Desklib - Online Library for Study Material with Solved Assignments, Essays, Dissertations
VerifiedAdded on 2023/06/11
|20
|3651
|133
AI Summary
Desklib is an online library for study material with solved assignments, essays, dissertations, and more. The article discusses network security and its implementation in a network. It covers topics like network topology analysis, placement of security devices, VLAN implementation, firewall policies, IDS/IPS policies, and security policies for Lucent Pharma.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: NETWORK SECURITY
NETWORK SECURITY
Name of the Student
Name of the University
Author Note:
NETWORK SECURITY
Name of the Student
Name of the University
Author Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1NETWORK SECUIRITY
Table of Contents
Part 1 – Network Design..................................................................................................................3
1. Analysis of the current Network Topology.............................................................................3
2. Placement of the security device/ controls for the improvement of the network performance
.....................................................................................................................................................4
3. Justification for the placement of the device...........................................................................6
4. Segregation of the network into multiple domain...................................................................7
5. Set of firewall policy and firewall rules:................................................................................7
6. Set of IDS /IPS policies implemented by the network administrator......................................8
7. Ten Security policy essential for Lucent Pharma....................................................................9
8. Proposed Secure Network Design.........................................................................................11
Part 2 (Hands-On)..........................................................................................................................12
1. Using Nmap tool to scan server scanme.nmap.org................................................................12
2. Recording of the above traffic...............................................................................................12
3. Scanning with different options.............................................................................................12
3.1. TCP SYN Scan...............................................................................................................12
3.2. OS detection and version detection................................................................................13
3.3. Quick Scan......................................................................................................................13
3.4. Single Port scan..............................................................................................................14
3.5. Range of port scan..........................................................................................................14
Table of Contents
Part 1 – Network Design..................................................................................................................3
1. Analysis of the current Network Topology.............................................................................3
2. Placement of the security device/ controls for the improvement of the network performance
.....................................................................................................................................................4
3. Justification for the placement of the device...........................................................................6
4. Segregation of the network into multiple domain...................................................................7
5. Set of firewall policy and firewall rules:................................................................................7
6. Set of IDS /IPS policies implemented by the network administrator......................................8
7. Ten Security policy essential for Lucent Pharma....................................................................9
8. Proposed Secure Network Design.........................................................................................11
Part 2 (Hands-On)..........................................................................................................................12
1. Using Nmap tool to scan server scanme.nmap.org................................................................12
2. Recording of the above traffic...............................................................................................12
3. Scanning with different options.............................................................................................12
3.1. TCP SYN Scan...............................................................................................................12
3.2. OS detection and version detection................................................................................13
3.3. Quick Scan......................................................................................................................13
3.4. Single Port scan..............................................................................................................14
3.5. Range of port scan..........................................................................................................14

2NETWORK SECUIRITY
3.6. All port scan....................................................................................................................15
4. Report in Tabular Form.........................................................................................................15
5. Wireshark Analysis................................................................................................................16
5.1. Filtering the packet using “HTTP’ traffic only...............................................................16
5.2. Filtering the packet to exclude ‘HTTP’ traffic...............................................................17
5.3. Difference between ‘Capture Filter’ and ‘Display Filter’..............................................17
References......................................................................................................................................18
3.6. All port scan....................................................................................................................15
4. Report in Tabular Form.........................................................................................................15
5. Wireshark Analysis................................................................................................................16
5.1. Filtering the packet using “HTTP’ traffic only...............................................................16
5.2. Filtering the packet to exclude ‘HTTP’ traffic...............................................................17
5.3. Difference between ‘Capture Filter’ and ‘Display Filter’..............................................17
References......................................................................................................................................18

3NETWORK SECUIRITY
Part 1 – Network Design
1. Analysis of the current Network Topology
Some of vulnerabilities which has been seen in the concept of network are given below:
Missing of patches: It is mainly taken by various kinds of attackers to easily indulge in
various kinds of illegal activity within the idea of network which is missing a proper kind of
match for the server. It also allows various kinds of authentication of command prompt or any
other kind of backdoor for the working environment of the web. The ultimate goal of this project
is to take into the consideration of various kinds of patches in a careful way.
Weak or default password: The main kind of vulnerability or issue that is taken into
account is idea of weak password or any kind of default password. The main objective is to take
into account of any kind of intruders which can directly change different kind of activity. The
activity can easily arise from accessing of required data of the user and of the system. Password
should be kept secure and care should be taken of this fact. It should not go in the hand of some
unauthorized person. It can directly affect the securing of network channel and also focus in
building a proper kind of network that is needed to be kept secured.
Misconfiguration of firewall: It can be rule base that is mainly used for
misconfiguration of various kinds of firewall and it is considered to be one of the important kind
of vulnerability in the domain of networking. It can be easily stated as a kind of assumption that
is mainly used in the concept in the domain of concept and firewall. The idea of digging the
proper kind of firewall is considered to be same for serious kind of effect which is mainly
working in the different kind of available scenario. It mainly allows various kinds of
unauthorized users to have an idea regarding the various concept of networking.
Part 1 – Network Design
1. Analysis of the current Network Topology
Some of vulnerabilities which has been seen in the concept of network are given below:
Missing of patches: It is mainly taken by various kinds of attackers to easily indulge in
various kinds of illegal activity within the idea of network which is missing a proper kind of
match for the server. It also allows various kinds of authentication of command prompt or any
other kind of backdoor for the working environment of the web. The ultimate goal of this project
is to take into the consideration of various kinds of patches in a careful way.
Weak or default password: The main kind of vulnerability or issue that is taken into
account is idea of weak password or any kind of default password. The main objective is to take
into account of any kind of intruders which can directly change different kind of activity. The
activity can easily arise from accessing of required data of the user and of the system. Password
should be kept secure and care should be taken of this fact. It should not go in the hand of some
unauthorized person. It can directly affect the securing of network channel and also focus in
building a proper kind of network that is needed to be kept secured.
Misconfiguration of firewall: It can be rule base that is mainly used for
misconfiguration of various kinds of firewall and it is considered to be one of the important kind
of vulnerability in the domain of networking. It can be easily stated as a kind of assumption that
is mainly used in the concept in the domain of concept and firewall. The idea of digging the
proper kind of firewall is considered to be same for serious kind of effect which is mainly
working in the different kind of available scenario. It mainly allows various kinds of
unauthorized users to have an idea regarding the various concept of networking.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4NETWORK SECUIRITY
Unauthorized access: It can be easily defined as well-known sector which can be
defined as an important parameter which can easily bring a large amount of harm in the overall
working of the given system. It mainly takes when a user attempts to get an access to certain
areas or zones of the system. Some of the system administrator comes up with alert so that user
can easily have an idea regarding any kind of authorized access or any kind of attempt. Various
kinds of secure system come up proper kind of lock and also have various kinds of failed login
attempts. Security of the network is considered to be an important kind of aspect which must be
taken into consideration.
2. Placement of the security device/ controls for the improvement of the network
performance
Firewall: A firewall can be easily defined as a network security which has been designed
in such a way it can easily use for prevention of any kind of access to a private network. Firewall
can be easily used in both hardware and software or even combination of both the available
technology. Network firewalls are generally used for blocking of any kind of unauthorized users
from accessing any kind of private network which are connected to the network which are
connected to internet especially the intranet. All the message which enter or leave the internet to
easily pass through the firewall. It mainly examines the each and every kind of block which does
not meet the specific kind of security criteria. Firewalls can be used for either hardware and
software but along with this should contain ideal kind of configuration for both. Apart from this
there should be any kind of limitation for the access to any kind of network. A firewall is
considered to be useful as it allows remote kind of access to any kind of network which has been
obtained for any kind of authentication of secure authentication and certification. Hardware
firewall can be easily used for any kind of purchase for various kinds of standalone programs but
Unauthorized access: It can be easily defined as well-known sector which can be
defined as an important parameter which can easily bring a large amount of harm in the overall
working of the given system. It mainly takes when a user attempts to get an access to certain
areas or zones of the system. Some of the system administrator comes up with alert so that user
can easily have an idea regarding any kind of authorized access or any kind of attempt. Various
kinds of secure system come up proper kind of lock and also have various kinds of failed login
attempts. Security of the network is considered to be an important kind of aspect which must be
taken into consideration.
2. Placement of the security device/ controls for the improvement of the network
performance
Firewall: A firewall can be easily defined as a network security which has been designed
in such a way it can easily use for prevention of any kind of access to a private network. Firewall
can be easily used in both hardware and software or even combination of both the available
technology. Network firewalls are generally used for blocking of any kind of unauthorized users
from accessing any kind of private network which are connected to the network which are
connected to internet especially the intranet. All the message which enter or leave the internet to
easily pass through the firewall. It mainly examines the each and every kind of block which does
not meet the specific kind of security criteria. Firewalls can be used for either hardware and
software but along with this should contain ideal kind of configuration for both. Apart from this
there should be any kind of limitation for the access to any kind of network. A firewall is
considered to be useful as it allows remote kind of access to any kind of network which has been
obtained for any kind of authentication of secure authentication and certification. Hardware
firewall can be easily used for any kind of purchase for various kinds of standalone programs but

5NETWORK SECUIRITY
are mainly found in various kinds of broadband routers. Major of the network firewalls have
minimum number of four ports which are mainly connected to a network. But for a large number
network it comes up with business networking for various kind of firewall solution.
IDS/IPS: Intrusion detection can be defined as a method of processing for proper
monitoring of various kinds of events that mainly occur in a network. It mainly focuses on
analysing various kinds of sign for possible number of incidents. It aims in violation of imminent
kinds of threats which are present in various kinds of security policies. Intrusion prevention can
be defined as a process for performance of various kinds of intrusion detection and after that
detection of this kind of incident. Various kinds of security measures are generally available as
an intrusion detection system and intrusion prevention system (IPS) has become an important
part of network defect and stopping of any kind of potential incidents. A typical kind of business
network comes up business network which comes up with various kinds of access point for
maintenance of network on both public and private domains. The challenge is all about
maintaining of security in this network.
Honeypot: A honeypot can be easily defined as decoy system which is mainly used for trapping
of various kinds of hackers or trace of unconventional or new kind of hacking methods.
Honeypots has been designed in such a way for engaging and deceiving various kinds of hackers.
It also aims in identifying various kinds of malicious activity which are mainly performed on the
internet. There are large number of advantages of making use of honey pots. The first advantage
is all about the ease with which it is mainly employed. Second advantage of honeypot is that it
can easily seek small amount or information of the hacker. The obtained information is
considered to be much useful for high valuable high kind of information for studying and
uncovering of motivation of various hackers.
are mainly found in various kinds of broadband routers. Major of the network firewalls have
minimum number of four ports which are mainly connected to a network. But for a large number
network it comes up with business networking for various kind of firewall solution.
IDS/IPS: Intrusion detection can be defined as a method of processing for proper
monitoring of various kinds of events that mainly occur in a network. It mainly focuses on
analysing various kinds of sign for possible number of incidents. It aims in violation of imminent
kinds of threats which are present in various kinds of security policies. Intrusion prevention can
be defined as a process for performance of various kinds of intrusion detection and after that
detection of this kind of incident. Various kinds of security measures are generally available as
an intrusion detection system and intrusion prevention system (IPS) has become an important
part of network defect and stopping of any kind of potential incidents. A typical kind of business
network comes up business network which comes up with various kinds of access point for
maintenance of network on both public and private domains. The challenge is all about
maintaining of security in this network.
Honeypot: A honeypot can be easily defined as decoy system which is mainly used for trapping
of various kinds of hackers or trace of unconventional or new kind of hacking methods.
Honeypots has been designed in such a way for engaging and deceiving various kinds of hackers.
It also aims in identifying various kinds of malicious activity which are mainly performed on the
internet. There are large number of advantages of making use of honey pots. The first advantage
is all about the ease with which it is mainly employed. Second advantage of honeypot is that it
can easily seek small amount or information of the hacker. The obtained information is
considered to be much useful for high valuable high kind of information for studying and
uncovering of motivation of various hackers.

6NETWORK SECUIRITY
Router and switches: Router and switches are considered to be both kind of computer based
networking devices which mainly allows one more kind of computers to be easily connected to
network device or any other kind of available network. The function of router, switches and hubs
are all considered to be different and in many cases it is observed that it is integrated into single
kind of device. Router are mainly used for mapping one to one kind of physical interface for
large number of routers.
3. Justification for the placement of the device
Firewall: A firewall is mainly used or place at the network which mainly arises to the
factor for proper kind of protection of the given network from any kind of intruders. The main
notion which is mainly related to the concept or idea is proper kind of securing of system for the
given network. It is mainly done for improving the improving the quality of the given of the
network which are mainly involved in the given processes. Firewall can be easily used for
prevention of attack from any kind of intruders. It will ultimately improve the overall the
efficiency of the given network. It can be easily defined as a main kind of functionality of the
firewall of the given network which has been used for securing the overall process that is mainly
available. Various kinds of components are mainly involved which is considered as an important
kind of aspect.
IDS/IPS: Deployment of IDS/ IPS in the given network is mainly related for securing of
the given network by the help of various kinds of forms like various kinds of available attack
which can be easily applied to various concept or idea of networking.
Honeypot: The main kind of implementation of honeypot in the given sector is all about
providing a help that is mainly used for establishment of communication of network that can be
easily used for providing help to large number of service in the network.
Router and switches: Router and switches are considered to be both kind of computer based
networking devices which mainly allows one more kind of computers to be easily connected to
network device or any other kind of available network. The function of router, switches and hubs
are all considered to be different and in many cases it is observed that it is integrated into single
kind of device. Router are mainly used for mapping one to one kind of physical interface for
large number of routers.
3. Justification for the placement of the device
Firewall: A firewall is mainly used or place at the network which mainly arises to the
factor for proper kind of protection of the given network from any kind of intruders. The main
notion which is mainly related to the concept or idea is proper kind of securing of system for the
given network. It is mainly done for improving the improving the quality of the given of the
network which are mainly involved in the given processes. Firewall can be easily used for
prevention of attack from any kind of intruders. It will ultimately improve the overall the
efficiency of the given network. It can be easily defined as a main kind of functionality of the
firewall of the given network which has been used for securing the overall process that is mainly
available. Various kinds of components are mainly involved which is considered as an important
kind of aspect.
IDS/IPS: Deployment of IDS/ IPS in the given network is mainly related for securing of
the given network by the help of various kinds of forms like various kinds of available attack
which can be easily applied to various concept or idea of networking.
Honeypot: The main kind of implementation of honeypot in the given sector is all about
providing a help that is mainly used for establishment of communication of network that can be
easily used for providing help to large number of service in the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK SECUIRITY
Routers/ Switches: A given router and switch is mainly used for redirecting of various
kinds of networks. In major of the cases it is easily seen that placement of router or switch is
much important in the given network and this mainly arises due to the fact of decision that
should be taken into consideration for the given device. The given function of router can be
considered to be much important as it mainly arises by taking into consideration of this given
device as it can easily increase the overall function of the given network.
4. Segregation of the network into multiple domain
VLAN mainly stands for virtual area network (VLAN) can be defined as a logical group
of workstation, network devices and server which tends to appear on same kind of LAN
irrespective of the distribution in geographical way. A VLAN mainly allows various kinds of
network computers and user to easily establish various kinds of communication in a given
environment. Now if VLAN exist as single kind of LAN and are merely used for establishing
communication in a single kind of environment and multicast domain. VLANs are mainly
implemented for achieving scalability, security and ease of management of network and easily
adapt to for achieving scalability, security and ease with each network management can easily
adapt to large number of changes in the requirements of network and reallocation of various
kinds of workstation and various kinds nodes for server nodes. High end switches mainly allow
various kinds of functionality along with implementation of VLANs. The main aim of
implementation of VLAN is to easily improve the performance of given network or can easily
apply for large number of security features.
5. Set of firewall policy and firewall rules:
The main purpose of this policy is to easily establish a proper kind of approach which is
used for approaching the given information security. It is mainly used for establishment of
Routers/ Switches: A given router and switch is mainly used for redirecting of various
kinds of networks. In major of the cases it is easily seen that placement of router or switch is
much important in the given network and this mainly arises due to the fact of decision that
should be taken into consideration for the given device. The given function of router can be
considered to be much important as it mainly arises by taking into consideration of this given
device as it can easily increase the overall function of the given network.
4. Segregation of the network into multiple domain
VLAN mainly stands for virtual area network (VLAN) can be defined as a logical group
of workstation, network devices and server which tends to appear on same kind of LAN
irrespective of the distribution in geographical way. A VLAN mainly allows various kinds of
network computers and user to easily establish various kinds of communication in a given
environment. Now if VLAN exist as single kind of LAN and are merely used for establishing
communication in a single kind of environment and multicast domain. VLANs are mainly
implemented for achieving scalability, security and ease of management of network and easily
adapt to for achieving scalability, security and ease with each network management can easily
adapt to large number of changes in the requirements of network and reallocation of various
kinds of workstation and various kinds nodes for server nodes. High end switches mainly allow
various kinds of functionality along with implementation of VLANs. The main aim of
implementation of VLAN is to easily improve the performance of given network or can easily
apply for large number of security features.
5. Set of firewall policy and firewall rules:
The main purpose of this policy is to easily establish a proper kind of approach which is
used for approaching the given information security. It is mainly used for establishment of

8NETWORK SECUIRITY
procedure that is mainly used for identification and prevention and compromising of information
in the given organization.
Individuals covered: This particular policy is mainly used for large number of people
for accessing and making use of all the computing, network and telephony and various kinds of
resources any kind of given organization.
System and resource covered: This particular policy covers all kind of computing,
network and telephony and various kinds of information that mainly proceed by the organization.
This policy also covers any kinds of computing device to establish connectivity to the
information of resources which is available. It is mainly inclusive of various kinds of computing
and network system which is used for establishment of connection is the given organization.
Information classification and its protection: For ensuring the given information of the
various kinds of members of an organization is a proper way. It is expected that all the
information is mainly established by the data classification policy.
Users training and awareness: Effective kind of information security mainly needs a
proper kind of participation of all the given members of the given organization. It is mainly
considered to be informed kind of responsibility which is mainly obtained or gathered as per the
need.
6. Set of IDS /IPS policies implemented by the network administrator
Packets which mainly enter into the network should be free from any kind of virus that is
mainly included in the network.
The point should be taken into consideration that no kind of malware is detected in the
given system.
procedure that is mainly used for identification and prevention and compromising of information
in the given organization.
Individuals covered: This particular policy is mainly used for large number of people
for accessing and making use of all the computing, network and telephony and various kinds of
resources any kind of given organization.
System and resource covered: This particular policy covers all kind of computing,
network and telephony and various kinds of information that mainly proceed by the organization.
This policy also covers any kinds of computing device to establish connectivity to the
information of resources which is available. It is mainly inclusive of various kinds of computing
and network system which is used for establishment of connection is the given organization.
Information classification and its protection: For ensuring the given information of the
various kinds of members of an organization is a proper way. It is expected that all the
information is mainly established by the data classification policy.
Users training and awareness: Effective kind of information security mainly needs a
proper kind of participation of all the given members of the given organization. It is mainly
considered to be informed kind of responsibility which is mainly obtained or gathered as per the
need.
6. Set of IDS /IPS policies implemented by the network administrator
Packets which mainly enter into the network should be free from any kind of virus that is
mainly included in the network.
The point should be taken into consideration that no kind of malware is detected in the
given system.

9NETWORK SECUIRITY
Passing of the given packet should be taken care so any kinds of packets are not missed
with respect to transferring from one point to another.
An acknowledgement of the given network is taken into taken consideration one cannot
receive things from one end to another end.
One should be taken into consideration there is no kind of gap or framework of time
available for various packets that is mainly transferred in the given process.
In most of cases it is seen that one cannot easily relate to packet transfer for more than a
time period of millisecond.
7. Ten Security policy essential for Lucent Pharma
System Admin: System admin comes up with overall kind of power of the network. He
has function. He mainly takes care of the overall function of the network and its functionality
and mainly focused to providing much amount of network. He should be capable for dealing
with any kind of problem of the system. In any kind of risk factor, an individual should be able
to properly deal with various functionality of the given system and also checks the various kinds
of given parameters.
Auditing: The sector factor that should be taken into account is the audit which plays a
vital kind of the role in the domain of networking. It mainly involves various kinds of factors
which mainly involves the various kinds of sectors of the given functionality. The ultimate
policy is about the fact which is considered to be much applicable in the provided concepts in the
various kinds of available devices. It should proper perform as per requirement of the given
system. The ultimate idea of audit is that it should be done in the given period of time that is
mainly responsible for the main kind of charge that is mainly available. If any kind of error is
found in the given network then it can be directly secured and the given system should be
Passing of the given packet should be taken care so any kinds of packets are not missed
with respect to transferring from one point to another.
An acknowledgement of the given network is taken into taken consideration one cannot
receive things from one end to another end.
One should be taken into consideration there is no kind of gap or framework of time
available for various packets that is mainly transferred in the given process.
In most of cases it is seen that one cannot easily relate to packet transfer for more than a
time period of millisecond.
7. Ten Security policy essential for Lucent Pharma
System Admin: System admin comes up with overall kind of power of the network. He
has function. He mainly takes care of the overall function of the network and its functionality
and mainly focused to providing much amount of network. He should be capable for dealing
with any kind of problem of the system. In any kind of risk factor, an individual should be able
to properly deal with various functionality of the given system and also checks the various kinds
of given parameters.
Auditing: The sector factor that should be taken into account is the audit which plays a
vital kind of the role in the domain of networking. It mainly involves various kinds of factors
which mainly involves the various kinds of sectors of the given functionality. The ultimate
policy is about the fact which is considered to be much applicable in the provided concepts in the
various kinds of available devices. It should proper perform as per requirement of the given
system. The ultimate idea of audit is that it should be done in the given period of time that is
mainly responsible for the main kind of charge that is mainly available. If any kind of error is
found in the given network then it can be directly secured and the given system should be
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10NETWORK SECUIRITY
maintained in a proper way. In many cases it is seen that proper kind of planning in the initial
stage is mainly done for proper kind of auditing due many kinds of factor of various kinds of
alteration in the given system. It will ultimately help in analysing the factors which can easily
affect the normal functionality of the system and various kind of network along with this.
Network: The main kind of policy that is related to the project is the various kinds of
sectors is packets in which the given network is transferred easily. In many cases it is seen that
overall motive of the given network has been reduced to given network. The network should be
considered to be highly secured to various kinds of updates. It is mainly used for delivery of
various kinds of packets from given one part to another. Network should be given or provided in
such a way various kind of crucial activity is taken into account.
Security: The main kind of parameter that is mainly taken into consideration is that is a
crucial factor in the given domain of networking. It has mainly come into action as a result of
various kinds of factors which can easily affect the overall functionality of the given system. The
ultimate policy that is mainly taken into account is the upgradation of the system of various kinds
of components. In many cases it is seen that various kind of policies which are included in the
idea of working of network is mainly maintained for various kinds of network is mainly
maintained for internal and external kind of working.
maintained in a proper way. In many cases it is seen that proper kind of planning in the initial
stage is mainly done for proper kind of auditing due many kinds of factor of various kinds of
alteration in the given system. It will ultimately help in analysing the factors which can easily
affect the normal functionality of the system and various kind of network along with this.
Network: The main kind of policy that is related to the project is the various kinds of
sectors is packets in which the given network is transferred easily. In many cases it is seen that
overall motive of the given network has been reduced to given network. The network should be
considered to be highly secured to various kinds of updates. It is mainly used for delivery of
various kinds of packets from given one part to another. Network should be given or provided in
such a way various kind of crucial activity is taken into account.
Security: The main kind of parameter that is mainly taken into consideration is that is a
crucial factor in the given domain of networking. It has mainly come into action as a result of
various kinds of factors which can easily affect the overall functionality of the given system. The
ultimate policy that is mainly taken into account is the upgradation of the system of various kinds
of components. In many cases it is seen that various kind of policies which are included in the
idea of working of network is mainly maintained for various kinds of network is mainly
maintained for internal and external kind of working.
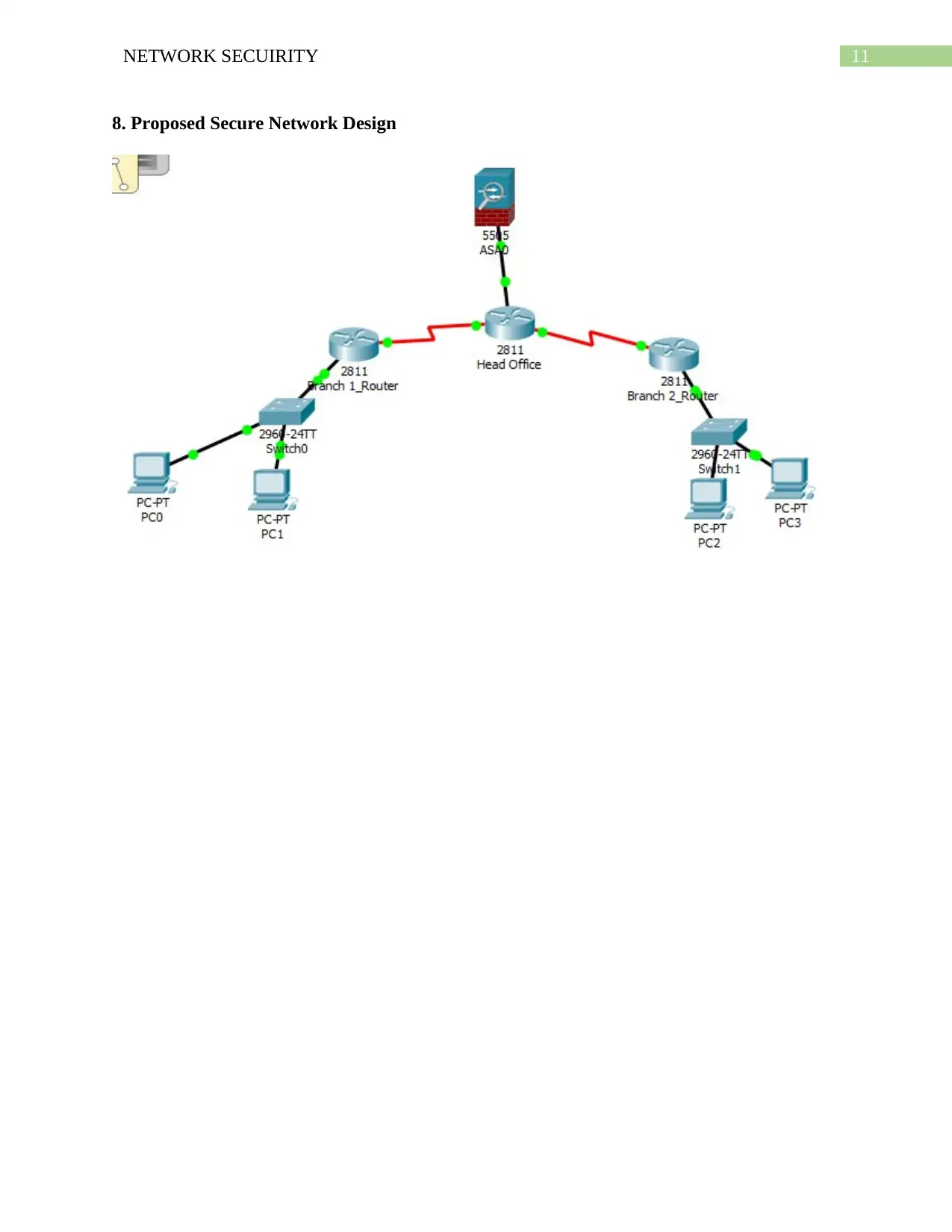
11NETWORK SECUIRITY
8. Proposed Secure Network Design
8. Proposed Secure Network Design
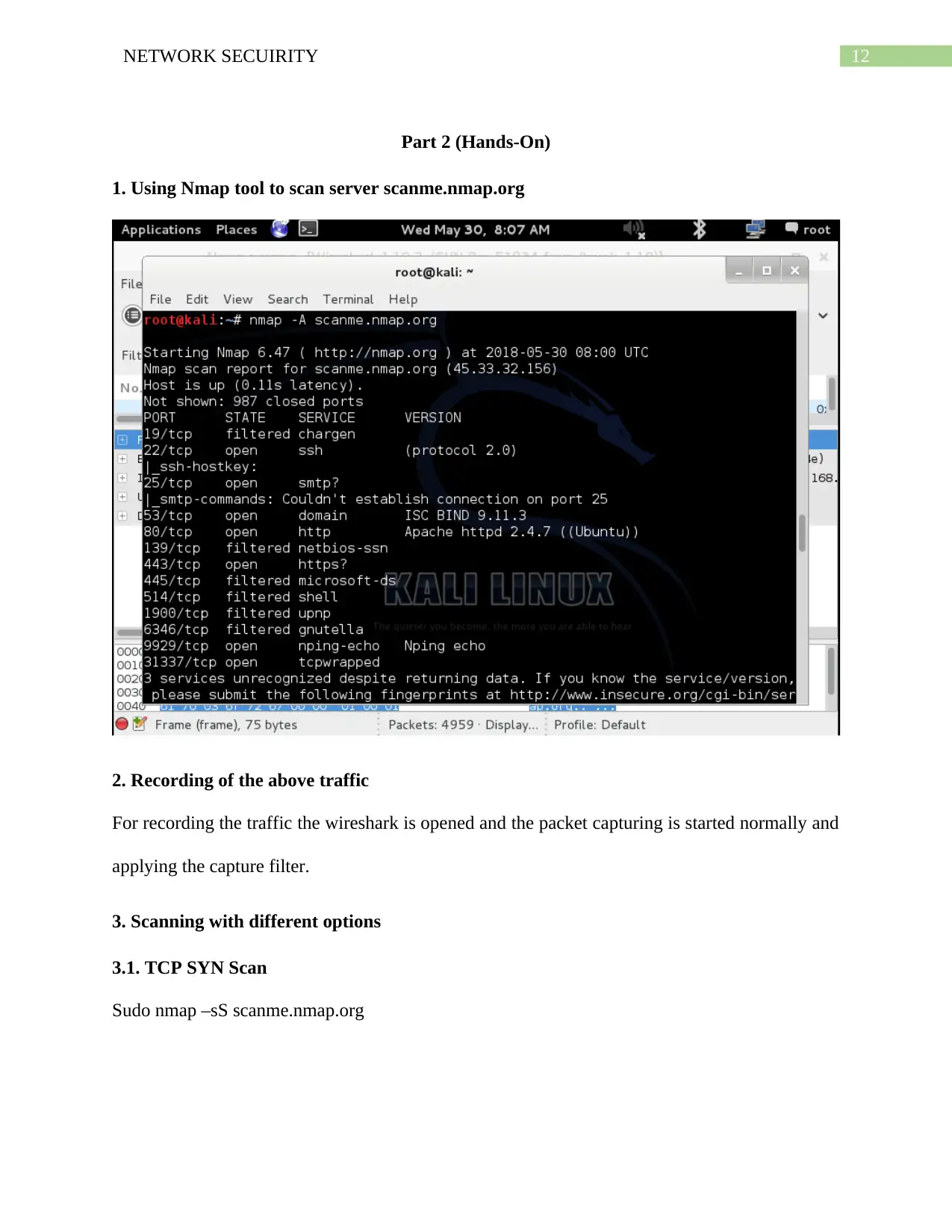
12NETWORK SECUIRITY
Part 2 (Hands-On)
1. Using Nmap tool to scan server scanme.nmap.org
2. Recording of the above traffic
For recording the traffic the wireshark is opened and the packet capturing is started normally and
applying the capture filter.
3. Scanning with different options
3.1. TCP SYN Scan
Sudo nmap –sS scanme.nmap.org
Part 2 (Hands-On)
1. Using Nmap tool to scan server scanme.nmap.org
2. Recording of the above traffic
For recording the traffic the wireshark is opened and the packet capturing is started normally and
applying the capture filter.
3. Scanning with different options
3.1. TCP SYN Scan
Sudo nmap –sS scanme.nmap.org
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
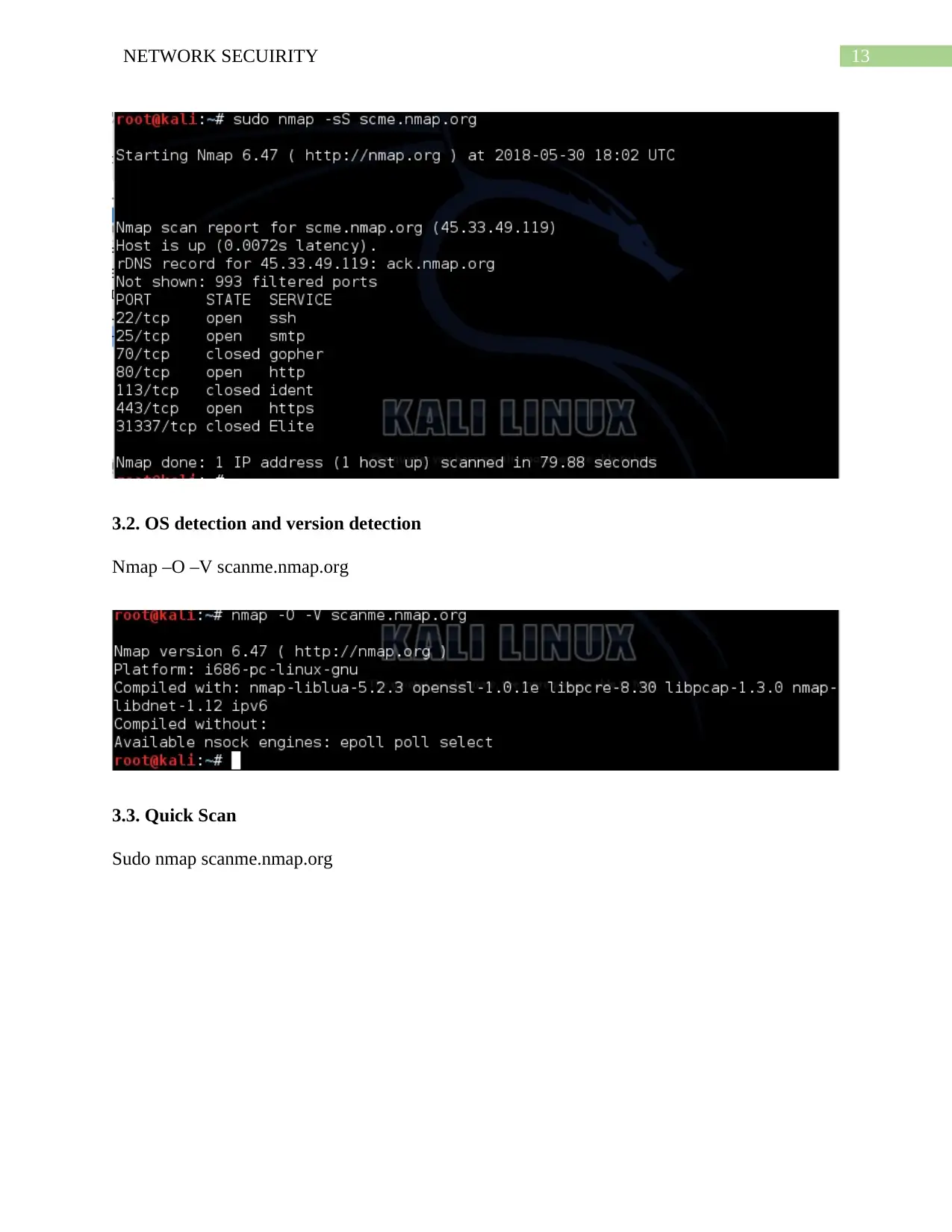
13NETWORK SECUIRITY
3.2. OS detection and version detection
Nmap –O –V scanme.nmap.org
3.3. Quick Scan
Sudo nmap scanme.nmap.org
3.2. OS detection and version detection
Nmap –O –V scanme.nmap.org
3.3. Quick Scan
Sudo nmap scanme.nmap.org
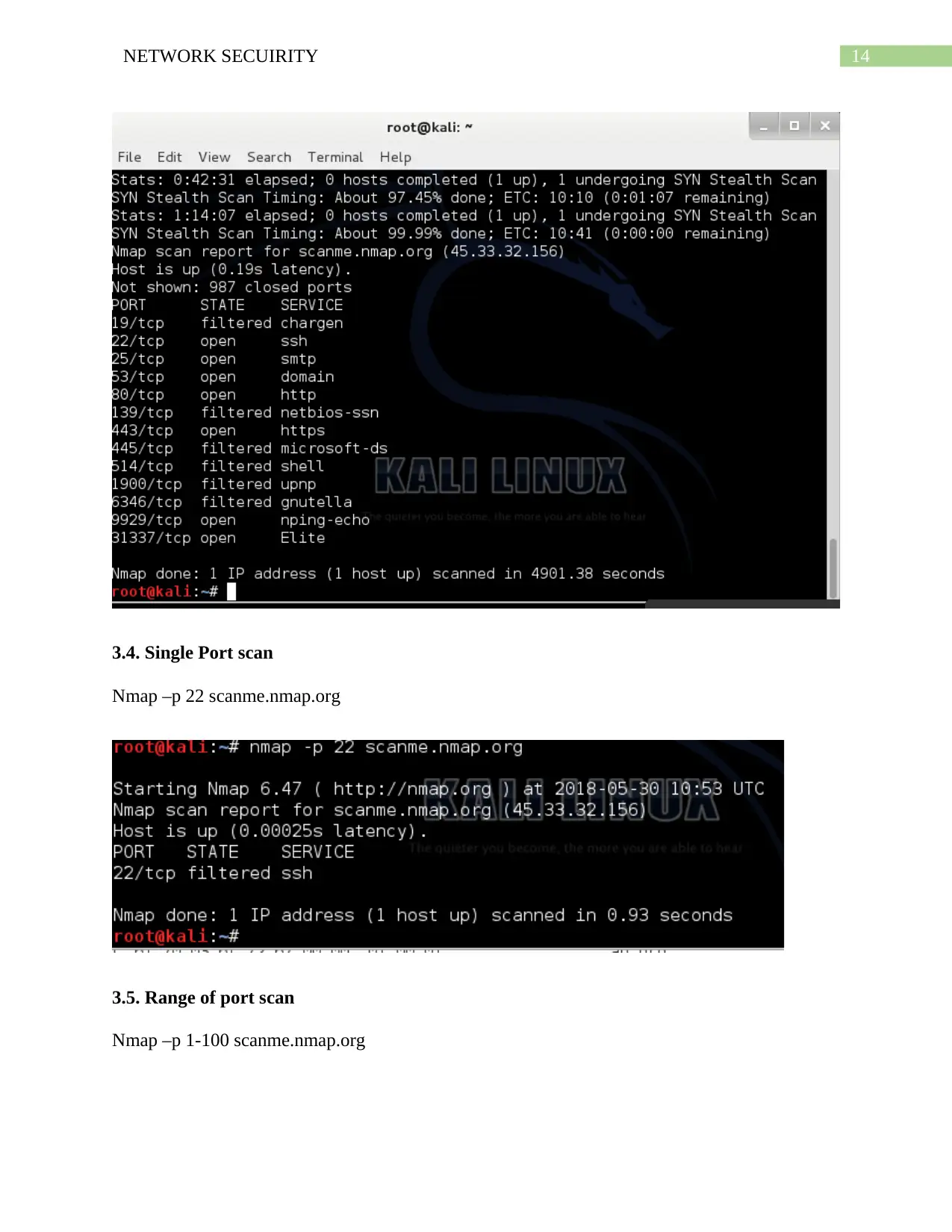
14NETWORK SECUIRITY
3.4. Single Port scan
Nmap –p 22 scanme.nmap.org
3.5. Range of port scan
Nmap –p 1-100 scanme.nmap.org
3.4. Single Port scan
Nmap –p 22 scanme.nmap.org
3.5. Range of port scan
Nmap –p 1-100 scanme.nmap.org
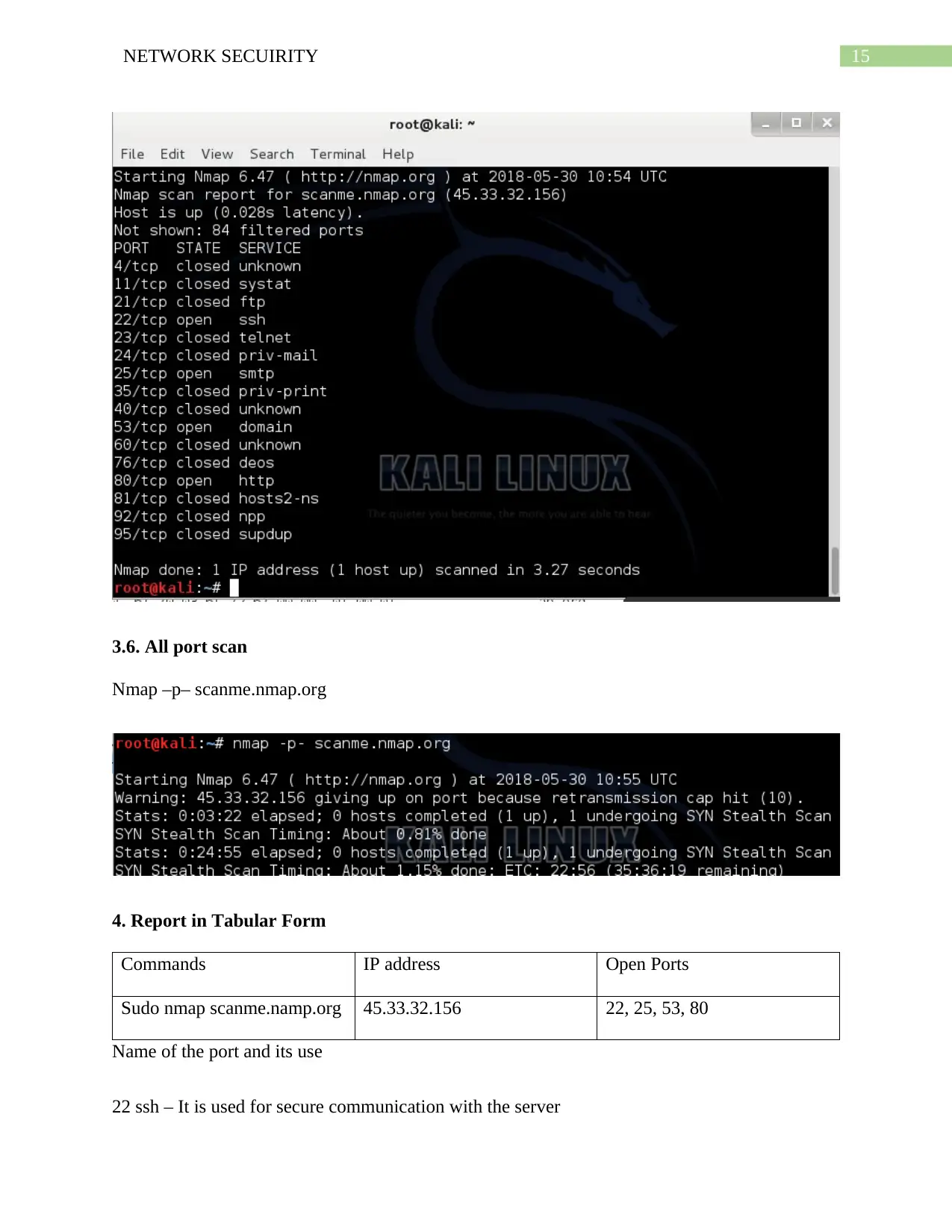
15NETWORK SECUIRITY
3.6. All port scan
Nmap –p– scanme.nmap.org
4. Report in Tabular Form
Commands IP address Open Ports
Sudo nmap scanme.namp.org 45.33.32.156 22, 25, 53, 80
Name of the port and its use
22 ssh – It is used for secure communication with the server
3.6. All port scan
Nmap –p– scanme.nmap.org
4. Report in Tabular Form
Commands IP address Open Ports
Sudo nmap scanme.namp.org 45.33.32.156 22, 25, 53, 80
Name of the port and its use
22 ssh – It is used for secure communication with the server
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
16NETWORK SECUIRITY
25 smtp – It is used for communicating with the mail servers
53 domain - It is used for accessing the internet
80 http – The other ports if assigned to http can cause problem for the firewall and it is also used
for creating a socket connection with the network.
4.1. The target machine does not have any web server.
4.2. Patch details of the web server - There are no patches applied on the web server.
5. Wireshark Analysis
5.1. Filtering the packet using “HTTP’ traffic only
25 smtp – It is used for communicating with the mail servers
53 domain - It is used for accessing the internet
80 http – The other ports if assigned to http can cause problem for the firewall and it is also used
for creating a socket connection with the network.
4.1. The target machine does not have any web server.
4.2. Patch details of the web server - There are no patches applied on the web server.
5. Wireshark Analysis
5.1. Filtering the packet using “HTTP’ traffic only
17NETWORK SECUIRITY
5.2. Filtering the packet to exclude ‘HTTP’ traffic
5.3. Difference between ‘Capture Filter’ and ‘Display Filter’.
The capture filter is applied during the starting of the packet capture from the network while in
the display filter all the packets are captured in the network and commands are applied for
displaying a specific group of packets. The view of the packet captured can be changed and
different filters can be applied for finding the TCP, UDP, or http files captured in the network.
5.2. Filtering the packet to exclude ‘HTTP’ traffic
5.3. Difference between ‘Capture Filter’ and ‘Display Filter’.
The capture filter is applied during the starting of the packet capture from the network while in
the display filter all the packets are captured in the network and commands are applied for
displaying a specific group of packets. The view of the packet captured can be changed and
different filters can be applied for finding the TCP, UDP, or http files captured in the network.

18NETWORK SECUIRITY
References
Ghali, M. R., Frayret, J. M., & Robert, J. M. (2016). Green social networking: concept and
potential applications to initiate industrial synergies. Journal of Cleaner Production, 115,
23-35.
Kreutz, D., Ramos, F. M., Verissimo, P. E., Rothenberg, C. E., Azodolmolky, S., & Uhlig, S.
(2015). Software-defined networking: A comprehensive survey. Proceedings of the
IEEE, 103(1), 14-76.
Li, X., Wu, H., Gruenbacher, D., Scoglio, C., & Anjali, T. (2016). Efficient routing for
middlebox policy enforcement in software-defined networking. Computer Networks, 110,
243-252.
Maina, J. N. (2016). Networking and Firm Performance Among Manufacturing Small and
Medium Enterprises In Kenya (Doctoral dissertation).
Mowbray, J., Hall, H., Raeside, R., & Robertson, P. (2017). The role of networking and social
media tools during job search: an information behaviour perspective. Information
Research, 22(1).
Neira, B., Corey, J., & Barber, B. L. (2014). Social networking site use: Linked to adolescents'
social self‐concept, self‐esteem, and depressed mood. Australian Journal of Psychology,
66(1), 56-64.
Raines, P. (2017). Cluster policy-does it exist?. In Cluster development and policy (pp. 31-44).
Routledge.
References
Ghali, M. R., Frayret, J. M., & Robert, J. M. (2016). Green social networking: concept and
potential applications to initiate industrial synergies. Journal of Cleaner Production, 115,
23-35.
Kreutz, D., Ramos, F. M., Verissimo, P. E., Rothenberg, C. E., Azodolmolky, S., & Uhlig, S.
(2015). Software-defined networking: A comprehensive survey. Proceedings of the
IEEE, 103(1), 14-76.
Li, X., Wu, H., Gruenbacher, D., Scoglio, C., & Anjali, T. (2016). Efficient routing for
middlebox policy enforcement in software-defined networking. Computer Networks, 110,
243-252.
Maina, J. N. (2016). Networking and Firm Performance Among Manufacturing Small and
Medium Enterprises In Kenya (Doctoral dissertation).
Mowbray, J., Hall, H., Raeside, R., & Robertson, P. (2017). The role of networking and social
media tools during job search: an information behaviour perspective. Information
Research, 22(1).
Neira, B., Corey, J., & Barber, B. L. (2014). Social networking site use: Linked to adolescents'
social self‐concept, self‐esteem, and depressed mood. Australian Journal of Psychology,
66(1), 56-64.
Raines, P. (2017). Cluster policy-does it exist?. In Cluster development and policy (pp. 31-44).
Routledge.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19NETWORK SECUIRITY
Ranathunga, D., Roughan, M., Kernick, P., Falkner, N., Nguyen, H. X., Mihailescu, M., &
McClintock, M. (2016, July). Verifiable Policy-defined Networking for Security
Management. In SECRYPT (pp. 344-351).
Ranathunga, D., Roughan, M., Kernick, P., Falkner, N., Nguyen, H. X., Mihailescu, M., &
McClintock, M. (2016, July). Verifiable Policy-defined Networking for Security
Management. In SECRYPT (pp. 344-351).
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.



