Electronic Crime and Digital Forensics Assignment 2022
Added on 2022-10-17
33 Pages2049 Words12 Views
Running head: Electronic Crime and Digital Forensics
Electronic Crime and Digital Forensics
Name of the Student
Name of the University
Author Note
Electronic Crime and Digital Forensics
Name of the Student
Name of the University
Author Note

Electronic Crime and Digital Forensics1
Table of Contents
Activity two:....................................................................................................................................4
Creating a new case:....................................................................................................................4
Addition of host or the files and devices:....................................................................................4
Initialize the process:...................................................................................................................4
Back-up of data and cloning for forensics:..................................................................................4
Data separation:...........................................................................................................................5
The generation of report:.............................................................................................................5
Creating a new case:....................................................................................................................5
Addition of host or the files and devices:....................................................................................6
Initialize the process:...................................................................................................................6
Back-up of data and cloning for forensics:..................................................................................6
Data separation:...........................................................................................................................6
The generation of report:.............................................................................................................7
Investigation:...............................................................................................................................7
pat-2009-12-11.mddramimage.zip:.........................................................................................7
jo-work-usb-2009-12-11.E01:...............................................................................................11
pat-2009-12-11.E01:..............................................................................................................17
• Who is spying on Pat?.................................................................................................................29
Table of Contents
Activity two:....................................................................................................................................4
Creating a new case:....................................................................................................................4
Addition of host or the files and devices:....................................................................................4
Initialize the process:...................................................................................................................4
Back-up of data and cloning for forensics:..................................................................................4
Data separation:...........................................................................................................................5
The generation of report:.............................................................................................................5
Creating a new case:....................................................................................................................5
Addition of host or the files and devices:....................................................................................6
Initialize the process:...................................................................................................................6
Back-up of data and cloning for forensics:..................................................................................6
Data separation:...........................................................................................................................6
The generation of report:.............................................................................................................7
Investigation:...............................................................................................................................7
pat-2009-12-11.mddramimage.zip:.........................................................................................7
jo-work-usb-2009-12-11.E01:...............................................................................................11
pat-2009-12-11.E01:..............................................................................................................17
• Who is spying on Pat?.................................................................................................................29

Electronic Crime and Digital Forensics2
• How are they doing it? Can you identify specific methods or software they have used to
facilitate this?.................................................................................................................................30
• Why is the employee spying on Pat?...........................................................................................32
• Is anyone else involved? Would you characterize them as accomplices?..................................32
Bibliography:.................................................................................................................................33
• How are they doing it? Can you identify specific methods or software they have used to
facilitate this?.................................................................................................................................30
• Why is the employee spying on Pat?...........................................................................................32
• Is anyone else involved? Would you characterize them as accomplices?..................................32
Bibliography:.................................................................................................................................33

Electronic Crime and Digital Forensics3
Activity two:
For investigation the files in activity two autopsy tool has been used. The following tasks have
been done by the autopsy tool.
Creating a new case:
After the autopsy tool has been started and the interface of the too is being initialized
with the facility on the environment in order to perform a digital data forensic that is effective
over the media that is specific. For creating new case, the create new case option should be
clicked from the graphical user interface of the autopsy tool. The name of the case and details of
location are filled in order to make sure its integrity. Then to make sure who is examining the
case is then fetched into the user interface.
Addition of host or the files and devices:
The analysis of the process begins with the data link that is given in the autopsy window.
Initialize the process:
In order to initialize the procedure, the configuration of wizard option is used in the
autopsy tool in order to finalize the data link that is being added for analysis.
Back-up of data and cloning for forensics:
After the above procedure, the data is saved automatically in order to avoid the loss of
data and then they are placed in the format as said in the previous step request as the look-up
hash, exit parser etc. The data is then stored in the folders as cache, temp, export file backup with
Activity two:
For investigation the files in activity two autopsy tool has been used. The following tasks have
been done by the autopsy tool.
Creating a new case:
After the autopsy tool has been started and the interface of the too is being initialized
with the facility on the environment in order to perform a digital data forensic that is effective
over the media that is specific. For creating new case, the create new case option should be
clicked from the graphical user interface of the autopsy tool. The name of the case and details of
location are filled in order to make sure its integrity. Then to make sure who is examining the
case is then fetched into the user interface.
Addition of host or the files and devices:
The analysis of the process begins with the data link that is given in the autopsy window.
Initialize the process:
In order to initialize the procedure, the configuration of wizard option is used in the
autopsy tool in order to finalize the data link that is being added for analysis.
Back-up of data and cloning for forensics:
After the above procedure, the data is saved automatically in order to avoid the loss of
data and then they are placed in the format as said in the previous step request as the look-up
hash, exit parser etc. The data is then stored in the folders as cache, temp, export file backup with

Electronic Crime and Digital Forensics4
the run time details and complete details about the procedure and can only be read by the
explorer of autopsy.
Data separation:
The separation of data is done as per the nature of the data as audio, video and some other
formats along with their files that are deleted and the files that are edited too. The specific details
of the documents and the details of metadata are retrieved using the autopsy tool. The next step is
the extraction using the autopsy tool. The files that are deleted and the other extra data are found
to be availed. The data that are present are detailed according to the criteria. The data that is in
the form of video can be played and examined. All the files that are in extension are named
according to their detail and nature. The details of the devices that are connected can reveal their
durations and establishments. The information that is about the software can be detailed.
The generation of report:
In this stage the details that are being retrieved are then formatted into a report for the
client or the case of use proceedings. The data format that is being required according to the
snapshot that is given is only possible with the version that is latest of the autopsy software.
These are the criteria’s that are required according to the preference of the client. The file of html
gives the data with the details that are limited or consolidated according to the policy of privacy
of data share according to the legal privacy policy f the government.
Creating a new case:
After the autopsy tool has been started and the interface of the too is being initialized
with the facility on the environment in order to perform a digital data forensic that is effective
the run time details and complete details about the procedure and can only be read by the
explorer of autopsy.
Data separation:
The separation of data is done as per the nature of the data as audio, video and some other
formats along with their files that are deleted and the files that are edited too. The specific details
of the documents and the details of metadata are retrieved using the autopsy tool. The next step is
the extraction using the autopsy tool. The files that are deleted and the other extra data are found
to be availed. The data that are present are detailed according to the criteria. The data that is in
the form of video can be played and examined. All the files that are in extension are named
according to their detail and nature. The details of the devices that are connected can reveal their
durations and establishments. The information that is about the software can be detailed.
The generation of report:
In this stage the details that are being retrieved are then formatted into a report for the
client or the case of use proceedings. The data format that is being required according to the
snapshot that is given is only possible with the version that is latest of the autopsy software.
These are the criteria’s that are required according to the preference of the client. The file of html
gives the data with the details that are limited or consolidated according to the policy of privacy
of data share according to the legal privacy policy f the government.
Creating a new case:
After the autopsy tool has been started and the interface of the too is being initialized
with the facility on the environment in order to perform a digital data forensic that is effective

Electronic Crime and Digital Forensics5
over the media that is specific. For creating new case, the create new case option should be
clicked from the graphical user interface of the autopsy tool. The name of the case and details of
location are filled in order to make sure its integrity. Then to make sure who is examining the
case is then fetched into the user interface.
Addition of host or the files and devices:
The analysis of the process begins with the data link that is given in the autopsy window.
Initialize the process:
In order to initialize the procedure, the configuration of wizard option is used in the
autopsy tool in order to finalize the data link that is being added for analysis.
Back-up of data and cloning for forensics:
After the above procedure, the data is saved automatically in order to avoid the loss of
data and then they are placed in the format as said in the previous step request as the look-up
hash, exit parser etc. The data is then stored in the folders as cache, temp, export file backup with
the run time details and complete details about the procedure and can only be read by the
explorer of autopsy.
Data separation:
The separation of data is done as per the nature of the data as audio, video and some other
formats along with their files that are deleted and the files that are edited too. The specific details
of the documents and the details of metadata are retrieved using the autopsy tool. The next step is
the extraction using the autopsy tool. The files that are deleted and the other extra data are found
to be availed. The data that are present are detailed according to the criteria. The data that is in
over the media that is specific. For creating new case, the create new case option should be
clicked from the graphical user interface of the autopsy tool. The name of the case and details of
location are filled in order to make sure its integrity. Then to make sure who is examining the
case is then fetched into the user interface.
Addition of host or the files and devices:
The analysis of the process begins with the data link that is given in the autopsy window.
Initialize the process:
In order to initialize the procedure, the configuration of wizard option is used in the
autopsy tool in order to finalize the data link that is being added for analysis.
Back-up of data and cloning for forensics:
After the above procedure, the data is saved automatically in order to avoid the loss of
data and then they are placed in the format as said in the previous step request as the look-up
hash, exit parser etc. The data is then stored in the folders as cache, temp, export file backup with
the run time details and complete details about the procedure and can only be read by the
explorer of autopsy.
Data separation:
The separation of data is done as per the nature of the data as audio, video and some other
formats along with their files that are deleted and the files that are edited too. The specific details
of the documents and the details of metadata are retrieved using the autopsy tool. The next step is
the extraction using the autopsy tool. The files that are deleted and the other extra data are found
to be availed. The data that are present are detailed according to the criteria. The data that is in

Electronic Crime and Digital Forensics6
the form of video can be played and examined. All the files that are in extension are named
according to their detail and nature. The details of the devices that are connected can reveal their
durations and establishments. The information that is about the software can be detailed.
The generation of report:
In this stage the details that are being retrieved are then formatted into a report for the
client or the case of use proceedings. The data format that is being required according to the
snapshot that is given is only possible with the version that is latest of the autopsy software.
These are the criteria’s that are required according to the preference of the client. The file of html
gives the data with the details that are limited or consolidated according to the policy of privacy
of data share according to the legal privacy policy f the government.
Investigation:
pat-2009-12-11.mddramimage.zip:
By investigation this file the results that have been got are given below:
the form of video can be played and examined. All the files that are in extension are named
according to their detail and nature. The details of the devices that are connected can reveal their
durations and establishments. The information that is about the software can be detailed.
The generation of report:
In this stage the details that are being retrieved are then formatted into a report for the
client or the case of use proceedings. The data format that is being required according to the
snapshot that is given is only possible with the version that is latest of the autopsy software.
These are the criteria’s that are required according to the preference of the client. The file of html
gives the data with the details that are limited or consolidated according to the policy of privacy
of data share according to the legal privacy policy f the government.
Investigation:
pat-2009-12-11.mddramimage.zip:
By investigation this file the results that have been got are given below:

Electronic Crime and Digital Forensics7
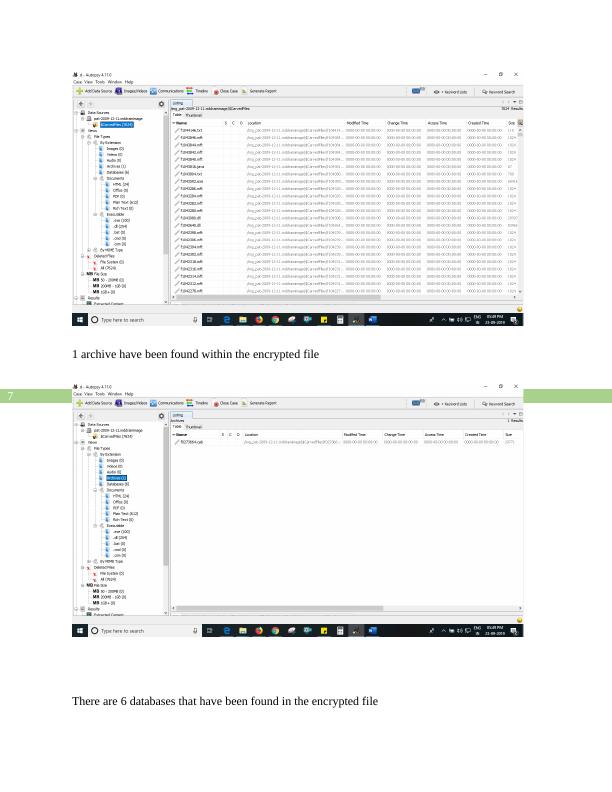
1 archive have been found within the encrypted file
There are 6 databases that have been found in the encrypted file
1 archive have been found within the encrypted file
There are 6 databases that have been found in the encrypted file
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Electronic Crime and Digital Forensics Assignment 2022lg...
|18
|1486
|14
Digital Forensics - Assignmentslg...
|39
|3425
|103
Demonstration of Autopsylg...
|22
|1475
|22
Digital forensics | Question and Answerlg...
|18
|1393
|19
Digital Forensic Investigation of USB Disk Image Filelg...
|21
|1701
|65
(Solution) Digital Forensics : PDFlg...
|22
|2968
|39
