Applied Distributed Systems Exam 2017: Concurrency and Transactions
VerifiedAdded on 2023/06/11
|27
|4351
|287
Homework Assignment
AI Summary
This assignment solution covers several key concepts in distributed systems. It begins by explaining how Alice signs a document using a hash algorithm and how Bob verifies the signature. It then details the components of DNS and the name resolution process. The solution further explains distributed transactions and the two-phase commit protocol. Fault tolerance through replication is also discussed, along with types of fault tolerance. A central server algorithm for mutual exclusion based on request priority is designed, and its safety, liveness, and ordering features are analyzed. Finally, the assignment includes examples of transaction interleaving and Java code snippets for patient management and network connections. This document is available on Desklib, a platform offering a wide range of study resources including past papers and solved assignments.

ASIGNMENT.
Question 1
.( Dominikus, S., 2002).
.
A hash algorithm is an algorithm used in hash function which is used to map data of a random
size to a fixed size. Hash functions are commonly used with table(s) as data structure(s).
Hash algorithm –H.
Public key –PubA.
Private key –PriA.
Document(data) –M.
How does Alice sign the document?
For Alice to sign a document the two keys are completely required, public key/private key pair
and the recipient must be in the know that the public key indeed belongs to her. This calls the
need of a hash algorithm also called the hash function which basically is a cryptographic
function represented mathematically.
Hash algorithm H
Input data
Output data
1 | P a g e
start
Read input
Input=input*M
Write
output
end
Question 1
.( Dominikus, S., 2002).
.
A hash algorithm is an algorithm used in hash function which is used to map data of a random
size to a fixed size. Hash functions are commonly used with table(s) as data structure(s).
Hash algorithm –H.
Public key –PubA.
Private key –PriA.
Document(data) –M.
How does Alice sign the document?
For Alice to sign a document the two keys are completely required, public key/private key pair
and the recipient must be in the know that the public key indeed belongs to her. This calls the
need of a hash algorithm also called the hash function which basically is a cryptographic
function represented mathematically.
Hash algorithm H
Input data
Output data
1 | P a g e
start
Read input
Input=input*M
Write
output
end
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
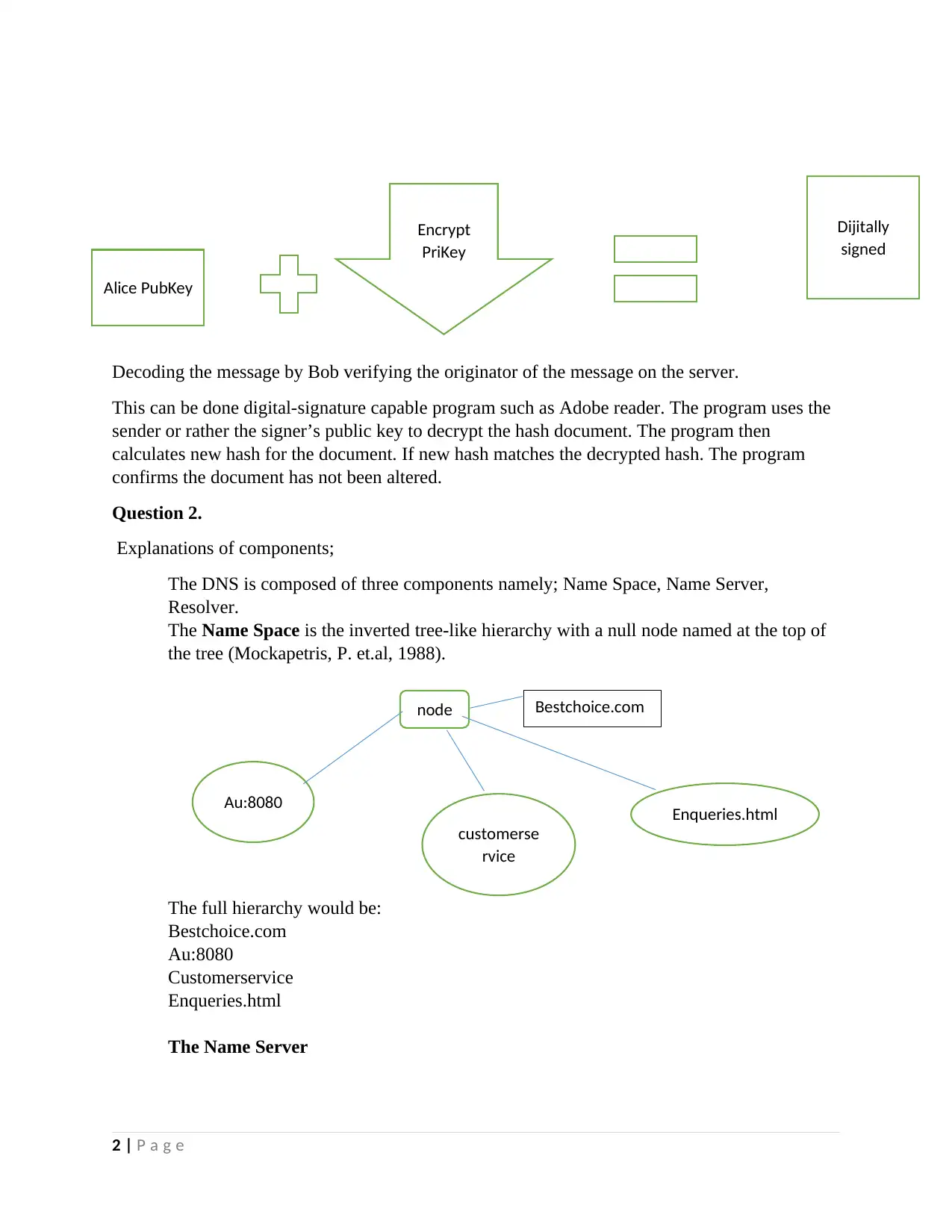
Decoding the message by Bob verifying the originator of the message on the server.
This can be done digital-signature capable program such as Adobe reader. The program uses the
sender or rather the signer’s public key to decrypt the hash document. The program then
calculates new hash for the document. If new hash matches the decrypted hash. The program
confirms the document has not been altered.
Question 2.
Explanations of components;
The DNS is composed of three components namely; Name Space, Name Server,
Resolver.
The Name Space is the inverted tree-like hierarchy with a null node named at the top of
the tree (Mockapetris, P. et.al, 1988).
The full hierarchy would be:
Bestchoice.com
Au:8080
Customerservice
Enqueries.html
The Name Server
2 | P a g e
Alice PubKey
Encrypt
PriKey
Dijitally
signed
node
Au:8080 Enqueries.html
Bestchoice.com
customerse
rvice
This can be done digital-signature capable program such as Adobe reader. The program uses the
sender or rather the signer’s public key to decrypt the hash document. The program then
calculates new hash for the document. If new hash matches the decrypted hash. The program
confirms the document has not been altered.
Question 2.
Explanations of components;
The DNS is composed of three components namely; Name Space, Name Server,
Resolver.
The Name Space is the inverted tree-like hierarchy with a null node named at the top of
the tree (Mockapetris, P. et.al, 1988).
The full hierarchy would be:
Bestchoice.com
Au:8080
Customerservice
Enqueries.html
The Name Server
2 | P a g e
Alice PubKey
Encrypt
PriKey
Dijitally
signed
node
Au:8080 Enqueries.html
Bestchoice.com
customerse
rvice

The name server is responsible for keeping the file that contains domain information.
Name servers precisely describe domain’s current DNS provider. Usually all domains
have at least two DNS servers which are checked by lookup tools. Anything related to the
domain name is returned when a request is made, it is sent back in form of IP address.
RESOLVER.
The resolver converts web links to IP addresses hence acts as a link between the
computer and the Internet’s DNS infrastructure. Precisely it is a local server that stores a
central database of DNS name servers and even manages the DNS requests of all the
clients on a particular network. The resolver plays a role of “first port of call”.
a. Every web server connected to the internet or any host connected to the web server has a
unique IP address in textual form which translates to IP either version 4 or version 6.
During name resolution or lookup, the website, webserver or the program wishing to do
the translation, a component contacts the DNS server that in turn returns the translated IP.
The user types an address into the browser and the address in textual form is sent to the
DNS server which searches the IP address assigned to that particular name and the IP
address is then passed to the server which gives the page corresponding to that IP
address.
Question 3.
(a)
It is a database transaction in which more than one nodes in a network of hosts are involved.
In distributed transactions the nodes provide transactional resources and the transaction
manager is responsible for managing a global transaction that surrounds all the operations
against these particular resources. Distributed transactions must be synchronized in some
way since they take place at different hosts over a network and the ACID property has to be
upheld therefore needs to be serialized.
(b)
The two-phase commit also termed as 2PC is globally accepted standard protocol/rules for
distributed transactions. The accuracy of the distributed commit protocol is basically in the
Atomicity property. Transaction is started by the coordinator, participating nodes execute the
transaction on the behalf of the coordinator and commit/cancel also called abort is directed
by the coordinator. Under the protocol all nodes have to agree for a commitment of data to be
done.(Mohan et.al, 1986).
1.Voting phase
The coordinator sends a message to instruct prepare, alongside this transactions to all the
participating nodes and technically asks the nodes to vote for commit or against/abort.
3 | P a g e
Name servers precisely describe domain’s current DNS provider. Usually all domains
have at least two DNS servers which are checked by lookup tools. Anything related to the
domain name is returned when a request is made, it is sent back in form of IP address.
RESOLVER.
The resolver converts web links to IP addresses hence acts as a link between the
computer and the Internet’s DNS infrastructure. Precisely it is a local server that stores a
central database of DNS name servers and even manages the DNS requests of all the
clients on a particular network. The resolver plays a role of “first port of call”.
a. Every web server connected to the internet or any host connected to the web server has a
unique IP address in textual form which translates to IP either version 4 or version 6.
During name resolution or lookup, the website, webserver or the program wishing to do
the translation, a component contacts the DNS server that in turn returns the translated IP.
The user types an address into the browser and the address in textual form is sent to the
DNS server which searches the IP address assigned to that particular name and the IP
address is then passed to the server which gives the page corresponding to that IP
address.
Question 3.
(a)
It is a database transaction in which more than one nodes in a network of hosts are involved.
In distributed transactions the nodes provide transactional resources and the transaction
manager is responsible for managing a global transaction that surrounds all the operations
against these particular resources. Distributed transactions must be synchronized in some
way since they take place at different hosts over a network and the ACID property has to be
upheld therefore needs to be serialized.
(b)
The two-phase commit also termed as 2PC is globally accepted standard protocol/rules for
distributed transactions. The accuracy of the distributed commit protocol is basically in the
Atomicity property. Transaction is started by the coordinator, participating nodes execute the
transaction on the behalf of the coordinator and commit/cancel also called abort is directed
by the coordinator. Under the protocol all nodes have to agree for a commitment of data to be
done.(Mohan et.al, 1986).
1.Voting phase
The coordinator sends a message to instruct prepare, alongside this transactions to all the
participating nodes and technically asks the nodes to vote for commit or against/abort.
3 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
If the participants commits, the transaction Vote-commit is submitted to the coordinator and
if otherwise vote for abort is sent.
2.Commit phase
The decision for commit or abort is taken up by the coordinator. If vote commit is received
from all the nodes a global commit is initiated and is sent to every node and if at least one
Vote-abort is received the coordinator sends a global abort to all the committed vote nodes.
Coordinator requests for acknowledgement from the nodes.If the nodes receive global-
commit , it commits the transaction in the distributed database .
Question 4.
Fault-tolerance.
Replication can be defined as : Providing numerous identical instances of a system or even a
subsystem, channeling tasks or requests to all of them in parallel, and choosing the accurate
outcome on the basis of a quorum
Fault tolerance is an aspect that enables a system/application to continue operating properly
despite the failure (one or more faults within) some of its modules.
Application-based Resilience.
Deals with faults using the information on the application.
Intercrosses Communication:
Majorly used by distributed systems in information sharing thus there is a dire need of
synchronizing all the processes involved. The synchrony should be controlled in a way that the
process may not make judgements of the speed of other processes. This communication is made
possible by message passing (scheme Lee et.al, 1990).
Question 5.
(a) .
Central server algorithms are usually used to solve the problem of synchronization.
Steps:
Use a coordinator which will enforce the aspect of mutual exclusion.
Initiate operations of course more than two operations.
Process one requests permission from the coordinator to enter the critical region and the
permission is granted to it.
Process two also requests for the permission but it is denied or rather the coordinator does not
reply. (Newell, et.al, Nortel Networks Ltd, 1999).
4 | P a g e
if otherwise vote for abort is sent.
2.Commit phase
The decision for commit or abort is taken up by the coordinator. If vote commit is received
from all the nodes a global commit is initiated and is sent to every node and if at least one
Vote-abort is received the coordinator sends a global abort to all the committed vote nodes.
Coordinator requests for acknowledgement from the nodes.If the nodes receive global-
commit , it commits the transaction in the distributed database .
Question 4.
Fault-tolerance.
Replication can be defined as : Providing numerous identical instances of a system or even a
subsystem, channeling tasks or requests to all of them in parallel, and choosing the accurate
outcome on the basis of a quorum
Fault tolerance is an aspect that enables a system/application to continue operating properly
despite the failure (one or more faults within) some of its modules.
Application-based Resilience.
Deals with faults using the information on the application.
Intercrosses Communication:
Majorly used by distributed systems in information sharing thus there is a dire need of
synchronizing all the processes involved. The synchrony should be controlled in a way that the
process may not make judgements of the speed of other processes. This communication is made
possible by message passing (scheme Lee et.al, 1990).
Question 5.
(a) .
Central server algorithms are usually used to solve the problem of synchronization.
Steps:
Use a coordinator which will enforce the aspect of mutual exclusion.
Initiate operations of course more than two operations.
Process one requests permission from the coordinator to enter the critical region and the
permission is granted to it.
Process two also requests for the permission but it is denied or rather the coordinator does not
reply. (Newell, et.al, Nortel Networks Ltd, 1999).
4 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

When the first process is done using the critical region it exists notifying the coordinator
which in turn replies the second the process and the system continues subsequently.
Coordinator
Loop
Receive(message);
Case message of
REQUEST: if no process in critical region(CR)
Reply GRANTED
Else queue REQUEST
Reply DENIED
RELEASE: if queue not empty
Remove first process from the queue
Reply GRANTED
End case
Client
Send(REQUEST)
Receive(message);
If message!=GRANTED receive (message);
Enter critical region;
Send (RELEASE)
(b) Discuss the safety, liveness and ordering features of the algorithm you have designed;
Liveness refers to a set of properties of concurrent systems that requires the systems to make
progress in spite of its concurrently running components may take turns to access and use the
critical region.
Liveness property cannot be tempered with in a finite execution of a distributed system due
to the "accept" event might only theoretically occur at some time after execution ends.
Eventual consistency is a typical example of a liveness property. All the aspects can be
5 | P a g e
which in turn replies the second the process and the system continues subsequently.
Coordinator
Loop
Receive(message);
Case message of
REQUEST: if no process in critical region(CR)
Reply GRANTED
Else queue REQUEST
Reply DENIED
RELEASE: if queue not empty
Remove first process from the queue
Reply GRANTED
End case
Client
Send(REQUEST)
Receive(message);
If message!=GRANTED receive (message);
Enter critical region;
Send (RELEASE)
(b) Discuss the safety, liveness and ordering features of the algorithm you have designed;
Liveness refers to a set of properties of concurrent systems that requires the systems to make
progress in spite of its concurrently running components may take turns to access and use the
critical region.
Liveness property cannot be tempered with in a finite execution of a distributed system due
to the "accept" event might only theoretically occur at some time after execution ends.
Eventual consistency is a typical example of a liveness property. All the aspects can be
5 | P a g e

expressed as the intersection of safety and liveness properties. Whereas safety properties
agrees to a finite witness, liveness properties may not be easy to establish as no finite witness
can be used to ascertain their existence
Liveness and safety
Liveness assumes different forms such as freedom from deadlock which is a safety property
which works by assuming the states of a system can be split into other smaller states while
there is deadlock.
Freedom from starvation also known as finite bypass is a stronger liveness guarantee than
deadlock-freedom. It states that all processes competing for access to the critical section
eventually makes progress. Any starvation-free system is also called deadlock-free.
Ordering guaranteed in mutual exclusion algorithms enabling the serializability of concurrent
operations.
Question 6.
(Tsai, et.al, 2008).
Transaction T – reads(a2)
Reads(a1)
Write(a2, a2+85)
Write(a1, a1-32)
Transaction U –reads(a2)
Reads(a3)
Write(a2, a2-34)
Write(a3, a3-77)
Original values a1 =124
A2 =156
A3 =133
Read(a) returns write(a,v)
Assigns v to a
(a) If the interleaving operations from T and U are serially equivalent to ‘T before U,’ what
are the values of a1, a2 and a3 after the two transactions have completed?
Transaction T values - a2= 156+85=241
6 | P a g e
agrees to a finite witness, liveness properties may not be easy to establish as no finite witness
can be used to ascertain their existence
Liveness and safety
Liveness assumes different forms such as freedom from deadlock which is a safety property
which works by assuming the states of a system can be split into other smaller states while
there is deadlock.
Freedom from starvation also known as finite bypass is a stronger liveness guarantee than
deadlock-freedom. It states that all processes competing for access to the critical section
eventually makes progress. Any starvation-free system is also called deadlock-free.
Ordering guaranteed in mutual exclusion algorithms enabling the serializability of concurrent
operations.
Question 6.
(Tsai, et.al, 2008).
Transaction T – reads(a2)
Reads(a1)
Write(a2, a2+85)
Write(a1, a1-32)
Transaction U –reads(a2)
Reads(a3)
Write(a2, a2-34)
Write(a3, a3-77)
Original values a1 =124
A2 =156
A3 =133
Read(a) returns write(a,v)
Assigns v to a
(a) If the interleaving operations from T and U are serially equivalent to ‘T before U,’ what
are the values of a1, a2 and a3 after the two transactions have completed?
Transaction T values - a2= 156+85=241
6 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

A1=124-32=92
Transaction U values - a2=241-34=207
A3=133-77=56
(b) For serial equivalence of ‘T before U,’ give a possible order of interleaving operations
from T and U
The order for operations would be read a1 and a2, write Write(a2, a2+85) Write(a1, a1-
32) then use the values for Transaction U read values(v) assign to a then use a2 to
execute the transaction.
(c) If the interleaving operations from T and U are serially equivalent to ‘U before T,’ what
are the values of a1, a2 and a3 after the two transactions have completed?
A3 = 56
A2 = 207+85=292
A1 = 92
(d)For serial equivalence of ‘U before T,’ give a possible order of interleaving operations
from T and U. Read the values in transaction U, assign the values(v) to a, use v to
perform transaction that follows which is a2.
(e)Give an example of interleaving operations from T and U, which are not serially
equivalent and cause the lost update problem. Write (a,v) before reading a.
Question 7.
Public class patients{
Private String patientName;
Private String patientNumber;
Private String patientGender;
Private String DOB;
Private String condition;
Patient(String patientName, String patientNumber, String patientGender, String DOB,
String condition) {
this.patientName = patientName;
this.patientNumber = patientNumber;
this.patientGender = patientGender;
this.DOB = DOB;
this.condition = condition;
}
Public String get patientName(){
7 | P a g e
Transaction U values - a2=241-34=207
A3=133-77=56
(b) For serial equivalence of ‘T before U,’ give a possible order of interleaving operations
from T and U
The order for operations would be read a1 and a2, write Write(a2, a2+85) Write(a1, a1-
32) then use the values for Transaction U read values(v) assign to a then use a2 to
execute the transaction.
(c) If the interleaving operations from T and U are serially equivalent to ‘U before T,’ what
are the values of a1, a2 and a3 after the two transactions have completed?
A3 = 56
A2 = 207+85=292
A1 = 92
(d)For serial equivalence of ‘U before T,’ give a possible order of interleaving operations
from T and U. Read the values in transaction U, assign the values(v) to a, use v to
perform transaction that follows which is a2.
(e)Give an example of interleaving operations from T and U, which are not serially
equivalent and cause the lost update problem. Write (a,v) before reading a.
Question 7.
Public class patients{
Private String patientName;
Private String patientNumber;
Private String patientGender;
Private String DOB;
Private String condition;
Patient(String patientName, String patientNumber, String patientGender, String DOB,
String condition) {
this.patientName = patientName;
this.patientNumber = patientNumber;
this.patientGender = patientGender;
this.DOB = DOB;
this.condition = condition;
}
Public String get patientName(){
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Return patientName;
}
Public String get patientNumber(){
Return patientNumber;
}
Public String get patientGender(){
Return patientGender;
}
Public String get patient
}
(Gosling, et.al, 2000).
Question 8.
package connection;
import java.net.*;
import java.io.*;
public class Connection {
public static void main(String[] args) {
String hostname = "time.nist.gov";
int port = 13;
try (Socket socket = new Socket(hostname, port)) {
InputStream input = socket.getInputStream();
InputStreamReader reader = new InputStreamReader(input);
int character;
StringBuilder data = new StringBuilder();
while ((character = reader.read()) != -1) {
data.append((char) character);
}
System.out.println(data);
} catch (UnknownHostException ex) {
System.out.println("Server not found: " + ex.getMessage());
8 | P a g e
}
Public String get patientNumber(){
Return patientNumber;
}
Public String get patientGender(){
Return patientGender;
}
Public String get patient
}
(Gosling, et.al, 2000).
Question 8.
package connection;
import java.net.*;
import java.io.*;
public class Connection {
public static void main(String[] args) {
String hostname = "time.nist.gov";
int port = 13;
try (Socket socket = new Socket(hostname, port)) {
InputStream input = socket.getInputStream();
InputStreamReader reader = new InputStreamReader(input);
int character;
StringBuilder data = new StringBuilder();
while ((character = reader.read()) != -1) {
data.append((char) character);
}
System.out.println(data);
} catch (UnknownHostException ex) {
System.out.println("Server not found: " + ex.getMessage());
8 | P a g e

} catch (IOException ex) {
System.out.println("I/O error: " + ex.getMessage());
}
}
}
Question 8.
The application requires two class the client class and the server class displayed here:
Import java.io.IOException;
Import java.io.PrintStream;
Import java.net.Socket;
Import java.util.Scanner;
Scanner sc1 = n
Public class CLI{
Public static void main(String []args){
Scanner c = new Scanner(System.in);
Socket sk = new Socket(“”,””);
Scanner c = new Scanner(sk.getInputStream());
9 | P a g e
System.out.println("I/O error: " + ex.getMessage());
}
}
}
Question 8.
The application requires two class the client class and the server class displayed here:
Import java.io.IOException;
Import java.io.PrintStream;
Import java.net.Socket;
Import java.util.Scanner;
Scanner sc1 = n
Public class CLI{
Public static void main(String []args){
Scanner c = new Scanner(System.in);
Socket sk = new Socket(“”,””);
Scanner c = new Scanner(sk.getInputStream());
9 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

System.out.println(“Enter details”);
PrintStream p = new PrintStream(sk.getOutputStream());
p.println(“details”);
String temp = c.nextLine();
System.out.println(temp);
}
}
Server class.
Import java.io.PrintStream;
Import java.net.ServerSocket;
Import java.netSocket;
Import java.util.Scanner;
Import java.util.logging.Level;
Import java.util.logging.Logger;
Public class server{
Public static void main(String[] args){
try{
serverSocket s2= new serverSocket (8080);
socket ss=s2.accept();
Scanner me = new Scanner(ss.getInputStream());
String details = me.nextLine();
printStream pr = new printstream(ss.getInputStream());
}catch(IOException ex){
Logger.getLogger(server.name.getName()).log(level.SEVER,null,ex)
10 | P a g e
PrintStream p = new PrintStream(sk.getOutputStream());
p.println(“details”);
String temp = c.nextLine();
System.out.println(temp);
}
}
Server class.
Import java.io.PrintStream;
Import java.net.ServerSocket;
Import java.netSocket;
Import java.util.Scanner;
Import java.util.logging.Level;
Import java.util.logging.Logger;
Public class server{
Public static void main(String[] args){
try{
serverSocket s2= new serverSocket (8080);
socket ss=s2.accept();
Scanner me = new Scanner(ss.getInputStream());
String details = me.nextLine();
printStream pr = new printstream(ss.getInputStream());
}catch(IOException ex){
Logger.getLogger(server.name.getName()).log(level.SEVER,null,ex)
10 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

}
}
}
Other dependant classes are the main classes.
Question 9.
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.net.InetAddress;
import java.net.ServerSocket;
import java.net.Socket;
import java.util.logging.Level;
import java.util.logging.Logger;
public class serverTCP {
private ServerSocket server;
public serverTCP (String ipAddress)throws Exception {
if(ipAddress != null && !ipAddress.isEmpty()){
this.server = new ServerSocket(0,1,InetAddress.getByName(ipAddress));
}else
11 | P a g e
}
}
Other dependant classes are the main classes.
Question 9.
import java.io.BufferedReader;
import java.io.InputStreamReader;
import java.net.InetAddress;
import java.net.ServerSocket;
import java.net.Socket;
import java.util.logging.Level;
import java.util.logging.Logger;
public class serverTCP {
private ServerSocket server;
public serverTCP (String ipAddress)throws Exception {
if(ipAddress != null && !ipAddress.isEmpty()){
this.server = new ServerSocket(0,1,InetAddress.getByName(ipAddress));
}else
11 | P a g e

this.server = new ServerSocket(0, 1,InetAddress.getLocalHost());
// TODO code application logic here
}
private void listen() throws Exception{
String data = null;
Socket client = this.server.accept();
String ClientAddress = client.getInetAddress().getHostAddress();
String clientAddress = null;
System.out.println("\r\nNew access from" +clientAddress);
BufferedReader in = new BufferedReader(new
InputStreamReader(client.getInputStream()));
while((data = in.readLine()) !=null){
System.out.println("\r\ntext from"+clientAddress + ":" + data);
}
}
public InetAddress getSocketAddress(){
return this.server.getInetAddress();
}
public int getPort(){
return this.server.getLocalPort();
}
public static void main(String[] args){
try {
serverTCP app = new serverTCP(args[0]);
System.out.println("\r\nRunning Server:" + "Host=" +
app.getSocketAddress().getHostAddress()+"Port=" + app.getPort());
12 | P a g e
// TODO code application logic here
}
private void listen() throws Exception{
String data = null;
Socket client = this.server.accept();
String ClientAddress = client.getInetAddress().getHostAddress();
String clientAddress = null;
System.out.println("\r\nNew access from" +clientAddress);
BufferedReader in = new BufferedReader(new
InputStreamReader(client.getInputStream()));
while((data = in.readLine()) !=null){
System.out.println("\r\ntext from"+clientAddress + ":" + data);
}
}
public InetAddress getSocketAddress(){
return this.server.getInetAddress();
}
public int getPort(){
return this.server.getLocalPort();
}
public static void main(String[] args){
try {
serverTCP app = new serverTCP(args[0]);
System.out.println("\r\nRunning Server:" + "Host=" +
app.getSocketAddress().getHostAddress()+"Port=" + app.getPort());
12 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




