gupta, D.P Agrawal, and S. Yamaguchi,
eds. Handbook of research on modern cryptographic solutions
for computer and cyber security. IGI global, 2016.
[7]K. Thakur, M. Qiu, K. Gai, and M.L . Ali. An
investigation on cyber security threats and security models.
In 2015 IEEE 2nd International Conference on Cyber Security
and Cloud Computing (pp. 307-311). IEEE, 2015.
[8] Z. Syed, A. Padia, T. Finin, L. Mathews, and A. Joshi.
UCO: A unified cybersecurity ontology. In Workshops at the
Thirtieth AAAI Conference on Artificial Intelligence, 2016.
[9] J. Pacheco, and S. Hariri. IoT security framework for smart
cyber infrastructures. In 2016 IEEE 1st International
Workshops on Foundations and Applications of Self* Systems
(FAS* W) (pp. 242-247). IEEE, 2016.
[10]D. DiMase, Z.A Collier, K. Heffner and I. Linkov.
Systems engineering framework for cyber physical security
and resilience. Environment Systems and Decisions, 35(2),
pp.291-300., 2015.
[11] S. Parkinson, P. Ward, K. Wilson and J. Miller. Cyber
threats facing autonomous and connected vehicles: Future
challenges. IEEE transactions on intelligent transportation
systems, 18(11), pp.2898-2915, 2017.
[12] D. Puthal, S.P Mohanty, P. Nanda, U. Choppali.
Building security perimeters to protect network systems
against cyber threats [future directions]. IEEE Consumer
Electronics Magazine, 6(4), pp.24-27, 2017.
[13] P. Trim, and D. Upton. Cyber security culture:
Counteracting cyber threats through organizational learning
and training. Routledge, 2016.
[14] L. Maglaras, M.A. Ferrag, A. Derhab, M. Mukherjee,
H. Janicke, and S. Rallis. Threats, Protection and Attribution
of Cyber Attacks on Critical Infrastructures. arXiv preprint
arXiv:1901.03899, 2019.
[15] M. Plachkinova, and C. Maurer. Teaching case: Security
breach at Target. Journal of Information Systems
Education, 29(1), p.11, 2018.
[16] D.A. McMullen, M.H. Sanchez, and M.O Reilly-Allen.
Target security: a case study of how hackers hit the jackpot at
the expense of customers. Review of Business & Finance
Studies, 7(2), pp.41-50, 2016.
[17] T. Li, E. Paja, J. Mylopoulos, J. Horkoff, and K.
Beckers. Security attack analysis using attack patterns.
In 2016 IEEE Tenth International Conference on Research
Challenges in Information Science (RCIS) (pp. 1-13). IEEE,
2016.
[18] A. Woland, V. Santuka, M. Harris, and J.
Sanbower. Integrated Security Technologies and Solutions-
Volume I: Cisco Security Solutions for Advanced Threat
Protection with Next Generation Firewall, Intrusion
Prevention, AMP, and Content Security. Cisco Press, 2018
[19] I. Riadi. Forensic Investigation Technique on Android's
Blackberry Messenger using NIST Framework. International
Journal of Cyber-Security and Digital Forensics, 6(4),
pp.198-206, 2017.
[20]"Target cyber breach hits 40 million payment cards
at holiday peak", U.S., 2019. [Online]. Available:
wide acceptance and reap the potentials of IoT [25].
IV. CONCLUSION
In this contemporary with technology spreading its
wings like never before, cyber security has become a major
concern. Cyber attacks have drastically increased tenfold in
the past few years. Large scale business firms, organizations,
government firms and even small and medium sized enterprise
have become vulnerable to cyber attacks. There are several
kinds of several attacks and the attacks wreck havoc in the
server system of the company or organisation. Organizations
lose confidential data which are sometimes used against the
company. A hefty price is paid for the aftermath of the attacks.
Organizations are investing hugely to provide better protection
to the network system.
REFERENCES
[1]B. Gupta, D.P. Agrawal, and S. Yamaguchi,
eds. Handbook of research on modern cryptographic solutions
for computer and cyber security. IGI global, 2016.
[2]L. Amini, M. Christodorescu, M.A. Cohen, S.
Parthasarathy, J. Rao, R. Sailer, D.L. Schales, W.Z. Venema,
and O. Verscheure, International Business Machines
Corp. Adaptive cyber-security analytics. U.S. Patent
9,032,521, 2015.
[3] M. Carr. Public–private partnerships in national cyber-
security strategies. International Affairs, 92(1), pp.43-62,
2016.
[4] W. Knowles, D. Prince, D. Hutchison, J.F.P. Disso, and
K. Jones. A survey of cyber security management in industrial
control systems. International journal of critical
infrastructure protection, 9, pp.52-80, 2015.
[5]A. Essa, T. Al-Shoura, A. Al Nabulsi, A.R. Al-Ali, and
F. Aloul. Cyber Physical Sensors System Security: Threats,
Vulnerabilities, and Solutions. In 2018 2nd International
Conference on Smart Grid and Smart Cities (ICSGSC) (pp.
62-67). IEEE, 2018.
[6]B. Gupta, D.P Agrawal, and S. Yamaguchi,
eds. Handbook of research on modern cryptographic solutions
for computer and cyber security. IGI global, 2016.
[7]K. Thakur, M. Qiu, K. Gai, and M.L . Ali. An
investigation on cyber security threats and security models.
In 2015 IEEE 2nd International Conference on Cyber Security
and Cloud Computing (pp. 307-311). IEEE, 2015.
[8] Z. Syed, A. Padia, T. Finin, L. Mathews, and A. Joshi.
UCO: A unified cybersecurity ontology. In Workshops at the
Thirtieth AAAI Conference on Artificial Intelligence, 2016.
[9] J. Pacheco, and S. Hariri. IoT security framework for smart
cyber infrastructures. In 2016 IEEE 1st International
Workshops on Foundations and Applications of Self* Systems
(FAS* W) (pp. 242-247). IEEE, 2016.
[10]D. DiMase, Z.A Collier, K. Heffner and I. Linkov.
Systems engineering framework for cyber physical security
and resilience. Environment Systems and Decisions, 35(2),
pp.291-300., 2015.
[11] S. Parkinson, P. Ward, K. Wilson and J. Miller. Cyber
threats facing autonomous and connected vehicles: Future
challenges. IEEE transactions on intelligent transportation
systems, 18(11), pp.2898-2915, 2017.
[12] D. Puthal, S.P Mohanty, P. Nanda, U. Choppali.
Building security perimeters to protect network systems
against cyber threats [future directions]. IEEE Consumer
Electronics Magazine, 6(4), pp.24-27, 2017.
[13] P. Trim, and D. Upton. Cyber security culture:
Counteracting cyber threats through organizational learning
and training. Routledge, 2016.
[14] L. Maglaras, M.A. Ferrag, A. Derhab, M. Mukherjee,
H. Janicke, and S. Rallis. Threats, Protection and Attribution
of Cyber Attacks on Critical Infrastructures. arXiv preprint
arXiv:1901.03899, 2019.
[15] M. Plachkinova, and C. Maurer. Teaching case: Security
breach at Target. Journal of Information Systems
Education, 29(1), p.11, 2018.
[16] D.A. McMullen, M.H. Sanchez, and M.O Reilly-Allen.
Target security: a case study of how hackers hit the jackpot at
the expense of customers. Review of Business & Finance
Studies, 7(2), pp.41-50, 2016.
[17] T. Li, E. Paja, J. Mylopoulos, J. Horkoff, and K.
Beckers. Security attack analysis using attack patterns.
In 2016 IEEE Tenth International Conference on Research
Challenges in Information Science (RCIS) (pp. 1-13). IEEE,
2016.
[18] A. Woland, V. Santuka, M. Harris, and J.
Sanbower. Integrated Security Technologies and Solutions-
Volume I: Cisco Security Solutions for Advanced Threat
Protection with Next Generation Firewall, Intrusion
Prevention, AMP, and Content Security. Cisco Press, 2018
[19] I. Riadi. Forensic Investigation Technique on Android's
Blackberry Messenger using NIST Framework. International
Journal of Cyber-Security and Digital Forensics, 6(4),
pp.198-206, 2017.
[20]"Target cyber breach hits 40 million payment cards
at holiday peak", U.S., 2019. [Online]. Available:

https://www.reuters.com/article/us-target-breach/target-
cyber-breach-hits-40-million-payment-cards-at-holiday-
peak-idUSBRE9BH1GX20131219. [Accessed: 09- May-
2019].
[21]"Cybersecurity Framework", NIST, 2019. [Online].
Available: https://www.nist.gov/cyberframework. [Accessed:
09- May- 2019].
[22]Cisco.com, 2019. [Online]. Available:
https://www.cisco.com/c/dam/en/us/solutions/collateral/enterp
rise/design-zone-security/safe-poster-components.pdf.
[Accessed: 09- May- 2019].
[23] N. Ben-Asher, and C. Gonzalez. Effects of cyber
security knowledge on attack detection. Computers in Human
Behavior, 48, pp.51-61, 2015.
[24] R.K. Pandey and M. Misra. Cyber security threats—
Smart grid infrastructure. In 2016 National Power Systems
Conference (NPSC) (pp. 1-6). IEEE, 2016.
[25] S. Tweneboah-Koduah, K.E. Skouby, and R. Tadayoni,
Cyber security threats to IoT applications and service
domains. Wireless Personal Communications, 95(1), pp.169-
185, 2017.
.
cyber-breach-hits-40-million-payment-cards-at-holiday-
peak-idUSBRE9BH1GX20131219. [Accessed: 09- May-
2019].
[21]"Cybersecurity Framework", NIST, 2019. [Online].
Available: https://www.nist.gov/cyberframework. [Accessed:
09- May- 2019].
[22]Cisco.com, 2019. [Online]. Available:
https://www.cisco.com/c/dam/en/us/solutions/collateral/enterp
rise/design-zone-security/safe-poster-components.pdf.
[Accessed: 09- May- 2019].
[23] N. Ben-Asher, and C. Gonzalez. Effects of cyber
security knowledge on attack detection. Computers in Human
Behavior, 48, pp.51-61, 2015.
[24] R.K. Pandey and M. Misra. Cyber security threats—
Smart grid infrastructure. In 2016 National Power Systems
Conference (NPSC) (pp. 1-6). IEEE, 2016.
[25] S. Tweneboah-Koduah, K.E. Skouby, and R. Tadayoni,
Cyber security threats to IoT applications and service
domains. Wireless Personal Communications, 95(1), pp.169-
185, 2017.
.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





