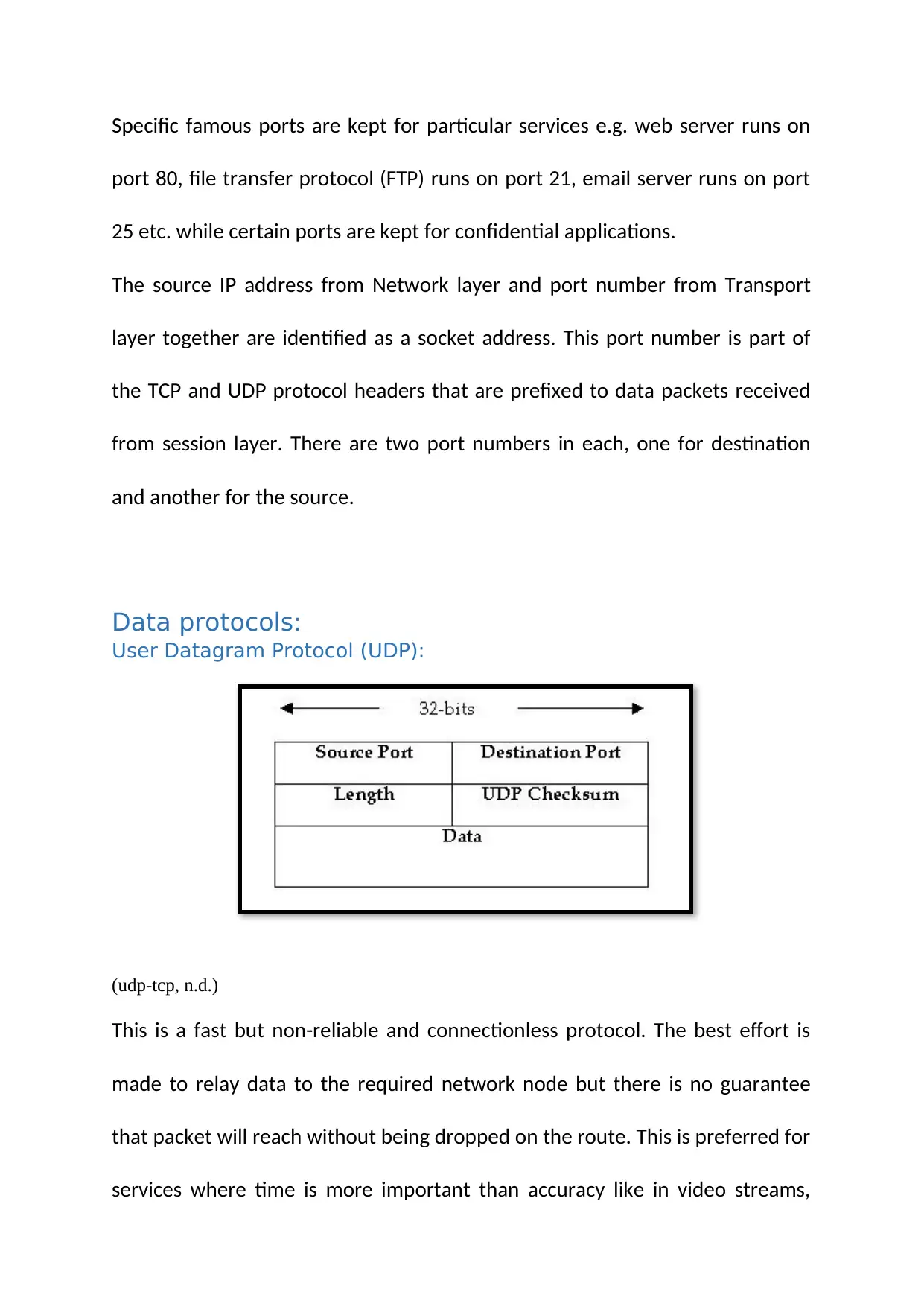
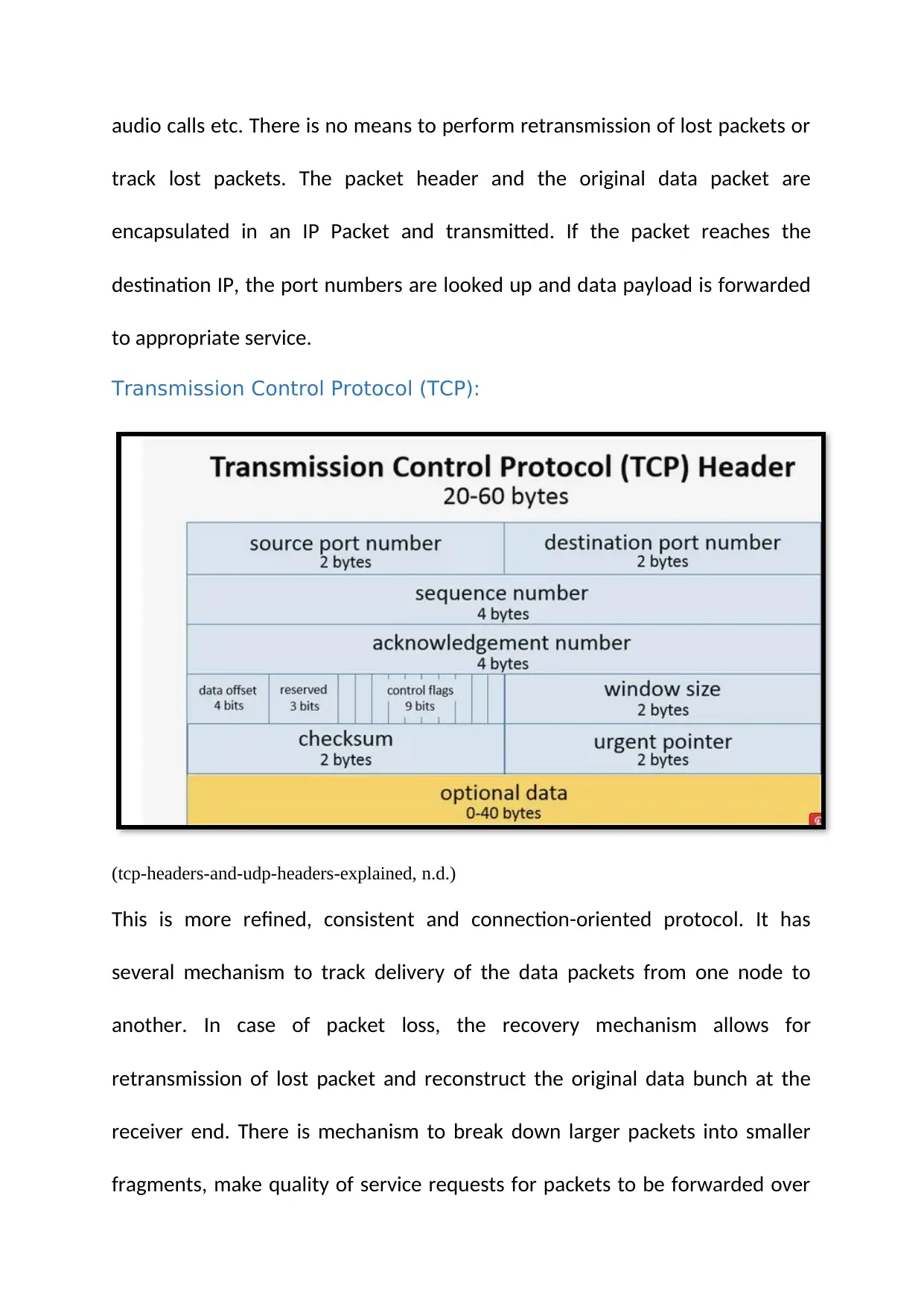
The data link layer is responsible for managing data packets between the physical and network layers. It handles encoding, framing, error detection and correction, link configuration control, packet synchronization, packet identification, and carrier sense and media access. Its functions include maintaining bit rate, passing data in and out from the network layer, transforming data packets into data bits for transmission, error checking, link configuration control, framing packets, packet synchronization, packet identification, and carrier sense and media access. The transport layer is responsible for delivering packets from host to client applications. It uses ports to identify applications and has protocols like UDP and TCP for data transfer. Its functions include data handling and packaging, data transfer, connection establishment, addressing/multiplexing, packet fragmentation, and flow control. Cloud computing involves users and providers where resources are provided and maintained by providers over the internet. It offers flexibility, scalability, and cost savings. Different types of services in cloud computing include software-as-a-service (SaaS), platform-as-a-service (PaaS), and infrastructure-as-a-service (IaaS).
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)