Ethical Concerns Related to Mobile Threats
Added on 2022-12-15
8 Pages1540 Words339 Views
End of preview
Want to access all the pages? Upload your documents or become a member.
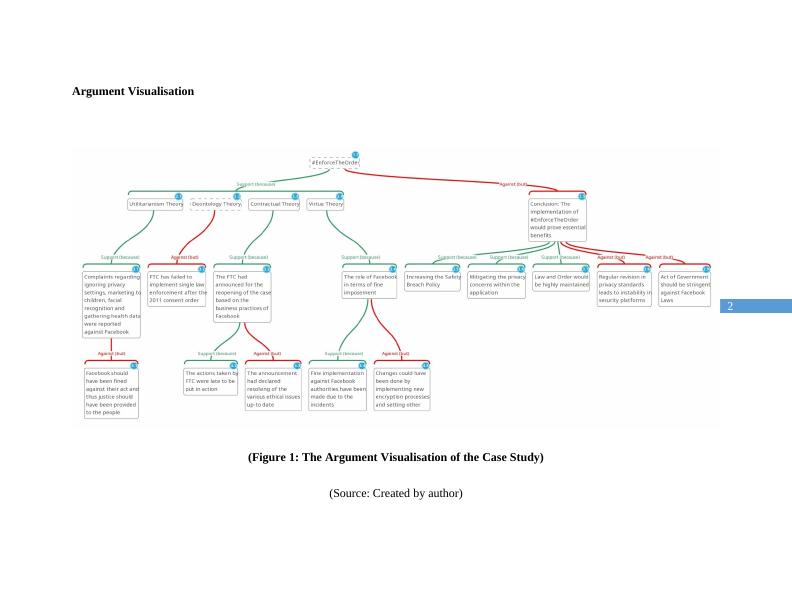
1.1. #EnforceTheOrder. Support (because). Against (but)
|1
|270
|77
Information Technology Ethics
|7
|1807
|60
Enforce the Order: A Case Study on Ethical Theories
|7
|1468
|491
5 Active Mobile Threats Spoofing Enterprise Apps
|6
|2194
|130
ICT Ethical Issue
|9
|1513
|392
Information Technology Ethics: Blame on Social Media for Christchurch Video
|7
|2280
|38