Deep Packet Analysis
VerifiedAdded on 2022/09/12
|14
|2284
|19
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: DEEP PACKET ANALYSIS
Deep Packet Analysis
Name of the Student
Name of the University
Author Note
Deep Packet Analysis
Name of the Student
Name of the University
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1DEEP PACKET ANALYSIS
Table of Contents
Introduction................................................................................................................................2
Statistical Analysis.....................................................................................................................2
Attack Identification...................................................................................................................2
Attack Explanation.....................................................................................................................3
Conclusion................................................................................................................................10
References................................................................................................................................12
Table of Contents
Introduction................................................................................................................................2
Statistical Analysis.....................................................................................................................2
Attack Identification...................................................................................................................2
Attack Explanation.....................................................................................................................3
Conclusion................................................................................................................................10
References................................................................................................................................12

2DEEP PACKET ANALYSIS
Introduction
While users on an individual basis carry out various searches on the internet, there is a
potential possibility of the sensitive data that belongs to the user can be stolen or used to
cause future damage to the user (Sanders, 2017). In this report, a Wireshark file has been
analysed in order to identify such threats that might be potentially active and acting upon the
activity of the user online. Wireshark provisions with the extensive interpretation of all the
traffic that is a common network of binary codes for identification of threats that might be
kept active by the potential hackers and might lead to serious consequences on the users end
(Chappell, 2017). Wireshark has been used for a number of advantages such as its
interpretive abilities along with the ability to record and monitor all the traffic that is present
on a single webpage and hence, has been used within this analysis to particular identify the
threat that might have been attacking and stealing personal information from the user who
had been browsing the webpages for personal usage.
Statistical Analysis
Using the statistical tools that share the existence within Wireshark provision with a
helping hand towards analysing the browsing activity of an individual user and help with the
identification of the attacks that are posed towards the users in general.
In this experiment we are observe different type of protocol. There are several kinds of
protocol are using such as DNS, TCP, ARP, HTTP, IGMPV3, SSH etc.
DNS:-
DNS is the domain name system and it is the distributed database applied in a
hierarchy of name servers. It is very much difficult to find out the protocol address which is
associated to a website because there are huge number of websites are able to create the
Introduction
While users on an individual basis carry out various searches on the internet, there is a
potential possibility of the sensitive data that belongs to the user can be stolen or used to
cause future damage to the user (Sanders, 2017). In this report, a Wireshark file has been
analysed in order to identify such threats that might be potentially active and acting upon the
activity of the user online. Wireshark provisions with the extensive interpretation of all the
traffic that is a common network of binary codes for identification of threats that might be
kept active by the potential hackers and might lead to serious consequences on the users end
(Chappell, 2017). Wireshark has been used for a number of advantages such as its
interpretive abilities along with the ability to record and monitor all the traffic that is present
on a single webpage and hence, has been used within this analysis to particular identify the
threat that might have been attacking and stealing personal information from the user who
had been browsing the webpages for personal usage.
Statistical Analysis
Using the statistical tools that share the existence within Wireshark provision with a
helping hand towards analysing the browsing activity of an individual user and help with the
identification of the attacks that are posed towards the users in general.
In this experiment we are observe different type of protocol. There are several kinds of
protocol are using such as DNS, TCP, ARP, HTTP, IGMPV3, SSH etc.
DNS:-
DNS is the domain name system and it is the distributed database applied in a
hierarchy of name servers. It is very much difficult to find out the protocol address which is
associated to a website because there are huge number of websites are able to create the

3DEEP PACKET ANALYSIS
several IP address instantly. It is a protocol within a set of standards for how the operating
systems exchange information on the internet and several private networks. Operating system
(Computer) and other network devices on the internet use a protocol address to route the user
request and trying to reach the final destination point. With the help of DNS protocol the user
are connect there server name, and manages through the database which can map in the
protocol.
In this attack there are several source are using in the DNS protocol. Several type of standard
query are using to these attack.
TCP:-
TCP is the transmission control protocol .TCP is defines the standard of the network
and also maintains the network conversation through the application program can exchange
data. Transmission protocol works with the IP and describes the operating systems which can
sends the every data packet. It is the standard and confirms a connection is maintained and
established until the exchange between the servers and receiving the complete message.
several IP address instantly. It is a protocol within a set of standards for how the operating
systems exchange information on the internet and several private networks. Operating system
(Computer) and other network devices on the internet use a protocol address to route the user
request and trying to reach the final destination point. With the help of DNS protocol the user
are connect there server name, and manages through the database which can map in the
protocol.
In this attack there are several source are using in the DNS protocol. Several type of standard
query are using to these attack.
TCP:-
TCP is the transmission control protocol .TCP is defines the standard of the network
and also maintains the network conversation through the application program can exchange
data. Transmission protocol works with the IP and describes the operating systems which can
sends the every data packet. It is the standard and confirms a connection is maintained and
established until the exchange between the servers and receiving the complete message.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
4DEEP PACKET ANALYSIS
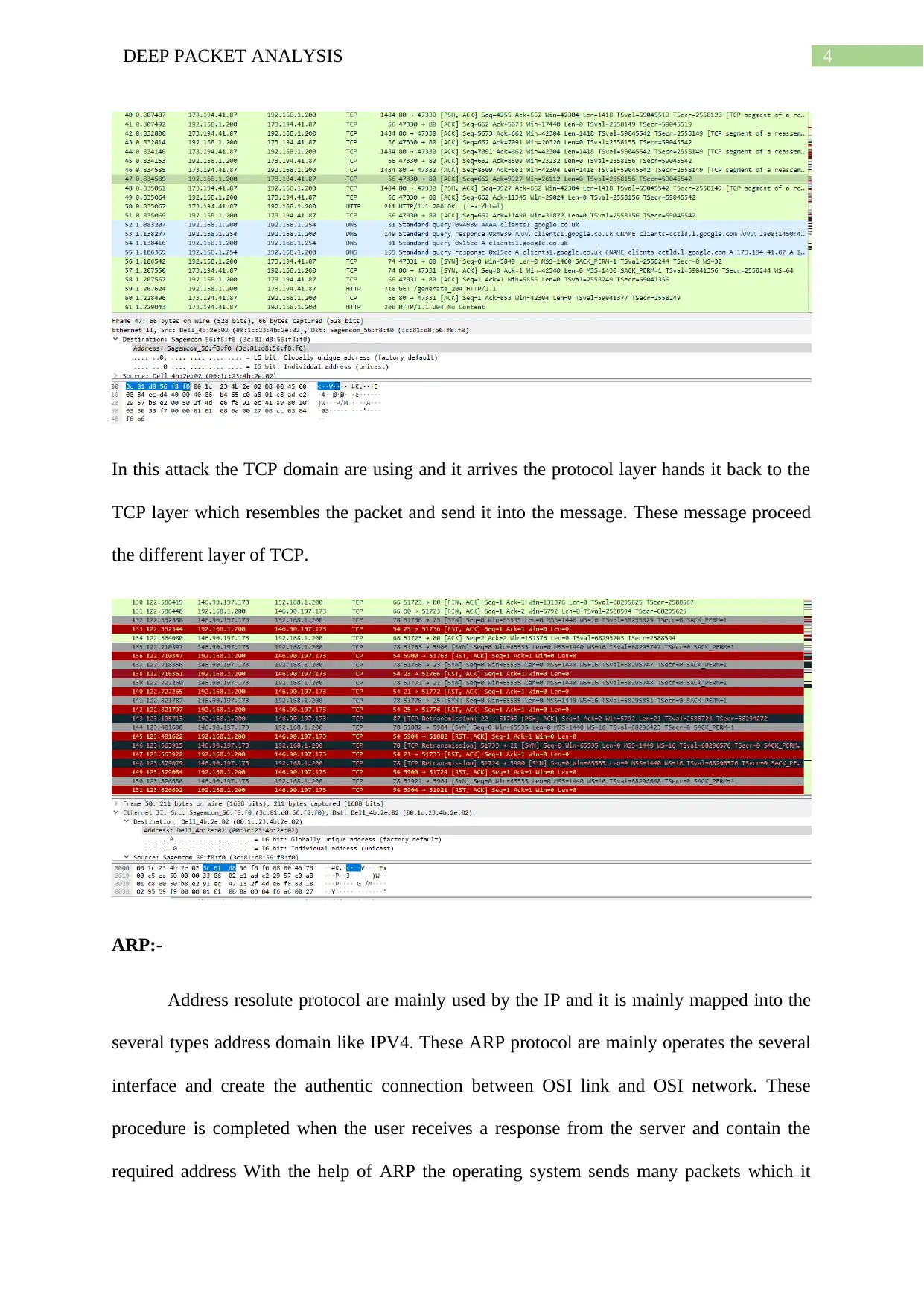
In this attack the TCP domain are using and it arrives the protocol layer hands it back to the
TCP layer which resembles the packet and send it into the message. These message proceed
the different layer of TCP.
ARP:-
Address resolute protocol are mainly used by the IP and it is mainly mapped into the
several types address domain like IPV4. These ARP protocol are mainly operates the several
interface and create the authentic connection between OSI link and OSI network. These
procedure is completed when the user receives a response from the server and contain the
required address With the help of ARP the operating system sends many packets which it
In this attack the TCP domain are using and it arrives the protocol layer hands it back to the
TCP layer which resembles the packet and send it into the message. These message proceed
the different layer of TCP.
ARP:-
Address resolute protocol are mainly used by the IP and it is mainly mapped into the
several types address domain like IPV4. These ARP protocol are mainly operates the several
interface and create the authentic connection between OSI link and OSI network. These
procedure is completed when the user receives a response from the server and contain the
required address With the help of ARP the operating system sends many packets which it
5DEEP PACKET ANALYSIS
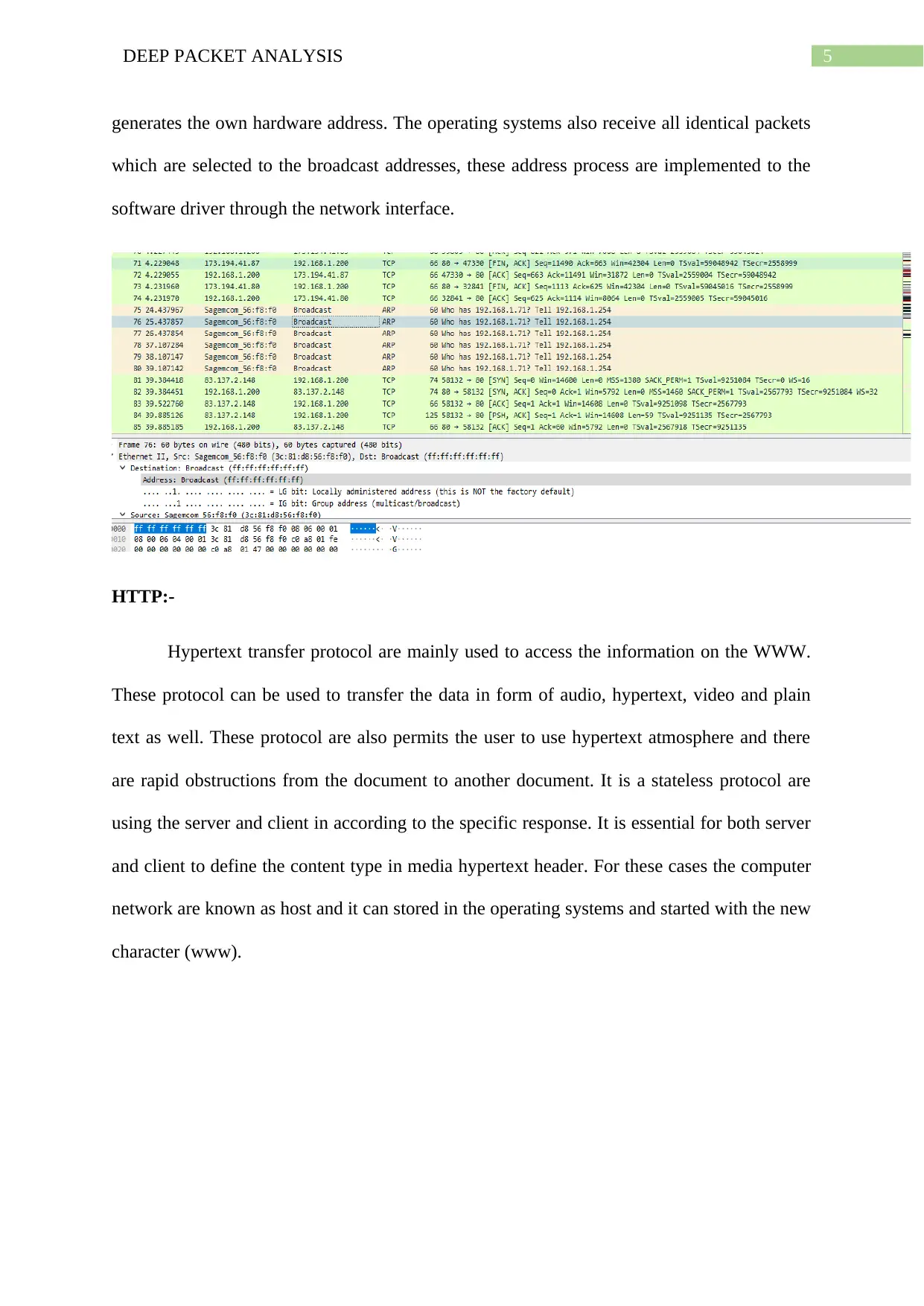
generates the own hardware address. The operating systems also receive all identical packets
which are selected to the broadcast addresses, these address process are implemented to the
software driver through the network interface.
HTTP:-
Hypertext transfer protocol are mainly used to access the information on the WWW.
These protocol can be used to transfer the data in form of audio, hypertext, video and plain
text as well. These protocol are also permits the user to use hypertext atmosphere and there
are rapid obstructions from the document to another document. It is a stateless protocol are
using the server and client in according to the specific response. It is essential for both server
and client to define the content type in media hypertext header. For these cases the computer
network are known as host and it can stored in the operating systems and started with the new
character (www).
generates the own hardware address. The operating systems also receive all identical packets
which are selected to the broadcast addresses, these address process are implemented to the
software driver through the network interface.
HTTP:-
Hypertext transfer protocol are mainly used to access the information on the WWW.
These protocol can be used to transfer the data in form of audio, hypertext, video and plain
text as well. These protocol are also permits the user to use hypertext atmosphere and there
are rapid obstructions from the document to another document. It is a stateless protocol are
using the server and client in according to the specific response. It is essential for both server
and client to define the content type in media hypertext header. For these cases the computer
network are known as host and it can stored in the operating systems and started with the new
character (www).
6DEEP PACKET ANALYSIS
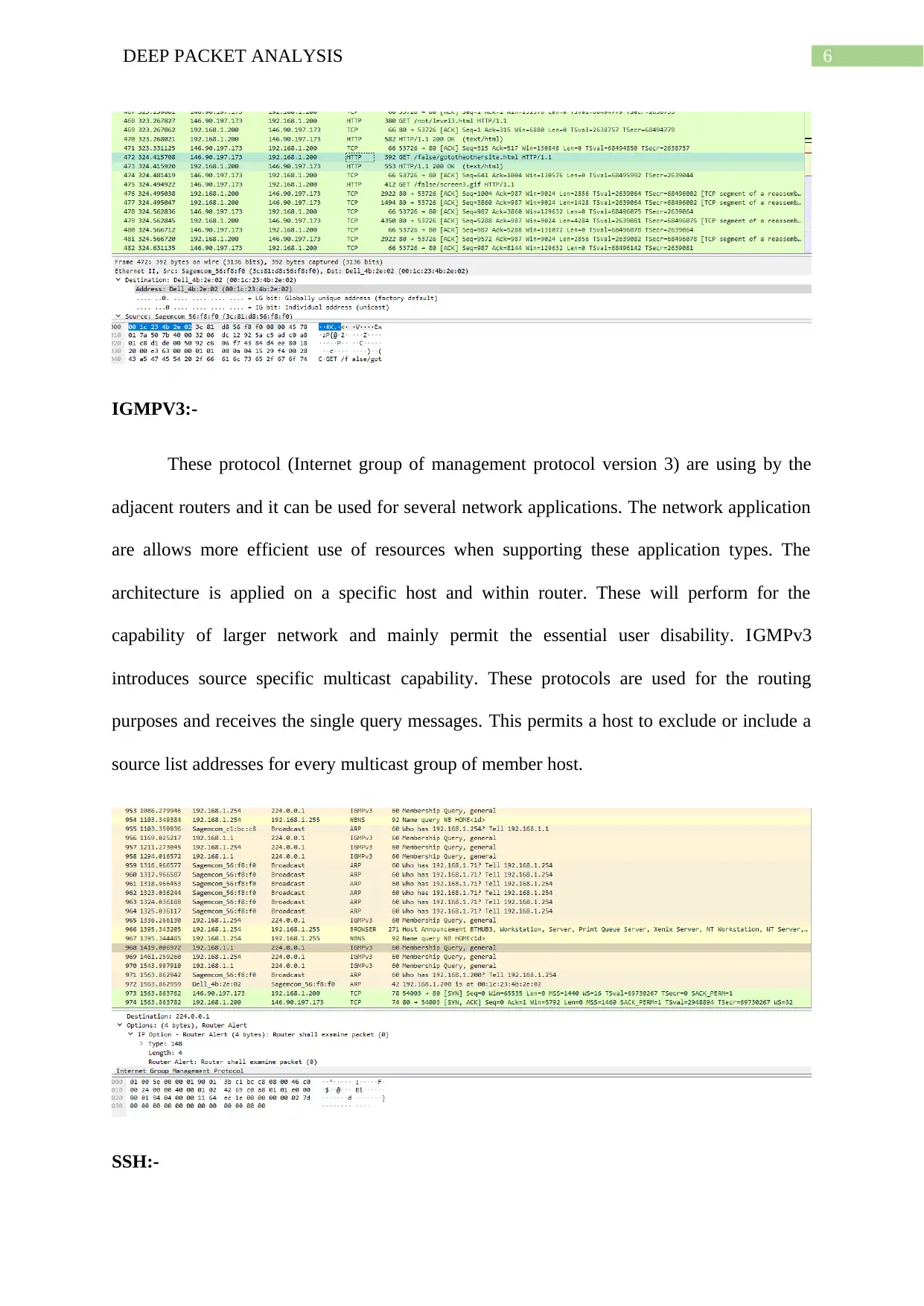
IGMPV3:-
These protocol (Internet group of management protocol version 3) are using by the
adjacent routers and it can be used for several network applications. The network application
are allows more efficient use of resources when supporting these application types. The
architecture is applied on a specific host and within router. These will perform for the
capability of larger network and mainly permit the essential user disability. IGMPv3
introduces source specific multicast capability. These protocols are used for the routing
purposes and receives the single query messages. This permits a host to exclude or include a
source list addresses for every multicast group of member host.
SSH:-
IGMPV3:-
These protocol (Internet group of management protocol version 3) are using by the
adjacent routers and it can be used for several network applications. The network application
are allows more efficient use of resources when supporting these application types. The
architecture is applied on a specific host and within router. These will perform for the
capability of larger network and mainly permit the essential user disability. IGMPv3
introduces source specific multicast capability. These protocols are used for the routing
purposes and receives the single query messages. This permits a host to exclude or include a
source list addresses for every multicast group of member host.
SSH:-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7DEEP PACKET ANALYSIS
The secure shell method are using for the remote login which delivers the alternative
options for high authentication and keeps the communication integrity and security with
strong encryption. The client of SSH try to determines the link setup process and uses
cryptography to confirm the SSH server identity. The SSH protocol uses hashing algorithms
and robust symmetric encryption to confirm the data privacy and integrity that is replaced
between the server and client. The SSH protocol are also consists a mechanism that confirms
the data integrity using common hash algorithm.
Attack Identification
The attacks that have been identified with the help of this Wireshark technique have been
mentioned below and individual explanation of each attack have been briefly explained in the
following section.
ET SCAN Potential VNC Scan 5900-5920
ET SCAN Potential VNC Scan 5800-5820
ET SCAN Nikto Web App Scan in Progress
GPL WEB_SERVER /~root access
Multiple tracing and scanning of packets transferring password information
The secure shell method are using for the remote login which delivers the alternative
options for high authentication and keeps the communication integrity and security with
strong encryption. The client of SSH try to determines the link setup process and uses
cryptography to confirm the SSH server identity. The SSH protocol uses hashing algorithms
and robust symmetric encryption to confirm the data privacy and integrity that is replaced
between the server and client. The SSH protocol are also consists a mechanism that confirms
the data integrity using common hash algorithm.
Attack Identification
The attacks that have been identified with the help of this Wireshark technique have been
mentioned below and individual explanation of each attack have been briefly explained in the
following section.
ET SCAN Potential VNC Scan 5900-5920
ET SCAN Potential VNC Scan 5800-5820
ET SCAN Nikto Web App Scan in Progress
GPL WEB_SERVER /~root access
Multiple tracing and scanning of packets transferring password information

8DEEP PACKET ANALYSIS
Pen test conducted by attacker with Nikto
Cross-site Scripting (XSS)
Remote Code execution
ET WEB_SERVER Possible CVE-2014-6271 Attempt.
Attack Explanation
Attack scripts run on packet
Cross-site Scripting (XSS) refers to a client-side injection attack that has been
identified in this scenario (Bock, 2019). This attack was specifically performed upon the user
by the respective hacker who had been doing the previous all of the attacks with the help of
certain tools in order to execute malicious scripts on the web browser in the form of a trap to
capture sensitive information belonging to the user.
Remote Code execution also refers to another type of attack that has been posed upon
the user in this scenario (Mishra, 2016). This attack is the ability of a particular hacker to
access a computing device that belongs to someone else as well as to make changes after the
access has been gained. The device that needs to be attacked by the hacker can be
geographically located at any place on the globe.
Pen test conducted by attacker with Nikto
Cross-site Scripting (XSS)
Remote Code execution
ET WEB_SERVER Possible CVE-2014-6271 Attempt.
Attack Explanation
Attack scripts run on packet
Cross-site Scripting (XSS) refers to a client-side injection attack that has been
identified in this scenario (Bock, 2019). This attack was specifically performed upon the user
by the respective hacker who had been doing the previous all of the attacks with the help of
certain tools in order to execute malicious scripts on the web browser in the form of a trap to
capture sensitive information belonging to the user.
Remote Code execution also refers to another type of attack that has been posed upon
the user in this scenario (Mishra, 2016). This attack is the ability of a particular hacker to
access a computing device that belongs to someone else as well as to make changes after the
access has been gained. The device that needs to be attacked by the hacker can be
geographically located at any place on the globe.
9DEEP PACKET ANALYSIS
https://packettotal.com/app/analysis?
id=9fcf1a39aada2b2317513ff3fe3ca47c&name=signature_alerts
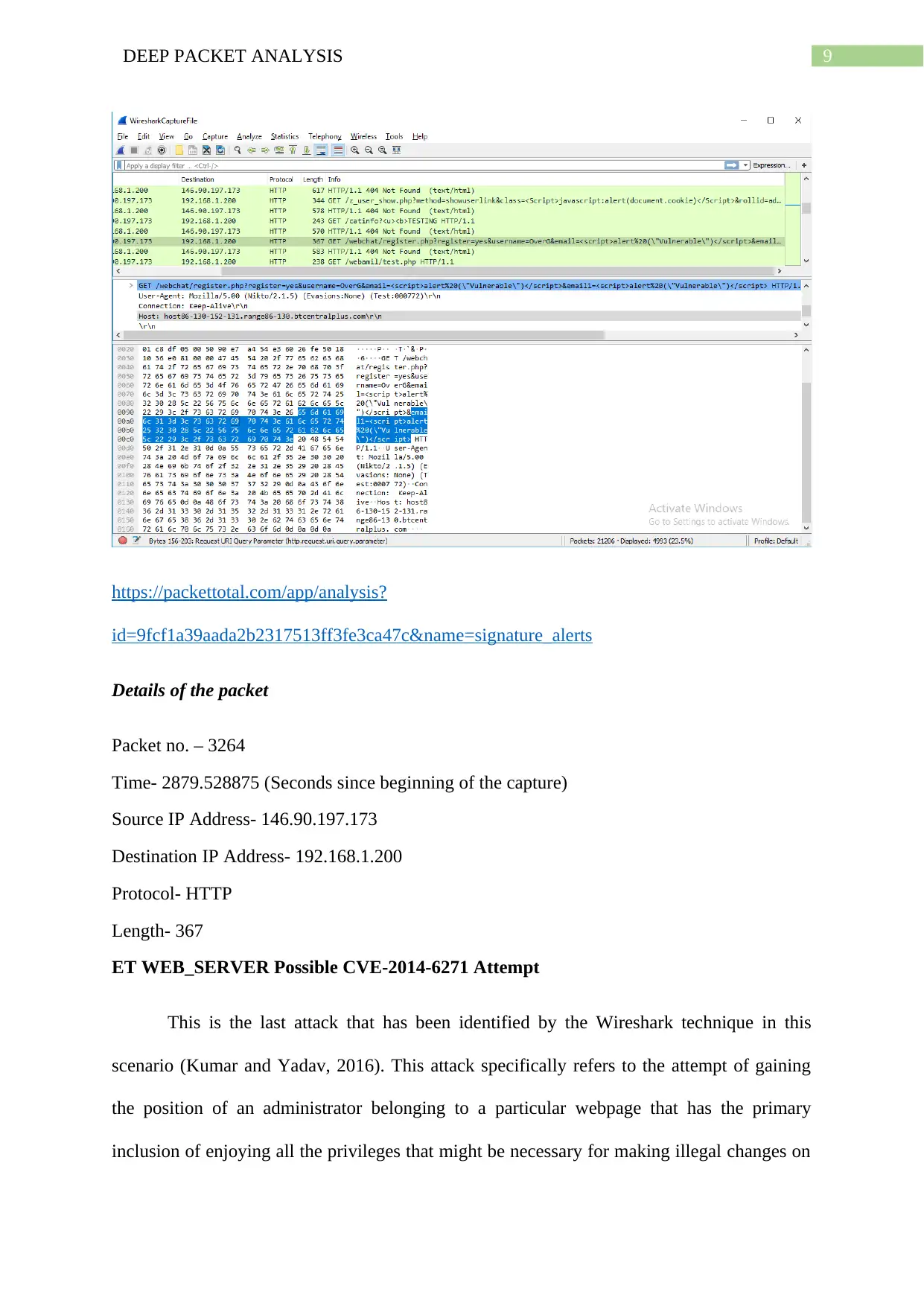
Details of the packet
Packet no. – 3264
Time- 2879.528875 (Seconds since beginning of the capture)
Source IP Address- 146.90.197.173
Destination IP Address- 192.168.1.200
Protocol- HTTP
Length- 367
ET WEB_SERVER Possible CVE-2014-6271 Attempt
This is the last attack that has been identified by the Wireshark technique in this
scenario (Kumar and Yadav, 2016). This attack specifically refers to the attempt of gaining
the position of an administrator belonging to a particular webpage that has the primary
inclusion of enjoying all the privileges that might be necessary for making illegal changes on
https://packettotal.com/app/analysis?
id=9fcf1a39aada2b2317513ff3fe3ca47c&name=signature_alerts
Details of the packet
Packet no. – 3264
Time- 2879.528875 (Seconds since beginning of the capture)
Source IP Address- 146.90.197.173
Destination IP Address- 192.168.1.200
Protocol- HTTP
Length- 367
ET WEB_SERVER Possible CVE-2014-6271 Attempt
This is the last attack that has been identified by the Wireshark technique in this
scenario (Kumar and Yadav, 2016). This attack specifically refers to the attempt of gaining
the position of an administrator belonging to a particular webpage that has the primary
inclusion of enjoying all the privileges that might be necessary for making illegal changes on
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10DEEP PACKET ANALYSIS
the webpages belonging to the original website administrator. In this scenario, the entire
session for which the user had been using or browsing through the web browser had been
posed with an attack where each of the webpage that the user had been visiting throughout
the entire time of browsing. In this regard, the hacker had the primary motive of gaining
access to all the websites and the information that was present on individual webpages of the
website (Nath, 2015). By using tools or techniques of gaining the access, the hacker would
have attempted to take the form of the administrator and to gain the access to edit all the
information that was present on each of the website if the access was gained by the hacker.
Through the session of the user browsing through the webpages, the hacker worked with such
tools and made attempts to be the administrator of all the pages and end up editing and
changing information that belonged to the website only.
Conclusion
Firstly, Wireshark is a tool with the help of which specific analysis or monitoring over
the activity on a browser is tracked. With the help of this procedure related to tracking, a
given scenario had been given of a user who had been browsing through a number of
websites. During the entire session of the user, a number of attacks had been suspected as a
part of the browsing activity that the used had been carrying out for a specific period of time.
The attacks that had been suspected to have occurred has been analysed with the help of this
Wireshark tool. After the entire analysis had been done, a number of attacks had been
identified to have potentially occurred and caused particular damage to the user whose
activity had been analysed. After the analysis was complete, each of the identified threats
have been taken a note of and mentioned down the report with the help of screenshots as a
part of the proof. In regards to this, it has been found that all of the attacks that had been
carried out by the hacker had the primary motive of causing harm to the user and to steal
sensitive information that belonged to the user by the hacker to use them for the purpose of
the webpages belonging to the original website administrator. In this scenario, the entire
session for which the user had been using or browsing through the web browser had been
posed with an attack where each of the webpage that the user had been visiting throughout
the entire time of browsing. In this regard, the hacker had the primary motive of gaining
access to all the websites and the information that was present on individual webpages of the
website (Nath, 2015). By using tools or techniques of gaining the access, the hacker would
have attempted to take the form of the administrator and to gain the access to edit all the
information that was present on each of the website if the access was gained by the hacker.
Through the session of the user browsing through the webpages, the hacker worked with such
tools and made attempts to be the administrator of all the pages and end up editing and
changing information that belonged to the website only.
Conclusion
Firstly, Wireshark is a tool with the help of which specific analysis or monitoring over
the activity on a browser is tracked. With the help of this procedure related to tracking, a
given scenario had been given of a user who had been browsing through a number of
websites. During the entire session of the user, a number of attacks had been suspected as a
part of the browsing activity that the used had been carrying out for a specific period of time.
The attacks that had been suspected to have occurred has been analysed with the help of this
Wireshark tool. After the entire analysis had been done, a number of attacks had been
identified to have potentially occurred and caused particular damage to the user whose
activity had been analysed. After the analysis was complete, each of the identified threats
have been taken a note of and mentioned down the report with the help of screenshots as a
part of the proof. In regards to this, it has been found that all of the attacks that had been
carried out by the hacker had the primary motive of causing harm to the user and to steal
sensitive information that belonged to the user by the hacker to use them for the purpose of

11DEEP PACKET ANALYSIS
illegal practices and generate benefits. The last attack that had been identified for the analysis
referred to the gaining of administrative privileges in order to gain access to a certain
webpage and to edit the information that is present on the webpage. By doing so, the hacker
aimed at removing important information on such pages and to replace them with
unnecessary and irrelevant information that might not be useful to the user searching for such
information online.
illegal practices and generate benefits. The last attack that had been identified for the analysis
referred to the gaining of administrative privileges in order to gain access to a certain
webpage and to edit the information that is present on the webpage. By doing so, the hacker
aimed at removing important information on such pages and to replace them with
unnecessary and irrelevant information that might not be useful to the user searching for such
information online.

12DEEP PACKET ANALYSIS
References
Bagyalakshmi, G., Rajkumar, G., Arunkumar, N., Easwaran, M., Narasimhan, K., Elamaran,
V., Solarte, M., Hernández, I. and Ramirez-Gonzalez, G., 2018. Network vulnerability
analysis on brain signal/image databases using Nmap and Wireshark tools. IEEE Access, 6,
pp.57144-57151.
Bock, L., 2019. Learn Wireshark: Confidently navigate the Wireshark interface and solve
real-world networking problems. Packt Publishing Ltd.
Bullock, J. and Parker, J.T., 2017. Wireshark for Security Professionals: Using Wireshark
and the Metasploit Framework. John Wiley & Sons.
Chappell, L., 2017. Wireshark 101: Essential Skills for Network Analysis-Wireshark Solution
Series. Laura Chappell University.
Das, R. and Tuna, G., 2017, April. Packet tracing and analysis of network cameras with
Wireshark. In 2017 5th International Symposium on Digital Forensic and Security
(ISDFS) (pp. 1-6). IEEE.
Goyal, P. and Goyal, A., 2017, September. Comparative study of two most popular packet
sniffing tools-Tcpdump and Wireshark. In 2017 9th International Conference on
Computational Intelligence and Communication Networks (CICN) (pp. 77-81). IEEE.
Kumar, A. and Yadav, J.B., 2016. Comparison: Wireshark on different
parameters. International Journal Of Engineering And Computer Science, 5(3), pp.16041-
16046.
Mishra, C., 2016. Mastering Wireshark. Packt Publishing Ltd.
Nath, A., 2015. Packet Analysis with Wireshark. Packt Publishing Ltd.
References
Bagyalakshmi, G., Rajkumar, G., Arunkumar, N., Easwaran, M., Narasimhan, K., Elamaran,
V., Solarte, M., Hernández, I. and Ramirez-Gonzalez, G., 2018. Network vulnerability
analysis on brain signal/image databases using Nmap and Wireshark tools. IEEE Access, 6,
pp.57144-57151.
Bock, L., 2019. Learn Wireshark: Confidently navigate the Wireshark interface and solve
real-world networking problems. Packt Publishing Ltd.
Bullock, J. and Parker, J.T., 2017. Wireshark for Security Professionals: Using Wireshark
and the Metasploit Framework. John Wiley & Sons.
Chappell, L., 2017. Wireshark 101: Essential Skills for Network Analysis-Wireshark Solution
Series. Laura Chappell University.
Das, R. and Tuna, G., 2017, April. Packet tracing and analysis of network cameras with
Wireshark. In 2017 5th International Symposium on Digital Forensic and Security
(ISDFS) (pp. 1-6). IEEE.
Goyal, P. and Goyal, A., 2017, September. Comparative study of two most popular packet
sniffing tools-Tcpdump and Wireshark. In 2017 9th International Conference on
Computational Intelligence and Communication Networks (CICN) (pp. 77-81). IEEE.
Kumar, A. and Yadav, J.B., 2016. Comparison: Wireshark on different
parameters. International Journal Of Engineering And Computer Science, 5(3), pp.16041-
16046.
Mishra, C., 2016. Mastering Wireshark. Packt Publishing Ltd.
Nath, A., 2015. Packet Analysis with Wireshark. Packt Publishing Ltd.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13DEEP PACKET ANALYSIS
Ndatinya, V., Xiao, Z., Manepalli, V.R., Meng, K. and Xiao, Y., 2015. Network forensics
analysis using Wireshark. International Journal of Security and Networks, 10(2), pp.91-106.
Sanders, C., 2017. Practical packet analysis: Using Wireshark to solve real-world network
problems. No Starch Press.
Sandhya, S., Purkayastha, S., Joshua, E. and Deep, A., 2017, January. Assessment of website
security by penetration testing using Wireshark. In 2017 4th International Conference on
Advanced Computing and Communication Systems (ICACCS) (pp. 1-4). IEEE.
Ndatinya, V., Xiao, Z., Manepalli, V.R., Meng, K. and Xiao, Y., 2015. Network forensics
analysis using Wireshark. International Journal of Security and Networks, 10(2), pp.91-106.
Sanders, C., 2017. Practical packet analysis: Using Wireshark to solve real-world network
problems. No Starch Press.
Sandhya, S., Purkayastha, S., Joshua, E. and Deep, A., 2017, January. Assessment of website
security by penetration testing using Wireshark. In 2017 4th International Conference on
Advanced Computing and Communication Systems (ICACCS) (pp. 1-4). IEEE.
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





