Digital Forensics Report for EMTS Organization
VerifiedAdded on 2023/06/12
|28
|2503
|371
AI Summary
This report discusses the use of Winhex, Steganography, and Pro Discover tools to recover lost data for EMTS organization. It includes step-by-step procedures and screenshots of the recovery process. The report covers the background, scope, and forensic tools used for the recovery process. It also includes the analysis of each tool and the findings and evidence obtained from the recovery process.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

DIGITAL FORENSICS
1
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Abstract
This project is needs to successfully create the digital forensic report for EMTS
organization because this organization lost the suspicious data. So, it needs to be recovered by
using the appropriate digital forensic tools. These tools are used to accomplish the data recovery
process for an organization. This organization chief was decided to recovery the deleted data and
it managed by Bob Aspen. The Bob Aspen is working as contract employee of the Exotic
Mountain Tour services (EMTS). This EMTS organization has completed a very expensive
marketing process and analysis on the customer services and it provided by the superior bicycle
LLC Company. In our case study, we are using the Winhex tool to recovery the corrupted images
from USB, recover the all the file from hard drive by using the pro discover forensic tool and
image steganography tool is used to recover the hidden text in the image from USB.
This project is needs to successfully create the digital forensic report for EMTS
organization because this organization lost the suspicious data. So, it needs to be recovered by
using the appropriate digital forensic tools. These tools are used to accomplish the data recovery
process for an organization. This organization chief was decided to recovery the deleted data and
it managed by Bob Aspen. The Bob Aspen is working as contract employee of the Exotic
Mountain Tour services (EMTS). This EMTS organization has completed a very expensive
marketing process and analysis on the customer services and it provided by the superior bicycle
LLC Company. In our case study, we are using the Winhex tool to recovery the corrupted images
from USB, recover the all the file from hard drive by using the pro discover forensic tool and
image steganography tool is used to recover the hidden text in the image from USB.

Table of Contents
1. Introduction.........................................................................................................................................4
1.1 Back ground.................................................................................................................................4
1.2 Scope...........................................................................................................................................4
1.3 Forensic tool................................................................................................................................4
2. Analysis...............................................................................................................................................4
2.1 Winhex........................................................................................................................................4
2.2 Steganography.............................................................................................................................5
2.3 Pro Discover Tool........................................................................................................................6
3. Finding and Evidence..........................................................................................................................7
3.1 Recover the deleted image in the usb Using Winhex...................................................................7
3.2 Recover the hidden text in Image using Steganography tool.....................................................14
3.3 Recovery the Files from USB by using Pro Discover Tool........................................................17
4. Conclusion.........................................................................................................................................21
References.................................................................................................................................................22
1. Introduction.........................................................................................................................................4
1.1 Back ground.................................................................................................................................4
1.2 Scope...........................................................................................................................................4
1.3 Forensic tool................................................................................................................................4
2. Analysis...............................................................................................................................................4
2.1 Winhex........................................................................................................................................4
2.2 Steganography.............................................................................................................................5
2.3 Pro Discover Tool........................................................................................................................6
3. Finding and Evidence..........................................................................................................................7
3.1 Recover the deleted image in the usb Using Winhex...................................................................7
3.2 Recover the hidden text in Image using Steganography tool.....................................................14
3.3 Recovery the Files from USB by using Pro Discover Tool........................................................17
4. Conclusion.........................................................................................................................................21
References.................................................................................................................................................22

Task – 1
1. Recover the Scrambled Bits
To recover the scrabbled bits by uses the Winhex forensic tools. The Winhex forensic tool is
used to recovery the data. It provides the effective data recovery. To recovery the scrambled bits
by follows the below steps.
First open the Winhex forensic Tool.
To open the scrambled bits by click the tools to select the start center. After, open the scrambled
bits of text. It is shown below.
1. Recover the Scrambled Bits
To recover the scrabbled bits by uses the Winhex forensic tools. The Winhex forensic tool is
used to recovery the data. It provides the effective data recovery. To recovery the scrambled bits
by follows the below steps.
First open the Winhex forensic Tool.
To open the scrambled bits by click the tools to select the start center. After, open the scrambled
bits of text. It is shown below.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
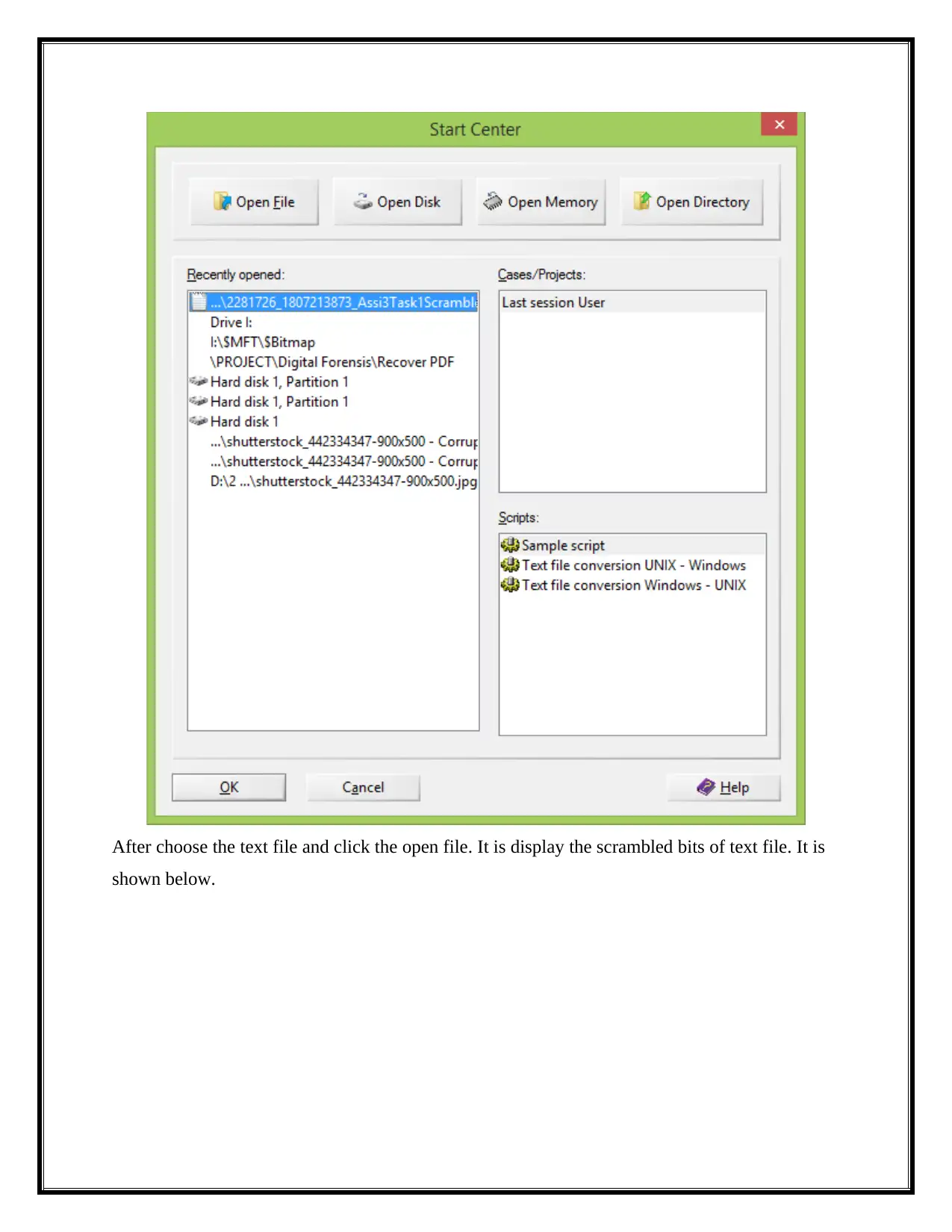
After choose the text file and click the open file. It is display the scrambled bits of text file. It is
shown below.
shown below.
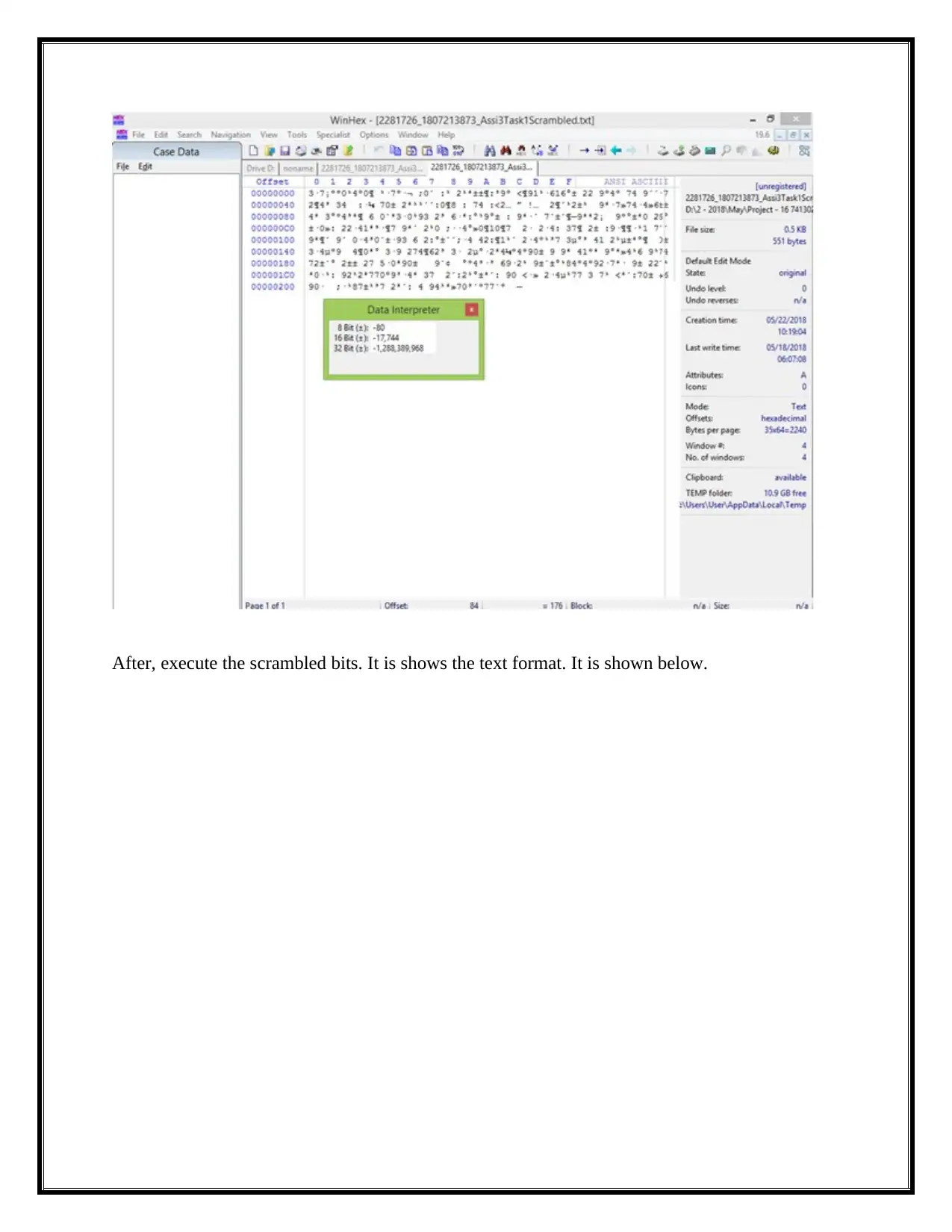
After, execute the scrambled bits. It is shows the text format. It is shown below.
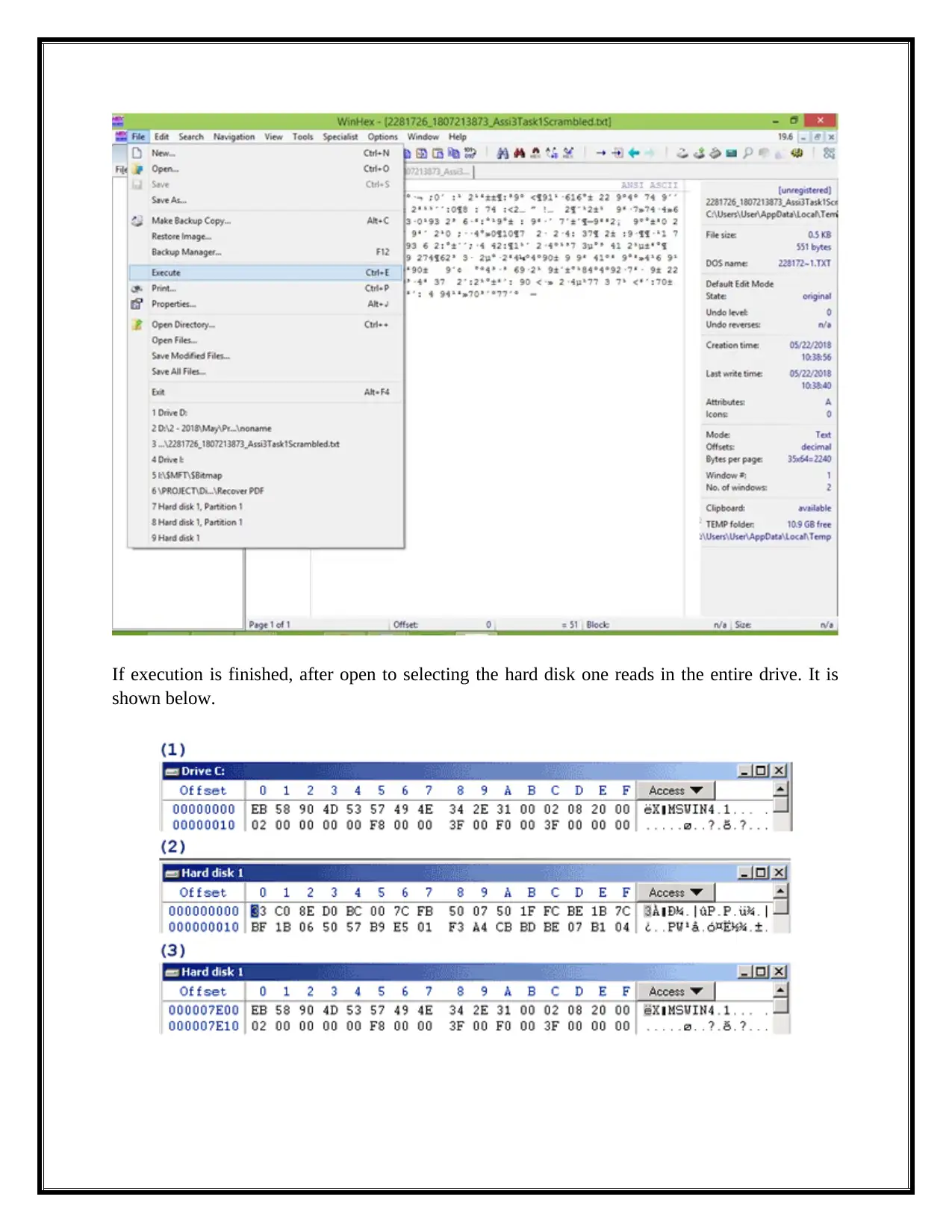
If execution is finished, after open to selecting the hard disk one reads in the entire drive. It is
shown below.
shown below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
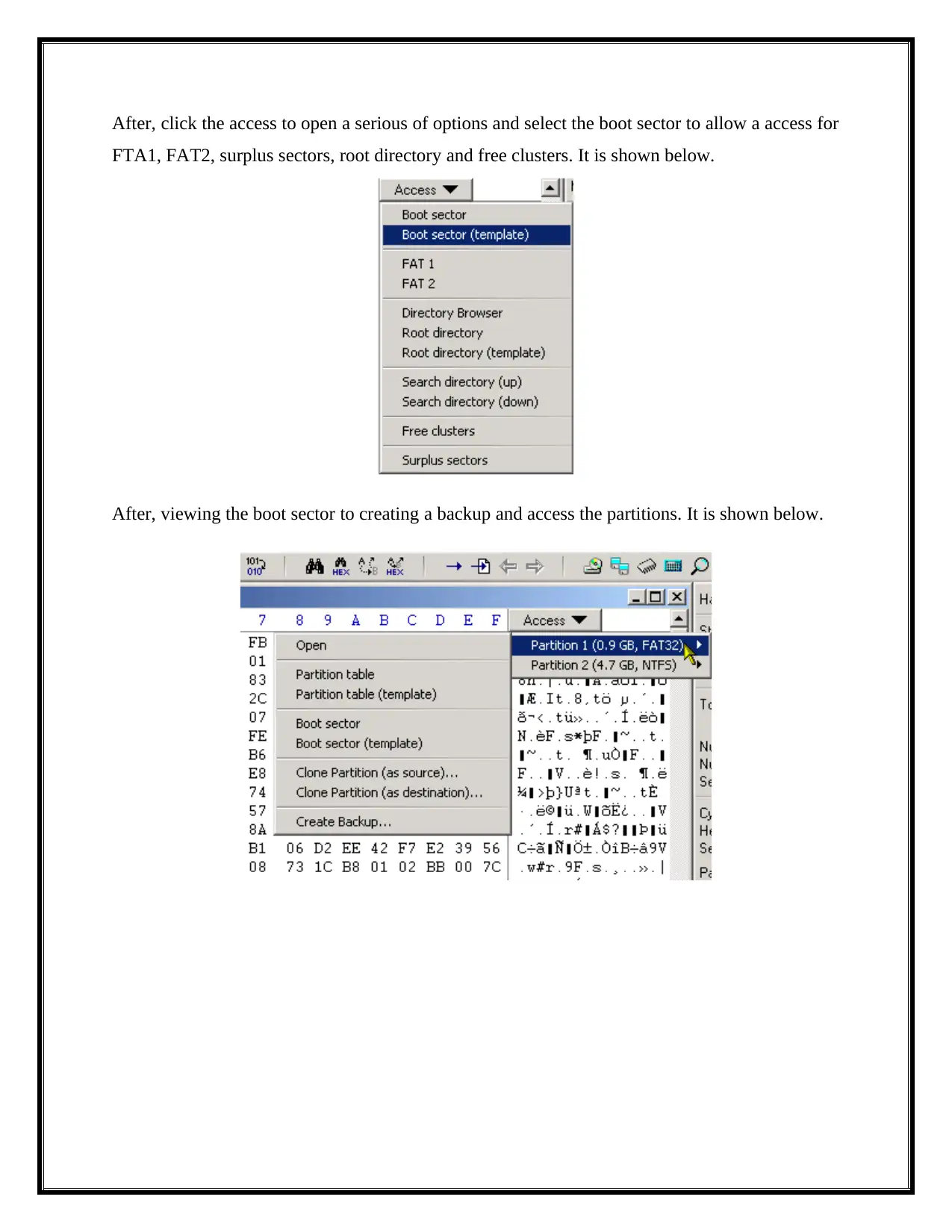
After, click the access to open a serious of options and select the boot sector to allow a access for
FTA1, FAT2, surplus sectors, root directory and free clusters. It is shown below.
After, viewing the boot sector to creating a backup and access the partitions. It is shown below.
FTA1, FAT2, surplus sectors, root directory and free clusters. It is shown below.
After, viewing the boot sector to creating a backup and access the partitions. It is shown below.
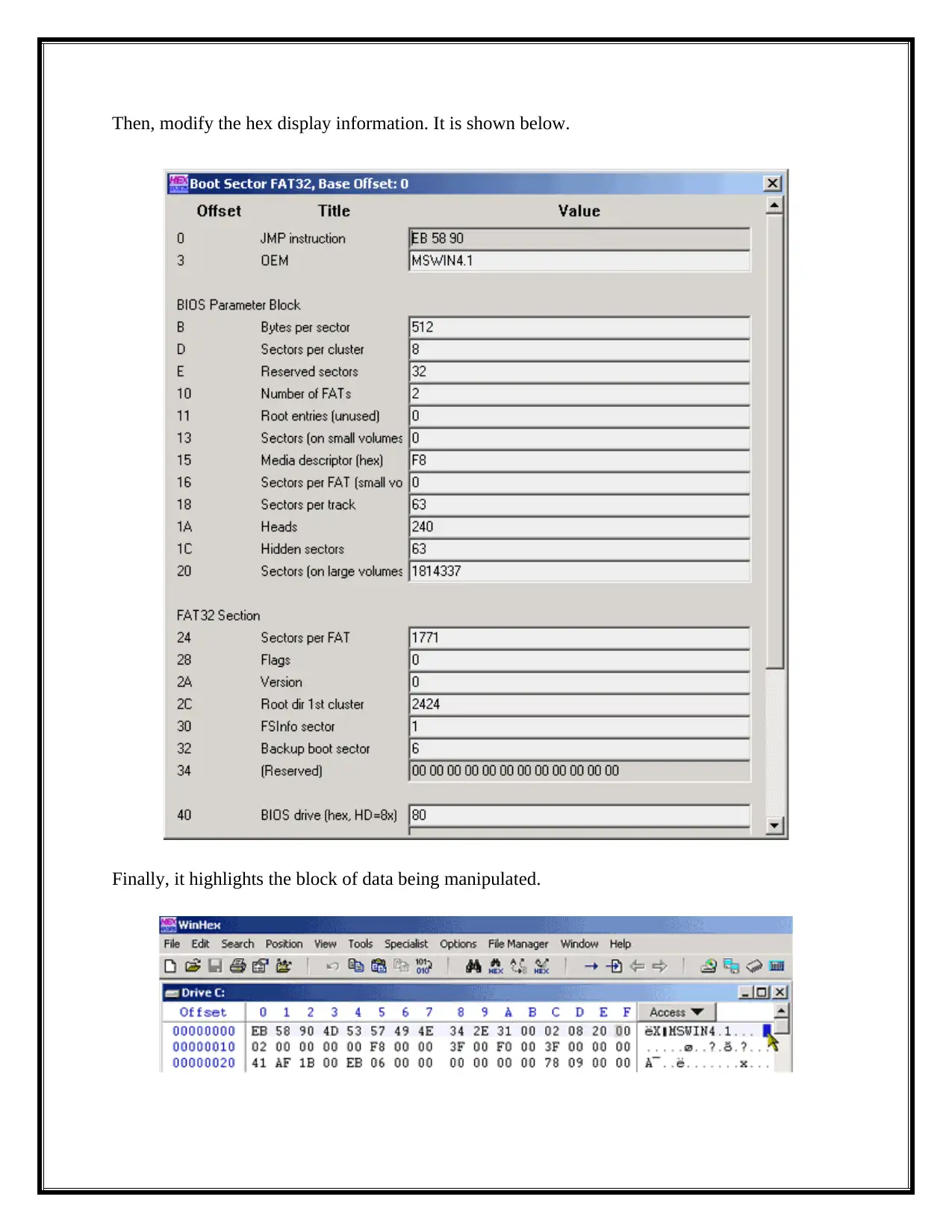
Then, modify the hex display information. It is shown below.
Finally, it highlights the block of data being manipulated.
Finally, it highlights the block of data being manipulated.
Task – 2
2. Introduction
2.1 Back ground
This project goal is to prepare the digital forensics report for an EMTS organization
because this organization lost the suspicious data and it needs to be recovers. So, creates digital
forensics data recovery process based reports. This organization is investigating the probable
intellectual property which is stolen by the Bob Aspen who is working as contract employee of
the Exotic Mountain Tour services (EMTS). This EMTS organization has completed a very
expensive marketing process and analysis on the customer services and it provided by the
superior bicycle LLC Company. The EMTS chief found a USB drive on the work area was
allocated to Bob aspen and this work decide if the drive you some intriguing the data he
accumulated from the web server executive.
2.2 Scope
Scope of this project is to create the digital forensic report for an organization. This
organization lost the suspicious data and it needs to be recovered by using the appropriate data
recovery techniques (Advances in Digital Forensics 9, 2016). Here, we will use three forensic
tools like pro discover, Winhex and image steganography. The Winhex forensic tool is used to
2. Introduction
2.1 Back ground
This project goal is to prepare the digital forensics report for an EMTS organization
because this organization lost the suspicious data and it needs to be recovers. So, creates digital
forensics data recovery process based reports. This organization is investigating the probable
intellectual property which is stolen by the Bob Aspen who is working as contract employee of
the Exotic Mountain Tour services (EMTS). This EMTS organization has completed a very
expensive marketing process and analysis on the customer services and it provided by the
superior bicycle LLC Company. The EMTS chief found a USB drive on the work area was
allocated to Bob aspen and this work decide if the drive you some intriguing the data he
accumulated from the web server executive.
2.2 Scope
Scope of this project is to create the digital forensic report for an organization. This
organization lost the suspicious data and it needs to be recovered by using the appropriate data
recovery techniques (Advances in Digital Forensics 9, 2016). Here, we will use three forensic
tools like pro discover, Winhex and image steganography. The Winhex forensic tool is used to
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

recover the corrupted images from the hard drive. The Pro discover tool is used to recover the all
the data from the hard drive. The image steganography tool is used to recover the hidden text in
the images from USB. These are will be analysed and discussed in detail.
2.3 Forensic tool
The ENTS using the following forensics tools to recover the suspicious data from USB. These
are,
Pro Discover Tool
Winhex Tool
Image Steganography Tool
These are discussed and analyzed in below.
3. Analysis
3.1 Winhex
The Winhex forensic tool is very helpful for realm of data recovery, low level data editing and
computer forensics (AG, 2018). It is used to recovery and editing the following aspects like CD-
ROM, computer flash, floppy and more. So, many organizations use Winhex tool to provide the
efficient and effective data recovery process for an organization. This tool has many features
such as,
It has scripting and programming interfaces
Wipe drives.
Make hashes and checksums.
Join and split records.
Disk cloning
Examine and look at records.
Convert between the Intel hex, ASCII, binary and more.
It uses the various data recovery techniques.
Recapture information.
Encode records.
The Winhex tool also has the printing, instant window switching and random
number generator.
Diving and unifying the even and odd words and bytes.
the data from the hard drive. The image steganography tool is used to recover the hidden text in
the images from USB. These are will be analysed and discussed in detail.
2.3 Forensic tool
The ENTS using the following forensics tools to recover the suspicious data from USB. These
are,
Pro Discover Tool
Winhex Tool
Image Steganography Tool
These are discussed and analyzed in below.
3. Analysis
3.1 Winhex
The Winhex forensic tool is very helpful for realm of data recovery, low level data editing and
computer forensics (AG, 2018). It is used to recovery and editing the following aspects like CD-
ROM, computer flash, floppy and more. So, many organizations use Winhex tool to provide the
efficient and effective data recovery process for an organization. This tool has many features
such as,
It has scripting and programming interfaces
Wipe drives.
Make hashes and checksums.
Join and split records.
Disk cloning
Examine and look at records.
Convert between the Intel hex, ASCII, binary and more.
It uses the various data recovery techniques.
Recapture information.
Encode records.
The Winhex tool also has the printing, instant window switching and random
number generator.
Diving and unifying the even and odd words and bytes.

It has disk editor for floppy disks, CD-ROM, smart media, floppy disks, hard
disks and more.
It splitting and concatenating and files
Support file of any size
Extensive program help
Import all the clip board formats
Editing data structures using templates
Comparing and analysing the files
3.2 Steganography
Generally, the steganography tools have different software’s and it is used to hide the
secret text from Images file, HTML file and any kind of files. Here, we are using the Image
steganography tool to hide the secret text from the Image file. The image steganography tool is
also used to hiding the user information in the image file. It can hide the text files inside the
image file ("Best Tools to Perform Steganography", 2018). To perform an image steganography
by select the source in which you want to hide the secret messages and select the files to hidden
the secrets text. Finally, select the output image locations because these tools do the both
encoding and decoding. We are doing the decoding techniques to hidden the text files from the
image.
3.3 Pro Discover Tool
The pro discover tool is the most powerful computer security tool and it used to provide the
powerful search capability is flexible and fast. It is very helpful capability and easy to use for an
organization ("ProDiscover Forensics - Software - Products", 2018). It can recover the deleted
files; dynamically allow a preview and examine slack space. It is used to utilizing the disk at the
sector level in the organization. It handles the organization security concerns. It designed to
NIST disk imaging tool and it insure the high quality. It previews all the files, even if hidden or
deleted without altering the data on disk. It supports the VM ware to run a captured image. It
creates the bit stream copy of disk to be analysed to keep original evidence safe ("Forensic
Toolkit", 2018). It maintains the multi tool compatibility by writing and reading the images. It
has various features such as,
Integrated thumbnail graphics
Internet history
disks and more.
It splitting and concatenating and files
Support file of any size
Extensive program help
Import all the clip board formats
Editing data structures using templates
Comparing and analysing the files
3.2 Steganography
Generally, the steganography tools have different software’s and it is used to hide the
secret text from Images file, HTML file and any kind of files. Here, we are using the Image
steganography tool to hide the secret text from the Image file. The image steganography tool is
also used to hiding the user information in the image file. It can hide the text files inside the
image file ("Best Tools to Perform Steganography", 2018). To perform an image steganography
by select the source in which you want to hide the secret messages and select the files to hidden
the secrets text. Finally, select the output image locations because these tools do the both
encoding and decoding. We are doing the decoding techniques to hidden the text files from the
image.
3.3 Pro Discover Tool
The pro discover tool is the most powerful computer security tool and it used to provide the
powerful search capability is flexible and fast. It is very helpful capability and easy to use for an
organization ("ProDiscover Forensics - Software - Products", 2018). It can recover the deleted
files; dynamically allow a preview and examine slack space. It is used to utilizing the disk at the
sector level in the organization. It handles the organization security concerns. It designed to
NIST disk imaging tool and it insure the high quality. It previews all the files, even if hidden or
deleted without altering the data on disk. It supports the VM ware to run a captured image. It
creates the bit stream copy of disk to be analysed to keep original evidence safe ("Forensic
Toolkit", 2018). It maintains the multi tool compatibility by writing and reading the images. It
has various features such as,
Integrated thumbnail graphics
Internet history

Event log file
Integrated viewer to examine the files
Integrated and GUI interface function is used to assure the ease of use and quick start.
Ensure high quality
Utilize the Perl scripts
Utilize the user provide and national Drug intelligence
Prove the data integrity
Search the entire disk
Extracts the EXIF information
Examine the sun Solaris UFS file
Examine the Linux file systems
Automated report generation
4. Finding and Evidence
3.1 Recover the deleted image in the usb Using Winhex
The digital forensic tool is used to recover the deleted and lost data from hard drive. The
EMTS organization is lost the suspicious data and it needs to be recovered by using the various
data recovery techniques (Gogolin, 2013). So, we will use the Winhex tool to recover the deleted
images in the USB. The Winhex tool is used to provide the efficient and effective data recovery
process for an organization. It is very helpful tool for an organization. The below screenshots is
shows the corrupted images and this images to needs recovered by using the Winhex forensics
tool.
Integrated viewer to examine the files
Integrated and GUI interface function is used to assure the ease of use and quick start.
Ensure high quality
Utilize the Perl scripts
Utilize the user provide and national Drug intelligence
Prove the data integrity
Search the entire disk
Extracts the EXIF information
Examine the sun Solaris UFS file
Examine the Linux file systems
Automated report generation
4. Finding and Evidence
3.1 Recover the deleted image in the usb Using Winhex
The digital forensic tool is used to recover the deleted and lost data from hard drive. The
EMTS organization is lost the suspicious data and it needs to be recovered by using the various
data recovery techniques (Gogolin, 2013). So, we will use the Winhex tool to recover the deleted
images in the USB. The Winhex tool is used to provide the efficient and effective data recovery
process for an organization. It is very helpful tool for an organization. The below screenshots is
shows the corrupted images and this images to needs recovered by using the Winhex forensics
tool.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
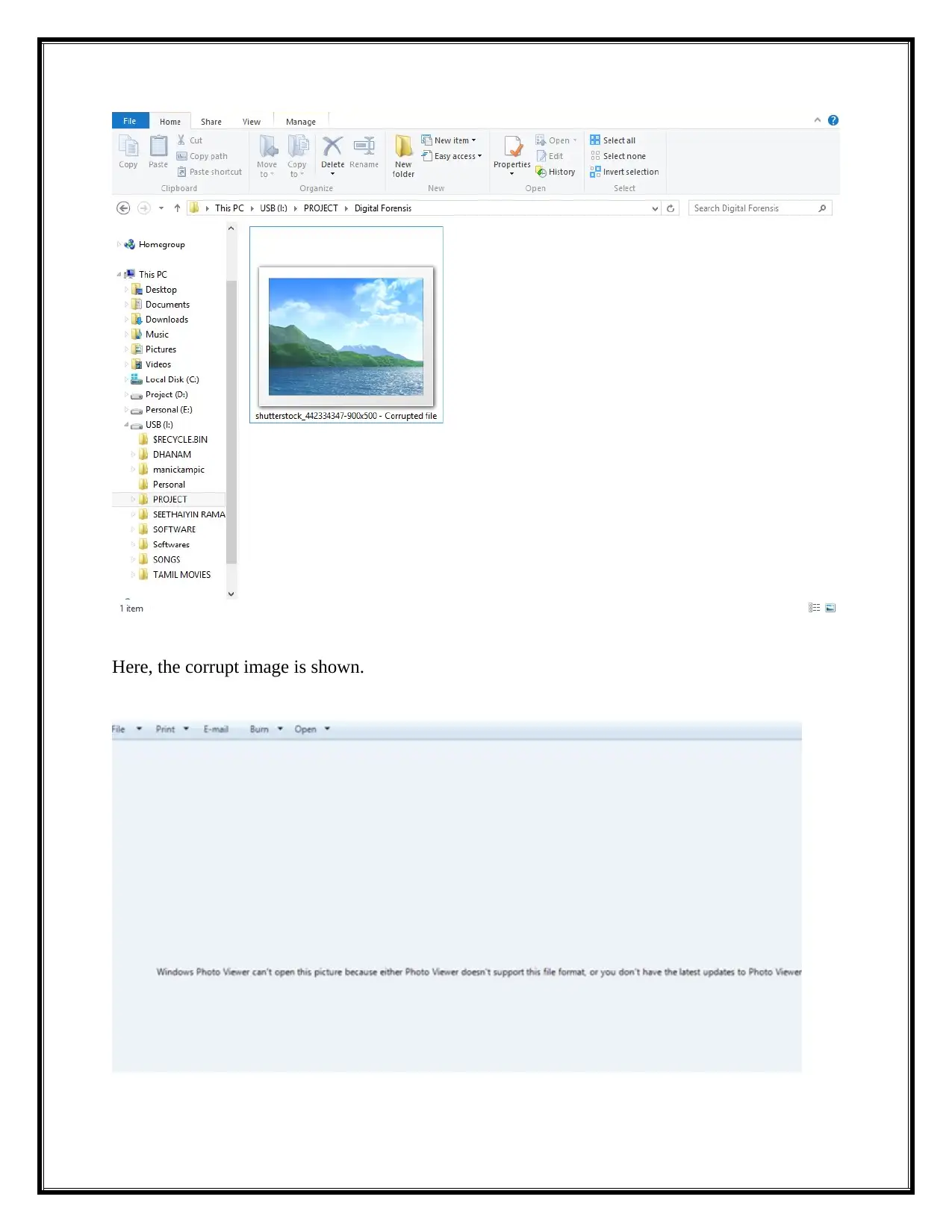
Here, the corrupt image is shown.
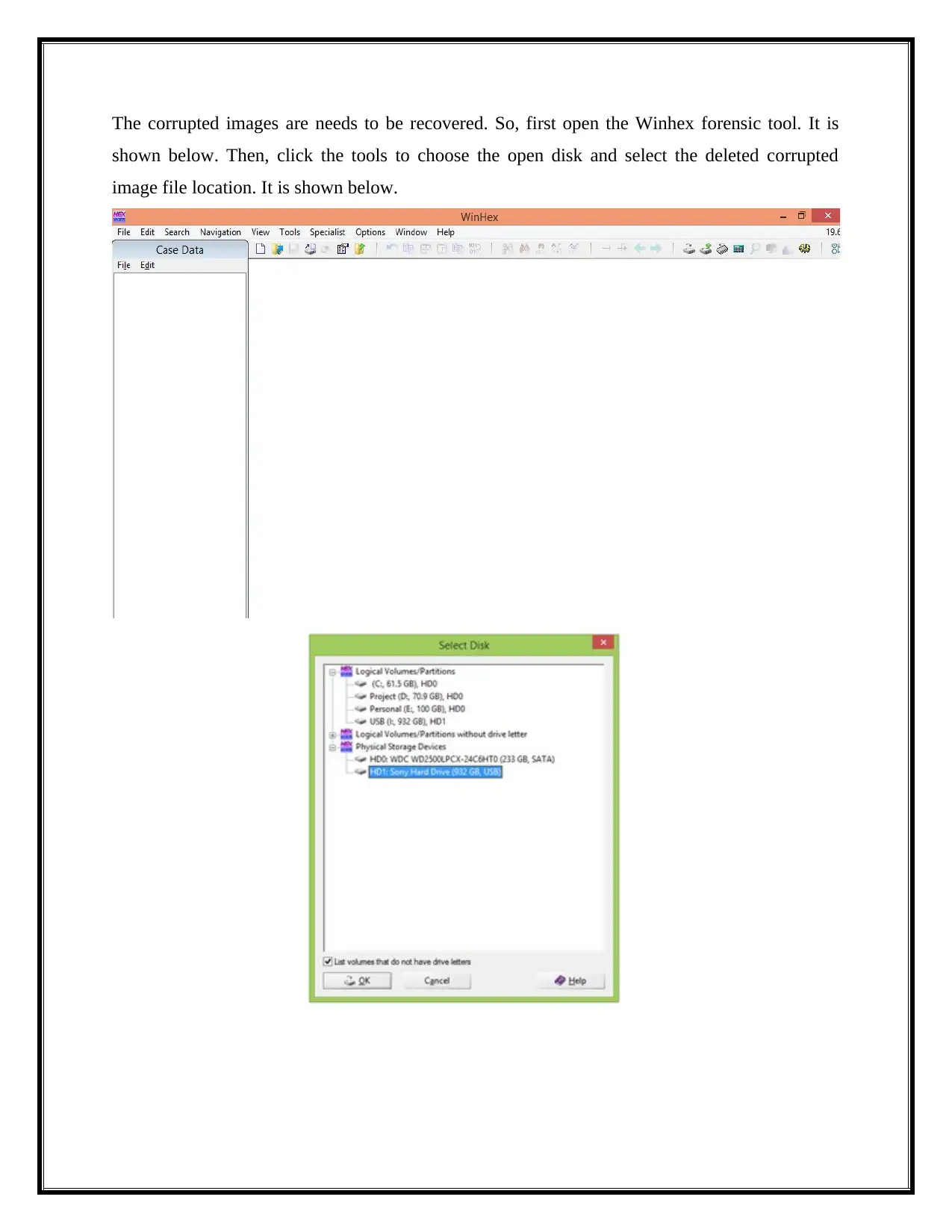
The corrupted images are needs to be recovered. So, first open the Winhex forensic tool. It is
shown below. Then, click the tools to choose the open disk and select the deleted corrupted
image file location. It is shown below.
shown below. Then, click the tools to choose the open disk and select the deleted corrupted
image file location. It is shown below.

After, choose the corrupted images from deleted location in USB. Then, the Winhex forensic
tool is display the deleted data. The corrupted images are shown below ("How to use
ProDiscover, ProDiscover Forensics,", 2018).
Then, initialize the hard drive by click the tool to and select the disk initialize and it used
to shows the recovered images properties. This process is used to free up the hard drive space to
saves the recovered images in the USB. It is shown below ("ProDiscover Forensic Data
Recovery", 2018).
tool is display the deleted data. The corrupted images are shown below ("How to use
ProDiscover, ProDiscover Forensics,", 2018).
Then, initialize the hard drive by click the tool to and select the disk initialize and it used
to shows the recovered images properties. This process is used to free up the hard drive space to
saves the recovered images in the USB. It is shown below ("ProDiscover Forensic Data
Recovery", 2018).
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
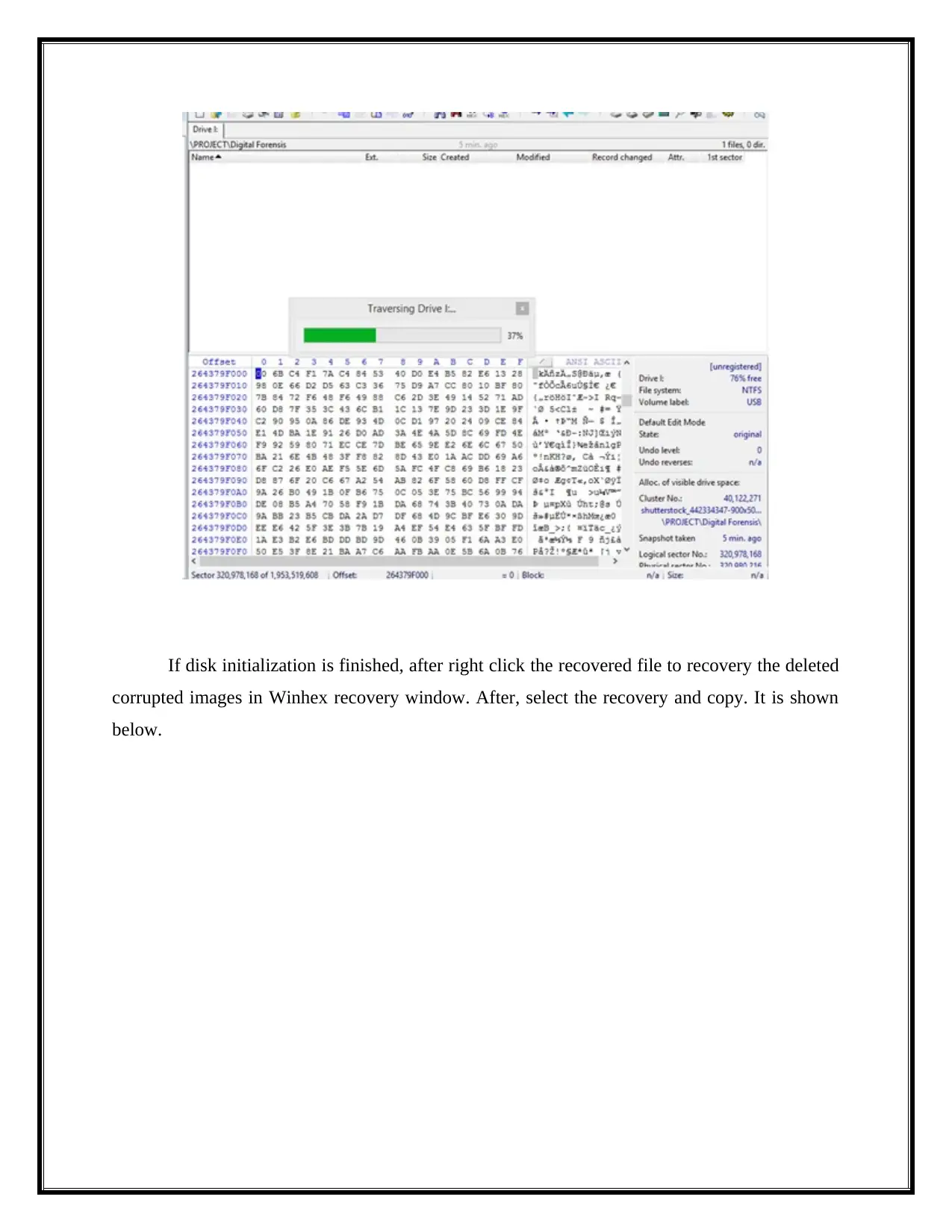
If disk initialization is finished, after right click the recovered file to recovery the deleted
corrupted images in Winhex recovery window. After, select the recovery and copy. It is shown
below.
corrupted images in Winhex recovery window. After, select the recovery and copy. It is shown
below.
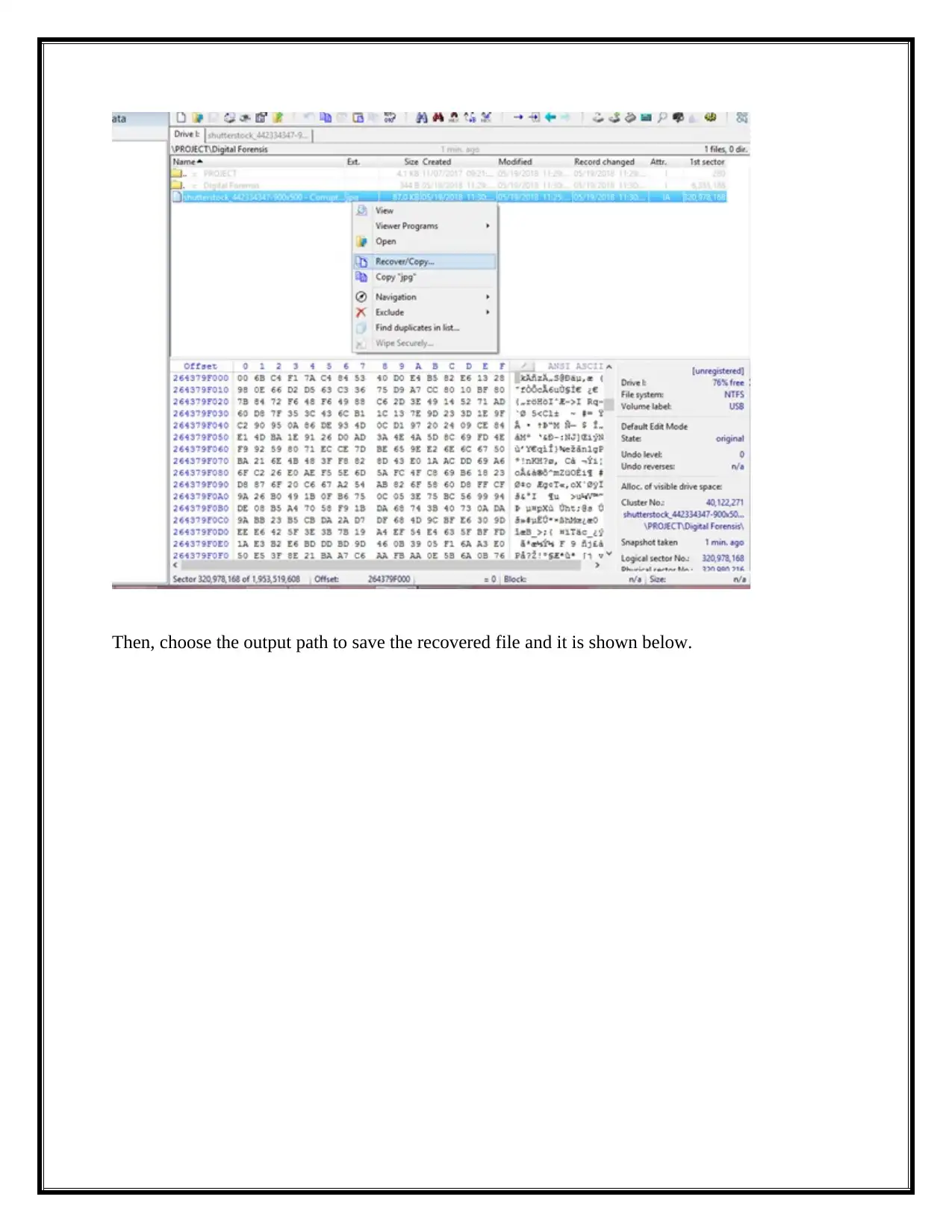
Then, choose the output path to save the recovered file and it is shown below.
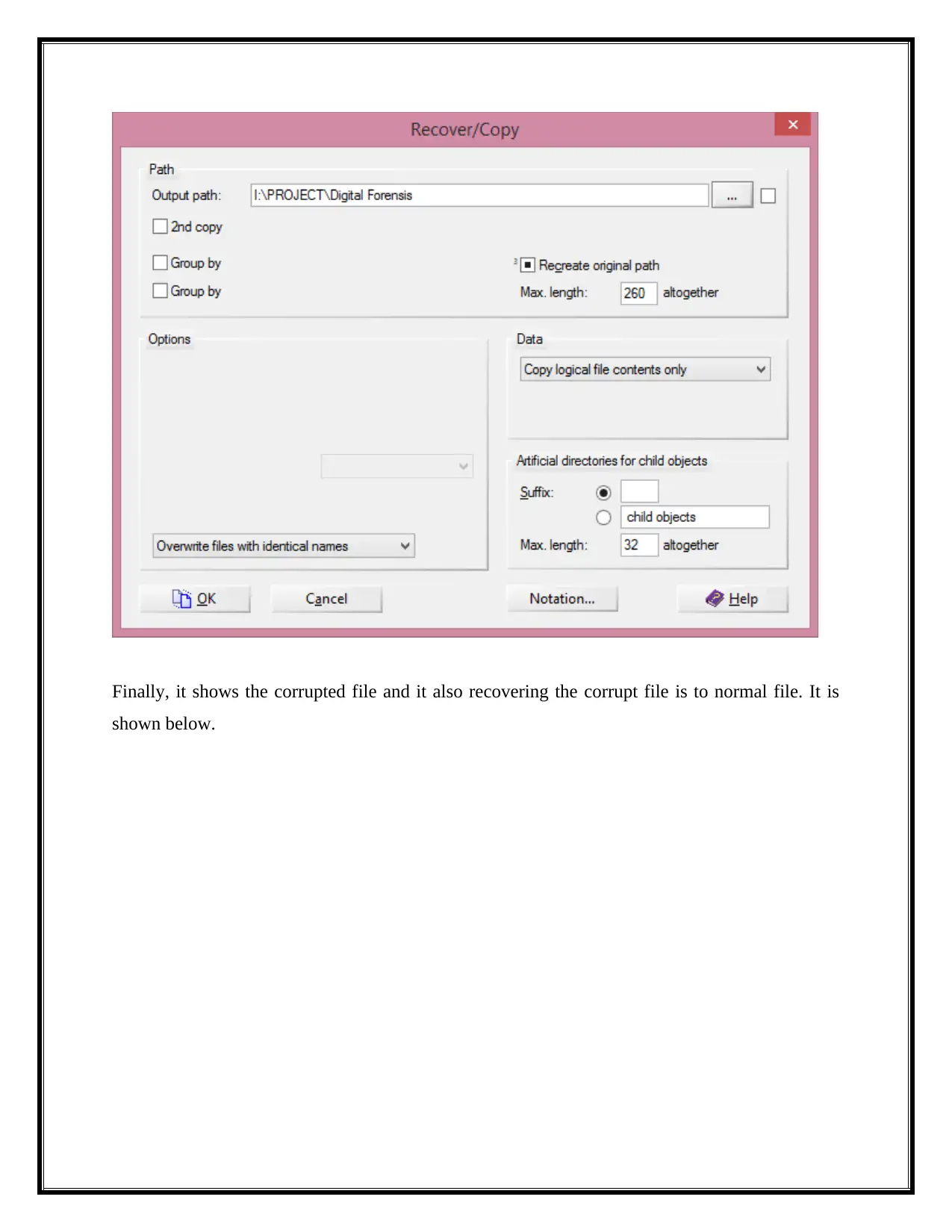
Finally, it shows the corrupted file and it also recovering the corrupt file is to normal file. It is
shown below.
shown below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3.2 Recover the hidden text in Image using Steganography tool
The stenography tool is a most commonly used to recovered the images and their hidden
text (Kolla, 2018). It is easily recovery the hidden text in the images from USB. The EMTS
organization lost the suspicious data and it needs to recover. So, we will use the steganography
The stenography tool is a most commonly used to recovered the images and their hidden
text (Kolla, 2018). It is easily recovery the hidden text in the images from USB. The EMTS
organization lost the suspicious data and it needs to recover. So, we will use the steganography
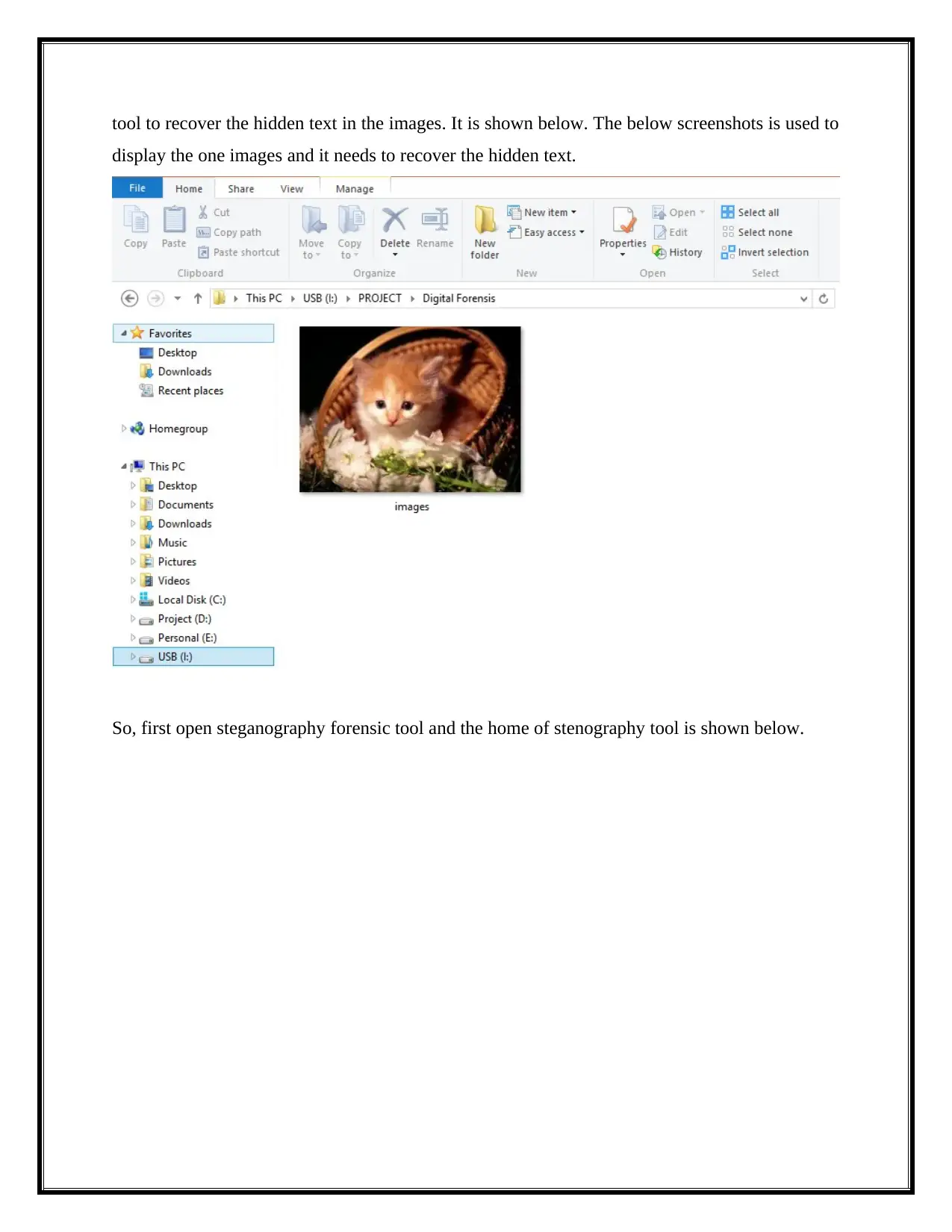
tool to recover the hidden text in the images. It is shown below. The below screenshots is used to
display the one images and it needs to recover the hidden text.
So, first open steganography forensic tool and the home of stenography tool is shown below.
display the one images and it needs to recover the hidden text.
So, first open steganography forensic tool and the home of stenography tool is shown below.
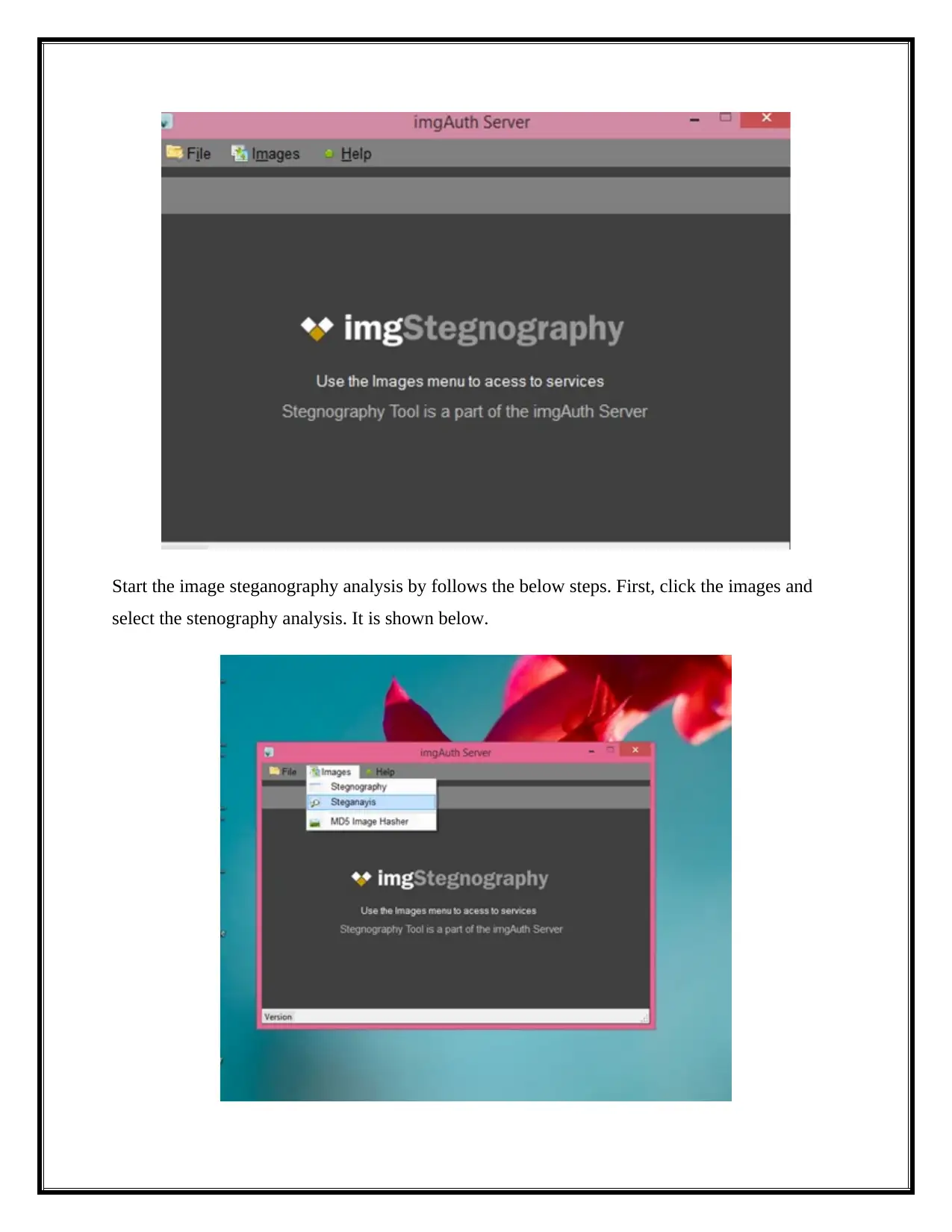
Start the image steganography analysis by follows the below steps. First, click the images and
select the stenography analysis. It is shown below.
select the stenography analysis. It is shown below.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
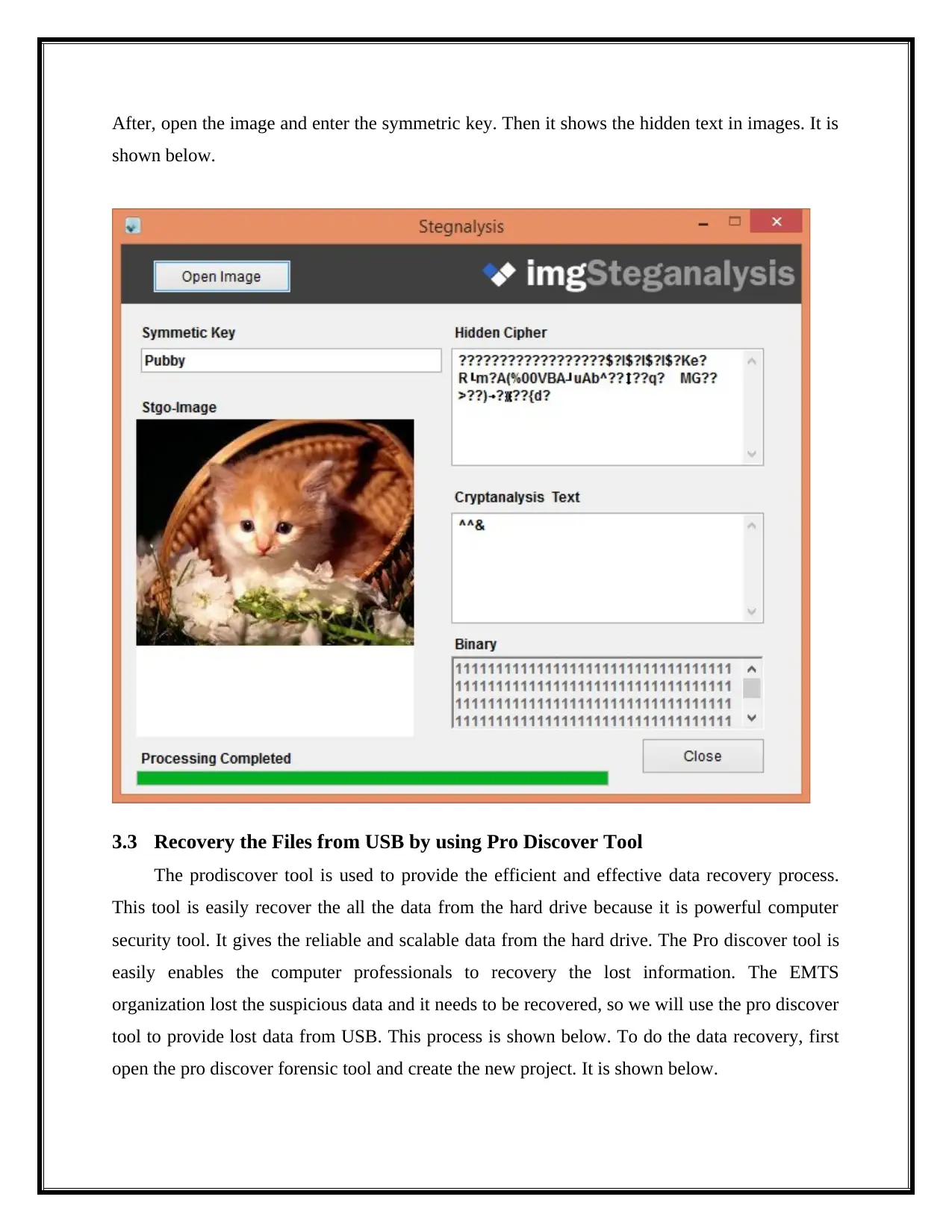
After, open the image and enter the symmetric key. Then it shows the hidden text in images. It is
shown below.
3.3 Recovery the Files from USB by using Pro Discover Tool
The prodiscover tool is used to provide the efficient and effective data recovery process.
This tool is easily recover the all the data from the hard drive because it is powerful computer
security tool. It gives the reliable and scalable data from the hard drive. The Pro discover tool is
easily enables the computer professionals to recovery the lost information. The EMTS
organization lost the suspicious data and it needs to be recovered, so we will use the pro discover
tool to provide lost data from USB. This process is shown below. To do the data recovery, first
open the pro discover forensic tool and create the new project. It is shown below.
shown below.
3.3 Recovery the Files from USB by using Pro Discover Tool
The prodiscover tool is used to provide the efficient and effective data recovery process.
This tool is easily recover the all the data from the hard drive because it is powerful computer
security tool. It gives the reliable and scalable data from the hard drive. The Pro discover tool is
easily enables the computer professionals to recovery the lost information. The EMTS
organization lost the suspicious data and it needs to be recovered, so we will use the pro discover
tool to provide lost data from USB. This process is shown below. To do the data recovery, first
open the pro discover forensic tool and create the new project. It is shown below.
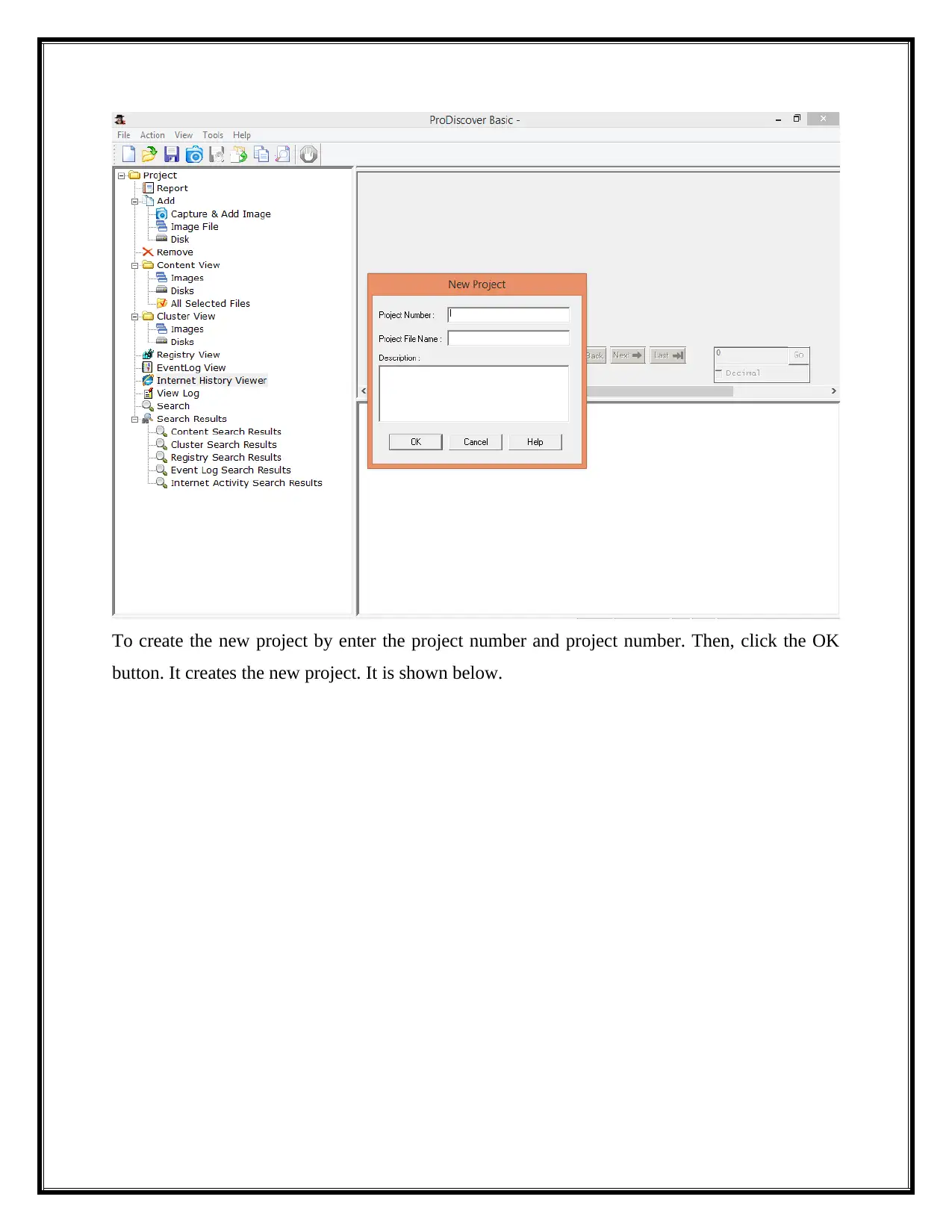
To create the new project by enter the project number and project number. Then, click the OK
button. It creates the new project. It is shown below.
button. It creates the new project. It is shown below.
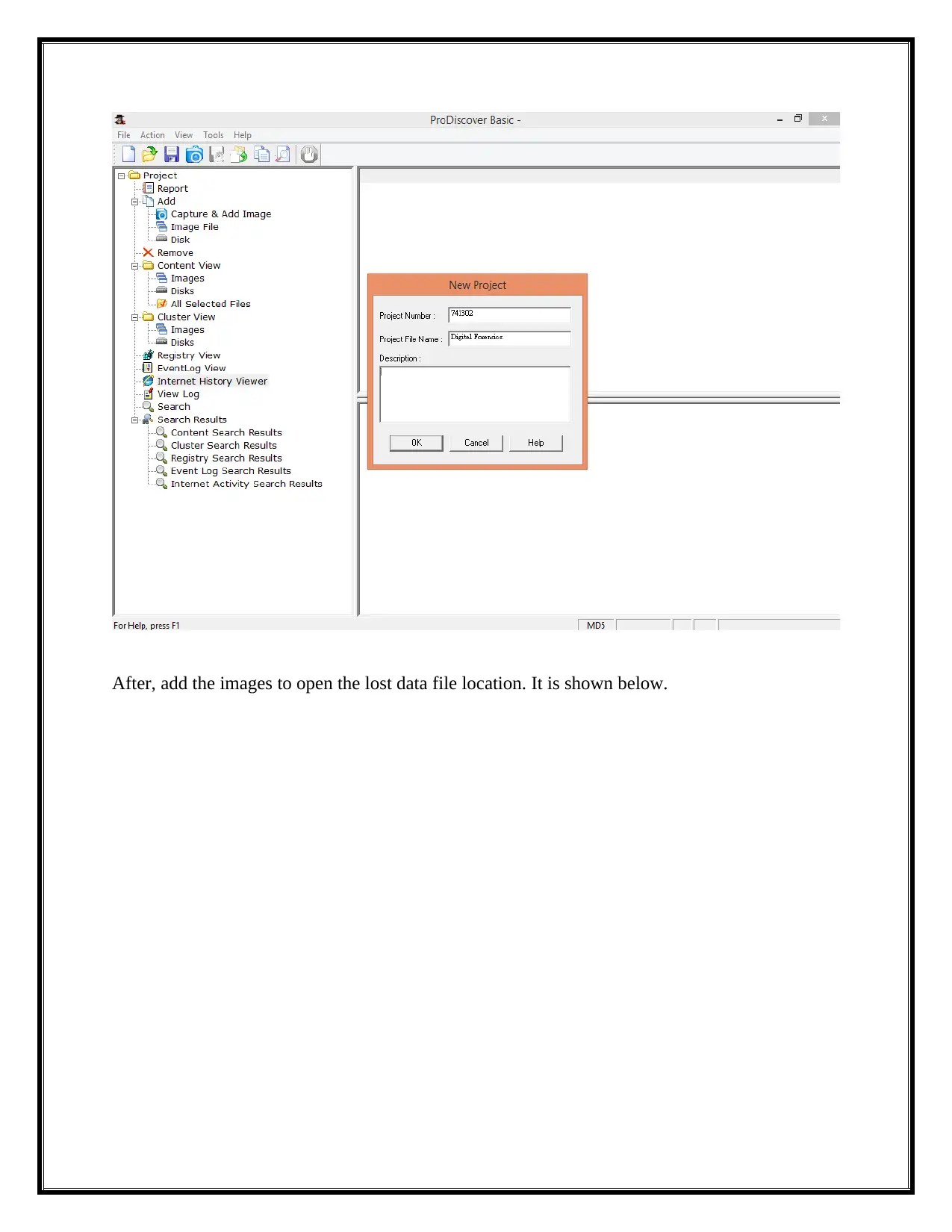
After, add the images to open the lost data file location. It is shown below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
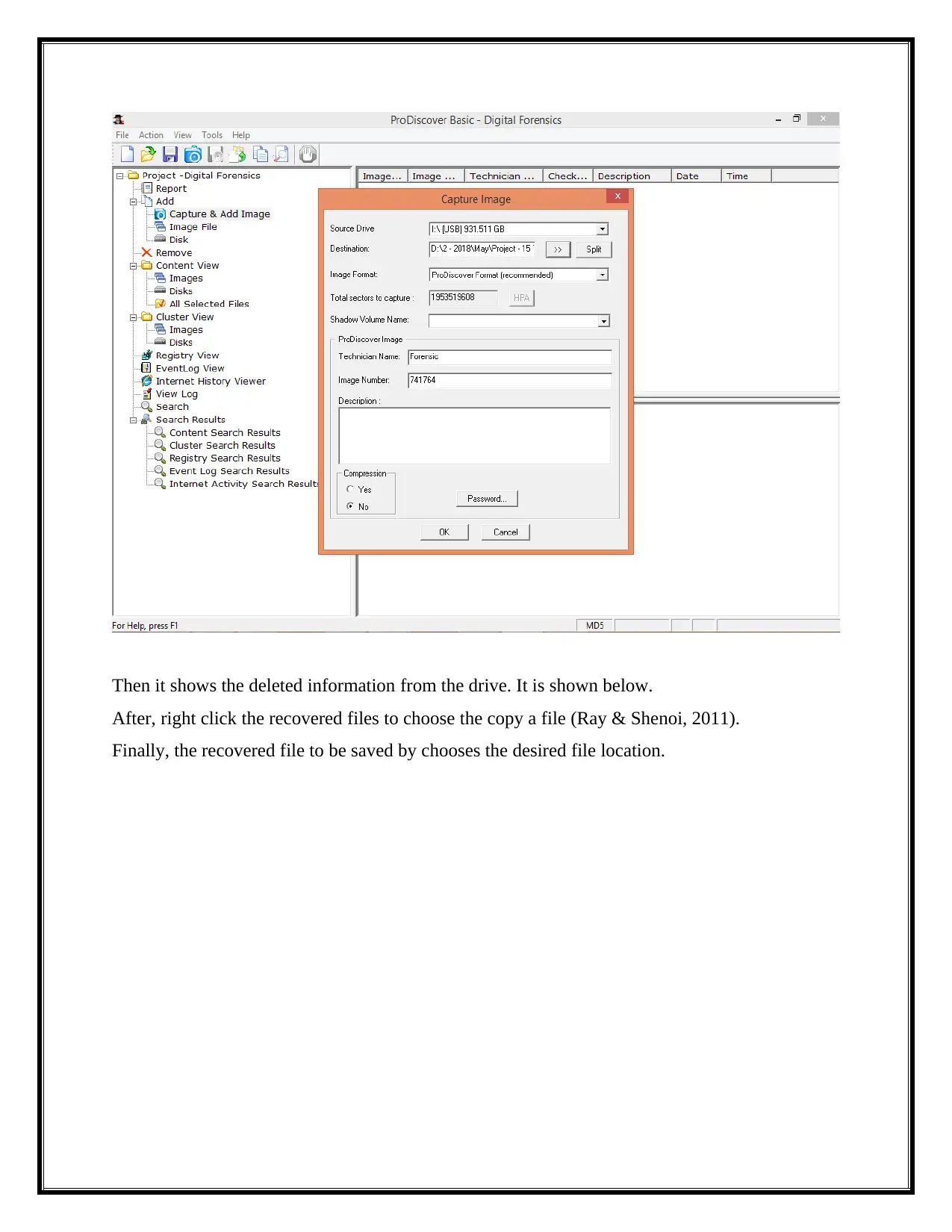
Then it shows the deleted information from the drive. It is shown below.
After, right click the recovered files to choose the copy a file (Ray & Shenoi, 2011).
Finally, the recovered file to be saved by chooses the desired file location.
After, right click the recovered files to choose the copy a file (Ray & Shenoi, 2011).
Finally, the recovered file to be saved by chooses the desired file location.
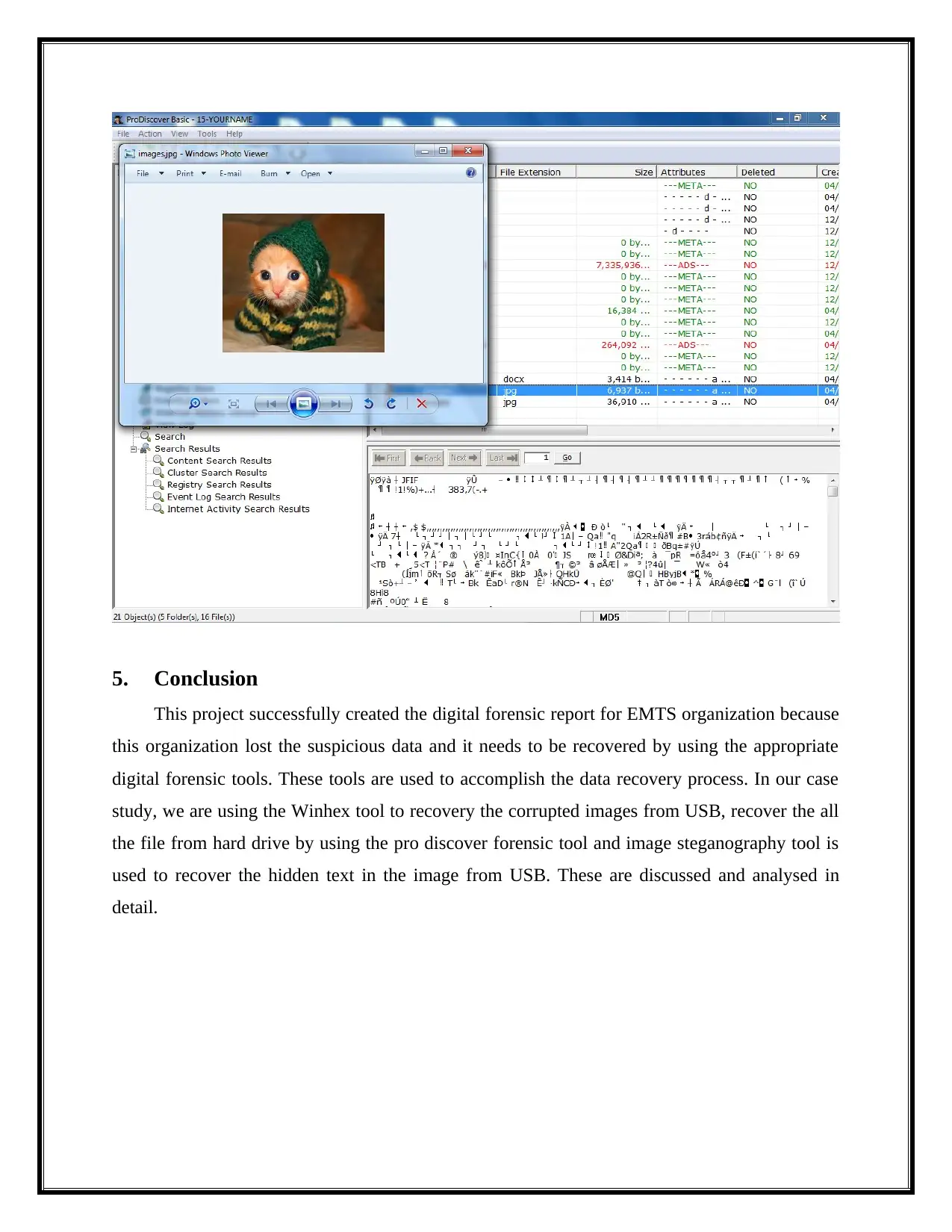
5. Conclusion
This project successfully created the digital forensic report for EMTS organization because
this organization lost the suspicious data and it needs to be recovered by using the appropriate
digital forensic tools. These tools are used to accomplish the data recovery process. In our case
study, we are using the Winhex tool to recovery the corrupted images from USB, recover the all
the file from hard drive by using the pro discover forensic tool and image steganography tool is
used to recover the hidden text in the image from USB. These are discussed and analysed in
detail.
This project successfully created the digital forensic report for EMTS organization because
this organization lost the suspicious data and it needs to be recovered by using the appropriate
digital forensic tools. These tools are used to accomplish the data recovery process. In our case
study, we are using the Winhex tool to recovery the corrupted images from USB, recover the all
the file from hard drive by using the pro discover forensic tool and image steganography tool is
used to recover the hidden text in the image from USB. These are discussed and analysed in
detail.

References
AG, X. (2018). WinHex: Hex Editor & Disk Editor, Computer Forensics & Data Recovery
Software. Retrieved from https://www.x-ways.net/winhex/
Best Tools to Perform Steganography. (2018). Retrieved from
https://resources.infosecinstitute.com/steganography-and-tools-to-perform-steganography/
#gref
Forensic Toolkit. (2018). Retrieved from https://accessdata.com/products-services/forensic-
toolkit-ftk
Gogolin, G. (2013). Digital forensics explained. Boca Raton, FL: CRC Press.
How to use ProDiscover, ProDiscover Forensics,. (2018). Retrieved from
http://hackforlab.com/how-to-use-prodiscover/
Kolla, A. (2018). 10 Best Steganography Tools/Software which are Free to Use. Retrieved from
https://www.geekdashboard.com/best-steganography-tools/
ProDiscover Forensic Data Recovery. (2018). Retrieved from
https://www.networkdefensesolutions.com/index.php/forensics/78-prodiscoverfilerecovery
ProDiscover Forensics - Software - Products. (2018). Retrieved from
https://siliconforensics.com/products/software/prodiscover-forensics.html
Ray, I., & Shenoi, S. (2011). Advances in digital forensics IV. New York: Springer.
Springer-Verlag New York Inc. (2016). Advances in Digital Forensics 9.
AG, X. (2018). WinHex: Hex Editor & Disk Editor, Computer Forensics & Data Recovery
Software. Retrieved from https://www.x-ways.net/winhex/
Best Tools to Perform Steganography. (2018). Retrieved from
https://resources.infosecinstitute.com/steganography-and-tools-to-perform-steganography/
#gref
Forensic Toolkit. (2018). Retrieved from https://accessdata.com/products-services/forensic-
toolkit-ftk
Gogolin, G. (2013). Digital forensics explained. Boca Raton, FL: CRC Press.
How to use ProDiscover, ProDiscover Forensics,. (2018). Retrieved from
http://hackforlab.com/how-to-use-prodiscover/
Kolla, A. (2018). 10 Best Steganography Tools/Software which are Free to Use. Retrieved from
https://www.geekdashboard.com/best-steganography-tools/
ProDiscover Forensic Data Recovery. (2018). Retrieved from
https://www.networkdefensesolutions.com/index.php/forensics/78-prodiscoverfilerecovery
ProDiscover Forensics - Software - Products. (2018). Retrieved from
https://siliconforensics.com/products/software/prodiscover-forensics.html
Ray, I., & Shenoi, S. (2011). Advances in digital forensics IV. New York: Springer.
Springer-Verlag New York Inc. (2016). Advances in Digital Forensics 9.
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.




