Ecommerce and Governance Security
VerifiedAdded on 2022/11/13
|8
|1575
|493
AI Summary
This report discusses the vulnerabilities in an online banking web application and how to fix them. It covers topics such as CSRF, SQL injection, session management, and more. The report also provides recommendations for improving the security of the website. Desklib provides solved assignments, essays, and dissertations for students.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Ecommerce and Governance Security
NAME:
COURSE:
QUESTION:
First, solve your assigned puzzle (Puzzle B112) using web application
exploitation techniques, provide screenshots, then write a report and discuss specifically
what type of mistake or overlook in codes, design or implementation has led to
successful exploitation. Research those existing vulnerabilities and explain what needs
to be changed to fix the problem. The report can be between 1000 to 1500 words. The
puzzles are on https://puzzle.academy
1
NAME:
COURSE:
QUESTION:
First, solve your assigned puzzle (Puzzle B112) using web application
exploitation techniques, provide screenshots, then write a report and discuss specifically
what type of mistake or overlook in codes, design or implementation has led to
successful exploitation. Research those existing vulnerabilities and explain what needs
to be changed to fix the problem. The report can be between 1000 to 1500 words. The
puzzles are on https://puzzle.academy
1
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Ecommerce and Governance Security
Solution to the puzzle
The money was transferred through Cross Site Request Forgery ( CSRF). The browser
William was using was fooled by an attackers 3rd party website which sent a request to
thttps://moonyland.com/banking/account.php using William’s cookie. He had login to one tab
on the home page which is https://moonyland.com/banking/index.php and the other tab which
is the account.php made the browser misuse its cookies on behalf of the hacker thus causing a
confused deputy problem. The site allows alteration of HTTP GET requests which are unsafe
thus allows alteration of the resource that is accessed. This can be prevented by implementing
secret tokens and storing then in hidden form fields that cannot be accessed by a 3rd party
site.
Application Vulnerabilities
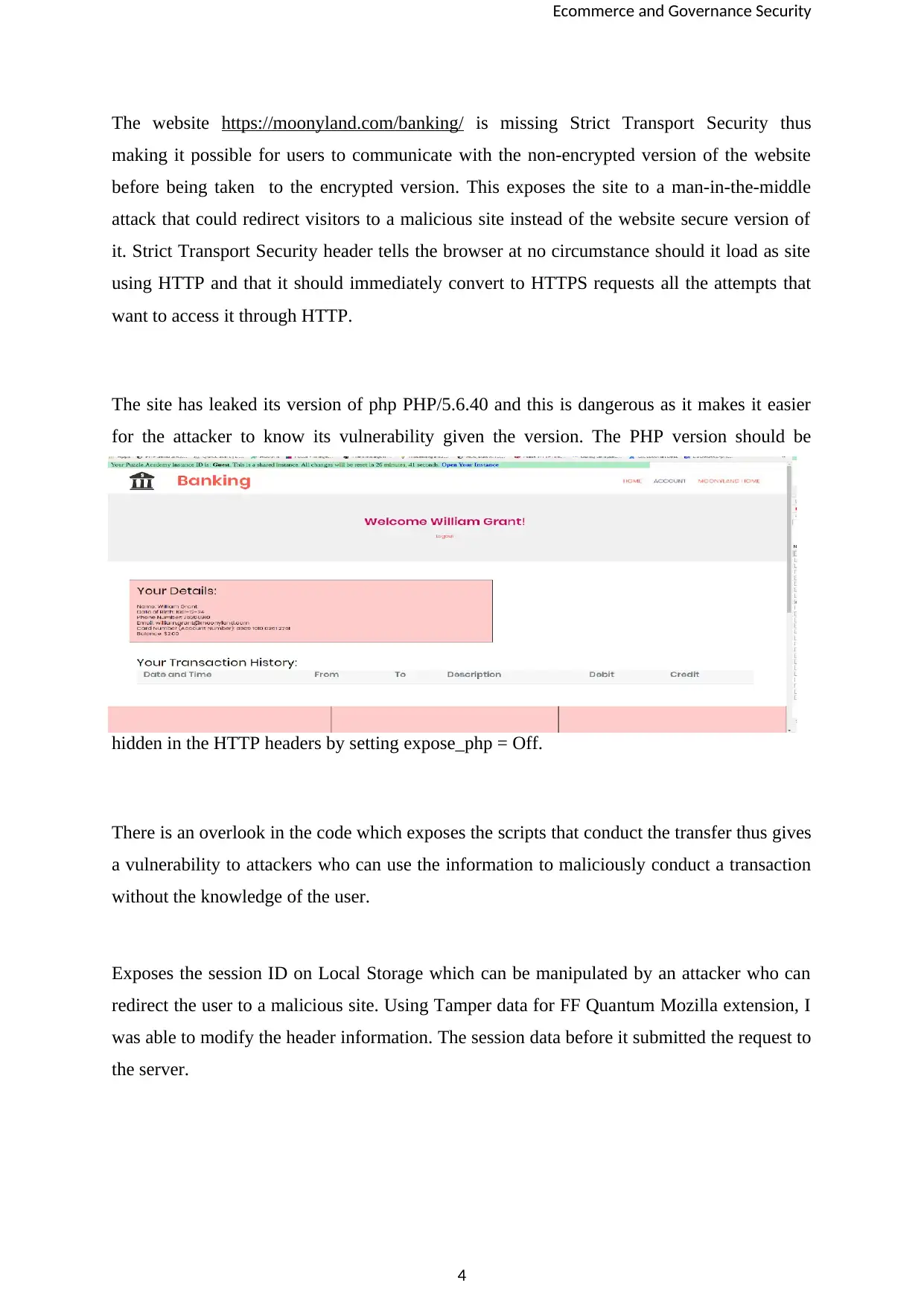
Firstly, the design makes the account vulnerable. Especially, where Williams details are Kept
openly. See the screenshot
This vulnerability of exposing the account details of william especially the card number thus
puts the account vulnerable to credential stealing attack (CSA), whereby the fraudsters can
gather users’ credentials through shoulder surfing and one can wipe out the account as the
card number and the account details are clearly exposed. This can be prevented by putting a
screen protector on your computer to make your screens obscure. Also, locking the computer
screen after a shorter period of inactivity to safeguard it especially when you leave your desk
or your laptop/tablet in a public place.
2
Solution to the puzzle
The money was transferred through Cross Site Request Forgery ( CSRF). The browser
William was using was fooled by an attackers 3rd party website which sent a request to
thttps://moonyland.com/banking/account.php using William’s cookie. He had login to one tab
on the home page which is https://moonyland.com/banking/index.php and the other tab which
is the account.php made the browser misuse its cookies on behalf of the hacker thus causing a
confused deputy problem. The site allows alteration of HTTP GET requests which are unsafe
thus allows alteration of the resource that is accessed. This can be prevented by implementing
secret tokens and storing then in hidden form fields that cannot be accessed by a 3rd party
site.
Application Vulnerabilities
Firstly, the design makes the account vulnerable. Especially, where Williams details are Kept
openly. See the screenshot
This vulnerability of exposing the account details of william especially the card number thus
puts the account vulnerable to credential stealing attack (CSA), whereby the fraudsters can
gather users’ credentials through shoulder surfing and one can wipe out the account as the
card number and the account details are clearly exposed. This can be prevented by putting a
screen protector on your computer to make your screens obscure. Also, locking the computer
screen after a shorter period of inactivity to safeguard it especially when you leave your desk
or your laptop/tablet in a public place.
2

Ecommerce and Governance Security
The site is missing security headers which is responsible for protection against attacks. The
missing security headers include: X-XSS protection against a certain cross-site-scripting
(XSS) attacks which can be enabled by adding X-XSS-Protection: 1; mode=block to the site.
The other missing security header is the X-Content-Type:nosniff exposes the user to a given
type of drive-by-downloads that results in unintentional download of malicious code to a
device that leaves it exposed to cyberattack and also phishing. Internet Explorer browser is
normally the one addressed to with this type of attack. Enabling this will improve the security
of the site and the user against this attack as it will instruct the browser to stop loading web
pages when it detects any Cross-Site Scripting attacks.
The anti-clickjacking X-Frame-Options header is not present, this exposed the user to
Clickjacking as the attacker will utilize many transparent tricks that will trick the user mouse
clicks. The attacker will ‘hijack’ clicks meant for this page and rout them to a malicious
page. This can be done on a button which can result to the user for example, subscribing to a
newsletter without his/her consent. Keystrokes can also be hijacked and a user can be made
to believe they are typing their email or bank account which instead they are inputting their
details to an invisible frame put there by the attacker to collect their details. X-Frame-options
should be added to every page of the website.
3
The site is missing security headers which is responsible for protection against attacks. The
missing security headers include: X-XSS protection against a certain cross-site-scripting
(XSS) attacks which can be enabled by adding X-XSS-Protection: 1; mode=block to the site.
The other missing security header is the X-Content-Type:nosniff exposes the user to a given
type of drive-by-downloads that results in unintentional download of malicious code to a
device that leaves it exposed to cyberattack and also phishing. Internet Explorer browser is
normally the one addressed to with this type of attack. Enabling this will improve the security
of the site and the user against this attack as it will instruct the browser to stop loading web
pages when it detects any Cross-Site Scripting attacks.
The anti-clickjacking X-Frame-Options header is not present, this exposed the user to
Clickjacking as the attacker will utilize many transparent tricks that will trick the user mouse
clicks. The attacker will ‘hijack’ clicks meant for this page and rout them to a malicious
page. This can be done on a button which can result to the user for example, subscribing to a
newsletter without his/her consent. Keystrokes can also be hijacked and a user can be made
to believe they are typing their email or bank account which instead they are inputting their
details to an invisible frame put there by the attacker to collect their details. X-Frame-options
should be added to every page of the website.
3
Ecommerce and Governance Security
The website https://moonyland.com/banking/ is missing Strict Transport Security thus
making it possible for users to communicate with the non-encrypted version of the website
before being taken to the encrypted version. This exposes the site to a man-in-the-middle
attack that could redirect visitors to a malicious site instead of the website secure version of
it. Strict Transport Security header tells the browser at no circumstance should it load as site
using HTTP and that it should immediately convert to HTTPS requests all the attempts that
want to access it through HTTP.
The site has leaked its version of php PHP/5.6.40 and this is dangerous as it makes it easier
for the attacker to know its vulnerability given the version. The PHP version should be
hidden in the HTTP headers by setting expose_php = Off.
There is an overlook in the code which exposes the scripts that conduct the transfer thus gives
a vulnerability to attackers who can use the information to maliciously conduct a transaction
without the knowledge of the user.
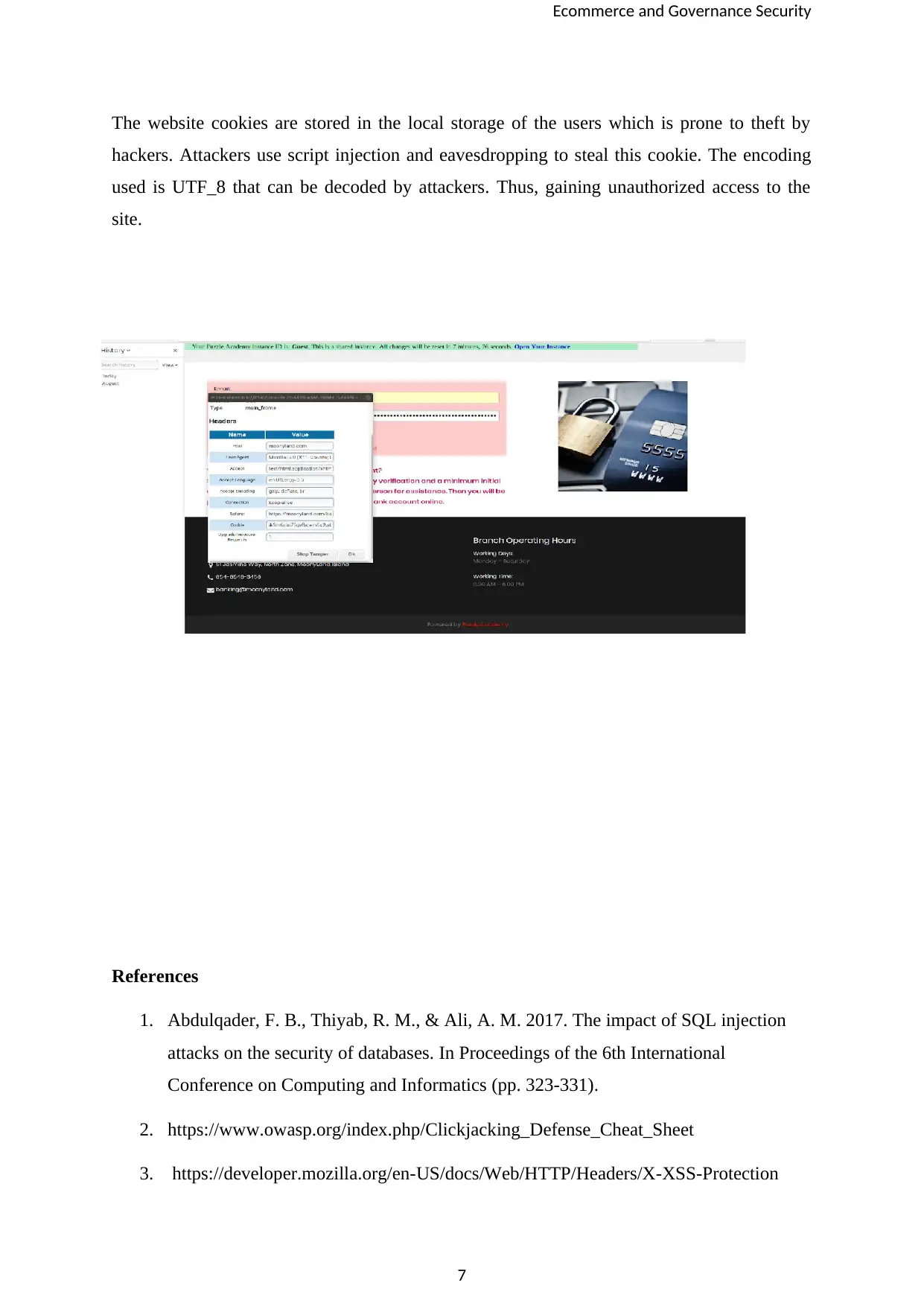
Exposes the session ID on Local Storage which can be manipulated by an attacker who can
redirect the user to a malicious site. Using Tamper data for FF Quantum Mozilla extension, I
was able to modify the header information. The session data before it submitted the request to
the server.
4
The website https://moonyland.com/banking/ is missing Strict Transport Security thus
making it possible for users to communicate with the non-encrypted version of the website
before being taken to the encrypted version. This exposes the site to a man-in-the-middle
attack that could redirect visitors to a malicious site instead of the website secure version of
it. Strict Transport Security header tells the browser at no circumstance should it load as site
using HTTP and that it should immediately convert to HTTPS requests all the attempts that
want to access it through HTTP.
The site has leaked its version of php PHP/5.6.40 and this is dangerous as it makes it easier
for the attacker to know its vulnerability given the version. The PHP version should be
hidden in the HTTP headers by setting expose_php = Off.
There is an overlook in the code which exposes the scripts that conduct the transfer thus gives
a vulnerability to attackers who can use the information to maliciously conduct a transaction
without the knowledge of the user.
Exposes the session ID on Local Storage which can be manipulated by an attacker who can
redirect the user to a malicious site. Using Tamper data for FF Quantum Mozilla extension, I
was able to modify the header information. The session data before it submitted the request to
the server.
4
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Ecommerce and Governance Security
I logged in the website using the URL
https://moonyland.com/banking/account.php/users.php?id=1
I was able to conduct operations in the site like updating my email and changing password.
After Adding /id=5 on the URL, It broke the website design also.
The page is vulnerable to sql injection which allows an attacker to tamper with the database
queries . It makes it possible for attackers to have access to data which normally they are
unable to get which includes a user data such as credit card details as in the case of williams
account or system data. The attacker can modify, delete this particular data hence causes
change to the application behaviour and also the content. Attackers attempt to insert
malicious SQL commands to the system using special variables which are targeting the
database. The website allowed blind SQL injection questions that mainly involved asking the
database a number of true or false queries with the attempt to get access to the vulnerable
code. I did this by querying the URL https://moonyland.com/banking/account.php/id=5.
SQL injection is prevented by the use of parameterized queries especially where untrusted
inputs appears as data inside the query instead of using string concatenation. Implement other
controls in inputs that allow hazardous characters such as passwords. Validating all data from
the client before they are processed and this includes all the HTTP header contents such as
cookie names and values, the URLs too
5
I logged in the website using the URL
https://moonyland.com/banking/account.php/users.php?id=1
I was able to conduct operations in the site like updating my email and changing password.
After Adding /id=5 on the URL, It broke the website design also.
The page is vulnerable to sql injection which allows an attacker to tamper with the database
queries . It makes it possible for attackers to have access to data which normally they are
unable to get which includes a user data such as credit card details as in the case of williams
account or system data. The attacker can modify, delete this particular data hence causes
change to the application behaviour and also the content. Attackers attempt to insert
malicious SQL commands to the system using special variables which are targeting the
database. The website allowed blind SQL injection questions that mainly involved asking the
database a number of true or false queries with the attempt to get access to the vulnerable
code. I did this by querying the URL https://moonyland.com/banking/account.php/id=5.
SQL injection is prevented by the use of parameterized queries especially where untrusted
inputs appears as data inside the query instead of using string concatenation. Implement other
controls in inputs that allow hazardous characters such as passwords. Validating all data from
the client before they are processed and this includes all the HTTP header contents such as
cookie names and values, the URLs too
5

Ecommerce and Governance Security
The website does not have authentication and password management. Especially on the
change passwords form. It does not have the same level of control as login or sign up. It
accepted the new password as any set of Character. I changed the password from willy3me to
Hello . I again changed from Hello to new and it did not prompt about the password strength
or the secure characters for the passwords. It does not ensure the complexity of passwords
thus makes the passwords vulnerable to attacks. It doesn’t result in validation failure upon
change of the password to any given characters, especially if the passwords are not strong. It
should ensure the passwords have alphabetic, numeric and special characters as well as the
password lengths.
Session management of the website is poor. Especially the logout function since it does not
terminate the associated sessions when the URL is bypassed. Logout functionality does not
work if it is accessed like this even if you click Logout. The URL changes to
https://moonyland.com/banking/account.php/logout.php but I am still logged in. The website
did not log me out after hours of inactivity. The session time did not refresh itself once it
expired. The cookies do not expire. It also allows more that one login to a specific account.
https://moonyland.com allows concurrent logins with the same user details I.e the user ID. It
maintains the same session identifier when the security changes to HTTPS from HTTP.
As an online banking web application. It should have a One Time Password (OTP) which can
be used for verification only once per a given authenticated transaction. This will protect the
user accounts since it is high security as they are usable within a short period of time like 30
seconds. OTPs are resistant to attacks.
6
The website does not have authentication and password management. Especially on the
change passwords form. It does not have the same level of control as login or sign up. It
accepted the new password as any set of Character. I changed the password from willy3me to
Hello . I again changed from Hello to new and it did not prompt about the password strength
or the secure characters for the passwords. It does not ensure the complexity of passwords
thus makes the passwords vulnerable to attacks. It doesn’t result in validation failure upon
change of the password to any given characters, especially if the passwords are not strong. It
should ensure the passwords have alphabetic, numeric and special characters as well as the
password lengths.
Session management of the website is poor. Especially the logout function since it does not
terminate the associated sessions when the URL is bypassed. Logout functionality does not
work if it is accessed like this even if you click Logout. The URL changes to
https://moonyland.com/banking/account.php/logout.php but I am still logged in. The website
did not log me out after hours of inactivity. The session time did not refresh itself once it
expired. The cookies do not expire. It also allows more that one login to a specific account.
https://moonyland.com allows concurrent logins with the same user details I.e the user ID. It
maintains the same session identifier when the security changes to HTTPS from HTTP.
As an online banking web application. It should have a One Time Password (OTP) which can
be used for verification only once per a given authenticated transaction. This will protect the
user accounts since it is high security as they are usable within a short period of time like 30
seconds. OTPs are resistant to attacks.
6
Ecommerce and Governance Security
The website cookies are stored in the local storage of the users which is prone to theft by
hackers. Attackers use script injection and eavesdropping to steal this cookie. The encoding
used is UTF_8 that can be decoded by attackers. Thus, gaining unauthorized access to the
site.
References
1. Abdulqader, F. B., Thiyab, R. M., & Ali, A. M. 2017. The impact of SQL injection
attacks on the security of databases. In Proceedings of the 6th International
Conference on Computing and Informatics (pp. 323-331).
2. https://www.owasp.org/index.php/Clickjacking_Defense_Cheat_Sheet
3. https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-XSS-Protection
7
The website cookies are stored in the local storage of the users which is prone to theft by
hackers. Attackers use script injection and eavesdropping to steal this cookie. The encoding
used is UTF_8 that can be decoded by attackers. Thus, gaining unauthorized access to the
site.
References
1. Abdulqader, F. B., Thiyab, R. M., & Ali, A. M. 2017. The impact of SQL injection
attacks on the security of databases. In Proceedings of the 6th International
Conference on Computing and Informatics (pp. 323-331).
2. https://www.owasp.org/index.php/Clickjacking_Defense_Cheat_Sheet
3. https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-XSS-Protection
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Ecommerce and Governance Security
4. https://www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet
5. https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Content-Type-
Options
6. How to Hack a Website: Online Example https://www.guru99.com/how-to-hack-
website.html
7. Kalman G. 10 Most common Web Security Vulnerabilities
https://www.toptal.com/security/10-most-common-web-security-vulnerabilities
8. Christopher Duffy, Mohit,, Cameron Buchanan, Terry Ip, Andrew Mabbitt, Benjamin
May, Dave Mound Python: Penetration Testing for Developers
8
4. https://www.owasp.org/index.php/HTTP_Strict_Transport_Security_Cheat_Sheet
5. https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Content-Type-
Options
6. How to Hack a Website: Online Example https://www.guru99.com/how-to-hack-
website.html
7. Kalman G. 10 Most common Web Security Vulnerabilities
https://www.toptal.com/security/10-most-common-web-security-vulnerabilities
8. Christopher Duffy, Mohit,, Cameron Buchanan, Terry Ip, Andrew Mabbitt, Benjamin
May, Dave Mound Python: Penetration Testing for Developers
8
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





