Ethical Hacking: Penetration Testing of FreeBSD OS Vulnerabilities
VerifiedAdded on 2023/01/12
|12
|2002
|39
Report
AI Summary
This report delves into the realm of ethical hacking, focusing on the identification and exploitation of operating system (OS) vulnerabilities, specifically within the FreeBSD environment. The report outlines the rationale behind vulnerability testing, employing black box penetration testing techniques to uncover security weaknesses. It details the methodology used, including reconnaissance, scanning, gaining and maintaining access, and analysis. The findings reveal several vulnerabilities, including open ports (SSH, HTTP, MySQL) and associated CVEs, along with potential exploits like brute-force attacks and remote code execution. Recommendations are provided to mitigate these risks, such as closing unused ports and implementing strong password policies. The report concludes by emphasizing the importance of continuous penetration testing to maintain a secure network and system.

Ethical Hacking
Table of Contents
Table of Contents
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction......................................................................................................................................3
OS Vulnerabilities..................................................................................................................3
Vulnerability test rationale.....................................................................................................4
Methodology...........................................................................................................................5
Findings..................................................................................................................................7
Recommendations................................................................................................................10
Conclusion.....................................................................................................................................10
References......................................................................................................................................12
Appendix 1.....................................................................................................................................13
OS Vulnerabilities..................................................................................................................3
Vulnerability test rationale.....................................................................................................4
Methodology...........................................................................................................................5
Findings..................................................................................................................................7
Recommendations................................................................................................................10
Conclusion.....................................................................................................................................10
References......................................................................................................................................12
Appendix 1.....................................................................................................................................13

Introduction
Ethical hacking refers to authorized practice that is associated with bypassing system
securities for identification of data breaches as well as threats within a network. An ethical
hacker aims at investigating network or system for weak points which can be used by malicious
hackers to destroy or exploit (Ahvanooey and et. al, 2020). This report will provide insight
operating vulnerabilities and penetrating testing is being used to exploiting them.
OS Vulnerabilities
Vulnerability refers to weaknesses which permits attackers within minimisation of
systems information assurance. It denotes flaws that can be exploited via threat actor like
attacker who carry out unauthorised actions in a system. For exploitation of vulnerability,
attacker needs to at least one applicable technique or tool which is liable for connecting them to
system weaknesses. It is also denoted by attack surface. The operating system used here is
FreeBSB which is free as well as open-source Unix like operating system. It is a modern
operating system for laptops, embedded systems and servers that is liable for supporting wide
range of platforms. It is liable for rendering fast as well as general purpose operating system that
can be utilised without any kind of strings. All the communication which takes place via internet
is exchanged through ports (Cerdeira and et. al, 2020). Each IP address comprises of two ports,
UDP (user datagram protocol) and TCP (transmission control protocol) along with this there are
around 65,535 ports for any given IP address. Services which are connected via internet like
email client, file transfer services and web browsers makes use of peculiar ports for receiving
information. The internet-connected services need peculiar ports to be open through which
functions can be conducted. But legitimate operations are exploited by malicious services or
code vulnerabilities which are being introduced into system through malware. Here, cyber
criminals utilise these services in conjunction with open ports for having access to sensitive
information that is present in peculiar system. Closing unused ports is identical to shutting down
the door for cyber criminals. So the vulnerability addressed in this report is open port
vulnerability.
When network is small that means there are few IP addresses, then closing ports is easy
and not a big deal but in case it is a large network then it is not easy as it can be time consuming
process (Hay and et. al, 2020). Thus, it is necessary that information which is exchanged
Ethical hacking refers to authorized practice that is associated with bypassing system
securities for identification of data breaches as well as threats within a network. An ethical
hacker aims at investigating network or system for weak points which can be used by malicious
hackers to destroy or exploit (Ahvanooey and et. al, 2020). This report will provide insight
operating vulnerabilities and penetrating testing is being used to exploiting them.
OS Vulnerabilities
Vulnerability refers to weaknesses which permits attackers within minimisation of
systems information assurance. It denotes flaws that can be exploited via threat actor like
attacker who carry out unauthorised actions in a system. For exploitation of vulnerability,
attacker needs to at least one applicable technique or tool which is liable for connecting them to
system weaknesses. It is also denoted by attack surface. The operating system used here is
FreeBSB which is free as well as open-source Unix like operating system. It is a modern
operating system for laptops, embedded systems and servers that is liable for supporting wide
range of platforms. It is liable for rendering fast as well as general purpose operating system that
can be utilised without any kind of strings. All the communication which takes place via internet
is exchanged through ports (Cerdeira and et. al, 2020). Each IP address comprises of two ports,
UDP (user datagram protocol) and TCP (transmission control protocol) along with this there are
around 65,535 ports for any given IP address. Services which are connected via internet like
email client, file transfer services and web browsers makes use of peculiar ports for receiving
information. The internet-connected services need peculiar ports to be open through which
functions can be conducted. But legitimate operations are exploited by malicious services or
code vulnerabilities which are being introduced into system through malware. Here, cyber
criminals utilise these services in conjunction with open ports for having access to sensitive
information that is present in peculiar system. Closing unused ports is identical to shutting down
the door for cyber criminals. So the vulnerability addressed in this report is open port
vulnerability.
When network is small that means there are few IP addresses, then closing ports is easy
and not a big deal but in case it is a large network then it is not easy as it can be time consuming
process (Hay and et. al, 2020). Thus, it is necessary that information which is exchanged
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

through them is monitored by making use of BitSight Security Ratings Platform. It provides
users with A to F grades for open ports on network. These are generated, updated as well as
reflect performance with respect to other firms.
Vulnerability test rationale
A black box testing technique in which authorised attempt is made for violating peculiar
constraints which are stated within form of integrity or security policies of system, network,
applications or database is referred to as penetration testing. It is a testing technique which is
liable for discovering as well as documenting essential security holes which are present within
system (Ahvanooey and et. al, 2020). It is liable for identification of weak within security
posture of organisation along with measures for compliance of security policies. The reports
which are being furnished by penetration testing are liable for rendering feedback which is
needed by organisation for prioritising investments within plans for making entire system
secured. These reports will aid application developer for creating more secured applications. The
major aspect related with penetration testing is that it is liable for defining scope in which testers
operate. This involves different stages.
Planning & reconnaissance: It is liable for defining scope as well as goals related test
that have to be addressed along with acquisition of intelligence for understanding ways in which
target works along with probable vulnerabilities associated with this.
Scanning: This furnishes information related with ways in which target application will
reply to distinct intrusion attempts (Casella, Singh and Covell, 2020). This involves static as well
as dynamic analysis. Tools will scan code in single pass and furnish real-time view for
performance of application respectively.
Gaining access: This stage makes use of web applications attacks like SSQL injection,
backdoors and SQL injection for uncovering vulnerabilities in target system. After this, tester
will exploit these vulnerabilities to acknowledge damage that can be caused by these.
Maintaining access: The rationale of this stage is to look that vulnerability can be
utilised for attaining persistent presence within exploited system. Basic idea is to imitate
persistent threats within system for stealing sensitive data of organisation.
Analysis: The outcome attained from penetration testing is compiled which will involve
peculiar vulnerabilities that are exploited, sensitive information which is accessed and time till
when tester was undetected by the system (Yasasin and et. al, 2020).
users with A to F grades for open ports on network. These are generated, updated as well as
reflect performance with respect to other firms.
Vulnerability test rationale
A black box testing technique in which authorised attempt is made for violating peculiar
constraints which are stated within form of integrity or security policies of system, network,
applications or database is referred to as penetration testing. It is a testing technique which is
liable for discovering as well as documenting essential security holes which are present within
system (Ahvanooey and et. al, 2020). It is liable for identification of weak within security
posture of organisation along with measures for compliance of security policies. The reports
which are being furnished by penetration testing are liable for rendering feedback which is
needed by organisation for prioritising investments within plans for making entire system
secured. These reports will aid application developer for creating more secured applications. The
major aspect related with penetration testing is that it is liable for defining scope in which testers
operate. This involves different stages.
Planning & reconnaissance: It is liable for defining scope as well as goals related test
that have to be addressed along with acquisition of intelligence for understanding ways in which
target works along with probable vulnerabilities associated with this.
Scanning: This furnishes information related with ways in which target application will
reply to distinct intrusion attempts (Casella, Singh and Covell, 2020). This involves static as well
as dynamic analysis. Tools will scan code in single pass and furnish real-time view for
performance of application respectively.
Gaining access: This stage makes use of web applications attacks like SSQL injection,
backdoors and SQL injection for uncovering vulnerabilities in target system. After this, tester
will exploit these vulnerabilities to acknowledge damage that can be caused by these.
Maintaining access: The rationale of this stage is to look that vulnerability can be
utilised for attaining persistent presence within exploited system. Basic idea is to imitate
persistent threats within system for stealing sensitive data of organisation.
Analysis: The outcome attained from penetration testing is compiled which will involve
peculiar vulnerabilities that are exploited, sensitive information which is accessed and time till
when tester was undetected by the system (Yasasin and et. al, 2020).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The above steps illustrated above will provide a report with respect to different aspects
like vulnerabilities identified along with sensitive information. If vulnerability is open ports or
weak passwords then relevant steps can be taken. Like ports can be closed and strong
alphanumeric passwords can be used (Yihunie, Singh and Bhatia, 2020). In this way depending
upon vulnerability that is identified adequate strategies can be formulated for mitigating them.
Methodology
Step 1: Probes
Attacker tried to network mapping victim machine through Hping2 and Xprobe2.
Attackers machine 10.10.10.15 through Nessus start reconnaissance host 10.10.10.10
Victim machine is scanned via NStealth and Nmap. Along with this HTTP
reconnaissance is also scanned through Nikto
Attacker scans 10.10.10.10 through 10.10.10.15 using GGFILanGuard. Attack machine
10.10.10.20 probes web server of target through HTTPrint.
Open ports are found to probable penetration Port SSH (22), HTTP (80) and MySQL
(3306). Various guesses are made to seek exploits.
Step 2: Brute Force Attackers attempt to attack host 10.10.10.10 through SSH brute-force. Dictionary
passwords are changed into guessing password Attackers failed pass.
Step 3: Escalating privilege Attackers tried to enter into system through admin and carried out remote exploitation. Alert attempts made sensepost.exe, c99shell.php. Attackers attempt to implant malware
as well as create backdoor. Attacker login as well as exploit escalates privileges.
Step 4: DoS Attackers attempt against network through TCP/UDP flooding and launch IICMP
flooding.
like vulnerabilities identified along with sensitive information. If vulnerability is open ports or
weak passwords then relevant steps can be taken. Like ports can be closed and strong
alphanumeric passwords can be used (Yihunie, Singh and Bhatia, 2020). In this way depending
upon vulnerability that is identified adequate strategies can be formulated for mitigating them.
Methodology
Step 1: Probes
Attacker tried to network mapping victim machine through Hping2 and Xprobe2.
Attackers machine 10.10.10.15 through Nessus start reconnaissance host 10.10.10.10
Victim machine is scanned via NStealth and Nmap. Along with this HTTP
reconnaissance is also scanned through Nikto
Attacker scans 10.10.10.10 through 10.10.10.15 using GGFILanGuard. Attack machine
10.10.10.20 probes web server of target through HTTPrint.
Open ports are found to probable penetration Port SSH (22), HTTP (80) and MySQL
(3306). Various guesses are made to seek exploits.
Step 2: Brute Force Attackers attempt to attack host 10.10.10.10 through SSH brute-force. Dictionary
passwords are changed into guessing password Attackers failed pass.
Step 3: Escalating privilege Attackers tried to enter into system through admin and carried out remote exploitation. Alert attempts made sensepost.exe, c99shell.php. Attackers attempt to implant malware
as well as create backdoor. Attacker login as well as exploit escalates privileges.
Step 4: DoS Attackers attempt against network through TCP/UDP flooding and launch IICMP
flooding.
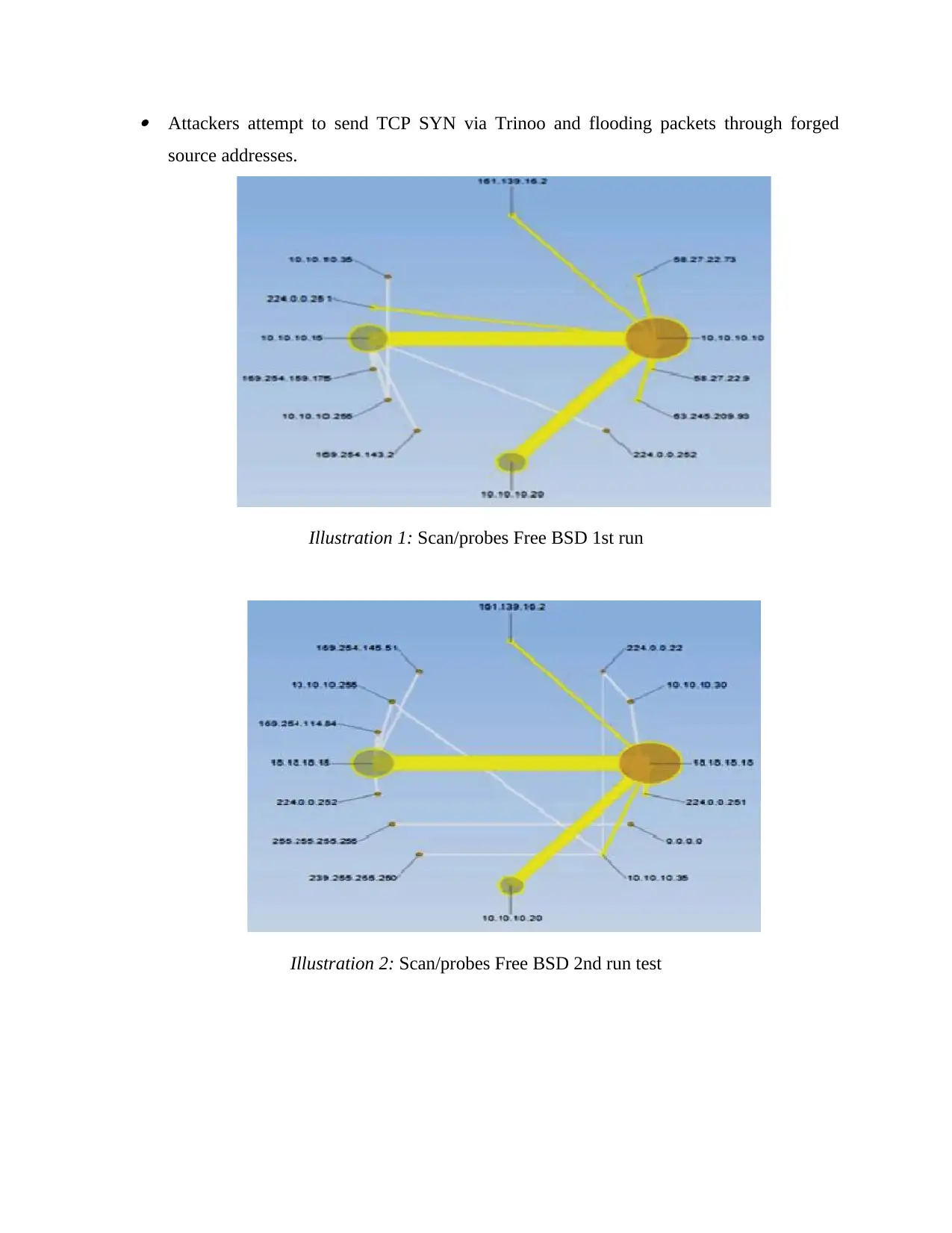
Attackers attempt to send TCP SYN via Trinoo and flooding packets through forged
source addresses.
Illustration 1: Scan/probes Free BSD 1st run
Illustration 2: Scan/probes Free BSD 2nd run test
source addresses.
Illustration 1: Scan/probes Free BSD 1st run
Illustration 2: Scan/probes Free BSD 2nd run test
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
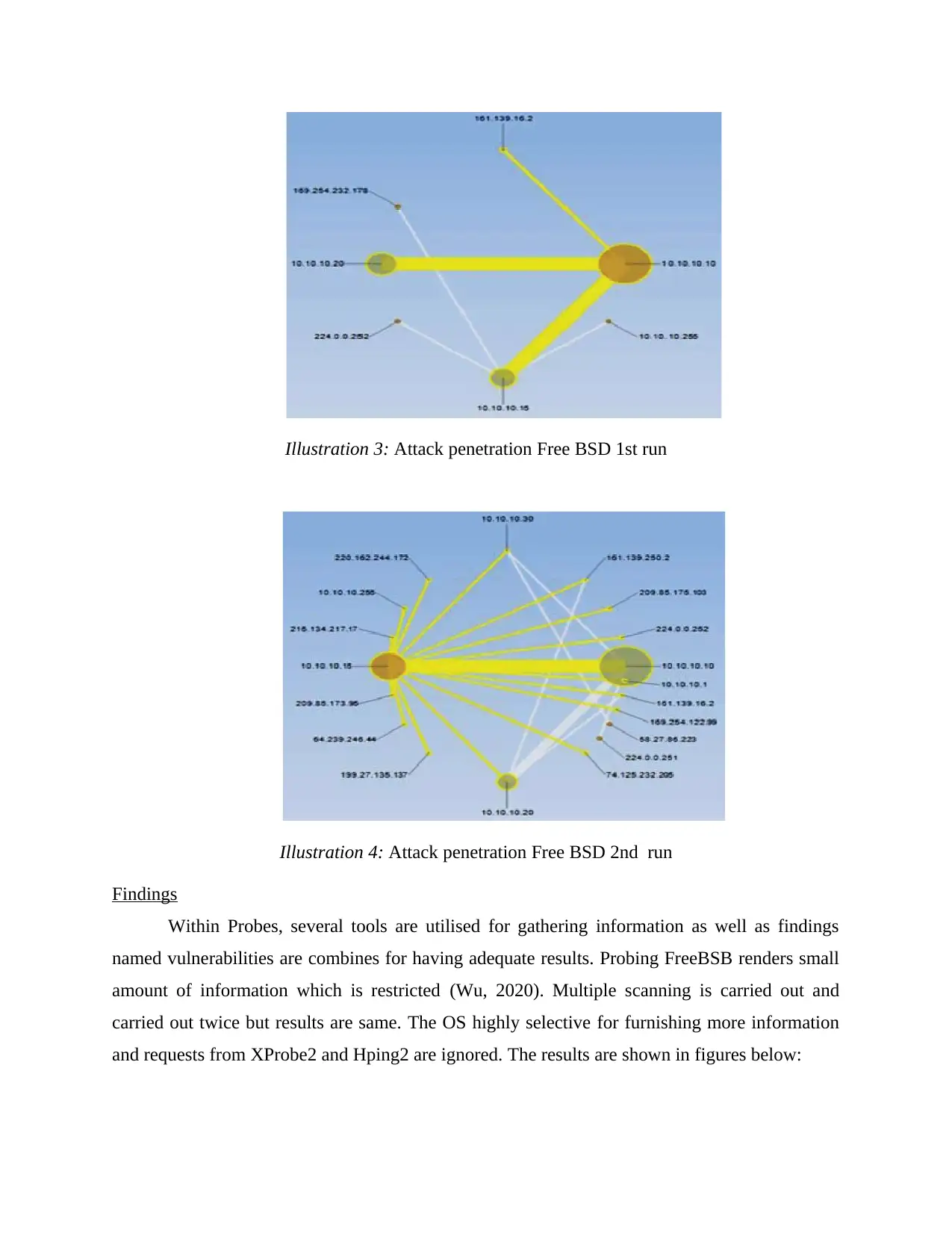
Illustration 3: Attack penetration Free BSD 1st run
Illustration 4: Attack penetration Free BSD 2nd run
Findings
Within Probes, several tools are utilised for gathering information as well as findings
named vulnerabilities are combines for having adequate results. Probing FreeBSB renders small
amount of information which is restricted (Wu, 2020). Multiple scanning is carried out and
carried out twice but results are same. The OS highly selective for furnishing more information
and requests from XProbe2 and Hping2 are ignored. The results are shown in figures below:
Illustration 4: Attack penetration Free BSD 2nd run
Findings
Within Probes, several tools are utilised for gathering information as well as findings
named vulnerabilities are combines for having adequate results. Probing FreeBSB renders small
amount of information which is restricted (Wu, 2020). Multiple scanning is carried out and
carried out twice but results are same. The OS highly selective for furnishing more information
and requests from XProbe2 and Hping2 are ignored. The results are shown in figures below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
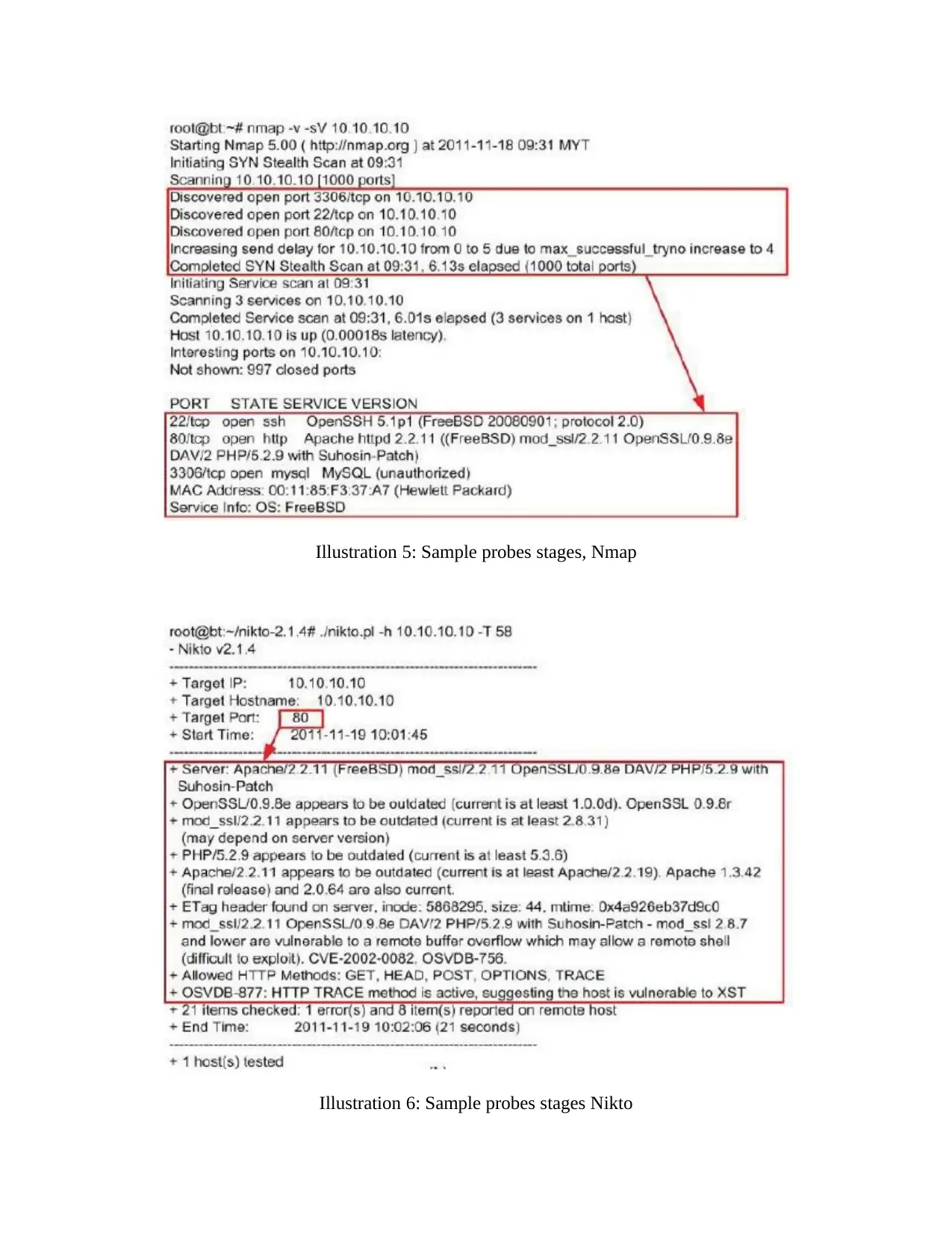
Illustration 5: Sample probes stages, Nmap
Illustration 6: Sample probes stages Nikto
Illustration 6: Sample probes stages Nikto

Illustration 7: Sample probes stages Xprobes
CVE is used for updating information as well as knowledge which opens to security
services for allowing cross links (Ahvanooey and et. al, 2020). Some vulnerability that has been
identified within FreeBSB are specified below:
Port Protocol Services Information CVE
CVE is used for updating information as well as knowledge which opens to security
services for allowing cross links (Ahvanooey and et. al, 2020). Some vulnerability that has been
identified within FreeBSB are specified below:
Port Protocol Services Information CVE
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
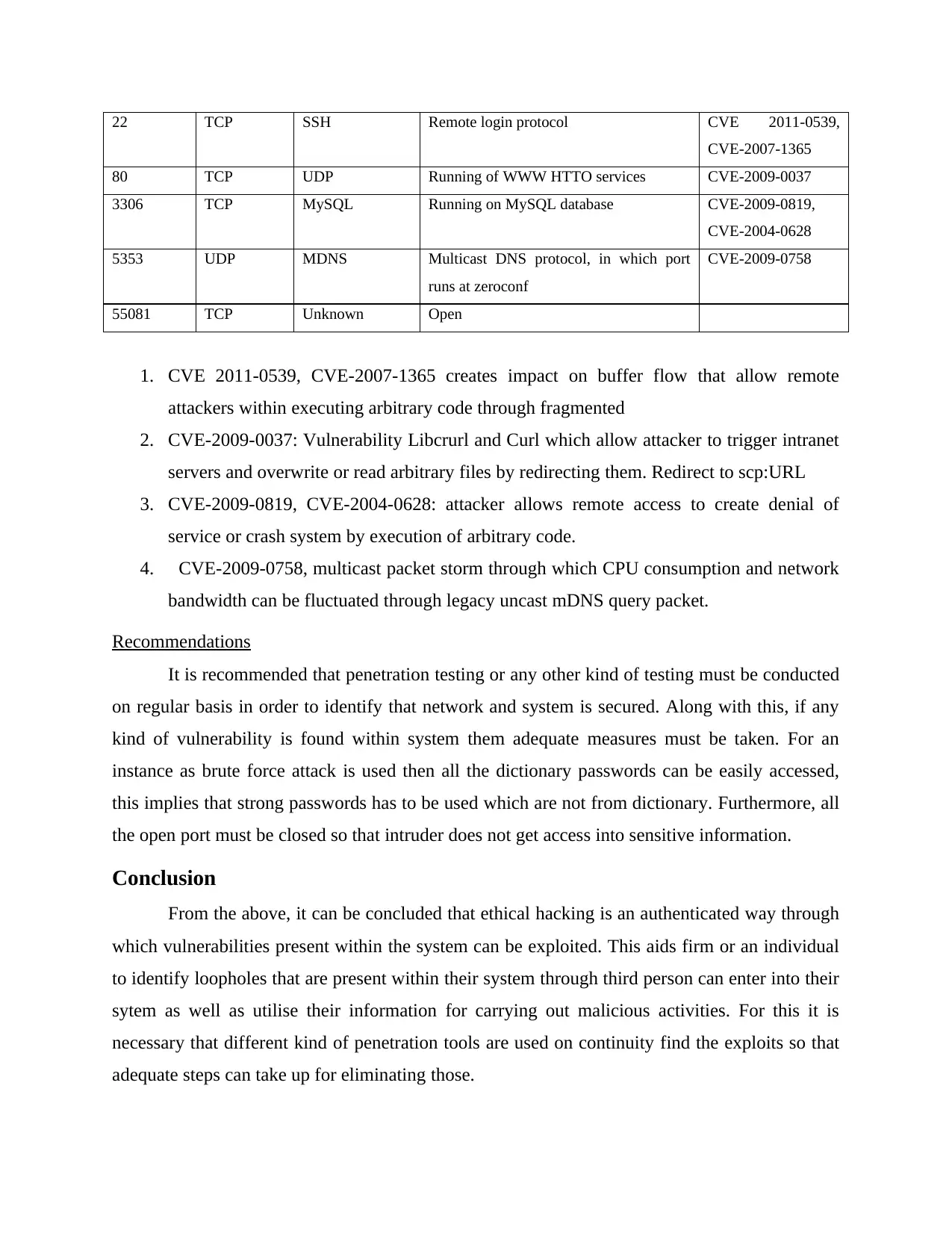
22 TCP SSH Remote login protocol CVE 2011-0539,
CVE-2007-1365
80 TCP UDP Running of WWW HTTO services CVE-2009-0037
3306 TCP MySQL Running on MySQL database CVE-2009-0819,
CVE-2004-0628
5353 UDP MDNS Multicast DNS protocol, in which port
runs at zeroconf
CVE-2009-0758
55081 TCP Unknown Open
1. CVE 2011-0539, CVE-2007-1365 creates impact on buffer flow that allow remote
attackers within executing arbitrary code through fragmented
2. CVE-2009-0037: Vulnerability Libcrurl and Curl which allow attacker to trigger intranet
servers and overwrite or read arbitrary files by redirecting them. Redirect to scp:URL
3. CVE-2009-0819, CVE-2004-0628: attacker allows remote access to create denial of
service or crash system by execution of arbitrary code.
4. CVE-2009-0758, multicast packet storm through which CPU consumption and network
bandwidth can be fluctuated through legacy uncast mDNS query packet.
Recommendations
It is recommended that penetration testing or any other kind of testing must be conducted
on regular basis in order to identify that network and system is secured. Along with this, if any
kind of vulnerability is found within system them adequate measures must be taken. For an
instance as brute force attack is used then all the dictionary passwords can be easily accessed,
this implies that strong passwords has to be used which are not from dictionary. Furthermore, all
the open port must be closed so that intruder does not get access into sensitive information.
Conclusion
From the above, it can be concluded that ethical hacking is an authenticated way through
which vulnerabilities present within the system can be exploited. This aids firm or an individual
to identify loopholes that are present within their system through third person can enter into their
sytem as well as utilise their information for carrying out malicious activities. For this it is
necessary that different kind of penetration tools are used on continuity find the exploits so that
adequate steps can take up for eliminating those.
CVE-2007-1365
80 TCP UDP Running of WWW HTTO services CVE-2009-0037
3306 TCP MySQL Running on MySQL database CVE-2009-0819,
CVE-2004-0628
5353 UDP MDNS Multicast DNS protocol, in which port
runs at zeroconf
CVE-2009-0758
55081 TCP Unknown Open
1. CVE 2011-0539, CVE-2007-1365 creates impact on buffer flow that allow remote
attackers within executing arbitrary code through fragmented
2. CVE-2009-0037: Vulnerability Libcrurl and Curl which allow attacker to trigger intranet
servers and overwrite or read arbitrary files by redirecting them. Redirect to scp:URL
3. CVE-2009-0819, CVE-2004-0628: attacker allows remote access to create denial of
service or crash system by execution of arbitrary code.
4. CVE-2009-0758, multicast packet storm through which CPU consumption and network
bandwidth can be fluctuated through legacy uncast mDNS query packet.
Recommendations
It is recommended that penetration testing or any other kind of testing must be conducted
on regular basis in order to identify that network and system is secured. Along with this, if any
kind of vulnerability is found within system them adequate measures must be taken. For an
instance as brute force attack is used then all the dictionary passwords can be easily accessed,
this implies that strong passwords has to be used which are not from dictionary. Furthermore, all
the open port must be closed so that intruder does not get access into sensitive information.
Conclusion
From the above, it can be concluded that ethical hacking is an authenticated way through
which vulnerabilities present within the system can be exploited. This aids firm or an individual
to identify loopholes that are present within their system through third person can enter into their
sytem as well as utilise their information for carrying out malicious activities. For this it is
necessary that different kind of penetration tools are used on continuity find the exploits so that
adequate steps can take up for eliminating those.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
Books and Journals
Ahvanooey, M.T. and et. al, 2020. A survey on smartphones security: Software vulnerabilities,
malware, and attacks. arXiv preprint arXiv:2001.09406.
Cerdeira, D. and et. al, 2020, May. SoK: Understanding the Prevailing Security Vulnerabilities in
TrustZone-assisted TEE Systems. In Proceedings of the IEEE Symposium on Security
and Privacy (S&P), San Francisco, CA, USA (pp. 18-20).
Hay, R. and et. al, International Business Machines Corp, 2020. Detecting security
vulnerabilities on computing devices. U.S. Patent 10,528,744.
Ahvanooey, M.T. and et. al, 2020. A survey on smartphones security: Software vulnerabilities,
malware, and attacks. arXiv preprint arXiv:2001.09406.
Casella, A., Singh, M. and Covell, G., International Business Machines Corp, 2020. Detecting
and patching network vulnerabilities. U.S. Patent Application 16/044,631.
Yasasin, E. and et. al, 2020. Forecasting IT security vulnerabilities–An empirical
analysis. Computers & Security, 88, p.101610.
Yihunie, F.L., Singh, A.K. and Bhatia, S., 2020. Assessing and Exploiting Security
Vulnerabilities of Unmanned Aerial Vehicles. In Smart Systems and IoT: Innovations in
Computing (pp. 701-710). Springer, Singapore.
Wu, J., 2020. Security Risks from Vulnerabilities and Backdoors. In Cyberspace Mimic
Defense (pp. 3-38). Springer, Cham.
Books and Journals
Ahvanooey, M.T. and et. al, 2020. A survey on smartphones security: Software vulnerabilities,
malware, and attacks. arXiv preprint arXiv:2001.09406.
Cerdeira, D. and et. al, 2020, May. SoK: Understanding the Prevailing Security Vulnerabilities in
TrustZone-assisted TEE Systems. In Proceedings of the IEEE Symposium on Security
and Privacy (S&P), San Francisco, CA, USA (pp. 18-20).
Hay, R. and et. al, International Business Machines Corp, 2020. Detecting security
vulnerabilities on computing devices. U.S. Patent 10,528,744.
Ahvanooey, M.T. and et. al, 2020. A survey on smartphones security: Software vulnerabilities,
malware, and attacks. arXiv preprint arXiv:2001.09406.
Casella, A., Singh, M. and Covell, G., International Business Machines Corp, 2020. Detecting
and patching network vulnerabilities. U.S. Patent Application 16/044,631.
Yasasin, E. and et. al, 2020. Forecasting IT security vulnerabilities–An empirical
analysis. Computers & Security, 88, p.101610.
Yihunie, F.L., Singh, A.K. and Bhatia, S., 2020. Assessing and Exploiting Security
Vulnerabilities of Unmanned Aerial Vehicles. In Smart Systems and IoT: Innovations in
Computing (pp. 701-710). Springer, Singapore.
Wu, J., 2020. Security Risks from Vulnerabilities and Backdoors. In Cyberspace Mimic
Defense (pp. 3-38). Springer, Cham.
Appendix 1
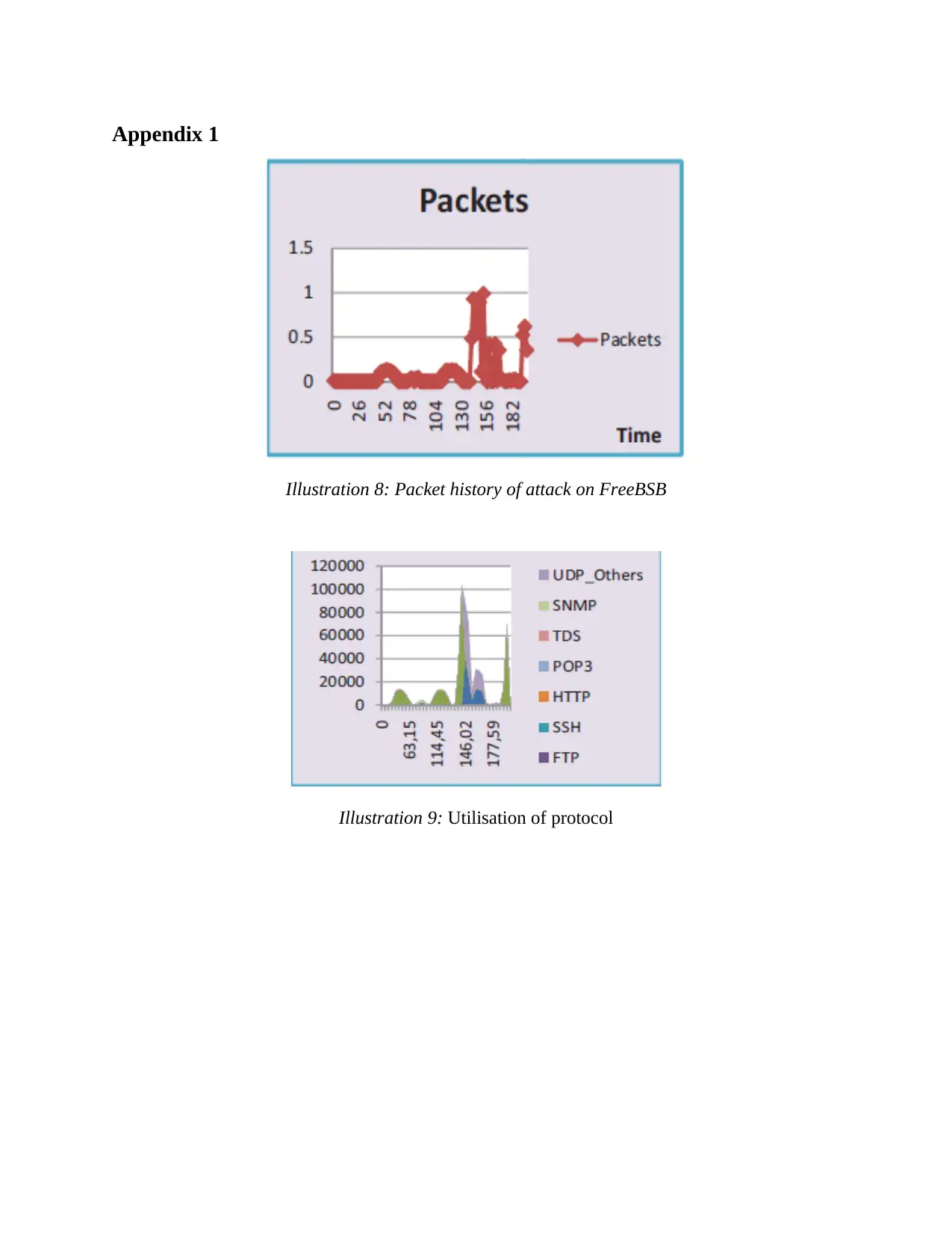
Illustration 8: Packet history of attack on FreeBSB
Illustration 9: Utilisation of protocol
Illustration 8: Packet history of attack on FreeBSB
Illustration 9: Utilisation of protocol
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





