Data Communication and Networks: Network Proposal for Biomedical Org
VerifiedAdded on 2020/03/16
|13
|2498
|34
Report
AI Summary
This report provides a comprehensive network proposal for a biomedical software development organization. It begins with an introduction outlining the purpose, background, and scope of the project, followed by a detailed requirement analysis, considering the organization's clients, data transmission needs, remote management requirements, and the necessity of mobility. The report then analyzes the current network infrastructure, including circuits, hardware, topology, and software, identifying areas for improvement. Subsequently, it proposes a new network design, detailing circuits, hardware, topology, and software configurations, including the use of VLANs, VPN, and firewall. A cost estimation is provided, breaking down the expenses for hardware, software, and implementation fees. The report concludes with recommendations for implementing the proposed network, emphasizing the benefits of increased productivity, improved security, and scalability. The report highlights the use of advanced technologies like Layer 3 switches, fiber optic connections, and high-end servers to optimize network performance and management.

Running head: DATA COMMUNICATION AND NETWORKS
Data Communication and Networks
Name of the Student
Name of the University
Author’s Note
Data Communication and Networks
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
DATA COMMUNICATION AND NETWORKS
Table of Contents
1. Introduction......................................................................................................................3
1.1. Purpose.....................................................................................................................3
1.2. Background...............................................................................................................3
1.3. Scope.........................................................................................................................3
2. Requirement Analysis......................................................................................................4
2.1. Clients of the system and need.................................................................................4
2.2. Required data transmission.......................................................................................4
2.3. Remote Management................................................................................................4
2.4. Necessity of Mobility...............................................................................................5
3. Analysis and description of the current network.............................................................5
3.1. Circuits......................................................................................................................5
3.2. Hardware...................................................................................................................6
3.3. Topology...................................................................................................................6
3.4. Software....................................................................................................................6
3.5. Analysis....................................................................................................................6
4. Analysis and description of the proposed network..........................................................7
4.1. Circuits......................................................................................................................7
4.2. Hardware...................................................................................................................7
4.3. Topology...................................................................................................................7
DATA COMMUNICATION AND NETWORKS
Table of Contents
1. Introduction......................................................................................................................3
1.1. Purpose.....................................................................................................................3
1.2. Background...............................................................................................................3
1.3. Scope.........................................................................................................................3
2. Requirement Analysis......................................................................................................4
2.1. Clients of the system and need.................................................................................4
2.2. Required data transmission.......................................................................................4
2.3. Remote Management................................................................................................4
2.4. Necessity of Mobility...............................................................................................5
3. Analysis and description of the current network.............................................................5
3.1. Circuits......................................................................................................................5
3.2. Hardware...................................................................................................................6
3.3. Topology...................................................................................................................6
3.4. Software....................................................................................................................6
3.5. Analysis....................................................................................................................6
4. Analysis and description of the proposed network..........................................................7
4.1. Circuits......................................................................................................................7
4.2. Hardware...................................................................................................................7
4.3. Topology...................................................................................................................7

2
DATA COMMUNICATION AND NETWORKS
4.4. Software....................................................................................................................7
5. Cost Estimation................................................................................................................8
6. Conclusion.....................................................................................................................10
7. Recommendations..........................................................................................................11
Bibliography......................................................................................................................12
DATA COMMUNICATION AND NETWORKS
4.4. Software....................................................................................................................7
5. Cost Estimation................................................................................................................8
6. Conclusion.....................................................................................................................10
7. Recommendations..........................................................................................................11
Bibliography......................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
DATA COMMUNICATION AND NETWORKS
1. Introduction
1.1. Purpose
The purpose of the report is to propose a network for a private biomedical development
organization for obliging the present development of the association along its 2 adjoining three
story structures. The proposed arrange comprises of web server, database servers and appropriate
cabling plan for the substitution of the present system of the association. Remote access point is
likewise required to be introduced in the system for empowering the network of the remote
gadgets of the representatives, for example, ipads, advanced cells and tablets.
1.2. Background
The system is subnetted for various branches and the switches are required to be designed
with VPN for empowering remote association in the system. The adaptability of the system is
investigated and late innovation are utilized for the advancement of the system and handle the
future development of the association. The switches are additionally designed with get to control
list for hindering the unapproved clients to associate with the center system segments, for
example, the servers and database. A legitimate and physical system chart of the system is made
for show of the system segments utilized for the improvement of the system. The cost of the
arrangement of the proposed organize framework in the association is given in the report that
would assist the system head with getting the points of interest of the system gadgets utilized and
appraise the financial plan.
1.3. Scope
A different system for the servers are made and the servers are required to be introduced
in a different space for diminishing the danger of physical strike and increment the security of
DATA COMMUNICATION AND NETWORKS
1. Introduction
1.1. Purpose
The purpose of the report is to propose a network for a private biomedical development
organization for obliging the present development of the association along its 2 adjoining three
story structures. The proposed arrange comprises of web server, database servers and appropriate
cabling plan for the substitution of the present system of the association. Remote access point is
likewise required to be introduced in the system for empowering the network of the remote
gadgets of the representatives, for example, ipads, advanced cells and tablets.
1.2. Background
The system is subnetted for various branches and the switches are required to be designed
with VPN for empowering remote association in the system. The adaptability of the system is
investigated and late innovation are utilized for the advancement of the system and handle the
future development of the association. The switches are additionally designed with get to control
list for hindering the unapproved clients to associate with the center system segments, for
example, the servers and database. A legitimate and physical system chart of the system is made
for show of the system segments utilized for the improvement of the system. The cost of the
arrangement of the proposed organize framework in the association is given in the report that
would assist the system head with getting the points of interest of the system gadgets utilized and
appraise the financial plan.
1.3. Scope
A different system for the servers are made and the servers are required to be introduced
in a different space for diminishing the danger of physical strike and increment the security of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
DATA COMMUNICATION AND NETWORKS
the system. A firewall is likewise introduced in the system for expanding the security and screen
the movement of the system (Righi, Saurin and Wachs 2015). For expanding the accessibility of
the system a heap balancer is introduced that would divert the system activity through various
channels and lessen the blockage of the system movement.
2. Requirement Analysis
2.1. Clients of the system and need
The product engineers, web designer and different workers are the principle clients of the
proposed arrange plan and they would get to the system segments from various areas. In this way
the diverse branches are required to be associated to such an extent that the representatives can
speak with each other for expanding the profitability of their work.
2.2. Required data transmission
The clients are portioned into various classes for assignment of the data transfer capacity
of the system to them and diminish the blockage in the system. The principle classes are the
substantial client and the customary clients and the product improvement group and the web
advancement are under the overwhelming clients since they run distinctive application that
creates information movement in the system (Cardoso, Costa and Francês 2015). Diverse vlans
are made for the clients and load balancers are utilized for expanding the productivity of the
system. The direct clients are those having least printing occupations and they are allocated with
various Vlans and distinctive printers for diminishing the holding up time.
2.3. Remote Management
The switches are designed with VPN to such an extent that the remote clients can get to
the hierarchical assets from remote area and increment their profitability. The VPN association is
DATA COMMUNICATION AND NETWORKS
the system. A firewall is likewise introduced in the system for expanding the security and screen
the movement of the system (Righi, Saurin and Wachs 2015). For expanding the accessibility of
the system a heap balancer is introduced that would divert the system activity through various
channels and lessen the blockage of the system movement.
2. Requirement Analysis
2.1. Clients of the system and need
The product engineers, web designer and different workers are the principle clients of the
proposed arrange plan and they would get to the system segments from various areas. In this way
the diverse branches are required to be associated to such an extent that the representatives can
speak with each other for expanding the profitability of their work.
2.2. Required data transmission
The clients are portioned into various classes for assignment of the data transfer capacity
of the system to them and diminish the blockage in the system. The principle classes are the
substantial client and the customary clients and the product improvement group and the web
advancement are under the overwhelming clients since they run distinctive application that
creates information movement in the system (Cardoso, Costa and Francês 2015). Diverse vlans
are made for the clients and load balancers are utilized for expanding the productivity of the
system. The direct clients are those having least printing occupations and they are allocated with
various Vlans and distinctive printers for diminishing the holding up time.
2.3. Remote Management
The switches are designed with VPN to such an extent that the remote clients can get to
the hierarchical assets from remote area and increment their profitability. The VPN association is

5
DATA COMMUNICATION AND NETWORKS
built up utilizing a firewall for expanding the security of the system and moderate the danger of
information adjustment and information theft.
2.4. Necessity of Mobility
For empowering BYOD in the association the portability bolster is required to be
empowered and remote access point is required to be introduced in various area of the building
to such an extent that the representatives can utilize the system for interfacing their gadgets and
continue with the work. The entrance of the network indicates is additionally required be secured
with legitimate encryption calculation to such an extent that unapproved clients does not
approach of the hierarchical system.
3. Analysis and description of the current network
3.1. Circuits
The framework is made with a less response time and cabling plan is required to be used
for supporting huge measure of transmission. Cisco 1900 series routers are utilized for the
transmission of data packets in the network and there is no option of remote accessibility. No
wireless access point are installed in the network for supporting the employees to connect their
devices and laptops in the organizational network. The essential building contains the item
design and the site authority and a colossal measure of movement is made from the building and
therefore there is a need of working up the framework to diminish blockage and handle the
request of the customer gainfully. The switches installed in the network supports VLAN
configuration but it is not configured for reducing the collision of network traffic. Cat 5 cables
joins the different interfaces of the devices used in the network and makes it accessible to the
users.
DATA COMMUNICATION AND NETWORKS
built up utilizing a firewall for expanding the security of the system and moderate the danger of
information adjustment and information theft.
2.4. Necessity of Mobility
For empowering BYOD in the association the portability bolster is required to be
empowered and remote access point is required to be introduced in various area of the building
to such an extent that the representatives can utilize the system for interfacing their gadgets and
continue with the work. The entrance of the network indicates is additionally required be secured
with legitimate encryption calculation to such an extent that unapproved clients does not
approach of the hierarchical system.
3. Analysis and description of the current network
3.1. Circuits
The framework is made with a less response time and cabling plan is required to be used
for supporting huge measure of transmission. Cisco 1900 series routers are utilized for the
transmission of data packets in the network and there is no option of remote accessibility. No
wireless access point are installed in the network for supporting the employees to connect their
devices and laptops in the organizational network. The essential building contains the item
design and the site authority and a colossal measure of movement is made from the building and
therefore there is a need of working up the framework to diminish blockage and handle the
request of the customer gainfully. The switches installed in the network supports VLAN
configuration but it is not configured for reducing the collision of network traffic. Cat 5 cables
joins the different interfaces of the devices used in the network and makes it accessible to the
users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
DATA COMMUNICATION AND NETWORKS
3.2. Hardware
The hardware used for the employees are obsolete and affects the productivity of the
employees. It does not supports virtualization and thus required to be replaced. The router is
required to be upgraded and wireless access points is also required to be installed at all of the
branches for connecting the wireless devices (Zhu, Crainic and Gendreau 2014). The memory
and the processing speed of the employees machine is also required to be increased.
3.3. Topology
3.4. Software
Windows Server 2008 is installed and utilized for the management of the network. Some
of the desktops have free licensed antivirus software’s and other are left unprotected. For
network analysis wireshark is utilized and it is installed on a PC to capture the network traffic
and keep it as an evidence of any kind of attacks.
3.5. Analysis
A genuine and a physical framework diagram is made for the framework and it is
required to be orchestrated with appropriate frameworks organization traditions for dealing with
the request from the customers. The current is required to be upgraded for the settlement of the
more number of centers and workstation in the working environment (Saarman et al. 2013). The
present course of action uses a Hub for trading of the data packs and it is required to be
supplanted with switches and switches for extending the adequacy of the game plan. The present
framework have heaps of degree of progress, there is an essential of execution of the remote
access point on the present framework structure for the difference in the system.
DATA COMMUNICATION AND NETWORKS
3.2. Hardware
The hardware used for the employees are obsolete and affects the productivity of the
employees. It does not supports virtualization and thus required to be replaced. The router is
required to be upgraded and wireless access points is also required to be installed at all of the
branches for connecting the wireless devices (Zhu, Crainic and Gendreau 2014). The memory
and the processing speed of the employees machine is also required to be increased.
3.3. Topology
3.4. Software
Windows Server 2008 is installed and utilized for the management of the network. Some
of the desktops have free licensed antivirus software’s and other are left unprotected. For
network analysis wireshark is utilized and it is installed on a PC to capture the network traffic
and keep it as an evidence of any kind of attacks.
3.5. Analysis
A genuine and a physical framework diagram is made for the framework and it is
required to be orchestrated with appropriate frameworks organization traditions for dealing with
the request from the customers. The current is required to be upgraded for the settlement of the
more number of centers and workstation in the working environment (Saarman et al. 2013). The
present course of action uses a Hub for trading of the data packs and it is required to be
supplanted with switches and switches for extending the adequacy of the game plan. The present
framework have heaps of degree of progress, there is an essential of execution of the remote
access point on the present framework structure for the difference in the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
DATA COMMUNICATION AND NETWORKS
4. Analysis and description of the proposed network
4.1. Circuits
For the development of the proposed network design different technology are analyzed
and applied for increasing the efficiency of the current network of the organization. The main
goals of the network is to increase the productivity of the employees and thus the switches used
in the network solution are layer 2 and is configured with vlans for the different levels of users.
Cat 5 cables of the old network is replaced with the cat 6 cables and the interconnection of the
interfaces of the routers are done with serial cables.
4.2. Hardware
The servers are developed with multi core processors and larger memory to handle more
number of requests generated from the network. The server also supports virtualization that it it
can be virtualized when the load of the network increases and thus makes the proposed network
flexible. Firewall devices are also installed at different points of the network for blocking the
unknown request to reach the servers and increase the security of the network.
4.3. Topology
4.4. Software
Microsoft Windows Server 2010 is used for the development of the servers and Avast
Internet Security is installed on the client and the employee’s machine for compel virus and
spam protection. There are other software required such as Corel premium collection required for
designing software, Turbo Cad deluxe, etc. for increasing the efficiency of the software
developers.
DATA COMMUNICATION AND NETWORKS
4. Analysis and description of the proposed network
4.1. Circuits
For the development of the proposed network design different technology are analyzed
and applied for increasing the efficiency of the current network of the organization. The main
goals of the network is to increase the productivity of the employees and thus the switches used
in the network solution are layer 2 and is configured with vlans for the different levels of users.
Cat 5 cables of the old network is replaced with the cat 6 cables and the interconnection of the
interfaces of the routers are done with serial cables.
4.2. Hardware
The servers are developed with multi core processors and larger memory to handle more
number of requests generated from the network. The server also supports virtualization that it it
can be virtualized when the load of the network increases and thus makes the proposed network
flexible. Firewall devices are also installed at different points of the network for blocking the
unknown request to reach the servers and increase the security of the network.
4.3. Topology
4.4. Software
Microsoft Windows Server 2010 is used for the development of the servers and Avast
Internet Security is installed on the client and the employee’s machine for compel virus and
spam protection. There are other software required such as Corel premium collection required for
designing software, Turbo Cad deluxe, etc. for increasing the efficiency of the software
developers.
8
DATA COMMUNICATION AND NETWORKS
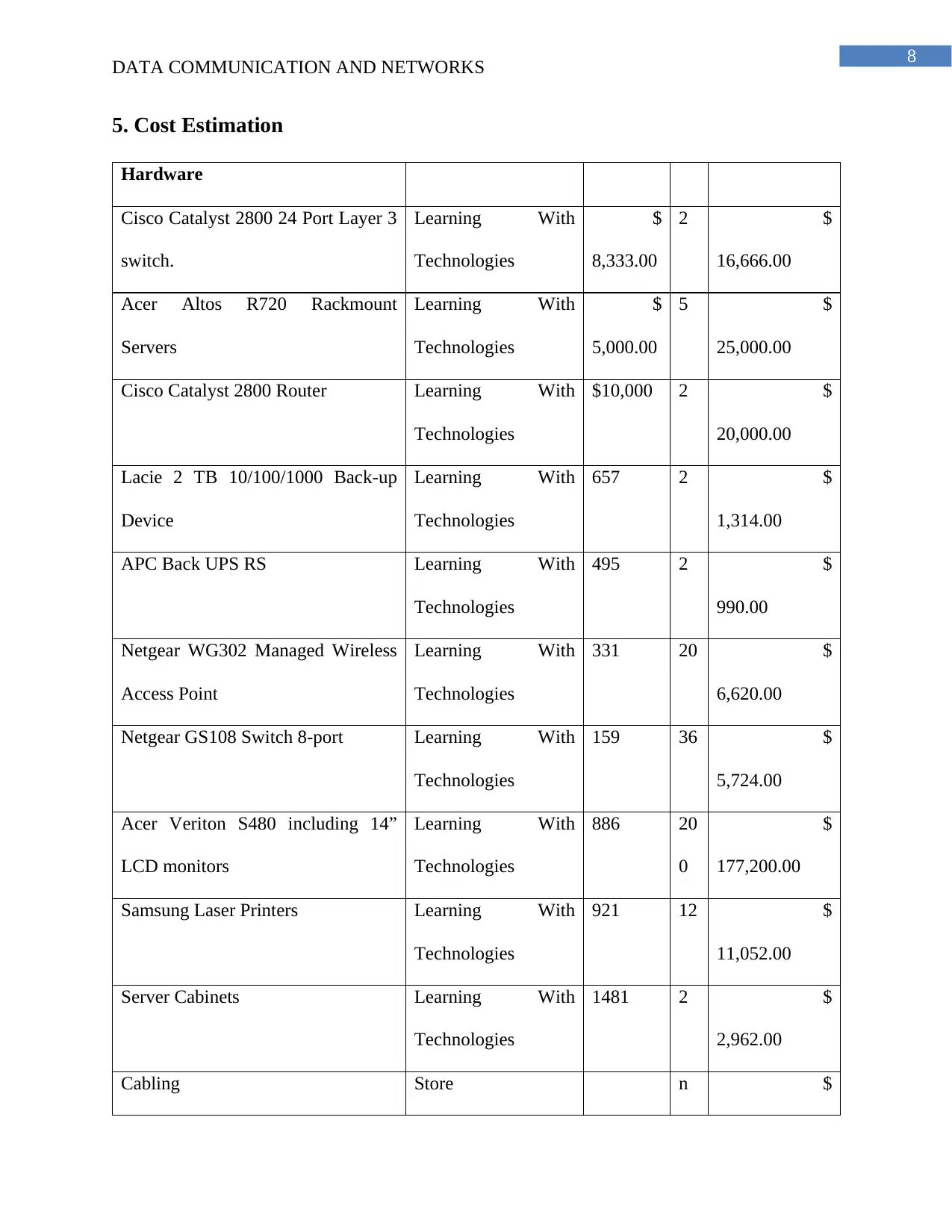
5. Cost Estimation
Hardware
Cisco Catalyst 2800 24 Port Layer 3
switch.
Learning With
Technologies
$
8,333.00
2 $
16,666.00
Acer Altos R720 Rackmount
Servers
Learning With
Technologies
$
5,000.00
5 $
25,000.00
Cisco Catalyst 2800 Router Learning With
Technologies
$10,000 2 $
20,000.00
Lacie 2 TB 10/100/1000 Back-up
Device
Learning With
Technologies
657 2 $
1,314.00
APC Back UPS RS Learning With
Technologies
495 2 $
990.00
Netgear WG302 Managed Wireless
Access Point
Learning With
Technologies
331 20 $
6,620.00
Netgear GS108 Switch 8-port Learning With
Technologies
159 36 $
5,724.00
Acer Veriton S480 including 14”
LCD monitors
Learning With
Technologies
886 20
0
$
177,200.00
Samsung Laser Printers Learning With
Technologies
921 12 $
11,052.00
Server Cabinets Learning With
Technologies
1481 2 $
2,962.00
Cabling Store n $
DATA COMMUNICATION AND NETWORKS
5. Cost Estimation
Hardware
Cisco Catalyst 2800 24 Port Layer 3
switch.
Learning With
Technologies
$
8,333.00
2 $
16,666.00
Acer Altos R720 Rackmount
Servers
Learning With
Technologies
$
5,000.00
5 $
25,000.00
Cisco Catalyst 2800 Router Learning With
Technologies
$10,000 2 $
20,000.00
Lacie 2 TB 10/100/1000 Back-up
Device
Learning With
Technologies
657 2 $
1,314.00
APC Back UPS RS Learning With
Technologies
495 2 $
990.00
Netgear WG302 Managed Wireless
Access Point
Learning With
Technologies
331 20 $
6,620.00
Netgear GS108 Switch 8-port Learning With
Technologies
159 36 $
5,724.00
Acer Veriton S480 including 14”
LCD monitors
Learning With
Technologies
886 20
0
$
177,200.00
Samsung Laser Printers Learning With
Technologies
921 12 $
11,052.00
Server Cabinets Learning With
Technologies
1481 2 $
2,962.00
Cabling Store n $
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
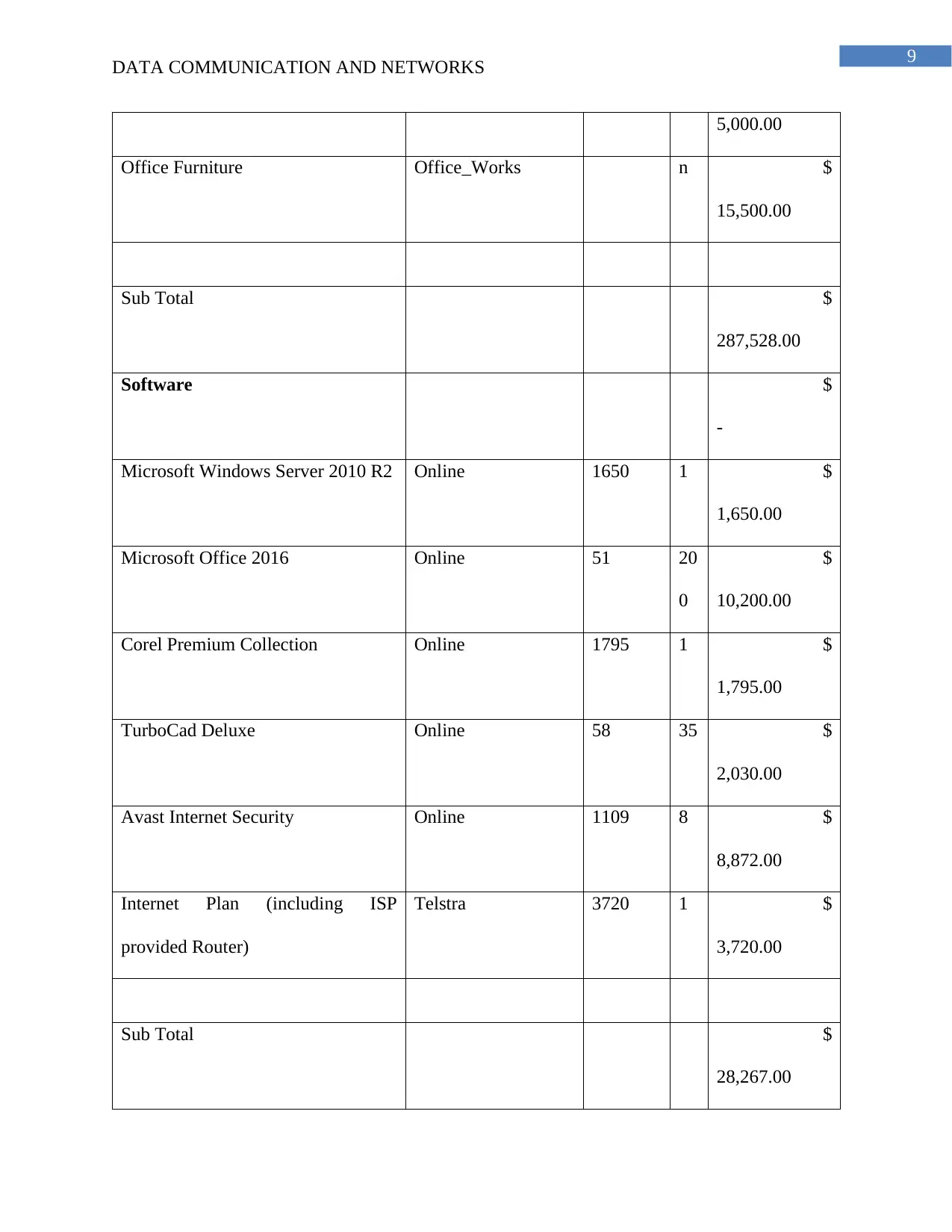
DATA COMMUNICATION AND NETWORKS
5,000.00
Office Furniture Office_Works n $
15,500.00
Sub Total $
287,528.00
Software $
-
Microsoft Windows Server 2010 R2 Online 1650 1 $
1,650.00
Microsoft Office 2016 Online 51 20
0
$
10,200.00
Corel Premium Collection Online 1795 1 $
1,795.00
TurboCad Deluxe Online 58 35 $
2,030.00
Avast Internet Security Online 1109 8 $
8,872.00
Internet Plan (including ISP
provided Router)
Telstra 3720 1 $
3,720.00
Sub Total $
28,267.00
DATA COMMUNICATION AND NETWORKS
5,000.00
Office Furniture Office_Works n $
15,500.00
Sub Total $
287,528.00
Software $
-
Microsoft Windows Server 2010 R2 Online 1650 1 $
1,650.00
Microsoft Office 2016 Online 51 20
0
$
10,200.00
Corel Premium Collection Online 1795 1 $
1,795.00
TurboCad Deluxe Online 58 35 $
2,030.00
Avast Internet Security Online 1109 8 $
8,872.00
Internet Plan (including ISP
provided Router)
Telstra 3720 1 $
3,720.00
Sub Total $
28,267.00
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
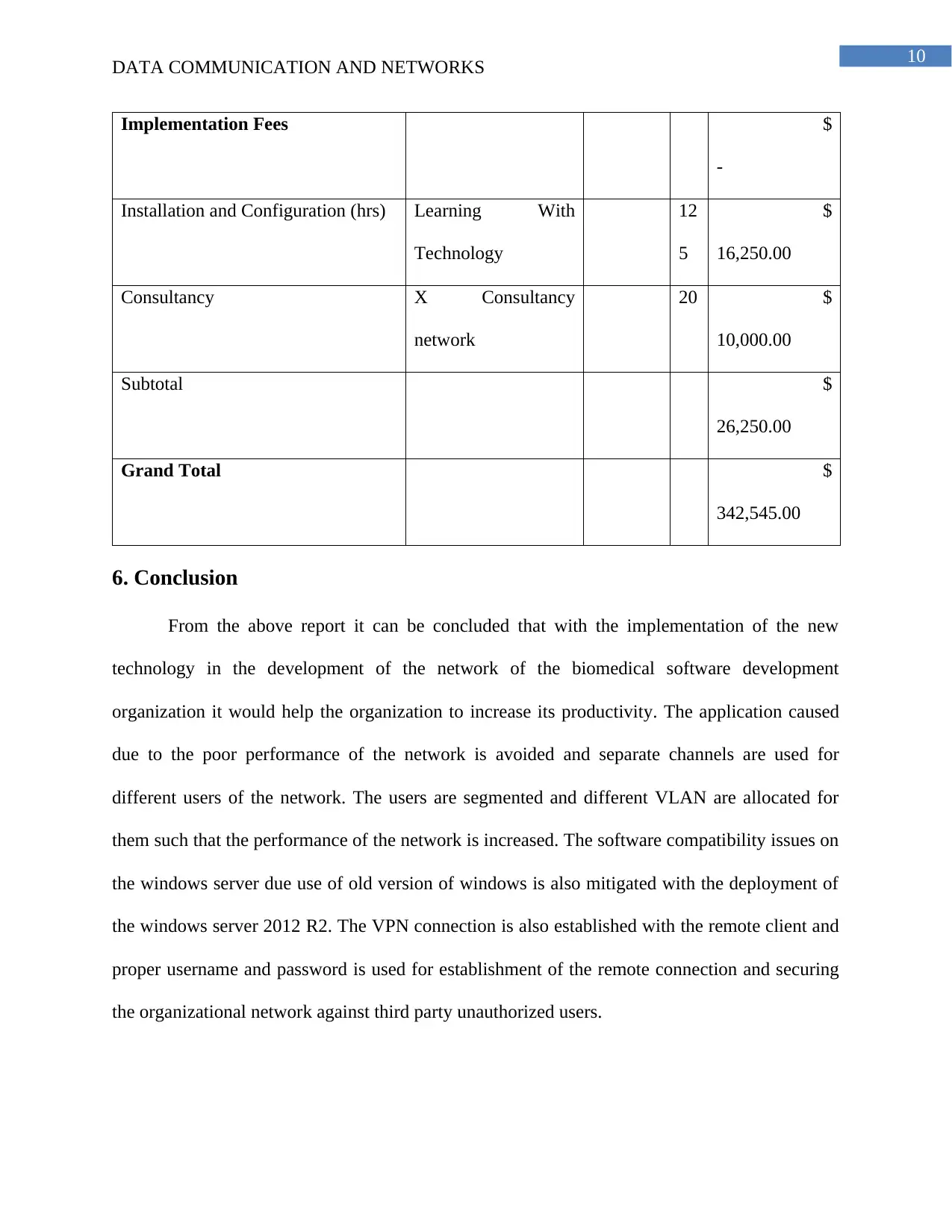
DATA COMMUNICATION AND NETWORKS
Implementation Fees $
-
Installation and Configuration (hrs) Learning With
Technology
12
5
$
16,250.00
Consultancy X Consultancy
network
20 $
10,000.00
Subtotal $
26,250.00
Grand Total $
342,545.00
6. Conclusion
From the above report it can be concluded that with the implementation of the new
technology in the development of the network of the biomedical software development
organization it would help the organization to increase its productivity. The application caused
due to the poor performance of the network is avoided and separate channels are used for
different users of the network. The users are segmented and different VLAN are allocated for
them such that the performance of the network is increased. The software compatibility issues on
the windows server due use of old version of windows is also mitigated with the deployment of
the windows server 2012 R2. The VPN connection is also established with the remote client and
proper username and password is used for establishment of the remote connection and securing
the organizational network against third party unauthorized users.
DATA COMMUNICATION AND NETWORKS
Implementation Fees $
-
Installation and Configuration (hrs) Learning With
Technology
12
5
$
16,250.00
Consultancy X Consultancy
network
20 $
10,000.00
Subtotal $
26,250.00
Grand Total $
342,545.00
6. Conclusion
From the above report it can be concluded that with the implementation of the new
technology in the development of the network of the biomedical software development
organization it would help the organization to increase its productivity. The application caused
due to the poor performance of the network is avoided and separate channels are used for
different users of the network. The users are segmented and different VLAN are allocated for
them such that the performance of the network is increased. The software compatibility issues on
the windows server due use of old version of windows is also mitigated with the deployment of
the windows server 2012 R2. The VPN connection is also established with the remote client and
proper username and password is used for establishment of the remote connection and securing
the organizational network against third party unauthorized users.

11
DATA COMMUNICATION AND NETWORKS
7. Recommendations
The VPN connection is required to be established using a tunneling infrastructure
and the main backbone of the network should be fiber optic connection
Layer 3 switches can be used increasing the scalability and performance of the
VLAN management of the network
A high end server is required to be used instead of multiple server for reduction of
the storage issues and compatibility issues
The VPN connection is required to pass through firewall for blocking the
unknown request to reach the organizational network
DATA COMMUNICATION AND NETWORKS
7. Recommendations
The VPN connection is required to be established using a tunneling infrastructure
and the main backbone of the network should be fiber optic connection
Layer 3 switches can be used increasing the scalability and performance of the
VLAN management of the network
A high end server is required to be used instead of multiple server for reduction of
the storage issues and compatibility issues
The VPN connection is required to pass through firewall for blocking the
unknown request to reach the organizational network
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





