Database Design and Development Report: Analysis of Hospital System
VerifiedAdded on 2021/01/02
|20
|5246
|146
Report
AI Summary
This report focuses on the design and development of a database system for a hospital, addressing the limitations of manual data processing. It begins by outlining the system and user requirements, emphasizing the need for efficient data recording, patient information management, and doctor scheduling. The report then delves into the database design, including a visual representation, followed by an analysis of how effectively the designed database meets both system and user needs. A fully functional database system is presented, alongside an evaluation of its effectiveness, incorporating aspects like security, user interface, and information extraction. The report also suggests strategies for future improvements to sustain database effectiveness, such as regular data cleaning and backups. Furthermore, it covers database testing, test data choices, and a comprehensive test plan. Finally, the report concludes with the technical and user documentation developed for the database system.

DATABASE DESIGN AND
DEVELOPMENT
DEVELOPMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
PART 1............................................................................................................................................1
1. Requirements of system and users ....................................................................................1
P1 ...........................................................................................................................................2
2. Design of database .............................................................................................................2
3. Understanding user and system requirements....................................................................3
4. Analysing effectiveness of database wrt system and user requirements............................4
PART 2............................................................................................................................................4
Completely functional database system.................................................................................4
P2............................................................................................................................................4
Effectiveness of database solution and suggestions for future improvement .................................7
Database effectiveness in relation with the prescribed requirements....................................7
Database effectiveness in relation with requirements of user................................................8
Future improvement strategies for sustaining effectiveness..................................................8
PART 3............................................................................................................................................9
Effectiveness of database testing............................................................................................9
P4..........................................................................................................................................10
Test data choice in effectiveness of testing..........................................................................11
Test plan ..............................................................................................................................13
PART 4..........................................................................................................................................13
P5..........................................................................................................................................13
Technical and user documentation for the developed database system ..............................13
CONCLUSION..............................................................................................................................16
REFERENCES..............................................................................................................................17
INTRODUCTION...........................................................................................................................1
PART 1............................................................................................................................................1
1. Requirements of system and users ....................................................................................1
P1 ...........................................................................................................................................2
2. Design of database .............................................................................................................2
3. Understanding user and system requirements....................................................................3
4. Analysing effectiveness of database wrt system and user requirements............................4
PART 2............................................................................................................................................4
Completely functional database system.................................................................................4
P2............................................................................................................................................4
Effectiveness of database solution and suggestions for future improvement .................................7
Database effectiveness in relation with the prescribed requirements....................................7
Database effectiveness in relation with requirements of user................................................8
Future improvement strategies for sustaining effectiveness..................................................8
PART 3............................................................................................................................................9
Effectiveness of database testing............................................................................................9
P4..........................................................................................................................................10
Test data choice in effectiveness of testing..........................................................................11
Test plan ..............................................................................................................................13
PART 4..........................................................................................................................................13
P5..........................................................................................................................................13
Technical and user documentation for the developed database system ..............................13
CONCLUSION..............................................................................................................................16
REFERENCES..............................................................................................................................17

INTRODUCTION
Designing of database refers to the fact of involving every essential feature that is
required by the organisation. Elements are to be verified carefully at the time of designing of the
database as it should be in an order to achieve the specific requirements of a firm (Jagadish and
et.al, 2016). Also, after the database has been successfully designed, its implementation takes
place when the specified database is being implemented in the company so that it can help them
to attain their objectives at a much faster time. The report is about analysing the user and system
requirements of the organisation. It also involves the effectiveness of design of the database
covering system and user requirements. A well and fully functional database has also been
designed in the report. Also, the report involves testing of the requirements and a proper
documentation for user as well as technical measures.
PART 1
1. Requirements of system and users
There are some factors that are causing issues with the manual processing of routine
functions of hospital So, in order to overcome the issue, the business has decided to choose a
well designed database through which they can record necessary information and tracks of their
activities. This will help them to focus on achieving a great productivity with minimum error and
trust of their patients. Therefore, there must be some user as well as system requirements for this
database as well. Some well known example of user requirement can be that hospital deals with a
variety of information management such as keeping track of details related to their patients,
schedules and information of doctors, purchasing slips related to medicines and other
equipments. So, recording a proper set of information about all case studies of their facility
seekers and service providers is required to be maintained. These should be integrated with terms
such as parameters like blood groups and other related parameters used in hospitals. Therefore,
these should be kept in mind while the designing of database. Also, system requirements can be
that the systems on which they will implement database should be up to date, whether it is in
terms of software or of hardware, both of these should be well developed so that the database
may not create any issue on the system such as heating up of system, hanging etc. These users
and system requirements are necessary to be ensured while the designing as well as
implementation of the database so that they can help them to achieve their objectives in a most
efficient manner.
Designing of database refers to the fact of involving every essential feature that is
required by the organisation. Elements are to be verified carefully at the time of designing of the
database as it should be in an order to achieve the specific requirements of a firm (Jagadish and
et.al, 2016). Also, after the database has been successfully designed, its implementation takes
place when the specified database is being implemented in the company so that it can help them
to attain their objectives at a much faster time. The report is about analysing the user and system
requirements of the organisation. It also involves the effectiveness of design of the database
covering system and user requirements. A well and fully functional database has also been
designed in the report. Also, the report involves testing of the requirements and a proper
documentation for user as well as technical measures.
PART 1
1. Requirements of system and users
There are some factors that are causing issues with the manual processing of routine
functions of hospital So, in order to overcome the issue, the business has decided to choose a
well designed database through which they can record necessary information and tracks of their
activities. This will help them to focus on achieving a great productivity with minimum error and
trust of their patients. Therefore, there must be some user as well as system requirements for this
database as well. Some well known example of user requirement can be that hospital deals with a
variety of information management such as keeping track of details related to their patients,
schedules and information of doctors, purchasing slips related to medicines and other
equipments. So, recording a proper set of information about all case studies of their facility
seekers and service providers is required to be maintained. These should be integrated with terms
such as parameters like blood groups and other related parameters used in hospitals. Therefore,
these should be kept in mind while the designing of database. Also, system requirements can be
that the systems on which they will implement database should be up to date, whether it is in
terms of software or of hardware, both of these should be well developed so that the database
may not create any issue on the system such as heating up of system, hanging etc. These users
and system requirements are necessary to be ensured while the designing as well as
implementation of the database so that they can help them to achieve their objectives in a most
efficient manner.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
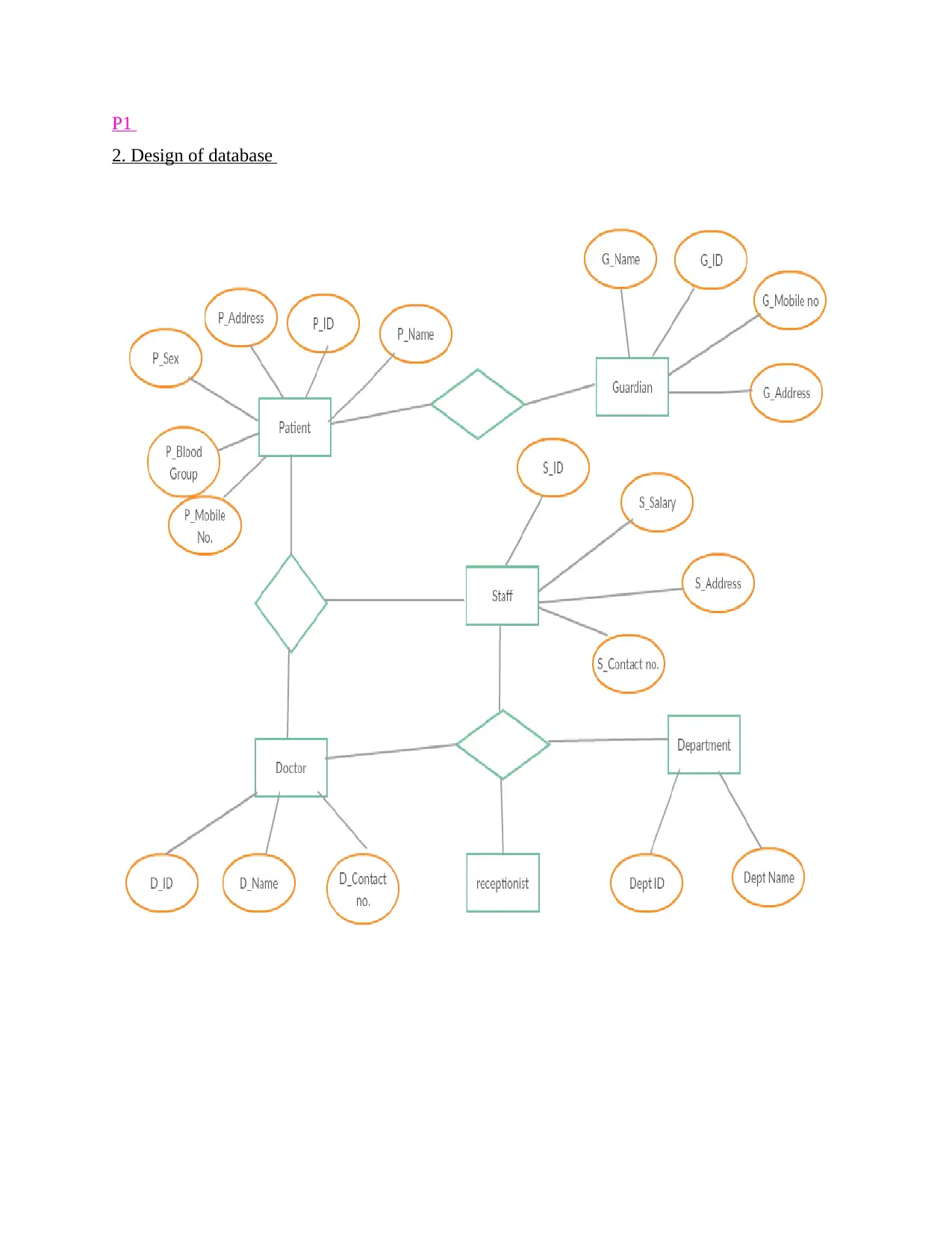
P1
2. Design of database
2. Design of database
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. Understanding user and system requirements
A clear view of system and user requirements of hospital is as under :
User requirements
Hospital manages the details of its patients, employee's and schedules of doctors
manually. The purchasing of medicines and other clinical equipments is also
accomplished with manual records. So in this case, they may face losing data. It is
because a manual record of above functionalities can get lost and cause complications for
hospital to analyse their expected and achieved outcomes.
Also, their tracking of health status of patients and visiting time table of doctors is being
done manually, which can also get difficult at the time of making schedule or providing
treatment guidelines to patients when they are discharged from the hospital (Clifford and
et.al, 2016). So, as per this, they require a database that is capable of recording all this
information and data, i.e. of employees, health status of patients, doctors and their
availability etc. so that they can be even able to evaluate their performance as compare to
other clinics and hospitals. Therefore, these can be considered as the user requirements of
hospital for an efficient designing and implementation of database.
System requirements
One of the major factor that is required for an efficient implementation of database is that
the system should be up to date with the latest hardware and software's.
The hardware of the system on which database has to be implemented should have
efficient amount of space and memory so that it can cope with the requirements and data
of database. Also, if there will be an appropriate hardware on the system, then there are
very minor chances of occurring any issues such as heating of system, hanging up etc.
Along with the hardware, ensuring all applications required and appropriate software's is
important because the software should be up to date in the system in which database has
to be implemented. It is important because it helps in easing the operations, thus not
making them complex that it can have an influence on the outputs of the system. So, the
software and the hardware, both should be up to date and as per the requirement so that
A clear view of system and user requirements of hospital is as under :
User requirements
Hospital manages the details of its patients, employee's and schedules of doctors
manually. The purchasing of medicines and other clinical equipments is also
accomplished with manual records. So in this case, they may face losing data. It is
because a manual record of above functionalities can get lost and cause complications for
hospital to analyse their expected and achieved outcomes.
Also, their tracking of health status of patients and visiting time table of doctors is being
done manually, which can also get difficult at the time of making schedule or providing
treatment guidelines to patients when they are discharged from the hospital (Clifford and
et.al, 2016). So, as per this, they require a database that is capable of recording all this
information and data, i.e. of employees, health status of patients, doctors and their
availability etc. so that they can be even able to evaluate their performance as compare to
other clinics and hospitals. Therefore, these can be considered as the user requirements of
hospital for an efficient designing and implementation of database.
System requirements
One of the major factor that is required for an efficient implementation of database is that
the system should be up to date with the latest hardware and software's.
The hardware of the system on which database has to be implemented should have
efficient amount of space and memory so that it can cope with the requirements and data
of database. Also, if there will be an appropriate hardware on the system, then there are
very minor chances of occurring any issues such as heating of system, hanging up etc.
Along with the hardware, ensuring all applications required and appropriate software's is
important because the software should be up to date in the system in which database has
to be implemented. It is important because it helps in easing the operations, thus not
making them complex that it can have an influence on the outputs of the system. So, the
software and the hardware, both should be up to date and as per the requirement so that
the database can be able to function properly and efficiently thus recording all the
necessary data and information of the hospital.
4. Analysing effectiveness of database wrt system and user requirements
The database designed can be termed as effective enough because the requirements of
hospital staff members have been kept in mind while designing it. The database is designed in
such a manner that hospital can maintain all of its information which is processed on daily basis
and along with that, managing the record of total number of convalescents (Harrington, 2016).
Also, the software's and hardware's have been updated well so that the database cannot throw
any pressure on the system because when any of them are not installed properly, there are
chances that the system will heat up and this can result in shutting down of system as well. So,
the database has been made in accordance with all system and user requirements so that it can be
able to cope with the basic requirements of hospital.
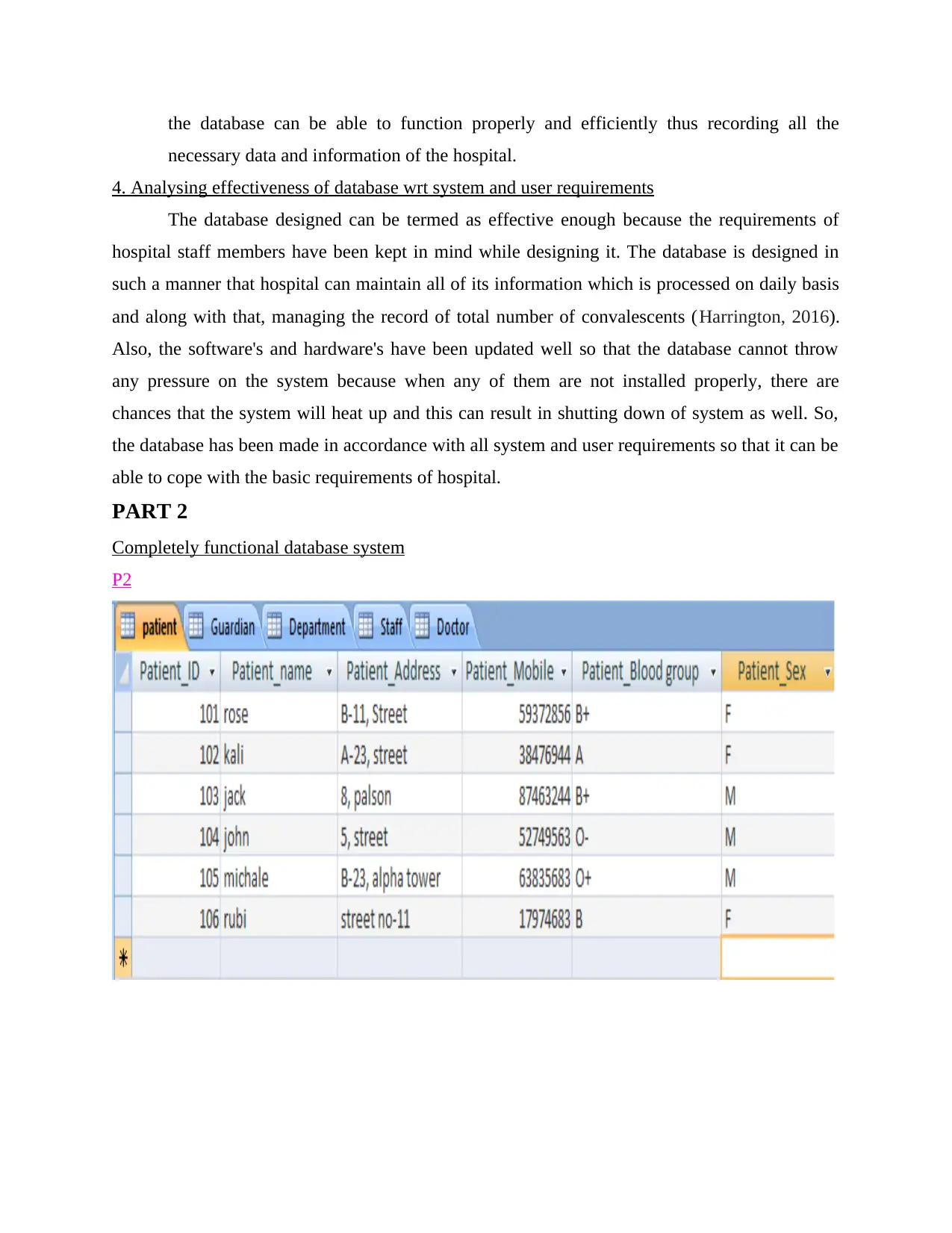
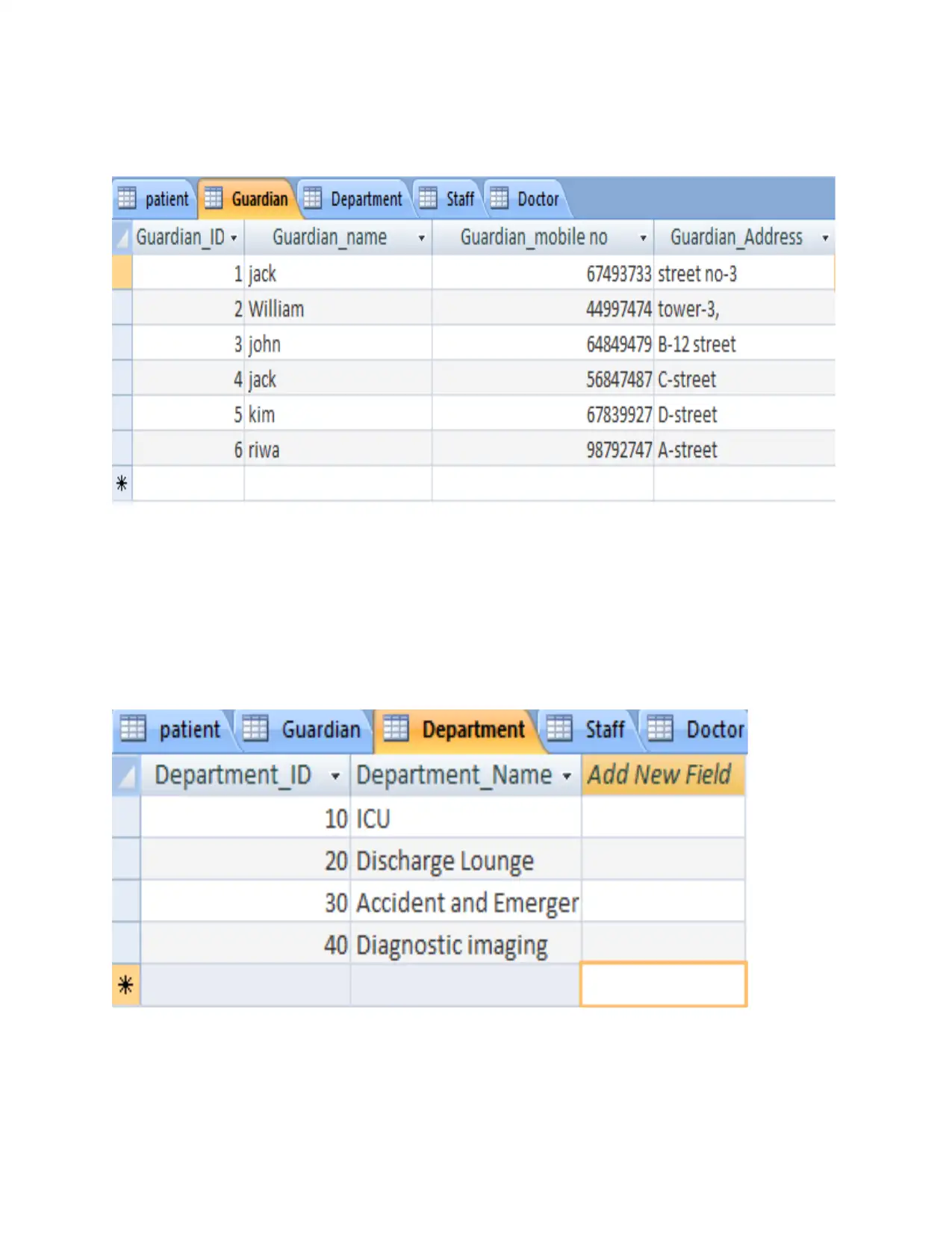
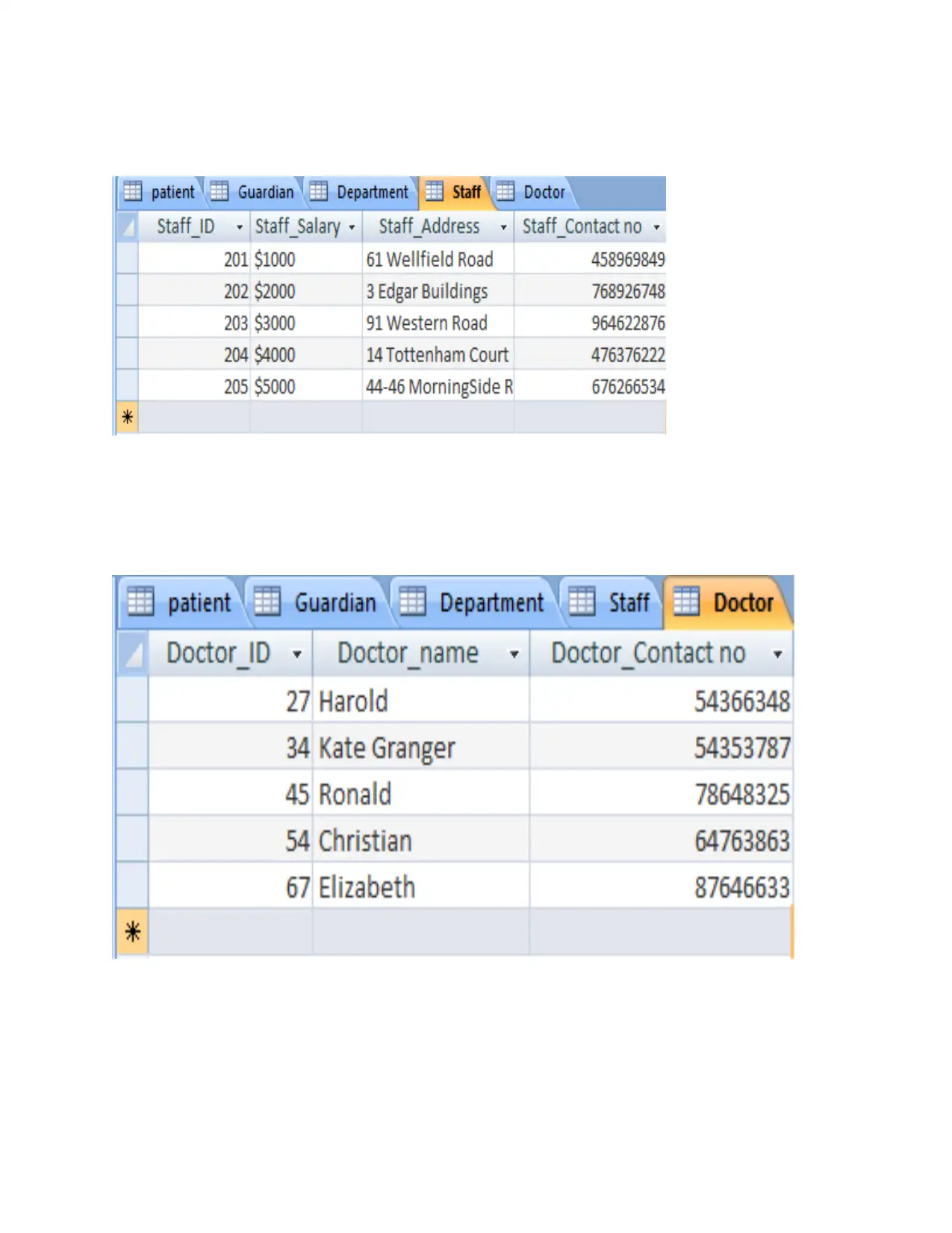
PART 2
Completely functional database system
P2
necessary data and information of the hospital.
4. Analysing effectiveness of database wrt system and user requirements
The database designed can be termed as effective enough because the requirements of
hospital staff members have been kept in mind while designing it. The database is designed in
such a manner that hospital can maintain all of its information which is processed on daily basis
and along with that, managing the record of total number of convalescents (Harrington, 2016).
Also, the software's and hardware's have been updated well so that the database cannot throw
any pressure on the system because when any of them are not installed properly, there are
chances that the system will heat up and this can result in shutting down of system as well. So,
the database has been made in accordance with all system and user requirements so that it can be
able to cope with the basic requirements of hospital.
PART 2
Completely functional database system
P2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Effectiveness of database solution and suggestions for future improvement
For evaluation of the quality of designed database system, it is essential to evaluate
performance of various criteria such as security features, complexity of user interface, easiness
of information extraction and flow along with above mentioned requirements.
Database effectiveness in relation with the prescribed requirements
The development of designed database system must be able to fulfil the system
requirements. The effective database system provides feature of flexibility thus designed system
must be compatible with existing hardware and software of hospital. The database system must
support concurrent data processing.
Database system must essentially consider the concepts of data validation. The database
processes the information only when user enters sensible and valid data. For instance, extraction
of employee's record or details of any patient is possible only when valid employee id or patient
id is fed into database. In case of invalid or null id, database will not be able to provide results to
the user.
Data validation tools regularly validate consistency and sensibility of inserted data. Data
validation in database ensures that data type and range are valid values, which can be processed.
The system is effective to check presence, length and format of the data inserted into database.
For evaluating effectiveness of database in terms of extracting useful information, a database
system is analysed as multi component system. The data is allocated and managed in distributed
form so that effectiveness of database dynamics can be evaluated. For evaluation of installation
and operational aspects of the designed database, benchmarking evaluation techniques must be
performed.
The extent up to which hospital will share the data is also an important factor in
evaluation of effectiveness. The effectiveness of designed database system is guaranteed by
designers only after analysing the utilization of disks during processing of various queries across
multiple tables of database. It requires critical evaluation of different levels of central processing
unit. The queries, which are used to extract data from designed system must be effective to
minimize the time delay in processing as well as occupies the least space in disk. The system and
user interface must not enhance complexity of the database. The increased complexity and
unnecessary queries will not only reduce effectiveness of database system but will also make it
difficult for users of hospital to implement it. In that case, objectives of database may not be
For evaluation of the quality of designed database system, it is essential to evaluate
performance of various criteria such as security features, complexity of user interface, easiness
of information extraction and flow along with above mentioned requirements.
Database effectiveness in relation with the prescribed requirements
The development of designed database system must be able to fulfil the system
requirements. The effective database system provides feature of flexibility thus designed system
must be compatible with existing hardware and software of hospital. The database system must
support concurrent data processing.
Database system must essentially consider the concepts of data validation. The database
processes the information only when user enters sensible and valid data. For instance, extraction
of employee's record or details of any patient is possible only when valid employee id or patient
id is fed into database. In case of invalid or null id, database will not be able to provide results to
the user.
Data validation tools regularly validate consistency and sensibility of inserted data. Data
validation in database ensures that data type and range are valid values, which can be processed.
The system is effective to check presence, length and format of the data inserted into database.
For evaluating effectiveness of database in terms of extracting useful information, a database
system is analysed as multi component system. The data is allocated and managed in distributed
form so that effectiveness of database dynamics can be evaluated. For evaluation of installation
and operational aspects of the designed database, benchmarking evaluation techniques must be
performed.
The extent up to which hospital will share the data is also an important factor in
evaluation of effectiveness. The effectiveness of designed database system is guaranteed by
designers only after analysing the utilization of disks during processing of various queries across
multiple tables of database. It requires critical evaluation of different levels of central processing
unit. The queries, which are used to extract data from designed system must be effective to
minimize the time delay in processing as well as occupies the least space in disk. The system and
user interface must not enhance complexity of the database. The increased complexity and
unnecessary queries will not only reduce effectiveness of database system but will also make it
difficult for users of hospital to implement it. In that case, objectives of database may not be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

fulfilled. The designed system must be effective so that it can integrate with all types of security
features. The support and integration with other external application will enable the system to
enhance its functionality and range of operational activities. Data base system can provide
effective outputs only if regular maintenance actions are performed properly. The system must
provide support to implement features, which are necessary to sustain the effectiveness of
database system.
Database effectiveness in relation with requirements of user
The major requirement of hospital is to manage its useful and sensitive information via
database system instead of manual data handling. Thus, the database must have sufficient
capacity for storing and processing the entire data. It must not be ineffective in handling huge
data, otherwise system failure may occur. Database must be effective in terms of processing. The
considerably large delay in processing queries or operation can degrade the effectiveness of the
system and may not provide effective results hospital in its operational activities. The parameters
like storage capacity and corresponding time delay in processing data are key factors for hospital
to evaluate the effectiveness of database system. Organisation will also operate some additional
application software in integration with database system.
Thus, database must be able to simulate with such external applications. The user
interface of designed system must be simple so that users of the health service provider can
easily interact with system and do not find it difficult or complex as compared to manual system.
Database system effectiveness is significantly dependent on attached security measurements. The
developed system must provide guarantee of the security of processed data against unauthorised
access and network security threats. These requirements by an organisation act as key factor in
evaluating the performance and effectiveness of the database system.
Future improvement strategies for sustaining effectiveness
Hospital requires implementation and guidance of certain strategies, which are necessary
for maintaining effectiveness of database system. They must perform regular cleaning of waste
data from its database. Unnecessary and useless data is generally not required by organisation
any more must be removed. This unused data not only affects the speed of operational activities
but also acts as a vulnerable threat for the security of entire system. Organisation must update its
features. The support and integration with other external application will enable the system to
enhance its functionality and range of operational activities. Data base system can provide
effective outputs only if regular maintenance actions are performed properly. The system must
provide support to implement features, which are necessary to sustain the effectiveness of
database system.
Database effectiveness in relation with requirements of user
The major requirement of hospital is to manage its useful and sensitive information via
database system instead of manual data handling. Thus, the database must have sufficient
capacity for storing and processing the entire data. It must not be ineffective in handling huge
data, otherwise system failure may occur. Database must be effective in terms of processing. The
considerably large delay in processing queries or operation can degrade the effectiveness of the
system and may not provide effective results hospital in its operational activities. The parameters
like storage capacity and corresponding time delay in processing data are key factors for hospital
to evaluate the effectiveness of database system. Organisation will also operate some additional
application software in integration with database system.
Thus, database must be able to simulate with such external applications. The user
interface of designed system must be simple so that users of the health service provider can
easily interact with system and do not find it difficult or complex as compared to manual system.
Database system effectiveness is significantly dependent on attached security measurements. The
developed system must provide guarantee of the security of processed data against unauthorised
access and network security threats. These requirements by an organisation act as key factor in
evaluating the performance and effectiveness of the database system.
Future improvement strategies for sustaining effectiveness
Hospital requires implementation and guidance of certain strategies, which are necessary
for maintaining effectiveness of database system. They must perform regular cleaning of waste
data from its database. Unnecessary and useless data is generally not required by organisation
any more must be removed. This unused data not only affects the speed of operational activities
but also acts as a vulnerable threat for the security of entire system. Organisation must update its
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

database periodically so that effectiveness is maintained. In order to avoid information loss data
stored in the database must be back up on an essential routine. The data backup will not only
protect data from destruction but will also be helpful for future requirements.
Data encryption and regular monitoring of all data transfers and activities can reduce the
risk of security threats to a great extent. Hospital must also keep its data free from unauthorised
accessing and corruption related activities. This approach will increase data integrity and
effectiveness of database system is sustained for long term. The network security strategies must
be implemented strictly in order to avoid data security concerns. For instance, strong passwords
for authorized accessing, regular update of licensed antivirus software's is beneficial for ensuring
the security of system. Hospital must give authorised access to only selected individuals who can
modify and insert the data into database. It will greatly reduce the risk of unauthorised access
and database effectiveness will be maintained for longer term.
PART 3
Effectiveness of database testing
In order to ensure consistency and effectiveness of designed database system, various
components and functionality of database can be tested.
The effective database testing analyses and considers the following aspects:
An effective Database testing ensures that all transactions included in database
processing holds a valid and sensible output. These outputs must be durable in nature;
this means they must be stored safely in database without vulnerability of data loss due to
system crash or power loss.
Data base testing provides assurance that the designed database is completely able to
reflect changes made in input values. The immediate reflection of changes made into
output provides confirmation that functional requirements of user and system are
successfully implemented.
The database testing will analyse the effectiveness of validity and integrity of data. It will
evaluate the performance factor of database such as time delay in data processing, storage
capacity and load handling ability. The database testing also aims at evaluating the
performance of various functions and triggering activities of the designed database.
stored in the database must be back up on an essential routine. The data backup will not only
protect data from destruction but will also be helpful for future requirements.
Data encryption and regular monitoring of all data transfers and activities can reduce the
risk of security threats to a great extent. Hospital must also keep its data free from unauthorised
accessing and corruption related activities. This approach will increase data integrity and
effectiveness of database system is sustained for long term. The network security strategies must
be implemented strictly in order to avoid data security concerns. For instance, strong passwords
for authorized accessing, regular update of licensed antivirus software's is beneficial for ensuring
the security of system. Hospital must give authorised access to only selected individuals who can
modify and insert the data into database. It will greatly reduce the risk of unauthorised access
and database effectiveness will be maintained for longer term.
PART 3
Effectiveness of database testing
In order to ensure consistency and effectiveness of designed database system, various
components and functionality of database can be tested.
The effective database testing analyses and considers the following aspects:
An effective Database testing ensures that all transactions included in database
processing holds a valid and sensible output. These outputs must be durable in nature;
this means they must be stored safely in database without vulnerability of data loss due to
system crash or power loss.
Data base testing provides assurance that the designed database is completely able to
reflect changes made in input values. The immediate reflection of changes made into
output provides confirmation that functional requirements of user and system are
successfully implemented.
The database testing will analyse the effectiveness of validity and integrity of data. It will
evaluate the performance factor of database such as time delay in data processing, storage
capacity and load handling ability. The database testing also aims at evaluating the
performance of various functions and triggering activities of the designed database.

P4
The database testing will provide feedback regarding drawbacks in the design and development
process. The feedback can be used to improve the functionality of the designed database. In
order to gain the effective results for database testing organisation must apply an in-memory
approach. It will increase the speed of database testing. The testing must be performed by skilled
team of designers. The selection of test data type plays crucial role in determining the
effectiveness of database testing. The organisation can use following database testing methods
which can provide effective testing results:
Black box testing:
This testing approach is considered as high level testing and it usually emphasis on
software behaviour instead of internal coding and working of the developed system. It prioritizes
the expectations and requirements of user as compare to the design approach of the database.
Black box testing does not require the knowledge of programming and implementation and is
difficult to be performed in automation mode. This type of testing use the concept of trial and
detecting error method for evaluating the functionality of database. It is less time consuming
testing procedure as compare to white box testing but this type of testing is suitable for large
segments of code.
The designed database system can be tested by using different methods of black box
testing. For evaluating the data validity and integration the most common black box method is
equivalence partitioning method. In this method of database testing inputs values are divided into
two categories of valid and invalid inputs and corresponding tests are performed from each set of
values. For analysing the test results of database in context of boundary value or range of data
values boundary value analysis method for testing is used.
White box testing:
White box testing is considered as low level testing and it requires the internal structure
and coding of the designed database. This type of testing evaluate the effectiveness of internal
functioning of database. Since this type of testing requires the detail knowledge of internal
coding it is essential for the tester to have great understanding of programming and detailed
knowledge about testing procedure. The main purpose of this type of testing is to evaluate the
code quality. Some of the most common method used in white box testing are statement and
branch coverage and path coverage. These testing methods ensures that every statement and
The database testing will provide feedback regarding drawbacks in the design and development
process. The feedback can be used to improve the functionality of the designed database. In
order to gain the effective results for database testing organisation must apply an in-memory
approach. It will increase the speed of database testing. The testing must be performed by skilled
team of designers. The selection of test data type plays crucial role in determining the
effectiveness of database testing. The organisation can use following database testing methods
which can provide effective testing results:
Black box testing:
This testing approach is considered as high level testing and it usually emphasis on
software behaviour instead of internal coding and working of the developed system. It prioritizes
the expectations and requirements of user as compare to the design approach of the database.
Black box testing does not require the knowledge of programming and implementation and is
difficult to be performed in automation mode. This type of testing use the concept of trial and
detecting error method for evaluating the functionality of database. It is less time consuming
testing procedure as compare to white box testing but this type of testing is suitable for large
segments of code.
The designed database system can be tested by using different methods of black box
testing. For evaluating the data validity and integration the most common black box method is
equivalence partitioning method. In this method of database testing inputs values are divided into
two categories of valid and invalid inputs and corresponding tests are performed from each set of
values. For analysing the test results of database in context of boundary value or range of data
values boundary value analysis method for testing is used.
White box testing:
White box testing is considered as low level testing and it requires the internal structure
and coding of the designed database. This type of testing evaluate the effectiveness of internal
functioning of database. Since this type of testing requires the detail knowledge of internal
coding it is essential for the tester to have great understanding of programming and detailed
knowledge about testing procedure. The main purpose of this type of testing is to evaluate the
code quality. Some of the most common method used in white box testing are statement and
branch coverage and path coverage. These testing methods ensures that every statement and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





