Data Communication Analysis: 3-way Handshake and DNS in Wireshark
VerifiedAdded on 2022/08/25
|6
|792
|46
Homework Assignment
AI Summary
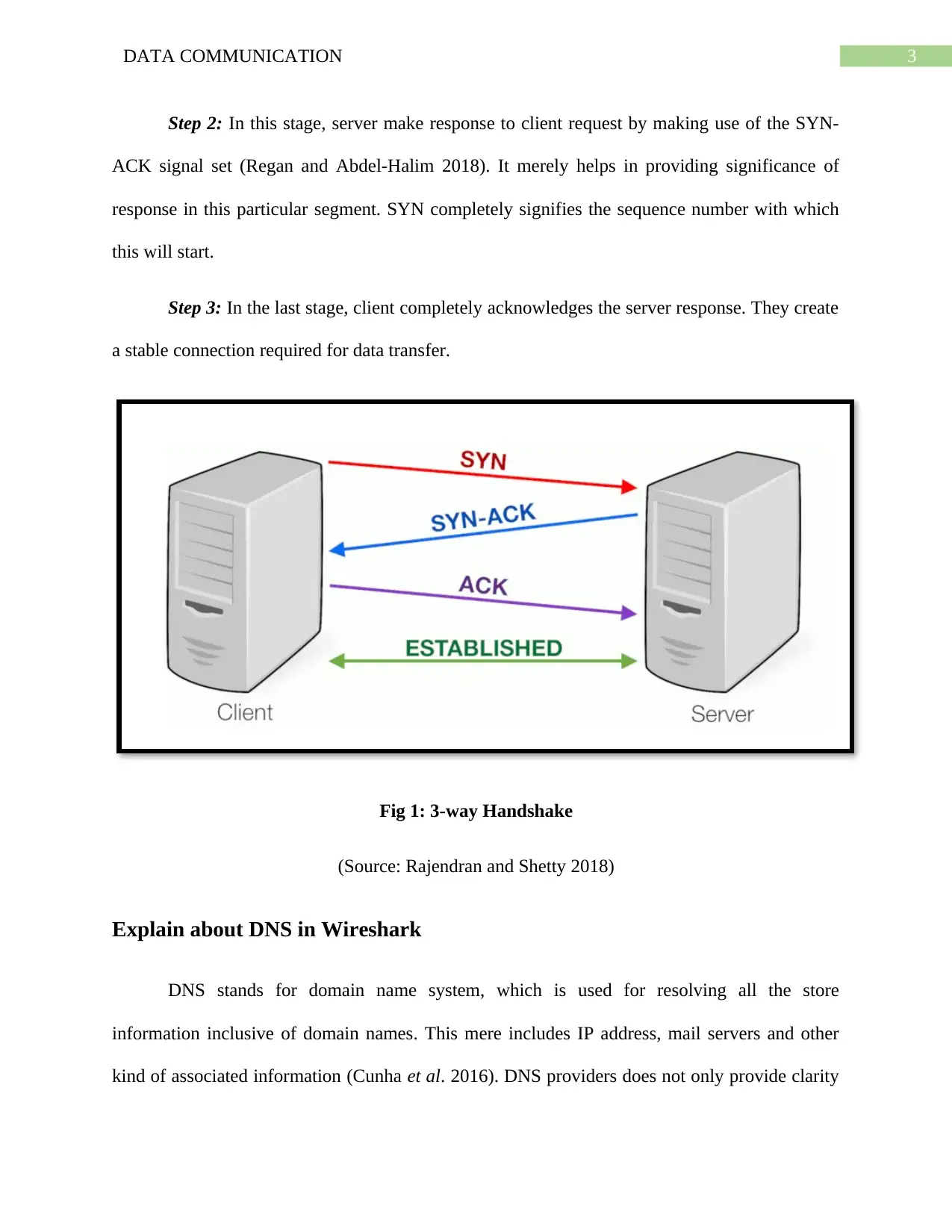
This assignment solution delves into the core concepts of data communication, specifically focusing on the 3-way handshake and DNS (Domain Name System) protocols as observed and analyzed within the Wireshark network analyzer. The solution thoroughly explains the 3-way handshake process, which is crucial for establishing TCP/IP connections, detailing each step of the client-server interaction (SYN, SYN-ACK, ACK) and its role in ensuring reliable data transfer. Furthermore, the assignment explores the functionality of DNS, including its role in resolving domain names to IP addresses and facilitating communication across networks. The solution also includes references to relevant academic sources. The assignment is aimed at providing a comprehensive understanding of these fundamental networking concepts, illustrating how they operate in a real-world scenario using Wireshark.
1 out of 6









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)