Data Encryption Standard (DES) and Advanced Encryption Standard (AES): A Comparative Analysis
VerifiedAdded on 2024/06/04
|19
|4600
|365
AI Summary
This report provides a comprehensive analysis of the Data Encryption Standard (DES) and the Advanced Encryption Standard (AES), two widely used symmetric-key encryption algorithms. It delves into the history, structure, and working principles of both algorithms, highlighting their strengths and weaknesses. The report also examines the security vulnerabilities of DES and the advancements made by AES in addressing these vulnerabilities. Finally, it concludes with a comparison of the two algorithms and their suitability for modern cryptographic applications.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Assessment 3
Data Encryption Standard (DES) and Advanced Encryption Standard
(AES)
Data Encryption Standard (DES) and Advanced Encryption Standard
(AES)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Executive Summary
The following report is regarding critical analysis and literature review of DES (Data
Encryption Standard) and AES (Advanced Encryption Standard). In the Standard of Data
Encryption, a brief introduction is given about what it actually is and followed by a
description of its structure and what all processes are involved in its working. Then the
security related issues and attacks are also discussed regarding DES algorithm. In the
Advanced Encryption Standard (AES) a brief introduction is given along with the description
of the algorithm and processes involved, followed by security issues. At last, the report is
concluded with various conclusions that came up while making the report.
1
The following report is regarding critical analysis and literature review of DES (Data
Encryption Standard) and AES (Advanced Encryption Standard). In the Standard of Data
Encryption, a brief introduction is given about what it actually is and followed by a
description of its structure and what all processes are involved in its working. Then the
security related issues and attacks are also discussed regarding DES algorithm. In the
Advanced Encryption Standard (AES) a brief introduction is given along with the description
of the algorithm and processes involved, followed by security issues. At last, the report is
concluded with various conclusions that came up while making the report.
1

Table of Contents
Executive Summary....................................................................................................................1
Data Encryption Standard..........................................................................................................3
Introduction...........................................................................................................................3
History................................................................................................................................3
Description.........................................................................................................................4
Structure of DES and Process of Algorithm.........................................................................5
Methods and function for security............................................................................................6
Security and cryptanalysis......................................................................................................9
Advanced Encryption Standard (AES)......................................................................................10
Introduction.........................................................................................................................10
Description...............................................................................................................................10
Optimization of the cipher.......................................................................................................12
Cryptography technology for Security.....................................................................................13
Conclusion................................................................................................................................15
References................................................................................................................................17
2
Executive Summary....................................................................................................................1
Data Encryption Standard..........................................................................................................3
Introduction...........................................................................................................................3
History................................................................................................................................3
Description.........................................................................................................................4
Structure of DES and Process of Algorithm.........................................................................5
Methods and function for security............................................................................................6
Security and cryptanalysis......................................................................................................9
Advanced Encryption Standard (AES)......................................................................................10
Introduction.........................................................................................................................10
Description...............................................................................................................................10
Optimization of the cipher.......................................................................................................12
Cryptography technology for Security.....................................................................................13
Conclusion................................................................................................................................15
References................................................................................................................................17
2

Data Encryption Standard
Introduction
The systematic key algorithm is used intended for data encryption of electronic data which
is called data encryption standard or DES. It has a great influence on the advancement of
modern cryptology despite being insecure in nature. It was urbanized at IBM in the near the
beginning of the 1970s. Its design was the foundation on an earlier design given by Horst
Feistel. In response to an invitation to offer an algorithm to protect and safeguard
unclassified and sensitive data, this algorithm is proposed to National Bureau of Standards
(NBS). Later in 1977 a slightly advanced version of it was selected for implementation and
was in print as a representative Federal Information Processing Standard (FIPS) for the
United States. This data encryption arrangement is insecure in nature. The major cause for
this its key size which is very small, only 52-bit. Some analytical results show that
theoretically, the cipher is weak. Practically, the algorithm is safe in the form of DES;
however, there is some conjectural assault This is the reason why that, later on, DES was
removed as a standard by the National Institute of Standards and Technology and that is
why some documentation refers it to as DEA (Data Encryption Algorithm) and not DES, not
considering it as a standard anymore (Thirumalai, 2016).
History
The Data Encryption Standard (DES) originated in the early 1970s. In the year 1972, in
response to an invitation to offer an algorithm to protect and safeguard unclassified and
sensitive government data this algorithm was proposed to National Bureau of Standards
(NBS) which is now termed as National Institute of Standards and Technology (NIST). Later
on, IBM developed a cipher between 1973 and 1974 that was on the basis of on a previous
algorithm, Horst Feistel’s Lucifer cipher. It was very much accepted. The NSA’s involvement
in the design was also considered to be a huge issue (Support.symantec, 2017). The notion
was that the algorithm was secretly damaged by the cleverness organization so that they
could read the encrypted messages. However, later on, it was found that there was no
tempering of design by NSA and the design was wholly invented and designed by IBM and
all the decisions regarding the design were made by IBM only including the key size.
According to IBM, the key size allotted to the algorithm was more than sufficient for all the
3
Introduction
The systematic key algorithm is used intended for data encryption of electronic data which
is called data encryption standard or DES. It has a great influence on the advancement of
modern cryptology despite being insecure in nature. It was urbanized at IBM in the near the
beginning of the 1970s. Its design was the foundation on an earlier design given by Horst
Feistel. In response to an invitation to offer an algorithm to protect and safeguard
unclassified and sensitive data, this algorithm is proposed to National Bureau of Standards
(NBS). Later in 1977 a slightly advanced version of it was selected for implementation and
was in print as a representative Federal Information Processing Standard (FIPS) for the
United States. This data encryption arrangement is insecure in nature. The major cause for
this its key size which is very small, only 52-bit. Some analytical results show that
theoretically, the cipher is weak. Practically, the algorithm is safe in the form of DES;
however, there is some conjectural assault This is the reason why that, later on, DES was
removed as a standard by the National Institute of Standards and Technology and that is
why some documentation refers it to as DEA (Data Encryption Algorithm) and not DES, not
considering it as a standard anymore (Thirumalai, 2016).
History
The Data Encryption Standard (DES) originated in the early 1970s. In the year 1972, in
response to an invitation to offer an algorithm to protect and safeguard unclassified and
sensitive government data this algorithm was proposed to National Bureau of Standards
(NBS) which is now termed as National Institute of Standards and Technology (NIST). Later
on, IBM developed a cipher between 1973 and 1974 that was on the basis of on a previous
algorithm, Horst Feistel’s Lucifer cipher. It was very much accepted. The NSA’s involvement
in the design was also considered to be a huge issue (Support.symantec, 2017). The notion
was that the algorithm was secretly damaged by the cleverness organization so that they
could read the encrypted messages. However, later on, it was found that there was no
tempering of design by NSA and the design was wholly invented and designed by IBM and
all the decisions regarding the design were made by IBM only including the key size.
According to IBM, the key size allotted to the algorithm was more than sufficient for all the
3
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

commercial applications. In 1773, NSA began working on its own algorithm. The IBM and
NSA effort intimately to make the algorithm stronger alongside all the assaults. Later on, the
size of the algorithm was brought down to a 56-bit key.
The DES, despite all the criticisms, was accepted as a federal standard in 1976 and in 1977
was authorized for utilizing on all the unstipulated data. It was revised again at various
occasions in the years 1983, 1988, 1993 and 1999. In 2002, the Data Encryption Standard
was at last superseded by AES (Advanced Encryption Standard) and in 2005 it was officially
withdrawn as a standard.
Description
In the study of cryptology, particularly the study of methods of cracking block ciphers, the
Data Encryption Standard (DES) algorithm has proved to be a catalyst. It initiated the
development of encrypted algorithms. Before its introduction, there were very
cryptographers and the study of cryptography was also not very advanced. But now, this is
not the case. The number of cryptographers has increased tremendously and is developing
strong programs in cryptology and working for the information security of the companies.
The DES is considered to be a standard against every symmetric key algorithm (Pukkawanna,
2014).
4
NSA effort intimately to make the algorithm stronger alongside all the assaults. Later on, the
size of the algorithm was brought down to a 56-bit key.
The DES, despite all the criticisms, was accepted as a federal standard in 1976 and in 1977
was authorized for utilizing on all the unstipulated data. It was revised again at various
occasions in the years 1983, 1988, 1993 and 1999. In 2002, the Data Encryption Standard
was at last superseded by AES (Advanced Encryption Standard) and in 2005 it was officially
withdrawn as a standard.
Description
In the study of cryptology, particularly the study of methods of cracking block ciphers, the
Data Encryption Standard (DES) algorithm has proved to be a catalyst. It initiated the
development of encrypted algorithms. Before its introduction, there were very
cryptographers and the study of cryptography was also not very advanced. But now, this is
not the case. The number of cryptographers has increased tremendously and is developing
strong programs in cryptology and working for the information security of the companies.
The DES is considered to be a standard against every symmetric key algorithm (Pukkawanna,
2014).
4
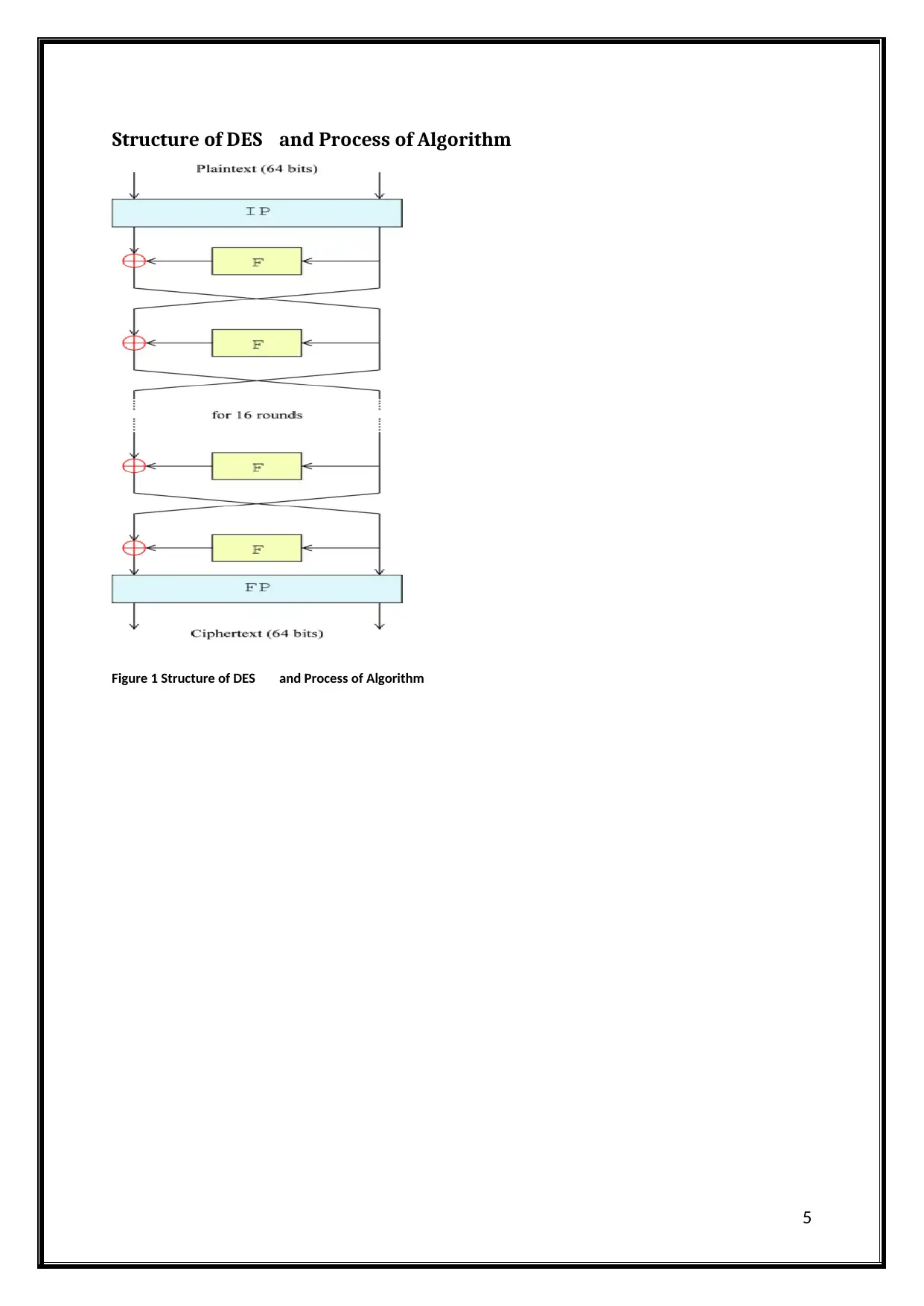
Structure of DES and Process of Algorithm
Figure 1 Structure of DES and Process of Algorithm
5
Figure 1 Structure of DES and Process of Algorithm
5

Methods and function for security
There are a total of 16 identical stages of processing. The preliminary variation is termed as
IP and the last permutation is termed as FP. They both are inverses to each other that mean
the task of IP is to undo the act of FP and vice versa. Although there is no cryptographic
implication of IP and FP they are added to make easy the loading of blocks in and out of 8-
bit hardware.
The piece is secluded into 32-bit segments before the essential round and dealt with then
again. This scrambling is recognized as the Feistel scheme. In the Feistel structure, the
unscrambling procedure resembles encryption. The key qualification is that in the
translating procedure the subkeys are connected in reverse demand. Whatever is left of the
figuring is equivalent so there is no prerequisite for disengaged counts for decryption &
encryption. The ⊕ photo shows the pick OR (XOR) venture. F-artistic creations join up a
huge piece of a square with a piece of the implemented key. F-words of art is from the yield
that is joined through the contrary piece of square, & the components are swapped sooner
than the ensuing circular. After last round, the segments are swapped; the defined segment
is a piece of the Feistel shape that generates the encryption and also unscrambling
comparable strategies (Rashidi, 2017).
The Feistel (F) function
Figure 2 The Feistel (F) function
6
There are a total of 16 identical stages of processing. The preliminary variation is termed as
IP and the last permutation is termed as FP. They both are inverses to each other that mean
the task of IP is to undo the act of FP and vice versa. Although there is no cryptographic
implication of IP and FP they are added to make easy the loading of blocks in and out of 8-
bit hardware.
The piece is secluded into 32-bit segments before the essential round and dealt with then
again. This scrambling is recognized as the Feistel scheme. In the Feistel structure, the
unscrambling procedure resembles encryption. The key qualification is that in the
translating procedure the subkeys are connected in reverse demand. Whatever is left of the
figuring is equivalent so there is no prerequisite for disengaged counts for decryption &
encryption. The ⊕ photo shows the pick OR (XOR) venture. F-artistic creations join up a
huge piece of a square with a piece of the implemented key. F-words of art is from the yield
that is joined through the contrary piece of square, & the components are swapped sooner
than the ensuing circular. After last round, the segments are swapped; the defined segment
is a piece of the Feistel shape that generates the encryption and also unscrambling
comparable strategies (Rashidi, 2017).
The Feistel (F) function
Figure 2 The Feistel (F) function
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

This F-function as given away in the given above figure that describes the works on the half
block (32 bits) during the performing time. It divided into four stages:
Extension This spreading out incarnation is used to expand the 48 bit with 32 bit half
block by reproduction half of its bits. After completing the task it contains the output
as eight 6 bit pieces. Every piece contains a corresponding 4 bits as input and a copy
of the adjacent bit from each input piece on either side.
Key-mixing- Using the operation XOR the result is combined with a subkey. 16
subkeys of 48 bit from each round are derived using a key schedule from the main
key.
Substitution- The block is divided after socializing in the substituting subkey into 6-
bit eight pieces before being processed by substitution containers. Every substitution
box or S-box changes its input six bits according to four output bits non-linear
alteration. The substitution boxes are considered the core of security for DES and in
their absence, the cipher would be trivially breakable and linear.
Permutation-Finally, there is a rearrangement of all the 32 outputs according to the
P-box or the fixed permutation. This is created so that, after degree, the bits from
the yield of each S-band this round are spread transversely more than four
extraordinary S-encases the ensuing circular (Liu, 2013).
The variant of unused data from S-boxes or exchange bits from the E-change and P-field
offers expected "perplexity and scattering" in my view, an idea perceived by a method for
Claude Shannon inside the Nineteen Forties as a key situation for a safe yet reachable
recognize.
The key list
7
block (32 bits) during the performing time. It divided into four stages:
Extension This spreading out incarnation is used to expand the 48 bit with 32 bit half
block by reproduction half of its bits. After completing the task it contains the output
as eight 6 bit pieces. Every piece contains a corresponding 4 bits as input and a copy
of the adjacent bit from each input piece on either side.
Key-mixing- Using the operation XOR the result is combined with a subkey. 16
subkeys of 48 bit from each round are derived using a key schedule from the main
key.
Substitution- The block is divided after socializing in the substituting subkey into 6-
bit eight pieces before being processed by substitution containers. Every substitution
box or S-box changes its input six bits according to four output bits non-linear
alteration. The substitution boxes are considered the core of security for DES and in
their absence, the cipher would be trivially breakable and linear.
Permutation-Finally, there is a rearrangement of all the 32 outputs according to the
P-box or the fixed permutation. This is created so that, after degree, the bits from
the yield of each S-band this round are spread transversely more than four
extraordinary S-encases the ensuing circular (Liu, 2013).
The variant of unused data from S-boxes or exchange bits from the E-change and P-field
offers expected "perplexity and scattering" in my view, an idea perceived by a method for
Claude Shannon inside the Nineteen Forties as a key situation for a safe yet reachable
recognize.
The key list
7

Figure 3The key list
The key schedule is the count that makes subkeys for encryption. At to begin with, from the
basic 64 bits by utilizing Permuted Choice 56 bits are picked. These bits are then isolated
into 28-bits components. These components are freely dealt with. In the accompanying
rounds, the parts are developed to end up nearer to one side with the guise or possibly a
couple changes which may be demonstrated for each round. After this, forty-eight subkey
bits are picked with the help of Permuted Choice 2. The forty-eight bits are isolated into
parts i.E. Left and right, 24 bits each. Each piece is used as a major aspect of cycle 14 out of
the sixteen subkeys. For unscrambling the key timetable is comparable anyway it is in
reverse demand (Lu, 2002).
8
The key schedule is the count that makes subkeys for encryption. At to begin with, from the
basic 64 bits by utilizing Permuted Choice 56 bits are picked. These bits are then isolated
into 28-bits components. These components are freely dealt with. In the accompanying
rounds, the parts are developed to end up nearer to one side with the guise or possibly a
couple changes which may be demonstrated for each round. After this, forty-eight subkey
bits are picked with the help of Permuted Choice 2. The forty-eight bits are isolated into
parts i.E. Left and right, 24 bits each. Each piece is used as a major aspect of cycle 14 out of
the sixteen subkeys. For unscrambling the key timetable is comparable anyway it is in
reverse demand (Lu, 2002).
8

Security and cryptanalysis
The most practical attack to the DES algorithm till date is brute-force approach. Other than
that, three other theoretical attacks are possible.
Brute-force attack
The brute-force attack is the most basic attack for any cipher. The feasibility approach
should be determined by the range of key which also establishes the number of keys
probably. In order to fit a chip, DES algorithm was reduced the key size from 128 bits to 56
bits. In the coming years since the development of DES algorithm, the development of the
DES cracking techniques also advanced taking lesser and lesser time to crack the message
from DES. The DES was delicate in preparation as well as in theory (Rashidi, 2017).
Faster Attacks as a comparison to the brute force
Here defined 3 type’s attacks that are capable of breaking complete DES 16 rounds that is
less complex as comparison to brute-force. These are:
Differential cryptanalysis
Davies’ attack
Linear cryptanalysis
All these attacks and threats are academic in nature and are careful to be infeasible in
preparation. The other term used for such type attacks is certification weaknesses.
Differential Cryptanalysis- Cryptanalysis attack is discovered by Eli Biham and Adi
Shamir in the late 1980s. It requires 247 select plaintexts to interrupt all the 16
rounds of the algorithm.
Linear Cryptanalysis- The linear cryptanalysis attack was discovered by Mitsuru
Matsui in the year 1993. It requires 243 known plaintexts to break all the 16 rounds
of the algorithm.
Improved Davies’ Attack- The improved Davies’ attack was discovered by Donald
Davies in the 1980s. This attack is exclusively a specialized technique for DES while
the other attacks are general techniques. It requires 250 plaintexts to break all the
16 rounds of the algorithm and has a success rate of 51% (Pereira, 2016).
9
The most practical attack to the DES algorithm till date is brute-force approach. Other than
that, three other theoretical attacks are possible.
Brute-force attack
The brute-force attack is the most basic attack for any cipher. The feasibility approach
should be determined by the range of key which also establishes the number of keys
probably. In order to fit a chip, DES algorithm was reduced the key size from 128 bits to 56
bits. In the coming years since the development of DES algorithm, the development of the
DES cracking techniques also advanced taking lesser and lesser time to crack the message
from DES. The DES was delicate in preparation as well as in theory (Rashidi, 2017).
Faster Attacks as a comparison to the brute force
Here defined 3 type’s attacks that are capable of breaking complete DES 16 rounds that is
less complex as comparison to brute-force. These are:
Differential cryptanalysis
Davies’ attack
Linear cryptanalysis
All these attacks and threats are academic in nature and are careful to be infeasible in
preparation. The other term used for such type attacks is certification weaknesses.
Differential Cryptanalysis- Cryptanalysis attack is discovered by Eli Biham and Adi
Shamir in the late 1980s. It requires 247 select plaintexts to interrupt all the 16
rounds of the algorithm.
Linear Cryptanalysis- The linear cryptanalysis attack was discovered by Mitsuru
Matsui in the year 1993. It requires 243 known plaintexts to break all the 16 rounds
of the algorithm.
Improved Davies’ Attack- The improved Davies’ attack was discovered by Donald
Davies in the 1980s. This attack is exclusively a specialized technique for DES while
the other attacks are general techniques. It requires 250 plaintexts to break all the
16 rounds of the algorithm and has a success rate of 51% (Pereira, 2016).
9
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Advanced Encryption Standard (AES)
Introduction
The AES (Advanced Encryption Standard) is devotion for encrypting data of computerized
records that set up through the U.S. (National Institute of Standards and Technology (NIST))
in 2001. It is a division of Rijndael assume that moved toward becoming made by means of
Vincent Rijmen and Joan Daemen, two Belgian cryptographers. An astonishing arrangement
of figures goes underneath Rijndael of various sizes of square and key. For AES, the NIST is
picked three individuals through the Rijndael hold family, with each piece of length of 128
bits, and the 3 particular key lengths: 192, 128, & 256 bits. Now, AES has been gotten and
used the overworld. It succeeds to implement the DES (Data Encryption Standard) that is
ends up administered since 1977. The portrayed computation by means of AES is the
estimation of symmetric-key. This infers for both encoding and unscrambling the data a
practically identical mystery's connected. In the US, on November 26, 2001, AES
transformed into pronounced with the guide of the NIST as U.S. Government Information
Processing Standard 197 (FIPS 197). After the affirmation inside the yr 2002, it wound up
practical as an administration standard and was avowed by Commerce Security. AES is fused
into the ISO/IEC 18033-3 well known. AES has to be had in a sizeable degree of diverse
packages of encryption and it is the essential and the first shamelessly open decide this is
permitted by the NSA (National Security Agency) for top spine chiller insights while
connected as a major aspect of a NSA suggested cryptographic (Rashidi, 2017).
Description
The Advanced Encryption Standard depends upon on the rule of the substitution-level plan.
This mix of substitution and alterations is short in each programming and also hardware.
AES, now not exactly like its harbinger DES, does now not make utilization of a Feistel
orchestrate. AES has a choice of Rijndael and has an established 128 bits which are
rectangular in size, and a key size of 192, 128, or 256 bits. As against that, the Rijndael
requirement is real with a bit and sizes of the key that should be several of 32 bits, through
as a base 128 and a most extreme extraordinary with 256 bits.
10
Introduction
The AES (Advanced Encryption Standard) is devotion for encrypting data of computerized
records that set up through the U.S. (National Institute of Standards and Technology (NIST))
in 2001. It is a division of Rijndael assume that moved toward becoming made by means of
Vincent Rijmen and Joan Daemen, two Belgian cryptographers. An astonishing arrangement
of figures goes underneath Rijndael of various sizes of square and key. For AES, the NIST is
picked three individuals through the Rijndael hold family, with each piece of length of 128
bits, and the 3 particular key lengths: 192, 128, & 256 bits. Now, AES has been gotten and
used the overworld. It succeeds to implement the DES (Data Encryption Standard) that is
ends up administered since 1977. The portrayed computation by means of AES is the
estimation of symmetric-key. This infers for both encoding and unscrambling the data a
practically identical mystery's connected. In the US, on November 26, 2001, AES
transformed into pronounced with the guide of the NIST as U.S. Government Information
Processing Standard 197 (FIPS 197). After the affirmation inside the yr 2002, it wound up
practical as an administration standard and was avowed by Commerce Security. AES is fused
into the ISO/IEC 18033-3 well known. AES has to be had in a sizeable degree of diverse
packages of encryption and it is the essential and the first shamelessly open decide this is
permitted by the NSA (National Security Agency) for top spine chiller insights while
connected as a major aspect of a NSA suggested cryptographic (Rashidi, 2017).
Description
The Advanced Encryption Standard depends upon on the rule of the substitution-level plan.
This mix of substitution and alterations is short in each programming and also hardware.
AES, now not exactly like its harbinger DES, does now not make utilization of a Feistel
orchestrate. AES has a choice of Rijndael and has an established 128 bits which are
rectangular in size, and a key size of 192, 128, or 256 bits. As against that, the Rijndael
requirement is real with a bit and sizes of the key that should be several of 32 bits, through
as a base 128 and a most extreme extraordinary with 256 bits.
10

AES wears down a 4 × four area genuine demand framework of bytes which is named on the
grounds that the nation. Scarcely any adjustments of Rijndael have an additional square
length and highlight additional areas in the country. Basically, AES figuring are done in a
chosen limited teach (Lu, 2002).
The figure of recurrences of alteration rounds is stated by the size of the key that is used for
the algorithm of AES. It converts the input into output. The converted input is named the
plaintext and the converted final output is named as ciphertext. The cycle’s number of
repetition is followed as:
o 12 cycles of repetition for 192-bit keys,
o 10 cycles of repetition for 128-bit keys,
o 14 cycles of repetition for 256-bit keys,
Every round contains numerous steps of processing. Every round contains 4 identical but
dissimilar stages, and it is including one that trusts the key of encryption itself. In order to
convert ciphertext spinal into the unique plaintext, reverse rounds of the set are applied
through the help of the similar encryption key (Jiang, 2016).
An algorithm with a high-level description
Key Expansions- These circular keys that are derived from the key of the cipher
which is using a key schedule of Rijndael.
Initial round
o AddRoundKey- Every bite of the state is joined with a block of round key
using bitwise XOR.
Next rounds
o SubBytes
o MixedColumns
o ShiftRows
o AddRoundKeys
Final round
o SubBytes
11
grounds that the nation. Scarcely any adjustments of Rijndael have an additional square
length and highlight additional areas in the country. Basically, AES figuring are done in a
chosen limited teach (Lu, 2002).
The figure of recurrences of alteration rounds is stated by the size of the key that is used for
the algorithm of AES. It converts the input into output. The converted input is named the
plaintext and the converted final output is named as ciphertext. The cycle’s number of
repetition is followed as:
o 12 cycles of repetition for 192-bit keys,
o 10 cycles of repetition for 128-bit keys,
o 14 cycles of repetition for 256-bit keys,
Every round contains numerous steps of processing. Every round contains 4 identical but
dissimilar stages, and it is including one that trusts the key of encryption itself. In order to
convert ciphertext spinal into the unique plaintext, reverse rounds of the set are applied
through the help of the similar encryption key (Jiang, 2016).
An algorithm with a high-level description
Key Expansions- These circular keys that are derived from the key of the cipher
which is using a key schedule of Rijndael.
Initial round
o AddRoundKey- Every bite of the state is joined with a block of round key
using bitwise XOR.
Next rounds
o SubBytes
o MixedColumns
o ShiftRows
o AddRoundKeys
Final round
o SubBytes
11

o AddRoundKey
o ShiftRows
The ShifrRows step
The ShiftRows step wears down on the strains of the kingdom. It activities the bytes in each
line through a couple of offset. The essential line, in any case, proceeds as sooner than in
AES. Every bite of the second line is moved one to 1 perspective and inside the equivalent
way, the 0.33 and fourth follows are moved by methods for parties of and 3 independently.
The moving case is equivalent for piece sizes 192 bits and 128 bits. Section n is moved left
round through n-1 bytes. In a similar way, each area of the yield country is created from
bytes from each portion of actualities nation. For a 256-piece block, the chief push is
unaltered and second one is moved according to instruction, 0.33 and fourth section is 1
byte, three bytes,and four bytes consistently (Lu, 2002).
The SubBytes Step
In this step, every byte in the matrix of the state is replaced by SubByteS (a ij) with the help
of the Rijndael substitution box and an 8-bit substitution box. Non-linearity is provided by
this operation to the cipher. S-box has made by joining inverse functions through an
invertible transformation to avoid it from simple and basic algebraic properties. The
InvSubBytes are used while performing the decryption that needs to first take the affine
inverse transformation and it starts to search the multiplicative inverse (JA, 2016).
The MixColumns step
In this step, four bytes from every column has combined with the help of invertible linear
transformation. In this step, the four bytes are taken as input that affects the four output
bytes. The Shift Rows and Mixed Columns when combined together give diffusion to the
cipher. The matrix multiplication is made of addition and multiplication of entries (Jiang,
2016).
The AddRoundKey step
In this step, with the use of XOR operation, each byte is shared through the round of subkey
byte. The subkey is combined with the state. Schedule of Rijndael’s key is used to derive a
12
o ShiftRows
The ShifrRows step
The ShiftRows step wears down on the strains of the kingdom. It activities the bytes in each
line through a couple of offset. The essential line, in any case, proceeds as sooner than in
AES. Every bite of the second line is moved one to 1 perspective and inside the equivalent
way, the 0.33 and fourth follows are moved by methods for parties of and 3 independently.
The moving case is equivalent for piece sizes 192 bits and 128 bits. Section n is moved left
round through n-1 bytes. In a similar way, each area of the yield country is created from
bytes from each portion of actualities nation. For a 256-piece block, the chief push is
unaltered and second one is moved according to instruction, 0.33 and fourth section is 1
byte, three bytes,and four bytes consistently (Lu, 2002).
The SubBytes Step
In this step, every byte in the matrix of the state is replaced by SubByteS (a ij) with the help
of the Rijndael substitution box and an 8-bit substitution box. Non-linearity is provided by
this operation to the cipher. S-box has made by joining inverse functions through an
invertible transformation to avoid it from simple and basic algebraic properties. The
InvSubBytes are used while performing the decryption that needs to first take the affine
inverse transformation and it starts to search the multiplicative inverse (JA, 2016).
The MixColumns step
In this step, four bytes from every column has combined with the help of invertible linear
transformation. In this step, the four bytes are taken as input that affects the four output
bytes. The Shift Rows and Mixed Columns when combined together give diffusion to the
cipher. The matrix multiplication is made of addition and multiplication of entries (Jiang,
2016).
The AddRoundKey step
In this step, with the use of XOR operation, each byte is shared through the round of subkey
byte. The subkey is combined with the state. Schedule of Rijndael’s key is used to derive a
12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

subkey for every round. The subkey is added by joining each state byte through the
corresponding byte of the subkey using bitwise XOR (Asangi, 2017).
Cryptography technology for Security
The only attacks that were successful against the full Advanced Encryption System were
side-channel attacks until May 2009. The National Security Agency reviewed and declared
the AES finalists as secure for the government for protection of unclassified information and
data. The strength and design of all key lengths as announced by the government in June
2003 were declared to be safe and secure to defend the confidential information up to
secret level (Liu, 2013).
Known attacks
The cryptographers consider a cryptographic ‘break’ that is anything faster than a brute
attack? A break can include infeasible results in the present technology also. The theoretical
breaks give an insight of the vulnerability patterns of the algorithm. There is an increase in
the key space by a factor of 2 for every bit length with addition given that the possible value
of every key is equally probable. This increases twice the brute-force key search time. If the
key length is very long that does not mean that it is safe from attacks (Ji, 2015).
Side-channel attacks
The side-channel attacks are not related to the cipher security because they do not attack
the cipher. They attack the software and the hardware that are implementations of cipher
and leak data. There are several known side-attacks. In the year 2005 and in the month of
April Bernstein professed an attack of cache-timing that is used to disruption a custom
server. This is used AES encryption with OpenSSL's. It was designed to provide the timing
information. In the year 2005 and in the month of October a paper was presented by, Dag
Arne Osvik, Adi Shamir, and EranTrimer that also demonstrated many cache-timing attacks
against AES. In the year 2009, in the month of December, an attacked was published. It was
on some hardware implementations. It took into use differential default analysis and
allowed recovery of a key with the complexity of 232. The attack required key-retrieval
algorithms run under a minute and standard user privilege (Li, 2017).
13
corresponding byte of the subkey using bitwise XOR (Asangi, 2017).
Cryptography technology for Security
The only attacks that were successful against the full Advanced Encryption System were
side-channel attacks until May 2009. The National Security Agency reviewed and declared
the AES finalists as secure for the government for protection of unclassified information and
data. The strength and design of all key lengths as announced by the government in June
2003 were declared to be safe and secure to defend the confidential information up to
secret level (Liu, 2013).
Known attacks
The cryptographers consider a cryptographic ‘break’ that is anything faster than a brute
attack? A break can include infeasible results in the present technology also. The theoretical
breaks give an insight of the vulnerability patterns of the algorithm. There is an increase in
the key space by a factor of 2 for every bit length with addition given that the possible value
of every key is equally probable. This increases twice the brute-force key search time. If the
key length is very long that does not mean that it is safe from attacks (Ji, 2015).
Side-channel attacks
The side-channel attacks are not related to the cipher security because they do not attack
the cipher. They attack the software and the hardware that are implementations of cipher
and leak data. There are several known side-attacks. In the year 2005 and in the month of
April Bernstein professed an attack of cache-timing that is used to disruption a custom
server. This is used AES encryption with OpenSSL's. It was designed to provide the timing
information. In the year 2005 and in the month of October a paper was presented by, Dag
Arne Osvik, Adi Shamir, and EranTrimer that also demonstrated many cache-timing attacks
against AES. In the year 2009, in the month of December, an attacked was published. It was
on some hardware implementations. It took into use differential default analysis and
allowed recovery of a key with the complexity of 232. The attack required key-retrieval
algorithms run under a minute and standard user privilege (Li, 2017).
13

Performance
The requirements for the AES selection process were low RAM and high speed. The AES
algorithm works very well with a various hardware, 8-bit smart cards as well as high-
presentation PCs.
14
The requirements for the AES selection process were low RAM and high speed. The AES
algorithm works very well with a various hardware, 8-bit smart cards as well as high-
presentation PCs.
14

Conclusion
A systematic key algorithm used for data encryption of electronic data is called data
encryption standard or DES. It has a great influence on the advancement of modern
cryptology despite being insecure in nature. In response to an invitation to offer an
algorithm to protect and safeguard unclassified and sensitive data, this algorithm
was proposed to National Bureau of Standards (NBS).
The Data Encryption Standard (DES) originated in the early 1970s. In the year 1972,
in response to an invitation to offer an algorithm to protect and safeguard
unclassified and sensitive government data this algorithm was proposed to National
Bureau of Standards (NBS) which is now named as National Institute of Standards
and Technology (NIST).
In the study of cryptology, particularly the study of methods of cracking block
ciphers, the Data Encryption Standard (DES) algorithm has proved to be a catalyst. It
initiated the development of encrypted algorithms (Pukkawanna, 2014).
There are a total of 16 identical stages of processing or encircling. The initial
permutation is termed as IP and the final permutation is termed as FP (Pereira,
2016). They both are inverses to each other that mean the task of IP is to undo the
action of FP and vice versa.
The key schedule is the algorithm that generates subkeys for encryption. Initially,
from the initial 64 bits by Permuted Choice 56 bits are selected. These bits are then
divided into two 28-bits halves.
The brute-force attack is the most basic attack for any cipher. The feasibility of the
approach depends on the duration of the key which also concludes the number of
keys achievable. In order to fit a chip, the key size of the DES algorithm was reduced
from 128 bits to 56 bits.
There are three attacks that are capable of breaking full 16 rounds of DES that are
less complex than brute-force search. These are:
o Differential cryptanalysis
o Davies’ attack
o Linear cryptanalysis
15
A systematic key algorithm used for data encryption of electronic data is called data
encryption standard or DES. It has a great influence on the advancement of modern
cryptology despite being insecure in nature. In response to an invitation to offer an
algorithm to protect and safeguard unclassified and sensitive data, this algorithm
was proposed to National Bureau of Standards (NBS).
The Data Encryption Standard (DES) originated in the early 1970s. In the year 1972,
in response to an invitation to offer an algorithm to protect and safeguard
unclassified and sensitive government data this algorithm was proposed to National
Bureau of Standards (NBS) which is now named as National Institute of Standards
and Technology (NIST).
In the study of cryptology, particularly the study of methods of cracking block
ciphers, the Data Encryption Standard (DES) algorithm has proved to be a catalyst. It
initiated the development of encrypted algorithms (Pukkawanna, 2014).
There are a total of 16 identical stages of processing or encircling. The initial
permutation is termed as IP and the final permutation is termed as FP (Pereira,
2016). They both are inverses to each other that mean the task of IP is to undo the
action of FP and vice versa.
The key schedule is the algorithm that generates subkeys for encryption. Initially,
from the initial 64 bits by Permuted Choice 56 bits are selected. These bits are then
divided into two 28-bits halves.
The brute-force attack is the most basic attack for any cipher. The feasibility of the
approach depends on the duration of the key which also concludes the number of
keys achievable. In order to fit a chip, the key size of the DES algorithm was reduced
from 128 bits to 56 bits.
There are three attacks that are capable of breaking full 16 rounds of DES that are
less complex than brute-force search. These are:
o Differential cryptanalysis
o Davies’ attack
o Linear cryptanalysis
15
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

All these attacks are conjectural in nature and are considered to be infeasible in
3preparation
The only attacks that were successful against the full Advanced Encryption System
were side-channel attacks until May 2009. The cryptographers consider A break can
include infeasible results in the present technology also. The theoretical breaks give
an insight of the vulnerability patterns of the algorithm. The side-channel attacks are
not related to the cipher security because they do not attack the cipher. They attack
the software and the hardware that are implementations of cipher and leak data.
A known set of ciphers for a given key and input are called test vectors. The requirements
for the AES selection process were low RAM and high speed. The AES algorithm works very
well with various hardware, 8-bit smart cards as well as high-performance computers
(Pereira, 2016).
16
3preparation
The only attacks that were successful against the full Advanced Encryption System
were side-channel attacks until May 2009. The cryptographers consider A break can
include infeasible results in the present technology also. The theoretical breaks give
an insight of the vulnerability patterns of the algorithm. The side-channel attacks are
not related to the cipher security because they do not attack the cipher. They attack
the software and the hardware that are implementations of cipher and leak data.
A known set of ciphers for a given key and input are called test vectors. The requirements
for the AES selection process were low RAM and high speed. The AES algorithm works very
well with various hardware, 8-bit smart cards as well as high-performance computers
(Pereira, 2016).
16

References
Apsangi, S., Guduru, S., Schnitzer, J.K., Markley, J.P., Carlucci, J.B. and Bevilacqua,
J.G., Time Warner Cable Enterprises LLC, 2017. Apparatus and methods for
provisioning in a download-enabled system. U.S. Patent 9,674,224.
Güler, Z., Özkaynak, F., andÇınar, A., 2017, September. CUDA Implementation of DES
Algorithm for Lightweight Platforms. In Proceedings of the 2017 International
Conference on Biomedical Engineering and Bioinformatics (pp. 49-52). ACM.
JA, A., 2016. Recommendations for Providing Digital Signature Services. [online]
Cryptomathic.com. Available at:
<https://www.cryptomathic.com/news-events/blog/recommendations-for-
providing-digital-signature-services> [Accessed 30 May 2018].
Ji, B., Wang, L. and Yang, Q., 2015. New Version of AES-ECC Encryption System Based
on FPGA in WSNs. Journal of Software Engineering, 9(1), pp.87-95.
Jiang, Q., Zeng, W., Ou, W. and Xu, R., 2016, October. A scrambling and encryption
algorithm for a selective block of identification photo. In Wireless Communications &
Signal Processing (WCSP), 2016 8th International Conference on(pp. 1-5). IEEE.
Li, T., Wang, G. and Chen, C., 2017. Research on DPA Attack Based on Back and Forth
Random Round with DES Algorithm. , 28(1), pp.69-71.
Liu, B. and Baas, B.M., 2013. Parallel AES encryption engines for many-core
processor arrays. IEEE transactions on computers, 62(3), pp.536-547.
Lu, C.C.,and Tseng, S.Y., 2002. Integrated design of AES (Advanced Encryption
Standard) encrypter and decrypter. In Application-Specific Systems,
Architectures,and Processors, 2002. Proceedings. The IEEE International Conference
on(pp. 277-285). IEEE.
Pereira, R., 2016. Digital Certificates Cheatsheet - Generate, convert, etc. [online]
JBay Solutions - The Dev Blog. Available at:
<http://blog.jbaysolutions.com/2016/02/24/generate-convert-certificat/> [Accessed
30 May 2018].
Pukkawanna, S., Blanc, G., Garcia-Alfaro, J., Kadobayashi, Y. and Debar, H., 2014,
September. Classification of SSL servers based on their SSL handshake for automated
17
Apsangi, S., Guduru, S., Schnitzer, J.K., Markley, J.P., Carlucci, J.B. and Bevilacqua,
J.G., Time Warner Cable Enterprises LLC, 2017. Apparatus and methods for
provisioning in a download-enabled system. U.S. Patent 9,674,224.
Güler, Z., Özkaynak, F., andÇınar, A., 2017, September. CUDA Implementation of DES
Algorithm for Lightweight Platforms. In Proceedings of the 2017 International
Conference on Biomedical Engineering and Bioinformatics (pp. 49-52). ACM.
JA, A., 2016. Recommendations for Providing Digital Signature Services. [online]
Cryptomathic.com. Available at:
<https://www.cryptomathic.com/news-events/blog/recommendations-for-
providing-digital-signature-services> [Accessed 30 May 2018].
Ji, B., Wang, L. and Yang, Q., 2015. New Version of AES-ECC Encryption System Based
on FPGA in WSNs. Journal of Software Engineering, 9(1), pp.87-95.
Jiang, Q., Zeng, W., Ou, W. and Xu, R., 2016, October. A scrambling and encryption
algorithm for a selective block of identification photo. In Wireless Communications &
Signal Processing (WCSP), 2016 8th International Conference on(pp. 1-5). IEEE.
Li, T., Wang, G. and Chen, C., 2017. Research on DPA Attack Based on Back and Forth
Random Round with DES Algorithm. , 28(1), pp.69-71.
Liu, B. and Baas, B.M., 2013. Parallel AES encryption engines for many-core
processor arrays. IEEE transactions on computers, 62(3), pp.536-547.
Lu, C.C.,and Tseng, S.Y., 2002. Integrated design of AES (Advanced Encryption
Standard) encrypter and decrypter. In Application-Specific Systems,
Architectures,and Processors, 2002. Proceedings. The IEEE International Conference
on(pp. 277-285). IEEE.
Pereira, R., 2016. Digital Certificates Cheatsheet - Generate, convert, etc. [online]
JBay Solutions - The Dev Blog. Available at:
<http://blog.jbaysolutions.com/2016/02/24/generate-convert-certificat/> [Accessed
30 May 2018].
Pukkawanna, S., Blanc, G., Garcia-Alfaro, J., Kadobayashi, Y. and Debar, H., 2014,
September. Classification of SSL servers based on their SSL handshake for automated
17

security assessment. In Building Analysis Datasets and Gathering Experience Returns
for Security (BADGERS), 2014 Third International Workshop on (pp. 30-39). IEEE.
Rashidi, E., Medal, H., Gordon, J., Grala, R. and Varner, M., 2017. A maximal covering
location-based model for analyzing the vulnerability of landscapes to wildfires:
Assessing the worst-case scenario. European Journal of Operational
Research, 258(3), pp.1095-1105.
Support.symantec, 2017. How to create a self-signed SSL Certificate using OpenSSL
for Reporter 9.x. [online] Support.symantec. Available at:
<https://support.symantec.com/en_US/article.TECH242030.html> [Accessed 30 May
2018]
Thirumalai, C., 2016. Review on the memory efficient RSA variants. International
Journal of Pharmacy and Technology, 8(4), pp.4907-4916.
18
for Security (BADGERS), 2014 Third International Workshop on (pp. 30-39). IEEE.
Rashidi, E., Medal, H., Gordon, J., Grala, R. and Varner, M., 2017. A maximal covering
location-based model for analyzing the vulnerability of landscapes to wildfires:
Assessing the worst-case scenario. European Journal of Operational
Research, 258(3), pp.1095-1105.
Support.symantec, 2017. How to create a self-signed SSL Certificate using OpenSSL
for Reporter 9.x. [online] Support.symantec. Available at:
<https://support.symantec.com/en_US/article.TECH242030.html> [Accessed 30 May
2018]
Thirumalai, C., 2016. Review on the memory efficient RSA variants. International
Journal of Pharmacy and Technology, 8(4), pp.4907-4916.
18
1 out of 19
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.

