Cybersecurity Project: MHR System Analysis and Algorithms
VerifiedAdded on 2022/08/17
|11
|1481
|18
Project
AI Summary
This assignment focuses on the cybersecurity aspects of the Australian My Healthy Record (MHR) system. It begins by identifying two key processes: logging into the system and accessing patient health information. The assignment details the steps involved in each process and analyzes potential malicious actions, such as brute-force attacks, eavesdropping, denial-of-service attacks, and SQL injections, using activity diagrams to illustrate these threats. It then explores error detection algorithms used in data transmission to maintain data integrity. Furthermore, the assignment emphasizes the importance of ACID properties (Atomicity, Consistency, Isolation, Durability) for secure transactions and recommends Role-Based Access Control (RBAC) to enhance data security and user access management within the MHR system. The document concludes with recommendations and highlights the importance of patching system vulnerabilities to prevent unauthorized access and maintain data integrity.

Running head: CYBER SECURITY
Cyber security
Name of the Student:
Name of the University:
Author note:
Cyber security
Name of the Student:
Name of the University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY
Introduction:
The primary goal of the assignment is identification of the algorithmic requirements for
enhancing cybersecurity and other error detection algorithms and correction algorithms for
enhancing the security of the organization [1].
Part A:
Activity 1:
The two processes identified for the MHR scenario are given below:
1. Logging in to the system
2. Accessing the patients’ information for health
Description of the process:
1. Logging in to the system:
This process is developed for authentication of the users in the system. For proper
log in to the system, a user has to provide a proof of its validation by presenting a valid
username and a corresponding password. This plays an important role in the system as it
prevents unauthorized access to the system and its data. Certain actions has to be taken in
order to successfully ‘log in’ to the system and they are:
a. Enter the credentials for logging in
b. Authentication of the log in credentials
The possible malicious actions which can be affect the above actions are given
below:
a. Eavesdropping attack
Introduction:
The primary goal of the assignment is identification of the algorithmic requirements for
enhancing cybersecurity and other error detection algorithms and correction algorithms for
enhancing the security of the organization [1].
Part A:
Activity 1:
The two processes identified for the MHR scenario are given below:
1. Logging in to the system
2. Accessing the patients’ information for health
Description of the process:
1. Logging in to the system:
This process is developed for authentication of the users in the system. For proper
log in to the system, a user has to provide a proof of its validation by presenting a valid
username and a corresponding password. This plays an important role in the system as it
prevents unauthorized access to the system and its data. Certain actions has to be taken in
order to successfully ‘log in’ to the system and they are:
a. Enter the credentials for logging in
b. Authentication of the log in credentials
The possible malicious actions which can be affect the above actions are given
below:
a. Eavesdropping attack
2CYBER SECURITY
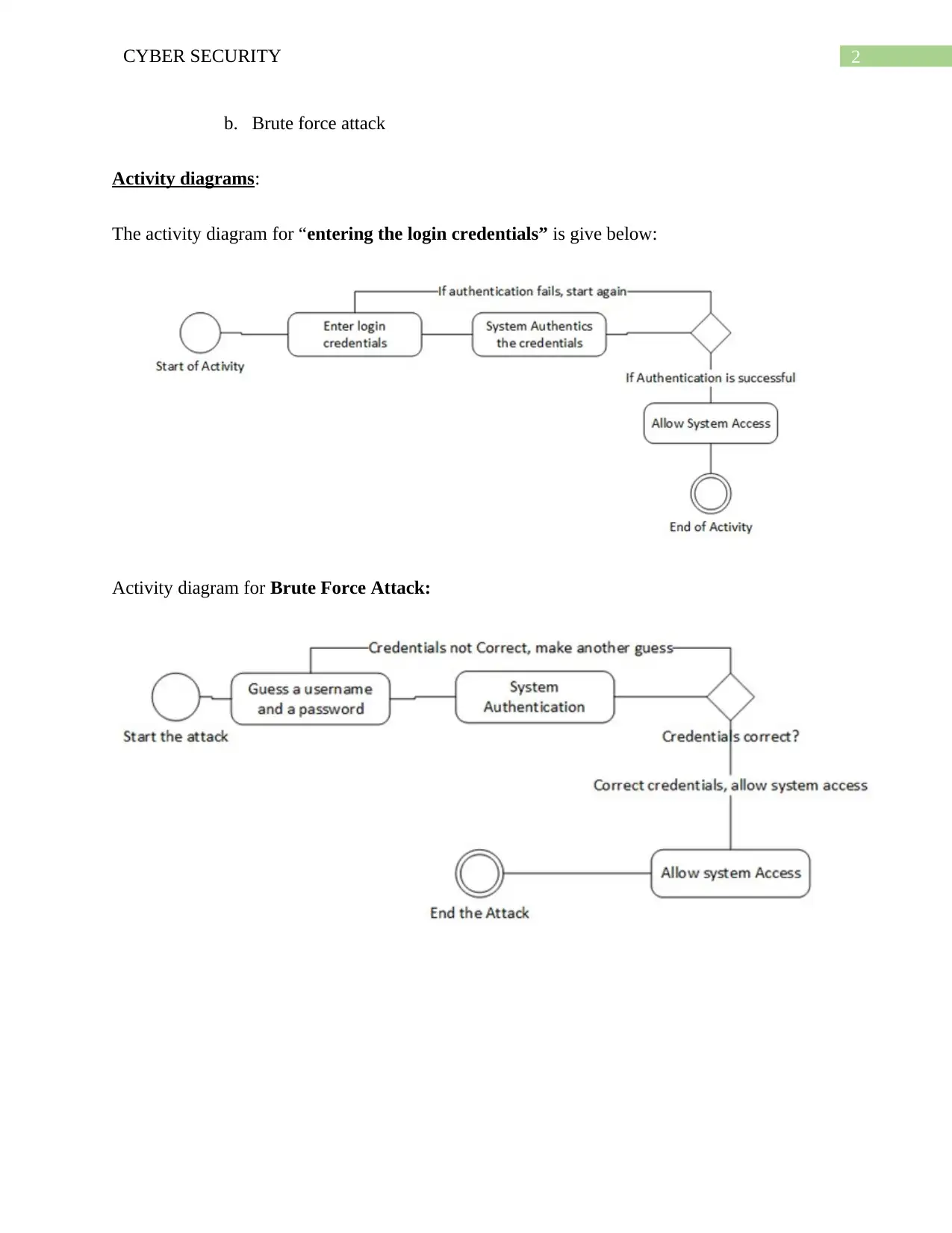
b. Brute force attack
Activity diagrams:
The activity diagram for “entering the login credentials” is give below:
Activity diagram for Brute Force Attack:
b. Brute force attack
Activity diagrams:
The activity diagram for “entering the login credentials” is give below:
Activity diagram for Brute Force Attack:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY
The activity diagram for “Authentication of the Log in credential”: is given below:
The activity diagram for the “eaves dropping attack” is given in the section below:
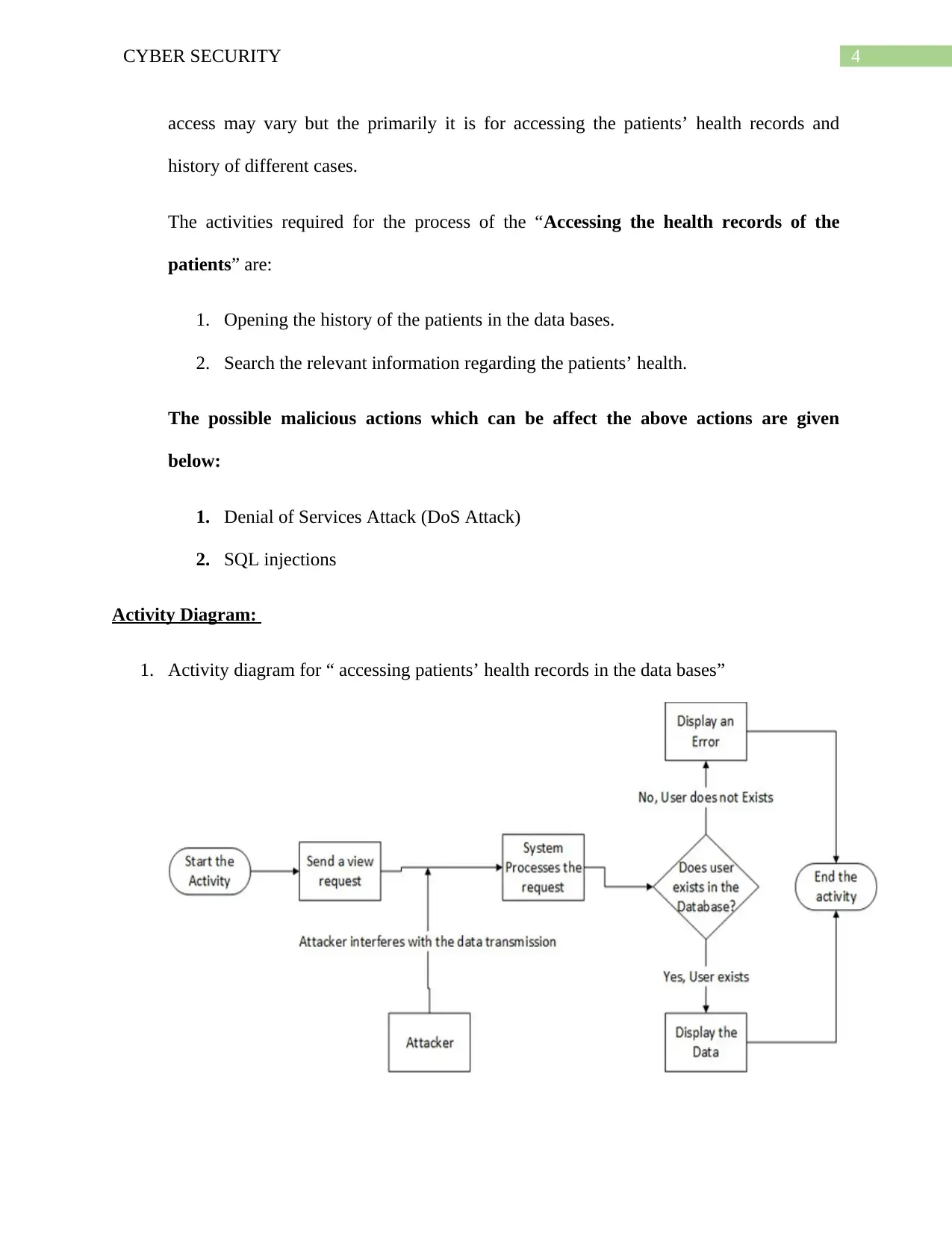
2. Accessing the patients’ information for health:
The goal of this process is to permit the valid and authenticate users of MHR
system for accessing the data stowed in the database of the system. The purpose of the
The activity diagram for “Authentication of the Log in credential”: is given below:
The activity diagram for the “eaves dropping attack” is given in the section below:
2. Accessing the patients’ information for health:
The goal of this process is to permit the valid and authenticate users of MHR
system for accessing the data stowed in the database of the system. The purpose of the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CYBER SECURITY
access may vary but the primarily it is for accessing the patients’ health records and
history of different cases.
The activities required for the process of the “Accessing the health records of the
patients” are:
1. Opening the history of the patients in the data bases.
2. Search the relevant information regarding the patients’ health.
The possible malicious actions which can be affect the above actions are given
below:
1. Denial of Services Attack (DoS Attack)
2. SQL injections
Activity Diagram:
1. Activity diagram for “ accessing patients’ health records in the data bases”
access may vary but the primarily it is for accessing the patients’ health records and
history of different cases.
The activities required for the process of the “Accessing the health records of the
patients” are:
1. Opening the history of the patients in the data bases.
2. Search the relevant information regarding the patients’ health.
The possible malicious actions which can be affect the above actions are given
below:
1. Denial of Services Attack (DoS Attack)
2. SQL injections
Activity Diagram:
1. Activity diagram for “ accessing patients’ health records in the data bases”

5CYBER SECURITY
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6CYBER SECURITY
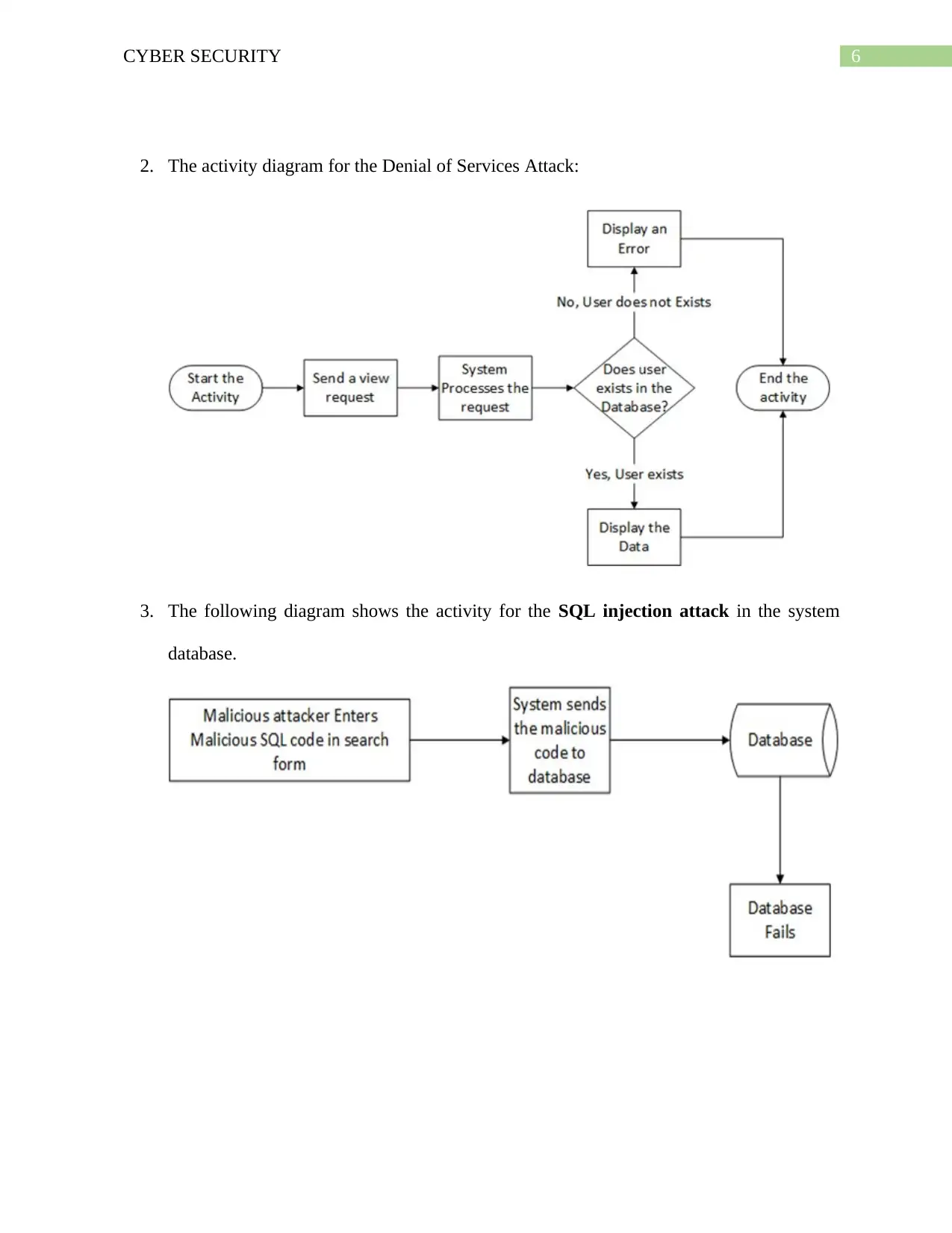
2. The activity diagram for the Denial of Services Attack:
3. The following diagram shows the activity for the SQL injection attack in the system
database.
2. The activity diagram for the Denial of Services Attack:
3. The following diagram shows the activity for the SQL injection attack in the system
database.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY
Lesson learnt form the activities:
From all the actions and their respective activity diagrams it can be said that all the
activities in the system is exposed to severe attacks. The main objectives of these attacks are
either to access the data of an individual or simply hinder the day to day activities of a system.
This has also taught us that the attacks can be generated through any “hole” or vulnerabilities
present in the system. The attackers can even launch attacks from the regular features of a
system. Thus for preventing the attacks from affecting the system and the performance of the
system all the loopholes of the system has to be mended at a short notice [2].
Activity 2:
Description:
The system of MHR involves the process of the data transmission in the system between
the server that is hosting the data and the devices used by the users. Often there are certain
hindrances that may occur in the transmission process which includes noises in the signal. This
results in errors in the signal which may alter the subject matter of the data. Hence, to prevent it
from occurring and hampering the system certain error detection algorithms are used. The aim
of this algorithm is to detect the errors in the system which alters the value of the data under
transit. Once the error is detected by the algorithm, it is verified with the original message and
fixed within a fraction of time.
The process of error detection follows certain particular steps which includes, encoding
of data, transmission of the data with a particular “code-word”, received at the destination. The
receiver on the other end checks for the code word after decoding the message. The error can be
checked with the help of the code word in the message as it is known by both the recipient and
Lesson learnt form the activities:
From all the actions and their respective activity diagrams it can be said that all the
activities in the system is exposed to severe attacks. The main objectives of these attacks are
either to access the data of an individual or simply hinder the day to day activities of a system.
This has also taught us that the attacks can be generated through any “hole” or vulnerabilities
present in the system. The attackers can even launch attacks from the regular features of a
system. Thus for preventing the attacks from affecting the system and the performance of the
system all the loopholes of the system has to be mended at a short notice [2].
Activity 2:
Description:
The system of MHR involves the process of the data transmission in the system between
the server that is hosting the data and the devices used by the users. Often there are certain
hindrances that may occur in the transmission process which includes noises in the signal. This
results in errors in the signal which may alter the subject matter of the data. Hence, to prevent it
from occurring and hampering the system certain error detection algorithms are used. The aim
of this algorithm is to detect the errors in the system which alters the value of the data under
transit. Once the error is detected by the algorithm, it is verified with the original message and
fixed within a fraction of time.
The process of error detection follows certain particular steps which includes, encoding
of data, transmission of the data with a particular “code-word”, received at the destination. The
receiver on the other end checks for the code word after decoding the message. The error can be
checked with the help of the code word in the message as it is known by both the recipient and

8CYBER SECURITY
the sender of the message. It can be verified with the help of the parity check. If the code word of
the received in the message matches the code word in the sent message the task is verified.
Reflection:
With the increasing trends in the technology there are numerous interferences over the air
that affect the process of data transmission. Thus to prevent this from occurring, various
protocols are implemented like the error detection algorithm and correction algorithms along
with the data transmission protocols. The data can be modified and distorted without these
protocols in action. Not only that, the integrity and the privacy of the data can be at stake if not
protected and corrected [3].
Activity 3:
As per the principles of MHR, they are instructed to provide access to the Health and
Medical Information of the Australian. For the sensitive information like the medical
information, the security of the data along with its integrity has to be maintained and the
customers has to be ensured that their data are safe and protected in the data base of the
healthcare unit. Thus to ensure successful transaction in the databases, certain ACID properties
has to be taken under consideration.
The importance of the transaction musty be consistence throughout the process of
transaction. Each and every part of the transaction is essential and has to be dealt with utmost
importance no matter what. The rule of “all or nothing” must be followed while the patients’
databases are taken into consideration.
One of the most important aspect of the ACID property is consistency. No matter what
format is followed the consistency of the data must be maintained.
the sender of the message. It can be verified with the help of the parity check. If the code word of
the received in the message matches the code word in the sent message the task is verified.
Reflection:
With the increasing trends in the technology there are numerous interferences over the air
that affect the process of data transmission. Thus to prevent this from occurring, various
protocols are implemented like the error detection algorithm and correction algorithms along
with the data transmission protocols. The data can be modified and distorted without these
protocols in action. Not only that, the integrity and the privacy of the data can be at stake if not
protected and corrected [3].
Activity 3:
As per the principles of MHR, they are instructed to provide access to the Health and
Medical Information of the Australian. For the sensitive information like the medical
information, the security of the data along with its integrity has to be maintained and the
customers has to be ensured that their data are safe and protected in the data base of the
healthcare unit. Thus to ensure successful transaction in the databases, certain ACID properties
has to be taken under consideration.
The importance of the transaction musty be consistence throughout the process of
transaction. Each and every part of the transaction is essential and has to be dealt with utmost
importance no matter what. The rule of “all or nothing” must be followed while the patients’
databases are taken into consideration.
One of the most important aspect of the ACID property is consistency. No matter what
format is followed the consistency of the data must be maintained.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY
Another most important property of the MHR is durability. The information stored and
updated in the system must be everlasting and should be accessible from other devices for the
purpose of emergency if the system crashes.
Application of RBAC:
As per the description of the system, it can be said that it is used by certain groups of
users. Each of them has a specific requirement of the data. Thus for ensuring the security of the
data, role based access control must be implemented in the system. In order to do so, the users
has to be categorized into groups such that they can only access the data they are meant to deal
with. In this way the sensitivity of data is protected along with the privacy [4]. The groups
include, admin, pharmacists, nurse, doctors, medical specialist and few others in the medical
services. The abuse of the system due to the unauthorized users can be prevented with the
appropriate usage of the role based access control within the system.
Recommendations:
The highest recommendation for the system is the Role Based Access Control or RBAC
in MHR. This helps in maintaining the privacy, security and integrity of the MHR data with
enhancing relevant access to the system’s data.
Conclusion:
Thus from the above observations it can be concluded that any system or database is
prone to attacks. Not only that, the attacks can be initiated from any part of the system.
Therefore, patching the holes in the system such that the attackers do not get access to the
database and integrity is maintained.
Another most important property of the MHR is durability. The information stored and
updated in the system must be everlasting and should be accessible from other devices for the
purpose of emergency if the system crashes.
Application of RBAC:
As per the description of the system, it can be said that it is used by certain groups of
users. Each of them has a specific requirement of the data. Thus for ensuring the security of the
data, role based access control must be implemented in the system. In order to do so, the users
has to be categorized into groups such that they can only access the data they are meant to deal
with. In this way the sensitivity of data is protected along with the privacy [4]. The groups
include, admin, pharmacists, nurse, doctors, medical specialist and few others in the medical
services. The abuse of the system due to the unauthorized users can be prevented with the
appropriate usage of the role based access control within the system.
Recommendations:
The highest recommendation for the system is the Role Based Access Control or RBAC
in MHR. This helps in maintaining the privacy, security and integrity of the MHR data with
enhancing relevant access to the system’s data.
Conclusion:
Thus from the above observations it can be concluded that any system or database is
prone to attacks. Not only that, the attacks can be initiated from any part of the system.
Therefore, patching the holes in the system such that the attackers do not get access to the
database and integrity is maintained.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY
References:
[1] W. C. Huffman, & V., Pless, Fundamentals of Error-Correcting Codes, Cambridge
University Press, New York, 2010.
[2] T. K., Moon, Error Correction Coding: Mathematical Methods and Algorithms, Wiley,
2005.
[3] D. R. Sharma, & D. S., Kaushik, DATABASE MANAGEMENT SYSTEM, Horizon Books
( A Division of Ignited Minds Edutech P Ltd), 2015.
[4] Z., Yong, Cloud Security: Concepts, Methodologies, Tools, and Applications: Concepts,
Methodologies, Tools, and Applications, IGI Global, 2019.
References:
[1] W. C. Huffman, & V., Pless, Fundamentals of Error-Correcting Codes, Cambridge
University Press, New York, 2010.
[2] T. K., Moon, Error Correction Coding: Mathematical Methods and Algorithms, Wiley,
2005.
[3] D. R. Sharma, & D. S., Kaushik, DATABASE MANAGEMENT SYSTEM, Horizon Books
( A Division of Ignited Minds Edutech P Ltd), 2015.
[4] Z., Yong, Cloud Security: Concepts, Methodologies, Tools, and Applications: Concepts,
Methodologies, Tools, and Applications, IGI Global, 2019.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




