Detailed Report on DDoS Attacks: Case Study and Prevention Techniques
VerifiedAdded on 2023/06/06
|10
|2237
|162
Report
AI Summary
This report provides an overview of Distributed Denial of Service (DDoS) attacks, a significant security threat to computer systems. It outlines the fundamental concepts of DDoS, detailing the steps involved in an attack, including the use of botnets and traffic flooding. A case study of the GitHub DDoS attack in 2018 is presented, highlighting the impact and mitigation strategies employed. The report also explores various methods to avoid DDoS attacks, such as early detection, bandwidth overprovisioning, network perimeter defense, and the adoption of security programs like firewalls and encryption. It concludes by emphasizing the increasing prevalence of DDoS attacks and the importance of implementing robust security measures to protect personal information and organizational assets, suggesting backup plans like cloud computing to secure data.

Running Head: DDOS
1
Distributed Denial of Service
1
Distributed Denial of Service
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DDOS
2
Contents
Introduction.................................................................................................................................................3
Overview of DDOS.......................................................................................................................................3
Steps involved in DDOS attack.................................................................................................................4
GitHub DDOS attack (Case study)................................................................................................................5
Methods to avoid DDOS attack....................................................................................................................7
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9
2
Contents
Introduction.................................................................................................................................................3
Overview of DDOS.......................................................................................................................................3
Steps involved in DDOS attack.................................................................................................................4
GitHub DDOS attack (Case study)................................................................................................................5
Methods to avoid DDOS attack....................................................................................................................7
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9

DDOS
3
Introduction
DDOS is defined as the distributed denial of service which is a part of a DOS assault.
It is one of the biggest security problems for any wireless and computer devices and the
rate of DDOS is growing rapidly since the last few years (Bawany, Shamsi, & Salah, 2017).
This type of attacks includes various hacking devices and algorithms which are also called
the botnet and in which hackers target online websites by sending traffic signals. The main
objective of this report is to understand the fundamental concept of DDOS and various
prevention techniques to reduce this type of problem (Bhuyan, Bhattacharyya, & Kalita,
2015). This report is divided into three parts, for example, the overview of DDOS, a recent
case study, and prevention methods.
Overview of DDOS
In a computer system, the distributed denial of services is a kind of attack in which
hacker design a network system that produces various traffic signals into user personal
servers. This is a very serious problem for an organization and it also impacts the user
personal information or data files (Kamikubo, & Saito, 2017). This type of security risk uses
flooding mechanism to block user’s computer systems and peripheral devices. DDOS
targets on business industries, banking servers, credit and debit cards, and online payment
methods (Kolias, Kambourakis, Stavrou, & Voas, 2017). A distributed denial of service
(DDoS) is a huge scale DoS assault where the culprit utilizes in excess of one remarkable IP
address, regularly a huge number of them (Mansfield, 2016). It likewise makes it very hard
to identify better client motion from attack movement when extend crosswise over such a
large number the source. As an option or enlargement of a DDoS, assaults may comprise
fashioning of IP dispatcher addresses additionally confusing recognizing and crushing the
assault (Modi, & Quadir, 2014).
Sometimes hacker utilizes a scheme of zombie PCs to undermine a meticulous Web
website. The attention is entirely clear that is hacker tells each one of the PCs on his botnet
to contact a exacting attendant (Saied, Overill, & Radzik, 2016). We judge this type of
3
Introduction
DDOS is defined as the distributed denial of service which is a part of a DOS assault.
It is one of the biggest security problems for any wireless and computer devices and the
rate of DDOS is growing rapidly since the last few years (Bawany, Shamsi, & Salah, 2017).
This type of attacks includes various hacking devices and algorithms which are also called
the botnet and in which hackers target online websites by sending traffic signals. The main
objective of this report is to understand the fundamental concept of DDOS and various
prevention techniques to reduce this type of problem (Bhuyan, Bhattacharyya, & Kalita,
2015). This report is divided into three parts, for example, the overview of DDOS, a recent
case study, and prevention methods.
Overview of DDOS
In a computer system, the distributed denial of services is a kind of attack in which
hacker design a network system that produces various traffic signals into user personal
servers. This is a very serious problem for an organization and it also impacts the user
personal information or data files (Kamikubo, & Saito, 2017). This type of security risk uses
flooding mechanism to block user’s computer systems and peripheral devices. DDOS
targets on business industries, banking servers, credit and debit cards, and online payment
methods (Kolias, Kambourakis, Stavrou, & Voas, 2017). A distributed denial of service
(DDoS) is a huge scale DoS assault where the culprit utilizes in excess of one remarkable IP
address, regularly a huge number of them (Mansfield, 2016). It likewise makes it very hard
to identify better client motion from attack movement when extend crosswise over such a
large number the source. As an option or enlargement of a DDoS, assaults may comprise
fashioning of IP dispatcher addresses additionally confusing recognizing and crushing the
assault (Modi, & Quadir, 2014).
Sometimes hacker utilizes a scheme of zombie PCs to undermine a meticulous Web
website. The attention is entirely clear that is hacker tells each one of the PCs on his botnet
to contact a exacting attendant (Saied, Overill, & Radzik, 2016). We judge this type of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
DDOS
4
assault as Distributed Denial of Service (DDoS) assault. There are various parts of DDOS
which are following-
Ping of Death: in which hackers generate large electronic data packets and transfer these
traffic signals to victims.
Mail bomb: attackers share a massive number of spam e-mails and messages by which
they block the server of any user.
Smurf Attack: in this bots or attackers transfer internet control message protocol systems
into computer systems and other peripheral devices (Singh, Singh, & Kumar, 2017).
Teardrop: In which hackers produce pieces of the illegitimate data system. After that user
system tries to recombine the pieces into a packet and crashes as a result.
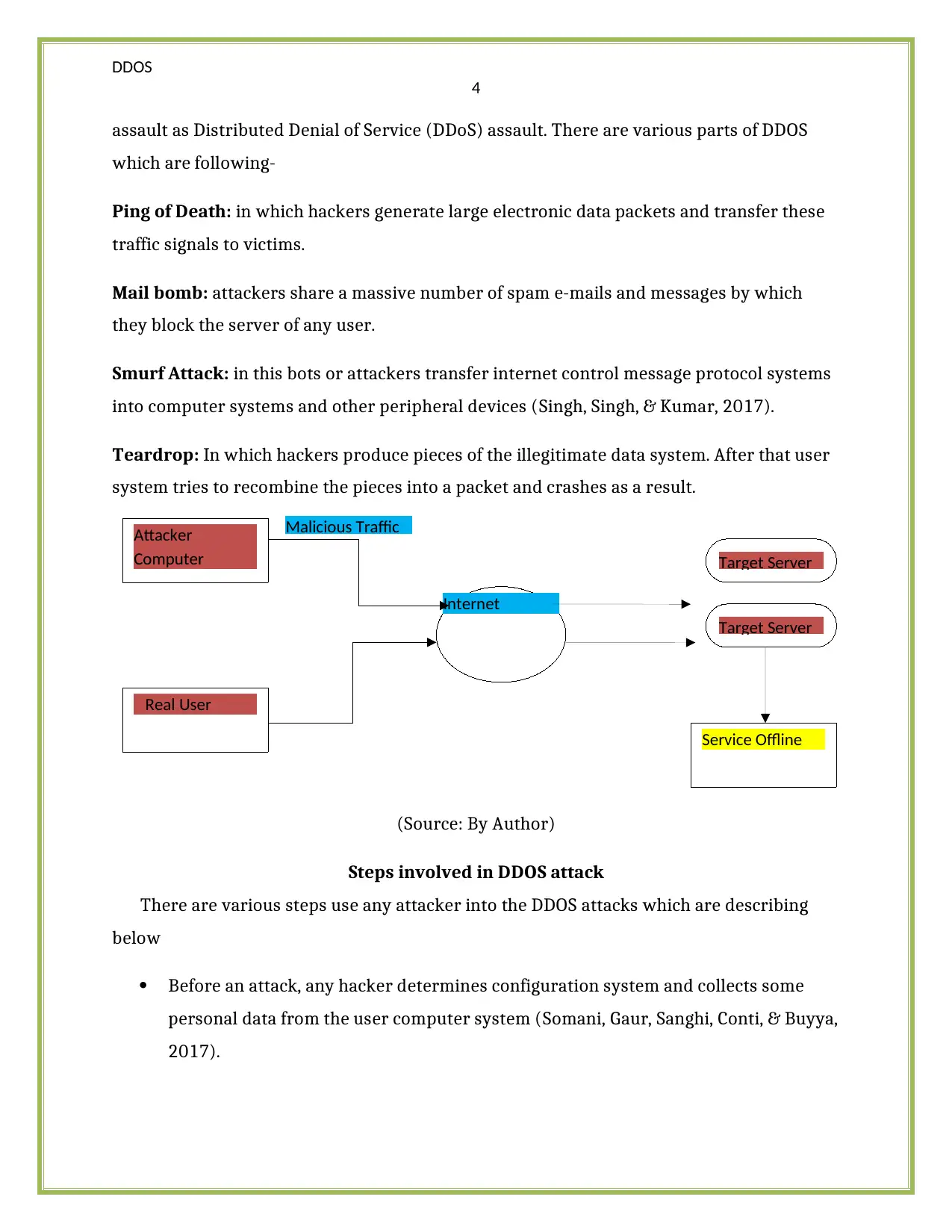
(Source: By Author)
Steps involved in DDOS attack
There are various steps use any attacker into the DDOS attacks which are describing
below
Before an attack, any hacker determines configuration system and collects some
personal data from the user computer system (Somani, Gaur, Sanghi, Conti, & Buyya,
2017).
Attacker
Computer
Real User
Internet
Target Server
Service Offline
Target Server
Malicious Traffic
4
assault as Distributed Denial of Service (DDoS) assault. There are various parts of DDOS
which are following-
Ping of Death: in which hackers generate large electronic data packets and transfer these
traffic signals to victims.
Mail bomb: attackers share a massive number of spam e-mails and messages by which
they block the server of any user.
Smurf Attack: in this bots or attackers transfer internet control message protocol systems
into computer systems and other peripheral devices (Singh, Singh, & Kumar, 2017).
Teardrop: In which hackers produce pieces of the illegitimate data system. After that user
system tries to recombine the pieces into a packet and crashes as a result.
(Source: By Author)
Steps involved in DDOS attack
There are various steps use any attacker into the DDOS attacks which are describing
below
Before an attack, any hacker determines configuration system and collects some
personal data from the user computer system (Somani, Gaur, Sanghi, Conti, & Buyya,
2017).
Attacker
Computer
Real User
Internet
Target Server
Service Offline
Target Server
Malicious Traffic
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
DDOS
5
Attackers produce an online server in which they use flooding process and generate
unwanted traffic signals
For DDOS attack bots or hackers spread malicious algorithm to vulnerable networks
in which they send spam e-mails and message into user personal accounts.
After that, they produce a jamming network which is also called as botnet system
The hacker can monitor and control the botnet system and transfer this into user
personal servers
In the end, hacker enters into the user computer system and encrypts all data or
information files and demand money to restore back.
GitHub DDOS attack (Case study)
On February 28 the year 2018, distributed denial of service attacked on GitHub
websites. It is one of the largest DOS attack and in which hackers send botnet and flooding
traffic signals into GitHub websites (Wang, Zheng, Lou, & Hou, 2015). A DDOS assault is a
standout amongst the most well-known techniques utilized by programmers to bring sites
down: it includes besieging locales with more movement than they can deal with, in order
to overpower their servers and it has the ability to crash all personal information or online
website.
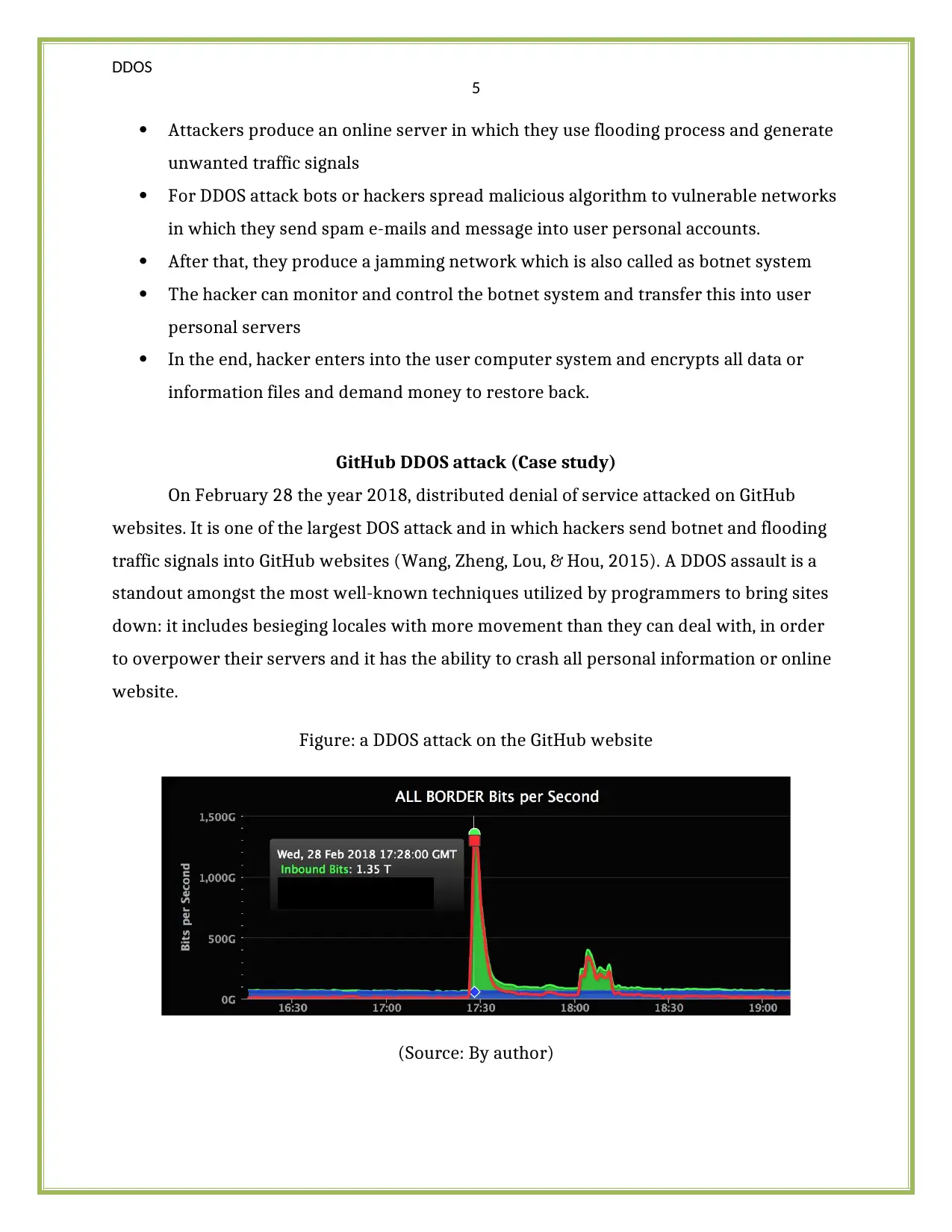
Figure: a DDOS attack on the GitHub website
(Source: By author)
5
Attackers produce an online server in which they use flooding process and generate
unwanted traffic signals
For DDOS attack bots or hackers spread malicious algorithm to vulnerable networks
in which they send spam e-mails and message into user personal accounts.
After that, they produce a jamming network which is also called as botnet system
The hacker can monitor and control the botnet system and transfer this into user
personal servers
In the end, hacker enters into the user computer system and encrypts all data or
information files and demand money to restore back.
GitHub DDOS attack (Case study)
On February 28 the year 2018, distributed denial of service attacked on GitHub
websites. It is one of the largest DOS attack and in which hackers send botnet and flooding
traffic signals into GitHub websites (Wang, Zheng, Lou, & Hou, 2015). A DDOS assault is a
standout amongst the most well-known techniques utilized by programmers to bring sites
down: it includes besieging locales with more movement than they can deal with, in order
to overpower their servers and it has the ability to crash all personal information or online
website.
Figure: a DDOS attack on the GitHub website
(Source: By author)

DDOS
6
In this case, around 1.35 Tb per second of traffic signals transferred to the Github
website and many users faced this problem. In which the overall service of this website go
down for 10 minutes and many users lose their personal data or information (Yan, Yu,
Gong, & Li, 2016). After that incidents, this online website requested helped from Akamai
Prolexic and they also produced various security plans like cryptography and encryption
method. After that Github changed their security plans and also replaced connecting wires
to avoid this type of problem in future (Yu, Tian, Guo, & Wu, 2014). Akami monitored and
managed online server of GitHub and avoid the problem of a DDOS attack in a few minutes.
Before this attack, in the year 2016, the US-based DNS organization suffered from this
attack and it was hit b 1.2 terabits per second of traffic signals. Hackers first identified the
IP address of this online websites and also transfer various flooding signals into their
online servers.
Therefore, it is estimated that this is one of the biggest DDOS attacks in the year
2016 and people can lose their personal information. Encryption is one of the best methods
which block spam e-mails and messages and also improve the performance of the human
communication system. In this attack, hackers used a Memcached protocol which is also
called as a Memcached DDOS attack (Yu, Tian, Guo, & Wu, 2014). It is a free space
distributed caching process which is used to improve the speed of dynamic websites with
the help of alleviating database system.
Figure: DDOS process
6
In this case, around 1.35 Tb per second of traffic signals transferred to the Github
website and many users faced this problem. In which the overall service of this website go
down for 10 minutes and many users lose their personal data or information (Yan, Yu,
Gong, & Li, 2016). After that incidents, this online website requested helped from Akamai
Prolexic and they also produced various security plans like cryptography and encryption
method. After that Github changed their security plans and also replaced connecting wires
to avoid this type of problem in future (Yu, Tian, Guo, & Wu, 2014). Akami monitored and
managed online server of GitHub and avoid the problem of a DDOS attack in a few minutes.
Before this attack, in the year 2016, the US-based DNS organization suffered from this
attack and it was hit b 1.2 terabits per second of traffic signals. Hackers first identified the
IP address of this online websites and also transfer various flooding signals into their
online servers.
Therefore, it is estimated that this is one of the biggest DDOS attacks in the year
2016 and people can lose their personal information. Encryption is one of the best methods
which block spam e-mails and messages and also improve the performance of the human
communication system. In this attack, hackers used a Memcached protocol which is also
called as a Memcached DDOS attack (Yu, Tian, Guo, & Wu, 2014). It is a free space
distributed caching process which is used to improve the speed of dynamic websites with
the help of alleviating database system.
Figure: DDOS process
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

DDOS
7
(Source: By author)
At 17:28 GMT, February 28th, Akamai encountered a 1.3 Tb per second DDOS
assault against one of our clients, a product advancement organization, driven by
Memcached reflection (Yu, Tian, Guo, & Wu, 2014). This assault was the biggest assault
seen to date by Akamai, more than double the span of the September 2016 assaults that
reported the Mirai botnet and potentially the biggest DDOS assault freely uncovered. Due
to this attack, GitHub faced the financial problem and it also reduced their value into the
market. Many people removed their personal accounts from this websites and at that time
around 50% of computer systems were defected due to this attack.
Methods to avoid DDOS attack
There are various kinds of process or steps which are used by many organization and
online communities to avoid the problem of DDOS attacks which are following-
Identify the DDOS attacks early
Overprovision bandwidth
Defend at the network perimeter
Call your hosting provider
Adopt various security programs like firewall, encryption and pattern recognition
Generate a DDOS playbook
Use a Content Delivery Network
Practice for attacks
Buy a dedicated server
Hardware upgrades
System Hardening
Block spoofed IP addresses
Blacklist and Whitelist
Create an incident report
Improve the security of your Internet of Things (IoT) devices
Monitor traffic levels (Wang, Zheng, Lou, & Hou, 2015).
7
(Source: By author)
At 17:28 GMT, February 28th, Akamai encountered a 1.3 Tb per second DDOS
assault against one of our clients, a product advancement organization, driven by
Memcached reflection (Yu, Tian, Guo, & Wu, 2014). This assault was the biggest assault
seen to date by Akamai, more than double the span of the September 2016 assaults that
reported the Mirai botnet and potentially the biggest DDOS assault freely uncovered. Due
to this attack, GitHub faced the financial problem and it also reduced their value into the
market. Many people removed their personal accounts from this websites and at that time
around 50% of computer systems were defected due to this attack.
Methods to avoid DDOS attack
There are various kinds of process or steps which are used by many organization and
online communities to avoid the problem of DDOS attacks which are following-
Identify the DDOS attacks early
Overprovision bandwidth
Defend at the network perimeter
Call your hosting provider
Adopt various security programs like firewall, encryption and pattern recognition
Generate a DDOS playbook
Use a Content Delivery Network
Practice for attacks
Buy a dedicated server
Hardware upgrades
System Hardening
Block spoofed IP addresses
Blacklist and Whitelist
Create an incident report
Improve the security of your Internet of Things (IoT) devices
Monitor traffic levels (Wang, Zheng, Lou, & Hou, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

DDOS
8
All these steps are used by many organization and online websites and it is estimated
that these prevention methods can avoid DDOS attack by 70%. Therefore this type of
security risk can be reduced by adopting security plans and by increasing authentic servers
(Wang, Zheng, Lou, & Hou, 2015).
Conclusion
DDOS and DOS both are very common cyber- attacks in the field of the computer
system and it is observed that the rate of DDOS is increased by 34% between 2016 and
2018. Many people lost their privacy and various organizations are also suffering from this
security risk. This report described the working principle of DDOS attack and one real-
world example of this attack. GitHub is one of the best examples of this attack and it is
estimated that this is a largest DDOS attack in the field of cyber crimes that produced 1.3
Tbps traffic signals. To reduce this type of problem various organizations developed many
policies and strategies which are described in this report. However, users can avoid this
type of issue by using a backup plan like cloud computing in which they can secure their
personal information. Hacker's uses a flooding process in the DDOS attack which cannot be
easily blocked and they attacks banking servers, and online communities. People should
adopt security programs and update their software on a regular basis and use only
authentic websites by which they can reduce this DDOS and other various cyber-attacks.
8
All these steps are used by many organization and online websites and it is estimated
that these prevention methods can avoid DDOS attack by 70%. Therefore this type of
security risk can be reduced by adopting security plans and by increasing authentic servers
(Wang, Zheng, Lou, & Hou, 2015).
Conclusion
DDOS and DOS both are very common cyber- attacks in the field of the computer
system and it is observed that the rate of DDOS is increased by 34% between 2016 and
2018. Many people lost their privacy and various organizations are also suffering from this
security risk. This report described the working principle of DDOS attack and one real-
world example of this attack. GitHub is one of the best examples of this attack and it is
estimated that this is a largest DDOS attack in the field of cyber crimes that produced 1.3
Tbps traffic signals. To reduce this type of problem various organizations developed many
policies and strategies which are described in this report. However, users can avoid this
type of issue by using a backup plan like cloud computing in which they can secure their
personal information. Hacker's uses a flooding process in the DDOS attack which cannot be
easily blocked and they attacks banking servers, and online communities. People should
adopt security programs and update their software on a regular basis and use only
authentic websites by which they can reduce this DDOS and other various cyber-attacks.

DDOS
9
References
Bawany, N. Z., Shamsi, J. A., & Salah, K. (2017). DDoS attack detection and mitigation using
SDN: methods, practices, and solutions. Arabian Journal for Science and Engineering,
42(2), 425-441.
Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2015). An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern
Recognition Letters, 51, 1-7.
Kamikubo, R., & Saito, T. (2017). Browser-Based DDoS Attacks without Javascript.
international journal of advanced computer science and applications, 8(12), 276-280.
Kolias, C., Kambourakis, G., Stavrou, A., & Voas, J. (2017). DDoS in the IoT: Mirai and other
botnets. Computer, 50(7), 80-84.
Mansfield-Devine, S. (2016). DDoS goes mainstream: how headline-grabbing attacks could
make this threat an organization's biggest nightmare. Network Security, 2016(11), 7-
13.
Modi, K., & Quadir, A. (2014). Detection and Prevention of DDoS Attacks on the Cloud using
Double-TCP Mechanism and HMM-based Architecture. International Journal of Cloud
Computing and Services Science, 3(2), 113.
Saied, A., Overill, R. E., & Radzik, T. (2016). Detection of known and unknown DDoS attacks
using Artificial Neural Networks. Neurocomputing, 172, 385-393.
Singh, K., Singh, P., & Kumar, K. (2017). Application layer HTTP-GET floods DDoS attacks:
Research landscape and challenges. Computers & security, 65, 344-372.
Somani, G., Gaur, M. S., Sanghi, D., Conti, M., & Buyya, R. (2017). DDoS attacks in cloud
computing: Issues, taxonomy, and future directions. Computer Communications, 107,
30-48.
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, 308-319.
Yan, Q., Yu, F. R., Gong, Q., & Li, J. (2016). Software-defined networking (SDN) and
distributed denial of service (DDoS) attacks in cloud computing environments: A
9
References
Bawany, N. Z., Shamsi, J. A., & Salah, K. (2017). DDoS attack detection and mitigation using
SDN: methods, practices, and solutions. Arabian Journal for Science and Engineering,
42(2), 425-441.
Bhuyan, M. H., Bhattacharyya, D. K., & Kalita, J. K. (2015). An empirical evaluation of
information metrics for low-rate and high-rate DDoS attack detection. Pattern
Recognition Letters, 51, 1-7.
Kamikubo, R., & Saito, T. (2017). Browser-Based DDoS Attacks without Javascript.
international journal of advanced computer science and applications, 8(12), 276-280.
Kolias, C., Kambourakis, G., Stavrou, A., & Voas, J. (2017). DDoS in the IoT: Mirai and other
botnets. Computer, 50(7), 80-84.
Mansfield-Devine, S. (2016). DDoS goes mainstream: how headline-grabbing attacks could
make this threat an organization's biggest nightmare. Network Security, 2016(11), 7-
13.
Modi, K., & Quadir, A. (2014). Detection and Prevention of DDoS Attacks on the Cloud using
Double-TCP Mechanism and HMM-based Architecture. International Journal of Cloud
Computing and Services Science, 3(2), 113.
Saied, A., Overill, R. E., & Radzik, T. (2016). Detection of known and unknown DDoS attacks
using Artificial Neural Networks. Neurocomputing, 172, 385-393.
Singh, K., Singh, P., & Kumar, K. (2017). Application layer HTTP-GET floods DDoS attacks:
Research landscape and challenges. Computers & security, 65, 344-372.
Somani, G., Gaur, M. S., Sanghi, D., Conti, M., & Buyya, R. (2017). DDoS attacks in cloud
computing: Issues, taxonomy, and future directions. Computer Communications, 107,
30-48.
Wang, B., Zheng, Y., Lou, W., & Hou, Y. T. (2015). DDoS attack protection in the era of cloud
computing and software-defined networking. Computer Networks, 81, 308-319.
Yan, Q., Yu, F. R., Gong, Q., & Li, J. (2016). Software-defined networking (SDN) and
distributed denial of service (DDoS) attacks in cloud computing environments: A
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

DDOS
10
survey, some research issues, and challenges. IEEE Communications Surveys &
Tutorials, 18(1), 602-622.
Yu, S., Tian, Y., Guo, S., & Wu, D. O. (2014). Can we beat DDoS attacks in clouds?. IEEE
Transactions on Parallel and Distributed Systems, 25(9), 2245-2254.
10
survey, some research issues, and challenges. IEEE Communications Surveys &
Tutorials, 18(1), 602-622.
Yu, S., Tian, Y., Guo, S., & Wu, D. O. (2014). Can we beat DDoS attacks in clouds?. IEEE
Transactions on Parallel and Distributed Systems, 25(9), 2245-2254.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





