Identifying Duplicate Data with Asymmetric Encryption Access Control to the Cloud Data
VerifiedAdded on 2023/06/18
|105
|19954
|58
AI Summary
This report discusses the identification of duplicate data with asymmetric encryption access control to the cloud data. It is submitted in partial fulfillment of the requirement for the degree of Master of Computer Science in Cyber Security at the University of Hertfordshire (UH). The report aims to provide a data storage management system that will identify the duplication of data and access control using asymmetric encryption techniques in cloud service providers (CSPs). The report also discusses the subject, course code, course name, and college/university.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

.
7COM1070 and Cyber Security Masters Project.
Date: 03-09-2021.
IDENTIFICATION OF DUPLICATE DATA WITH
ASYMMETRIC ENCRYPTION ACCESS CONTROL
TO THE CLOUD DATA.
7COM1070 and Cyber Security Masters Project.
Date: 03-09-2021.
IDENTIFICATION OF DUPLICATE DATA WITH
ASYMMETRIC ENCRYPTION ACCESS CONTROL
TO THE CLOUD DATA.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

This report is submitted in partial fulfillment of the requirement for the degree of Master of
Computer Science in Cyber Security at the University of Hertfordshire (UH).
It is my own work except where indicated in the report.
I did not use human participants in my MSc Project.
I hereby give permission for the report to be made available on the university website
provided the source is acknowledged.
2
Computer Science in Cyber Security at the University of Hertfordshire (UH).
It is my own work except where indicated in the report.
I did not use human participants in my MSc Project.
I hereby give permission for the report to be made available on the university website
provided the source is acknowledged.
2

ACKNOWLEDGEMENT
This paper is part of my dissertation. I must thank the specialist for his support in finishing
this proposal report and help me to produce the highest quality results. I have managed the
concept well in a beneficial manner. I am glad that the facilitators who had allowed me to
express this idea to the whole community. I would like to Thanks to Professor Silvia Moros,
for giving me a legitimate direction to characterize my proposal report.
3
This paper is part of my dissertation. I must thank the specialist for his support in finishing
this proposal report and help me to produce the highest quality results. I have managed the
concept well in a beneficial manner. I am glad that the facilitators who had allowed me to
express this idea to the whole community. I would like to Thanks to Professor Silvia Moros,
for giving me a legitimate direction to characterize my proposal report.
3

ABSTRACT
Cloud storage is an effective approach to increase storage requirements for companies and
individuals. Users can encrypt data to ensure security and privacy before downloading to the
cloud. In such cases, the same or other users can encrypt the same data, and it will be rising
the duplicate data in the cloud. In order to provide security and privacy for cloud users, data
is constantly encrypted. However, encrypted data might lead to much waste storage in the
cloud and complex data sharing among authorized users. In terms of encrypted storage and
de-dupe management, we continue to confront problems. Traditional de-duplication solutions
always focus on unique applications where de-duplication is handled by both data owners and
cloud servers. They cannot flexibly address the diverse demands of data owners, depending
on data sensitivity. This paper shows a data storage management system that will Identify the
duplication of data and access control using the asymmetric encryption techniques in cloud
services providers (CSPs). This study will evaluate its performance through safety
assessment, comparison and implementation. The results show their safety efficiency for
practical application.
4
Cloud storage is an effective approach to increase storage requirements for companies and
individuals. Users can encrypt data to ensure security and privacy before downloading to the
cloud. In such cases, the same or other users can encrypt the same data, and it will be rising
the duplicate data in the cloud. In order to provide security and privacy for cloud users, data
is constantly encrypted. However, encrypted data might lead to much waste storage in the
cloud and complex data sharing among authorized users. In terms of encrypted storage and
de-dupe management, we continue to confront problems. Traditional de-duplication solutions
always focus on unique applications where de-duplication is handled by both data owners and
cloud servers. They cannot flexibly address the diverse demands of data owners, depending
on data sensitivity. This paper shows a data storage management system that will Identify the
duplication of data and access control using the asymmetric encryption techniques in cloud
services providers (CSPs). This study will evaluate its performance through safety
assessment, comparison and implementation. The results show their safety efficiency for
practical application.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

TABLE OF CONTENTS
ACKNOWLEDGEMENT...............................................................................................................
ABSTRACT....................................................................................................................................
1. INTRODUCTION...................................................................................................................
1.1 PROJECT OVERVIEW:.......................................................................................................
1.2 INTRODUCTION:................................................................................................................
1.3 OBJECTIVES:................................................................................................................
2.0 LITERATURE REVIEW........................................................................................................
2.1 Background:.........................................................................................................................
2.2 RESEARCH QUESTIONS:................................................................................................
3. METHODOLOGY....................................................................................................................
3.1 EXPERIMENT SCREENSHOTS:......................................................................................
4. DESIGNING.............................................................................................................................
4.1 SYSTEM DESIGN REQUIREMENTS:.............................................................................
4.2 Fundamental Algorithms:....................................................................................................
SOFTWARE AND HARDWARE REQUIREMENT..............................................................
4.5 System Design:....................................................................................................................
4.6 TECHNOLOGIES USED:.................................................................................................
5. ETHICAL, PROFESSIONAL AND LEGAL ISSUES.............................................................
6. RESULTS AND DISCUSSION...............................................................................................
6.1 Access Control Techniques:................................................................................................
6.2 System Architecture:...........................................................................................................
6.3 System Configuration and Required Keys:.........................................................................
6.4 SYSTEM TESTING:...........................................................................................................
6.5 RESULTS LIST:.................................................................................................................
7. CONCLUSION AND FUTURE ENHANCEMENT............................................................
References:....................................................................................................................................
Appendix:......................................................................................................................................
5
ACKNOWLEDGEMENT...............................................................................................................
ABSTRACT....................................................................................................................................
1. INTRODUCTION...................................................................................................................
1.1 PROJECT OVERVIEW:.......................................................................................................
1.2 INTRODUCTION:................................................................................................................
1.3 OBJECTIVES:................................................................................................................
2.0 LITERATURE REVIEW........................................................................................................
2.1 Background:.........................................................................................................................
2.2 RESEARCH QUESTIONS:................................................................................................
3. METHODOLOGY....................................................................................................................
3.1 EXPERIMENT SCREENSHOTS:......................................................................................
4. DESIGNING.............................................................................................................................
4.1 SYSTEM DESIGN REQUIREMENTS:.............................................................................
4.2 Fundamental Algorithms:....................................................................................................
SOFTWARE AND HARDWARE REQUIREMENT..............................................................
4.5 System Design:....................................................................................................................
4.6 TECHNOLOGIES USED:.................................................................................................
5. ETHICAL, PROFESSIONAL AND LEGAL ISSUES.............................................................
6. RESULTS AND DISCUSSION...............................................................................................
6.1 Access Control Techniques:................................................................................................
6.2 System Architecture:...........................................................................................................
6.3 System Configuration and Required Keys:.........................................................................
6.4 SYSTEM TESTING:...........................................................................................................
6.5 RESULTS LIST:.................................................................................................................
7. CONCLUSION AND FUTURE ENHANCEMENT............................................................
References:....................................................................................................................................
Appendix:......................................................................................................................................
5

LIST OF FIGURES Page No’s
Figure 1: System Architecture…………………………………………………17
Figure 2: Use Case Diagram…………………………………………………...23
Figure 3: Sequence Diagram of Data Owner ………………………………….24
Figure 4: Sequence Diagram of AP, KGC, CSP……………………………….24
Figure 5: Collaboration Diagram of Data Owner………………………………25
Figure 6: Collaboration of AP, KGC, CSP…………………………………..26
Figure 7: Data Flow Diagram…………………………………………………..26
6
Figure 1: System Architecture…………………………………………………17
Figure 2: Use Case Diagram…………………………………………………...23
Figure 3: Sequence Diagram of Data Owner ………………………………….24
Figure 4: Sequence Diagram of AP, KGC, CSP……………………………….24
Figure 5: Collaboration Diagram of Data Owner………………………………25
Figure 6: Collaboration of AP, KGC, CSP…………………………………..26
Figure 7: Data Flow Diagram…………………………………………………..26
6

LIST OF TABLES Page No’s
Table 1: Different Approaches between USA and EU.………………64
Table 2: Positive Test Case…………………………………………….67
Table 3: Negative Test Case……………………………………………68
7
Table 1: Different Approaches between USA and EU.………………64
Table 2: Positive Test Case…………………………………………….67
Table 3: Negative Test Case……………………………………………68
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. INTRODUCTION
1.1 PROJECT OVERVIEW:
My Project is about securing the cloud storage by preventing the storage of duplicate or
repeated data uploaded by the data owner/ data user. In this project, we will develop a
prototype where the duplicate data is identified, and it will prevent from further uploading it
to the cloud by checking at various Cloud Service Providers. Here, we use different
techniques of the cryptographic system, namely Asymmetric Encryption Techniques are used
for the data on the cloud.
1.2 INTRODUCTION:
It uses new technologies to provide cloud computing services, enabling internet
reconfiguration and online delivery to clients. It plays an important role in supporting the
storage, processing, and management of data in the Internet of Things (IoT). Some of the
Cloud Service Providers (CSPs) offer large amounts of storage to store and manage IoT data
such as videos, personal information, etc(Yan et al., 2016). These CSPs provide the required
quality of service: scalability, flexibility, fault tolerance and pay-as-you-go. Therefore, cloud
computing has become a promising IoT application and IoT system deployment service
paradigm.
Information about the cloud can be continuously found through cloud specialists.
There are some security issues with these distributed computing. Some other clients can
modify or delete the data stored in the cloud. Cloud clients need to transfer data to other
meetings in certain cases and for certain reasons. These conditions allow customers to have
the option to use cloud management each time they receive and approve the information
about their data protection policy.
The main argument focused upon in this dissertation is existence of copied
information on Cloud. The capacity of the same information multiple times is known as
information duplication (Nahlah Aslam and Swaraj, 2019). Copied information is discarded
and extra space is wasted. There is huge memory in the cloud, but it does not use large
memory, and information processing becomes complicated. Therefore, deduplication was
important for preparing information in the cloud. Deduplication is to reduce the cost of
8
1.1 PROJECT OVERVIEW:
My Project is about securing the cloud storage by preventing the storage of duplicate or
repeated data uploaded by the data owner/ data user. In this project, we will develop a
prototype where the duplicate data is identified, and it will prevent from further uploading it
to the cloud by checking at various Cloud Service Providers. Here, we use different
techniques of the cryptographic system, namely Asymmetric Encryption Techniques are used
for the data on the cloud.
1.2 INTRODUCTION:
It uses new technologies to provide cloud computing services, enabling internet
reconfiguration and online delivery to clients. It plays an important role in supporting the
storage, processing, and management of data in the Internet of Things (IoT). Some of the
Cloud Service Providers (CSPs) offer large amounts of storage to store and manage IoT data
such as videos, personal information, etc(Yan et al., 2016). These CSPs provide the required
quality of service: scalability, flexibility, fault tolerance and pay-as-you-go. Therefore, cloud
computing has become a promising IoT application and IoT system deployment service
paradigm.
Information about the cloud can be continuously found through cloud specialists.
There are some security issues with these distributed computing. Some other clients can
modify or delete the data stored in the cloud. Cloud clients need to transfer data to other
meetings in certain cases and for certain reasons. These conditions allow customers to have
the option to use cloud management each time they receive and approve the information
about their data protection policy.
The main argument focused upon in this dissertation is existence of copied
information on Cloud. The capacity of the same information multiple times is known as
information duplication (Nahlah Aslam and Swaraj, 2019). Copied information is discarded
and extra space is wasted. There is huge memory in the cloud, but it does not use large
memory, and information processing becomes complicated. Therefore, deduplication was
important for preparing information in the cloud. Deduplication is to reduce the cost of
8

capacity. It's about building cloud productivity. Managing encoded deduction data is an
important issue.
The process of identifying and deleting duplicate data is called data deduplication.
There are several solutions for raw data deduplication. However, security allows users to
store their data in a cloud-encrypted way. `In such cases, you need to deduct the encrypted
data. Inferring encrypted data is a difficult problem. Deduplication of adaptive cloud
information by information access control is still an exceptional issue (Yan and et al., 2019).
Information copied to the cloud may be stored in the same or slightly CSP encoded way by
similar or different clients. From a viable standpoint, deduplication of information is strongly
expected to function well by controlling access to information. This is the same information
(whether scrambled or not), and it saves money only once in the cloud locale but differs
depending on the information owner's access or the information owner's strategy (i.e.,
keeping the information unique to the various clients).
Distributed storage is huge, but duplication of information reserves can lead to misuse
of organizational assets, energy use, increased work costs and information organization sins.
CSPs benefit cloud customers and benefit enormously from their financial capacity at a
reduced rate of support that reduces work costs. Cloud information deduplication is
especially important for the volume and organization of vast amounts of information.
Nevertheless, to create a statement, we still need adaptive deduplication of cloud information
from some CSPs. It cannot be widely deployed to maintain both cloud deduplication and
access in an adaptive and stable way.
Existing system:
Data storage is one of the most well-known cloud services. `Cloud users have gained a great
advantage of cloud storage because they can store huge amounts of data anytime, anywhere
without having to upgrade their devices. However, the storage of cloud data provided by
cloud service providers still has various problems (CSP). First, due to different sensitivities,
different data stored in the cloud may require different protection solutions. Cloud-specified
information includes confidentially shared information, group-shared personal information,
and so on. Naturally, important cloud data needs to be protected. A lot of redundant data is
stored on cloud servers without the prior knowledge of users and data providers.
Study Motivation and Contributions:
9
important issue.
The process of identifying and deleting duplicate data is called data deduplication.
There are several solutions for raw data deduplication. However, security allows users to
store their data in a cloud-encrypted way. `In such cases, you need to deduct the encrypted
data. Inferring encrypted data is a difficult problem. Deduplication of adaptive cloud
information by information access control is still an exceptional issue (Yan and et al., 2019).
Information copied to the cloud may be stored in the same or slightly CSP encoded way by
similar or different clients. From a viable standpoint, deduplication of information is strongly
expected to function well by controlling access to information. This is the same information
(whether scrambled or not), and it saves money only once in the cloud locale but differs
depending on the information owner's access or the information owner's strategy (i.e.,
keeping the information unique to the various clients).
Distributed storage is huge, but duplication of information reserves can lead to misuse
of organizational assets, energy use, increased work costs and information organization sins.
CSPs benefit cloud customers and benefit enormously from their financial capacity at a
reduced rate of support that reduces work costs. Cloud information deduplication is
especially important for the volume and organization of vast amounts of information.
Nevertheless, to create a statement, we still need adaptive deduplication of cloud information
from some CSPs. It cannot be widely deployed to maintain both cloud deduplication and
access in an adaptive and stable way.
Existing system:
Data storage is one of the most well-known cloud services. `Cloud users have gained a great
advantage of cloud storage because they can store huge amounts of data anytime, anywhere
without having to upgrade their devices. However, the storage of cloud data provided by
cloud service providers still has various problems (CSP). First, due to different sensitivities,
different data stored in the cloud may require different protection solutions. Cloud-specified
information includes confidentially shared information, group-shared personal information,
and so on. Naturally, important cloud data needs to be protected. A lot of redundant data is
stored on cloud servers without the prior knowledge of users and data providers.
Study Motivation and Contributions:
9

To solve the storage problem in this cloud environment, the damage of cloud storage has
become widespread. Provide an encrypted deduction method. This approach ensures that
shared data is seen as a significant issue in the cloud, where ownership dynamically changes
for efficient and secure cloud storage services, and authorization is only granted with
permission. In each group of owners, the company adopts a group key management method.
Compared with the previous deduplication algorithms used to encrypt data, the proposed
method has the following security and efficiency advantages. Use asymmetric encryption
technology to identify data duplication and access control. According to the information
owner assumption, which can be adapted to different applications, we give you a
heterogeneous information dashboard framework to achieve replication and access control.
Our framework can intelligently enable information sharing between qualified clients,
managed by the information owner or other trusted collectors, or both.
1.3 OBJECTIVES:
The main goal of the project is to identify duplication from an adaptive perspective, and
technology must be combined to control access to information. Therefore, although this
information is stored once in the cloud in an encrypted structure, different customers can
access the equivalent according to the information owner's strategy. We provide a framework
for deduplicating encrypted information stored in the cloud using attribute-based encryption
(ABE) while enhancing the security control of information access. Inspection and execution
show that our framework is protected and efficient.
1. To Identify the duplicate data over the cloud.
2. To save the storage of the cloud from multiple files of the same data being
stored.
3. Providing accurate analysis of the cloud data.
4. Implementing the efficient output algorithm.
5. To implement Asymmetric encryption- based security for encryption and
decryption of data at the cloud end.
10
become widespread. Provide an encrypted deduction method. This approach ensures that
shared data is seen as a significant issue in the cloud, where ownership dynamically changes
for efficient and secure cloud storage services, and authorization is only granted with
permission. In each group of owners, the company adopts a group key management method.
Compared with the previous deduplication algorithms used to encrypt data, the proposed
method has the following security and efficiency advantages. Use asymmetric encryption
technology to identify data duplication and access control. According to the information
owner assumption, which can be adapted to different applications, we give you a
heterogeneous information dashboard framework to achieve replication and access control.
Our framework can intelligently enable information sharing between qualified clients,
managed by the information owner or other trusted collectors, or both.
1.3 OBJECTIVES:
The main goal of the project is to identify duplication from an adaptive perspective, and
technology must be combined to control access to information. Therefore, although this
information is stored once in the cloud in an encrypted structure, different customers can
access the equivalent according to the information owner's strategy. We provide a framework
for deduplicating encrypted information stored in the cloud using attribute-based encryption
(ABE) while enhancing the security control of information access. Inspection and execution
show that our framework is protected and efficient.
1. To Identify the duplicate data over the cloud.
2. To save the storage of the cloud from multiple files of the same data being
stored.
3. Providing accurate analysis of the cloud data.
4. Implementing the efficient output algorithm.
5. To implement Asymmetric encryption- based security for encryption and
decryption of data at the cloud end.
10
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
11

2.0 LITERATURE REVIEW
2.1 Background:
Existing research recommends encryption of information before moving it to cloud to
avoid data protection at CSP, where there are varied advancement coming up in recent time
periods. Admission control on scrambled solicitation of information that should be
unscrambled by approved substances. Preferably, all information should be encoded only
once and route of an approved substance should only be granted once. Normal key update in
any case by changing the trust association will confuse key management. Access control
records are being used to ensure security of information for suspects or semi-trusted
individuals (such as CSPs). The information owner, further sorts information into several sets
with same effective conditions and encodes each set into scrambled message that is simply
circulated to client in a series of Access Control List (ACLs) before sending final information
to the CSP. Therefore, this bundle of information can be easily accessed by ACL clients.
Traditional deduplication strategies work for workers or owners. It is only
occasionally that a half-breed strategy for getting rewards from both methods has been
introduced. This document has proposed a deduplication agreement managed only by the
owner of the information. Management of entry of various information holders relies on
determining metadata that describes eligible clients and has CSPs. Applying public center
encryption in this way is very computationally complex and improves directly with the
number of clients. Hur et al, Recommended other encoded information worker side
deductions, If ownership changes strongly through any subscription, the cloud workers can
oversee the approval of stolen information in any case and ensure an exclusive collection
keyboard layout. This framework avoids information leaks from legitimate but curious
distributed storage users but abandons additional clients.
The innovation of deduplication reduces the copy information frequently used in
distributed storage management, saving only one copy, limiting the need for management
space and transport capacity. Replication is suitable when multiple clients reuse the same
information for distributed storage, but it introduces security and ownership issues. The
evaluation framework allows the individual to have the same information and verify that he
owns the information in a powerful way to the distributed storage worker. Many clients tend
to scramble information for ensuring protection, before it is re-evaluated for distributed
storage. This will randomize encryption and thus limit redundancy. Later, deduplication
framework recommends focus upon aspects that each owner be authorized to have a similar
12
2.1 Background:
Existing research recommends encryption of information before moving it to cloud to
avoid data protection at CSP, where there are varied advancement coming up in recent time
periods. Admission control on scrambled solicitation of information that should be
unscrambled by approved substances. Preferably, all information should be encoded only
once and route of an approved substance should only be granted once. Normal key update in
any case by changing the trust association will confuse key management. Access control
records are being used to ensure security of information for suspects or semi-trusted
individuals (such as CSPs). The information owner, further sorts information into several sets
with same effective conditions and encodes each set into scrambled message that is simply
circulated to client in a series of Access Control List (ACLs) before sending final information
to the CSP. Therefore, this bundle of information can be easily accessed by ACL clients.
Traditional deduplication strategies work for workers or owners. It is only
occasionally that a half-breed strategy for getting rewards from both methods has been
introduced. This document has proposed a deduplication agreement managed only by the
owner of the information. Management of entry of various information holders relies on
determining metadata that describes eligible clients and has CSPs. Applying public center
encryption in this way is very computationally complex and improves directly with the
number of clients. Hur et al, Recommended other encoded information worker side
deductions, If ownership changes strongly through any subscription, the cloud workers can
oversee the approval of stolen information in any case and ensure an exclusive collection
keyboard layout. This framework avoids information leaks from legitimate but curious
distributed storage users but abandons additional clients.
The innovation of deduplication reduces the copy information frequently used in
distributed storage management, saving only one copy, limiting the need for management
space and transport capacity. Replication is suitable when multiple clients reuse the same
information for distributed storage, but it introduces security and ownership issues. The
evaluation framework allows the individual to have the same information and verify that he
owns the information in a powerful way to the distributed storage worker. Many clients tend
to scramble information for ensuring protection, before it is re-evaluated for distributed
storage. This will randomize encryption and thus limit redundancy. Later, deduplication
framework recommends focus upon aspects that each owner be authorized to have a similar
12

key for encoding similar data. Nonetheless, most frameworks experience lack of health
because they do not take into account dynamic changes in the general information ownership
rematch of convenient distributed storage management(Hur et al., 2016a). The author also
further provides integral information, as per another deduplication of the encoded information
in work within article. Cloud workers also often use irregular focus for encoding to oversee
new secure distribution of owners' major meetings, despite dynamic changes evolving among
competencies. This not only denies clients despite their previous ownership but also prevents
information leakage from many employees who are legal and curious in relation to
distributed storage. The proposed approach guarantees working parameters, connected with
integrity of information about conflicting label attacks on business operations within digital
technology perspectives variedly. The proposed framework extends functional advancement,
evolving within recent aspects diversely on system aspects actively further enhancing focus
towards productive innovation. According to good test results, additional computational
overhead is low, but the recommended framework produces only the previous framework.
In this paper Hur et al., (2016), Provides guidance information pertaining to encoded
information, where technology plays significant role in recent time periods. The technology
is proposed as viable and secure distributed storage service which can be considered as the
number one issue in business environment, where ownership changes continuously guarantee
functional advancement. All unowned activities are carried out through collection key
management technology. The proposed framework in this paper by the author provides
contrasting security and proficiency improvements, where existing deduplication further
enables to encode information.
The original dynamic management ensures privacy and confidentiality, authenticity of
discovered data regarding varied working progress of the private business. Interestingly,
previous framework used states gathering signaling technology using two trees, and once
change of information is complete. Data encryption key is updated and specifically provides
efficacy to the real owner, with reliability towards conducting specific functional
engagement.
A semi-trusted cloud worker introduced into framework sometimes handles
significant aspects correlated towards untapped parameters ownership and key management
operations. This means that recommended framework holds high scale work advancement
rapidly, further building specific functional advancement diversely.
The proposed scheme also provides security for deployment of PoW by setting up a
re-encryption framework with additional collection keys for bunch of unique belongings.
Thus, while the encryption key (document hash evaluation) is made public to the PoW
13
because they do not take into account dynamic changes in the general information ownership
rematch of convenient distributed storage management(Hur et al., 2016a). The author also
further provides integral information, as per another deduplication of the encoded information
in work within article. Cloud workers also often use irregular focus for encoding to oversee
new secure distribution of owners' major meetings, despite dynamic changes evolving among
competencies. This not only denies clients despite their previous ownership but also prevents
information leakage from many employees who are legal and curious in relation to
distributed storage. The proposed approach guarantees working parameters, connected with
integrity of information about conflicting label attacks on business operations within digital
technology perspectives variedly. The proposed framework extends functional advancement,
evolving within recent aspects diversely on system aspects actively further enhancing focus
towards productive innovation. According to good test results, additional computational
overhead is low, but the recommended framework produces only the previous framework.
In this paper Hur et al., (2016), Provides guidance information pertaining to encoded
information, where technology plays significant role in recent time periods. The technology
is proposed as viable and secure distributed storage service which can be considered as the
number one issue in business environment, where ownership changes continuously guarantee
functional advancement. All unowned activities are carried out through collection key
management technology. The proposed framework in this paper by the author provides
contrasting security and proficiency improvements, where existing deduplication further
enables to encode information.
The original dynamic management ensures privacy and confidentiality, authenticity of
discovered data regarding varied working progress of the private business. Interestingly,
previous framework used states gathering signaling technology using two trees, and once
change of information is complete. Data encryption key is updated and specifically provides
efficacy to the real owner, with reliability towards conducting specific functional
engagement.
A semi-trusted cloud worker introduced into framework sometimes handles
significant aspects correlated towards untapped parameters ownership and key management
operations. This means that recommended framework holds high scale work advancement
rapidly, further building specific functional advancement diversely.
The proposed scheme also provides security for deployment of PoW by setting up a
re-encryption framework with additional collection keys for bunch of unique belongings.
Thus, while the encryption key (document hash evaluation) is made public to the PoW
13
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

installation, security of the inventory information is still protected from intruders. Exclusion
of duplication aspects, within information in encoded information is still allowed, and
honesty of the information is It is maintained against poison attacks.
In this article (Nahlah Aslam and Swaraj, 2019), cloud-based approach further leads
to deduplication and enhance deduplication of vast amounts of information. The framework
is equally shuffled and re-encoded. Innovation attempts to textual information documents at
the section level. A token is generated for each pass in the record before sending it to the
cloud. At the point in time, another transfer request is made, the framework will ensure that
these tools have access to the copy record. If the current document has a re-encryption
calculation in the cloud, the framework will not be sent. You can then deduct it from the
framework.
Data generation is one of the most trendy storage advances, and a business or buyer
can get significant sums for the cost of space, cost of moving information, information
stocking and speed of transmission. This is a great resource for cloud providers, within
significant aspects for attending towards untapped new performance goals dynamically. This
is because less equipment is needed even if storage opportunities are less. If duplication is
possible, case can be secured by utilizing the extra space conveniently. Likewise, the amount
of savings is also reduced. This suggests that equipment and reinforcement media will in fact
be reduced on the chance that storage volumes are shrinking. In the event of a disaster, you
get more cash for your facility and your organization's expense, and less information is sent
to your organization. The allowance for the cloud is shown to bring significant cost
investment funds as it can cut the use of reinforcement stockpiles by up to 90% - 95% and the
general record framework by up to 68%. These reductions benefit cloud buyers and cloud
organizations.
The deduplication cycle works at a sizable level in programming by simply removing
the copy information and storing the information's anomalous initiation event. Any excess
duplicates of indistinguishable program information are erased and a point or reference is set
on the first duplicate instead. The deduplication cycle is easy for both end clients and
applications. With further intrusion, deduplication programs typically use cryptographic
blurring factors to create a single identity for the data (Nahlah Aslam and Swaraj, 2019). The
document does not have enough capacity because a whole new duplicate of the record is
stored regardless, where practical engagement are further competently advanced up.
Therefore, this check attempts to subtract the record content at the block level.
In the paper Yan et al., (2016), Cloud information is usually maintained in a
scrambled structure to ensure cloud confidentiality and client protection. Copied information
14
of duplication aspects, within information in encoded information is still allowed, and
honesty of the information is It is maintained against poison attacks.
In this article (Nahlah Aslam and Swaraj, 2019), cloud-based approach further leads
to deduplication and enhance deduplication of vast amounts of information. The framework
is equally shuffled and re-encoded. Innovation attempts to textual information documents at
the section level. A token is generated for each pass in the record before sending it to the
cloud. At the point in time, another transfer request is made, the framework will ensure that
these tools have access to the copy record. If the current document has a re-encryption
calculation in the cloud, the framework will not be sent. You can then deduct it from the
framework.
Data generation is one of the most trendy storage advances, and a business or buyer
can get significant sums for the cost of space, cost of moving information, information
stocking and speed of transmission. This is a great resource for cloud providers, within
significant aspects for attending towards untapped new performance goals dynamically. This
is because less equipment is needed even if storage opportunities are less. If duplication is
possible, case can be secured by utilizing the extra space conveniently. Likewise, the amount
of savings is also reduced. This suggests that equipment and reinforcement media will in fact
be reduced on the chance that storage volumes are shrinking. In the event of a disaster, you
get more cash for your facility and your organization's expense, and less information is sent
to your organization. The allowance for the cloud is shown to bring significant cost
investment funds as it can cut the use of reinforcement stockpiles by up to 90% - 95% and the
general record framework by up to 68%. These reductions benefit cloud buyers and cloud
organizations.
The deduplication cycle works at a sizable level in programming by simply removing
the copy information and storing the information's anomalous initiation event. Any excess
duplicates of indistinguishable program information are erased and a point or reference is set
on the first duplicate instead. The deduplication cycle is easy for both end clients and
applications. With further intrusion, deduplication programs typically use cryptographic
blurring factors to create a single identity for the data (Nahlah Aslam and Swaraj, 2019). The
document does not have enough capacity because a whole new duplicate of the record is
stored regardless, where practical engagement are further competently advanced up.
Therefore, this check attempts to subtract the record content at the block level.
In the paper Yan et al., (2016), Cloud information is usually maintained in a
scrambled structure to ensure cloud confidentiality and client protection. Copied information
14

can be stored in the cloud, even if it is encoded under other encryption strategies, which
inherently slows down the usage of capacity, especially for huge pieces of information. In
any case, most of them lack security and are not adaptable to enable safety checks of access
to information. This article provides a framework for deduplicating scrambled information
stored in the cloud using ABE (Quality Based Encryption) as well as for greater control over
access to secure information. The results show that the technology for common sense use that
can be considered is productive, attractive and versatile.
This system considers your ID to true nature of the authorization of encoded information
stored in the SPS and oversees how to remove duplicates from other authorized information
clients. Our methodology applies to the conditions under which information owners store and
utilize information and to screen and track the location of information. The owner or owner
of each piece of information, the CSP client u, is used to create a user-defined secret
characteristic key, as well as the mysterious Sku key used for PKu-related decoding
processing. Holds the public PKu key. The owner or owner of the information uses the SKU
to create a unique public key PKIDu ID characteristic key for other clients. The CSP client U
uses PKIDu to scramble a randomly generated DEKu balance key to encode user information
to control access to information and deduplication. Proper PKIDu scrambled mysterious
quality keys are rebuilt by qualified information managers and provided by the owner. Of
information. What comes next will be integrated. All conveyors have specific mystery
characteristic keys that can be used to avoid alignment. SKID (u, u') is a mysterious attribute
key given to modified information medium u'by u'. In the middle, the client utilizes key pairs
pku and sku, such as PKC (Public Key Cryptography) mark creation and verification. The
keys (PKu, SKu), (pku, sku) are connected with the client's exceptional mysterious
personality. This limit is the basis for verifying new client identity. When the PKu and pku
frameworks were created, they were verified as Cert (PKu) Cert (pku) by an authorized
outsider, and can be verified by the CSP and all CSP clients.
In this article Tribhuwan, Bhuyar and Pirzade, (2010), Innovation allows IT
executives to leverage a common foundation or serving customers faster, better, and
financially without having to reconfigure or add to the basic framework. can do. Given the
benefits of distributed computing, the overall appeal is not unexpected. However, there are
some stresses with this new technology. It mainly acquires information stored in the cloud.
This exam consistently focuses on the security of cloud information reserves, which is an
important part of management quality for longer scale goodwill.
From the perspective of information security, which was a fundamental part of
continuous management and quality, distributed computing inevitably offers new and
15
inherently slows down the usage of capacity, especially for huge pieces of information. In
any case, most of them lack security and are not adaptable to enable safety checks of access
to information. This article provides a framework for deduplicating scrambled information
stored in the cloud using ABE (Quality Based Encryption) as well as for greater control over
access to secure information. The results show that the technology for common sense use that
can be considered is productive, attractive and versatile.
This system considers your ID to true nature of the authorization of encoded information
stored in the SPS and oversees how to remove duplicates from other authorized information
clients. Our methodology applies to the conditions under which information owners store and
utilize information and to screen and track the location of information. The owner or owner
of each piece of information, the CSP client u, is used to create a user-defined secret
characteristic key, as well as the mysterious Sku key used for PKu-related decoding
processing. Holds the public PKu key. The owner or owner of the information uses the SKU
to create a unique public key PKIDu ID characteristic key for other clients. The CSP client U
uses PKIDu to scramble a randomly generated DEKu balance key to encode user information
to control access to information and deduplication. Proper PKIDu scrambled mysterious
quality keys are rebuilt by qualified information managers and provided by the owner. Of
information. What comes next will be integrated. All conveyors have specific mystery
characteristic keys that can be used to avoid alignment. SKID (u, u') is a mysterious attribute
key given to modified information medium u'by u'. In the middle, the client utilizes key pairs
pku and sku, such as PKC (Public Key Cryptography) mark creation and verification. The
keys (PKu, SKu), (pku, sku) are connected with the client's exceptional mysterious
personality. This limit is the basis for verifying new client identity. When the PKu and pku
frameworks were created, they were verified as Cert (PKu) Cert (pku) by an authorized
outsider, and can be verified by the CSP and all CSP clients.
In this article Tribhuwan, Bhuyar and Pirzade, (2010), Innovation allows IT
executives to leverage a common foundation or serving customers faster, better, and
financially without having to reconfigure or add to the basic framework. can do. Given the
benefits of distributed computing, the overall appeal is not unexpected. However, there are
some stresses with this new technology. It mainly acquires information stored in the cloud.
This exam consistently focuses on the security of cloud information reserves, which is an
important part of management quality for longer scale goodwill.
From the perspective of information security, which was a fundamental part of
continuous management and quality, distributed computing inevitably offers new and
15

complex security opportunities. Best of all, the standard natives of information security
insurance are not easy to implement in that clients oversee the loss of information about
cloud computing. The correct cloud information stockpile confirmation, should be done in
effective format. Checking the accuracy of information stores in the cloud is increasingly
dangerous, as different types of information are stored in the cloud for all clients and require
continuous long-term information security. In this work, we certainly propose a powerful and
versatile framework for distributing unique information support to ensure the accuracy of
client cloud information.
We rely on eradication code tuning to ensure redundancy and information reliability
using document deployment planning. Unlike the prevalence of replication-based documents
in general, this technology basically communicates and reduces storage overhead(Tribhuwan,
Bhuyar and Pirzade, 2010). Using isomorphic tokens, our framework implements information
blunder areas through capacity-accuracy protection and distributed checking of deleted coded
information. Whenever damage is discovered during stockpiling checks, it is possible to
frequently guarantee information errors, such as evidence of misbehavior identification.
In the traditional cryptographic basic data security cloud computing cannot be
adopted directly through user data loss control. Therefore, it is important to check accurate
stockpile information in the cloud without clear information about the whole information.
Also, the cloud simply does not have a warehouse of information for various gatherings.
Clients can be included to continually update information stored in the cloud, such as cancels,
changes, modifications, and sorts. A single customer information is stored in several actual
submissions that are repeatedly submitted in response to requests that can be honestly
dangerous.
Clients are storing their information in the cloud information stockpiling framework, and
there is currently no information on nearby facilities. This involves ensuring that information
documents generated by scattered cloud workers are accurate and usable. The main part of
this part identifies the underlying mechanisms of coding hypotheses that are important for the
cycle of records among the cloud workers of the framework(Tribhuwan, Bhuyar and Pirzade,
2010). Then at that point, it gives you a quasi-equivalent token. Similarly, there is a public
way to create cumbersome answer rules to check the correctness of the stockpile and find
faults. Finally, the means of recovery of documents and negligence are drawn according to
the Extermination Amendment Code.
In this paper, Zhou et al., (2011), Data access control outsourced to legitimate cloud
workers has gained a lot of consideration, especially when the information owner is not
suited to the massive amount of information documents that can be re-encrypted and
16
insurance are not easy to implement in that clients oversee the loss of information about
cloud computing. The correct cloud information stockpile confirmation, should be done in
effective format. Checking the accuracy of information stores in the cloud is increasingly
dangerous, as different types of information are stored in the cloud for all clients and require
continuous long-term information security. In this work, we certainly propose a powerful and
versatile framework for distributing unique information support to ensure the accuracy of
client cloud information.
We rely on eradication code tuning to ensure redundancy and information reliability
using document deployment planning. Unlike the prevalence of replication-based documents
in general, this technology basically communicates and reduces storage overhead(Tribhuwan,
Bhuyar and Pirzade, 2010). Using isomorphic tokens, our framework implements information
blunder areas through capacity-accuracy protection and distributed checking of deleted coded
information. Whenever damage is discovered during stockpiling checks, it is possible to
frequently guarantee information errors, such as evidence of misbehavior identification.
In the traditional cryptographic basic data security cloud computing cannot be
adopted directly through user data loss control. Therefore, it is important to check accurate
stockpile information in the cloud without clear information about the whole information.
Also, the cloud simply does not have a warehouse of information for various gatherings.
Clients can be included to continually update information stored in the cloud, such as cancels,
changes, modifications, and sorts. A single customer information is stored in several actual
submissions that are repeatedly submitted in response to requests that can be honestly
dangerous.
Clients are storing their information in the cloud information stockpiling framework, and
there is currently no information on nearby facilities. This involves ensuring that information
documents generated by scattered cloud workers are accurate and usable. The main part of
this part identifies the underlying mechanisms of coding hypotheses that are important for the
cycle of records among the cloud workers of the framework(Tribhuwan, Bhuyar and Pirzade,
2010). Then at that point, it gives you a quasi-equivalent token. Similarly, there is a public
way to create cumbersome answer rules to check the correctness of the stockpile and find
faults. Finally, the means of recovery of documents and negligence are drawn according to
the Extermination Amendment Code.
In this paper, Zhou et al., (2011), Data access control outsourced to legitimate cloud
workers has gained a lot of consideration, especially when the information owner is not
suited to the massive amount of information documents that can be re-encrypted and
16
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

retransmitted. In this article, we propose a strategy for realizing inpatient adaptive
sophisticated control on re-evaluated records in light of client's protection and security in the
cloud environment. Deploy by setting keys on clients that explicitly depend on a different set
of attributes, and externally review tests that cover access restrictions, such as client data
from cloud workers. In part, our proposed plan is based on our determination that each client
is likely to be associated with a variety of huge characteristics for information recording and
entry strategies in a true application environment. As a result, access strategies can be
established at various quality settings, as well as with justifiable Arty equations that reflect
the range of information records that a client type can obtain. Each entry strategy can be
passed to a particularly consistent definition, which can be very well implemented for fine-
grained control.
In order to access the records of information stored in the cloud, the user downloads a
favorable one from the cloud provider and decodes it using his own descramble key. The
supervisors of the framework should not generally be online until the entry structure, which
operates on the client or by the denial, is changed in an appropriate way. Because cloud
workers require varying capacities and computational power, what is created by record re-
scramble is converted to cloud workers without running out of content or data in customer
information documents along with a number of clients and client ID records. Worker re-
encryption equipment running on cloud workers re-encodes data file operations without the
need for clients to re-encode the descrambling key and restore re-encoding information
records.
Fan et al have introduced a cross-approach to eliminate duplication of information.
You can deduplication text and passphrases. There is lack of functional engagement as per
scaled up working efficacy diversely, which needs competitive exploration on wider
phenomenon’s. In such situations, it cannot be used to fully trust the owner of the CSP
information. Li et al. Explicitly managed derivation issues for allowed information. Unlike
the average deduplication framework, despite the cross-type cloud design information itself,
the differentiated client benefits are further seen as a copy test. The focus of the efforts
mentioned above was to solve some of the questions in our exam.
2.2 RESEARCH QUESTIONS:
Some of the main research questions that this dissertation will answer are as follows:
In what ways duplicate data over the cloud can be identified?
Which output algorithm is faster that can be applied to reduce data duplication?
17
sophisticated control on re-evaluated records in light of client's protection and security in the
cloud environment. Deploy by setting keys on clients that explicitly depend on a different set
of attributes, and externally review tests that cover access restrictions, such as client data
from cloud workers. In part, our proposed plan is based on our determination that each client
is likely to be associated with a variety of huge characteristics for information recording and
entry strategies in a true application environment. As a result, access strategies can be
established at various quality settings, as well as with justifiable Arty equations that reflect
the range of information records that a client type can obtain. Each entry strategy can be
passed to a particularly consistent definition, which can be very well implemented for fine-
grained control.
In order to access the records of information stored in the cloud, the user downloads a
favorable one from the cloud provider and decodes it using his own descramble key. The
supervisors of the framework should not generally be online until the entry structure, which
operates on the client or by the denial, is changed in an appropriate way. Because cloud
workers require varying capacities and computational power, what is created by record re-
scramble is converted to cloud workers without running out of content or data in customer
information documents along with a number of clients and client ID records. Worker re-
encryption equipment running on cloud workers re-encodes data file operations without the
need for clients to re-encode the descrambling key and restore re-encoding information
records.
Fan et al have introduced a cross-approach to eliminate duplication of information.
You can deduplication text and passphrases. There is lack of functional engagement as per
scaled up working efficacy diversely, which needs competitive exploration on wider
phenomenon’s. In such situations, it cannot be used to fully trust the owner of the CSP
information. Li et al. Explicitly managed derivation issues for allowed information. Unlike
the average deduplication framework, despite the cross-type cloud design information itself,
the differentiated client benefits are further seen as a copy test. The focus of the efforts
mentioned above was to solve some of the questions in our exam.
2.2 RESEARCH QUESTIONS:
Some of the main research questions that this dissertation will answer are as follows:
In what ways duplicate data over the cloud can be identified?
Which output algorithm is faster that can be applied to reduce data duplication?
17

How Asymmetric encryption- based security can be used for encryption and decryption of
data at the cloud end?
FEASIBILITY STUDY:
Overview:
Robust and reliable organizations rely 100% on the PC cloud. LAN (Local Area Network)
and Internet availability are all stable and require the use of business-level network hardware.
Propose excess ISP. We propose an iterative ISP. It is necessary to set the transmission
capacity and inactivity of the Internet circuits that are important to meet the requirements of
the application.
Internet:
Internet latency is the amount of time a packet travels from its origin to its destination
and returns. The idle state is estimated to be milliseconds or one-hundredth of a second. For a
valuable presentation, cloud applications need a stable dormancy of less than 60ms(CNS,
2011). Second-class web connections such as links and DSLs have high latency in the range
of 30-500m. Advanced circuits such as fiber optics and T1 providing a stable idle state almost
in the 2040ms region.
Transit marks Internet connections are generally fast, low hibernation, but data
transfer and idleness over the Internet which are not guaranteed. We can guarantee the data
transmission capacity and inactivity of the personal information line only. If no web
connectivity is provided, iterative web circuits are suggested to help office employees stay
dynamic. It is recommended that the two circuits of fiber optics or reinforced T1 maintain
acceptable quality while applying critical uptime which lowers efficiency. When cost matters,
you can sponsor a good connection with a poor connection such as a link or DSL. Cloud
application execution is reduced if the required connectivity is lost.
Private data:
Personal data connections typically provide a dedicated connection between both sites, with
backup speed and service level agreement (SLA) latency. Personal data is typically provided
with Layer 2 or Layer 3 connectivity and is reliable via methods for sound, video, and remote
workspaces, for example for the highest level of quality of service (QoS). Specifies a label
for the transfer in progress.
The line of personal information in terms of quality and cost is beyond the Internet,
which further signifies functional engagement diversly. The circuit of personal information
that requires cloud applications is important. Most server farms and numerous public fogs
18
data at the cloud end?
FEASIBILITY STUDY:
Overview:
Robust and reliable organizations rely 100% on the PC cloud. LAN (Local Area Network)
and Internet availability are all stable and require the use of business-level network hardware.
Propose excess ISP. We propose an iterative ISP. It is necessary to set the transmission
capacity and inactivity of the Internet circuits that are important to meet the requirements of
the application.
Internet:
Internet latency is the amount of time a packet travels from its origin to its destination
and returns. The idle state is estimated to be milliseconds or one-hundredth of a second. For a
valuable presentation, cloud applications need a stable dormancy of less than 60ms(CNS,
2011). Second-class web connections such as links and DSLs have high latency in the range
of 30-500m. Advanced circuits such as fiber optics and T1 providing a stable idle state almost
in the 2040ms region.
Transit marks Internet connections are generally fast, low hibernation, but data
transfer and idleness over the Internet which are not guaranteed. We can guarantee the data
transmission capacity and inactivity of the personal information line only. If no web
connectivity is provided, iterative web circuits are suggested to help office employees stay
dynamic. It is recommended that the two circuits of fiber optics or reinforced T1 maintain
acceptable quality while applying critical uptime which lowers efficiency. When cost matters,
you can sponsor a good connection with a poor connection such as a link or DSL. Cloud
application execution is reduced if the required connectivity is lost.
Private data:
Personal data connections typically provide a dedicated connection between both sites, with
backup speed and service level agreement (SLA) latency. Personal data is typically provided
with Layer 2 or Layer 3 connectivity and is reliable via methods for sound, video, and remote
workspaces, for example for the highest level of quality of service (QoS). Specifies a label
for the transfer in progress.
The line of personal information in terms of quality and cost is beyond the Internet,
which further signifies functional engagement diversly. The circuit of personal information
that requires cloud applications is important. Most server farms and numerous public fogs
18

provide a combination of personal information. Work with a communications expert to
ensure that your personal information is essential to the correct development of your WAN
connection.
RESEARCH QUESTIONS:
How to develop asymmetric encryption in the access control of cloud data?
The development of the appropriation of ABE is an information proprietor who
possibly encodes a key when various qualified information managers are given
admittance rights. Since the gave unscrambling keys to the information holders are
modified, they can't work together. Fine grain access control is promptly done by
ABE, which improves our framework further. To accomplish information encryption
effectiveness, we can either use CP-ABE to improve on key administration or KP-
ABE.
How to Identify duplicate data over the cloud?
We use the Hybrid Cloud approach to prevent improper duplication and ensure
anonymity in the cloud. It's anything but a mix of private and public nodes. Half breed
distributed storage unites the upsides of adaptability, dependability, fast sending, and
potential investment funds out in the open distributed storage with full security and
protection for the executives.
How to provide secure and efficient performance over the cloud?
Cloud cryptography is a procedure to defend the cloud framework. Cloud specialist
co-ops like Azure employ cryptography to give framework-level security data layers
and safe admittance to anyone who needs shared cloud administrations. This
encryption layer depends on the Quantum Direct Key plan, a cutting-edge balanced
encryption strategy. Public and private keys coupled to a specific ID are gotten by
clients. Cryptographic distributed computing may likewise diminish blockage in the
organization.
How the de-dupe process will be effective at the Cloud Service Providers end?
Data set examinations things (ordinarily documents or hinders) and wipes out things
that as of now exist inside a bunch of information. Information de-duplication the
cycle of duplication dispenses with non-one-of-a-kind squares. Basically, four stages
are engaged with the cycle:
Separation of the info data into "pieces" or chunks.
For each chunk of information, compute hash esteem.
19
ensure that your personal information is essential to the correct development of your WAN
connection.
RESEARCH QUESTIONS:
How to develop asymmetric encryption in the access control of cloud data?
The development of the appropriation of ABE is an information proprietor who
possibly encodes a key when various qualified information managers are given
admittance rights. Since the gave unscrambling keys to the information holders are
modified, they can't work together. Fine grain access control is promptly done by
ABE, which improves our framework further. To accomplish information encryption
effectiveness, we can either use CP-ABE to improve on key administration or KP-
ABE.
How to Identify duplicate data over the cloud?
We use the Hybrid Cloud approach to prevent improper duplication and ensure
anonymity in the cloud. It's anything but a mix of private and public nodes. Half breed
distributed storage unites the upsides of adaptability, dependability, fast sending, and
potential investment funds out in the open distributed storage with full security and
protection for the executives.
How to provide secure and efficient performance over the cloud?
Cloud cryptography is a procedure to defend the cloud framework. Cloud specialist
co-ops like Azure employ cryptography to give framework-level security data layers
and safe admittance to anyone who needs shared cloud administrations. This
encryption layer depends on the Quantum Direct Key plan, a cutting-edge balanced
encryption strategy. Public and private keys coupled to a specific ID are gotten by
clients. Cryptographic distributed computing may likewise diminish blockage in the
organization.
How the de-dupe process will be effective at the Cloud Service Providers end?
Data set examinations things (ordinarily documents or hinders) and wipes out things
that as of now exist inside a bunch of information. Information de-duplication the
cycle of duplication dispenses with non-one-of-a-kind squares. Basically, four stages
are engaged with the cycle:
Separation of the info data into "pieces" or chunks.
For each chunk of information, compute hash esteem.
19
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

To decide if another chunk of similar information has effectively been put away
utilize these qualities.
Supplant a reference to the item in the data set with the copy information.
How does the encryption and decryption of data take place at the cloud end?
Encryption and decryption keys are identical in this way and are best suited to closed
systems and individual users. These keys are used for communication protection. This
algorithm is also known as the secret key and is generally used for the encryption of
bulk data. Hardware implements this simply and rapidly and faster than the
asymmetrical technique. However, even if it is not for them, anybody with the key are
able to pertain significant information for data handling.
2.3 Proposed system:
In a variety of scenarios, consider saving cloud storage between multiple CSPs to manage
encrypted deduplication inventory and maintain data confidentiality and privacy. In line with
the expectations of data owners, it uses asymmetric encryption technology from cloud service
providers (CSPs) to verify data redundancy and provides a data storage management system
for access control. Our system can flexibly promote the exchange of data between data
owners and entitled users to be managed by other trust relationships or both. The
performance of the proposed system is justified by security analysis, comparison with current
work, and performance evaluation based on implementation. The proposed system will
identify similar files and file content during the signing into the cloud and identifies the file
with their ID, Thus it will save a lot of space in the cloud preventing it from data anonymity
and reliability to the data.
Advantages:
Delaying and access control flexible cloud data.
Our system is safe, sophisticated and efficient.
Can save a lot of storage in the cloud environment.
20
utilize these qualities.
Supplant a reference to the item in the data set with the copy information.
How does the encryption and decryption of data take place at the cloud end?
Encryption and decryption keys are identical in this way and are best suited to closed
systems and individual users. These keys are used for communication protection. This
algorithm is also known as the secret key and is generally used for the encryption of
bulk data. Hardware implements this simply and rapidly and faster than the
asymmetrical technique. However, even if it is not for them, anybody with the key are
able to pertain significant information for data handling.
2.3 Proposed system:
In a variety of scenarios, consider saving cloud storage between multiple CSPs to manage
encrypted deduplication inventory and maintain data confidentiality and privacy. In line with
the expectations of data owners, it uses asymmetric encryption technology from cloud service
providers (CSPs) to verify data redundancy and provides a data storage management system
for access control. Our system can flexibly promote the exchange of data between data
owners and entitled users to be managed by other trust relationships or both. The
performance of the proposed system is justified by security analysis, comparison with current
work, and performance evaluation based on implementation. The proposed system will
identify similar files and file content during the signing into the cloud and identifies the file
with their ID, Thus it will save a lot of space in the cloud preventing it from data anonymity
and reliability to the data.
Advantages:
Delaying and access control flexible cloud data.
Our system is safe, sophisticated and efficient.
Can save a lot of storage in the cloud environment.
20
3. METHODOLOGY
3.1 EXPERIMENT SCREENSHOTS:
The following are the screenshots shows the Execution of the Project.
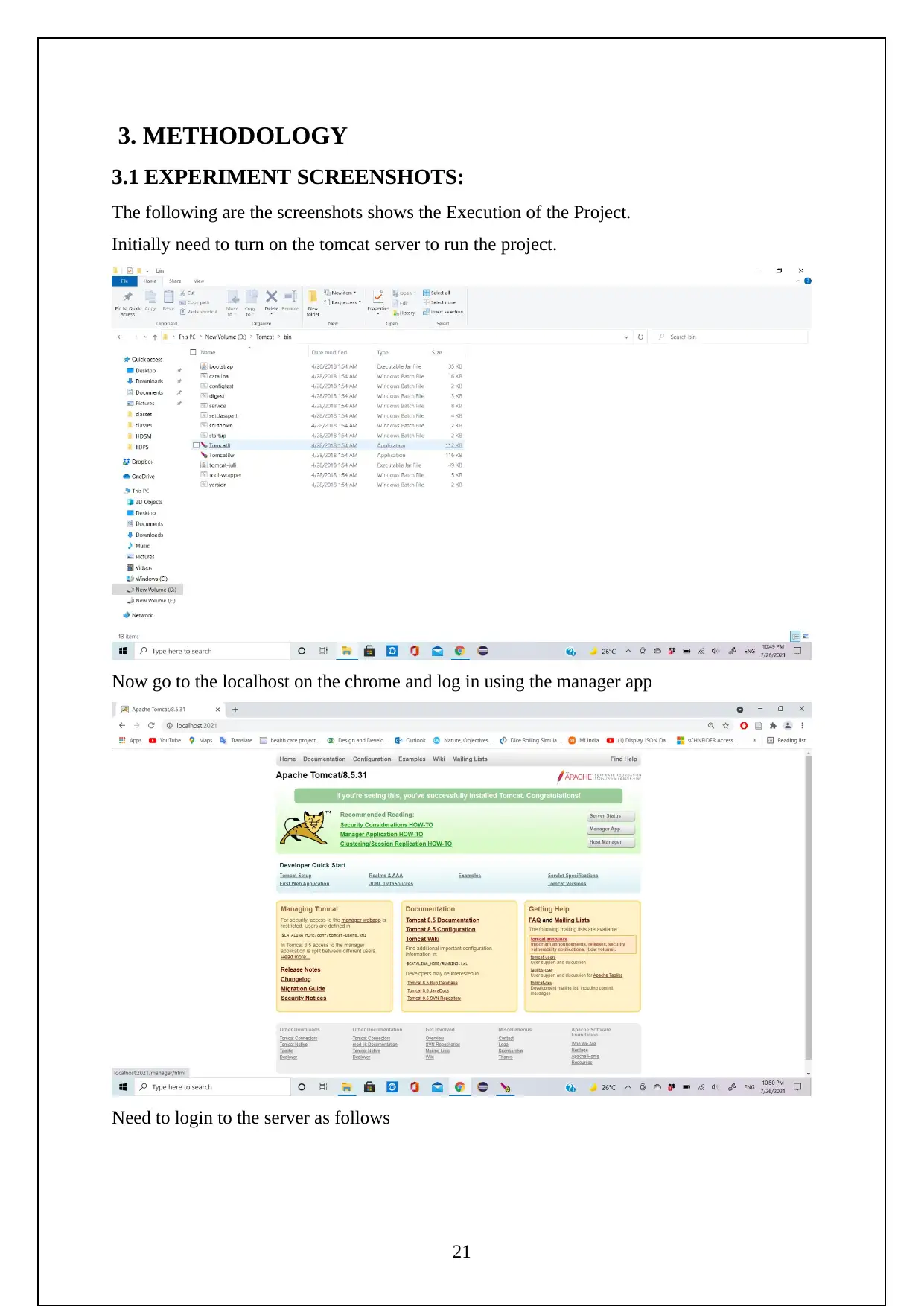
Initially need to turn on the tomcat server to run the project.
Now go to the localhost on the chrome and log in using the manager app
Need to login to the server as follows
21
3.1 EXPERIMENT SCREENSHOTS:
The following are the screenshots shows the Execution of the Project.
Initially need to turn on the tomcat server to run the project.
Now go to the localhost on the chrome and log in using the manager app
Need to login to the server as follows
21
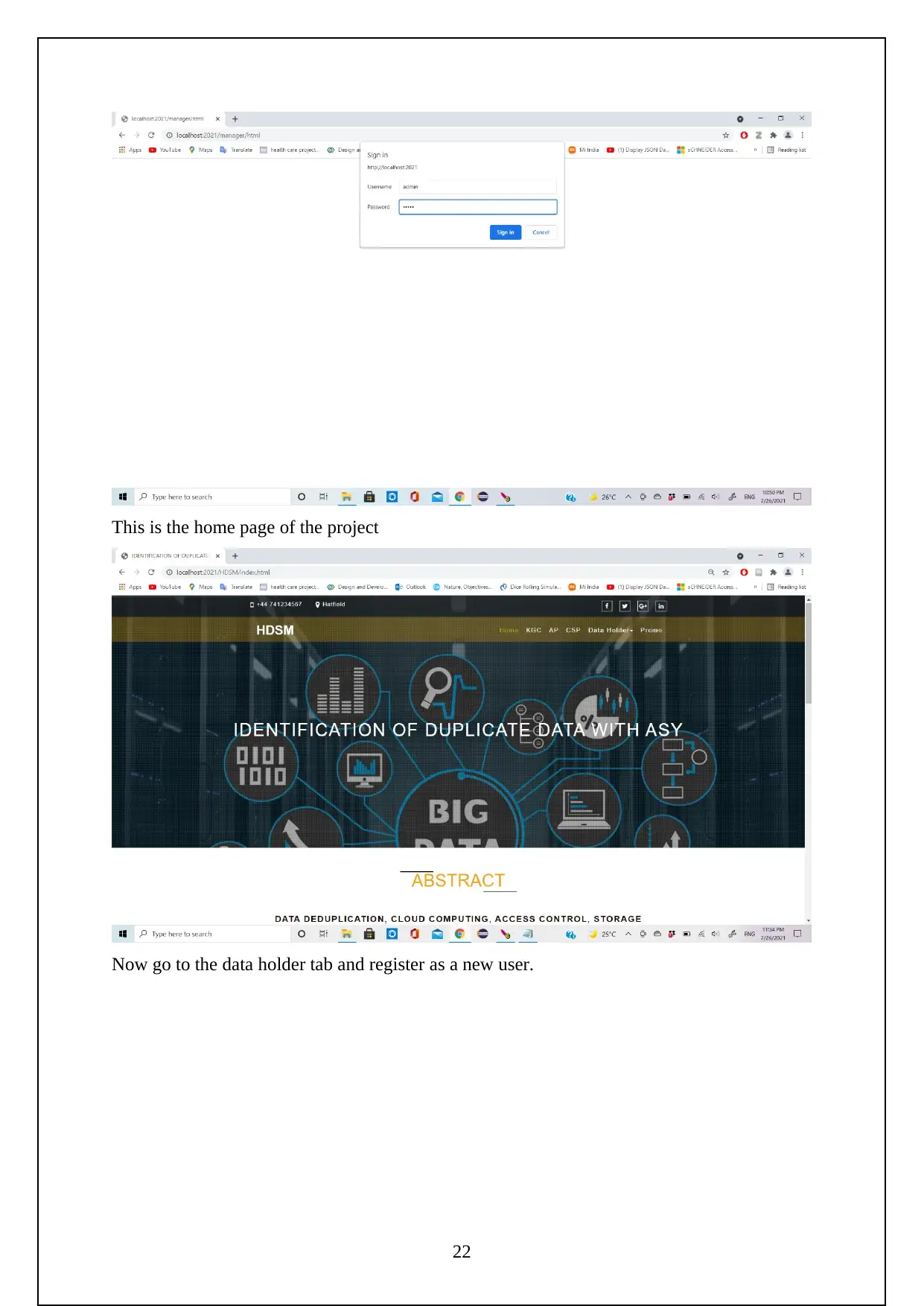
This is the home page of the project
Now go to the data holder tab and register as a new user.
22
Now go to the data holder tab and register as a new user.
22
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
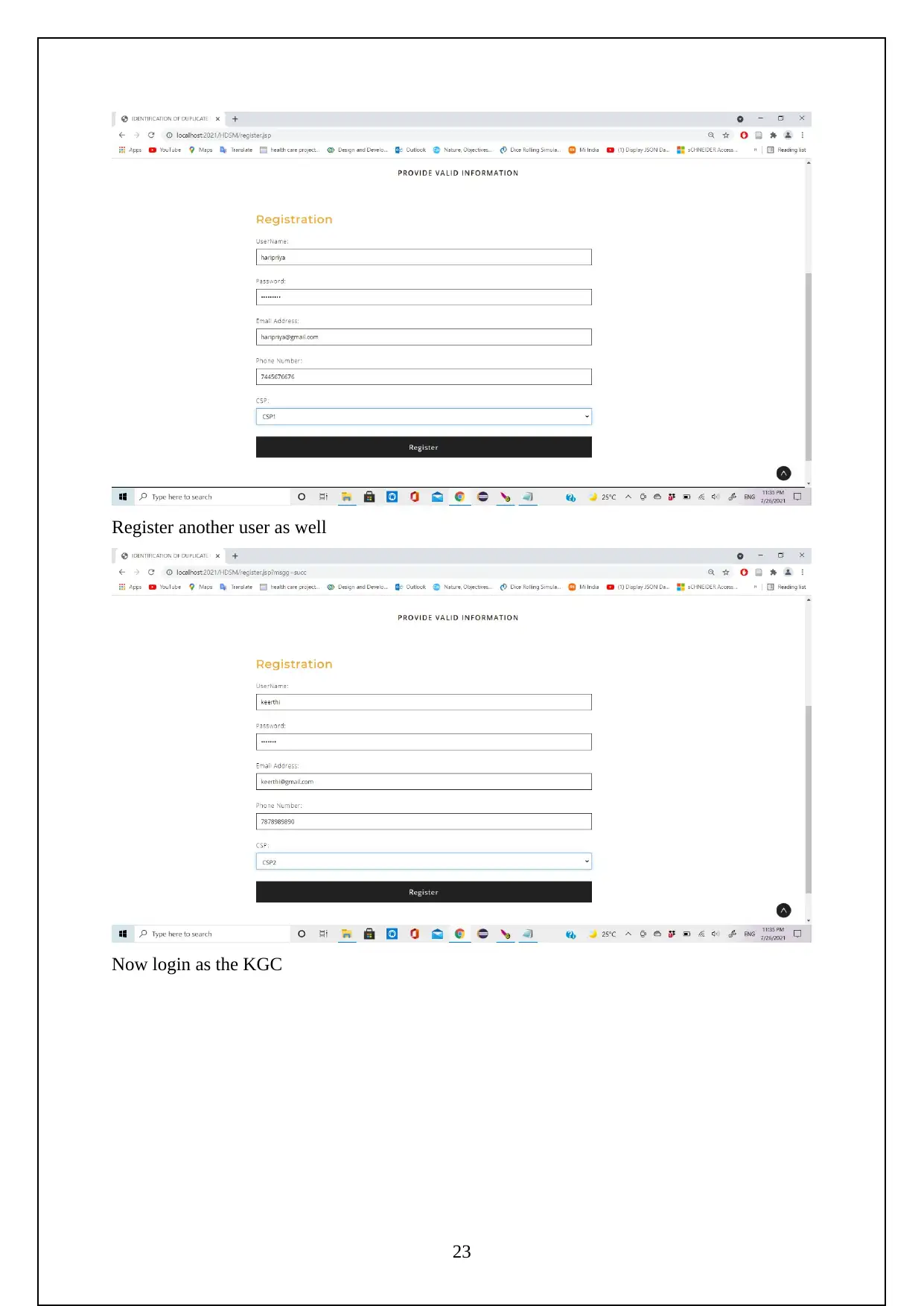
Register another user as well
Now login as the KGC
23
Now login as the KGC
23
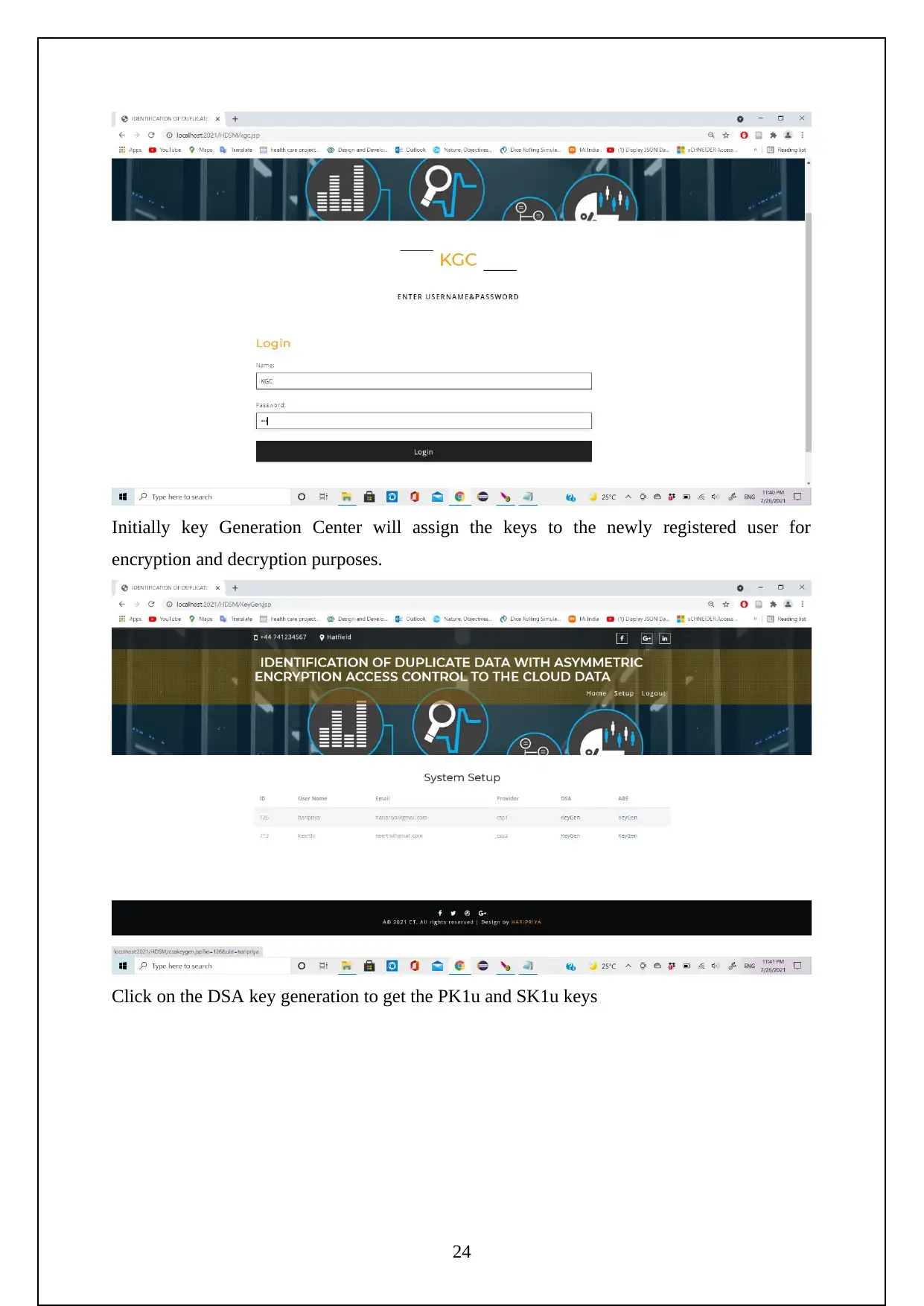
Initially key Generation Center will assign the keys to the newly registered user for
encryption and decryption purposes.
Click on the DSA key generation to get the PK1u and SK1u keys
24
encryption and decryption purposes.
Click on the DSA key generation to get the PK1u and SK1u keys
24
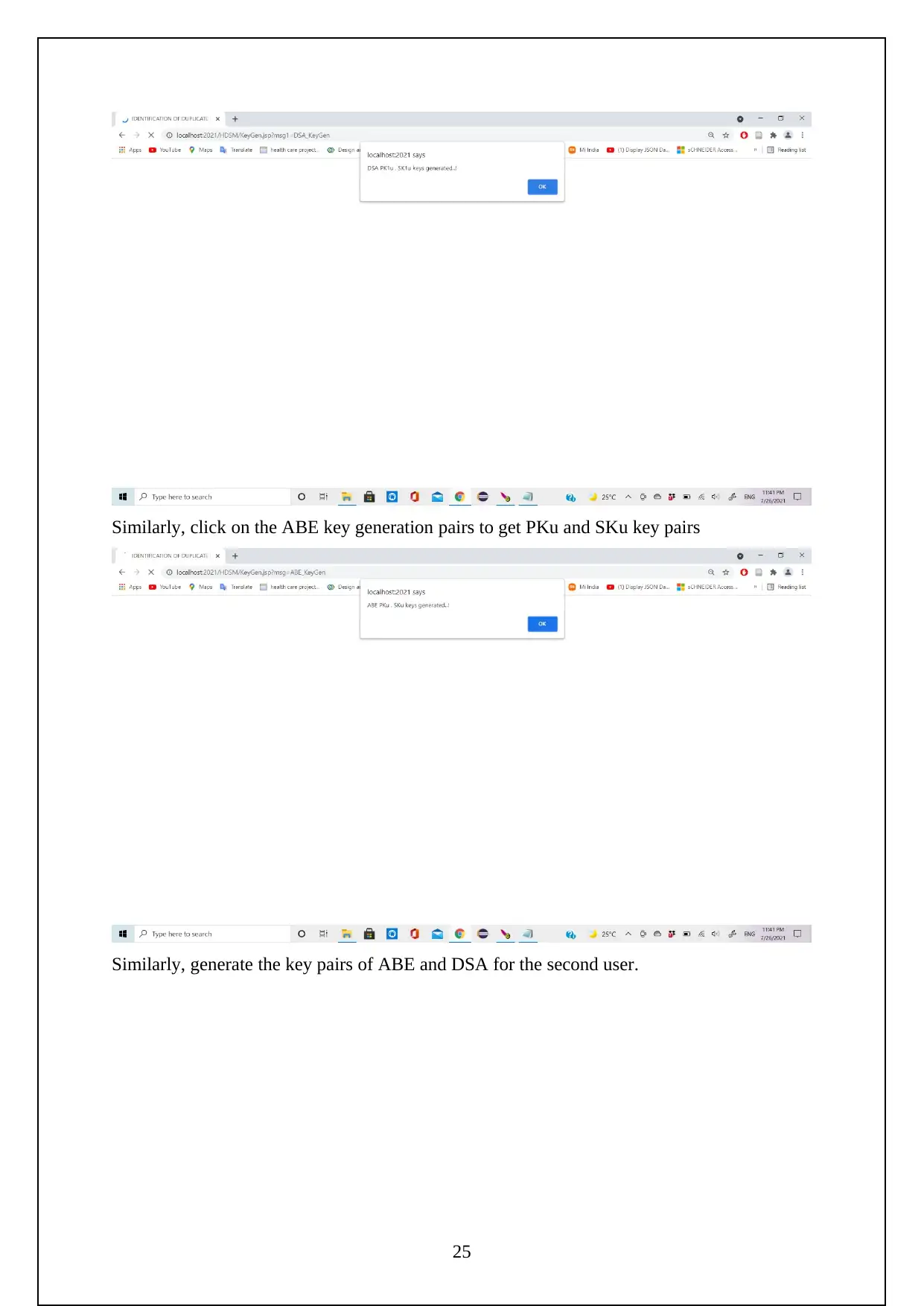
Similarly, click on the ABE key generation pairs to get PKu and SKu key pairs
Similarly, generate the key pairs of ABE and DSA for the second user.
25
Similarly, generate the key pairs of ABE and DSA for the second user.
25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
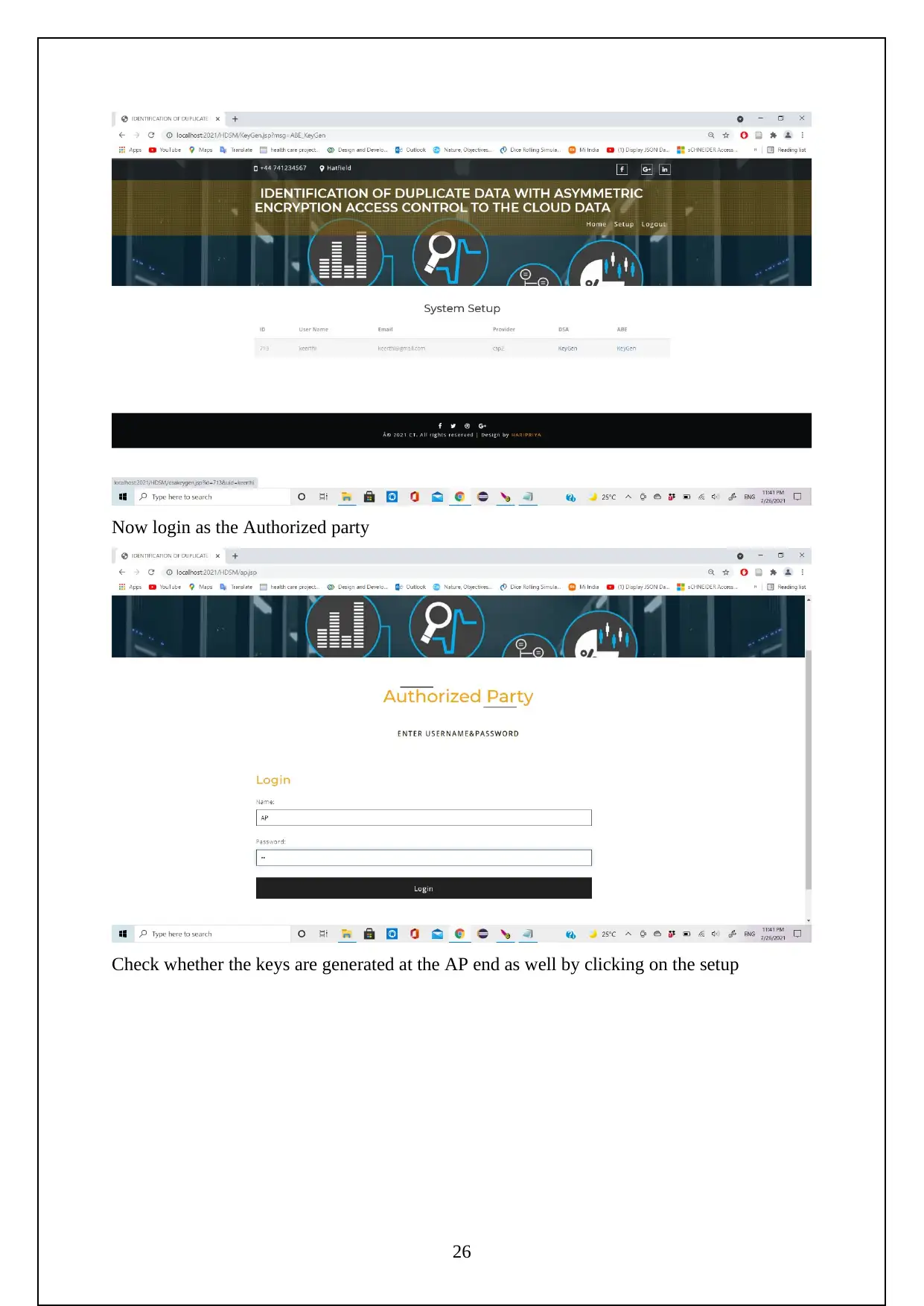
Now login as the Authorized party
Check whether the keys are generated at the AP end as well by clicking on the setup
26
Check whether the keys are generated at the AP end as well by clicking on the setup
26
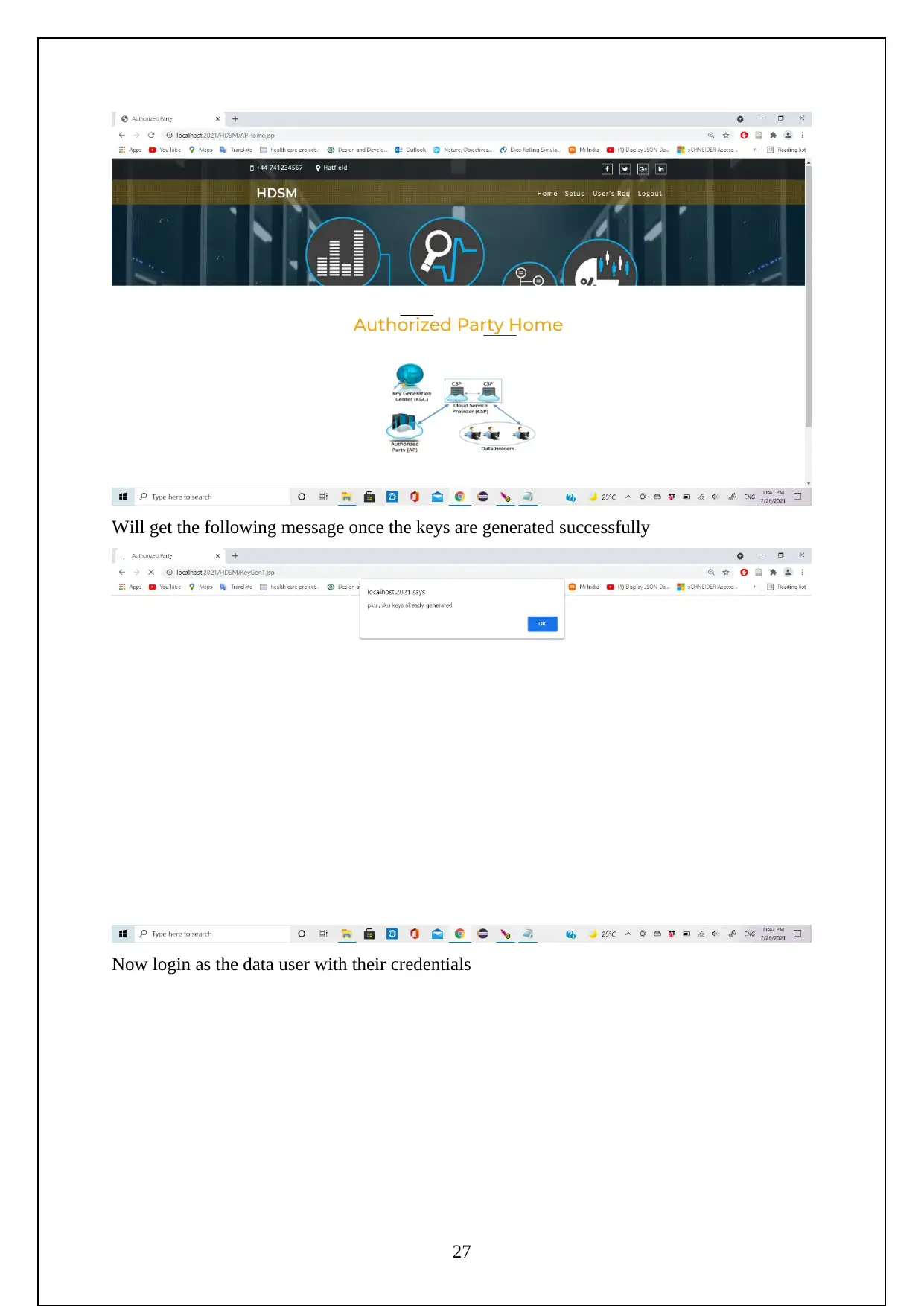
Will get the following message once the keys are generated successfully
Now login as the data user with their credentials
27
Now login as the data user with their credentials
27
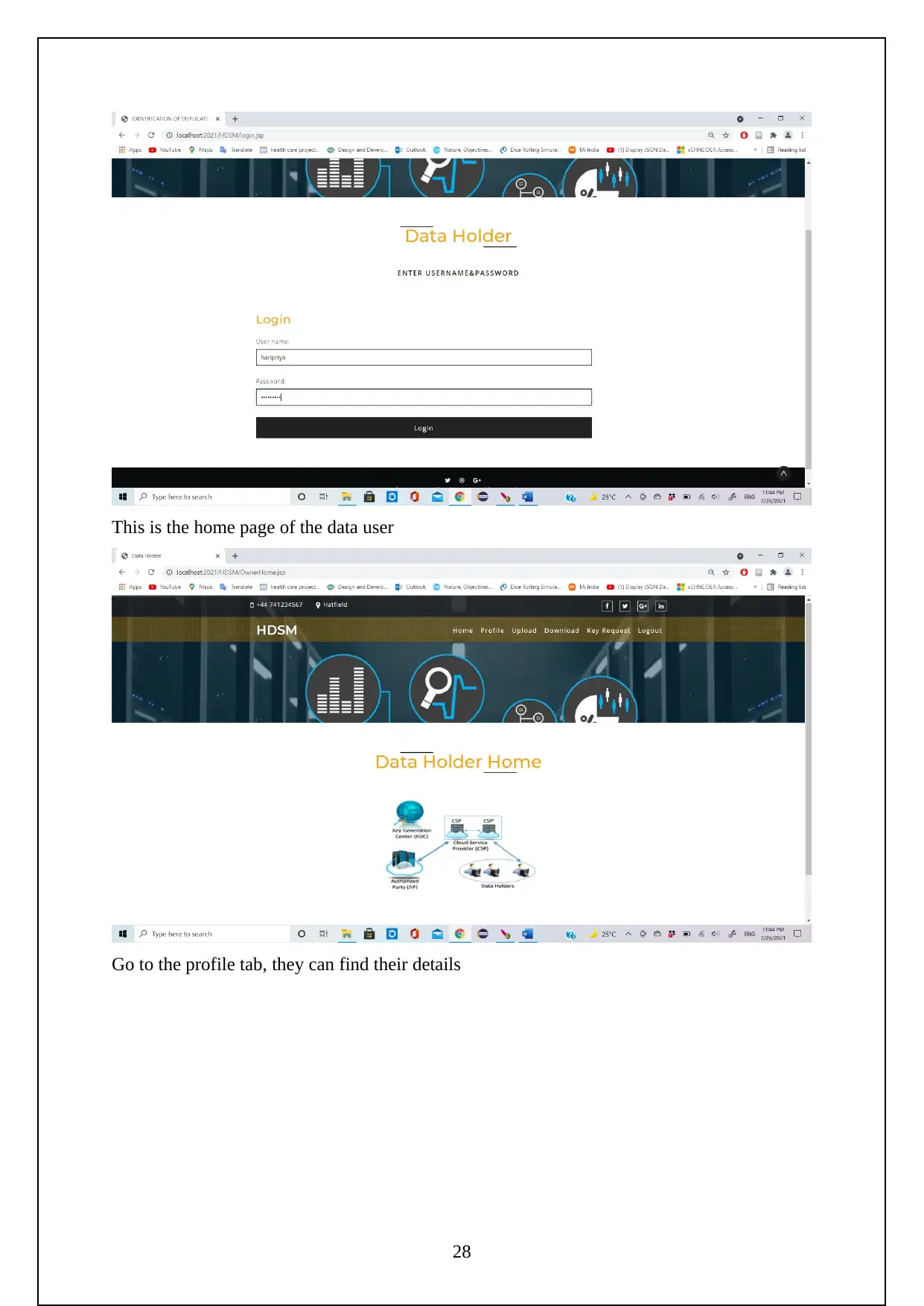
This is the home page of the data user
Go to the profile tab, they can find their details
28
Go to the profile tab, they can find their details
28
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
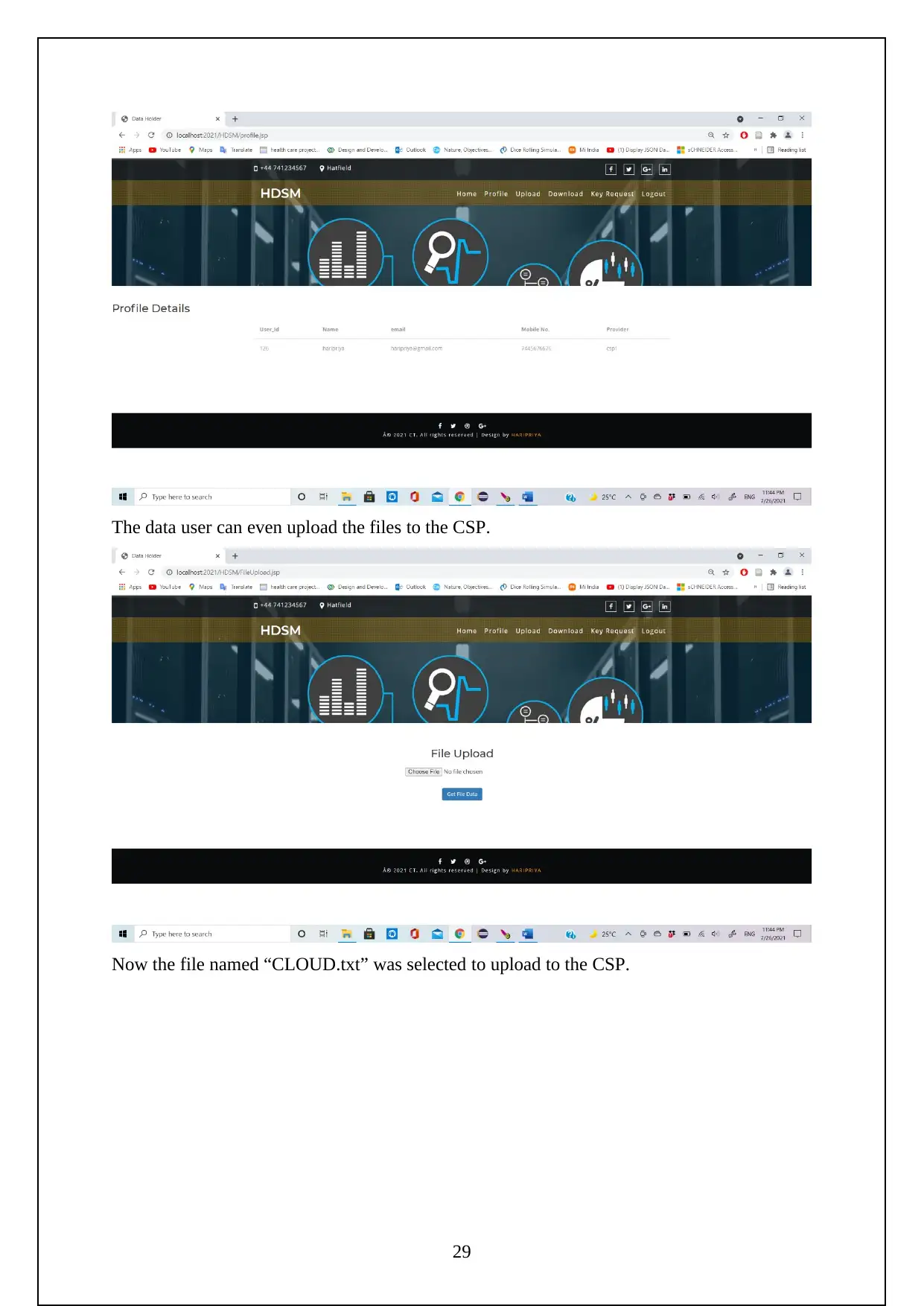
The data user can even upload the files to the CSP.
Now the file named “CLOUD.txt” was selected to upload to the CSP.
29
Now the file named “CLOUD.txt” was selected to upload to the CSP.
29
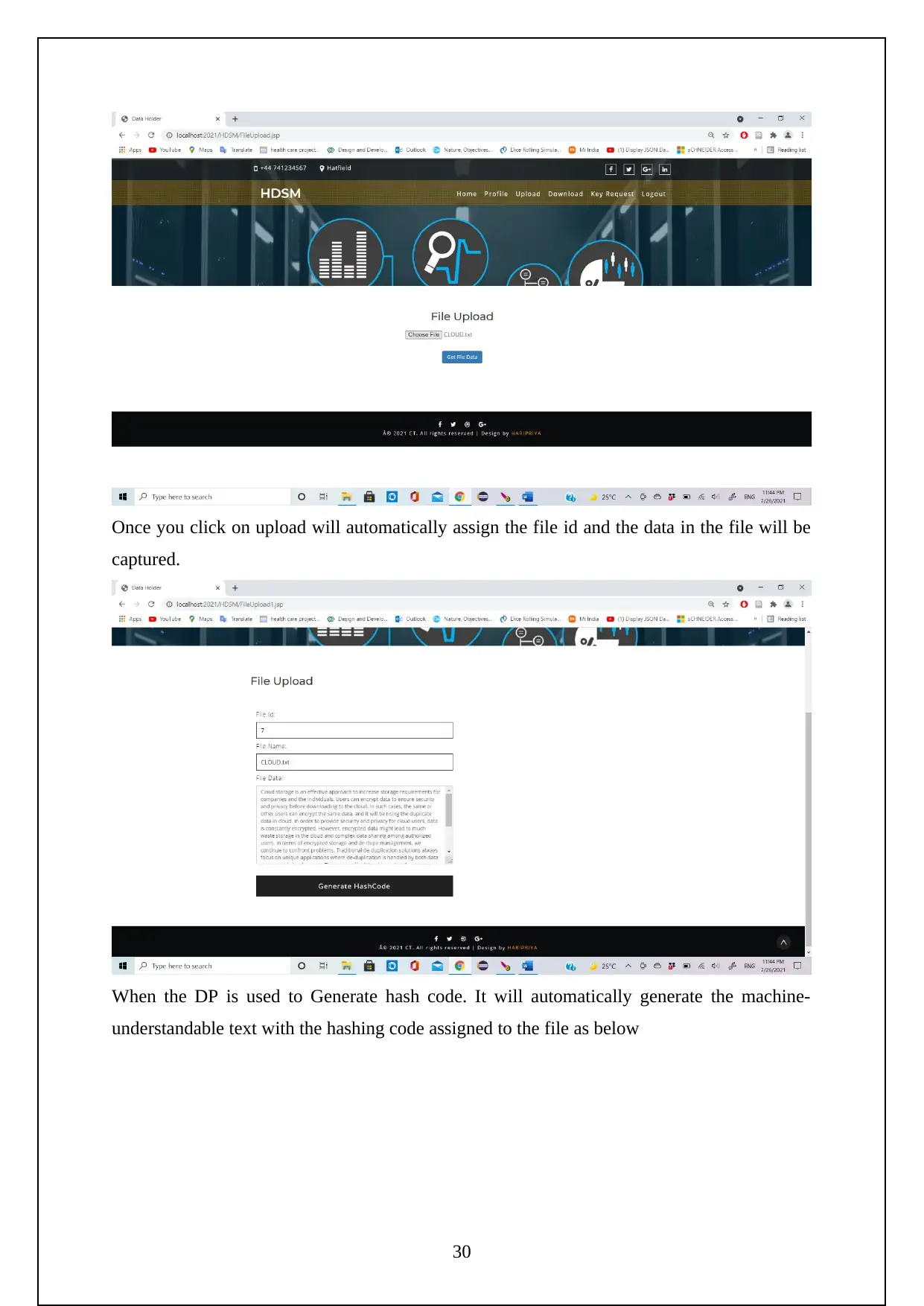
Once you click on upload will automatically assign the file id and the data in the file will be
captured.
When the DP is used to Generate hash code. It will automatically generate the machine-
understandable text with the hashing code assigned to the file as below
30
captured.
When the DP is used to Generate hash code. It will automatically generate the machine-
understandable text with the hashing code assigned to the file as below
30
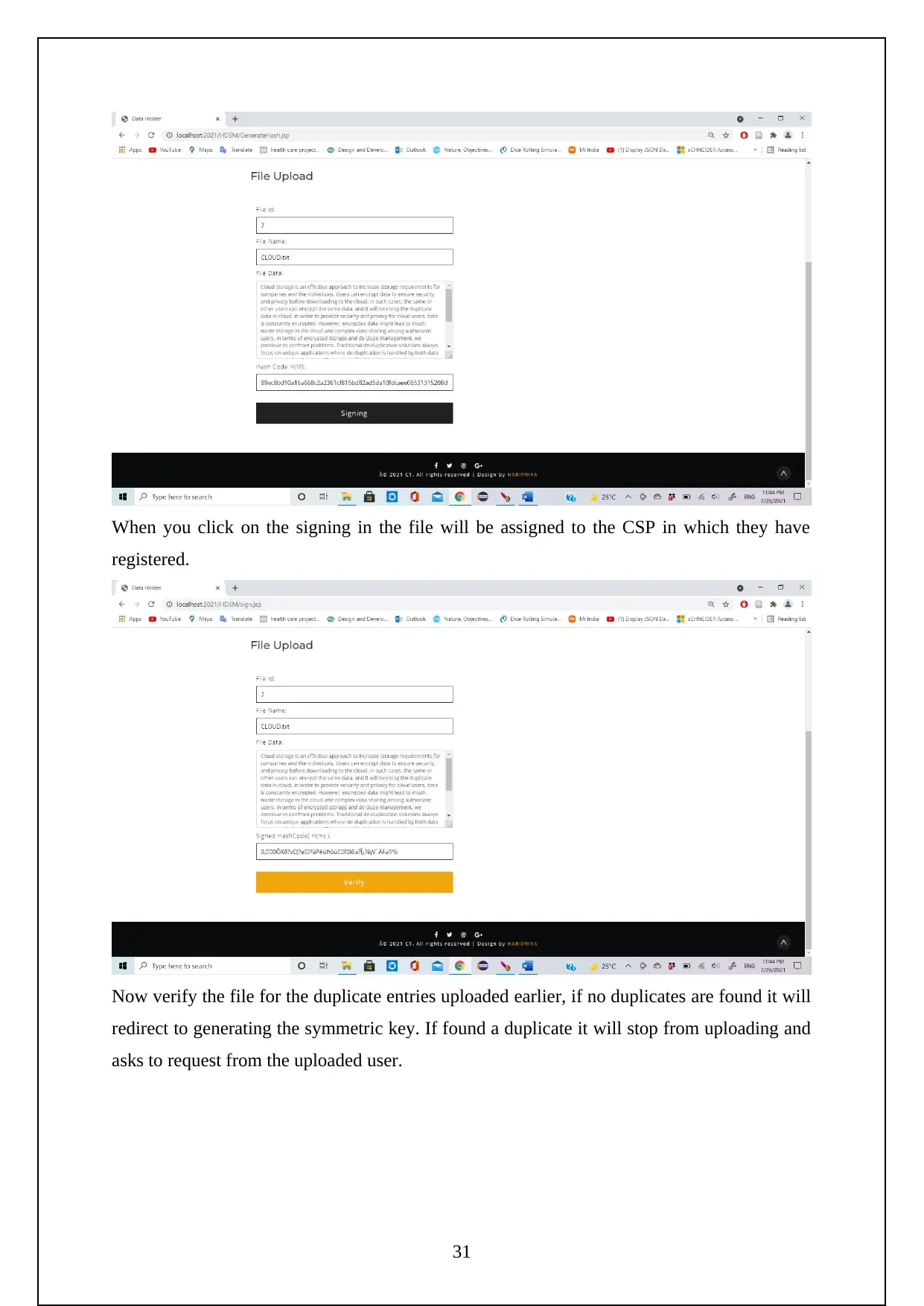
When you click on the signing in the file will be assigned to the CSP in which they have
registered.
Now verify the file for the duplicate entries uploaded earlier, if no duplicates are found it will
redirect to generating the symmetric key. If found a duplicate it will stop from uploading and
asks to request from the uploaded user.
31
registered.
Now verify the file for the duplicate entries uploaded earlier, if no duplicates are found it will
redirect to generating the symmetric key. If found a duplicate it will stop from uploading and
asks to request from the uploaded user.
31
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
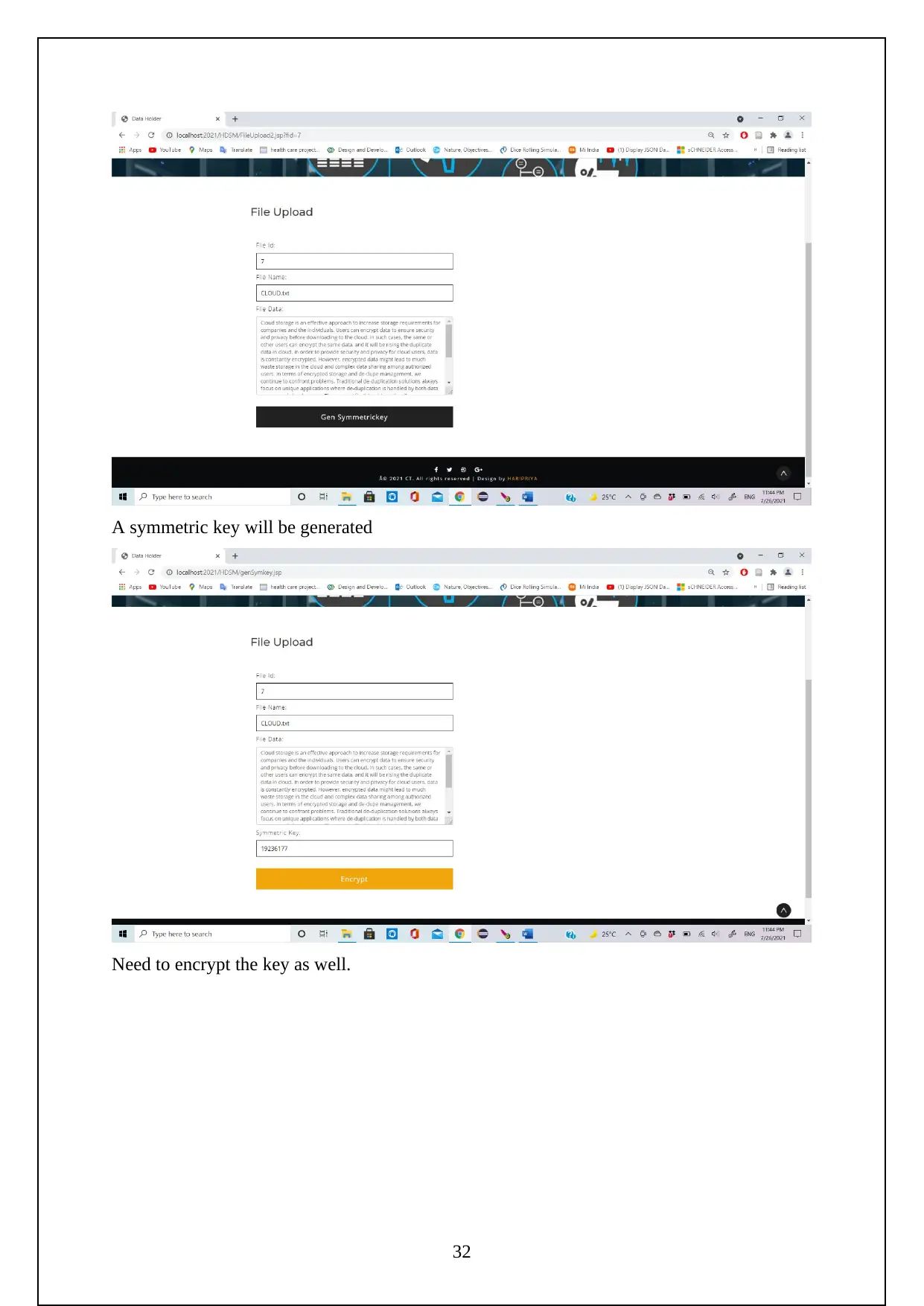
A symmetric key will be generated
Need to encrypt the key as well.
32
Need to encrypt the key as well.
32
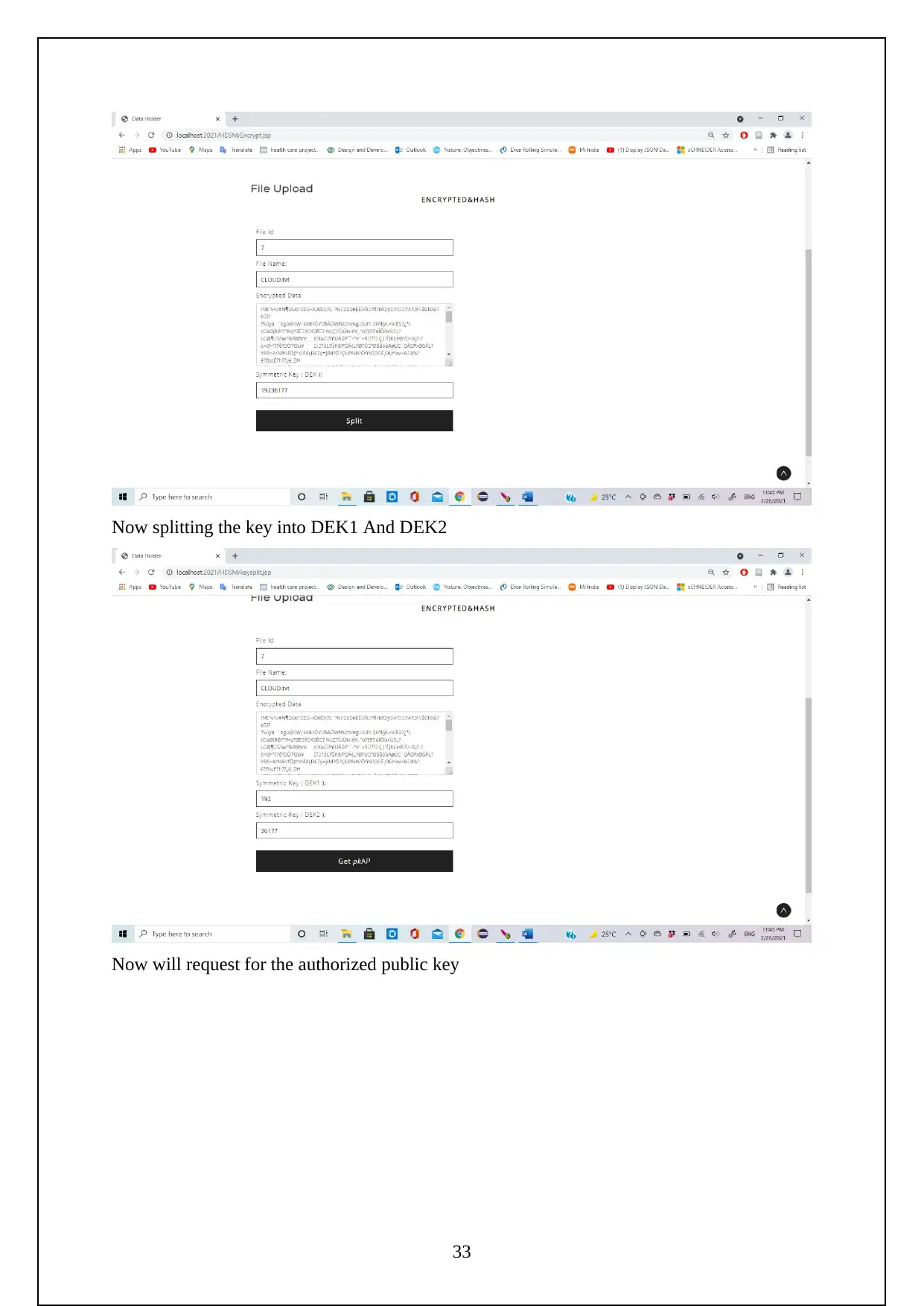
Now splitting the key into DEK1 And DEK2
Now will request for the authorized public key
33
Now will request for the authorized public key
33
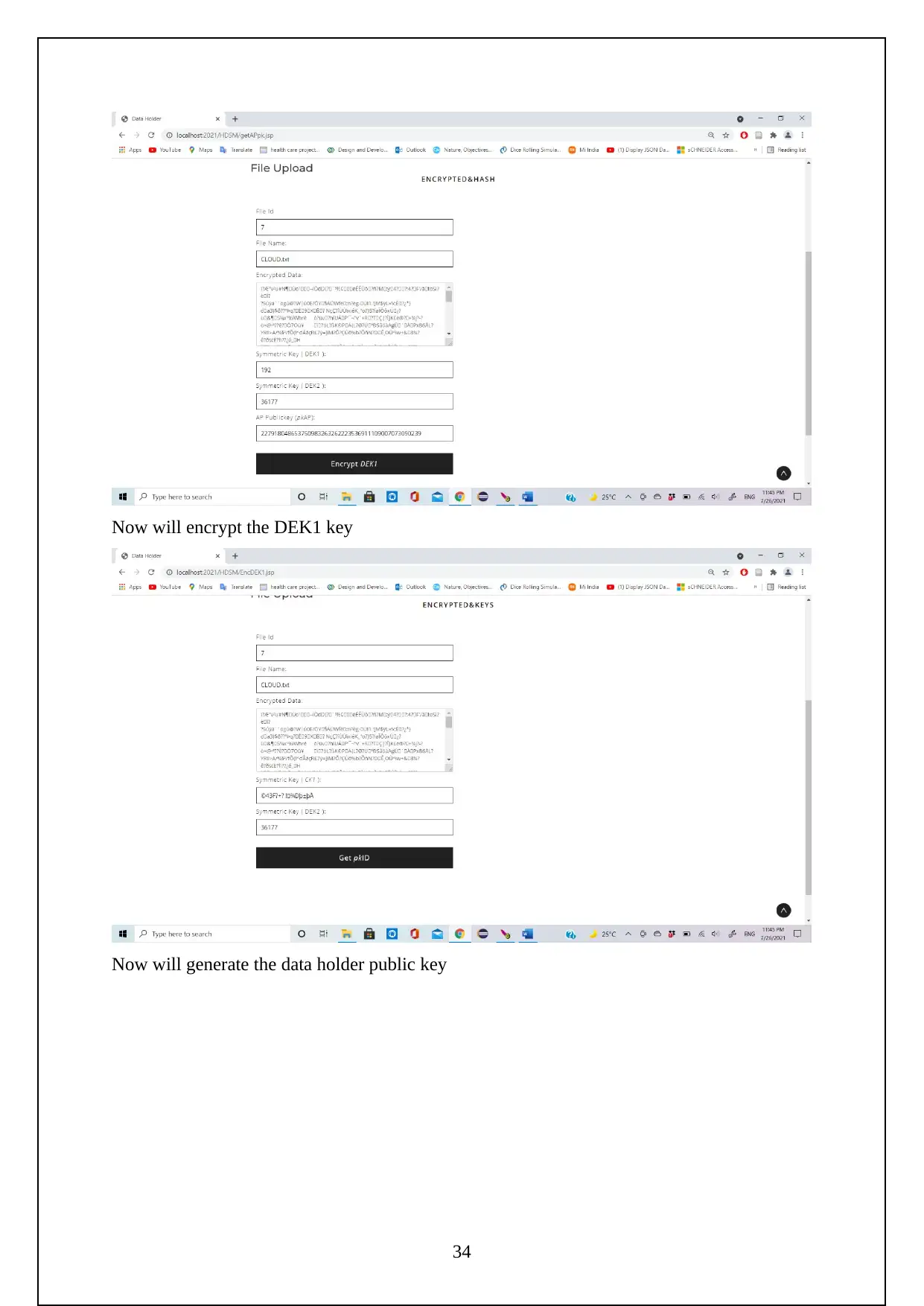
Now will encrypt the DEK1 key
Now will generate the data holder public key
34
Now will generate the data holder public key
34
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Now after encrypting all the data in the file along with the CK1 and CK2 will upload the file
to the server.
Once the file is uploaded will get a pop message of successfully uploaded thing. Can check
the uploaded files in the downloads.
35
to the server.
Once the file is uploaded will get a pop message of successfully uploaded thing. Can check
the uploaded files in the downloads.
35
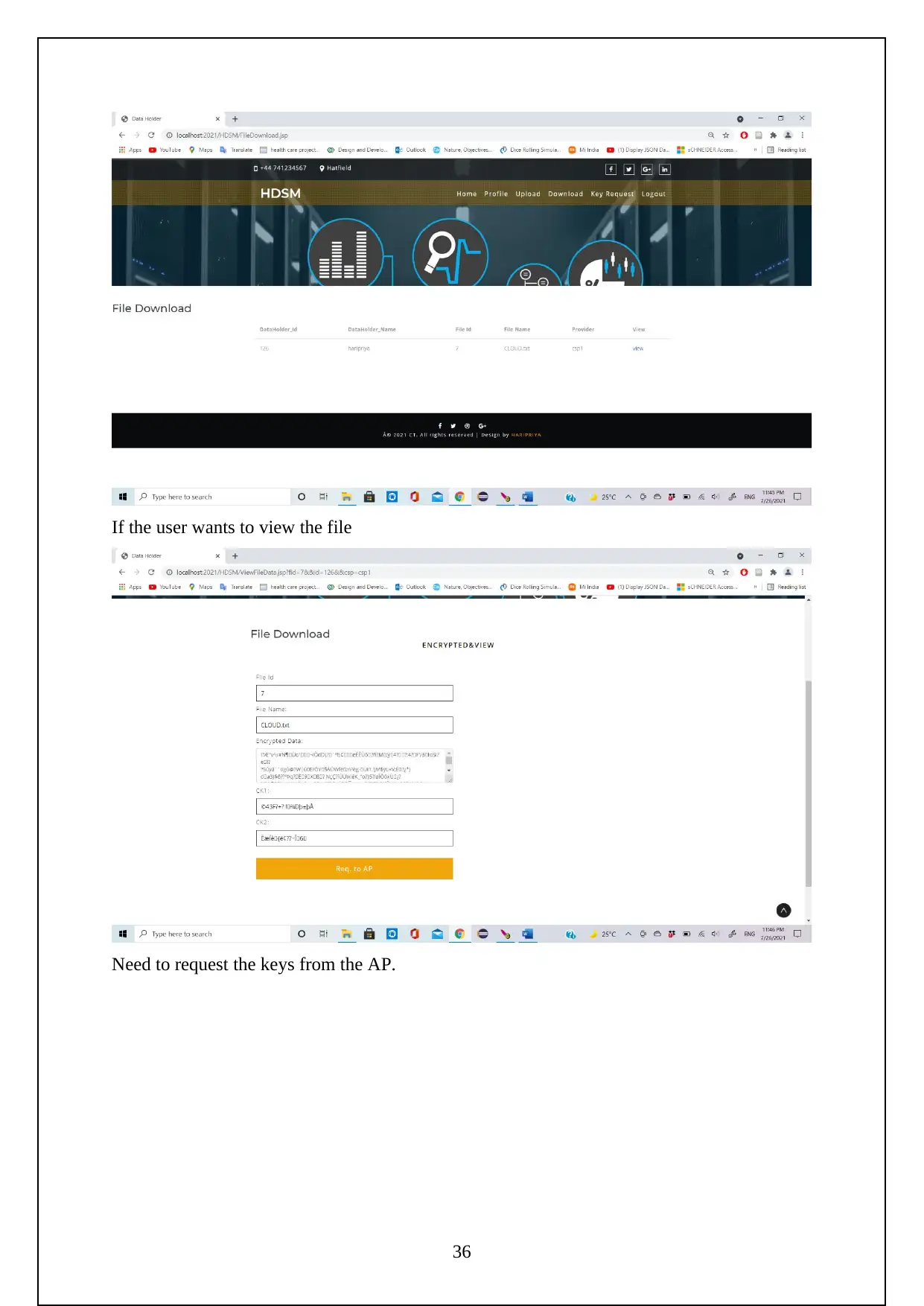
If the user wants to view the file
Need to request the keys from the AP.
36
Need to request the keys from the AP.
36
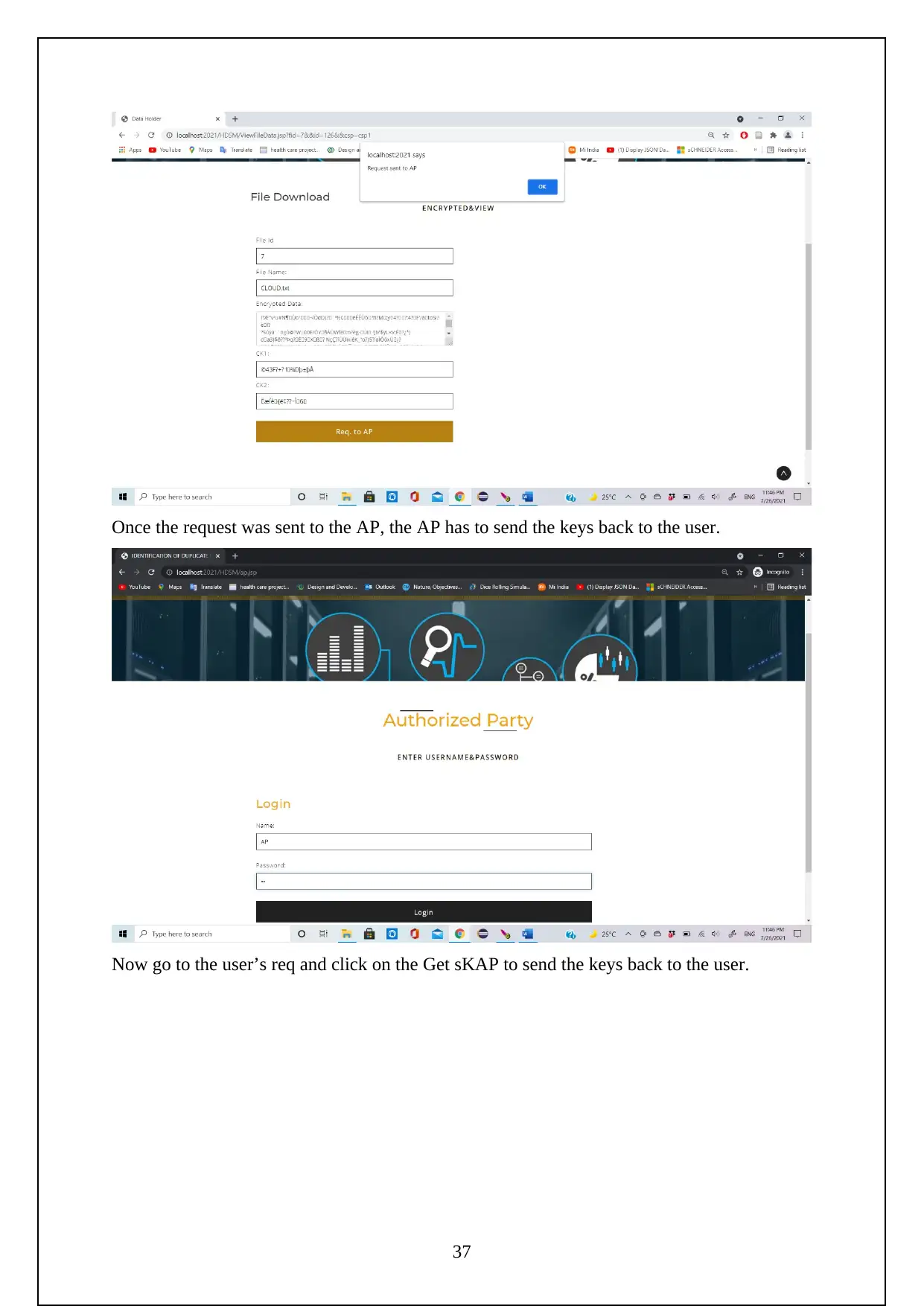
Once the request was sent to the AP, the AP has to send the keys back to the user.
Now go to the user’s req and click on the Get sKAP to send the keys back to the user.
37
Now go to the user’s req and click on the Get sKAP to send the keys back to the user.
37
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
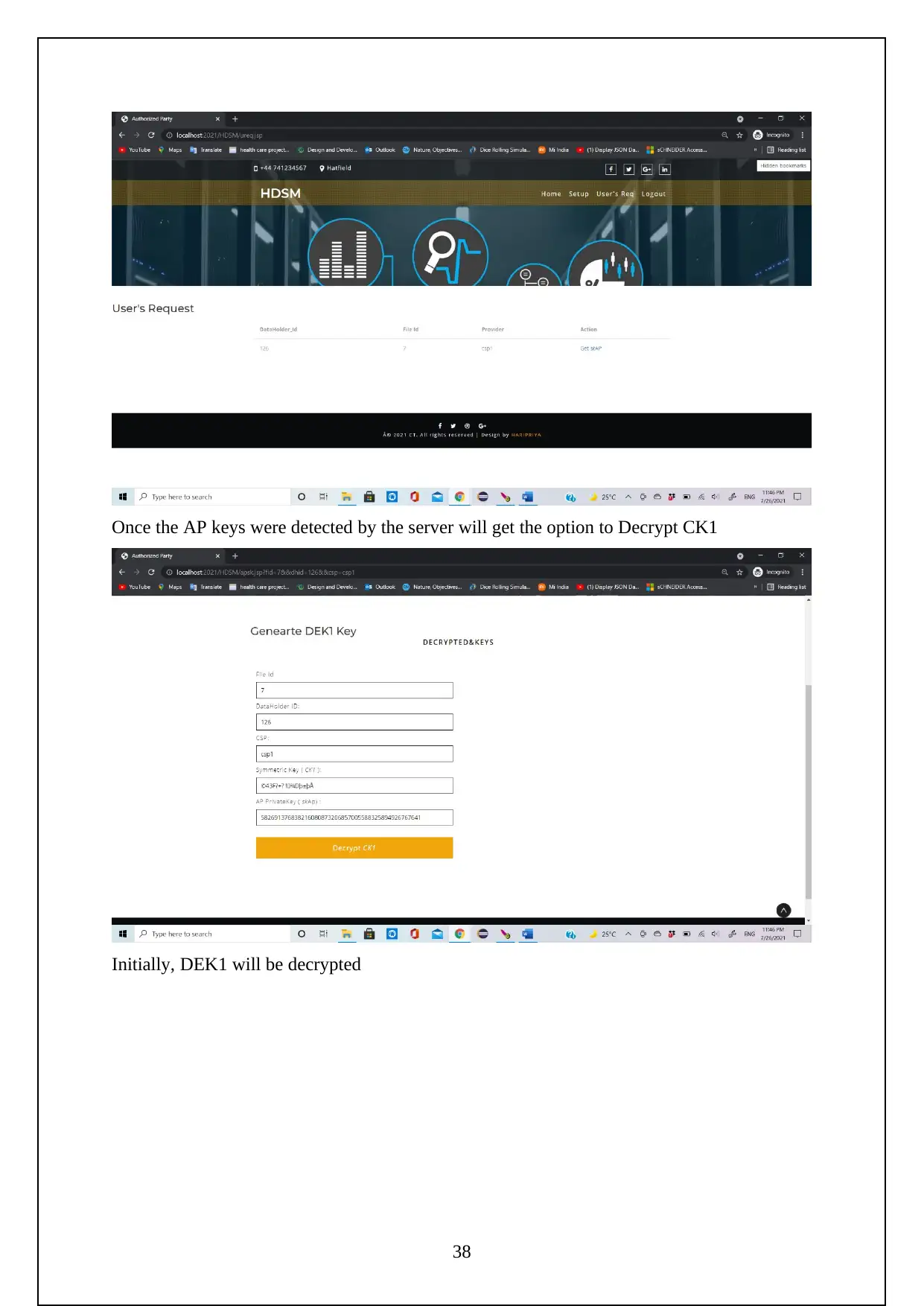
Once the AP keys were detected by the server will get the option to Decrypt CK1
Initially, DEK1 will be decrypted
38
Initially, DEK1 will be decrypted
38
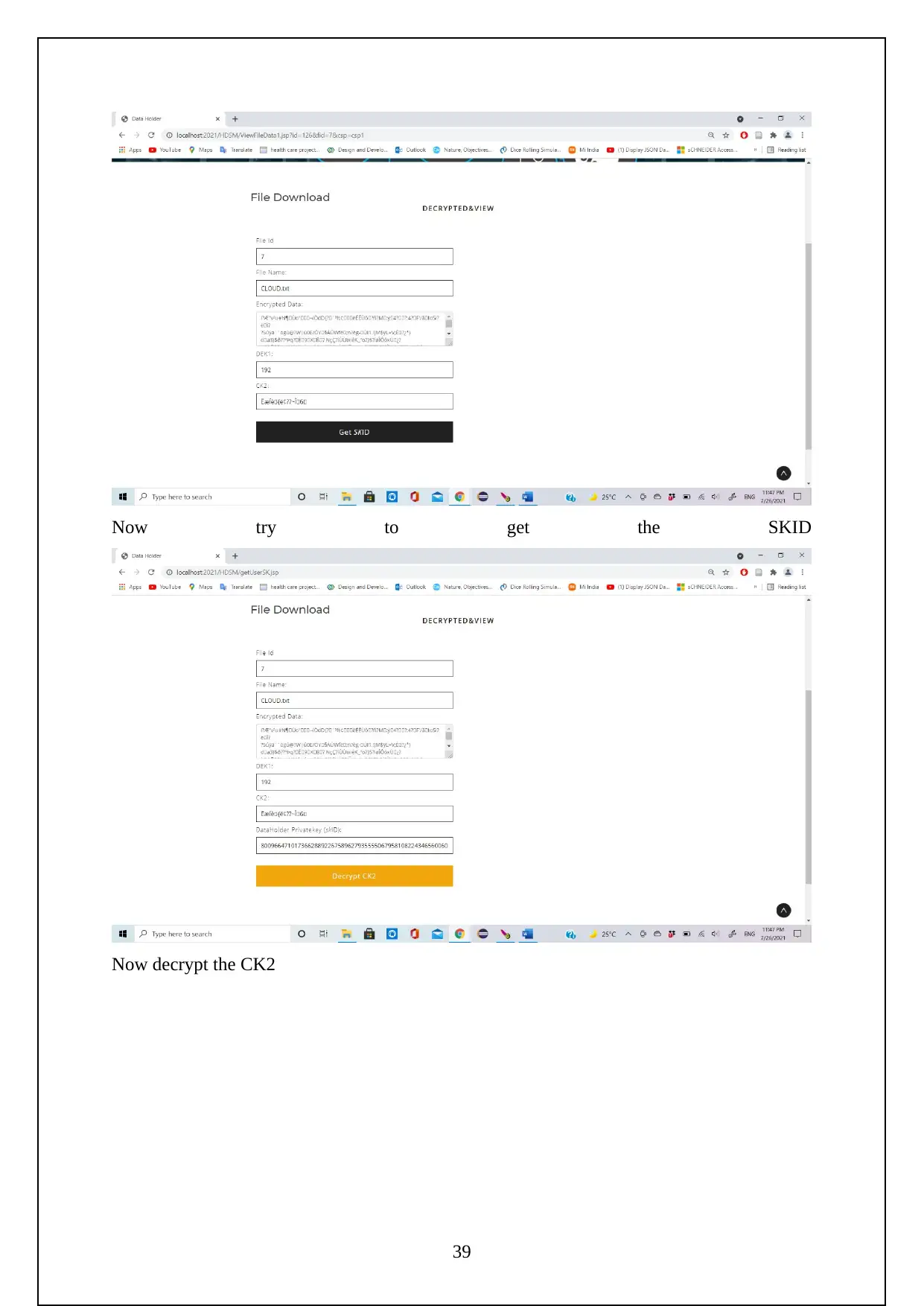
Now try to get the SKID
Now decrypt the CK2
39
Now decrypt the CK2
39
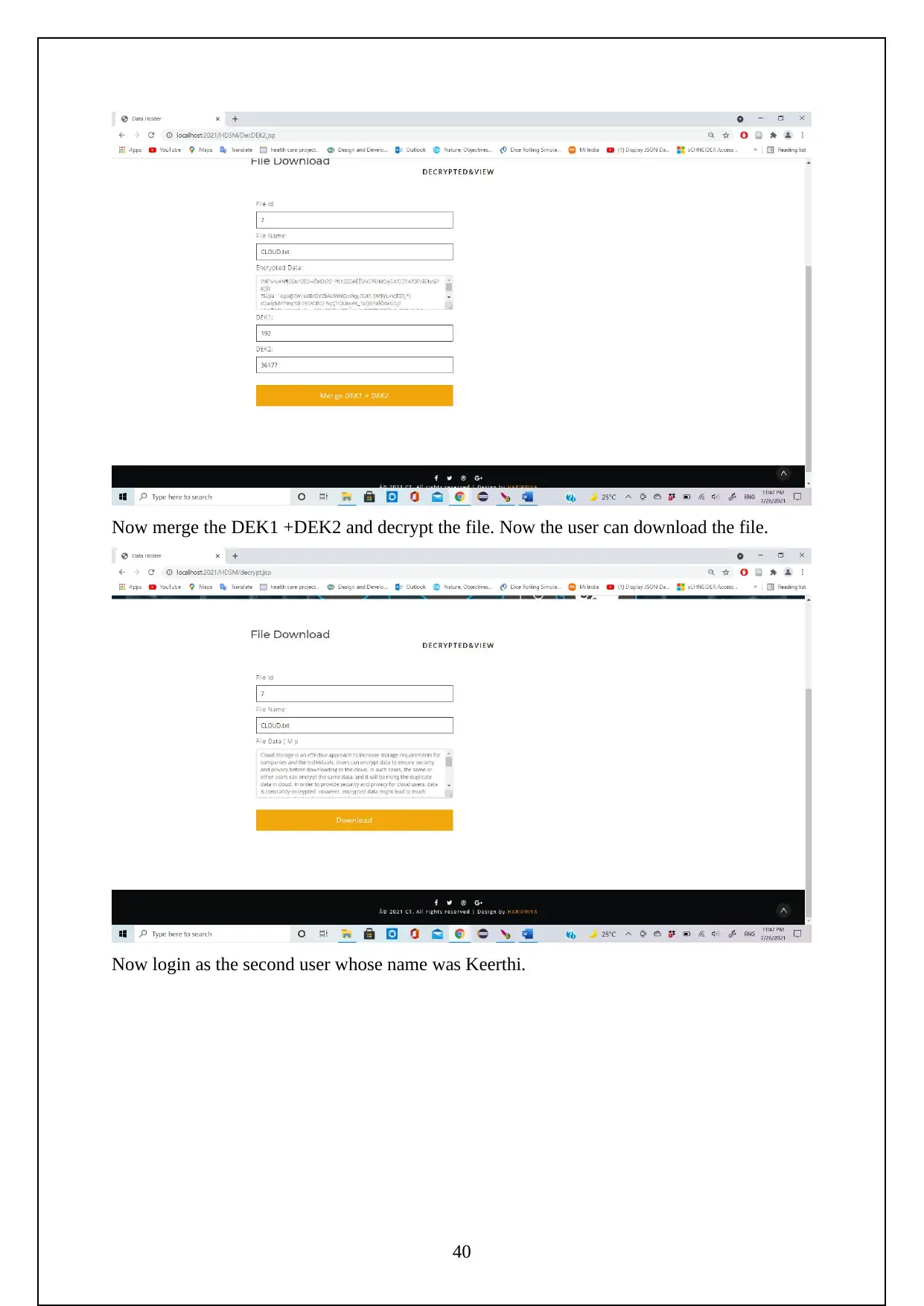
Now merge the DEK1 +DEK2 and decrypt the file. Now the user can download the file.
Now login as the second user whose name was Keerthi.
40
Now login as the second user whose name was Keerthi.
40
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
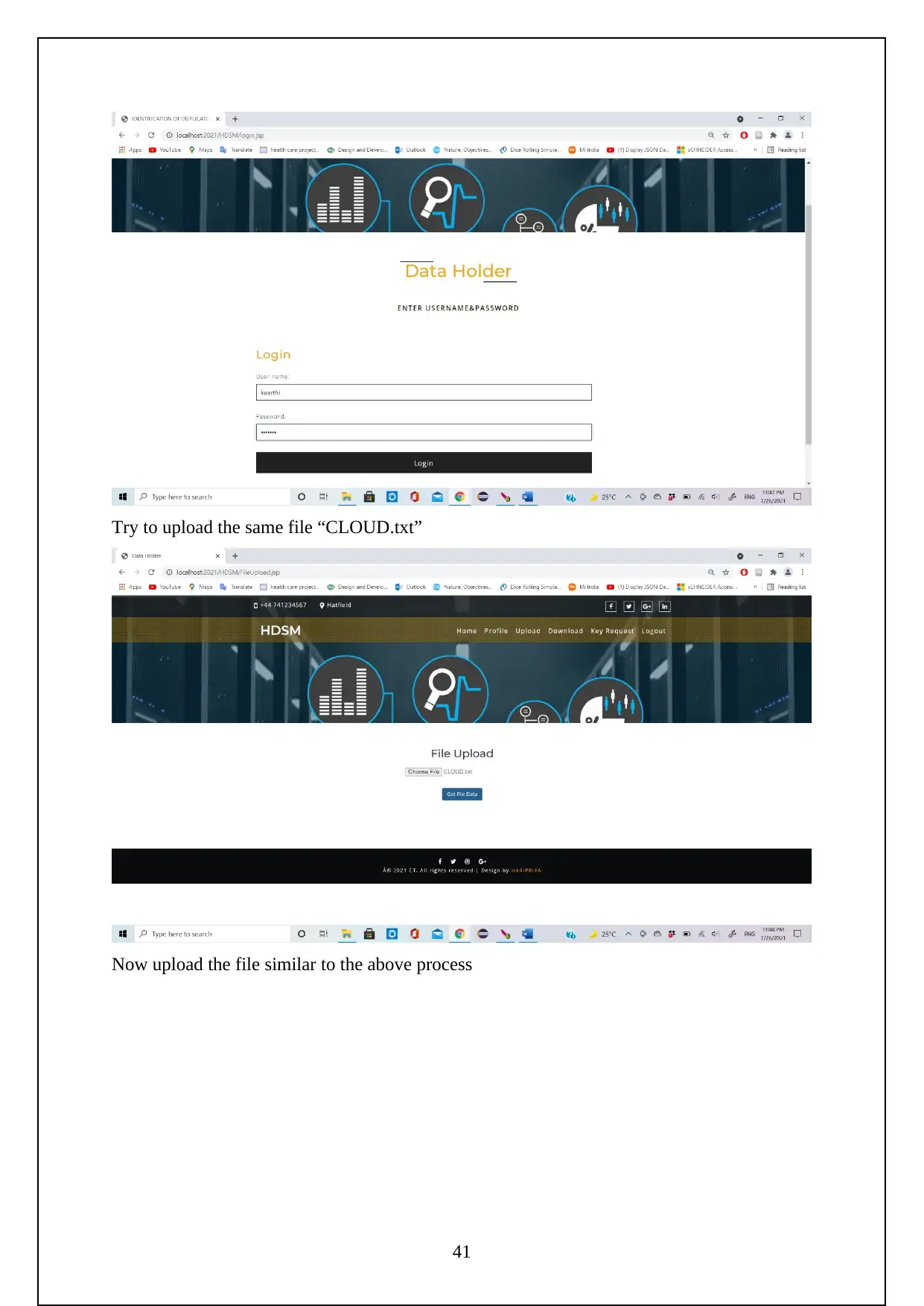
Try to upload the same file “CLOUD.txt”
Now upload the file similar to the above process
41
Now upload the file similar to the above process
41
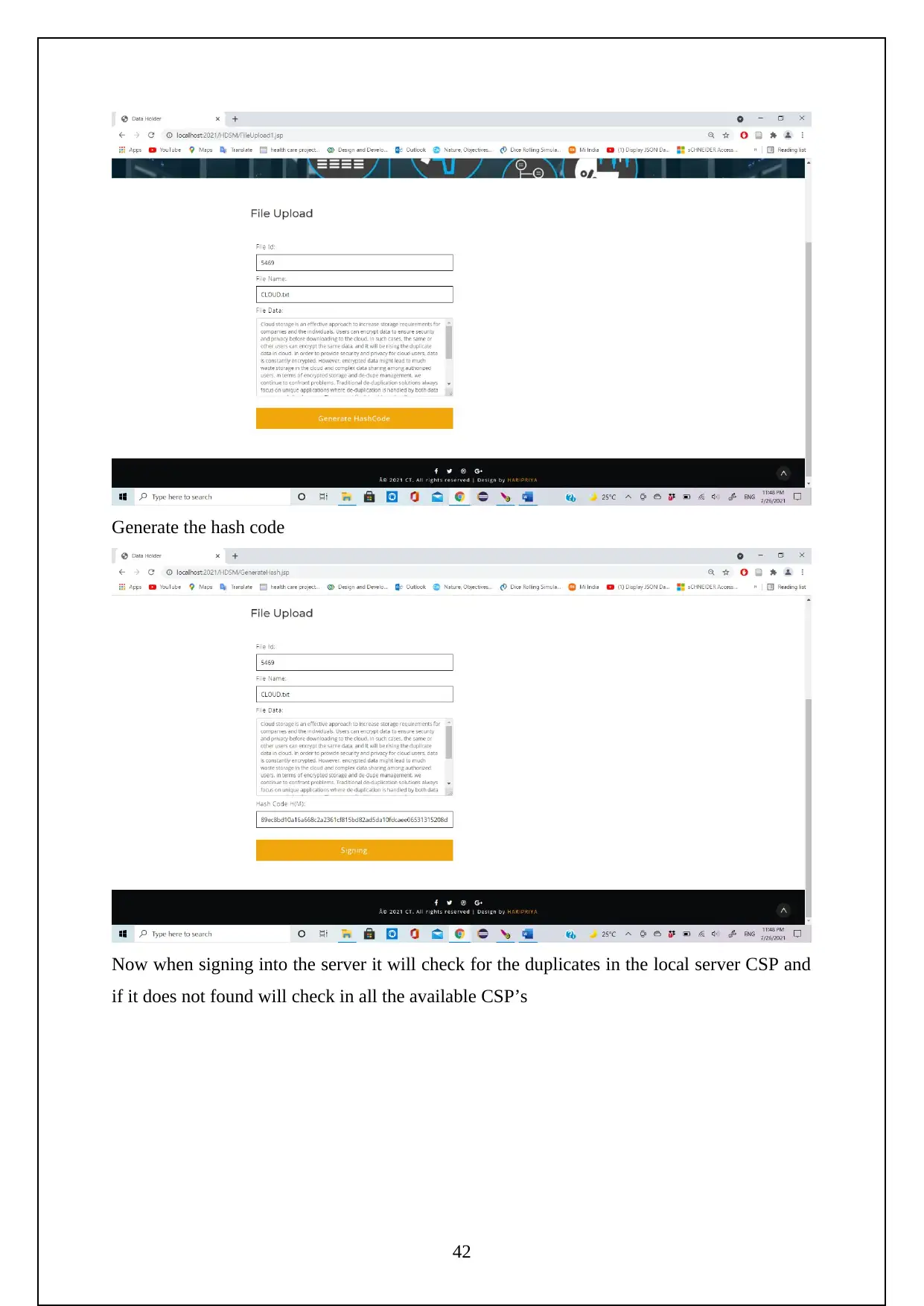
Generate the hash code
Now when signing into the server it will check for the duplicates in the local server CSP and
if it does not found will check in all the available CSP’s
42
Now when signing into the server it will check for the duplicates in the local server CSP and
if it does not found will check in all the available CSP’s
42
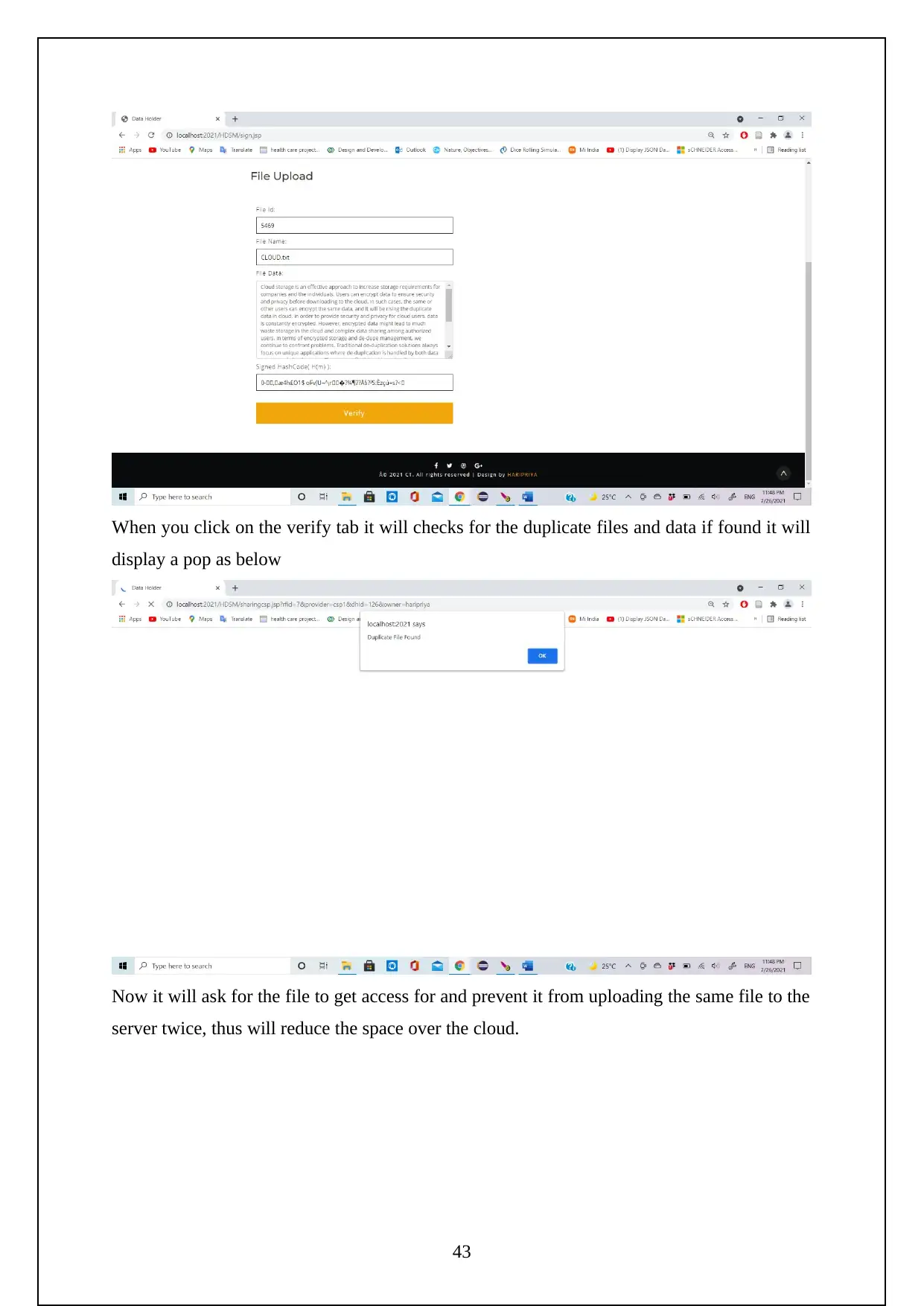
When you click on the verify tab it will checks for the duplicate files and data if found it will
display a pop as below
Now it will ask for the file to get access for and prevent it from uploading the same file to the
server twice, thus will reduce the space over the cloud.
43
display a pop as below
Now it will ask for the file to get access for and prevent it from uploading the same file to the
server twice, thus will reduce the space over the cloud.
43
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
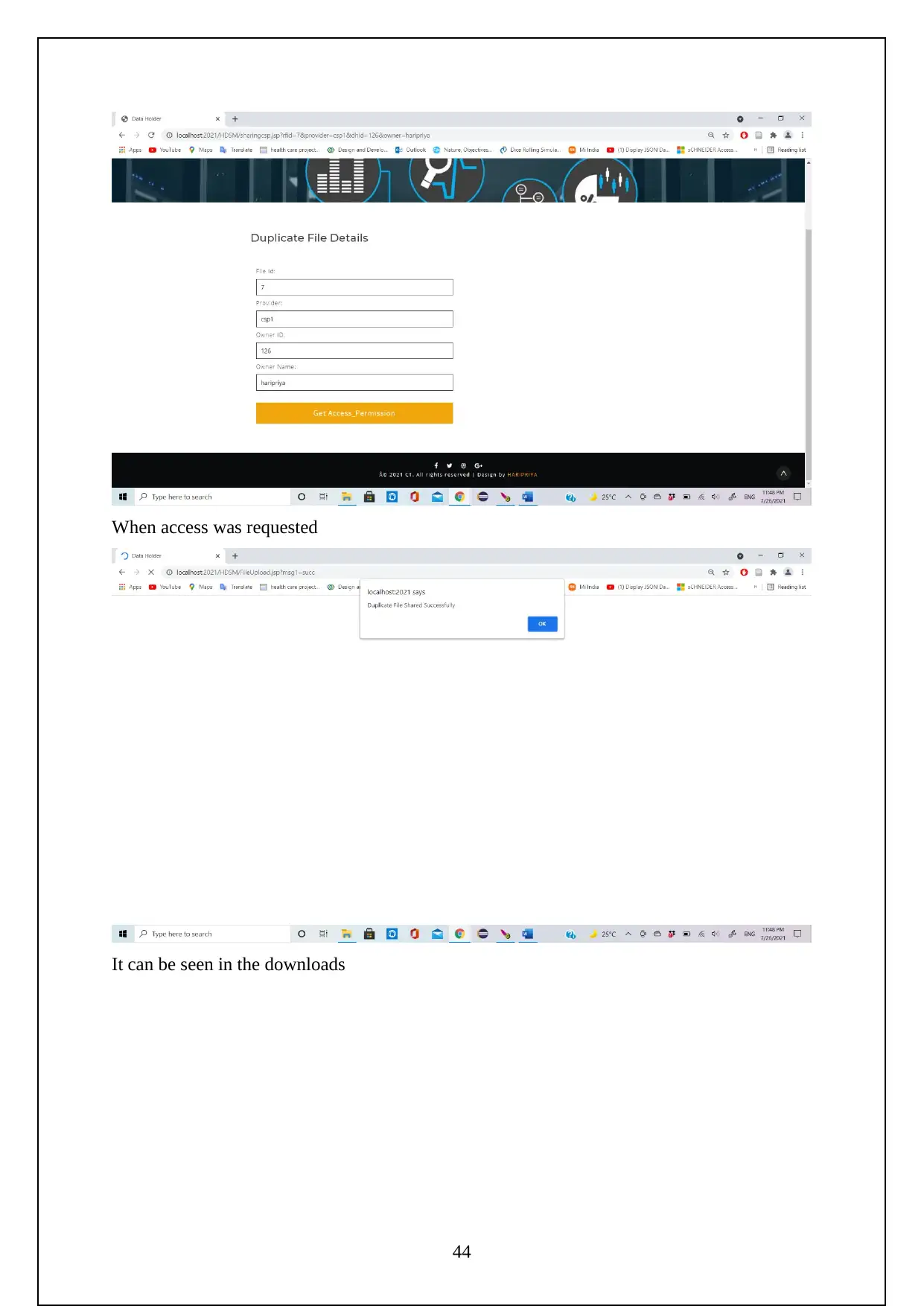
When access was requested
It can be seen in the downloads
44
It can be seen in the downloads
44
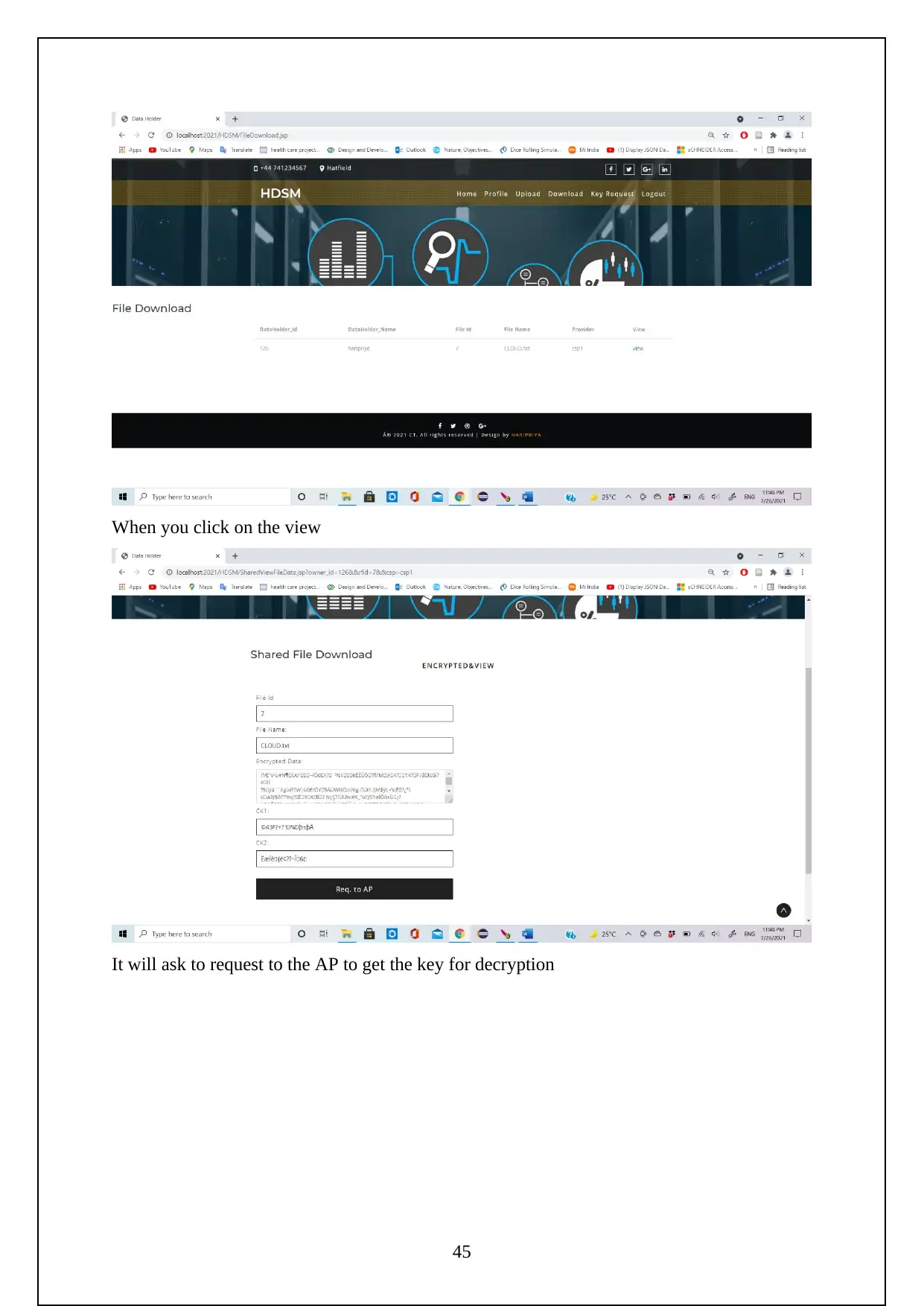
When you click on the view
It will ask to request to the AP to get the key for decryption
45
It will ask to request to the AP to get the key for decryption
45
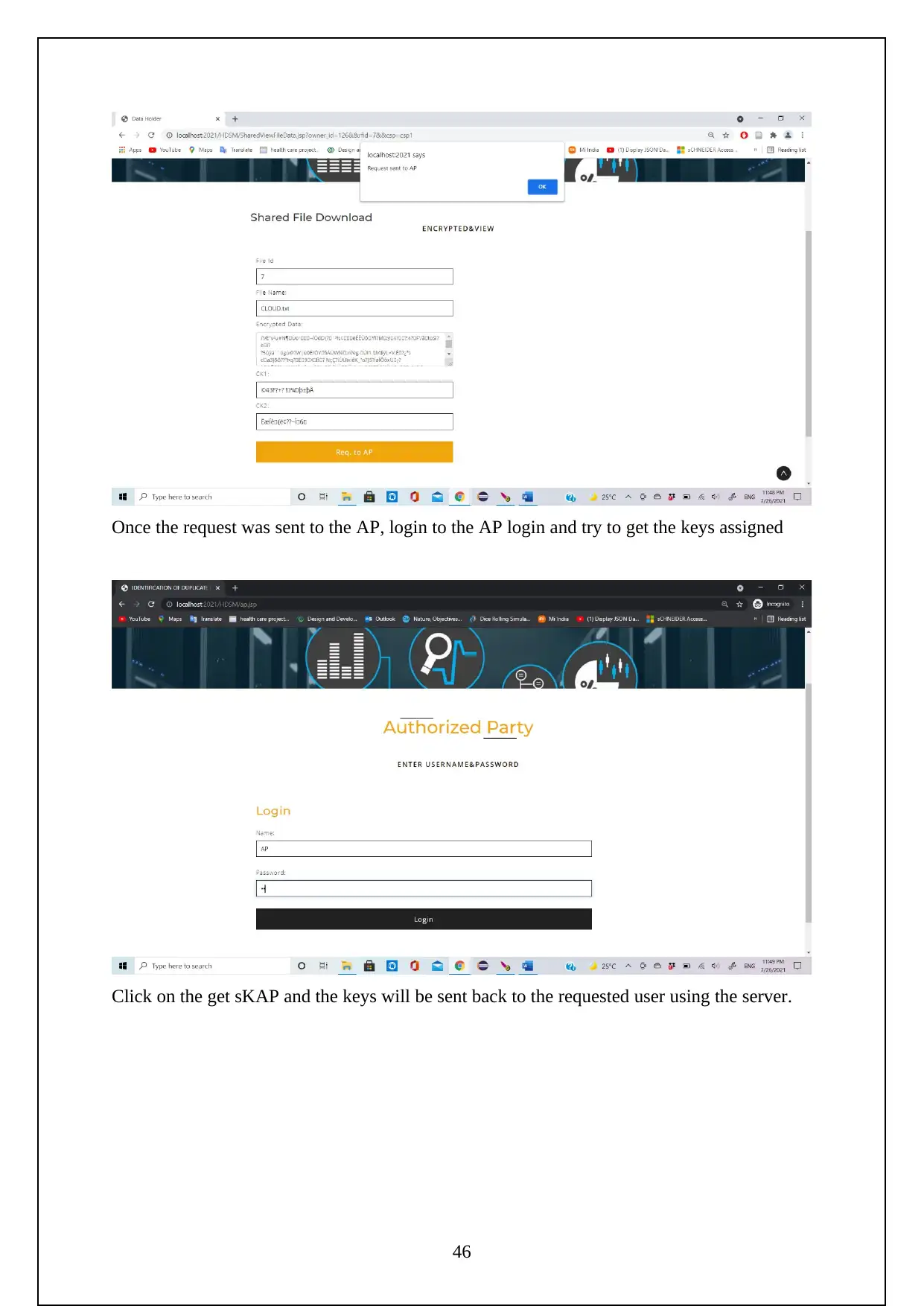
Once the request was sent to the AP, login to the AP login and try to get the keys assigned
Click on the get sKAP and the keys will be sent back to the requested user using the server.
46
Click on the get sKAP and the keys will be sent back to the requested user using the server.
46
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
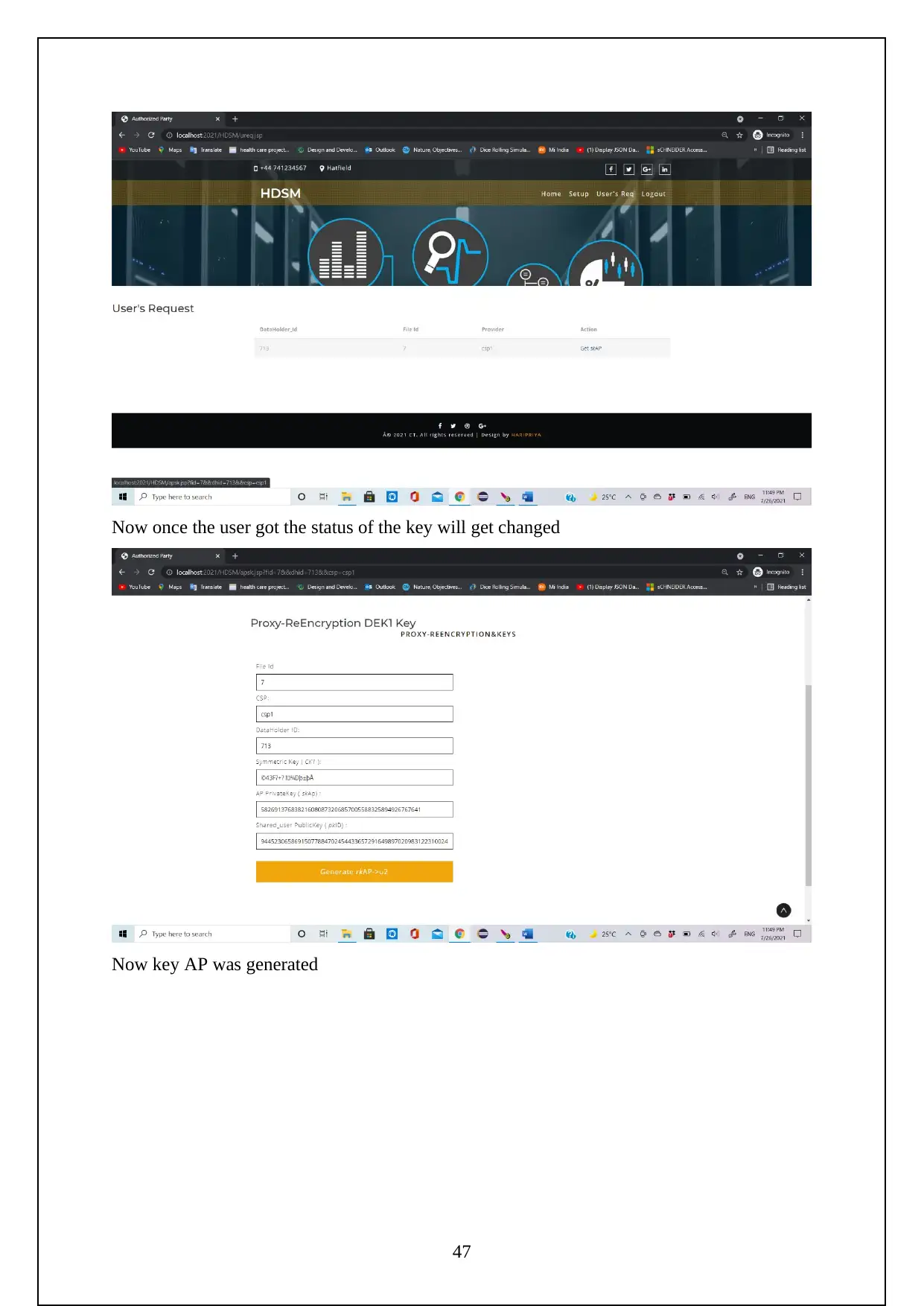
Now once the user got the status of the key will get changed
Now key AP was generated
47
Now key AP was generated
47
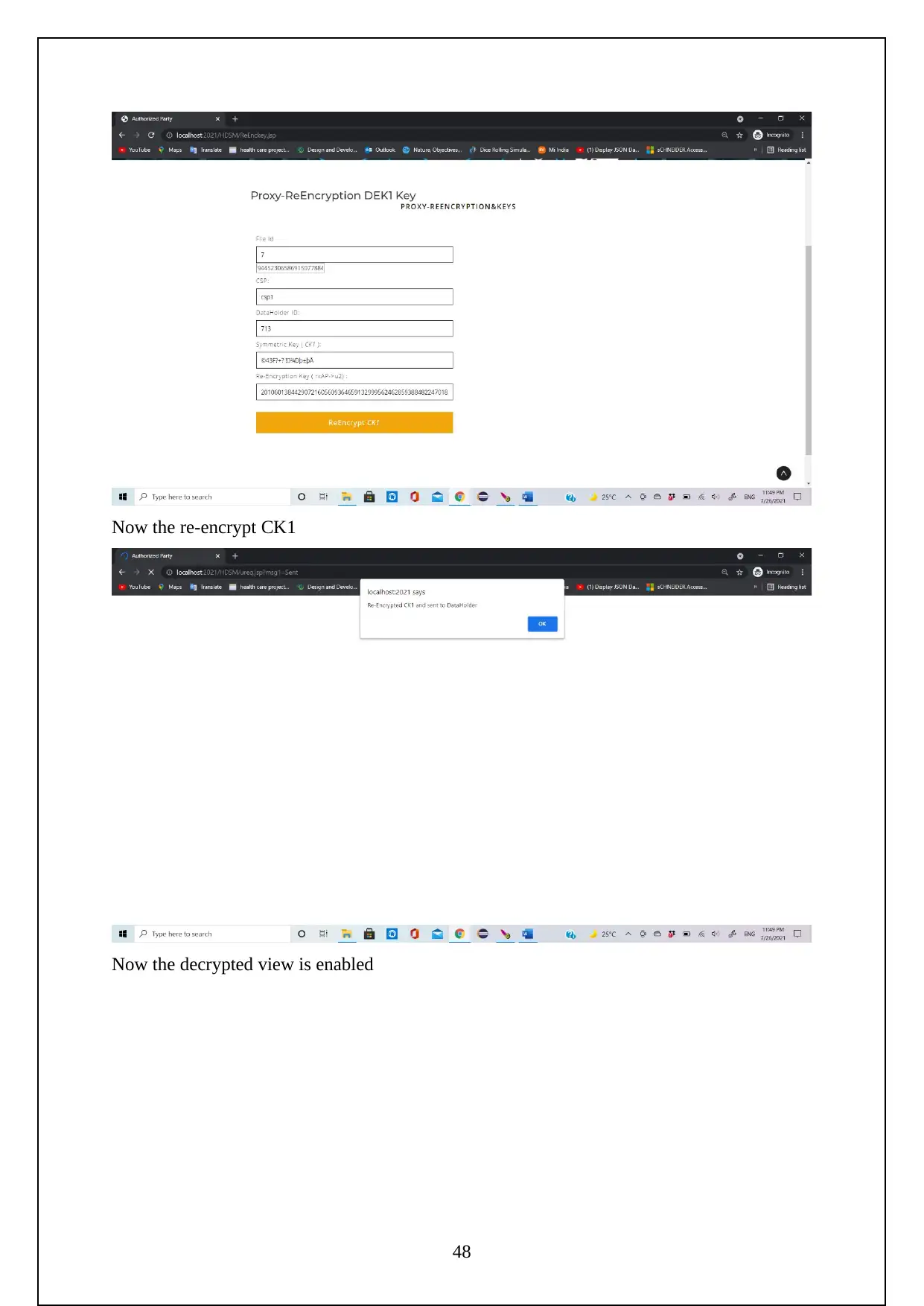
Now the re-encrypt CK1
Now the decrypted view is enabled
48
Now the decrypted view is enabled
48

Once the data holder
Now the CK1 was decrypted
49
Now the CK1 was decrypted
49
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
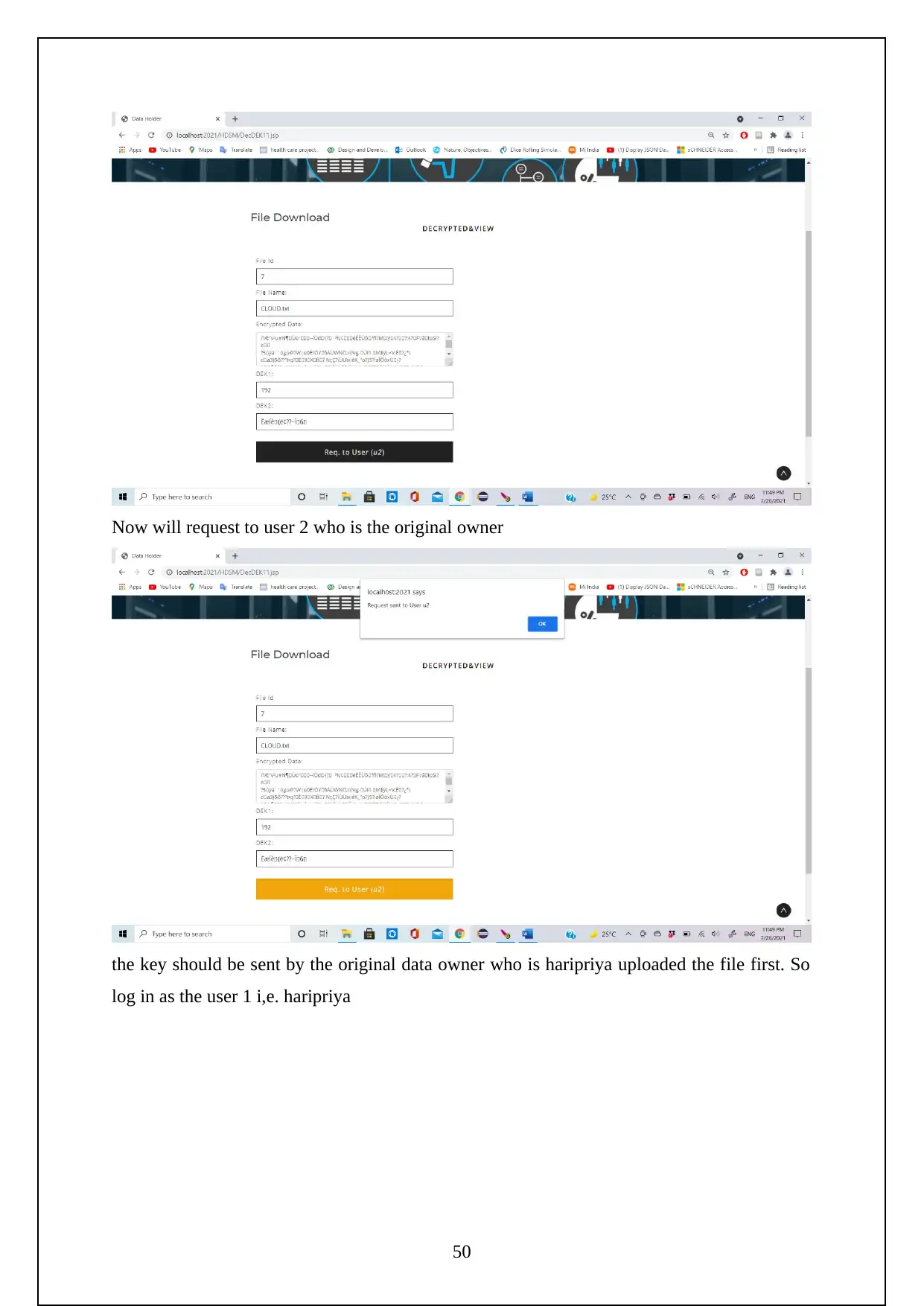
Now will request to user 2 who is the original owner
the key should be sent by the original data owner who is haripriya uploaded the file first. So
log in as the user 1 i,e. haripriya
50
the key should be sent by the original data owner who is haripriya uploaded the file first. So
log in as the user 1 i,e. haripriya
50
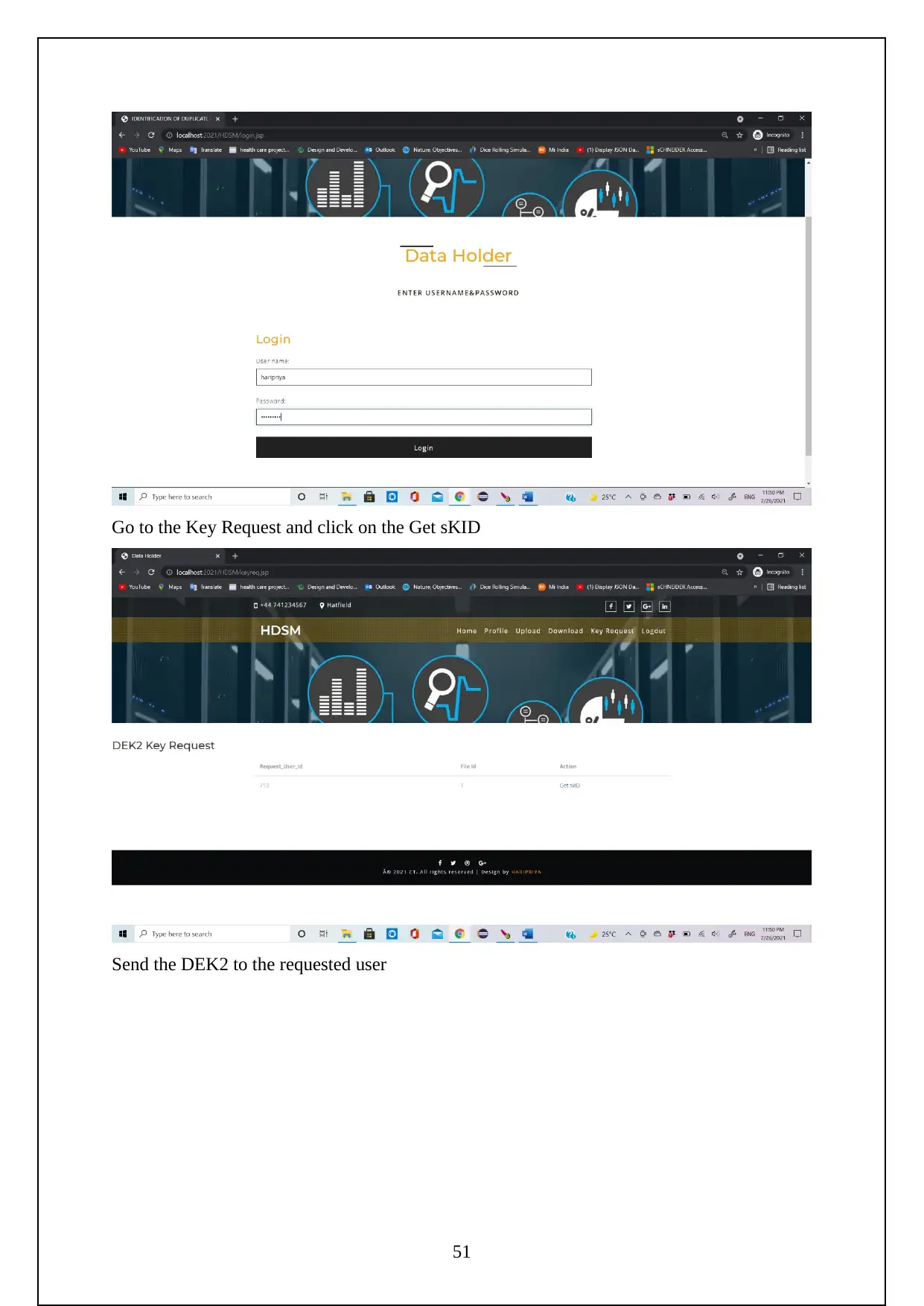
Go to the Key Request and click on the Get sKID
Send the DEK2 to the requested user
51
Send the DEK2 to the requested user
51
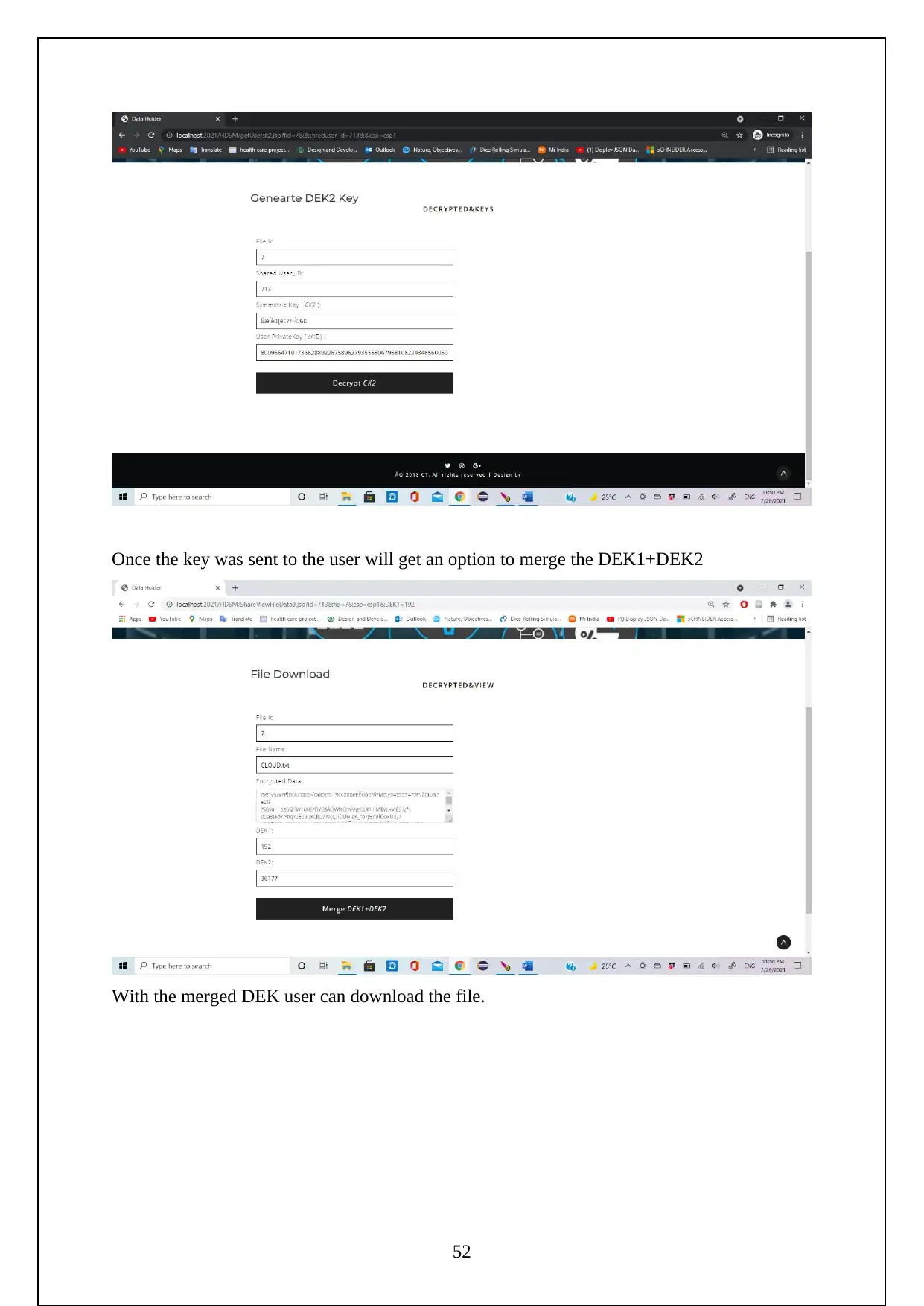
Once the key was sent to the user will get an option to merge the DEK1+DEK2
With the merged DEK user can download the file.
52
With the merged DEK user can download the file.
52
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
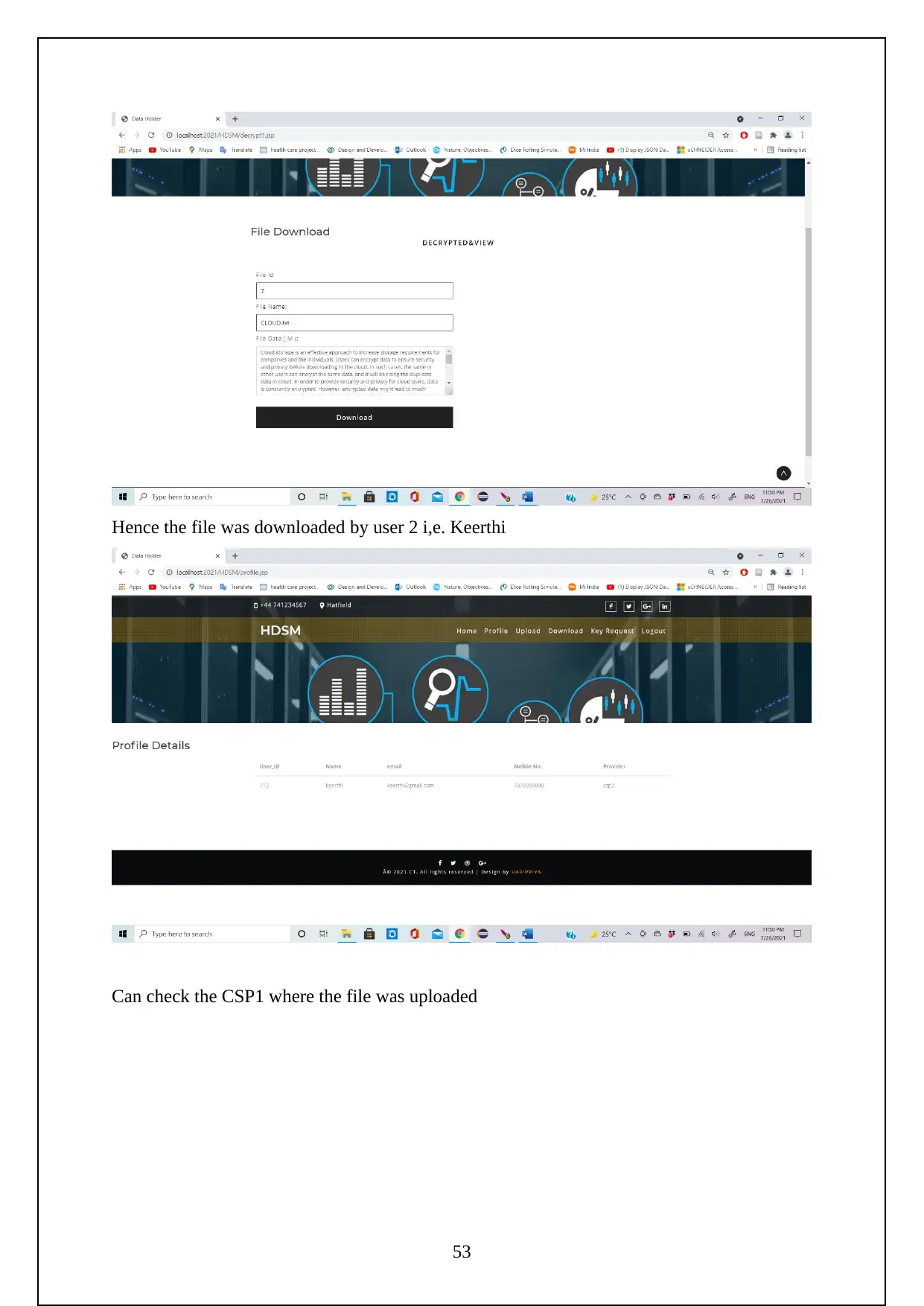
Hence the file was downloaded by user 2 i,e. Keerthi
Can check the CSP1 where the file was uploaded
53
Can check the CSP1 where the file was uploaded
53
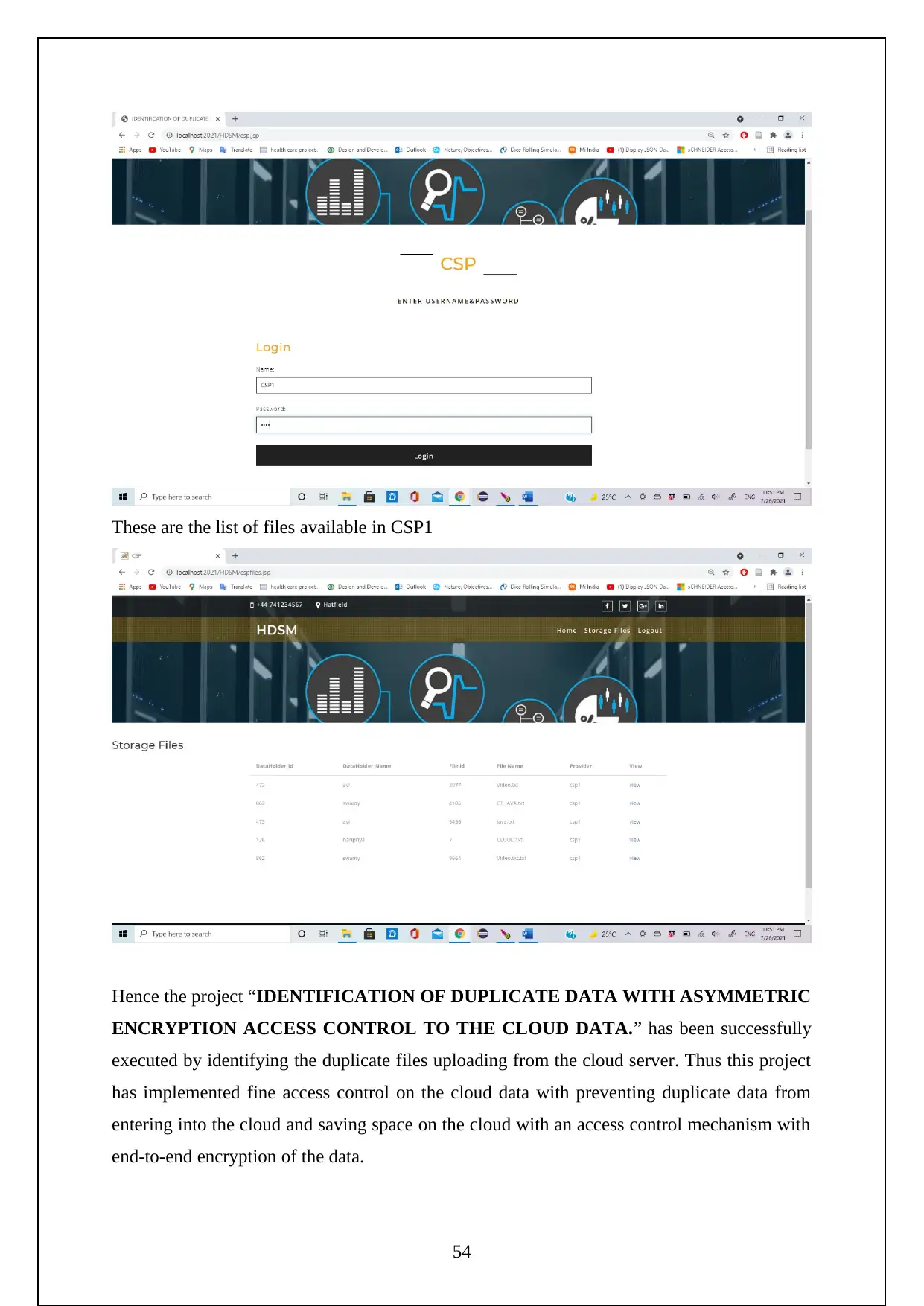
These are the list of files available in CSP1
Hence the project “IDENTIFICATION OF DUPLICATE DATA WITH ASYMMETRIC
ENCRYPTION ACCESS CONTROL TO THE CLOUD DATA.” has been successfully
executed by identifying the duplicate files uploading from the cloud server. Thus this project
has implemented fine access control on the cloud data with preventing duplicate data from
entering into the cloud and saving space on the cloud with an access control mechanism with
end-to-end encryption of the data.
54
Hence the project “IDENTIFICATION OF DUPLICATE DATA WITH ASYMMETRIC
ENCRYPTION ACCESS CONTROL TO THE CLOUD DATA.” has been successfully
executed by identifying the duplicate files uploading from the cloud server. Thus this project
has implemented fine access control on the cloud data with preventing duplicate data from
entering into the cloud and saving space on the cloud with an access control mechanism with
end-to-end encryption of the data.
54

4. DESIGNING
4.1 SYSTEM DESIGN REQUIREMENTS:
This article proposes a heterogeneous management approach for deductible
information stockpiles. In these situations, 1) it tends to be cleverly applied to properly
deduct cloud information from the information subject. 2) From everyone who confided to
outsiders; 3) From both the owner of the information and a trusted outsider 4) Nobody (eg the
cloud stores general information) 5) Ownership of the information From someone or a trusted
outsider.
In particular, we use the information M hash code to approve the multiplication of
information during distributed storage. The information medium signs the hash code of the
information in order to pass the CSP Innovation Inspection. In the meantime, a list of
randomly selected information segments is used to process various hash codes (for example,
M's main hash code 15.1%, M's hash code 2125%). These hash codes are known as a set of
hash codes for information M (HC (M)).
If the owner/owner saves M in CSP, the displayed hash code for M will be shipped in
CSP to check for duplicates. If the CSP does not have copy information, the information
owner scrambles the accidentally generated DEK with a symmetric key to obtain the
encrypted information CT. DEK1 and DEK2 are split into two segments. DEK1 with pkAP
scrambles ABE and DEK2 by using PRE to bring CK1 and using pkID to get CK2(Yan et al.,
2019). The second DEK parcel is scrambled by CT and shipped by CSP. If the above copy
test is unlikely to be positive, the CSP also grants the responsibility of the information
conveyor to the specific hash code by explicitly controlling the hash code set in M. If a
constraint check is agreed upon, the CSP will refer the information owner or potentially the
AP for deduplication.
In the case of deduplication, the altered mystery key is provided from the information
owner via a protected communication channel (such as a public key cryptosystem) and
interprets CK2. do. The qualification check is great (i.e. the information owner is supposed to
have the information owner store the information M in the CSP). Meanwhile, the AP
provides the CSP re-encryption key. This key is used to allow the copied information career
to re-encrypt CT1 and decrypt it to get DEK1. Copied information careers can procure both
DEK1 and DEK2, allowing access to DEK1 and CT from CSPs. Verification and
deduplication of information between CSPs must be possible in the interests of the CSPs. For
55
4.1 SYSTEM DESIGN REQUIREMENTS:
This article proposes a heterogeneous management approach for deductible
information stockpiles. In these situations, 1) it tends to be cleverly applied to properly
deduct cloud information from the information subject. 2) From everyone who confided to
outsiders; 3) From both the owner of the information and a trusted outsider 4) Nobody (eg the
cloud stores general information) 5) Ownership of the information From someone or a trusted
outsider.
In particular, we use the information M hash code to approve the multiplication of
information during distributed storage. The information medium signs the hash code of the
information in order to pass the CSP Innovation Inspection. In the meantime, a list of
randomly selected information segments is used to process various hash codes (for example,
M's main hash code 15.1%, M's hash code 2125%). These hash codes are known as a set of
hash codes for information M (HC (M)).
If the owner/owner saves M in CSP, the displayed hash code for M will be shipped in
CSP to check for duplicates. If the CSP does not have copy information, the information
owner scrambles the accidentally generated DEK with a symmetric key to obtain the
encrypted information CT. DEK1 and DEK2 are split into two segments. DEK1 with pkAP
scrambles ABE and DEK2 by using PRE to bring CK1 and using pkID to get CK2(Yan et al.,
2019). The second DEK parcel is scrambled by CT and shipped by CSP. If the above copy
test is unlikely to be positive, the CSP also grants the responsibility of the information
conveyor to the specific hash code by explicitly controlling the hash code set in M. If a
constraint check is agreed upon, the CSP will refer the information owner or potentially the
AP for deduplication.
In the case of deduplication, the altered mystery key is provided from the information
owner via a protected communication channel (such as a public key cryptosystem) and
interprets CK2. do. The qualification check is great (i.e. the information owner is supposed to
have the information owner store the information M in the CSP). Meanwhile, the AP
provides the CSP re-encryption key. This key is used to allow the copied information career
to re-encrypt CT1 and decrypt it to get DEK1. Copied information careers can procure both
DEK1 and DEK2, allowing access to DEK1 and CT from CSPs. Verification and
deduplication of information between CSPs must be possible in the interests of the CSPs. For
55
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

other CSPs, sometimes one CSP stores information. CSP may support accessing copied
information from supported CSP clients.
DEK can be divided into various parts that are processed by several gatherings
approved based on the information management strategy set by the information owner. We
will explain the strategy by dividing DEK into two areas to work with the programs DEK1
and DEK2. You can flexibly provide applications in the following cases. 1) The data owner
confirms data deduplication only if DEK1 is null and DEK2 = DEK. 2) When DEK1 = DEK
and DEK2 = 0, the data deduction is controlled independently by the AP. 3) Data
deduplication when DEK1 ≠ null, DEK2 ≠ null and DEK1∥DEK2 = DEK is regulated by the
data owner with the AP. 4) DEK1 = DEK2 = DEK deduplication is handled by the AP or data
owner.
5) When DEK1 = DEK2 = DEK = null, the plaintext of the data owner is stored in the CSP
without any special control.
4.2 Fundamental Algorithms:
A variety of basic algorithms for the suggested scheme are presented in this section.
Initiate System: The algorithm will be performed at the KGC. It produces major ABE and
PRE frameworks, like generators and widespread attributes, and so forth.
Initiate Node(u): Based on system settings, cloud user u produces its own key pairs
comprising PKu and SKu used for ABE encryption and user decryption key issuance, PKC
key pair pk'u and SK'u key for signing, pku and sku for PRE code generation, etc.
Setup Node(u): This strategy performs numerous client certifications, Cert(PKu), Cert[PK
′u] and Cert(pku) at KGC yield, and might be checked by CSPs and their clients, utilizing hub
character u and public keys for input.
Initiate AP: AP begins with pkAP and skAP generation. PkAP is sent to CSP user.
SOFTWARE AND HARDWARE REQUIREMENT
Hardware requirements:
Processer : Any Update Processer
Ram : Min 1 GB
Hard Disk : Min 100 GB
Software requirements:
Operating System : Windows family
Technology : Java (1.7/1.8)
Front-End Technologies : Html, Html-5, JavaScript, CSS.
56
information from supported CSP clients.
DEK can be divided into various parts that are processed by several gatherings
approved based on the information management strategy set by the information owner. We
will explain the strategy by dividing DEK into two areas to work with the programs DEK1
and DEK2. You can flexibly provide applications in the following cases. 1) The data owner
confirms data deduplication only if DEK1 is null and DEK2 = DEK. 2) When DEK1 = DEK
and DEK2 = 0, the data deduction is controlled independently by the AP. 3) Data
deduplication when DEK1 ≠ null, DEK2 ≠ null and DEK1∥DEK2 = DEK is regulated by the
data owner with the AP. 4) DEK1 = DEK2 = DEK deduplication is handled by the AP or data
owner.
5) When DEK1 = DEK2 = DEK = null, the plaintext of the data owner is stored in the CSP
without any special control.
4.2 Fundamental Algorithms:
A variety of basic algorithms for the suggested scheme are presented in this section.
Initiate System: The algorithm will be performed at the KGC. It produces major ABE and
PRE frameworks, like generators and widespread attributes, and so forth.
Initiate Node(u): Based on system settings, cloud user u produces its own key pairs
comprising PKu and SKu used for ABE encryption and user decryption key issuance, PKC
key pair pk'u and SK'u key for signing, pku and sku for PRE code generation, etc.
Setup Node(u): This strategy performs numerous client certifications, Cert(PKu), Cert[PK
′u] and Cert(pku) at KGC yield, and might be checked by CSPs and their clients, utilizing hub
character u and public keys for input.
Initiate AP: AP begins with pkAP and skAP generation. PkAP is sent to CSP user.
SOFTWARE AND HARDWARE REQUIREMENT
Hardware requirements:
Processer : Any Update Processer
Ram : Min 1 GB
Hard Disk : Min 100 GB
Software requirements:
Operating System : Windows family
Technology : Java (1.7/1.8)
Front-End Technologies : Html, Html-5, JavaScript, CSS.
56

Application Server : Tomcat 7/8
Database (Back – End) : My SQL5.5
IDE : Edit Plus
4.4 FUNCTIONAL REQUIREMENTS
KGC:
KGC is a system setup environment, where it will provide the DSA(PKIu, SKIu) and
ABE(PKu, SKu) key generation pair to the cloud services providers in the network.
AP:
AP is the Authorized Party that will create the Key pairs of the PKap and SKap. PKap
will be sent to the cloud services on request.
CSP:
(CSP) offering support for information stockpiling. In the framework, there may be a
few CSPs. A cloud client may subsequently pick one to deal with his/her transferred
information and quest for upgraded insight. To store space by deduplication saving,
CSPs can likewise work together under a business game plan.
Data Holder:
It will display the list of data owners and to which cloud service provider they are
connected to.
Login:
CSP registered users can use this option to login into the cloud and can upload the
data files at the cloud end
Registration:
Using this option new users can register to the CSP Services.
Storage Files:
This will display the files of the users who have been uploaded to the server without
any duplicates in it.
Profile:
Using this option user can check their profiles.
Upload:
Using this option user can upload the new documents to the cloud with the two DSA
folded encryption.
Download:
Genuine users can decrypt the files by requesting it to the AP, when the AP generates
the key pairs they can download with the genuine key pairs.
57
Database (Back – End) : My SQL5.5
IDE : Edit Plus
4.4 FUNCTIONAL REQUIREMENTS
KGC:
KGC is a system setup environment, where it will provide the DSA(PKIu, SKIu) and
ABE(PKu, SKu) key generation pair to the cloud services providers in the network.
AP:
AP is the Authorized Party that will create the Key pairs of the PKap and SKap. PKap
will be sent to the cloud services on request.
CSP:
(CSP) offering support for information stockpiling. In the framework, there may be a
few CSPs. A cloud client may subsequently pick one to deal with his/her transferred
information and quest for upgraded insight. To store space by deduplication saving,
CSPs can likewise work together under a business game plan.
Data Holder:
It will display the list of data owners and to which cloud service provider they are
connected to.
Login:
CSP registered users can use this option to login into the cloud and can upload the
data files at the cloud end
Registration:
Using this option new users can register to the CSP Services.
Storage Files:
This will display the files of the users who have been uploaded to the server without
any duplicates in it.
Profile:
Using this option user can check their profiles.
Upload:
Using this option user can upload the new documents to the cloud with the two DSA
folded encryption.
Download:
Genuine users can decrypt the files by requesting it to the AP, when the AP generates
the key pairs they can download with the genuine key pairs.
57
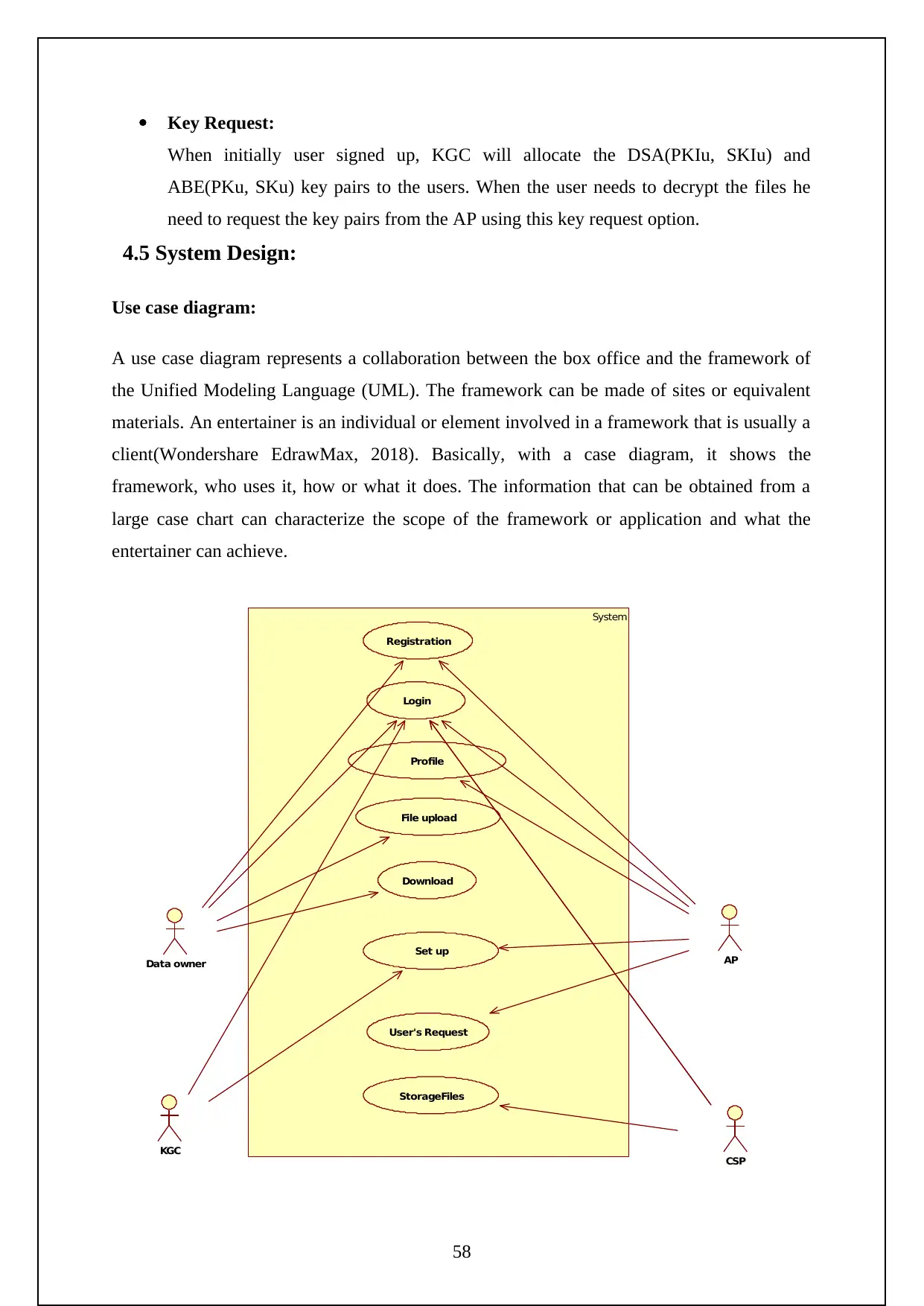
Key Request:
When initially user signed up, KGC will allocate the DSA(PKIu, SKIu) and
ABE(PKu, SKu) key pairs to the users. When the user needs to decrypt the files he
need to request the key pairs from the AP using this key request option.
4.5 System Design:
Use case diagram:
A use case diagram represents a collaboration between the box office and the framework of
the Unified Modeling Language (UML). The framework can be made of sites or equivalent
materials. An entertainer is an individual or element involved in a framework that is usually a
client(Wondershare EdrawMax, 2018). Basically, with a case diagram, it shows the
framework, who uses it, how or what it does. The information that can be obtained from a
large case chart can characterize the scope of the framework or application and what the
entertainer can achieve.
System
AP
Login
Profile
File upload
Set up
Data owner
CSP
StorageFiles
User's Request
KGC
Registration
Download
58
When initially user signed up, KGC will allocate the DSA(PKIu, SKIu) and
ABE(PKu, SKu) key pairs to the users. When the user needs to decrypt the files he
need to request the key pairs from the AP using this key request option.
4.5 System Design:
Use case diagram:
A use case diagram represents a collaboration between the box office and the framework of
the Unified Modeling Language (UML). The framework can be made of sites or equivalent
materials. An entertainer is an individual or element involved in a framework that is usually a
client(Wondershare EdrawMax, 2018). Basically, with a case diagram, it shows the
framework, who uses it, how or what it does. The information that can be obtained from a
large case chart can characterize the scope of the framework or application and what the
entertainer can achieve.
System
AP
Login
Profile
File upload
Set up
Data owner
CSP
StorageFiles
User's Request
KGC
Registration
Download
58
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
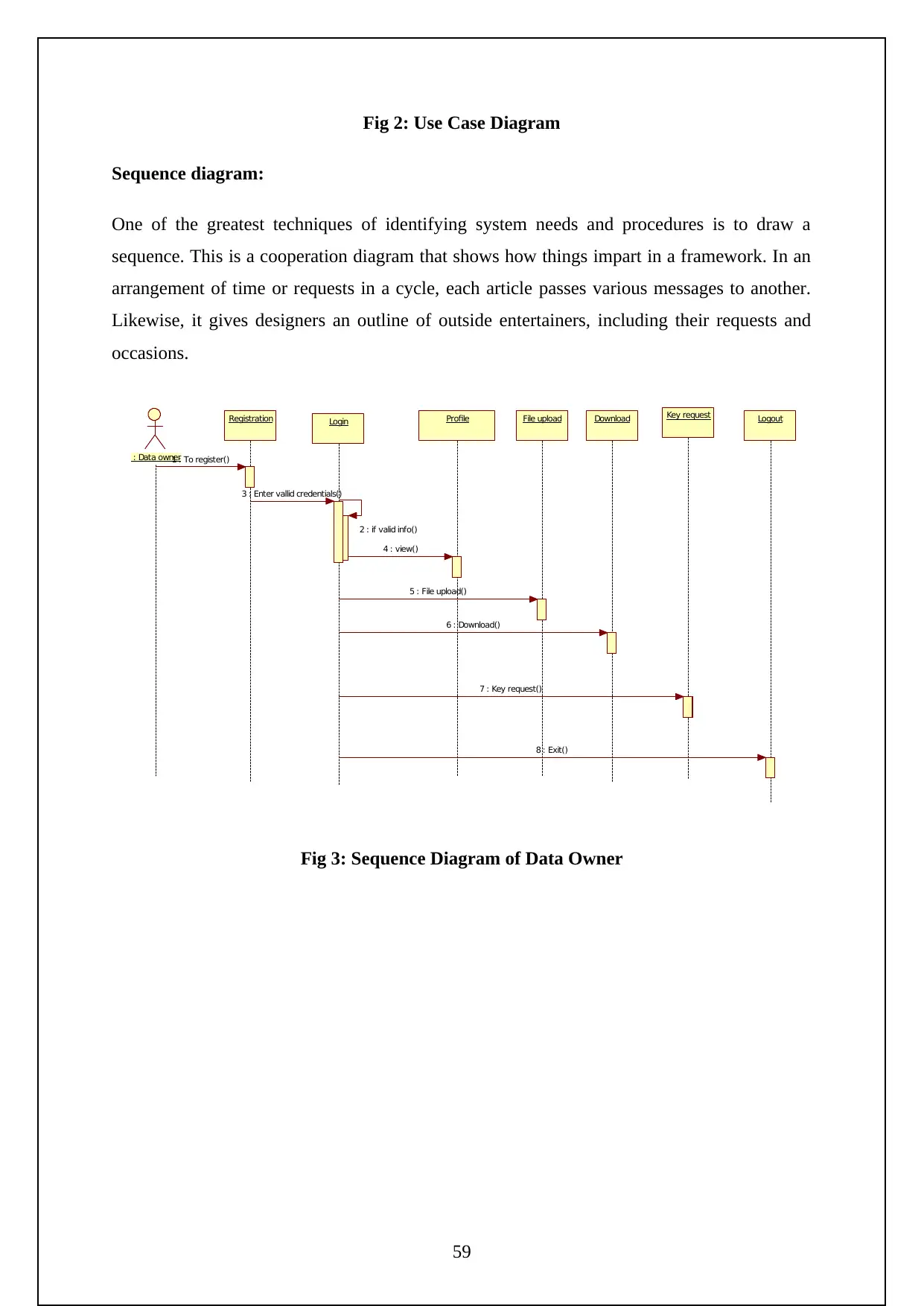
Fig 2: Use Case Diagram
Sequence diagram:
One of the greatest techniques of identifying system needs and procedures is to draw a
sequence. This is a cooperation diagram that shows how things impart in a framework. In an
arrangement of time or requests in a cycle, each article passes various messages to another.
Likewise, it gives designers an outline of outside entertainers, including their requests and
occasions.
Login Profile LogoutRegistration
: Data owner
File upload Download Key request
1 : To register()
2 : if valid info()
3 : Enter vallid credentials()
4 : view()
5 : File upload()
6 : Download()
7 : Key request()
8 : Exit()
Fig 3: Sequence Diagram of Data Owner
59
Sequence diagram:
One of the greatest techniques of identifying system needs and procedures is to draw a
sequence. This is a cooperation diagram that shows how things impart in a framework. In an
arrangement of time or requests in a cycle, each article passes various messages to another.
Likewise, it gives designers an outline of outside entertainers, including their requests and
occasions.
Login Profile LogoutRegistration
: Data owner
File upload Download Key request
1 : To register()
2 : if valid info()
3 : Enter vallid credentials()
4 : view()
5 : File upload()
6 : Download()
7 : Key request()
8 : Exit()
Fig 3: Sequence Diagram of Data Owner
59
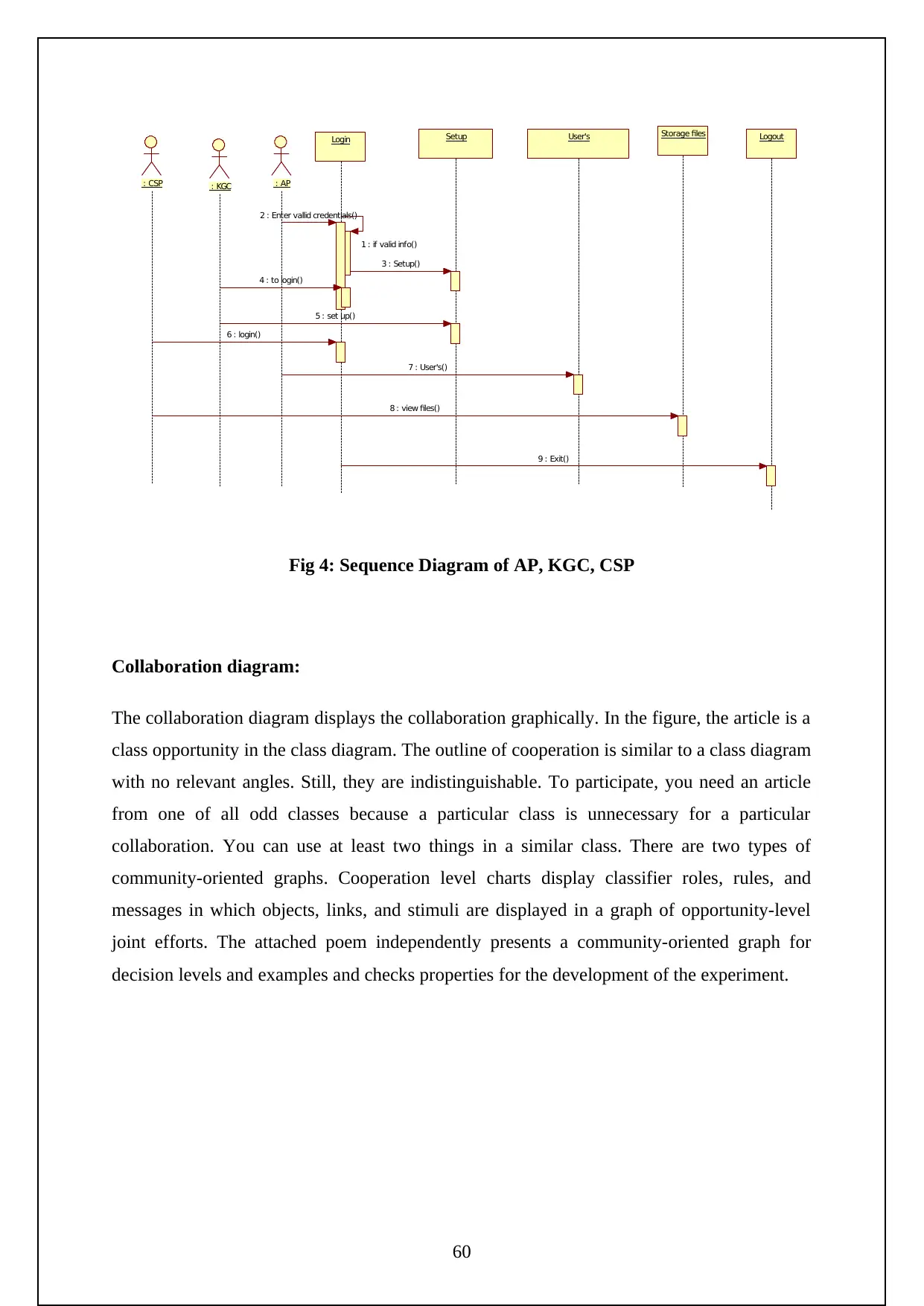
Login Setup LogoutUser's Storage files
: CSP : AP: KGC
1 : if valid info()
2 : Enter vallid credentials()
3 : Setup()
4 : to login()
5 : set up()
6 : login()
7 : User's()
8 : view files()
9 : Exit()
Fig 4: Sequence Diagram of AP, KGC, CSP
Collaboration diagram:
The collaboration diagram displays the collaboration graphically. In the figure, the article is a
class opportunity in the class diagram. The outline of cooperation is similar to a class diagram
with no relevant angles. Still, they are indistinguishable. To participate, you need an article
from one of all odd classes because a particular class is unnecessary for a particular
collaboration. You can use at least two things in a similar class. There are two types of
community-oriented graphs. Cooperation level charts display classifier roles, rules, and
messages in which objects, links, and stimuli are displayed in a graph of opportunity-level
joint efforts. The attached poem independently presents a community-oriented graph for
decision levels and examples and checks properties for the development of the experiment.
60
: CSP : AP: KGC
1 : if valid info()
2 : Enter vallid credentials()
3 : Setup()
4 : to login()
5 : set up()
6 : login()
7 : User's()
8 : view files()
9 : Exit()
Fig 4: Sequence Diagram of AP, KGC, CSP
Collaboration diagram:
The collaboration diagram displays the collaboration graphically. In the figure, the article is a
class opportunity in the class diagram. The outline of cooperation is similar to a class diagram
with no relevant angles. Still, they are indistinguishable. To participate, you need an article
from one of all odd classes because a particular class is unnecessary for a particular
collaboration. You can use at least two things in a similar class. There are two types of
community-oriented graphs. Cooperation level charts display classifier roles, rules, and
messages in which objects, links, and stimuli are displayed in a graph of opportunity-level
joint efforts. The attached poem independently presents a community-oriented graph for
decision levels and examples and checks properties for the development of the experiment.
60
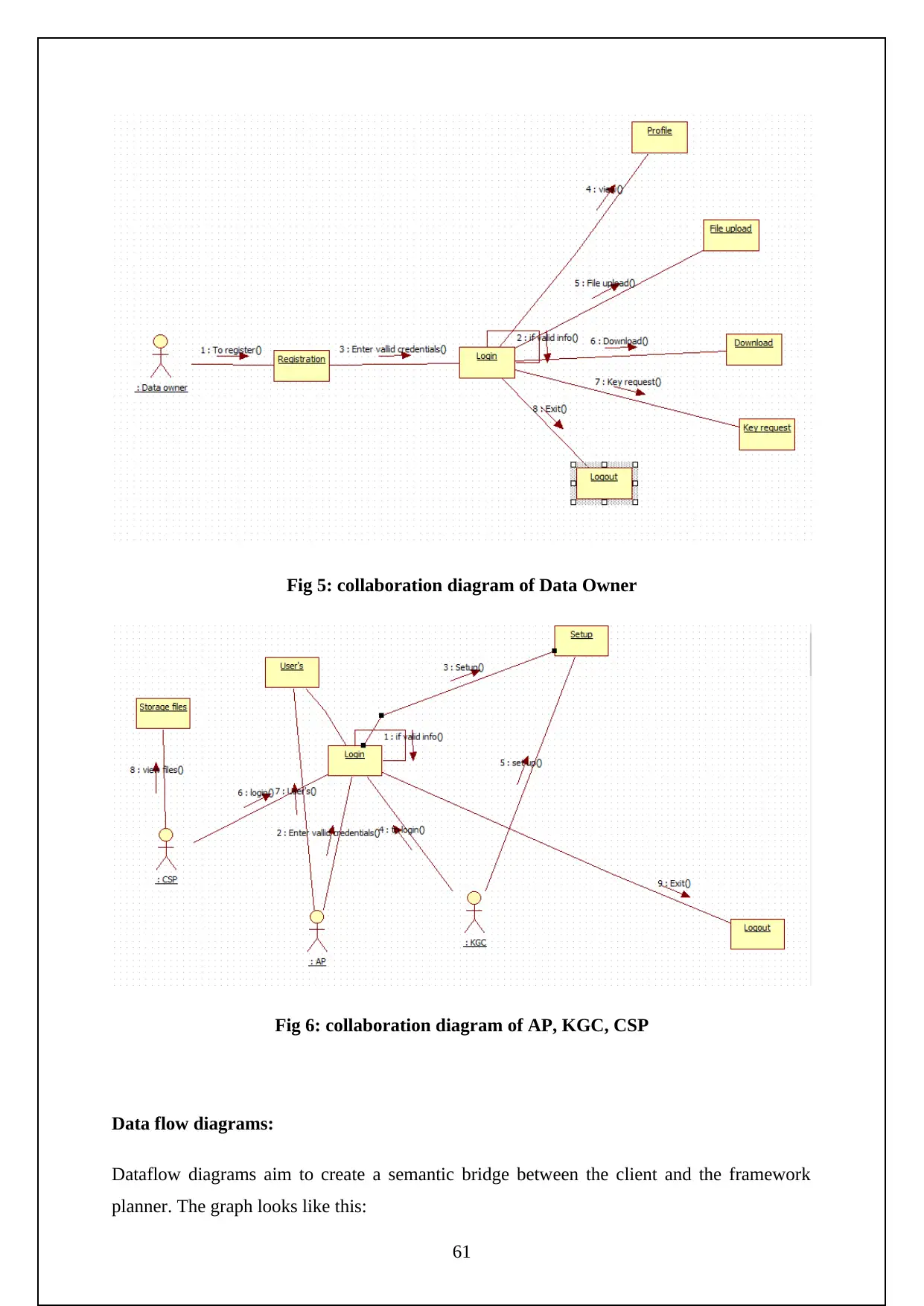
Fig 5: collaboration diagram of Data Owner
Fig 6: collaboration diagram of AP, KGC, CSP
Data flow diagrams:
Dataflow diagrams aim to create a semantic bridge between the client and the framework
planner. The graph looks like this:
61
Fig 6: collaboration diagram of AP, KGC, CSP
Data flow diagrams:
Dataflow diagrams aim to create a semantic bridge between the client and the framework
planner. The graph looks like this:
61
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
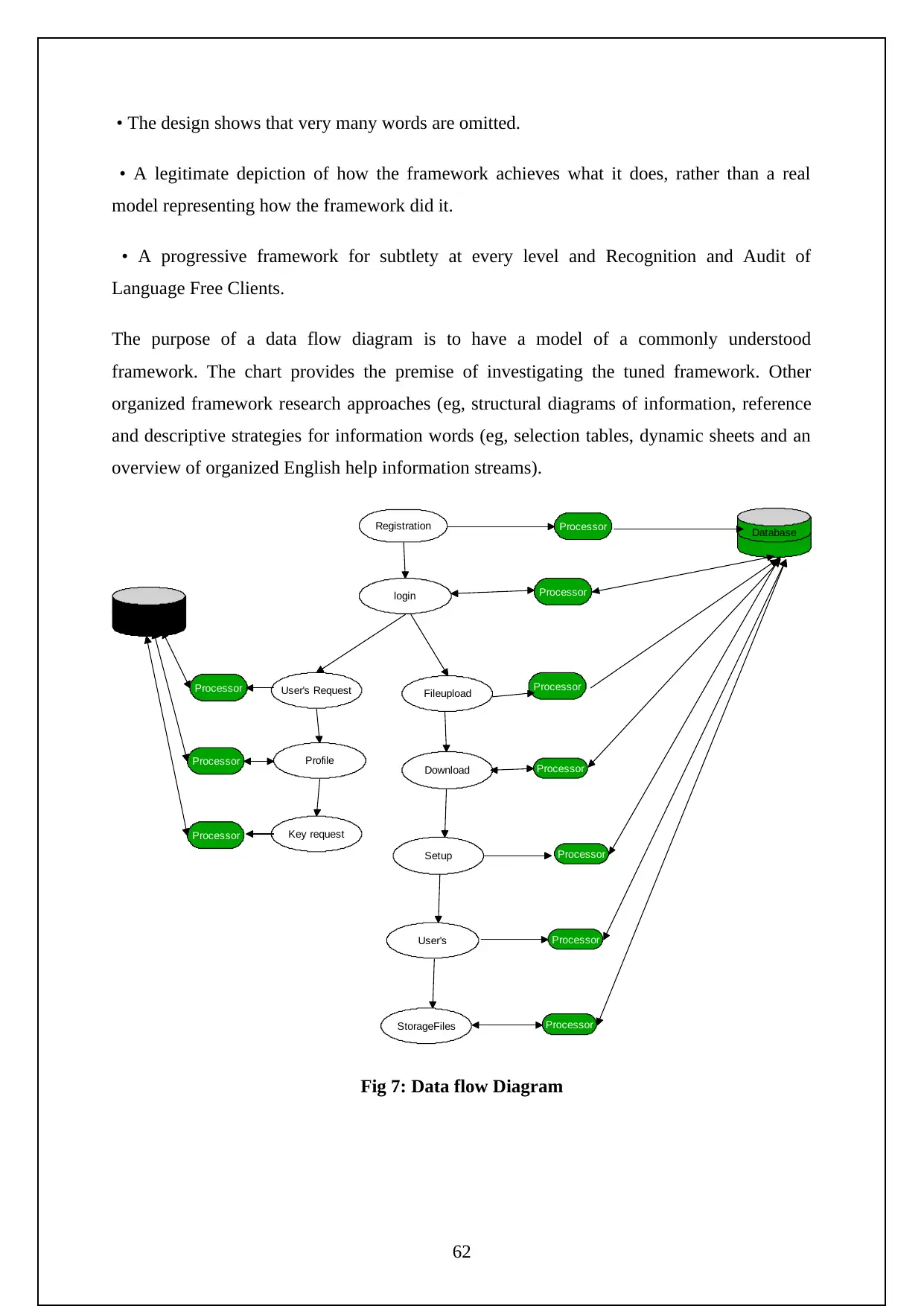
• The design shows that very many words are omitted.
• A legitimate depiction of how the framework achieves what it does, rather than a real
model representing how the framework did it.
• A progressive framework for subtlety at every level and Recognition and Audit of
Language Free Clients.
The purpose of a data flow diagram is to have a model of a commonly understood
framework. The chart provides the premise of investigating the tuned framework. Other
organized framework research approaches (eg, structural diagrams of information, reference
and descriptive strategies for information words (eg, selection tables, dynamic sheets and an
overview of organized English help information streams).
Registration Processor Database
login Processor
Processor
Processor
Processor
Database
Processor
Processor
Processor
User's Request
Key request
Profile
Fileupload
Download
Setup
ProcessorUser's
ProcessorStorageFiles
Fig 7: Data flow Diagram
62
• A legitimate depiction of how the framework achieves what it does, rather than a real
model representing how the framework did it.
• A progressive framework for subtlety at every level and Recognition and Audit of
Language Free Clients.
The purpose of a data flow diagram is to have a model of a commonly understood
framework. The chart provides the premise of investigating the tuned framework. Other
organized framework research approaches (eg, structural diagrams of information, reference
and descriptive strategies for information words (eg, selection tables, dynamic sheets and an
overview of organized English help information streams).
Registration Processor Database
login Processor
Processor
Processor
Processor
Database
Processor
Processor
Processor
User's Request
Key request
Profile
Fileupload
Download
Setup
ProcessorUser's
ProcessorStorageFiles
Fig 7: Data flow Diagram
62

4.6 TECHNOLOGIES USED:
Java:
Java is a programming language used to improve applications on PCs. A major public
execution was provided in 1995 by Sun Microsystems under the name Java1.0. It gives the
execution time of a critical step sans cost, it claims, "write once, run anywhere". Similarly, it
is often used to build entire applications that run on a single machine and can be distributed
across an organization's workers and clients. After procuring Sun Microsystems on January
27, 2010, Oracle Corporation is now responsible for the entitlement execution of the Java SE
stage. According to the Prophet, Java is probably the most mainstream programming dialect
in use since 2016, especially with online applications from client workers and 9 million
engineers.
JSP:
JSP is a Java server page. Dynamic web applications are used for these innovations. Using
the JSP label, the JSP adds Java code to the HTML. Both worker-side JSPs and Html can be
used to switch between customer-side events. JSP allows you to develop tag-based HTML
code that can integrate modern Java applications. JSP makes it easy to isolate the rationale of
your show business, because the experts on your website can create and update your JSP
show layer pages.
SQL:
A structured query language (commonly referred to as SQL) is a language used in connected
datasets to evaluate, control, control, and interrogate the characteristics of the data. Since its
creation in the mid-1970s, SQL has gained widespread acceptance and is now the primary
language used for interacting with social data set management frameworks. SQL is the right
answer for the management of organized information that fits well with the current
information model. Understanding how to use SQL in different settings is an important skill
for engineers and framework administrators(Drake, 2020). The SQL standard is characterized
by two things: the American Standards Institute (ANSI) and the International Organization
for Standardization (ISO). Nevertheless, social information-based management frameworks
generally execute a unique subset of SQL that rarely meets SQL instructions. Despite the fact
that it provides the client with functionality that is important not to open in other SQL
63
Java:
Java is a programming language used to improve applications on PCs. A major public
execution was provided in 1995 by Sun Microsystems under the name Java1.0. It gives the
execution time of a critical step sans cost, it claims, "write once, run anywhere". Similarly, it
is often used to build entire applications that run on a single machine and can be distributed
across an organization's workers and clients. After procuring Sun Microsystems on January
27, 2010, Oracle Corporation is now responsible for the entitlement execution of the Java SE
stage. According to the Prophet, Java is probably the most mainstream programming dialect
in use since 2016, especially with online applications from client workers and 9 million
engineers.
JSP:
JSP is a Java server page. Dynamic web applications are used for these innovations. Using
the JSP label, the JSP adds Java code to the HTML. Both worker-side JSPs and Html can be
used to switch between customer-side events. JSP allows you to develop tag-based HTML
code that can integrate modern Java applications. JSP makes it easy to isolate the rationale of
your show business, because the experts on your website can create and update your JSP
show layer pages.
SQL:
A structured query language (commonly referred to as SQL) is a language used in connected
datasets to evaluate, control, control, and interrogate the characteristics of the data. Since its
creation in the mid-1970s, SQL has gained widespread acceptance and is now the primary
language used for interacting with social data set management frameworks. SQL is the right
answer for the management of organized information that fits well with the current
information model. Understanding how to use SQL in different settings is an important skill
for engineers and framework administrators(Drake, 2020). The SQL standard is characterized
by two things: the American Standards Institute (ANSI) and the International Organization
for Standardization (ISO). Nevertheless, social information-based management frameworks
generally execute a unique subset of SQL that rarely meets SQL instructions. Despite the fact
that it provides the client with functionality that is important not to open in other SQL
63
executions, the exceptional highlight of SQL extensions is well remembered in these special
arrays.
SQL Schema
Authorized Party SQL Schema:
Cloud Service Provider (CSP1) SQL Schema:
Cloud Service Provider (CSP2) SQL Schema:
Cloud Service Provider (CSP3) SQL Schema:
Registration SQL Schema:
64
arrays.
SQL Schema
Authorized Party SQL Schema:
Cloud Service Provider (CSP1) SQL Schema:
Cloud Service Provider (CSP2) SQL Schema:
Cloud Service Provider (CSP3) SQL Schema:
Registration SQL Schema:
64
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

File Request for DEK1 SQL Schema:
File Request for DEK2 SQL Schema:
File Sharing SQL Schema:
5. ETHICAL, PROFESSIONAL AND
LEGAL ISSUES
Ethical Issues:
While computer morals are a set of superior rules governing the use of PCs, ethics can be
described as codes of conduct in human behavior. As superior rules are related with the use
of internet and computers so these would be counted as moral and ethical concerns with
regard to computers (Moor, 2017). These may includes using of intellectual property rights,
privacy policy and various others. These rules are connected with the aspect of ethical moral
principles with the use of computers. New innovations regularly result in new mechanical
breakdowns and new moral problems. Exchange Innovations Fast-growing external risks will
65
File Request for DEK2 SQL Schema:
File Sharing SQL Schema:
5. ETHICAL, PROFESSIONAL AND
LEGAL ISSUES
Ethical Issues:
While computer morals are a set of superior rules governing the use of PCs, ethics can be
described as codes of conduct in human behavior. As superior rules are related with the use
of internet and computers so these would be counted as moral and ethical concerns with
regard to computers (Moor, 2017). These may includes using of intellectual property rights,
privacy policy and various others. These rules are connected with the aspect of ethical moral
principles with the use of computers. New innovations regularly result in new mechanical
breakdowns and new moral problems. Exchange Innovations Fast-growing external risks will
65

probably change much faster than insurance. How much of the general freedoms are affected
by distributed computing depends on the kind of management provided by the vendor.
Distributed computing first evolved in the mid-1950s, but fast organizations and more
famous information storage spaces have been supporting cloud-based application changes
from normal processing (Trope & Ray, 2010). Since computers have no in-build rules but
with regard to the use of computer there are certain moral principles and rules. The rules that
will be implied with the moral principles includes use of computers that will not harm the
others, non-interference in other work, no use of computer for steal, and various others
(Ferreira and Vardi, 2020). Several moral questions can arise about certain parts of the Web
that have been found to dominate its proliferation in distributed computing scaling. One of
the important issues to be investigated is that distributed computing will enable partnerships
and the ability to obtain data and individual data from a variety of people without
fundamentally notifying them that they are accessing the data.
Legal Issues:
The most difficult legal issues of cloud-based technology are as follows:
Security procedure:
Most associations that are using consent and management of the cloud are not security
measures. You need components to support or evaluate cloud applications. For
example, when organizations adopt the BYOD pattern, they need such security
rehearsals as never before. Some of the possible outcomes open to information in
organizations include general information security preparations, different levels of
security, and difficult cycles of sending or copying information using gadgets.
Basically, security measures should be characterized according to the points and work
processes of all associations.
Third-party access issues:
Outsider investment can be dangerous. Allows a small number of residents to use a
common cloud for all outsiders to use a similar management interface to access
multifaceted validation and enhanced security. Similarly, search for providers that
agree with HIPAA (RICK’S CLOUD, 2013). External business partner agreements
are important to ensure protection and security guidelines with external providers who
enter protected health information. A viable way to do this effectively and ensure that
66
by distributed computing depends on the kind of management provided by the vendor.
Distributed computing first evolved in the mid-1950s, but fast organizations and more
famous information storage spaces have been supporting cloud-based application changes
from normal processing (Trope & Ray, 2010). Since computers have no in-build rules but
with regard to the use of computer there are certain moral principles and rules. The rules that
will be implied with the moral principles includes use of computers that will not harm the
others, non-interference in other work, no use of computer for steal, and various others
(Ferreira and Vardi, 2020). Several moral questions can arise about certain parts of the Web
that have been found to dominate its proliferation in distributed computing scaling. One of
the important issues to be investigated is that distributed computing will enable partnerships
and the ability to obtain data and individual data from a variety of people without
fundamentally notifying them that they are accessing the data.
Legal Issues:
The most difficult legal issues of cloud-based technology are as follows:
Security procedure:
Most associations that are using consent and management of the cloud are not security
measures. You need components to support or evaluate cloud applications. For
example, when organizations adopt the BYOD pattern, they need such security
rehearsals as never before. Some of the possible outcomes open to information in
organizations include general information security preparations, different levels of
security, and difficult cycles of sending or copying information using gadgets.
Basically, security measures should be characterized according to the points and work
processes of all associations.
Third-party access issues:
Outsider investment can be dangerous. Allows a small number of residents to use a
common cloud for all outsiders to use a similar management interface to access
multifaceted validation and enhanced security. Similarly, search for providers that
agree with HIPAA (RICK’S CLOUD, 2013). External business partner agreements
are important to ensure protection and security guidelines with external providers who
enter protected health information. A viable way to do this effectively and ensure that
66
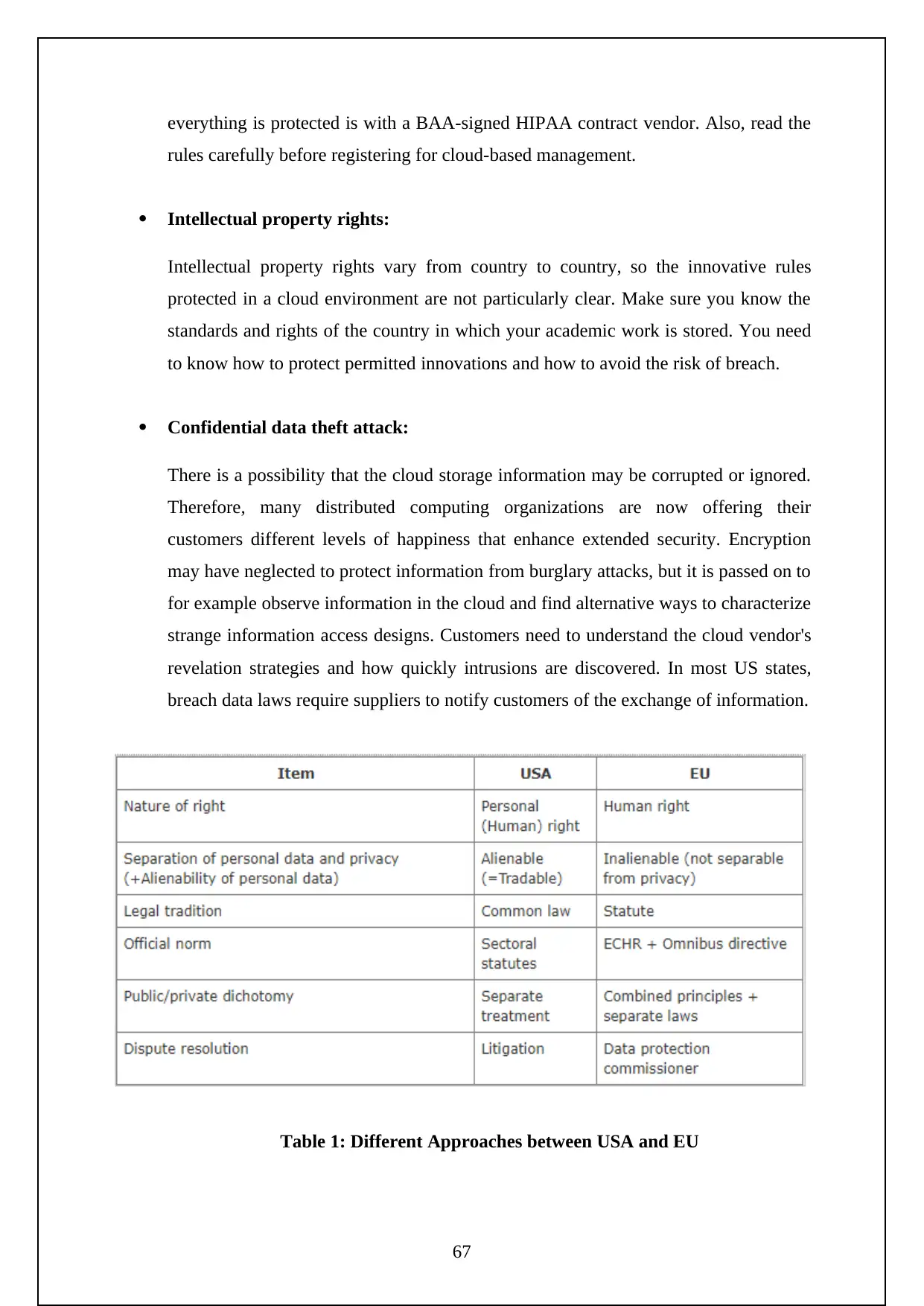
everything is protected is with a BAA-signed HIPAA contract vendor. Also, read the
rules carefully before registering for cloud-based management.
Intellectual property rights:
Intellectual property rights vary from country to country, so the innovative rules
protected in a cloud environment are not particularly clear. Make sure you know the
standards and rights of the country in which your academic work is stored. You need
to know how to protect permitted innovations and how to avoid the risk of breach.
Confidential data theft attack:
There is a possibility that the cloud storage information may be corrupted or ignored.
Therefore, many distributed computing organizations are now offering their
customers different levels of happiness that enhance extended security. Encryption
may have neglected to protect information from burglary attacks, but it is passed on to
for example observe information in the cloud and find alternative ways to characterize
strange information access designs. Customers need to understand the cloud vendor's
revelation strategies and how quickly intrusions are discovered. In most US states,
breach data laws require suppliers to notify customers of the exchange of information.
Table 1: Different Approaches between USA and EU
67
rules carefully before registering for cloud-based management.
Intellectual property rights:
Intellectual property rights vary from country to country, so the innovative rules
protected in a cloud environment are not particularly clear. Make sure you know the
standards and rights of the country in which your academic work is stored. You need
to know how to protect permitted innovations and how to avoid the risk of breach.
Confidential data theft attack:
There is a possibility that the cloud storage information may be corrupted or ignored.
Therefore, many distributed computing organizations are now offering their
customers different levels of happiness that enhance extended security. Encryption
may have neglected to protect information from burglary attacks, but it is passed on to
for example observe information in the cloud and find alternative ways to characterize
strange information access designs. Customers need to understand the cloud vendor's
revelation strategies and how quickly intrusions are discovered. In most US states,
breach data laws require suppliers to notify customers of the exchange of information.
Table 1: Different Approaches between USA and EU
67
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Professional Issues:
The vast amount of information and distributed computing as a better imaginative way to
build client efficiency and joy is slowly being appreciated by financial experts and academia.
“All the while, I have serious concerns with conservationists and even clients as a whole, and
an important topic in any field of logical investigation is how to track the right balance. In
any case, the enigmatic idea of what constitutes the basic elements of protection has rarely
been considered.
The first step in understanding overall security is to recognize the individual data of
protection. Although the contrast between security and privacy protection is still more
fundamental, the two ideas are mostly mutually exclusive(Hayashi, 2013). Confidentiality is
one of the CIA's main requirements when individuals discuss management security, and we
believe that security guarantees the protection of personal information.
Cloud information infrastructure protection and information wellness are key issues to
remove and supervise disruptive information so that it can participate in a secure platform. `A
cloud database, an innovation that joins the world of distributed computing, presents
protection and security issues such as the absence of information and information authority,
exchange logging, and hostile behavior(Izang et al., 2017). The moral issues of the cloud also
include trust issues. Residents do not contribute to the outside, and it is difficult to occupy
important data to a cloud specialized institution, so the number of residents.
6. RESULTS AND DISCUSSION
6.1 Access Control Techniques:
Encrypted Data Access Control:
Existing studies have suggested scrambling information in the cloud before leaving CSP
information security. Access control of encrypted requests for information that can only
interpret scrambled information on approved substances. In a perfect world, each piece of
information would have to be encoded once, and the underlying key would have to be given
only once to an approved substance. Nevertheless, a common significant redesign of the
volatility of confidence confuses key management. Access control records (ACLs) have been
enforced to gain information security from suspicious or semi-trusted collections. The
information owner just orders the information from the various collections and forwards them
to the client in the collection ACLs before sending the information to the CSP(Yan et al.,
2019a), scrambles each collection with an even key. This collection of information is along
68
The vast amount of information and distributed computing as a better imaginative way to
build client efficiency and joy is slowly being appreciated by financial experts and academia.
“All the while, I have serious concerns with conservationists and even clients as a whole, and
an important topic in any field of logical investigation is how to track the right balance. In
any case, the enigmatic idea of what constitutes the basic elements of protection has rarely
been considered.
The first step in understanding overall security is to recognize the individual data of
protection. Although the contrast between security and privacy protection is still more
fundamental, the two ideas are mostly mutually exclusive(Hayashi, 2013). Confidentiality is
one of the CIA's main requirements when individuals discuss management security, and we
believe that security guarantees the protection of personal information.
Cloud information infrastructure protection and information wellness are key issues to
remove and supervise disruptive information so that it can participate in a secure platform. `A
cloud database, an innovation that joins the world of distributed computing, presents
protection and security issues such as the absence of information and information authority,
exchange logging, and hostile behavior(Izang et al., 2017). The moral issues of the cloud also
include trust issues. Residents do not contribute to the outside, and it is difficult to occupy
important data to a cloud specialized institution, so the number of residents.
6. RESULTS AND DISCUSSION
6.1 Access Control Techniques:
Encrypted Data Access Control:
Existing studies have suggested scrambling information in the cloud before leaving CSP
information security. Access control of encrypted requests for information that can only
interpret scrambled information on approved substances. In a perfect world, each piece of
information would have to be encoded once, and the underlying key would have to be given
only once to an approved substance. Nevertheless, a common significant redesign of the
volatility of confidence confuses key management. Access control records (ACLs) have been
enforced to gain information security from suspicious or semi-trusted collections. The
information owner just orders the information from the various collections and forwards them
to the client in the collection ACLs before sending the information to the CSP(Yan et al.,
2019a), scrambles each collection with an even key. This collection of information is along
68

these lines, making it easily accessible to ACL clients. There are drawbacks to this technique,
mainly because the number of symmetric keys increases with the amount of collection.
Additionally, by reconciling the trust connection between one client and the owner of the
information, the appropriate symmetric key is updated by default to affect additional clients
with the same ACL. In many real-world applications where trust relationships between
different clients are constantly changing, this step won't work forever. Cloud information
access control is proposed to integrate standard symmetric encryption systems with biased
encryption frameworks. The estimated cost of key encryption developing everything is
considered to be represented by the number of ACL clients.
Attribute-based encryption (ABE) for access control of cloud-encoded data has been
proposed. It characterizes different qualities for differentiating clients in such a way that they
encode information that depends on a particular property access structure. Therefore, only
clients that have the characteristics to satisfy the inlet structure can unravel the encoded
information. ABE has two types: ABE key method and ABE ciphertext strategy and is
controlled by linking attributes to ciphertext and decryption key. ABE highlights diversity
and adaptability when it comes to entry guidelines that rely on the management of properties
and access crops. In recent years, it has been available several times for the safe storage of
cloud information. In any case, any consent that made it possible to access the contextual
access control of scrambled information especially encoded data storage did not examine how
to address the problem of copy information stored in the cloud in a comprehensive and
complete manner. To safely stockpile massive amounts of information in the cloud, this issue
is fundamentally important.
Encryption Data De-duplication:
It is under investigation to support client-side allowances and encryption. The need to
deduplicate information can be similarly used by measurable examiners for the recovery of
evidence from cloud management. There are up-to-date answers on scrambled info from
Dropbox, Google Drives, Mozy, etc, but they neglect to deduct. To alleviate this problem,
Message Locked Encryption (MLE) has been proposed. The main MLE indication is that
Converged Encryption (CE) has been sent. The client uses CE to calculate information M
according to the hash code K ← H (M) (Yan et al., 2019) and encrypts M to K. Other clients
with indistinguishable information can deduct after generating the same encoded information.
CE, relying on mutilated brutal word reference attacks. So if your primary data is to assemble
in a vast exhaust space, the CE can probably provide great security. Additionally, access to
69
mainly because the number of symmetric keys increases with the amount of collection.
Additionally, by reconciling the trust connection between one client and the owner of the
information, the appropriate symmetric key is updated by default to affect additional clients
with the same ACL. In many real-world applications where trust relationships between
different clients are constantly changing, this step won't work forever. Cloud information
access control is proposed to integrate standard symmetric encryption systems with biased
encryption frameworks. The estimated cost of key encryption developing everything is
considered to be represented by the number of ACL clients.
Attribute-based encryption (ABE) for access control of cloud-encoded data has been
proposed. It characterizes different qualities for differentiating clients in such a way that they
encode information that depends on a particular property access structure. Therefore, only
clients that have the characteristics to satisfy the inlet structure can unravel the encoded
information. ABE has two types: ABE key method and ABE ciphertext strategy and is
controlled by linking attributes to ciphertext and decryption key. ABE highlights diversity
and adaptability when it comes to entry guidelines that rely on the management of properties
and access crops. In recent years, it has been available several times for the safe storage of
cloud information. In any case, any consent that made it possible to access the contextual
access control of scrambled information especially encoded data storage did not examine how
to address the problem of copy information stored in the cloud in a comprehensive and
complete manner. To safely stockpile massive amounts of information in the cloud, this issue
is fundamentally important.
Encryption Data De-duplication:
It is under investigation to support client-side allowances and encryption. The need to
deduplicate information can be similarly used by measurable examiners for the recovery of
evidence from cloud management. There are up-to-date answers on scrambled info from
Dropbox, Google Drives, Mozy, etc, but they neglect to deduct. To alleviate this problem,
Message Locked Encryption (MLE) has been proposed. The main MLE indication is that
Converged Encryption (CE) has been sent. The client uses CE to calculate information M
according to the hash code K ← H (M) (Yan et al., 2019) and encrypts M to K. Other clients
with indistinguishable information can deduct after generating the same encoded information.
CE, relying on mutilated brutal word reference attacks. So if your primary data is to assemble
in a vast exhaust space, the CE can probably provide great security. Additionally, access to
69

information governed by information owners and other authorized assemblies is not endorsed
by the CE. Denial of information is difficult to implement. since it is difficult for both the
information holder and the information holder to generate such an encryption key to re-
scramble the information.
The existing deduplication strategy was passed by the worker or owner. Smoothing strategies
that benefit from either procedure have been introduced from time to time. The author
recommends a procedure in which only the owner of the information can handle
deduplication. The position control of other information holders relies on determining
metadata explained and provided by qualified clients. Using this method with public key
cryptography creates significant computational complexity, which scales with the volume of
clients and requires adaptability to mandate a unique stockpile situation. is. Another
deduplication sequence of encoded information is Hur et al. Introduced by. Worker side. It
oversees the approval of re-proprietary information and the secure delivery of ownership by
cloud operators using irregular integrated encryption, regardless of whether ownership
changes strongly. Grant permissions. This framework has authenticity in relation to the cloud,
but avoids information that curiosity leaks to rejected clients as well as many employees.
70
by the CE. Denial of information is difficult to implement. since it is difficult for both the
information holder and the information holder to generate such an encryption key to re-
scramble the information.
The existing deduplication strategy was passed by the worker or owner. Smoothing strategies
that benefit from either procedure have been introduced from time to time. The author
recommends a procedure in which only the owner of the information can handle
deduplication. The position control of other information holders relies on determining
metadata explained and provided by qualified clients. Using this method with public key
cryptography creates significant computational complexity, which scales with the volume of
clients and requires adaptability to mandate a unique stockpile situation. is. Another
deduplication sequence of encoded information is Hur et al. Introduced by. Worker side. It
oversees the approval of re-proprietary information and the secure delivery of ownership by
cloud operators using irregular integrated encryption, regardless of whether ownership
changes strongly. Grant permissions. This framework has authenticity in relation to the cloud,
but avoids information that curiosity leaks to rejected clients as well as many employees.
70
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
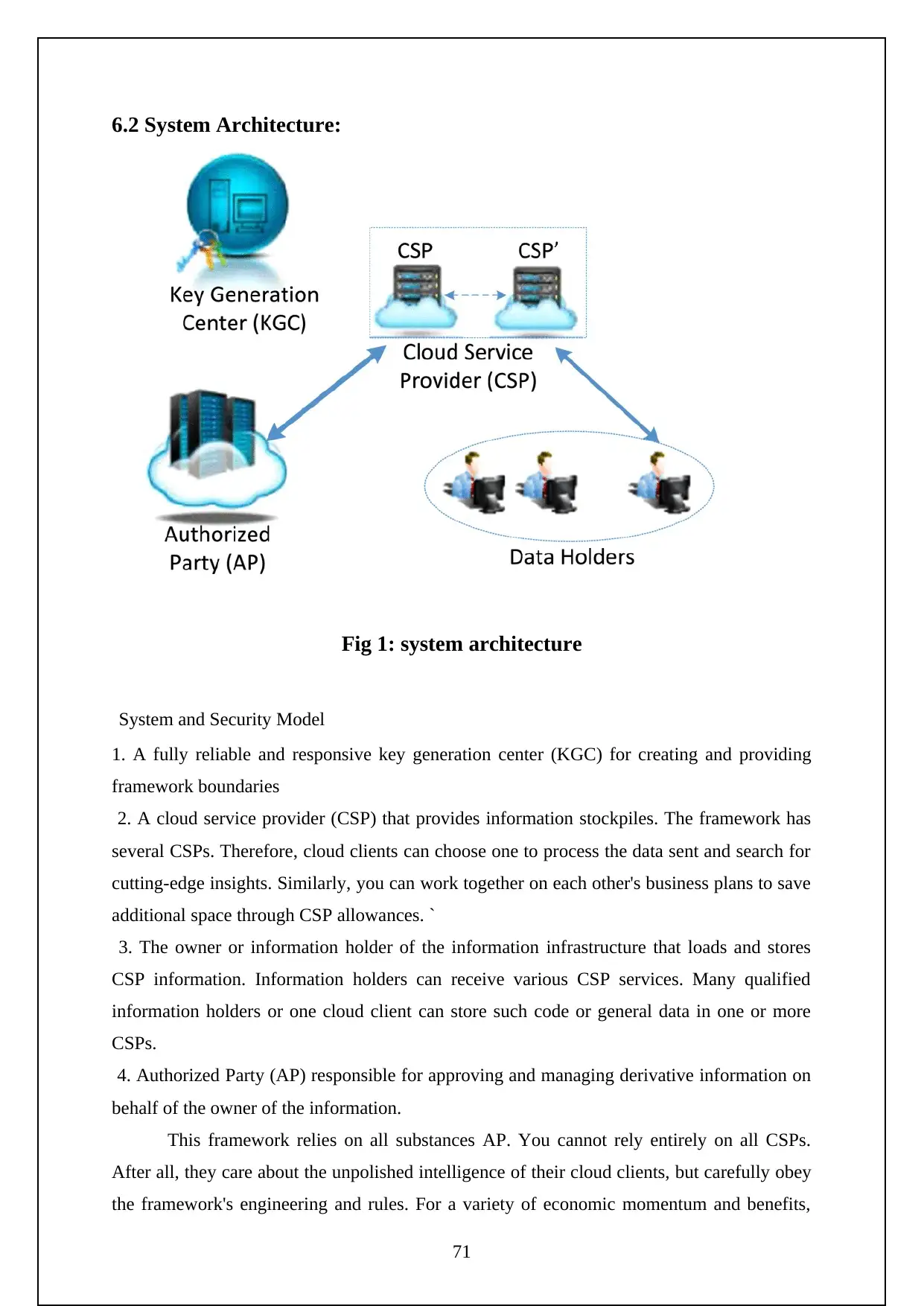
6.2 System Architecture:
Fig 1: system architecture
System and Security Model
1. A fully reliable and responsive key generation center (KGC) for creating and providing
framework boundaries
2. A cloud service provider (CSP) that provides information stockpiles. The framework has
several CSPs. Therefore, cloud clients can choose one to process the data sent and search for
cutting-edge insights. Similarly, you can work together on each other's business plans to save
additional space through CSP allowances. `
3. The owner or information holder of the information infrastructure that loads and stores
CSP information. Information holders can receive various CSP services. Many qualified
information holders or one cloud client can store such code or general data in one or more
CSPs.
4. Authorized Party (AP) responsible for approving and managing derivative information on
behalf of the owner of the information.
This framework relies on all substances AP. You cannot rely entirely on all CSPs.
After all, they care about the unpolished intelligence of their cloud clients, but carefully obey
the framework's engineering and rules. For a variety of economic momentum and benefits,
71
Fig 1: system architecture
System and Security Model
1. A fully reliable and responsive key generation center (KGC) for creating and providing
framework boundaries
2. A cloud service provider (CSP) that provides information stockpiles. The framework has
several CSPs. Therefore, cloud clients can choose one to process the data sent and search for
cutting-edge insights. Similarly, you can work together on each other's business plans to save
additional space through CSP allowances. `
3. The owner or information holder of the information infrastructure that loads and stores
CSP information. Information holders can receive various CSP services. Many qualified
information holders or one cloud client can store such code or general data in one or more
CSPs.
4. Authorized Party (AP) responsible for approving and managing derivative information on
behalf of the owner of the information.
This framework relies on all substances AP. You cannot rely entirely on all CSPs.
After all, they care about the unpolished intelligence of their cloud clients, but carefully obey
the framework's engineering and rules. For a variety of economic momentum and benefits,
71

we anticipate that the AP will never run on the CSP. Joint effort weakens the effectiveness of
CSP and causes unhappiness. The system also accepts this assumption. To verify ownership
of information, information owners provide the correct set of hash codes for their
information. The information owner is the main qualified information holder for the transfer
of information. The framework is likely to exist in any AP and can keep the basic
engineering. I'm assuming it's obvious that one AP can easily see it in the framework. To talk
to each other, CSPs, APs and information owners/owners use scrambled channels. Organized
information is usually sponsored using CSP, and the topic of this paper is not about
information specifically copying to eliminate the risk of space. Appointment understanding
may be set and approved by information holders during booking confirmation for
management information access. If the information holder does not require a designation, our
planning method will continue to be the owner of the information in connection with the
approval of this information. This means that the owner of this information and the owner of
the information interact with the entrance on the web. We assume that all information holders
can agree to assign tasks to the framework.
Proxy Re-Encryption (PRE):
With the public key of entity A, PRE converts the ciphertext of m into the text which can be
decrypted by the personal key for entity B in a proxy.
Ciphertext E(pkA, m) produces Ciphe rA=E(pkA,m) with pkA and m inputs.
RG(skA, pkB), the key algorithm generation re-encryption outputs rkA→B key for the
procurement (e.g., CSP) by taking the input (skA, pkB).
R(rkA→B, CipherA),the re-encryption algorithm
outputs R (rkA→B,CipherA)= E (pkB, m)= CipherB by taking
input rkA→B and CipherA. CipherB can be decrypted with skB.
By accepting the skB and CipherB input, D(skB, CipherB) (Yan et al., 2019a) releases plain
m data.
Each client has a PRE key pair that is applied when AP assumes liability for the
deduplication of information and for access control. PRE empowers AP to give the right of
access by re-encoding information in a CSP to the qualified client, while straightforward
information can't be acquired by the CSP.
Attribute-Based Encryption
During deduplication, users rely on ABE to check access to information against client-
recognizable attestations. The development of ABE is that the information owner encodes the
72
CSP and causes unhappiness. The system also accepts this assumption. To verify ownership
of information, information owners provide the correct set of hash codes for their
information. The information owner is the main qualified information holder for the transfer
of information. The framework is likely to exist in any AP and can keep the basic
engineering. I'm assuming it's obvious that one AP can easily see it in the framework. To talk
to each other, CSPs, APs and information owners/owners use scrambled channels. Organized
information is usually sponsored using CSP, and the topic of this paper is not about
information specifically copying to eliminate the risk of space. Appointment understanding
may be set and approved by information holders during booking confirmation for
management information access. If the information holder does not require a designation, our
planning method will continue to be the owner of the information in connection with the
approval of this information. This means that the owner of this information and the owner of
the information interact with the entrance on the web. We assume that all information holders
can agree to assign tasks to the framework.
Proxy Re-Encryption (PRE):
With the public key of entity A, PRE converts the ciphertext of m into the text which can be
decrypted by the personal key for entity B in a proxy.
Ciphertext E(pkA, m) produces Ciphe rA=E(pkA,m) with pkA and m inputs.
RG(skA, pkB), the key algorithm generation re-encryption outputs rkA→B key for the
procurement (e.g., CSP) by taking the input (skA, pkB).
R(rkA→B, CipherA),the re-encryption algorithm
outputs R (rkA→B,CipherA)= E (pkB, m)= CipherB by taking
input rkA→B and CipherA. CipherB can be decrypted with skB.
By accepting the skB and CipherB input, D(skB, CipherB) (Yan et al., 2019a) releases plain
m data.
Each client has a PRE key pair that is applied when AP assumes liability for the
deduplication of information and for access control. PRE empowers AP to give the right of
access by re-encoding information in a CSP to the qualified client, while straightforward
information can't be acquired by the CSP.
Attribute-Based Encryption
During deduplication, users rely on ABE to check access to information against client-
recognizable attestations. The development of ABE is that the information owner encodes the
72

information encryption key only once when it reaches various qualified information owners.
The radiated unscramble key does not match because it has been changed to information
carrier grade. Fine-grained access control can only be implemented using ABE, improving
the adaptability of the plan. To increase your proficiency in information encryption, you can
use CPABE to run key management or KPABE. CPABE was used to describe the framework
of the entire construction. All clients hold the ABE mystery Sku key in the proposed plot.
The client's ABE decode key is generated by Sku and other client IDs based on the
characteristic ID assigned to the mystery quality key. ID is a characteristic of ID that can be
an unknown identifier for a client. PkID, u are public keys for encoding the DEKu fountain
key. The information owner uses the redid secret attribute key skID(Yan et al., 2019a), u, u'
to transform the pkID, u-encoded part of the encryption key through the secure channel using
the data owner u' as the modifier.
Here the frame can adapt and the heterogeneity. Information owners want to control simple
conditions in clear conditions if the information holder is known. The proposed framework in
this survey is superior to the current job as it is adjusted under different conditions. For
example, the information owner can immediately deal with immediate duplication, or he
cannot use the job to use it/she has appointed her, but something out of double control or
uncontrollable. Our frames may require all the above situations.
In particular, techniques can be adapted to the customer rules to change information.
Owner information use ABE calculations to easily control and share information. Entrance
strategies, prevention based on the sensitivity of the information and the ability of the owner
may vary from different conditions from another person. For the use, we take into account the
proof of distinction is the main attribute of ABE and the information owner is responsible for
ABS foundation and organization. If there are more prone security options, it is very
important, and the management of smooth particles is required, the entrance strategy can be
confused and carried out depending on the properties of ABE.
Data Encryption and Decryption:
Encrypt(DEKu, M) scrambles M utilizing DEKu and produces ciphertext CTu to ensure M
saved at CSP
Decrypt(DEKu, CTu) decrypts DEKu and M outputs from CTu. The simple contents of CTu
saved at CSP are performed by data holder.
Symmetric Key Management:
73
The radiated unscramble key does not match because it has been changed to information
carrier grade. Fine-grained access control can only be implemented using ABE, improving
the adaptability of the plan. To increase your proficiency in information encryption, you can
use CPABE to run key management or KPABE. CPABE was used to describe the framework
of the entire construction. All clients hold the ABE mystery Sku key in the proposed plot.
The client's ABE decode key is generated by Sku and other client IDs based on the
characteristic ID assigned to the mystery quality key. ID is a characteristic of ID that can be
an unknown identifier for a client. PkID, u are public keys for encoding the DEKu fountain
key. The information owner uses the redid secret attribute key skID(Yan et al., 2019a), u, u'
to transform the pkID, u-encoded part of the encryption key through the secure channel using
the data owner u' as the modifier.
Here the frame can adapt and the heterogeneity. Information owners want to control simple
conditions in clear conditions if the information holder is known. The proposed framework in
this survey is superior to the current job as it is adjusted under different conditions. For
example, the information owner can immediately deal with immediate duplication, or he
cannot use the job to use it/she has appointed her, but something out of double control or
uncontrollable. Our frames may require all the above situations.
In particular, techniques can be adapted to the customer rules to change information.
Owner information use ABE calculations to easily control and share information. Entrance
strategies, prevention based on the sensitivity of the information and the ability of the owner
may vary from different conditions from another person. For the use, we take into account the
proof of distinction is the main attribute of ABE and the information owner is responsible for
ABS foundation and organization. If there are more prone security options, it is very
important, and the management of smooth particles is required, the entrance strategy can be
confused and carried out depending on the properties of ABE.
Data Encryption and Decryption:
Encrypt(DEKu, M) scrambles M utilizing DEKu and produces ciphertext CTu to ensure M
saved at CSP
Decrypt(DEKu, CTu) decrypts DEKu and M outputs from CTu. The simple contents of CTu
saved at CSP are performed by data holder.
Symmetric Key Management:
73
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Separate Key(DEKU) . On DEKu input, this method produces several partial keys based on
random separation, for instance, DEK1,u and DEK2,u. If required, DEKu can be separated
into numerous sections.
Combine key (DEK1,u, DEK2,u). This method produces the complete key DEKu using the
combination of partial DEKu keys such as DEK1,u and DEK2,u entered.
6.3 System Configuration and Required Keys:
This methodology handles the key of deduplication by thinking of its personality (ID) as a
satisfactory characteristic where various authorized information clients are admitted to the
encoded information stored in the CSP. Our system allows information owners to be keen on
the management and acquisition of information, subject to that information area and sharp
conditions to which conditions apply. The installation of the framework ensures that each
information owner or owner, the CSP client u, maintains a public PKu key used by various
clients to create user mystery attribute keys and a mystery SKu key used for decoding PKu-
related. Information owners, or owners, use SKu to provide odd quality IDs to various clients
of the PKIDu public key. The CSP client u scrambles the accidentally created symmetric key
DEKu and generates a PKIDu for encoding U information and controlling data access and
deduplication(Yan et al., 2016). For a qualified information performer, the adjustment of the
secret's attribute key to unraveling the PKIDu-encoded encryption key is presented and
communicated individually by the information owner u. Each owner has a strange property
key, which can only be used to get out of the settlement. SKID(u, u`) is a mysterious attribute
ID key generated by u for a qualified u` information conveyor. Meanwhile, usage u makes
additional pku and sku important pairs, such as the creation of marks and verification of
public key cryptosystem (PKC).The keys (PKu, SKu), (pku, sku) are connected to the
uniqueness of u, a one of a kind mysterious personality. This is fundamental for the
confirmation of client ID. PKu and pku are Cert(PKu), Cert(pku), which the CSP and any
client of CSP can approve during framework set-up, checked by an approved outsider.
6.4 SYSTEM TESTING:
After significant progress in the improvement group for steady development or achievement,
the structural director builds a Quality Assurance Group (QA) product establishment, which
in most cases is used for framework testing. To set up the application for system test points,
performance, e.g., delivery. A system test project is the entire work of an engineer who is fit
to try(IBM, 2021). It contains items for document transformations, bags, which are required
to test the framework and prepare for shipping. As engineers make changes and test them as
74
random separation, for instance, DEK1,u and DEK2,u. If required, DEKu can be separated
into numerous sections.
Combine key (DEK1,u, DEK2,u). This method produces the complete key DEKu using the
combination of partial DEKu keys such as DEK1,u and DEK2,u entered.
6.3 System Configuration and Required Keys:
This methodology handles the key of deduplication by thinking of its personality (ID) as a
satisfactory characteristic where various authorized information clients are admitted to the
encoded information stored in the CSP. Our system allows information owners to be keen on
the management and acquisition of information, subject to that information area and sharp
conditions to which conditions apply. The installation of the framework ensures that each
information owner or owner, the CSP client u, maintains a public PKu key used by various
clients to create user mystery attribute keys and a mystery SKu key used for decoding PKu-
related. Information owners, or owners, use SKu to provide odd quality IDs to various clients
of the PKIDu public key. The CSP client u scrambles the accidentally created symmetric key
DEKu and generates a PKIDu for encoding U information and controlling data access and
deduplication(Yan et al., 2016). For a qualified information performer, the adjustment of the
secret's attribute key to unraveling the PKIDu-encoded encryption key is presented and
communicated individually by the information owner u. Each owner has a strange property
key, which can only be used to get out of the settlement. SKID(u, u`) is a mysterious attribute
ID key generated by u for a qualified u` information conveyor. Meanwhile, usage u makes
additional pku and sku important pairs, such as the creation of marks and verification of
public key cryptosystem (PKC).The keys (PKu, SKu), (pku, sku) are connected to the
uniqueness of u, a one of a kind mysterious personality. This is fundamental for the
confirmation of client ID. PKu and pku are Cert(PKu), Cert(pku), which the CSP and any
client of CSP can approve during framework set-up, checked by an approved outsider.
6.4 SYSTEM TESTING:
After significant progress in the improvement group for steady development or achievement,
the structural director builds a Quality Assurance Group (QA) product establishment, which
in most cases is used for framework testing. To set up the application for system test points,
performance, e.g., delivery. A system test project is the entire work of an engineer who is fit
to try(IBM, 2021). It contains items for document transformations, bags, which are required
to test the framework and prepare for shipping. As engineers make changes and test them as
74

they go about their errands, new updates for designers participating in the test project
continue to occur. The structure administrator should set the tests for a more reliable
framework in an area separate from the reassessed changes. The form administrator provides
an accurate overview of the challenges of testing to update the form launched by the board to
develop for testing the framework. The group can maintain a specific overview of the
assignments contained in the item and treat, operate, and test the program until quality
guidelines are met. Periodically iterative is the framework's test cycle. The group has
exceeded the required level of value to be able to create, test, modify and add assignments.
Unit tests:
Unit testing is a product testing innovation that starts small parts of an application and
autonomously confirms the execution of each part. A delete unit test is passed while the
application is running. Gadgets have almost the same potential in technology, work, etc.
Engineers most often run unit tests directly. Unit testing is the basic procedure before mixed
testing with Model, SDLC and STLC. It's just a white box testing approach, and QA
designers can perform unit tests as well, if they're basic. Unit tests are separated into huge,
manual computerized gatherings. Mechanized testing is an important case, but you can do it
physically as well. Computerized instrument testing is a great alternative here, but the hassle
of using one for the other. To utilize the document little by little manually.
Integration tests:
An integration test is a type of test that looks at a mixture of specific units, the
communication in question, how the subsystems are integrated into one common
framework, and how the prerequisites in the code are adhered to. For example, we
consider login verification and register usefulness in individual parts in web-based
business programming. Customers add products to trucks, wish to proceed with the
registration, and check the combination of the two usefulness’s when confirming the
possibility of registration or enlistment. The group uses segments that were previously
attempted as separate parts for integration testing(TESTING GENEZ, 2019). These units
are assembled into sets for each group and confirmed by a test plan. Integration testing
allows you to break your code into blocks that consist of several units and inspect parts of
your product bit by bit before it is fully integrated into the overall framework. That means
that all frameworks have the right inventory, how and why they were generated at any
given time.
Black box testing:
Black box testing has several advantages over white box testing. This methodology is
well known for its productive results and use of time. A vast range of activity is
75
continue to occur. The structure administrator should set the tests for a more reliable
framework in an area separate from the reassessed changes. The form administrator provides
an accurate overview of the challenges of testing to update the form launched by the board to
develop for testing the framework. The group can maintain a specific overview of the
assignments contained in the item and treat, operate, and test the program until quality
guidelines are met. Periodically iterative is the framework's test cycle. The group has
exceeded the required level of value to be able to create, test, modify and add assignments.
Unit tests:
Unit testing is a product testing innovation that starts small parts of an application and
autonomously confirms the execution of each part. A delete unit test is passed while the
application is running. Gadgets have almost the same potential in technology, work, etc.
Engineers most often run unit tests directly. Unit testing is the basic procedure before mixed
testing with Model, SDLC and STLC. It's just a white box testing approach, and QA
designers can perform unit tests as well, if they're basic. Unit tests are separated into huge,
manual computerized gatherings. Mechanized testing is an important case, but you can do it
physically as well. Computerized instrument testing is a great alternative here, but the hassle
of using one for the other. To utilize the document little by little manually.
Integration tests:
An integration test is a type of test that looks at a mixture of specific units, the
communication in question, how the subsystems are integrated into one common
framework, and how the prerequisites in the code are adhered to. For example, we
consider login verification and register usefulness in individual parts in web-based
business programming. Customers add products to trucks, wish to proceed with the
registration, and check the combination of the two usefulness’s when confirming the
possibility of registration or enlistment. The group uses segments that were previously
attempted as separate parts for integration testing(TESTING GENEZ, 2019). These units
are assembled into sets for each group and confirmed by a test plan. Integration testing
allows you to break your code into blocks that consist of several units and inspect parts of
your product bit by bit before it is fully integrated into the overall framework. That means
that all frameworks have the right inventory, how and why they were generated at any
given time.
Black box testing:
Black box testing has several advantages over white box testing. This methodology is
well known for its productive results and use of time. A vast range of activity is
75

commonly seen in tests found for obvious reasons. Black box testing is a somewhat
different procedure. The main qualification from an analyzer's point of view between
black box testing and white box testing is that the analyzer has access to things.
White box testing:
White-box testing is a typical methodology that can be used in several conditions. With
the discovery, structural tests have a significant impact on each test. For white-box
programming and testing, the internal configuration and configuration are simple. There
are no thoughts or data on the items that the analysis evaluated. White-box testing has
several advantages. The methodology is regularly experienced with a limited range of
practice. You have access to a wide range of test equipment decisions to develop
robotized interactions.
6.5 RESULTS LIST:
AP (Authorized Party):
Home
Key setup: Using the option Authorized person can assign the generated key pairs
(pku and sku) to the CSP Users.
User’s Request: When the user requests the uploaded file to the CSP then a request is
sent here and AP needs to generate the key pairs for decryption and sent it back to the
user.
Data Provider:
Home
Profile: Using this option details of the user can be seen.
Upload: Using this option user can upload files to the cloud server and encrypt them.
Initially, it will generate the hash code for the data present in the file. This hash code
is sent to the CSP to check the duplicate files in the cloud providers. If no file is found
it will be assigned with the signed hash code and can generate symmetric key pair for
the file i,e DEK to encrypt the data. The encrypted DEK is split into two keys for
76
different procedure. The main qualification from an analyzer's point of view between
black box testing and white box testing is that the analyzer has access to things.
White box testing:
White-box testing is a typical methodology that can be used in several conditions. With
the discovery, structural tests have a significant impact on each test. For white-box
programming and testing, the internal configuration and configuration are simple. There
are no thoughts or data on the items that the analysis evaluated. White-box testing has
several advantages. The methodology is regularly experienced with a limited range of
practice. You have access to a wide range of test equipment decisions to develop
robotized interactions.
6.5 RESULTS LIST:
AP (Authorized Party):
Home
Key setup: Using the option Authorized person can assign the generated key pairs
(pku and sku) to the CSP Users.
User’s Request: When the user requests the uploaded file to the CSP then a request is
sent here and AP needs to generate the key pairs for decryption and sent it back to the
user.
Data Provider:
Home
Profile: Using this option details of the user can be seen.
Upload: Using this option user can upload files to the cloud server and encrypt them.
Initially, it will generate the hash code for the data present in the file. This hash code
is sent to the CSP to check the duplicate files in the cloud providers. If no file is found
it will be assigned with the signed hash code and can generate symmetric key pair for
the file i,e DEK to encrypt the data. The encrypted DEK is split into two keys for
76
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

confidentiality as DEK1 and DEK2. It will encrypt the DEK1 with PKap to get CK1
and DEK2 with PKid to get CK2. These encrypted files will be sent to the cloud
provider along with two DEK.
In case of duplicate file found in any CSP’s then it does not store in the cloud, and it
gets existing reference file id. If the file is not existing in the local CSP then it will
search for all the CSPs present in the network. Then they will share original data with
the requested users. If the file is not existing, in any of the CSP then only it will be
encrypted and uploaded to the cloud.
Download file: It will display the list of uploaded files to the cloud service providers,
when we click on view it will ask Request AP the keys for decryption. And once the
AP accepts and issues keys, we can automatically decrypt the desired file.
Key Request: Using this option one user can request to the other user to access
similar files. Once the user accepts the request, they can access the files by requesting
to the AP.
KGC:
Home
Set Up: Using this option we can make Key Generation for the newly created users to
the CSPs. It will generate the DSA (i,e PK1u and SK1u keys are generated) and ABE
(i,e. PKu and SKu keys are generated). These pair of keys will be used at the time of
encryption and decryption of data at the CSP end.
POSITIVE TEST CASES
S.
No
Test case
Description
Actual
value
Expected
value
Result
1 Create a new user
registration process
Enter the
personal info
and address
Registration is
successful
True
77
and DEK2 with PKid to get CK2. These encrypted files will be sent to the cloud
provider along with two DEK.
In case of duplicate file found in any CSP’s then it does not store in the cloud, and it
gets existing reference file id. If the file is not existing in the local CSP then it will
search for all the CSPs present in the network. Then they will share original data with
the requested users. If the file is not existing, in any of the CSP then only it will be
encrypted and uploaded to the cloud.
Download file: It will display the list of uploaded files to the cloud service providers,
when we click on view it will ask Request AP the keys for decryption. And once the
AP accepts and issues keys, we can automatically decrypt the desired file.
Key Request: Using this option one user can request to the other user to access
similar files. Once the user accepts the request, they can access the files by requesting
to the AP.
KGC:
Home
Set Up: Using this option we can make Key Generation for the newly created users to
the CSPs. It will generate the DSA (i,e PK1u and SK1u keys are generated) and ABE
(i,e. PKu and SKu keys are generated). These pair of keys will be used at the time of
encryption and decryption of data at the CSP end.
POSITIVE TEST CASES
S.
No
Test case
Description
Actual
value
Expected
value
Result
1 Create a new user
registration process
Enter the
personal info
and address
Registration is
successful
True
77
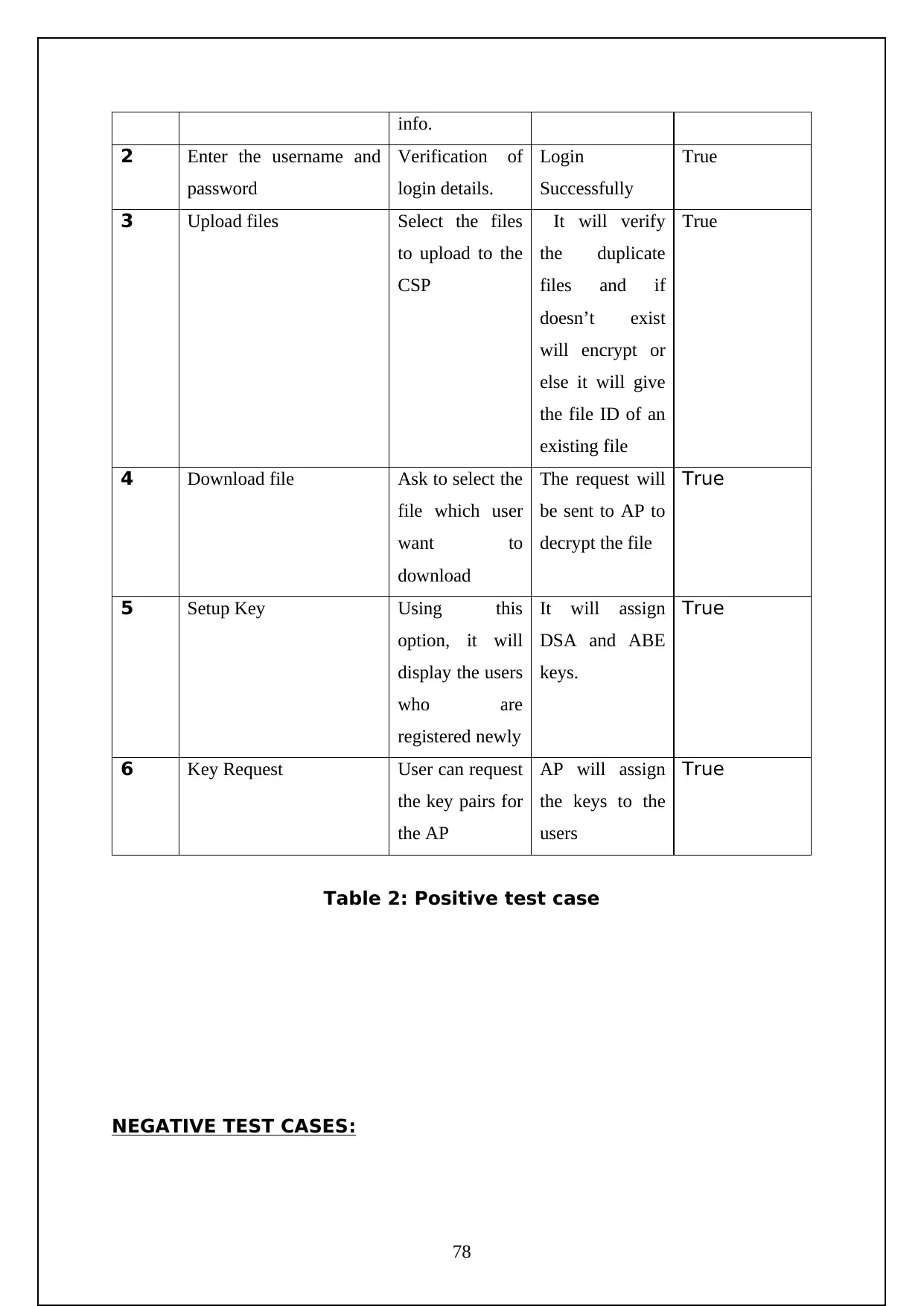
info.
2 Enter the username and
password
Verification of
login details.
Login
Successfully
True
3 Upload files Select the files
to upload to the
CSP
It will verify
the duplicate
files and if
doesn’t exist
will encrypt or
else it will give
the file ID of an
existing file
True
4 Download file Ask to select the
file which user
want to
download
The request will
be sent to AP to
decrypt the file
True
5 Setup Key Using this
option, it will
display the users
who are
registered newly
It will assign
DSA and ABE
keys.
True
6 Key Request User can request
the key pairs for
the AP
AP will assign
the keys to the
users
True
Table 2: Positive test case
NEGATIVE TEST CASES:
78
2 Enter the username and
password
Verification of
login details.
Login
Successfully
True
3 Upload files Select the files
to upload to the
CSP
It will verify
the duplicate
files and if
doesn’t exist
will encrypt or
else it will give
the file ID of an
existing file
True
4 Download file Ask to select the
file which user
want to
download
The request will
be sent to AP to
decrypt the file
True
5 Setup Key Using this
option, it will
display the users
who are
registered newly
It will assign
DSA and ABE
keys.
True
6 Key Request User can request
the key pairs for
the AP
AP will assign
the keys to the
users
True
Table 2: Positive test case
NEGATIVE TEST CASES:
78
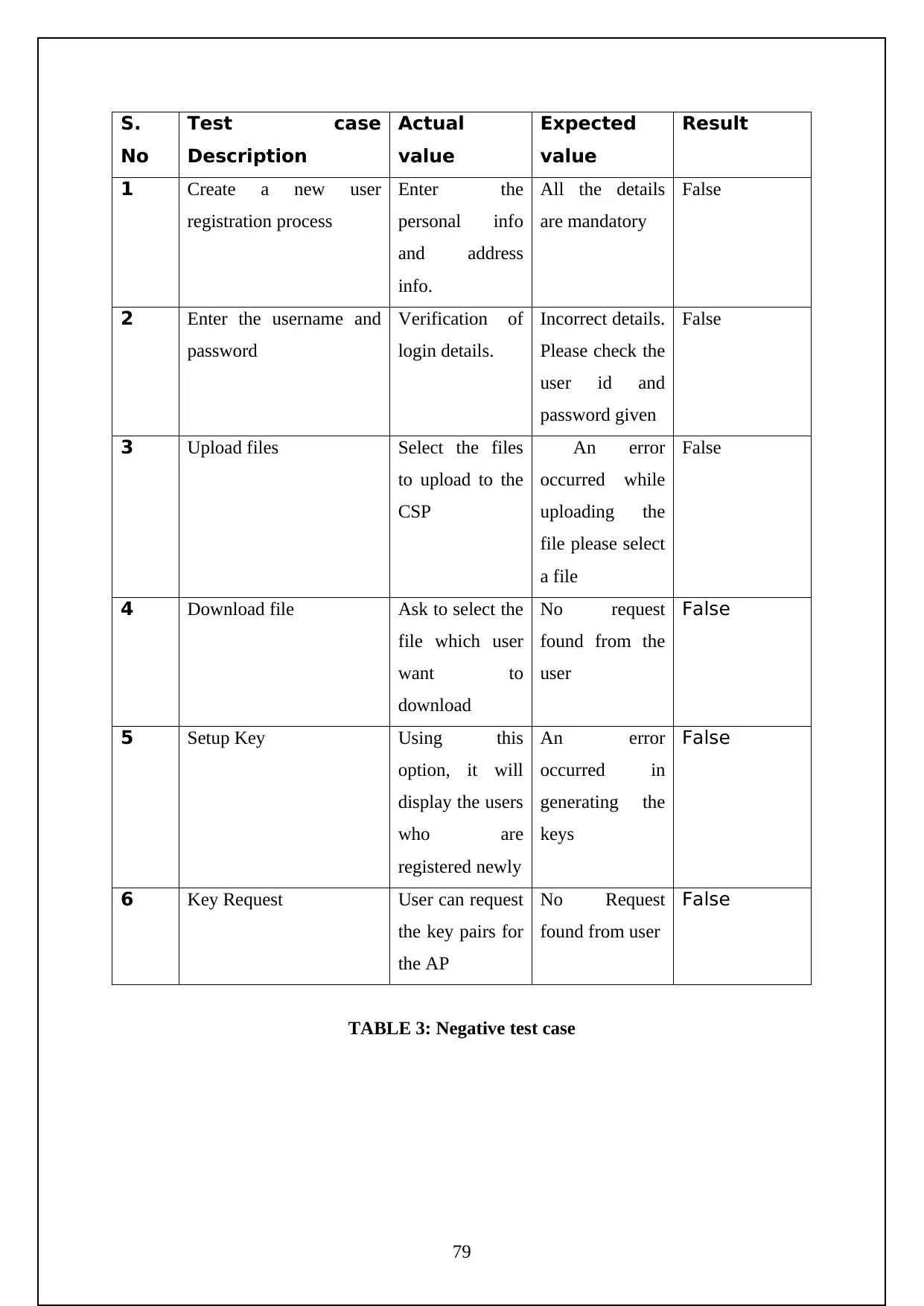
S.
No
Test case
Description
Actual
value
Expected
value
Result
1 Create a new user
registration process
Enter the
personal info
and address
info.
All the details
are mandatory
False
2 Enter the username and
password
Verification of
login details.
Incorrect details.
Please check the
user id and
password given
False
3 Upload files Select the files
to upload to the
CSP
An error
occurred while
uploading the
file please select
a file
False
4 Download file Ask to select the
file which user
want to
download
No request
found from the
user
False
5 Setup Key Using this
option, it will
display the users
who are
registered newly
An error
occurred in
generating the
keys
False
6 Key Request User can request
the key pairs for
the AP
No Request
found from user
False
TABLE 3: Negative test case
79
No
Test case
Description
Actual
value
Expected
value
Result
1 Create a new user
registration process
Enter the
personal info
and address
info.
All the details
are mandatory
False
2 Enter the username and
password
Verification of
login details.
Incorrect details.
Please check the
user id and
password given
False
3 Upload files Select the files
to upload to the
CSP
An error
occurred while
uploading the
file please select
a file
False
4 Download file Ask to select the
file which user
want to
download
No request
found from the
user
False
5 Setup Key Using this
option, it will
display the users
who are
registered newly
An error
occurred in
generating the
keys
False
6 Key Request User can request
the key pairs for
the AP
No Request
found from user
False
TABLE 3: Negative test case
79
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
80

7. CONCLUSION AND FUTURE ENHANCEMENT
Dynamic management of encrypted information in cloud storage with secure
deduplication is a necessary and difficult problem. In this paper, we propose another secure
information deduplication framework that leverages elements of the cloud information board
framework to perform fine-grained ownership management tasks. The proposed approach has
a re-encoding strategy that allows dynamic reporting on changing capacity responsibilities. If
it is not possible to retain the re-evaluated information and there is a difference in ownership,
the information will be re-scrambled into a recently updated set of ownership, which will
only be safely shipped to full-fledged owners. Therefore, the recommended game plan further
develops the mystery of client information protection and distributed storage, rather than
owning legitimate information like the truth is curious cloud work. Label consistency is
guaranteed as well, and the deduplication of executable information across the encoded
information is leveraged as the framework's greatest advantage. The recommended strategy is
better than previously planned in terms of communication costs. In terms of estimated cost, it
takes more than 0.10.2ms as opposed to the RCE plot, which is essentially insignificant. As
such, the recommended framework is cloud-protected and provides complex ownership
management for information security and deduplication.
In the future, this framework may be improved to deduplication when updated or
deleted documents are empty, leveraging a map minimization strategy to reduce execution
time. I can. Not only that, but they are sometimes written to deduct sound, video, and images
from various sources. Advances in distributed computing are taking advantage of the capacity
assets of equipment devices. Therefore, any organization can develop its own private cloud
for various reasons. Anyway, I don't have permission to a specific capacity, but it's likely to
be presented in the future. What comes next are these kinds of highlights. Currently, only
content documents are being evaluated for improvements in capacity strategies. New records
of various kinds, such as sound documents and video documents, are likely to be supported in
the future. This framework works for level content documents, but not for encoded records. If
the client sends an encoded document, this framework will not work. Anyway, it can work
very well, since the later confused rationale is essential.
81
Dynamic management of encrypted information in cloud storage with secure
deduplication is a necessary and difficult problem. In this paper, we propose another secure
information deduplication framework that leverages elements of the cloud information board
framework to perform fine-grained ownership management tasks. The proposed approach has
a re-encoding strategy that allows dynamic reporting on changing capacity responsibilities. If
it is not possible to retain the re-evaluated information and there is a difference in ownership,
the information will be re-scrambled into a recently updated set of ownership, which will
only be safely shipped to full-fledged owners. Therefore, the recommended game plan further
develops the mystery of client information protection and distributed storage, rather than
owning legitimate information like the truth is curious cloud work. Label consistency is
guaranteed as well, and the deduplication of executable information across the encoded
information is leveraged as the framework's greatest advantage. The recommended strategy is
better than previously planned in terms of communication costs. In terms of estimated cost, it
takes more than 0.10.2ms as opposed to the RCE plot, which is essentially insignificant. As
such, the recommended framework is cloud-protected and provides complex ownership
management for information security and deduplication.
In the future, this framework may be improved to deduplication when updated or
deleted documents are empty, leveraging a map minimization strategy to reduce execution
time. I can. Not only that, but they are sometimes written to deduct sound, video, and images
from various sources. Advances in distributed computing are taking advantage of the capacity
assets of equipment devices. Therefore, any organization can develop its own private cloud
for various reasons. Anyway, I don't have permission to a specific capacity, but it's likely to
be presented in the future. What comes next are these kinds of highlights. Currently, only
content documents are being evaluated for improvements in capacity strategies. New records
of various kinds, such as sound documents and video documents, are likely to be supported in
the future. This framework works for level content documents, but not for encoded records. If
the client sends an encoded document, this framework will not work. Anyway, it can work
very well, since the later confused rationale is essential.
81

References:
Abdurazik, A. and Offutt, Jeff (2000) ‘Using UML Collaboration Diagrams for Static
Checking and Test Generation’.
AgileIT (2017) ‘Data Encryption Methods to Secure Your Cloud’, Agile IT, 25 January.
Available at: https://www.agileit.com/news/data-encryption-methods-secure-cloud/
(Accessed: 28 June 2021).
Chow, R. et al. (2009) ‘Controlling data in the cloud: outsourcing computation without
outsourcing control’, in Proceedings of the 2009 ACM workshop on Cloud computing
security. New York, NY, USA: Association for Computing Machinery (CCSW ’09), pp. 85–
90. doi: 10.1145/1655008.1655020.
CNS (2011) ‘Cloud Computing Feasibility Assessment’. Available at: https://cnsit.com/wp-
content/uploads/2015/09/CloudComputingFeasibilityAssessment.pdf.
CODEBUN (2017) JSP tutorial || What is JSP || Why we use JSP, Codebun. Available at:
https://codebun.com/jsp-tutorial/ (Accessed: 28 June 2021).
Drake, M. (2020) What is SQL?, DigitalOcean. Available at:
https://www.digitalocean.com/community/tutorials/what-is-sql (Accessed: 28 June 2021).
Hayashi, K. (2013) ‘Social Issues of Big Data and Cloud: Privacy, Confidentiality, and
Public Utility’, in 2013 International Conference on Availability, Reliability and Security.
2013 International Conference on Availability, Reliability and Security, pp. 506–511. doi:
10.1109/ARES.2013.66.
Hur, J. et al. (2016a) ‘Secure Data Deduplication with Dynamic Ownership Management in
Cloud Storage’, IEEE Transactions on Knowledge and Data Engineering, 28(11), pp. 3113–
3125. doi: 10.1109/TKDE.2016.2580139.
IBM (2021) IBM Docs. Available at: https://prod.ibmdocs-production-dal-
6099123ce774e592a519d7c33db8265e-0000.us-south.containers.appdomain.cloud/docs/en/
rational-synergy/7.2.1?topic=workflow-system-test-cycle (Accessed: 29 June 2021).
Izang, A. A. et al. (2017) ‘Security and ethical issues to cloud database’, Journal of Computer
Science and Its Application, 24(2), pp. 65–75. doi: 10.4314/jcsia.v24i2.
82
Abdurazik, A. and Offutt, Jeff (2000) ‘Using UML Collaboration Diagrams for Static
Checking and Test Generation’.
AgileIT (2017) ‘Data Encryption Methods to Secure Your Cloud’, Agile IT, 25 January.
Available at: https://www.agileit.com/news/data-encryption-methods-secure-cloud/
(Accessed: 28 June 2021).
Chow, R. et al. (2009) ‘Controlling data in the cloud: outsourcing computation without
outsourcing control’, in Proceedings of the 2009 ACM workshop on Cloud computing
security. New York, NY, USA: Association for Computing Machinery (CCSW ’09), pp. 85–
90. doi: 10.1145/1655008.1655020.
CNS (2011) ‘Cloud Computing Feasibility Assessment’. Available at: https://cnsit.com/wp-
content/uploads/2015/09/CloudComputingFeasibilityAssessment.pdf.
CODEBUN (2017) JSP tutorial || What is JSP || Why we use JSP, Codebun. Available at:
https://codebun.com/jsp-tutorial/ (Accessed: 28 June 2021).
Drake, M. (2020) What is SQL?, DigitalOcean. Available at:
https://www.digitalocean.com/community/tutorials/what-is-sql (Accessed: 28 June 2021).
Hayashi, K. (2013) ‘Social Issues of Big Data and Cloud: Privacy, Confidentiality, and
Public Utility’, in 2013 International Conference on Availability, Reliability and Security.
2013 International Conference on Availability, Reliability and Security, pp. 506–511. doi:
10.1109/ARES.2013.66.
Hur, J. et al. (2016a) ‘Secure Data Deduplication with Dynamic Ownership Management in
Cloud Storage’, IEEE Transactions on Knowledge and Data Engineering, 28(11), pp. 3113–
3125. doi: 10.1109/TKDE.2016.2580139.
IBM (2021) IBM Docs. Available at: https://prod.ibmdocs-production-dal-
6099123ce774e592a519d7c33db8265e-0000.us-south.containers.appdomain.cloud/docs/en/
rational-synergy/7.2.1?topic=workflow-system-test-cycle (Accessed: 29 June 2021).
Izang, A. A. et al. (2017) ‘Security and ethical issues to cloud database’, Journal of Computer
Science and Its Application, 24(2), pp. 65–75. doi: 10.4314/jcsia.v24i2.
82
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

JanbaskTraining (2019) What is Unit Testing? Unit Testing Tutorial Guide for Beginners,
JanbaskTraining. Available at: https://www.janbasktraining.com/blog/unit-testing-tutorial
(Accessed: 29 June 2021).
Keerthika, K. (2018) ‘Avoid Duplicate Entries of Repeating Data in Hybrid Cloud Storage
Using Convergent Encryption Techniques’, International Journal of Engineering Research,
6(08), p. 4.
Kozar, K. A. (1997) Data Flow Diagramming Technique. Available at:
https://spot.colorado.edu/~kozar/DFDtechnique.html (Accessed: 28 June 2021).
Nahlah Aslam, K. P. and Swaraj, K. P. (2019) ‘Data Deduplication with Encrypted Big Data
Management in Cloud Computing’, in 2019 International Conference on Communication and
Electronics Systems (ICCES). 2019 International Conference on Communication and
Electronics Systems (ICCES), pp. 947–952. doi: 10.1109/ICCES45898.2019.9002170.
Net-informations (2019) What is Java. Available at:
http://net-informations.com/java/intro/java.htm (Accessed: 28 June 2021).
Norlyn Opinaldo (2021) UML Sequence Diagram Examples Online Free to Download.
Available at: https://gitmind.com/sequence-diagram-example.html (Accessed: 24 June 2021).
Poelker, C. (2013) Data deduplication in the cloud explained, part one, Computerworld.
Available at: https://www.computerworld.com/article/2474479/data-deduplication-in-the-
cloud-explained--part-one.html (Accessed: 28 June 2021).
RICK’S CLOUD (2013) ‘Legal Issues around Cloud Computing’, Rick’s Cloud, 2 July.
Available at: https://rickscloud.com/legal-issues-around-cloud-computing/ (Accessed: 28
June 2021).
TESTING GENEZ (2019) ‘Difference between Black Box and White Box Testing | Testing
Types’, TestingGenez, 12 October. Available at: https://testinggenez.com/black-box-and-
white-box-testing/ (Accessed: 29 June 2021).
Tribhuwan, M. R., Bhuyar, V. A. and Pirzade, S. (2010) ‘Ensuring Data Storage Security in
Cloud Computing through Two-Way Handshake Based on Token Management’, in 2010
International Conference on Advances in Recent Technologies in Communication and
Computing. 2010 International Conference on Advances in Recent Technologies in
Communication and Computing, pp. 386–389. doi: 10.1109/ARTCom.2010.23.
83
JanbaskTraining. Available at: https://www.janbasktraining.com/blog/unit-testing-tutorial
(Accessed: 29 June 2021).
Keerthika, K. (2018) ‘Avoid Duplicate Entries of Repeating Data in Hybrid Cloud Storage
Using Convergent Encryption Techniques’, International Journal of Engineering Research,
6(08), p. 4.
Kozar, K. A. (1997) Data Flow Diagramming Technique. Available at:
https://spot.colorado.edu/~kozar/DFDtechnique.html (Accessed: 28 June 2021).
Nahlah Aslam, K. P. and Swaraj, K. P. (2019) ‘Data Deduplication with Encrypted Big Data
Management in Cloud Computing’, in 2019 International Conference on Communication and
Electronics Systems (ICCES). 2019 International Conference on Communication and
Electronics Systems (ICCES), pp. 947–952. doi: 10.1109/ICCES45898.2019.9002170.
Net-informations (2019) What is Java. Available at:
http://net-informations.com/java/intro/java.htm (Accessed: 28 June 2021).
Norlyn Opinaldo (2021) UML Sequence Diagram Examples Online Free to Download.
Available at: https://gitmind.com/sequence-diagram-example.html (Accessed: 24 June 2021).
Poelker, C. (2013) Data deduplication in the cloud explained, part one, Computerworld.
Available at: https://www.computerworld.com/article/2474479/data-deduplication-in-the-
cloud-explained--part-one.html (Accessed: 28 June 2021).
RICK’S CLOUD (2013) ‘Legal Issues around Cloud Computing’, Rick’s Cloud, 2 July.
Available at: https://rickscloud.com/legal-issues-around-cloud-computing/ (Accessed: 28
June 2021).
TESTING GENEZ (2019) ‘Difference between Black Box and White Box Testing | Testing
Types’, TestingGenez, 12 October. Available at: https://testinggenez.com/black-box-and-
white-box-testing/ (Accessed: 29 June 2021).
Tribhuwan, M. R., Bhuyar, V. A. and Pirzade, S. (2010) ‘Ensuring Data Storage Security in
Cloud Computing through Two-Way Handshake Based on Token Management’, in 2010
International Conference on Advances in Recent Technologies in Communication and
Computing. 2010 International Conference on Advances in Recent Technologies in
Communication and Computing, pp. 386–389. doi: 10.1109/ARTCom.2010.23.
83

UTOR (2020) ‘Integration Testing – Types, Tips and Challenges You Should Be Aware Of’,
UTOR, 15 July. Available at: https://u-tor.com/topic/integration-testing (Accessed: 29 June
2021).
Wondershare EdrawMax (2018) Use Case Diagram Explained | EdrawMax, Edrawsoft.
Available at: https://www.edrawmax.com/article/use-case-diagram-uml.html (Accessed: 28
June 2021).
Yan, Z. et al. (2016) ‘Encrypted Data Management with Deduplication in Cloud Computing’,
IEEE Cloud Computing, 3(2), pp. 28–35. doi: 10.1109/MCC.2016.29.
Yan, Z. et al. (2019a) ‘Heterogeneous Data Storage Management with Deduplication in
Cloud Computing’, IEEE Transactions on Big Data, 5(3), pp. 393–407. doi:
10.1109/TBDATA.2017.2701352.
Zhou, M. et al. (2011) ‘Privacy-Preserved Access Control for Cloud Computing’, in
2011IEEE 10th International Conference on Trust, Security and Privacy in Computing and
Communications. 2011IEEE 10th International Conference on Trust, Security and Privacy in
Computing and Communications, pp. 83–90. doi: 10.1109/TrustCom.2011.14.
Moor, J.H., 2017. What is computer ethics?. In Computer Ethics (pp. 31-40). Routledge.
Ferreira, R. and Vardi, M.Y., 2020. Computer Ethics and Care: An Activity for Practicing
“Deep” Attention. Teaching Ethics. 20(1/2). pp.139-156.
84
UTOR, 15 July. Available at: https://u-tor.com/topic/integration-testing (Accessed: 29 June
2021).
Wondershare EdrawMax (2018) Use Case Diagram Explained | EdrawMax, Edrawsoft.
Available at: https://www.edrawmax.com/article/use-case-diagram-uml.html (Accessed: 28
June 2021).
Yan, Z. et al. (2016) ‘Encrypted Data Management with Deduplication in Cloud Computing’,
IEEE Cloud Computing, 3(2), pp. 28–35. doi: 10.1109/MCC.2016.29.
Yan, Z. et al. (2019a) ‘Heterogeneous Data Storage Management with Deduplication in
Cloud Computing’, IEEE Transactions on Big Data, 5(3), pp. 393–407. doi:
10.1109/TBDATA.2017.2701352.
Zhou, M. et al. (2011) ‘Privacy-Preserved Access Control for Cloud Computing’, in
2011IEEE 10th International Conference on Trust, Security and Privacy in Computing and
Communications. 2011IEEE 10th International Conference on Trust, Security and Privacy in
Computing and Communications, pp. 83–90. doi: 10.1109/TrustCom.2011.14.
Moor, J.H., 2017. What is computer ethics?. In Computer Ethics (pp. 31-40). Routledge.
Ferreira, R. and Vardi, M.Y., 2020. Computer Ethics and Care: An Activity for Practicing
“Deep” Attention. Teaching Ethics. 20(1/2). pp.139-156.
84
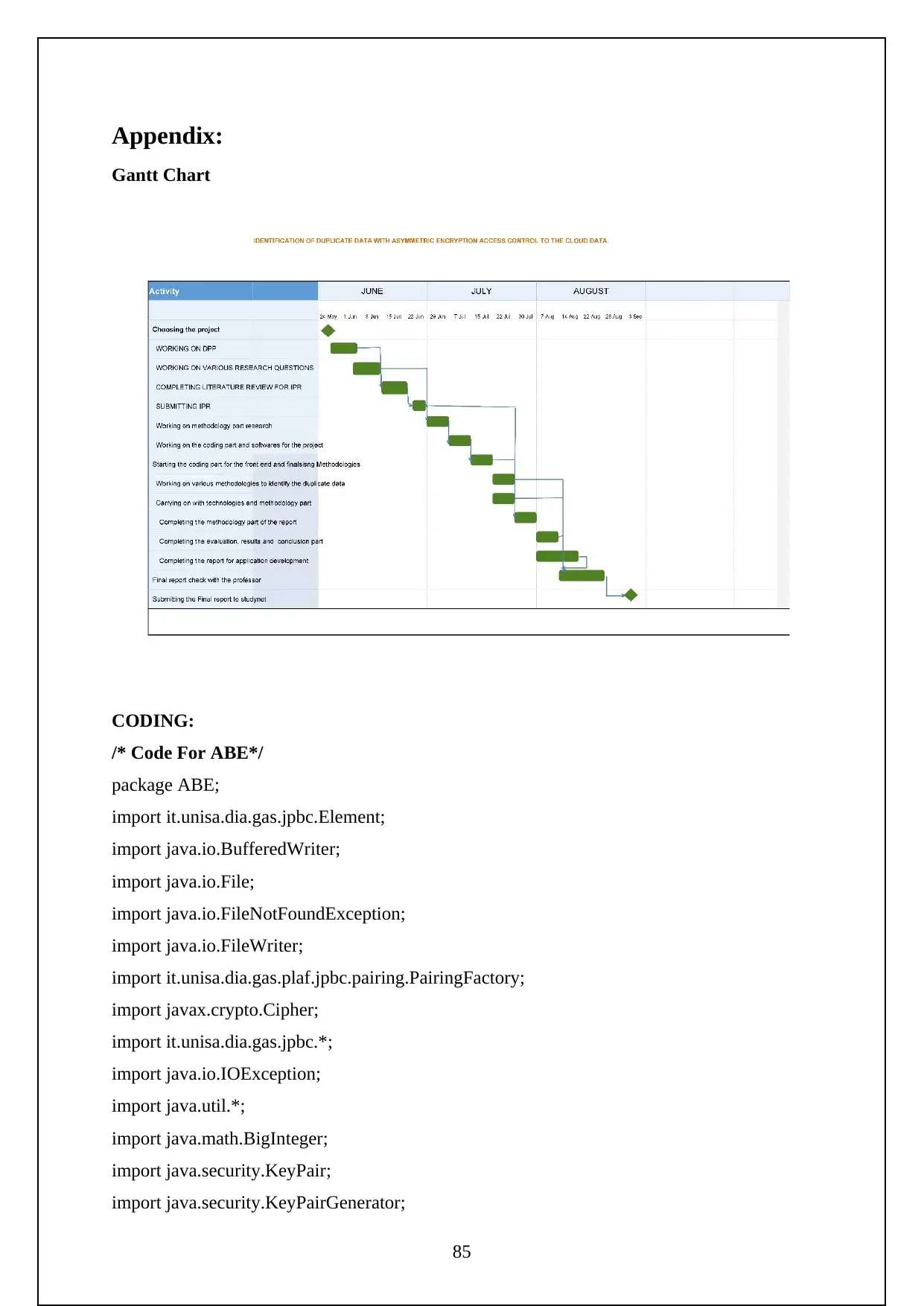
Appendix:
Gantt Chart
CODING:
/* Code For ABE*/
package ABE;
import it.unisa.dia.gas.jpbc.Element;
import java.io.BufferedWriter;
import java.io.File;
import java.io.FileNotFoundException;
import java.io.FileWriter;
import it.unisa.dia.gas.plaf.jpbc.pairing.PairingFactory;
import javax.crypto.Cipher;
import it.unisa.dia.gas.jpbc.*;
import java.io.IOException;
import java.util.*;
import java.math.BigInteger;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
85
Gantt Chart
CODING:
/* Code For ABE*/
package ABE;
import it.unisa.dia.gas.jpbc.Element;
import java.io.BufferedWriter;
import java.io.File;
import java.io.FileNotFoundException;
import java.io.FileWriter;
import it.unisa.dia.gas.plaf.jpbc.pairing.PairingFactory;
import javax.crypto.Cipher;
import it.unisa.dia.gas.jpbc.*;
import java.io.IOException;
import java.util.*;
import java.math.BigInteger;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
85
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

import java.security.Signature;
import java.security.*;
import java.security.spec.X509EncodedKeySpec;
import java.security.spec.*;
import java.util.Scanner;
import java.sql.*;
import java.security.*;
import java.security.spec.*;
import java.io.*;
public class ABE {
private static BigInteger KEY , n;
private static Element publicKey;
private static Element masterKey;
static Pairing pairing;
static byte[] privateKey;
static byte[] publicKeyBytes;
static byte[] sig1,sig2,sig3;
BigInteger public_key,private_key;
private long public_key_temp;
private BigInteger p;
private BigInteger q;
private BigInteger phi;
private BigInteger e;
private BigInteger d;
private int bitlength = 1024;
private Random r;
String ID;
public ABE(String ID){
this.ID = ID ;
public_key_temp = Math.abs(ID.hashCode());
r = new Random();
p = BigInteger.probablePrime(bitlength, r);
q = BigInteger.probablePrime(bitlength, r);
n = p.multiply(q);
}
86
import java.security.*;
import java.security.spec.X509EncodedKeySpec;
import java.security.spec.*;
import java.util.Scanner;
import java.sql.*;
import java.security.*;
import java.security.spec.*;
import java.io.*;
public class ABE {
private static BigInteger KEY , n;
private static Element publicKey;
private static Element masterKey;
static Pairing pairing;
static byte[] privateKey;
static byte[] publicKeyBytes;
static byte[] sig1,sig2,sig3;
BigInteger public_key,private_key;
private long public_key_temp;
private BigInteger p;
private BigInteger q;
private BigInteger phi;
private BigInteger e;
private BigInteger d;
private int bitlength = 1024;
private Random r;
String ID;
public ABE(String ID){
this.ID = ID ;
public_key_temp = Math.abs(ID.hashCode());
r = new Random();
p = BigInteger.probablePrime(bitlength, r);
q = BigInteger.probablePrime(bitlength, r);
n = p.multiply(q);
}
86

public BigInteger get_public_key(){ //
generating public key
phi = p.subtract(BigInteger.ONE).multiply(q.subtract(BigInteger.ONE));
e = BigInteger.valueOf(public_key_temp);
while (phi.gcd(e).compareTo(BigInteger.valueOf(1)) != 0 ) {
e = e.divide(phi.gcd(e));
}
public_key = e.multiply(BigInteger.probablePrime(bitlength, r));
//public_key = e;
return public_key;
}
public BigInteger get_private_key(){ // generating private key
get_public_key();
d = public_key.modInverse(phi);
private_key = extendedEuclid(public_key,
(this.p.subtract(BigInteger.ONE)).multiply(this.q.subtract(BigInteger.ONE)));
return private_key;
}
public BigInteger getn(){
return n;
}
public BigInteger extendedEuclid(BigInteger a, BigInteger b) {
BigInteger x = BigInteger.valueOf(1), y = BigInteger.valueOf(0);
BigInteger xLast = BigInteger.valueOf(0), yLast = BigInteger.valueOf(0);
BigInteger q, r, m, n;
while(a.compareTo(BigInteger.valueOf(0)) != 0) {
q = b.divide(a);
r = b.remainder(a);
m = xLast.subtract(q.multiply(x));
n = yLast.subtract(q.multiply(y));
xLast = x;
yLast = y;
x = m;
y = n;
b = a;
87
generating public key
phi = p.subtract(BigInteger.ONE).multiply(q.subtract(BigInteger.ONE));
e = BigInteger.valueOf(public_key_temp);
while (phi.gcd(e).compareTo(BigInteger.valueOf(1)) != 0 ) {
e = e.divide(phi.gcd(e));
}
public_key = e.multiply(BigInteger.probablePrime(bitlength, r));
//public_key = e;
return public_key;
}
public BigInteger get_private_key(){ // generating private key
get_public_key();
d = public_key.modInverse(phi);
private_key = extendedEuclid(public_key,
(this.p.subtract(BigInteger.ONE)).multiply(this.q.subtract(BigInteger.ONE)));
return private_key;
}
public BigInteger getn(){
return n;
}
public BigInteger extendedEuclid(BigInteger a, BigInteger b) {
BigInteger x = BigInteger.valueOf(1), y = BigInteger.valueOf(0);
BigInteger xLast = BigInteger.valueOf(0), yLast = BigInteger.valueOf(0);
BigInteger q, r, m, n;
while(a.compareTo(BigInteger.valueOf(0)) != 0) {
q = b.divide(a);
r = b.remainder(a);
m = xLast.subtract(q.multiply(x));
n = yLast.subtract(q.multiply(y));
xLast = x;
yLast = y;
x = m;
y = n;
b = a;
87

a = r;
}
if(xLast.compareTo(BigInteger.valueOf(0))<0)
xLast
xLast.add((this.p.subtract(BigInteger.ONE)).multiply(this.q.subtract(BigInteger.ONE)));
return xLast;
}
public long power(long a, long b,long p) {
// power funation a^b%p
long r = 1;
while(b!=0) {
if((b & 1) != 0) r = r * a % p;
a = (a * a)% p;
b >>= 1; }
return r;
}
public BigInteger gcd1(BigInteger x,BigInteger y){ //
computing gcd
if(y.compareTo(BigInteger.valueOf(0)) == 0) return x;
return gcd1(y,x.remainder(y));
}
public byte[] encrypt(String dek2,BigInteger public_key) {
// Encrypting message
byte[] message = dek2.getBytes();
byte [] CK2 = (new BigInteger(message)).modPow(public_key, n).toByteArray();
return CK2;
}
public byte[] decrypt(byte[] CK2,BigInteger private_key) { //
Message Decryption
return (new BigInteger(CK2)).modPow(private_key, n).toByteArray();
}
/*public static void main(String a[]){
ABE i=new ABE("ali");
BigInteger public_key=i.get_public_key();
BigInteger private_key=i.get_private_key();
88
}
if(xLast.compareTo(BigInteger.valueOf(0))<0)
xLast
xLast.add((this.p.subtract(BigInteger.ONE)).multiply(this.q.subtract(BigInteger.ONE)));
return xLast;
}
public long power(long a, long b,long p) {
// power funation a^b%p
long r = 1;
while(b!=0) {
if((b & 1) != 0) r = r * a % p;
a = (a * a)% p;
b >>= 1; }
return r;
}
public BigInteger gcd1(BigInteger x,BigInteger y){ //
computing gcd
if(y.compareTo(BigInteger.valueOf(0)) == 0) return x;
return gcd1(y,x.remainder(y));
}
public byte[] encrypt(String dek2,BigInteger public_key) {
// Encrypting message
byte[] message = dek2.getBytes();
byte [] CK2 = (new BigInteger(message)).modPow(public_key, n).toByteArray();
return CK2;
}
public byte[] decrypt(byte[] CK2,BigInteger private_key) { //
Message Decryption
return (new BigInteger(CK2)).modPow(private_key, n).toByteArray();
}
/*public static void main(String a[]){
ABE i=new ABE("ali");
BigInteger public_key=i.get_public_key();
BigInteger private_key=i.get_private_key();
88
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

byte[] enc=i.encrypt(public_key,"dek2");
System.out.println("dec="+new String(i.decrypt(private_key,enc)));
}*/
}
/* Code For AES*/
import java.security.Key;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
import org.bouncycastle.util.encoders.Base64;
public class AES {
/* We need the Thid Party Jar file commons-codec-1.7.jar */
private static final String ALGO = "AES";
public static String encrypt(String Data, String keyWord) throws Exception {
keyWord = keyWord.substring(0, 16);
byte[] keyValue = keyWord.getBytes();
System.out.println("Size : " + keyValue.length);
Key key = new SecretKeySpec(keyValue, ALGO);
Cipher c = Cipher.getInstance(ALGO);
c.init(Cipher.ENCRYPT_MODE, key);
String encryptedValue = new String(Base64.encode(Data.getBytes()));
return encryptedValue;
}
public static String decrypt(String encryptedData, String keyWord)
throws Exception {
keyWord = keyWord.substring(0, 16);
byte[] keyValue = keyWord.getBytes();
Key key = new SecretKeySpec(keyValue, ALGO);
Cipher c = Cipher.getInstance(ALGO);
89
System.out.println("dec="+new String(i.decrypt(private_key,enc)));
}*/
}
/* Code For AES*/
import java.security.Key;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
import org.bouncycastle.util.encoders.Base64;
public class AES {
/* We need the Thid Party Jar file commons-codec-1.7.jar */
private static final String ALGO = "AES";
public static String encrypt(String Data, String keyWord) throws Exception {
keyWord = keyWord.substring(0, 16);
byte[] keyValue = keyWord.getBytes();
System.out.println("Size : " + keyValue.length);
Key key = new SecretKeySpec(keyValue, ALGO);
Cipher c = Cipher.getInstance(ALGO);
c.init(Cipher.ENCRYPT_MODE, key);
String encryptedValue = new String(Base64.encode(Data.getBytes()));
return encryptedValue;
}
public static String decrypt(String encryptedData, String keyWord)
throws Exception {
keyWord = keyWord.substring(0, 16);
byte[] keyValue = keyWord.getBytes();
Key key = new SecretKeySpec(keyValue, ALGO);
Cipher c = Cipher.getInstance(ALGO);
89

c.init(Cipher.DECRYPT_MODE, key);
String decryptedValue = new String(Base64.decode(encryptedData
.getBytes()));
return decryptedValue;
}
public static void main(String[] args) {
String password = "mypassword";
String keyWord = "ef50a0ef2c3e3a5fdf803ae9752c8c66";
try {
String passwordEnc = AES.encrypt(password,
keyWord);
String passwordDec = AES.decrypt(
passwordEnc, keyWord);
System.out.println("Plain Text : " + password);
System.out.println("Encrypted Text : " + passwordEnc);
System.out.println("Decrypted Text : " + passwordDec);
} catch (Exception e) {
System.out
.println("Opps,Exception In
AES_EncrypterNdecrypter=>main() :");
e.printStackTrace();
}
}
}
/* Code For CSP*/
<%@ include file="header.jsp"%>
<!-- //banner -->
<!-- contact -->
<section class="contact-w3ls">
90
String decryptedValue = new String(Base64.decode(encryptedData
.getBytes()));
return decryptedValue;
}
public static void main(String[] args) {
String password = "mypassword";
String keyWord = "ef50a0ef2c3e3a5fdf803ae9752c8c66";
try {
String passwordEnc = AES.encrypt(password,
keyWord);
String passwordDec = AES.decrypt(
passwordEnc, keyWord);
System.out.println("Plain Text : " + password);
System.out.println("Encrypted Text : " + passwordEnc);
System.out.println("Decrypted Text : " + passwordDec);
} catch (Exception e) {
System.out
.println("Opps,Exception In
AES_EncrypterNdecrypter=>main() :");
e.printStackTrace();
}
}
}
/* Code For CSP*/
<%@ include file="header.jsp"%>
<!-- //banner -->
<!-- contact -->
<section class="contact-w3ls">
90

<div class="container">
<div class="wthree-heading">
<h2 class="w3l-titles">CSP</h2>
<p class="quia">Enter userName&Password</p>
</div>
<div class="con-top">
<%
String msg1 = request.getParameter("msg1");
if(msg1 != null){
out.println("<script>alert('Login Fail..!')</script>");
}
%>
<div class="col-lg-10 col-md-10 col-sm-10 contact-w3-agile2" data-
aos="flip-left">
<div class="contact-agileits">
<h4>Login</h4>
<form action="cspcheck.jsp" method="post">
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">Name:</label>
<input type="text" class="form-control" name="unm" id="name"
Placeholder=" " required="">
<p class="help-block"></p>
</div>
</div>
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">Password:</label>
<input type="Password" class="form-control" name="pwd" id="phone"
Placeholder=" " required="">
<p class="help-block"></p>
</div>
</div>
91
<div class="wthree-heading">
<h2 class="w3l-titles">CSP</h2>
<p class="quia">Enter userName&Password</p>
</div>
<div class="con-top">
<%
String msg1 = request.getParameter("msg1");
if(msg1 != null){
out.println("<script>alert('Login Fail..!')</script>");
}
%>
<div class="col-lg-10 col-md-10 col-sm-10 contact-w3-agile2" data-
aos="flip-left">
<div class="contact-agileits">
<h4>Login</h4>
<form action="cspcheck.jsp" method="post">
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">Name:</label>
<input type="text" class="form-control" name="unm" id="name"
Placeholder=" " required="">
<p class="help-block"></p>
</div>
</div>
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">Password:</label>
<input type="Password" class="form-control" name="pwd" id="phone"
Placeholder=" " required="">
<p class="help-block"></p>
</div>
</div>
91
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
<div id="success"></div>
<!-- For success/fail messages -->
<button type="submit" class="btn btn-primary">Login</button>
</form>
</div>
</div>
<div class="clearfix"></div>
</div>
</div>
</section>
<!-- map -->
<!-- footer -->
<%@ include file="footer.jsp"%>}
/* Code For database connection*/
package database;
import java.sql.*;
public class databasecon
{
static Connection con;
public static Connection getconnection()
{
try
{
Class.forName("com.mysql.jdbc.Driver");
con =
DriverManager.getConnection("jdbc:mysql://localhost:3306/hdsm","root","root");
}
catch(Exception e)
{
System.out.println("class error"+e);
}
return con;
92
<!-- For success/fail messages -->
<button type="submit" class="btn btn-primary">Login</button>
</form>
</div>
</div>
<div class="clearfix"></div>
</div>
</div>
</section>
<!-- map -->
<!-- footer -->
<%@ include file="footer.jsp"%>}
/* Code For database connection*/
package database;
import java.sql.*;
public class databasecon
{
static Connection con;
public static Connection getconnection()
{
try
{
Class.forName("com.mysql.jdbc.Driver");
con =
DriverManager.getConnection("jdbc:mysql://localhost:3306/hdsm","root","root");
}
catch(Exception e)
{
System.out.println("class error"+e);
}
return con;
92

}
}
/* Code For DSA key generation*/
package DSA;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.Signature;
import java.security.*;
import java.security.spec.X509EncodedKeySpec;
import java.security.spec.*;
public class DSA
{
byte[] privateKeyBytes;
byte[] publicKeyBytes;
public void keyGeneration(){
try{
KeyPairGenerator kpg = KeyPairGenerator.getInstance("DSA");
kpg.initialize(1024);
KeyPair keyPair = kpg.genKeyPair();
privateKeyBytes =keyPair.getPrivate().getEncoded();
publicKeyBytes =keyPair.getPublic().getEncoded();
}
catch(Exception e){
93
}
/* Code For DSA key generation*/
package DSA;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.Signature;
import java.security.*;
import java.security.spec.X509EncodedKeySpec;
import java.security.spec.*;
public class DSA
{
byte[] privateKeyBytes;
byte[] publicKeyBytes;
public void keyGeneration(){
try{
KeyPairGenerator kpg = KeyPairGenerator.getInstance("DSA");
kpg.initialize(1024);
KeyPair keyPair = kpg.genKeyPair();
privateKeyBytes =keyPair.getPrivate().getEncoded();
publicKeyBytes =keyPair.getPublic().getEncoded();
}
catch(Exception e){
93

e.printStackTrace();
}
}
public byte[] getPublicKey(){
return publicKeyBytes;
}
public byte[] getPrivateKey(){
return privateKeyBytes;
}
public byte[] Sign(String filedata,byte[] privatekeey){
byte[] signature=null;
try{
KeyFactory kf = KeyFactory.getInstance("DSA");
PrivateKey privateKey = kf.generatePrivate(new PKCS8EncodedKeySpec(privatekeey));
byte[] data = filedata.getBytes("UTF8");
Signature sig = Signature.getInstance("SHA1WithDSA");
sig.initSign(privateKey);
sig.update(data);
signature= sig.sign();
}catch(Exception e){
94
}
}
public byte[] getPublicKey(){
return publicKeyBytes;
}
public byte[] getPrivateKey(){
return privateKeyBytes;
}
public byte[] Sign(String filedata,byte[] privatekeey){
byte[] signature=null;
try{
KeyFactory kf = KeyFactory.getInstance("DSA");
PrivateKey privateKey = kf.generatePrivate(new PKCS8EncodedKeySpec(privatekeey));
byte[] data = filedata.getBytes("UTF8");
Signature sig = Signature.getInstance("SHA1WithDSA");
sig.initSign(privateKey);
sig.update(data);
signature= sig.sign();
}catch(Exception e){
94
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

e.printStackTrace();
}
return signature;
}
public boolean Verify(String filedata,byte[] publickkey,byte[] signature){
boolean sts=false;
try{
KeyFactory kf = KeyFactory.getInstance("DSA");
PublicKey publicKey = kf.generatePublic(new X509EncodedKeySpec(publickkey));
Signature sig = Signature.getInstance("SHA1WithDSA");
sig.initVerify(publicKey);
sig.update(filedata.getBytes());
sts=sig.verify(signature);
}catch(Exception e){
e.printStackTrace();
}
return sts;
}
}
/* Code For AP Module*/
<%@ include file="header.jsp"%>
<!-- //banner -->
<!-- contact -->
<section class="contact-w3ls">
<div class="container">
<div class="wthree-heading">
<h2 class="w3l-titles">Authorized Party</h2>
95
}
return signature;
}
public boolean Verify(String filedata,byte[] publickkey,byte[] signature){
boolean sts=false;
try{
KeyFactory kf = KeyFactory.getInstance("DSA");
PublicKey publicKey = kf.generatePublic(new X509EncodedKeySpec(publickkey));
Signature sig = Signature.getInstance("SHA1WithDSA");
sig.initVerify(publicKey);
sig.update(filedata.getBytes());
sts=sig.verify(signature);
}catch(Exception e){
e.printStackTrace();
}
return sts;
}
}
/* Code For AP Module*/
<%@ include file="header.jsp"%>
<!-- //banner -->
<!-- contact -->
<section class="contact-w3ls">
<div class="container">
<div class="wthree-heading">
<h2 class="w3l-titles">Authorized Party</h2>
95

<p class="quia">Enter userName&Password</p>
</div>
<div class="con-top">
<%
String msg1 = request.getParameter("msg1");
if(msg1 != null){
out.println("<script>alert('Login Fail..')</script>");
}
%>
<div class="col-lg-10 col-md-10 col-sm-10 contact-w3-agile2" data-
aos="flip-left">
<div class="contact-agileits">
<h4>Login</h4>
<form action="apcheck.jsp" method="post">
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">Name:</label>
<input type="text" class="form-control" name="unm" id="name"
Placeholder=" " required="">
<p class="help-block"></p>
</div>
</div>
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">Password:</label>
<input type="Password" class="form-control" name="pwd" id="phone"
Placeholder=" " required="">
<p class="help-block"></p>
</div>
</div>
<div id="success"></div>
<!-- For success/fail messages -->
<button type="submit" class="btn btn-primary">Login</button>
96
</div>
<div class="con-top">
<%
String msg1 = request.getParameter("msg1");
if(msg1 != null){
out.println("<script>alert('Login Fail..')</script>");
}
%>
<div class="col-lg-10 col-md-10 col-sm-10 contact-w3-agile2" data-
aos="flip-left">
<div class="contact-agileits">
<h4>Login</h4>
<form action="apcheck.jsp" method="post">
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">Name:</label>
<input type="text" class="form-control" name="unm" id="name"
Placeholder=" " required="">
<p class="help-block"></p>
</div>
</div>
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">Password:</label>
<input type="Password" class="form-control" name="pwd" id="phone"
Placeholder=" " required="">
<p class="help-block"></p>
</div>
</div>
<div id="success"></div>
<!-- For success/fail messages -->
<button type="submit" class="btn btn-primary">Login</button>
96

</form>
</div>
</div>
<div class="clearfix"></div>
</div>
</div>
</section>
<!-- map -->
<!-- footer -->
<%@ include file="footer.jsp"%>
/* Code For proxy reencryption*/
package PRE;
import it.unisa.dia.gas.jpbc.Element;
import java.io.BufferedWriter;
import java.io.File;
import java.io.FileNotFoundException;
import java.io.FileWriter;
import it.unisa.dia.gas.plaf.jpbc.pairing.PairingFactory;
import javax.crypto.Cipher;
import it.unisa.dia.gas.jpbc.*;
import java.io.IOException;
import java.util.*;
import java.math.BigInteger;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.Signature;
import java.security.*;
import java.security.spec.X509EncodedKeySpec;
import java.security.spec.*;
import java.util.Scanner;
import java.sql.*;
import java.security.*;
import java.security.spec.*;
97
</div>
</div>
<div class="clearfix"></div>
</div>
</div>
</section>
<!-- map -->
<!-- footer -->
<%@ include file="footer.jsp"%>
/* Code For proxy reencryption*/
package PRE;
import it.unisa.dia.gas.jpbc.Element;
import java.io.BufferedWriter;
import java.io.File;
import java.io.FileNotFoundException;
import java.io.FileWriter;
import it.unisa.dia.gas.plaf.jpbc.pairing.PairingFactory;
import javax.crypto.Cipher;
import it.unisa.dia.gas.jpbc.*;
import java.io.IOException;
import java.util.*;
import java.math.BigInteger;
import java.security.KeyPair;
import java.security.KeyPairGenerator;
import java.security.Signature;
import java.security.*;
import java.security.spec.X509EncodedKeySpec;
import java.security.spec.*;
import java.util.Scanner;
import java.sql.*;
import java.security.*;
import java.security.spec.*;
97
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

import PRE.*;
import it.unisa.dia.gas.plaf.jpbc.pairing.PairingFactory;
import it.unisa.dia.gas.jpbc.Field;
import java.io.*;
public class ProxyReEncryption {
private static BigInteger KEY ,n;
static String PRE="RSA";
private static Element publicKey;
private static Element privatekey;
static Pairing pairing;
private int bitlength = 1024;
private Random r;
public static Element getPublicKey(){
pairing= PairingManager.defaultPairing;
publicKey = pairing.getZr().newRandomElement().getImmutable();
return publicKey;
}
public static Element getPrivateKey(){
privatekey = pairing.getZr().newRandomElement().getImmutable();
return privatekey;
}
public static byte[] encrypt(String dek1,PublicKey appublickey) throws Exception{
KeyPairGenerator kpg = KeyPairGenerator.getInstance(PRE);
Cipher cipher = Cipher.getInstance(PRE);
cipher.init(Cipher.ENCRYPT_MODE, appublickey);
byte[] CK1= cipher.doFinal(dek1.getBytes());
98
import it.unisa.dia.gas.plaf.jpbc.pairing.PairingFactory;
import it.unisa.dia.gas.jpbc.Field;
import java.io.*;
public class ProxyReEncryption {
private static BigInteger KEY ,n;
static String PRE="RSA";
private static Element publicKey;
private static Element privatekey;
static Pairing pairing;
private int bitlength = 1024;
private Random r;
public static Element getPublicKey(){
pairing= PairingManager.defaultPairing;
publicKey = pairing.getZr().newRandomElement().getImmutable();
return publicKey;
}
public static Element getPrivateKey(){
privatekey = pairing.getZr().newRandomElement().getImmutable();
return privatekey;
}
public static byte[] encrypt(String dek1,PublicKey appublickey) throws Exception{
KeyPairGenerator kpg = KeyPairGenerator.getInstance(PRE);
Cipher cipher = Cipher.getInstance(PRE);
cipher.init(Cipher.ENCRYPT_MODE, appublickey);
byte[] CK1= cipher.doFinal(dek1.getBytes());
98

return CK1;
}
public static byte[] decrypt(String CK1,PrivateKey apprivatekey) throws Exception{
KeyPairGenerator kpg = KeyPairGenerator.getInstance(PRE);
Cipher cipher = Cipher.getInstance(PRE);
cipher.init(Cipher.DECRYPT_MODE, apprivatekey);
byte[] DEK1= cipher.doFinal(CK1.getBytes());
return DEK1;
}
public static Element getReEncryptionKey(byte[] upk,byte[] osk)
{
Pairing pairing = PairingFactory.getPairing("curve.properties");
Field G1 = pairing.getG1();
return G1.newRandomElement().setFromHash(upk,0,
upk.length).setFromHash(osk,0, osk.length);
}
}
/* Code For CSP View file data*/
<head>
<script>input[type=submit] {
background:url(images/lg.jpg);
}</script>
<link href="style.css" rel="stylesheet" type="text/css" />
<script>
function f1Submit() {
alert('Request sent to AP');
alert('Wait until get the Symmetric ( DEK1 )');
document.f1.action="req1.jsp";
document.f1.submit();
99
}
public static byte[] decrypt(String CK1,PrivateKey apprivatekey) throws Exception{
KeyPairGenerator kpg = KeyPairGenerator.getInstance(PRE);
Cipher cipher = Cipher.getInstance(PRE);
cipher.init(Cipher.DECRYPT_MODE, apprivatekey);
byte[] DEK1= cipher.doFinal(CK1.getBytes());
return DEK1;
}
public static Element getReEncryptionKey(byte[] upk,byte[] osk)
{
Pairing pairing = PairingFactory.getPairing("curve.properties");
Field G1 = pairing.getG1();
return G1.newRandomElement().setFromHash(upk,0,
upk.length).setFromHash(osk,0, osk.length);
}
}
/* Code For CSP View file data*/
<head>
<script>input[type=submit] {
background:url(images/lg.jpg);
}</script>
<link href="style.css" rel="stylesheet" type="text/css" />
<script>
function f1Submit() {
alert('Request sent to AP');
alert('Wait until get the Symmetric ( DEK1 )');
document.f1.action="req1.jsp";
document.f1.submit();
99

}
</script>
</head>
</head>
<%@ include file="UserHeader.jsp"%>
<%@ page import="database.*"%>
<%@ page import="java.sql.*"%>
<%! String hash=null;%>
<%
String fid=request.getParameter("fid");
String csp=request.getParameter("csp");
Connection con=databasecon.getconnection();
Statement st=con.createStatement();
ResultSet rs=st.executeQuery("select *from "+csp+" where fid='"+fid+"' ");
if(rs.next())
{
%>
<section class="contact-w3ls">
<div class="container">
<div class="wthree-heading">
<h2 class="w3l_header">File Details</h2>
<p class="quia">Encrypted Data</p>
</div>
<div class="con-top">
<div class="col-lg-6 col-md-6 col-sm-6 contact-w3-agile2" data-aos="flip-
left">
<div class="contact-agileits">
<form name="f1" method="post">
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">File Id</label>
<input type="text" class="form-control" name="fid" id="name" value="<
%=rs.getString("fid")%>" Placeholder=" " readonly required="">
100
</script>
</head>
</head>
<%@ include file="UserHeader.jsp"%>
<%@ page import="database.*"%>
<%@ page import="java.sql.*"%>
<%! String hash=null;%>
<%
String fid=request.getParameter("fid");
String csp=request.getParameter("csp");
Connection con=databasecon.getconnection();
Statement st=con.createStatement();
ResultSet rs=st.executeQuery("select *from "+csp+" where fid='"+fid+"' ");
if(rs.next())
{
%>
<section class="contact-w3ls">
<div class="container">
<div class="wthree-heading">
<h2 class="w3l_header">File Details</h2>
<p class="quia">Encrypted Data</p>
</div>
<div class="con-top">
<div class="col-lg-6 col-md-6 col-sm-6 contact-w3-agile2" data-aos="flip-
left">
<div class="contact-agileits">
<form name="f1" method="post">
<div class="control-group form-group">
<div class="controls">
<label class="contact-p1">File Id</label>
<input type="text" class="form-control" name="fid" id="name" value="<
%=rs.getString("fid")%>" Placeholder=" " readonly required="">
100
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

<p class="help-block"></p>
</div>
<div class="controls">
<label class="contact-p1">File Name:</label>
<input type="text" class="form-control" name="filename" id="name"
value="<%=rs.getString("fname")%>" Placeholder=" "readonly required="">
<p class="help-block"></p>
</div>
<div class="controls">
<label class="contact-p1">Encrypted Data:</label>
<textarea readonly class="form-
control" name="encfile" rows="7"><%=new String(rs.getBytes("encfile"))%></textarea>
<p class="help-block"></p>
</div>
</form>
</div>
</div>
<div class="clearfix"></div>
</div>
</div>
</section>
<%}
else
{
response.sendRedirect("FileDownload.jsp?file=decfail");
}%><br><br><br>
<%@ include file="Footer1.jsp"%>
/* Code For file Download*/
<%@ include file="UserHeader.jsp"%>
<%@ page import="database.*"%>
101
</div>
<div class="controls">
<label class="contact-p1">File Name:</label>
<input type="text" class="form-control" name="filename" id="name"
value="<%=rs.getString("fname")%>" Placeholder=" "readonly required="">
<p class="help-block"></p>
</div>
<div class="controls">
<label class="contact-p1">Encrypted Data:</label>
<textarea readonly class="form-
control" name="encfile" rows="7"><%=new String(rs.getBytes("encfile"))%></textarea>
<p class="help-block"></p>
</div>
</form>
</div>
</div>
<div class="clearfix"></div>
</div>
</div>
</section>
<%}
else
{
response.sendRedirect("FileDownload.jsp?file=decfail");
}%><br><br><br>
<%@ include file="Footer1.jsp"%>
/* Code For file Download*/
<%@ include file="UserHeader.jsp"%>
<%@ page import="database.*"%>
101

<%@ page import="java.sql.*,java.util.*"%>
<%
String msg = request.getParameter("file");
if(msg !=null &&msg.equals("decfail")){
out.println("<script>alert('Failed To Descypt Data..')</script>");
}
if(msg !=null &&msg.equals("downloadfail")){
out.println("<script>alert('Failed To Download File..')</script>");
}
%>
<%
try{
Connection con=databasecon.getconnection();
Statement st=con.createStatement();
Statement st1=con.createStatement();
Statement st2=con.createStatement();
String id=(String)session.getAttribute("id");
String unm=(String)session.getAttribute("unm");
ResultSet rs=st.executeQuery("select * from "+uprovider+" where unm='"+unm+"' and
id='"+id+"' ");
ResultSet rs1=st1.executeQuery("select * from sharing where sharedusers_id='"+id+"' and
share_provider='"+uprovider+"'");
%>
<br><br>
<div class="wthree-heading">
<h2 class="w3l_header">File Download </h2>
</div>
<div class="container">
<div class="bs-docs-example">
<table class="table table-hover">
<thead>
<tr>
102
<%
String msg = request.getParameter("file");
if(msg !=null &&msg.equals("decfail")){
out.println("<script>alert('Failed To Descypt Data..')</script>");
}
if(msg !=null &&msg.equals("downloadfail")){
out.println("<script>alert('Failed To Download File..')</script>");
}
%>
<%
try{
Connection con=databasecon.getconnection();
Statement st=con.createStatement();
Statement st1=con.createStatement();
Statement st2=con.createStatement();
String id=(String)session.getAttribute("id");
String unm=(String)session.getAttribute("unm");
ResultSet rs=st.executeQuery("select * from "+uprovider+" where unm='"+unm+"' and
id='"+id+"' ");
ResultSet rs1=st1.executeQuery("select * from sharing where sharedusers_id='"+id+"' and
share_provider='"+uprovider+"'");
%>
<br><br>
<div class="wthree-heading">
<h2 class="w3l_header">File Download </h2>
</div>
<div class="container">
<div class="bs-docs-example">
<table class="table table-hover">
<thead>
<tr>
102

<th>DataHolder_Id</th>
<th>DataHolder_Name</th>
<th>File Id</th>
<th>File Name</th>
<th>Provider</th>
<th>View</th>
</tr>
</thead>
<tbody>
<%
while(rs.next())
{
%>
<tr><td><%=rs.getString("id")%></td>
<td><%=rs.getString("unm")%></td>
<td><%=rs.getString("fid")%></td>
<td><%=rs.getString("fname")%></td>
<td><%=rs.getString("fprovider")%></td>
<td><a href="ViewFileData.jsp?fid=<
%=rs.getString("fid")%>&&id=<%=rs.getString("id")%>&&csp=<
%=rs.getString("fprovider")%>">view</a></td>
</tr>
<%
}
while(rs1.next())
{
ResultSet rs2=st2.executeQuery("select fname from
"+rs1.getString("owner_provider")+" where fid="+rs1.getString("rfid")+" ");
if(rs2.next()){
System.out.println("rs2.next()");
%>
<tr>
103
<th>DataHolder_Name</th>
<th>File Id</th>
<th>File Name</th>
<th>Provider</th>
<th>View</th>
</tr>
</thead>
<tbody>
<%
while(rs.next())
{
%>
<tr><td><%=rs.getString("id")%></td>
<td><%=rs.getString("unm")%></td>
<td><%=rs.getString("fid")%></td>
<td><%=rs.getString("fname")%></td>
<td><%=rs.getString("fprovider")%></td>
<td><a href="ViewFileData.jsp?fid=<
%=rs.getString("fid")%>&&id=<%=rs.getString("id")%>&&csp=<
%=rs.getString("fprovider")%>">view</a></td>
</tr>
<%
}
while(rs1.next())
{
ResultSet rs2=st2.executeQuery("select fname from
"+rs1.getString("owner_provider")+" where fid="+rs1.getString("rfid")+" ");
if(rs2.next()){
System.out.println("rs2.next()");
%>
<tr>
103
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

<td><%=rs1.getString("owner_id")%></td>
<td><%=rs1.getString("owner_name")%></td>
<td><%=rs1.getString("rfid")%></td>
<td><%=rs2.getString("fname")%></td>
<td><
%=rs1.getString("owner_provider")%></td>
<td><a href="SharedViewFileData.jsp?
owner_id=<%=rs1.getString("owner_id")%>&&rfid=<%=rs1.getString("rfid")%>&&csp=<
%=rs1.getString("owner_provider")%>">view</a></td>
</tr>
<%
}
}}
catch(Exception e)
{e.printStackTrace();}
%>
</tbody>
</table>
</div>
</div>
<br><br><br><br><br><br>
<%@ include file="Footer1.jsp"%>
/* Code For file Upload*/
<%@ include file="UserHeader.jsp"%>
<%@ page import="database.*"%>
<%@ page import="java.sql.*"%>
<%
String msg = request.getParameter("msg");
String fileid = request.getParameter("fid");
String fileprovider = request.getParameter("fp");
if(msg !=null){
104
<td><%=rs1.getString("owner_name")%></td>
<td><%=rs1.getString("rfid")%></td>
<td><%=rs2.getString("fname")%></td>
<td><
%=rs1.getString("owner_provider")%></td>
<td><a href="SharedViewFileData.jsp?
owner_id=<%=rs1.getString("owner_id")%>&&rfid=<%=rs1.getString("rfid")%>&&csp=<
%=rs1.getString("owner_provider")%>">view</a></td>
</tr>
<%
}
}}
catch(Exception e)
{e.printStackTrace();}
%>
</tbody>
</table>
</div>
</div>
<br><br><br><br><br><br>
<%@ include file="Footer1.jsp"%>
/* Code For file Upload*/
<%@ include file="UserHeader.jsp"%>
<%@ page import="database.*"%>
<%@ page import="java.sql.*"%>
<%
String msg = request.getParameter("msg");
String fileid = request.getParameter("fid");
String fileprovider = request.getParameter("fp");
if(msg !=null){
104

out.println("<script>alert('Local Duplicate File')</script>");
out.println("<br> <h3> <font
style='color:blue'>Original File id is : </font><b style='color:green'>"+fileid+"</b>");
}
if(request.getParameter("msg1")!=null){
out.println("<script>alert('Duplicate File Shared Successfully')</script>");
}
if(request.getParameter("upload")!=null){
out.println("<script>alert('Encrypted File Uploaded Successfully..!')</script>");
}
%><br><br><br>
<div align="center">
<div class="wthree-heading">
<h2 class="w3l_header">File Upload</h2>
</div>
<br>
<form action="FileUpload1.jsp" method="post" enctype="multipart/form-data">
<div class="control-group form-group">
<div class="controls">
<input type="file" name="filename" required="">
<p class="help-block"></p>
</div>
</div>
<div id="success"></div>
<!-- For success/fail messages -->
<button type="submit" class="btn btn-primary">Get File Data</button>
</form>
105
out.println("<br> <h3> <font
style='color:blue'>Original File id is : </font><b style='color:green'>"+fileid+"</b>");
}
if(request.getParameter("msg1")!=null){
out.println("<script>alert('Duplicate File Shared Successfully')</script>");
}
if(request.getParameter("upload")!=null){
out.println("<script>alert('Encrypted File Uploaded Successfully..!')</script>");
}
%><br><br><br>
<div align="center">
<div class="wthree-heading">
<h2 class="w3l_header">File Upload</h2>
</div>
<br>
<form action="FileUpload1.jsp" method="post" enctype="multipart/form-data">
<div class="control-group form-group">
<div class="controls">
<input type="file" name="filename" required="">
<p class="help-block"></p>
</div>
</div>
<div id="success"></div>
<!-- For success/fail messages -->
<button type="submit" class="btn btn-primary">Get File Data</button>
</form>
105
1 out of 105
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.
