ElGamal Cryptosystem: Key Generation, Encryption, Decryption Process
VerifiedAdded on 2023/06/15
|7
|1150
|264
Report
AI Summary
This report provides a detailed overview of the ElGamal cryptosystem, a public-key cryptosystem based on the discrete logarithm problem. It begins by introducing the ElGamal cryptosystem and its relationship to the Diffie-Hellman key exchange. The report then describes the procedure for key generation, detailing the steps Bob must take to generate a public and private key pair, including prime key and group generation, private key selection, and public key assembly and publishing. Next, the encryption process is explained from Alice's perspective, covering how she obtains Bob's public key, prepares the message for encoding, selects a random exponent, and computes the ciphertext. Finally, the report elucidates the decryption process that Bob undertakes upon receiving the encrypted message and the randomized public key, including computing the shared key and decrypting the message to recover the original plaintext. The report concludes with a list of references used in its preparation.

Running head: ELGAMAL CRYPTOSYSTEM
Elgamal Cryptosystem
Name of the Student
Name of the University
Author Note
Elgamal Cryptosystem
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ELGAMAL CRYPTOSYSTEM
Elgamal cryptosystem
Taher Elgamal first introduced and described the technique of the Elgamal cryptosystem
in the year of 1985. The system was closely related to the Diffie-Hellman key exchange which
provides the sharing of the secret key between Bob and Alice, but neither has the permission to
communicate otherwise. ElGamal abridged the Diffie-Hellman key exchange algorithm by
introducing a random exponent k. It is a public key cryptosystem which works on top of discrete
logarithm procedure (Balasubramaniam & Muthukumar, 2014). That is suppose every person has
a pair of key Sk, Pk, where Sk is the secret key and Pk is the public key. The task is to find the
secret key using the public key only. The cryptosystem has both the encryption and the
decryption schemes. The encryption system helps to people to send message in a unsecured
channel with the help of the secret key (Enriquez & Arboleda, 2017). The signature schemes like
the Schnorr signature scheme and Digital Signature Algorithm (DSA) are based on Elgamal
signature scheme but with shorter keys.
Key Generation Technique
The key generation technique used by the used by the Elgamal cystography is somewhat
similar to the general public key generators. In order to generate the key, the basic cryptographic
requirement are two keys for the asymmetrical and at least key for the symmetrical
algorithms.The receiver needs create the public key which can be passed through any public
channel in advance and publish it through the channel (Rao, 2017). Explaining the procedure of
the key generation technique suppose that Bob is generating the key and Alice is accepting the
key.
Elgamal cryptosystem
Taher Elgamal first introduced and described the technique of the Elgamal cryptosystem
in the year of 1985. The system was closely related to the Diffie-Hellman key exchange which
provides the sharing of the secret key between Bob and Alice, but neither has the permission to
communicate otherwise. ElGamal abridged the Diffie-Hellman key exchange algorithm by
introducing a random exponent k. It is a public key cryptosystem which works on top of discrete
logarithm procedure (Balasubramaniam & Muthukumar, 2014). That is suppose every person has
a pair of key Sk, Pk, where Sk is the secret key and Pk is the public key. The task is to find the
secret key using the public key only. The cryptosystem has both the encryption and the
decryption schemes. The encryption system helps to people to send message in a unsecured
channel with the help of the secret key (Enriquez & Arboleda, 2017). The signature schemes like
the Schnorr signature scheme and Digital Signature Algorithm (DSA) are based on Elgamal
signature scheme but with shorter keys.
Key Generation Technique
The key generation technique used by the used by the Elgamal cystography is somewhat
similar to the general public key generators. In order to generate the key, the basic cryptographic
requirement are two keys for the asymmetrical and at least key for the symmetrical
algorithms.The receiver needs create the public key which can be passed through any public
channel in advance and publish it through the channel (Rao, 2017). Explaining the procedure of
the key generation technique suppose that Bob is generating the key and Alice is accepting the
key.

2ELGAMAL CRYPTOSYSTEM
Bob will have to follow these following steps geniting the keypair.
1. Prime key and the group generation:
Initially Bob will have to generate a large prime number p and the generator g of a
multiplicative group (Z ∗ p) of the numerals modulo p.
2. The second task is to select the private key for the process.
In order to select the private key for the process Bob needs to select an integer b
from the group z randomly and with the help of the constraint 1 ≤ b ≤ p – 2 will
create the private exponent for the task (Kahate, 2013).
3. Public key assembling
After the above process is completed the and the private exponent is created, Bob
now can compute the public key part gb mod p. Here the Elgamal cryptosystem is
the triplet (p, g,pb) where b is the private key for the process.
4. Public key publishing
Now the private key b, public key p and is ready bob needs to transfer the public key
though any server or channel to Alice for advancing.
Encryption
In order to encrypt a message M for Bob, Alice will first require the public key triplet of
from any server or via any other medium. There is no security issue in this process, as the only
secret part b is sent as gb.
For the encryption of the plain text M Alice needs to follow the following:
Bob will have to follow these following steps geniting the keypair.
1. Prime key and the group generation:
Initially Bob will have to generate a large prime number p and the generator g of a
multiplicative group (Z ∗ p) of the numerals modulo p.
2. The second task is to select the private key for the process.
In order to select the private key for the process Bob needs to select an integer b
from the group z randomly and with the help of the constraint 1 ≤ b ≤ p – 2 will
create the private exponent for the task (Kahate, 2013).
3. Public key assembling
After the above process is completed the and the private exponent is created, Bob
now can compute the public key part gb mod p. Here the Elgamal cryptosystem is
the triplet (p, g,pb) where b is the private key for the process.
4. Public key publishing
Now the private key b, public key p and is ready bob needs to transfer the public key
though any server or channel to Alice for advancing.
Encryption
In order to encrypt a message M for Bob, Alice will first require the public key triplet of
from any server or via any other medium. There is no security issue in this process, as the only
secret part b is sent as gb.
For the encryption of the plain text M Alice needs to follow the following:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ELGAMAL CRYPTOSYSTEM
1. Alice will first need to obtain the public key of Bob and the triplet also.
2. Prepare the message M for encoding- that is integers (m1, m2, . . .) in the range of
{1, . . ., p − 1}. These integers will be encoded one by one.
3. Now Alice has to select a random experiment k that take places in Bobs private
exponent (Joye, 2016). The randomises in there is one of the key factors as the
possibility to guess that k gives a sensible amount of information which is
sensible amount of information which is necessary to decrypt a message.
4. After the completion of the given process, Alice needs to compute the public key
and to transmit the random exponent k to b, Alice needs to compute gk mod p and
combines it with the ciphertext that shall be sent to Bob (Jamgekar & Joshi,
2013).
5. After the completion of this steps the encryption process starts. For the encryption
process she iterates over the set created in step 2 and calculates for each of the mi
ci = m1
∗ (gb)k .
The desired cipher text C is the set of all the ci with 0 < i ≤ |M|. and this encrypted
message is sent to Bob along with the public keys.
Decryption of the text.
1. Bob receives the encoded message C and the randomized public key gk . In order
to compute the message, the first task to be done is understand the shared key that
is:
(g k ) p−1−b = (g k ) −b = b −bk
2. In order to decrypt the message Bob needs to follow the algorithm:
1. Alice will first need to obtain the public key of Bob and the triplet also.
2. Prepare the message M for encoding- that is integers (m1, m2, . . .) in the range of
{1, . . ., p − 1}. These integers will be encoded one by one.
3. Now Alice has to select a random experiment k that take places in Bobs private
exponent (Joye, 2016). The randomises in there is one of the key factors as the
possibility to guess that k gives a sensible amount of information which is
sensible amount of information which is necessary to decrypt a message.
4. After the completion of the given process, Alice needs to compute the public key
and to transmit the random exponent k to b, Alice needs to compute gk mod p and
combines it with the ciphertext that shall be sent to Bob (Jamgekar & Joshi,
2013).
5. After the completion of this steps the encryption process starts. For the encryption
process she iterates over the set created in step 2 and calculates for each of the mi
ci = m1
∗ (gb)k .
The desired cipher text C is the set of all the ci with 0 < i ≤ |M|. and this encrypted
message is sent to Bob along with the public keys.
Decryption of the text.
1. Bob receives the encoded message C and the randomized public key gk . In order
to compute the message, the first task to be done is understand the shared key that
is:
(g k ) p−1−b = (g k ) −b = b −bk
2. In order to decrypt the message Bob needs to follow the algorithm:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4ELGAMAL CRYPTOSYSTEM
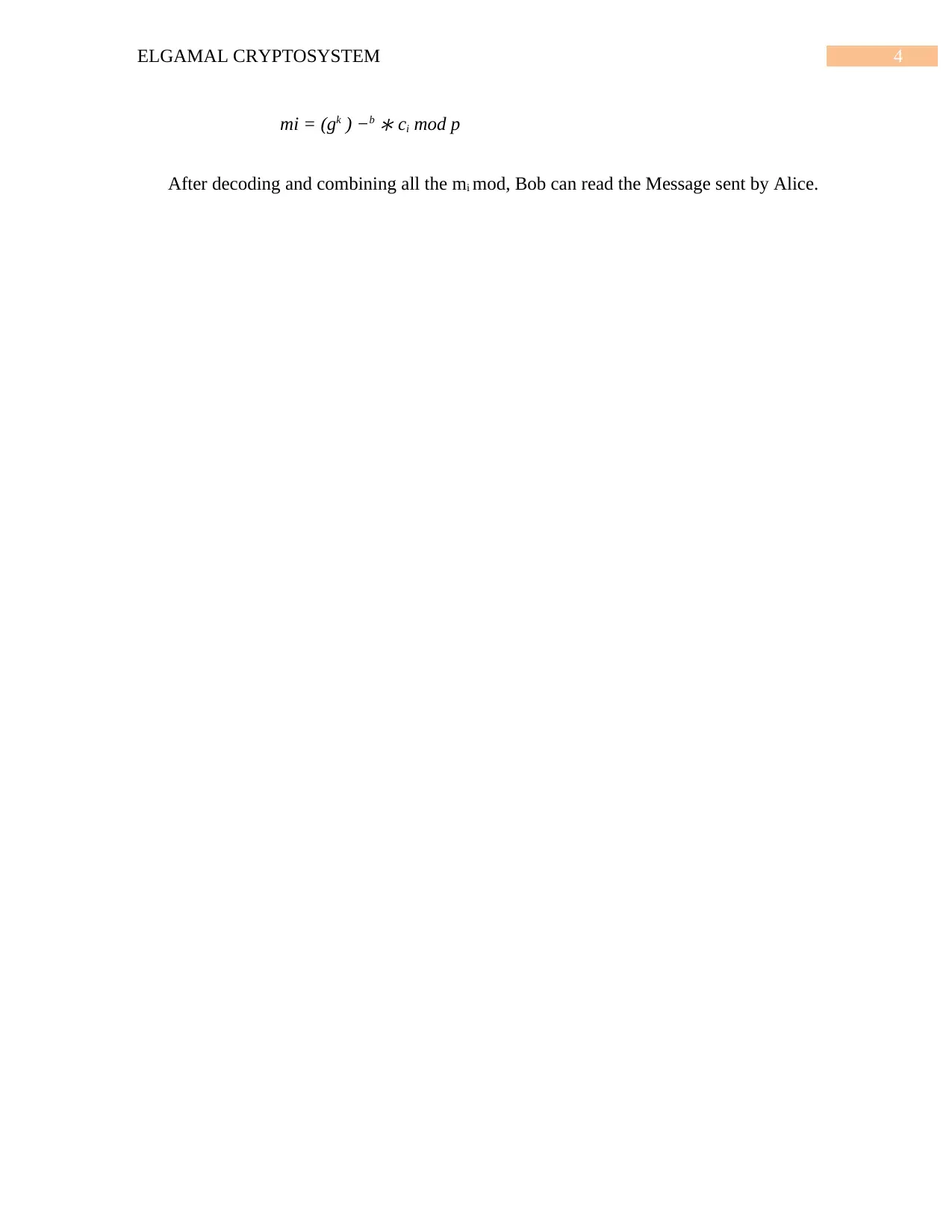
mi = (gk ) −b
∗ ci mod p
After decoding and combining all the mi mod, Bob can read the Message sent by Alice.
mi = (gk ) −b
∗ ci mod p
After decoding and combining all the mi mod, Bob can read the Message sent by Alice.

5ELGAMAL CRYPTOSYSTEM
References
Balasubramaniam, P., & Muthukumar, P. (2014). Synchronization of chaotic systems using
feedback controller: An application to Diffie–Hellman key exchange protocol and
ElGamal public key cryptosystem. Journal of the Egyptian Mathematical Society, 22(3),
365-372.
Enriquez, M., & Arboleda, E. (2017). Enhanced Hybrid Algorithm of Secure and Fast Chaos-
based, AES, RSA and ElGamal Cryptosystems. Indian Journal of Science and
Technology, 10(27).
Jamgekar, R. S., & Joshi, G. S. (2013). File encryption and decryption using secure
RSA. International Journal of Emerging Science and Engineering (IJESE), 1(4), 11-14.
Joye, M. (2016). Secure ElGamal-Type Cryptosystems Without Message Encoding. In The New
Codebreakers(pp. 470-478). Springer, Berlin, Heidelberg.
Kahate, A. (2013). Cryptography and network security. Tata McGraw-Hill Education.
Rao, F. Y. (2017). On the security of a variant of ELGamal encryption scheme. IEEE
Transactions on Dependable and Secure Computing.
References
Balasubramaniam, P., & Muthukumar, P. (2014). Synchronization of chaotic systems using
feedback controller: An application to Diffie–Hellman key exchange protocol and
ElGamal public key cryptosystem. Journal of the Egyptian Mathematical Society, 22(3),
365-372.
Enriquez, M., & Arboleda, E. (2017). Enhanced Hybrid Algorithm of Secure and Fast Chaos-
based, AES, RSA and ElGamal Cryptosystems. Indian Journal of Science and
Technology, 10(27).
Jamgekar, R. S., & Joshi, G. S. (2013). File encryption and decryption using secure
RSA. International Journal of Emerging Science and Engineering (IJESE), 1(4), 11-14.
Joye, M. (2016). Secure ElGamal-Type Cryptosystems Without Message Encoding. In The New
Codebreakers(pp. 470-478). Springer, Berlin, Heidelberg.
Kahate, A. (2013). Cryptography and network security. Tata McGraw-Hill Education.
Rao, F. Y. (2017). On the security of a variant of ELGamal encryption scheme. IEEE
Transactions on Dependable and Secure Computing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ELGAMAL CRYPTOSYSTEM
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





