Ethical Hacking and Defence: System Infiltration Report - ECU 2024
VerifiedAdded on 2023/06/04
|17
|1747
|274
Report
AI Summary
This report details an ethical hacking and defence project focused on infiltrating a system and attaining root-level privileges. It outlines the defined methodology, log testing procedures, and the discovery of five flags representing key points of system compromise. The report covers various tools and techniques, including Apache web server analysis, web shell exploitation, password cracking using Hashcat, network scanning with Nmap, and Linux privilege escalation. The findings include identifying open TCP ports and vulnerabilities, demonstrating methods for securing networks and systems against malicious access. Desklib provides this and many other solved assignments for students.

ETHICAL HACKING AND
DEFENCE
DEFENCE
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
Ethical hacking is a serious step that has to be taken for defence of a system and the network.
The following report’s target is to present a report which gives a through description on this
and has successfully completed the report. The report ensures to describe the log testing,
defined methodologies and the five flags with the respective results.
1
Ethical hacking is a serious step that has to be taken for defence of a system and the network.
The following report’s target is to present a report which gives a through description on this
and has successfully completed the report. The report ensures to describe the log testing,
defined methodologies and the five flags with the respective results.
1

Table of Contents
1 Target of the Project.........................................................................................................3
2 Defined Methodology and Log Testing...........................................................................3
Flag 1.....................................................................................................................................5
Flag 2.....................................................................................................................................7
Flag 3.....................................................................................................................................8
Flag 4...................................................................................................................................13
Flag 5...................................................................................................................................15
3 Result................................................................................................................................16
References...............................................................................................................................17
2
1 Target of the Project.........................................................................................................3
2 Defined Methodology and Log Testing...........................................................................3
Flag 1.....................................................................................................................................5
Flag 2.....................................................................................................................................7
Flag 3.....................................................................................................................................8
Flag 4...................................................................................................................................13
Flag 5...................................................................................................................................15
3 Result................................................................................................................................16
References...............................................................................................................................17
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 Target of the Project
Today, it is very much crucial for the users and the organizations to secure their
network, website, devices and system from the hackers. This report brings out the secure
methods to be opted for security the system from the malicious accessing of the hackers. The
report will ensure to describe the log testing, defined methodologies and the five flags with
the respective results.
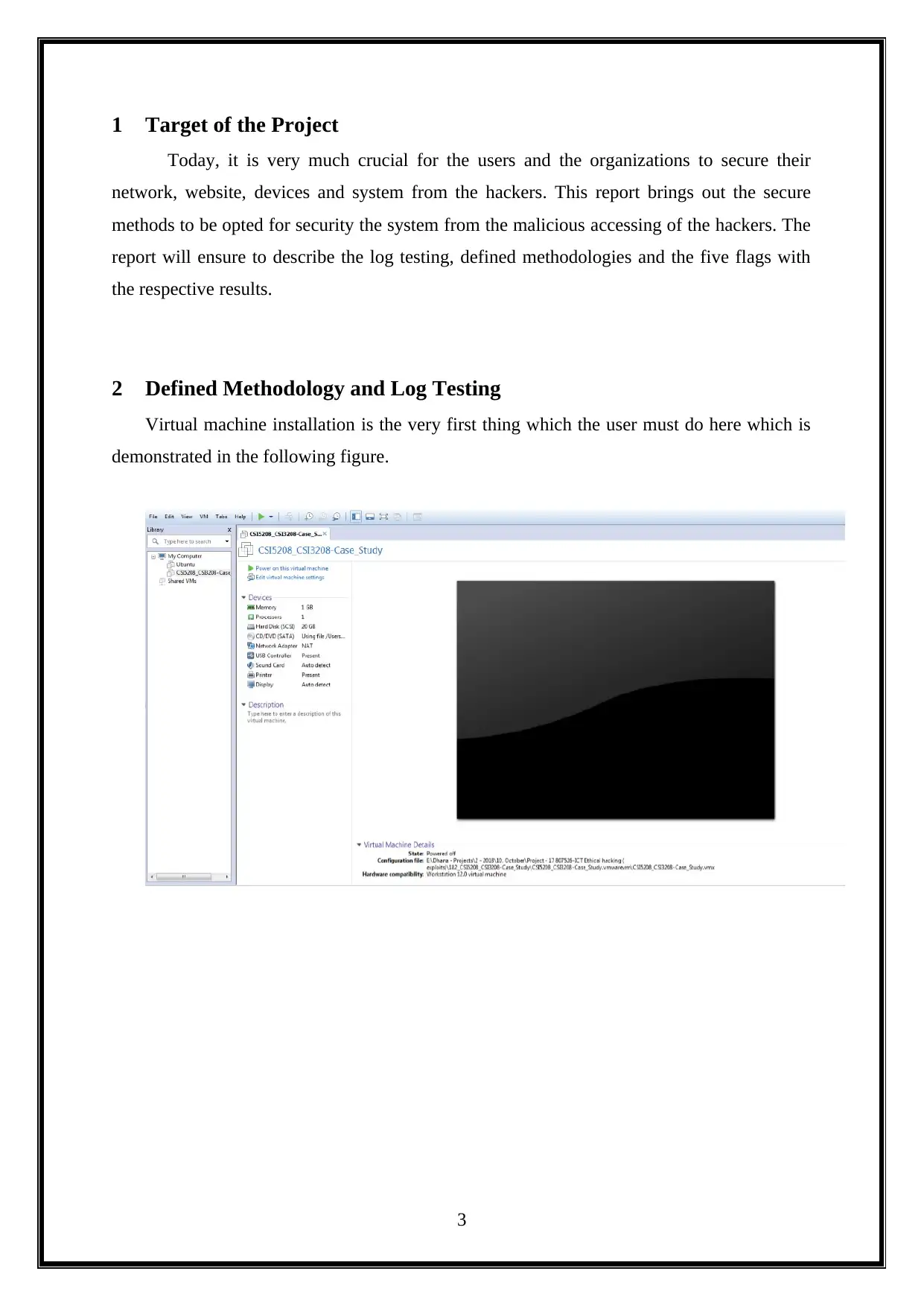
2 Defined Methodology and Log Testing
Virtual machine installation is the very first thing which the user must do here which is
demonstrated in the following figure.
3
Today, it is very much crucial for the users and the organizations to secure their
network, website, devices and system from the hackers. This report brings out the secure
methods to be opted for security the system from the malicious accessing of the hackers. The
report will ensure to describe the log testing, defined methodologies and the five flags with
the respective results.
2 Defined Methodology and Log Testing
Virtual machine installation is the very first thing which the user must do here which is
demonstrated in the following figure.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4

Flag 1
In general, web server could be defined as the server that contains the responsibility of
accepting the HTTP requests which comes from the web clients for serving the HTTP
responses. This basically has taken in a form of web pages which has static content along
with the dynamic content. The static content’s example can be as follows, pictures/images,
text and so on. Whereas, the dynamic content’s example can be the script (Ali, 2014).
This flag explains the usage of Apache Web server and its advantages. The first
important announcement to be made about apache is that it is a free open source. It is known
as a cross-platform that is robust as well as it is used by the small firms and also the big
organizations. Hence, the apache is wide spread the number of users have increased
significantly. Moreover, 50 percentage of the web servers utilize apache (Buchanan, 2014).
The next section will represent the web server content.
Apache httpd 2.4 default layout (apache.org source package):
Apache httpd 2.2 default layout (apache.org source package):
5
In general, web server could be defined as the server that contains the responsibility of
accepting the HTTP requests which comes from the web clients for serving the HTTP
responses. This basically has taken in a form of web pages which has static content along
with the dynamic content. The static content’s example can be as follows, pictures/images,
text and so on. Whereas, the dynamic content’s example can be the script (Ali, 2014).
This flag explains the usage of Apache Web server and its advantages. The first
important announcement to be made about apache is that it is a free open source. It is known
as a cross-platform that is robust as well as it is used by the small firms and also the big
organizations. Hence, the apache is wide spread the number of users have increased
significantly. Moreover, 50 percentage of the web servers utilize apache (Buchanan, 2014).
The next section will represent the web server content.
Apache httpd 2.4 default layout (apache.org source package):
Apache httpd 2.2 default layout (apache.org source package):
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Apache httpd 2.0 default layout (apache.org source package):
Flag 2
Only on the web, the web shells can run and it contains no socket communication,
exactly like the reverse shells. The program called netcat is the web server has to be
connected with each other in a reverse shell that is present on hacker’s system. This is why
the web shells have instant set up and usage. Along with positive aspects it also contains
certain negative aspects, which is it lacks interactive terminal style. For dealing with
vulnerabilities, the web shells are utilized, as it carries out the process like arbitrary file
6
Flag 2
Only on the web, the web shells can run and it contains no socket communication,
exactly like the reverse shells. The program called netcat is the web server has to be
connected with each other in a reverse shell that is present on hacker’s system. This is why
the web shells have instant set up and usage. Along with positive aspects it also contains
certain negative aspects, which is it lacks interactive terminal style. For dealing with
vulnerabilities, the web shells are utilized, as it carries out the process like arbitrary file
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
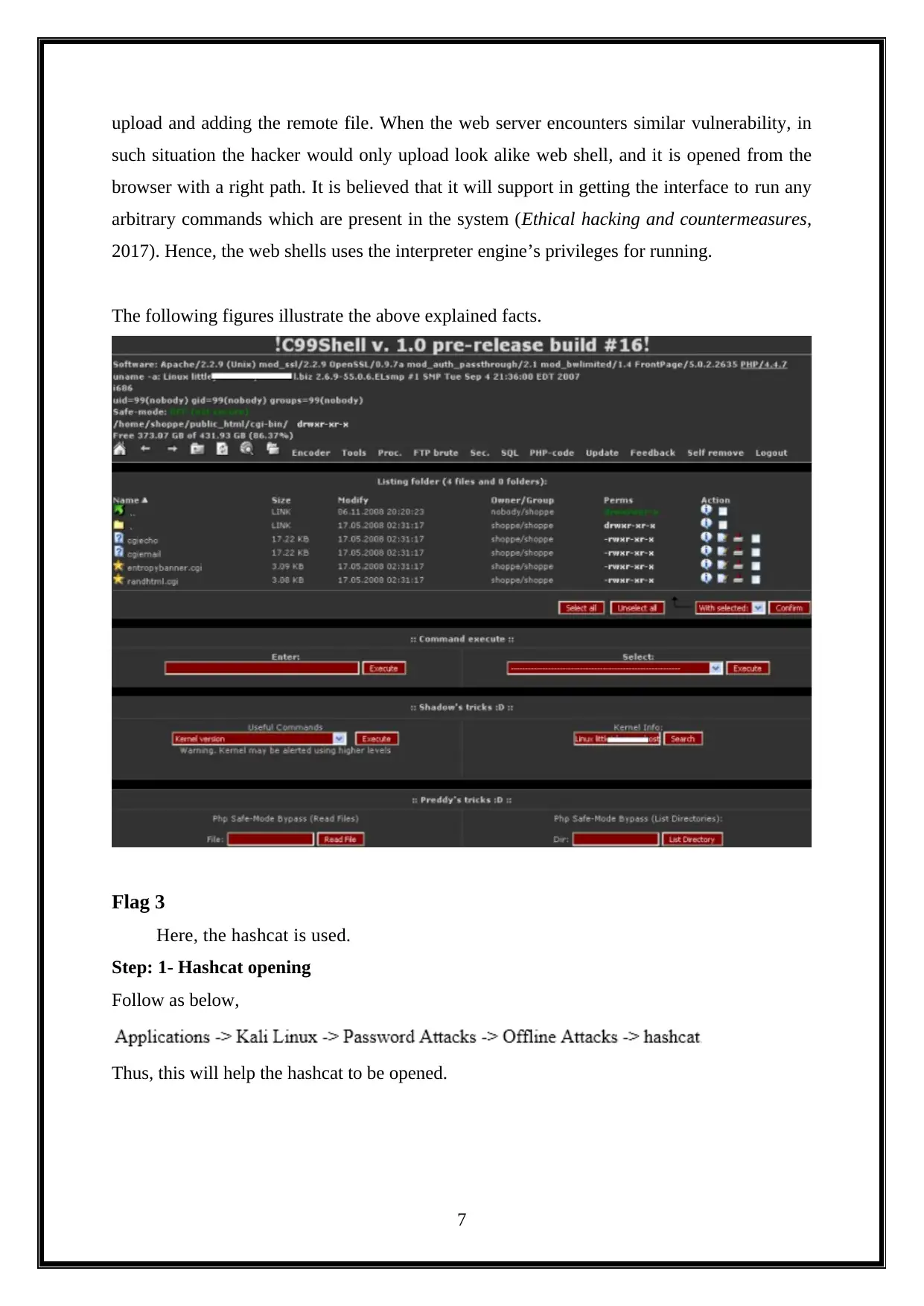
upload and adding the remote file. When the web server encounters similar vulnerability, in
such situation the hacker would only upload look alike web shell, and it is opened from the
browser with a right path. It is believed that it will support in getting the interface to run any
arbitrary commands which are present in the system (Ethical hacking and countermeasures,
2017). Hence, the web shells uses the interpreter engine’s privileges for running.
The following figures illustrate the above explained facts.
Flag 3
Here, the hashcat is used.
Step: 1- Hashcat opening
Follow as below,
Thus, this will help the hashcat to be opened.
7
such situation the hacker would only upload look alike web shell, and it is opened from the
browser with a right path. It is believed that it will support in getting the interface to run any
arbitrary commands which are present in the system (Ethical hacking and countermeasures,
2017). Hence, the web shells uses the interpreter engine’s privileges for running.
The following figures illustrate the above explained facts.
Flag 3
Here, the hashcat is used.
Step: 1- Hashcat opening
Follow as below,
Thus, this will help the hashcat to be opened.
7
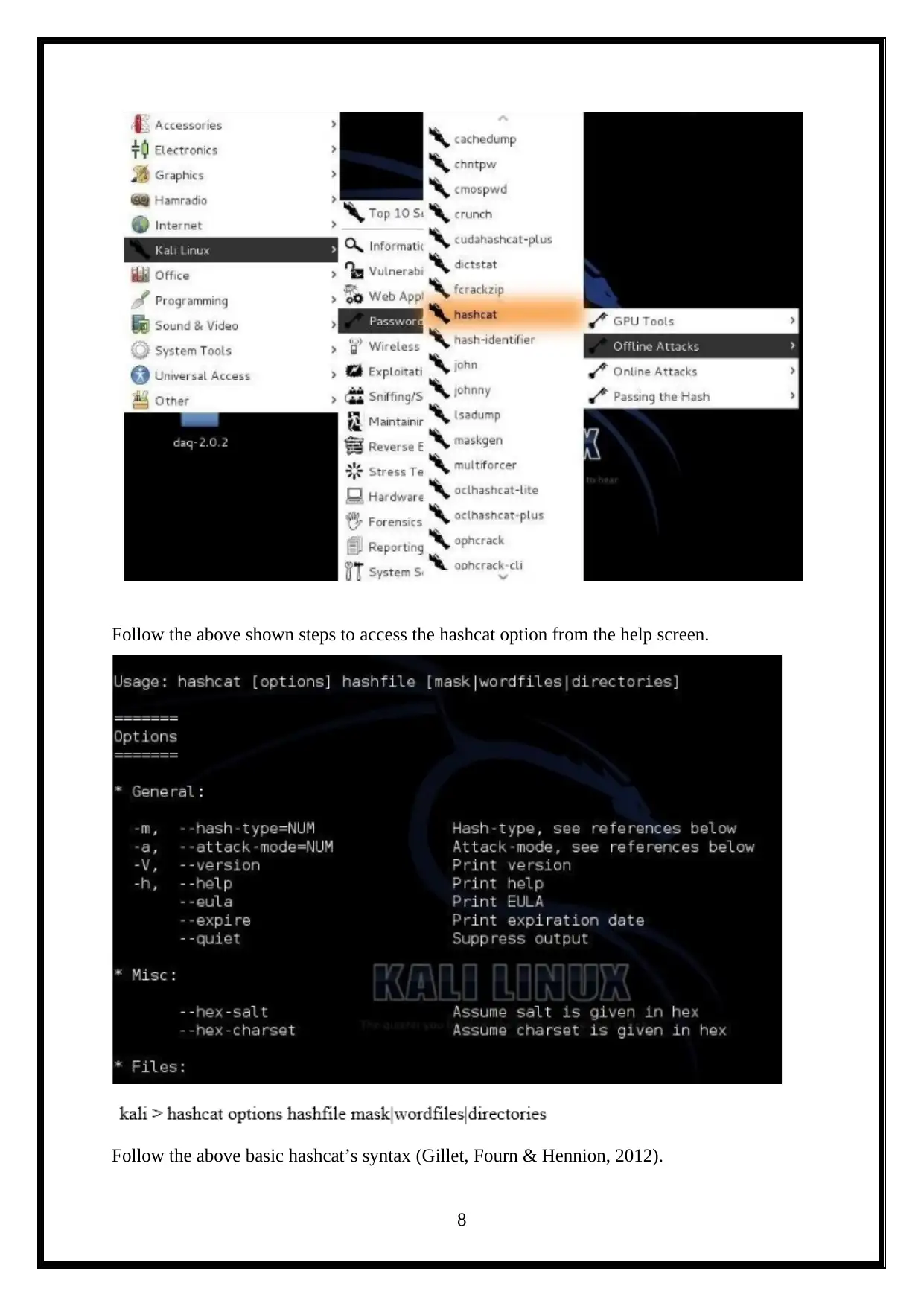
Follow the above shown steps to access the hashcat option from the help screen.
Follow the above basic hashcat’s syntax (Gillet, Fourn & Hennion, 2012).
8
Follow the above basic hashcat’s syntax (Gillet, Fourn & Hennion, 2012).
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
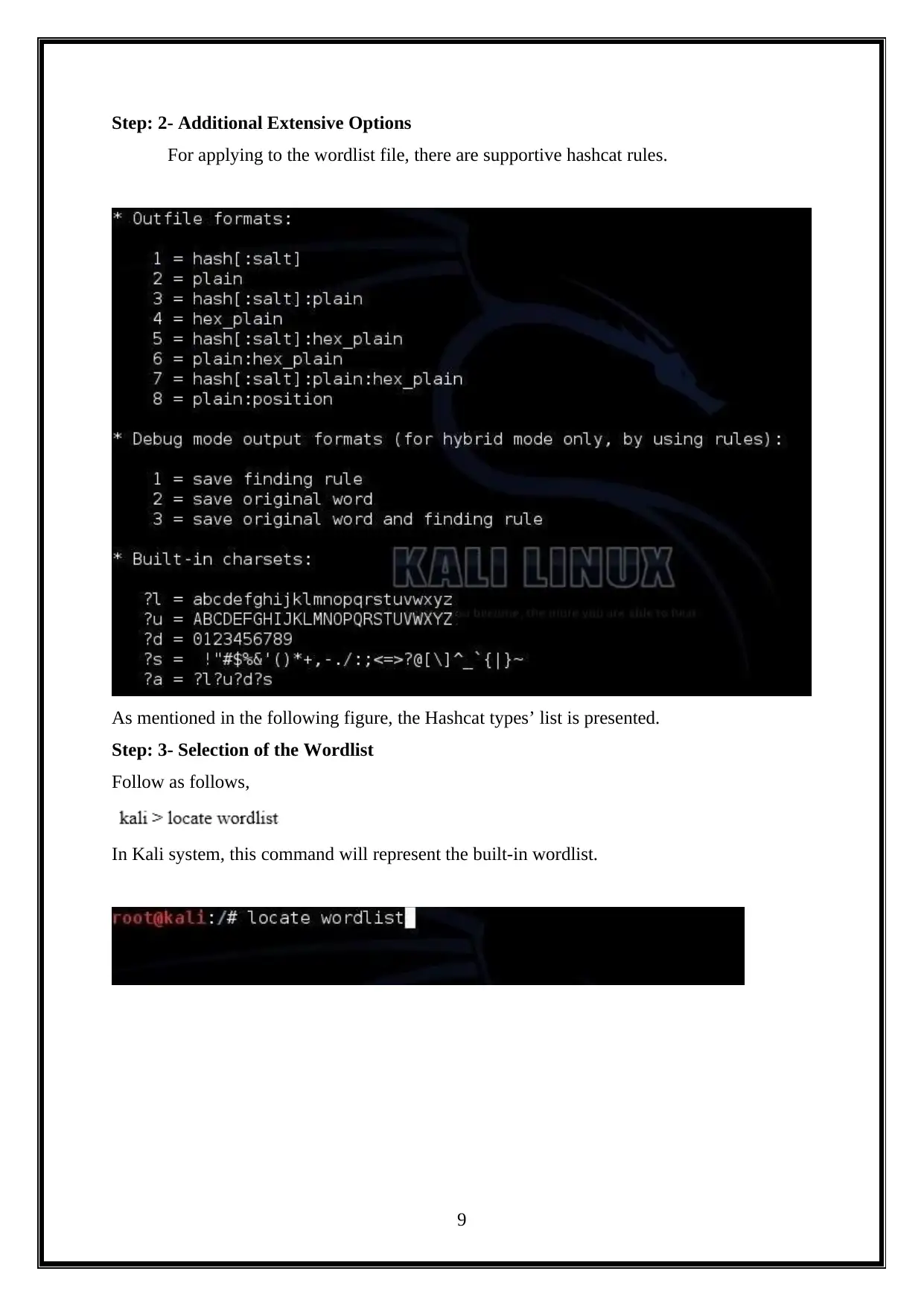
Step: 2- Additional Extensive Options
For applying to the wordlist file, there are supportive hashcat rules.
As mentioned in the following figure, the Hashcat types’ list is presented.
Step: 3- Selection of the Wordlist
Follow as follows,
In Kali system, this command will represent the built-in wordlist.
9
For applying to the wordlist file, there are supportive hashcat rules.
As mentioned in the following figure, the Hashcat types’ list is presented.
Step: 3- Selection of the Wordlist
Follow as follows,
In Kali system, this command will represent the built-in wordlist.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
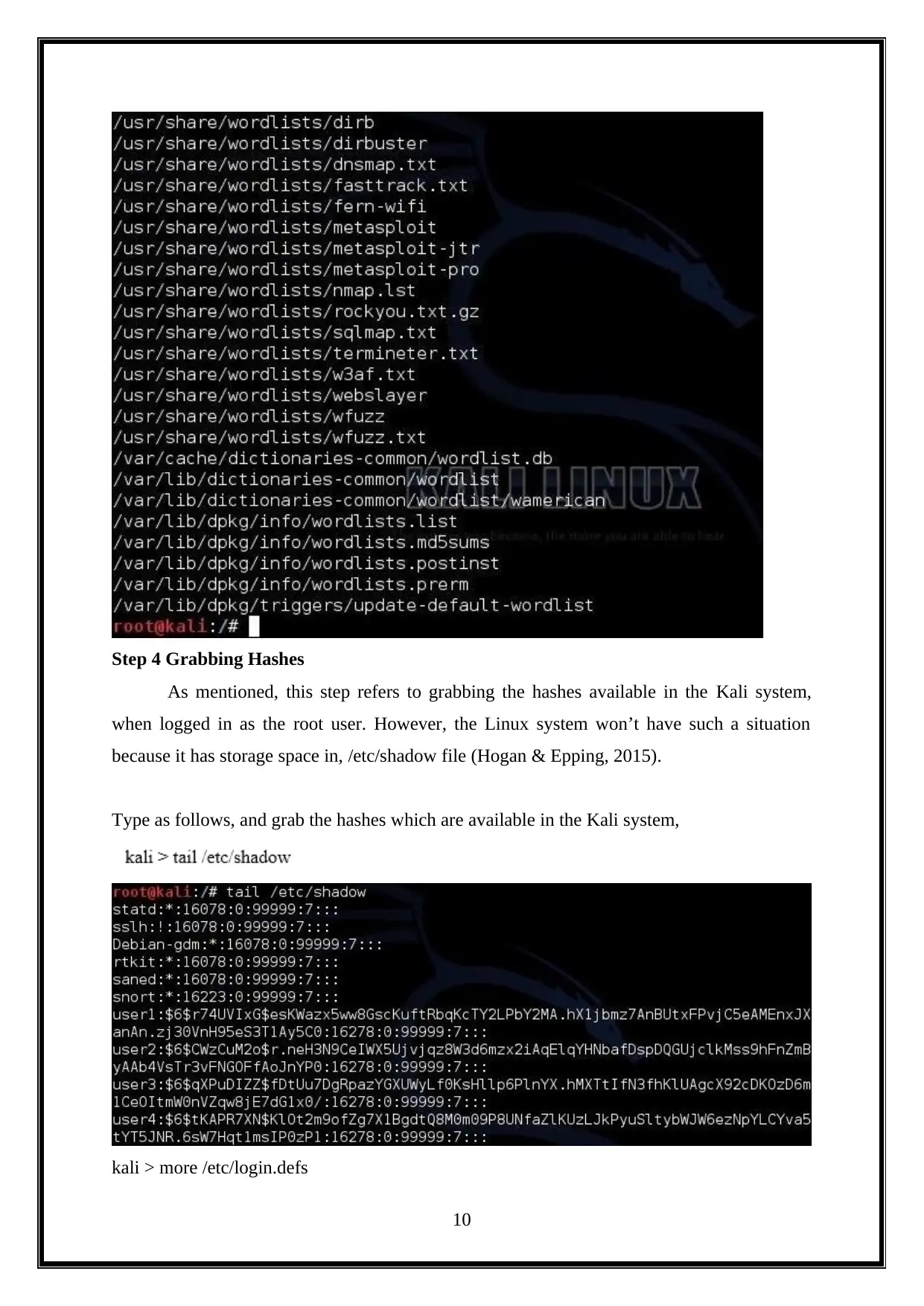
Step 4 Grabbing Hashes
As mentioned, this step refers to grabbing the hashes available in the Kali system,
when logged in as the root user. However, the Linux system won’t have such a situation
because it has storage space in, /etc/shadow file (Hogan & Epping, 2015).
Type as follows, and grab the hashes which are available in the Kali system,
kali > more /etc/login.defs
10
As mentioned, this step refers to grabbing the hashes available in the Kali system,
when logged in as the root user. However, the Linux system won’t have such a situation
because it has storage space in, /etc/shadow file (Hogan & Epping, 2015).
Type as follows, and grab the hashes which are available in the Kali system,
kali > more /etc/login.defs
10
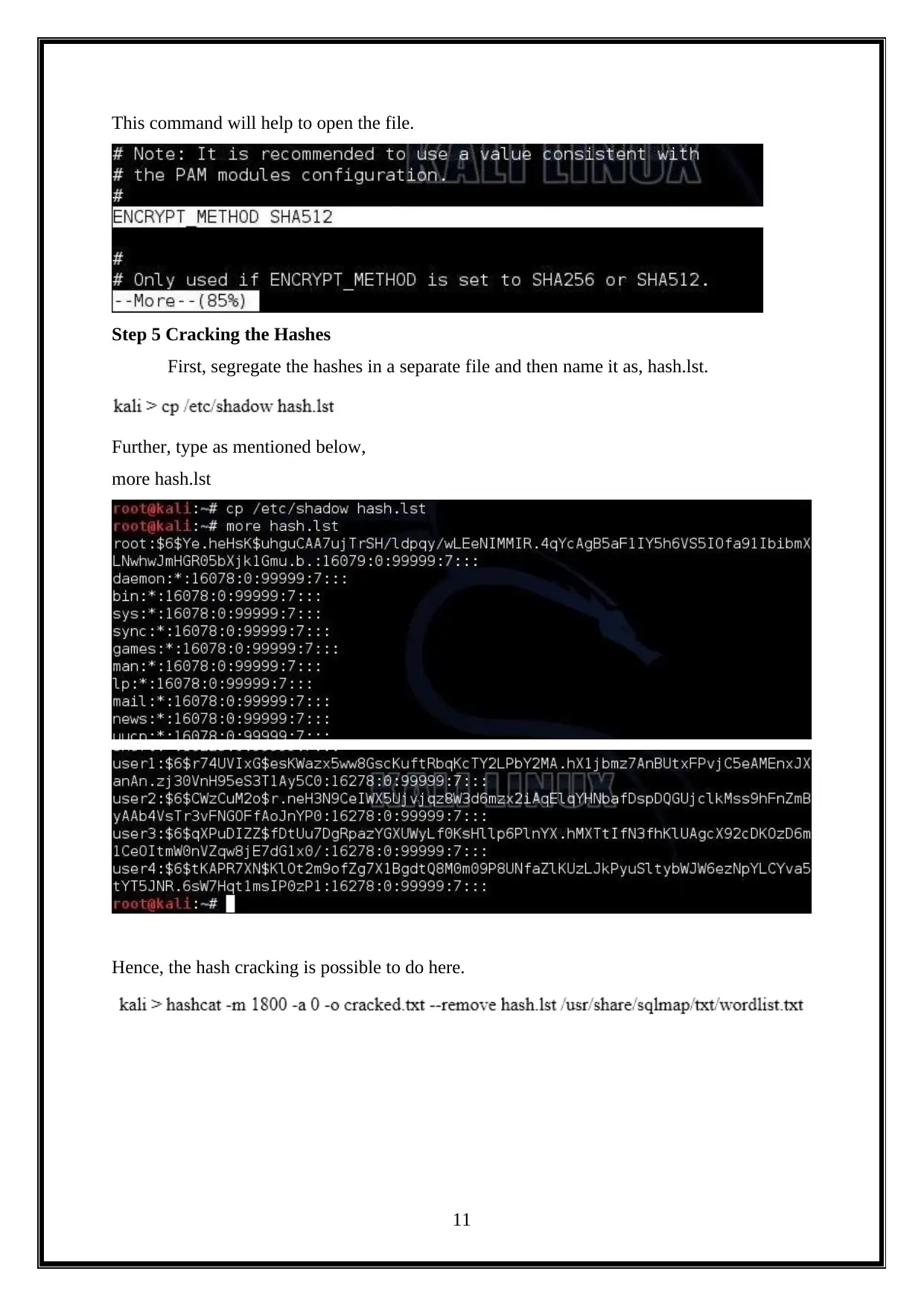
This command will help to open the file.
Step 5 Cracking the Hashes
First, segregate the hashes in a separate file and then name it as, hash.lst.
Further, type as mentioned below,
more hash.lst
Hence, the hash cracking is possible to do here.
11
Step 5 Cracking the Hashes
First, segregate the hashes in a separate file and then name it as, hash.lst.
Further, type as mentioned below,
more hash.lst
Hence, the hash cracking is possible to do here.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




