Enforcing Information Technology: An Organizational Analysis
VerifiedAdded on 2020/04/07
|8
|2300
|97
Report
AI Summary
This report investigates the enforcement of information technology (IT) within organizations, focusing on essential components such as security policies, IT models, security standards, risk analysis, and contingency planning. The study utilizes Amazon as a case study to illustrate practical applications of these concepts. The report delves into the main content of security policies, including enforcement mechanisms, user access controls, security profiles, password requirements, anti-virus measures, and backup/recovery plans. It explores security standards like ISO 17799 and ISO 27001, alongside various security controls implemented by Amazon. Furthermore, the analysis covers risk analysis, contingency planning, and an examination of IT threats, vulnerabilities, and the tools employed by attackers. The report provides a comprehensive understanding of the challenges and strategies involved in securing IT environments.

Running head: ENFORCING INFORMATION TECHNOLOGY 1
How IT can be enforced in an organization
Name:
Institution Affiliation:
How IT can be enforced in an organization
Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENFORCING INFORMATION TECHNOLOGY 2
Introduction
For the organization to remain competitive on the global economy, it needs to adapt the ever
changing environment to which it will meet the needs of the customers (Aghion, Bloom & Van,
2013). When remaining competitive it means that the business continue to evolve as the
organization makes changes to the processes as well as the technology in order to gain the
competitive edge over their competition (Aghion, Bloom & Van, 2013). They should adapt on
the new technologies and be able to manage on the challenges which goes in the implementing.
A security policy that comprise of the appropriate phases of the implementation, enforcement,
auditing along with the review is important in protecting the organization IT. The information
technology could be useful in the business when it comes to solving some of the requirements of
the clients especially in the management of their personal data and the security information.
When there is an effective security policy there would be reduction of the risk particularly when
there is crisis in the organization (Bennett, Segerberg & Walker, 2014). There is need for an
organization to be in a position of understanding the Information technology to enable them to
overcome any shortcomings. In this essay it intends to investigate on how the information
technology could be enforced in an organization (Dowling, 2014). It will highlights the main
content of the information technology security policy and how they are determined.
Additionally, there are other components to which will be discussed such as the IT model for an
organization, the security standards and the controls, the risk analysis and the contingency
planning for the organization as well as the analysis of the IT threats, vulnerabilities as well as
tools (Botta, De, Persico & Pescapé, 2016). The research has chosen Amazon organization as the
basis for the analysis of the IT security.
Overview of the organization
Introduction
For the organization to remain competitive on the global economy, it needs to adapt the ever
changing environment to which it will meet the needs of the customers (Aghion, Bloom & Van,
2013). When remaining competitive it means that the business continue to evolve as the
organization makes changes to the processes as well as the technology in order to gain the
competitive edge over their competition (Aghion, Bloom & Van, 2013). They should adapt on
the new technologies and be able to manage on the challenges which goes in the implementing.
A security policy that comprise of the appropriate phases of the implementation, enforcement,
auditing along with the review is important in protecting the organization IT. The information
technology could be useful in the business when it comes to solving some of the requirements of
the clients especially in the management of their personal data and the security information.
When there is an effective security policy there would be reduction of the risk particularly when
there is crisis in the organization (Bennett, Segerberg & Walker, 2014). There is need for an
organization to be in a position of understanding the Information technology to enable them to
overcome any shortcomings. In this essay it intends to investigate on how the information
technology could be enforced in an organization (Dowling, 2014). It will highlights the main
content of the information technology security policy and how they are determined.
Additionally, there are other components to which will be discussed such as the IT model for an
organization, the security standards and the controls, the risk analysis and the contingency
planning for the organization as well as the analysis of the IT threats, vulnerabilities as well as
tools (Botta, De, Persico & Pescapé, 2016). The research has chosen Amazon organization as the
basis for the analysis of the IT security.
Overview of the organization
ENFORCING INFORMATION TECHNOLOGY 3
Amazon is an American electronic commerce as well as the cloud computing organization which
is based in Seattle, Washington. It is the largest internet based retailer across the globe by total
sales as well as the market capitalization (Cummings & Worley, 2014). The organization started
as an online bookstore and they later diversified to sell the DVDs, CDs as well as the video. The
organization offers consumer electronics and it is also one of the world largest provider of the
cloud infrastructure services (Cummings & Worley, 2014). The organization is also able to sell
the low end products such as the USB cable which are in house brand.
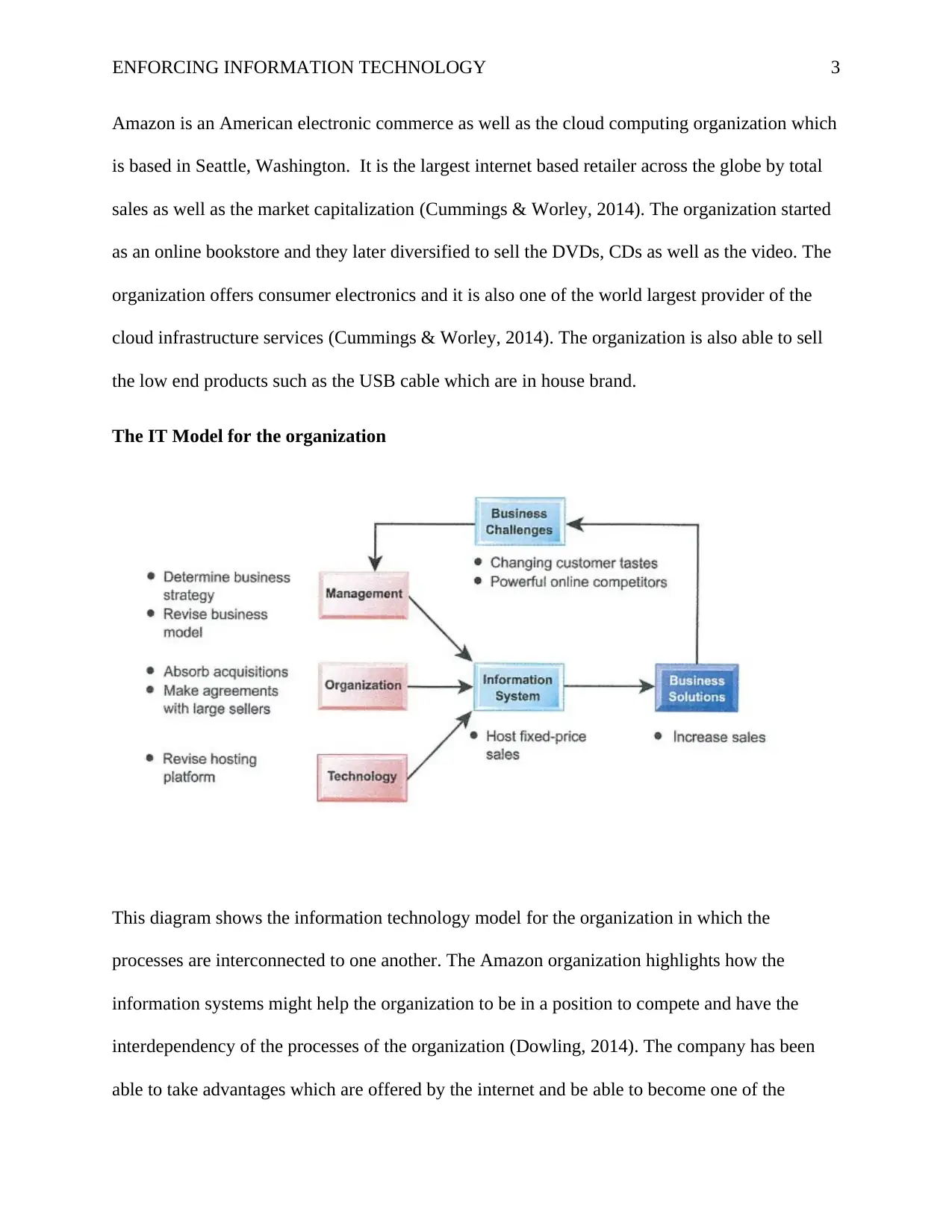
The IT Model for the organization
This diagram shows the information technology model for the organization in which the
processes are interconnected to one another. The Amazon organization highlights how the
information systems might help the organization to be in a position to compete and have the
interdependency of the processes of the organization (Dowling, 2014). The company has been
able to take advantages which are offered by the internet and be able to become one of the
Amazon is an American electronic commerce as well as the cloud computing organization which
is based in Seattle, Washington. It is the largest internet based retailer across the globe by total
sales as well as the market capitalization (Cummings & Worley, 2014). The organization started
as an online bookstore and they later diversified to sell the DVDs, CDs as well as the video. The
organization offers consumer electronics and it is also one of the world largest provider of the
cloud infrastructure services (Cummings & Worley, 2014). The organization is also able to sell
the low end products such as the USB cable which are in house brand.
The IT Model for the organization
This diagram shows the information technology model for the organization in which the
processes are interconnected to one another. The Amazon organization highlights how the
information systems might help the organization to be in a position to compete and have the
interdependency of the processes of the organization (Dowling, 2014). The company has been
able to take advantages which are offered by the internet and be able to become one of the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ENFORCING INFORMATION TECHNOLOGY 4
leading brand in the globe. Overtime they have been able to revise on their Information
technology model by acquiring some of the other businesses (Dowling, 2014). This model has
enabled them to become more competitive as well as cater for the needs of the organization in
terms of provision of security.
Main content of the security policy
The security policy should entail a well-defined security vision for the organization. The security
vision should be very clear as well as concise and is able to convey to the readers the intent of
the policy. Moreover, also included in the section should be able to detail of what if any security
standards of the organization has been following. Example is the ISO 27001 information security
management system. The following are the main components of the security policy;
On the first section is enforcement: in this section of the security policy it identifies how the
policy would be enforced and how the security breaches or perhaps the misconduct are to be
handled (Holtshouse, 2013). Whatever the enforcement action which will be undertaken they
should be cohesive to the actions which are already in place for any given enterprise security
breaches.
The user Access to the computer resource: on the security policy this section identifies on the
roles as well as the responsibilities of the users who are accessing on the resources on the
network of the organization (Holtshouse, 2013). There should be procedures which are included
but they are not limited to obtaining of the network access as well as the application permissions,
or the prohibiting on the personal use of the organizational computer systems.
Security profiles: This section it outline the information which identifies how the security
profiles would be applied uniformly all across the common devices.
leading brand in the globe. Overtime they have been able to revise on their Information
technology model by acquiring some of the other businesses (Dowling, 2014). This model has
enabled them to become more competitive as well as cater for the needs of the organization in
terms of provision of security.
Main content of the security policy
The security policy should entail a well-defined security vision for the organization. The security
vision should be very clear as well as concise and is able to convey to the readers the intent of
the policy. Moreover, also included in the section should be able to detail of what if any security
standards of the organization has been following. Example is the ISO 27001 information security
management system. The following are the main components of the security policy;
On the first section is enforcement: in this section of the security policy it identifies how the
policy would be enforced and how the security breaches or perhaps the misconduct are to be
handled (Holtshouse, 2013). Whatever the enforcement action which will be undertaken they
should be cohesive to the actions which are already in place for any given enterprise security
breaches.
The user Access to the computer resource: on the security policy this section identifies on the
roles as well as the responsibilities of the users who are accessing on the resources on the
network of the organization (Holtshouse, 2013). There should be procedures which are included
but they are not limited to obtaining of the network access as well as the application permissions,
or the prohibiting on the personal use of the organizational computer systems.
Security profiles: This section it outline the information which identifies how the security
profiles would be applied uniformly all across the common devices.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENFORCING INFORMATION TECHNOLOGY 5
Passwords: on this section it highlights on the requirements which are imposed to the users for
the passwords. The length, the character set as well as the password could be entered prior to
being disabled.
Anti-virus: this section identifies on the frequency for the updating on the files definition along
with how removable media, email attachment as well as the other files are scanned.
Backup and recovery: in a security policy it should have a comprehensive backup as well as a
recovery plan that is included (Franzoni & Sauermann, 2014). The section can be separated from
the initial policy as a whole and then included to the comprehensive business continuity template
plan for the Amazon organization.
Information security training: this is also a major component in the security policy. The
training could occur in various ways (Bennett, Segerberg & Walker, 2014). One kind of the
training which would be required by the organization would be the awareness training. The
policy document on what sort of the awareness program that has been in place and how it is
communicated on the regular basis.
Security standards and controls
There are numerous security standards as well as the controls which are observed by Amazon
organization. One of the security standard which they have implemented is the ISO 17799. This
standard highlights that the information is an asset that may exists in the various form and it has
a fundamental value to the company (Franzoni & Sauermann, 2014). The purpose of the IT
security is to protect the assets of the organization so that to ensure there is continuity of the
business and to enable the organization to maximize on the return. According to this standard it
has been characterized to provide confidentiality that could ensure that the data is only accessible
Passwords: on this section it highlights on the requirements which are imposed to the users for
the passwords. The length, the character set as well as the password could be entered prior to
being disabled.
Anti-virus: this section identifies on the frequency for the updating on the files definition along
with how removable media, email attachment as well as the other files are scanned.
Backup and recovery: in a security policy it should have a comprehensive backup as well as a
recovery plan that is included (Franzoni & Sauermann, 2014). The section can be separated from
the initial policy as a whole and then included to the comprehensive business continuity template
plan for the Amazon organization.
Information security training: this is also a major component in the security policy. The
training could occur in various ways (Bennett, Segerberg & Walker, 2014). One kind of the
training which would be required by the organization would be the awareness training. The
policy document on what sort of the awareness program that has been in place and how it is
communicated on the regular basis.
Security standards and controls
There are numerous security standards as well as the controls which are observed by Amazon
organization. One of the security standard which they have implemented is the ISO 17799. This
standard highlights that the information is an asset that may exists in the various form and it has
a fundamental value to the company (Franzoni & Sauermann, 2014). The purpose of the IT
security is to protect the assets of the organization so that to ensure there is continuity of the
business and to enable the organization to maximize on the return. According to this standard it
has been characterized to provide confidentiality that could ensure that the data is only accessible

ENFORCING INFORMATION TECHNOLOGY 6
to the individuals who it intended to have an access to. The ISO 17799 has provided Amazon a
benchmark to which are able to build on their information security policy. Other security
standard that are observed by the organization is the ISO 27001 which is the security
management on the specification. It is more of a framework that focuses on the procedures along
with the policies (Peppard & Ward, 2016). The standard has offered the company the security
measures in regards to the third parties, as well as the customers. Moreover, the standards enable
the organization is able to reduce on their cost by optimizing their structure (Rahimli, 2013). On
the controls there are various that have been implemented by Amazon organization such as
authentication. This is achieved through a multi factor authentication before anybody could gain
access to the system. This would help be able to keep the information of the company to be safe
from any vulnerabilities from any access.
The risk analysis and the contingency planning for the company
When it comes to the risk analysis the first thing would be to identify a given risk. This could be
achieved by understanding different hazards and the risk. The second aspect is to clearly identify
what may have caused on the occurrence of the risk (Rahimli, 2013). Amazon once they identify
on the risk which are affecting their processes they are then evaluate and an appropriate control
measure is implemented.
On the contingency planning there are control which are place which enable the organization to
maintain cohesion and be able to work towards enhancing its success (Rosemann & vom, 2015).
The organization observes the document protocol which ensures there has been accountability
for the compression, encryption as well as the verification of the information (Bennett, Segerberg
& Walker, 2014). The contingency plan could be employed when there is a worst case scenario
on the risks. The contingency plan contains different component which included the readiness of
to the individuals who it intended to have an access to. The ISO 17799 has provided Amazon a
benchmark to which are able to build on their information security policy. Other security
standard that are observed by the organization is the ISO 27001 which is the security
management on the specification. It is more of a framework that focuses on the procedures along
with the policies (Peppard & Ward, 2016). The standard has offered the company the security
measures in regards to the third parties, as well as the customers. Moreover, the standards enable
the organization is able to reduce on their cost by optimizing their structure (Rahimli, 2013). On
the controls there are various that have been implemented by Amazon organization such as
authentication. This is achieved through a multi factor authentication before anybody could gain
access to the system. This would help be able to keep the information of the company to be safe
from any vulnerabilities from any access.
The risk analysis and the contingency planning for the company
When it comes to the risk analysis the first thing would be to identify a given risk. This could be
achieved by understanding different hazards and the risk. The second aspect is to clearly identify
what may have caused on the occurrence of the risk (Rahimli, 2013). Amazon once they identify
on the risk which are affecting their processes they are then evaluate and an appropriate control
measure is implemented.
On the contingency planning there are control which are place which enable the organization to
maintain cohesion and be able to work towards enhancing its success (Rosemann & vom, 2015).
The organization observes the document protocol which ensures there has been accountability
for the compression, encryption as well as the verification of the information (Bennett, Segerberg
& Walker, 2014). The contingency plan could be employed when there is a worst case scenario
on the risks. The contingency plan contains different component which included the readiness of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

ENFORCING INFORMATION TECHNOLOGY 7
the plan of the vendor and every organization relies on this group to get the supplies and other
services.
Analysis of threat, vulnerabilities and tools
There are various threats which Amazon has encountered. One of the threat is the social
engineering. This usually occurs when the hackers is able to obtain information from individual
accounts or perhaps use this type for the functions of the malicious activities (Schwartz, 2014).
The social engineering used by the hackers is regarded as phishing, where there hackers uses
email to attempt to trick people on providing their sensitive information for example their social
security numbers and the credit card along with the passwords.
In regards to the tools which are utilized by the hackers they use keylogger tool that they use in
obtaining in the information of the customer. The attacker installs a background application to
the device of the users and this individual is able to monitor on what the user writes using the
keyboard and captures this on the screen (Schwartz, 2014). In Amazon organization in most of
the cases they use integrated sales and purchasing system to input on the information in the
system this may pose a risk when the hackers are able to gain access.
There are various to which Amazon have encountered. Some of the vulnerabilities are; out of the
date patches. There have been instances to which their computing systems have a quest for the
out of date patches. This could causes an easy entry for the cyber criminals (Rosemann & vom,
2015). Another vulnerability is the SQL injection which is very critical to the operation of the
organization and an easy to the exploit. Additionally there could be vulnerability of the risky
reuse of the password across the various multiple platform which is a risky business when it
comes to the business computing.
the plan of the vendor and every organization relies on this group to get the supplies and other
services.
Analysis of threat, vulnerabilities and tools
There are various threats which Amazon has encountered. One of the threat is the social
engineering. This usually occurs when the hackers is able to obtain information from individual
accounts or perhaps use this type for the functions of the malicious activities (Schwartz, 2014).
The social engineering used by the hackers is regarded as phishing, where there hackers uses
email to attempt to trick people on providing their sensitive information for example their social
security numbers and the credit card along with the passwords.
In regards to the tools which are utilized by the hackers they use keylogger tool that they use in
obtaining in the information of the customer. The attacker installs a background application to
the device of the users and this individual is able to monitor on what the user writes using the
keyboard and captures this on the screen (Schwartz, 2014). In Amazon organization in most of
the cases they use integrated sales and purchasing system to input on the information in the
system this may pose a risk when the hackers are able to gain access.
There are various to which Amazon have encountered. Some of the vulnerabilities are; out of the
date patches. There have been instances to which their computing systems have a quest for the
out of date patches. This could causes an easy entry for the cyber criminals (Rosemann & vom,
2015). Another vulnerability is the SQL injection which is very critical to the operation of the
organization and an easy to the exploit. Additionally there could be vulnerability of the risky
reuse of the password across the various multiple platform which is a risky business when it
comes to the business computing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

ENFORCING INFORMATION TECHNOLOGY 8
References
Aghion, P., Bloom, N., & Van Reenen, J. (2013). Incomplete contracts and the internal
organization of firms. The Journal of Law, Economics, & Organization, 30(suppl_1), i37-
i63.
Bennett, W. L., Segerberg, A., & Walker, S. (2014). Organization in the crowd: peer production
in large-scale networked protests. Information, Communication & Society, 17(2), 232-
260.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing and
internet of things: a survey. Future Generation Computer Systems, 56, 684-700.
Cummings, T. G., & Worley, C. G. (2014). Organization development and change. Cengage
learning.
Dowling, C. (2014). A Big 4 firm's use of information technology to control the audit process:
How an audit support system is changing auditor behavior. Contemporary Accounting
Research, 31(1), 230-252.
Franzoni, C., & Sauermann, H. (2014). Crowd science: The organization of scientific research in
open collaborative projects. Research Policy, 43(1), 1-20.
Holtshouse, D. K. (2013). Information technology for knowledge management. Springer Science
& Business Media.
Peppard, J., & Ward, J. (2016). The strategic management of information systems: Building a
digital strategy. John Wiley & Sons.
Rahimli, A. (2013). Factors influencing organization adoption decision on cloud computing.
International Journal of Cloud Computing and Services Science, 2(2), 141.
Rosemann, M., & vom Brocke, J. (2015). The six core elements of business process
management. In Handbook on business process management 1 (pp. 105-122). Springer
Berlin Heidelberg.
Schwartz, B. (2014). Queuing and waiting: Studies in the social organization of access and delay.
References
Aghion, P., Bloom, N., & Van Reenen, J. (2013). Incomplete contracts and the internal
organization of firms. The Journal of Law, Economics, & Organization, 30(suppl_1), i37-
i63.
Bennett, W. L., Segerberg, A., & Walker, S. (2014). Organization in the crowd: peer production
in large-scale networked protests. Information, Communication & Society, 17(2), 232-
260.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing and
internet of things: a survey. Future Generation Computer Systems, 56, 684-700.
Cummings, T. G., & Worley, C. G. (2014). Organization development and change. Cengage
learning.
Dowling, C. (2014). A Big 4 firm's use of information technology to control the audit process:
How an audit support system is changing auditor behavior. Contemporary Accounting
Research, 31(1), 230-252.
Franzoni, C., & Sauermann, H. (2014). Crowd science: The organization of scientific research in
open collaborative projects. Research Policy, 43(1), 1-20.
Holtshouse, D. K. (2013). Information technology for knowledge management. Springer Science
& Business Media.
Peppard, J., & Ward, J. (2016). The strategic management of information systems: Building a
digital strategy. John Wiley & Sons.
Rahimli, A. (2013). Factors influencing organization adoption decision on cloud computing.
International Journal of Cloud Computing and Services Science, 2(2), 141.
Rosemann, M., & vom Brocke, J. (2015). The six core elements of business process
management. In Handbook on business process management 1 (pp. 105-122). Springer
Berlin Heidelberg.
Schwartz, B. (2014). Queuing and waiting: Studies in the social organization of access and delay.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




