Information Security System Implementation Company Purpose
VerifiedAdded on 2022/05/12
|12
|3245
|246
AI Summary
In this assignment, we discuss F-Secure Information System Security System Implementation The business later grew to the point that it now has a large employee base and serves clients outside of its immediate vicinity. Thirteen doctors, seven optometrists, and a pool of one hundred and forty-four employees who are in charge of providing clinical and administrative assistance as well as a secure data transmission system make up the organization's total staff of one hundred and sixty-five.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Surname 1
Student’s Name
Tutor’s Name
Course
Date
F-Secure Information System Security System Implementation
Table of Contents
Company Purpose.......................................................................................................................................2
Problem & Solution.....................................................................................................................................3
Identification of Issues.............................................................................................................................4
Information security and credibility.....................................................................................................4
Integrity...............................................................................................................................................4
Infrastructural Issues...........................................................................................................................5
Financial constraints............................................................................................................................5
Market size..................................................................................................................................................6
Product........................................................................................................................................................8
Team............................................................................................................................................................9
Business Model...........................................................................................................................................9
Competition...............................................................................................................................................10
Financials:..................................................................................................................................................11
Works Cited...............................................................................................................................................12
Student’s Name
Tutor’s Name
Course
Date
F-Secure Information System Security System Implementation
Table of Contents
Company Purpose.......................................................................................................................................2
Problem & Solution.....................................................................................................................................3
Identification of Issues.............................................................................................................................4
Information security and credibility.....................................................................................................4
Integrity...............................................................................................................................................4
Infrastructural Issues...........................................................................................................................5
Financial constraints............................................................................................................................5
Market size..................................................................................................................................................6
Product........................................................................................................................................................8
Team............................................................................................................................................................9
Business Model...........................................................................................................................................9
Competition...............................................................................................................................................10
Financials:..................................................................................................................................................11
Works Cited...............................................................................................................................................12
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Surname 2
Company Purpose
Lansing Ophthalmology is an organization that has been in the medical care industry. The
organization has gradually grown to an extent it has employed a large number of employees and
gone beyond the boundaries of its locality to serve the customers. The organization has a total of
one hundred and sixty-five employees who comprise of fourteen physicians, seven optometrists
and a pool of one hundred and forty-four employees who are tasked with the responsibility of
providing clinical and administrative support and data transfer secure system (Siponen and
Anthony 489). Lansing Ophthalmology has been in a position to build a customer capacity of
over one hundred thousand patients of which seventy-five thousand are seen every year. One of
the leading facilities of Lansing Ophthalmology as an organization is East Lansing office which
is a 35000 square foot facility. East Lansing facility attends to about eighty percent of the
patients as it concentrates on various services which include eye examination, performing
surgery, and dispensing of eyewear (Benson 1346). The remaining twenty percent of the patients
are distributed to be examined in other six satellite offices which are located within a radius of
67 miles.
The issue with Lansing Ophthalmology is that it wanted to be in line with new management
improvement techniques to ensure that it achieves its goals in the healthcare industry. Lansing
Ophthalmology as a business organization wanted to implement improvement technique
commonly known as six sigma and Lean manufacturing which are used in the identification and
reduction of defects that are experienced in the production methods which were encountered in
the organization for more than two decades (Näslund 281). Despite the fact that was used in the
automotive and manufacturing industry with the aim of reducing costs and increase profits as
well as efficiency, there are some elements of the technique that can be applied in the healthcare
Company Purpose
Lansing Ophthalmology is an organization that has been in the medical care industry. The
organization has gradually grown to an extent it has employed a large number of employees and
gone beyond the boundaries of its locality to serve the customers. The organization has a total of
one hundred and sixty-five employees who comprise of fourteen physicians, seven optometrists
and a pool of one hundred and forty-four employees who are tasked with the responsibility of
providing clinical and administrative support and data transfer secure system (Siponen and
Anthony 489). Lansing Ophthalmology has been in a position to build a customer capacity of
over one hundred thousand patients of which seventy-five thousand are seen every year. One of
the leading facilities of Lansing Ophthalmology as an organization is East Lansing office which
is a 35000 square foot facility. East Lansing facility attends to about eighty percent of the
patients as it concentrates on various services which include eye examination, performing
surgery, and dispensing of eyewear (Benson 1346). The remaining twenty percent of the patients
are distributed to be examined in other six satellite offices which are located within a radius of
67 miles.
The issue with Lansing Ophthalmology is that it wanted to be in line with new management
improvement techniques to ensure that it achieves its goals in the healthcare industry. Lansing
Ophthalmology as a business organization wanted to implement improvement technique
commonly known as six sigma and Lean manufacturing which are used in the identification and
reduction of defects that are experienced in the production methods which were encountered in
the organization for more than two decades (Näslund 281). Despite the fact that was used in the
automotive and manufacturing industry with the aim of reducing costs and increase profits as
well as efficiency, there are some elements of the technique that can be applied in the healthcare

Surname 3
sector. The methods can be implemented in the identification and reduction of variance which is
used in the healthcare processes within the physician offices. What triggered the course of action
by Lansing Ophthalmology was the belief by medical professionals that the health care routine
complexity defies the categorization type which is essential in the process variation elimination
which leads to waste.
Problem & Solution
There is always need for a secure system. At home most of us use our computers for internet
banking, ordering things online, and social connection. Without a safe mode, an individual can
lose important data that can lead to fraud and identity theft. When an organization is not using a
secure computer system, the vital information of the company is at the risk of landing to the
wrong hands. Hackers can get the information and steal organizations revenue and also customer
information which is risky. Organizations are required by law to protect the confidentiality,
integrity, and authenticity of customer information.
The objectives of my project are met, the sole purpose of this project is of providing security as a
service in an organization and home computer systems which is working out well. It has
demonstrated that the safety of computer systems is achievable. F-Secure solution is on track and
has been able to achieve all the objectives highlighted at the initial stages of the project. The
method of delivery is followed to the later, and no shortcut was used in either installation or
acquiring of the software. The use of alternatives is a threat to incorporating security as a system
because hackers easily find loopholes in shortcuts. Although there are more recommendations in
the future, a secure system project should include a real working environment. There was an
underestimate on time required and, in future proper time analysis should be considered to avoid
a rush. There has been a risk of information loss due to lack of backup. In coming times back up
sector. The methods can be implemented in the identification and reduction of variance which is
used in the healthcare processes within the physician offices. What triggered the course of action
by Lansing Ophthalmology was the belief by medical professionals that the health care routine
complexity defies the categorization type which is essential in the process variation elimination
which leads to waste.
Problem & Solution
There is always need for a secure system. At home most of us use our computers for internet
banking, ordering things online, and social connection. Without a safe mode, an individual can
lose important data that can lead to fraud and identity theft. When an organization is not using a
secure computer system, the vital information of the company is at the risk of landing to the
wrong hands. Hackers can get the information and steal organizations revenue and also customer
information which is risky. Organizations are required by law to protect the confidentiality,
integrity, and authenticity of customer information.
The objectives of my project are met, the sole purpose of this project is of providing security as a
service in an organization and home computer systems which is working out well. It has
demonstrated that the safety of computer systems is achievable. F-Secure solution is on track and
has been able to achieve all the objectives highlighted at the initial stages of the project. The
method of delivery is followed to the later, and no shortcut was used in either installation or
acquiring of the software. The use of alternatives is a threat to incorporating security as a system
because hackers easily find loopholes in shortcuts. Although there are more recommendations in
the future, a secure system project should include a real working environment. There was an
underestimate on time required and, in future proper time analysis should be considered to avoid
a rush. There has been a risk of information loss due to lack of backup. In coming times back up

Surname 4
techniques should be employed to safeguard the information made for the project. Secure service
incorporation in computer systems is a significant challenge in organizations, and a real-time
demonstration of the system malfunction is significant alongside proper presentation and training
of all the organizational staff. The stakeholders will be informed of the next phase which is phase
4 and made clear that in step 4 we will spend more time solving real problems and analyzing any
responses we shall receive.
Identification of Issues
Information security and credibility
Information is exposed to outer impacts since it very well may be gotten to remotely from
wherever around the world, which uncovered specific information, for example, credit card data
for web-based obtaining held by organizations to potential security breaks. This lessens the
selection of big data computing framework in many developing organizations since the
administrations set up needs to keep up security over the web, hindering its development
particularly in the business environment. This is on account of distributed computing as an
innovation includes the interconnection of different applications and systems, which are inclined
to assaults accordingly decreasing the rates of data sending by numerous legislatures and
organizations in a large portion of the businesses.
Integrity
In addition, another security component that lessens the appropriation of the big data
innovation is Integrity. Integrity as a security challenge principally introduces itself since
information and data are not put away in the organization environment. This builds chance on
data as most organizations come up short on the infrastructural capacity of keeping up the
security of their IT frameworks. This hence displays an extraordinary test to governments and
organizations as most need appropriate foundations expected to help distributed database
systems, while in the meantime keeping up the security of such supporting frameworks
techniques should be employed to safeguard the information made for the project. Secure service
incorporation in computer systems is a significant challenge in organizations, and a real-time
demonstration of the system malfunction is significant alongside proper presentation and training
of all the organizational staff. The stakeholders will be informed of the next phase which is phase
4 and made clear that in step 4 we will spend more time solving real problems and analyzing any
responses we shall receive.
Identification of Issues
Information security and credibility
Information is exposed to outer impacts since it very well may be gotten to remotely from
wherever around the world, which uncovered specific information, for example, credit card data
for web-based obtaining held by organizations to potential security breaks. This lessens the
selection of big data computing framework in many developing organizations since the
administrations set up needs to keep up security over the web, hindering its development
particularly in the business environment. This is on account of distributed computing as an
innovation includes the interconnection of different applications and systems, which are inclined
to assaults accordingly decreasing the rates of data sending by numerous legislatures and
organizations in a large portion of the businesses.
Integrity
In addition, another security component that lessens the appropriation of the big data
innovation is Integrity. Integrity as a security challenge principally introduces itself since
information and data are not put away in the organization environment. This builds chance on
data as most organizations come up short on the infrastructural capacity of keeping up the
security of their IT frameworks. This hence displays an extraordinary test to governments and
organizations as most need appropriate foundations expected to help distributed database
systems, while in the meantime keeping up the security of such supporting frameworks
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Surname 5
interfacing with business applications, for example, web interfaces for internet managing an
account.
Then again, a portion of the established businesses confront a security challenge in
embracing the distributed computing innovations. This is because of absence of institutionalized
security benchmarks in such organizations, which diminishes the appropriation of the innovation
by different organizations because of the incredible worry in security, with most organizations
tending to modest far from receiving such mechanical developments.
Infrastructural Issues
The retail businesses likewise keeps on encountering a moderate take-up of distributed
computing and big data technology in some business establishments. There are dangers related
with moving information and data over the online retail entryways, because of much presentation
to security related ruptures, making individuals and organizations to fall behind in tolerating such
technologies (Kankanhalli 142). This is a result of administrative and infrastructural lack of
ability of certain retail organizations to interface the database frameworks being worked by
universal installment shippers with nearby retailers, essentially because of potential security and
configuration blemishes.
Financial constraints
The money related ascribe additionally stays to be an incredible angle that builds the
take-up of certain ICT-empowered administrations and big data analytics, for example, the data
computing technology. This is fundamentally delineated in various organizations due to low-
revenue levels that can't animate the technology of data computing in retail business fragments.
While there are impediments in realizing big data analytics as an innovation, there is requirement
for partners to break down how such components can be implemented, with the end goal to goad
interfacing with business applications, for example, web interfaces for internet managing an
account.
Then again, a portion of the established businesses confront a security challenge in
embracing the distributed computing innovations. This is because of absence of institutionalized
security benchmarks in such organizations, which diminishes the appropriation of the innovation
by different organizations because of the incredible worry in security, with most organizations
tending to modest far from receiving such mechanical developments.
Infrastructural Issues
The retail businesses likewise keeps on encountering a moderate take-up of distributed
computing and big data technology in some business establishments. There are dangers related
with moving information and data over the online retail entryways, because of much presentation
to security related ruptures, making individuals and organizations to fall behind in tolerating such
technologies (Kankanhalli 142). This is a result of administrative and infrastructural lack of
ability of certain retail organizations to interface the database frameworks being worked by
universal installment shippers with nearby retailers, essentially because of potential security and
configuration blemishes.
Financial constraints
The money related ascribe additionally stays to be an incredible angle that builds the
take-up of certain ICT-empowered administrations and big data analytics, for example, the data
computing technology. This is fundamentally delineated in various organizations due to low-
revenue levels that can't animate the technology of data computing in retail business fragments.
While there are impediments in realizing big data analytics as an innovation, there is requirement
for partners to break down how such components can be implemented, with the end goal to goad

Surname 6
the take-up of the technology in both established and developing businesses in different parts of
the world.
Market size
Given the moderate selection of database systems and computing in most organizations, its
impact has contrarily influenced a few fragments, for example, customer satisfaction and
business performance. In Sub-Saharan Africa for example, there are couple of nations embracing
the big data analytics in the arrangement of business administrations mostly because of deficient
registering offices. Most organizations and learning organizations will in general utilize the
regular methods for classes with the end goal to offer instructive administrations to its customers
with the use of computer analytics. This moderate appropriation has fundamentally influenced
higher establishments of learning in view of the negative picture of imaginative instructive
apparatuses combined with security issues, lacking aptitudes and information that can be utilized
in the creation and advancement of electronic administrations and applications that can
incorporate with cloud-based and big data business analytics frameworks to give customer-
oriented administrations through the results of the analytics. Lotte.com being an example
generally utilizes their big data analytics capabilities, which constrains the entrance and
utilization of present-day business advancements from the cutting-edge marketing strategies and
technological applications. This idea extraordinarily increases the reception of the products and
services in the marketing sector, with most customers feeling accommodated through the
utilization of this technologies in the marketing. This results to Lotte.com become ever growing
in terms of the profit margins and as well as customer base due to high levels of satisfaction
realized.
the take-up of the technology in both established and developing businesses in different parts of
the world.
Market size
Given the moderate selection of database systems and computing in most organizations, its
impact has contrarily influenced a few fragments, for example, customer satisfaction and
business performance. In Sub-Saharan Africa for example, there are couple of nations embracing
the big data analytics in the arrangement of business administrations mostly because of deficient
registering offices. Most organizations and learning organizations will in general utilize the
regular methods for classes with the end goal to offer instructive administrations to its customers
with the use of computer analytics. This moderate appropriation has fundamentally influenced
higher establishments of learning in view of the negative picture of imaginative instructive
apparatuses combined with security issues, lacking aptitudes and information that can be utilized
in the creation and advancement of electronic administrations and applications that can
incorporate with cloud-based and big data business analytics frameworks to give customer-
oriented administrations through the results of the analytics. Lotte.com being an example
generally utilizes their big data analytics capabilities, which constrains the entrance and
utilization of present-day business advancements from the cutting-edge marketing strategies and
technological applications. This idea extraordinarily increases the reception of the products and
services in the marketing sector, with most customers feeling accommodated through the
utilization of this technologies in the marketing. This results to Lotte.com become ever growing
in terms of the profit margins and as well as customer base due to high levels of satisfaction
realized.

Surname 7
The take-up and infiltration of data analytics is especially ease back because of moderate
web association from database systems ordinarily utilized in business. Many businesses still
utilize poor database systems to get to the web which can't bolster such trend setting innovations,
for example, distributed computing. This brings a greater gap as established business that possess
cloud-based frameworks utilize present day technologies to help their stages and which then
again can't incorporate with different frameworks which keep running on poor web
infrastructure. The issue in this case is on the grounds that such cloud-based databases are
generally facilitated in far areas which will require quick web internet whereby absence of this
totally crashes its reception in a business.
Developing businesses keep on lingering behind in the selection of distributed computing
because of absence of IT Infrastructure. This is on the grounds that the technology keeps running
in stable conditions without any cases of intrusions either because of intensity deficiencies or
lacking offices to help organizations and learning establishments utilizing such an innovation. In
a business battling with infrastructural improvements, it turns into an incredible test to actualize
distributed computing for the most part because of absence of basic offices which are expected to
convey or deliver the technology. For example, in organizations with poor framework, it is
troublesome for employees to get to web phases particularly when the foundation is associated
with business applications, which may obstruct individuals from getting to basic administrations.
While the selection of data analytics frameworks and options are upset by different
budgetary difficulties, there are different alleviation techniques which can be utilized by
organizations and instructive suppliers. In the innovative front, it is less demanding to rent than
to work without any preparation, consequently one of the solutions for money related difficulties
The take-up and infiltration of data analytics is especially ease back because of moderate
web association from database systems ordinarily utilized in business. Many businesses still
utilize poor database systems to get to the web which can't bolster such trend setting innovations,
for example, distributed computing. This brings a greater gap as established business that possess
cloud-based frameworks utilize present day technologies to help their stages and which then
again can't incorporate with different frameworks which keep running on poor web
infrastructure. The issue in this case is on the grounds that such cloud-based databases are
generally facilitated in far areas which will require quick web internet whereby absence of this
totally crashes its reception in a business.
Developing businesses keep on lingering behind in the selection of distributed computing
because of absence of IT Infrastructure. This is on the grounds that the technology keeps running
in stable conditions without any cases of intrusions either because of intensity deficiencies or
lacking offices to help organizations and learning establishments utilizing such an innovation. In
a business battling with infrastructural improvements, it turns into an incredible test to actualize
distributed computing for the most part because of absence of basic offices which are expected to
convey or deliver the technology. For example, in organizations with poor framework, it is
troublesome for employees to get to web phases particularly when the foundation is associated
with business applications, which may obstruct individuals from getting to basic administrations.
While the selection of data analytics frameworks and options are upset by different
budgetary difficulties, there are different alleviation techniques which can be utilized by
organizations and instructive suppliers. In the innovative front, it is less demanding to rent than
to work without any preparation, consequently one of the solutions for money related difficulties
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Surname 8
is frame a joint endeavor with outsider specialist organizations where the aggregate costs
engaged with executing the big data technology would be shared among the partners included.
Product
When attackers are lucky to gain access to an organization’s system, it is either using a loophole
in the system or by use of phishing using emails of the company or the employees of the
company. The attackers then work on the contrary by gaining access to the company data.
Attackers will use administrator tools and rights to control and manipulate the system in a
malicious way.
The use of F-Secure system Rapid Detection and Response application identifies all the
intrusions, endpoint attacks, networks, and any server attacks and use a cloud-based approach to
record real-time attacks and ways of mitigating the attacks (Fernandes, Soares, Gomes, Freire
and Inácio 147). The cloud-based technologies are vast and fast in detecting any system
abnormalities with the use of high-end technologies like big data, real-time, and reputational
analytics. The purpose of these technologies in combination with artificial intelligence detects
the known and unknown malicious system behaviors. The use of these different analytics
methods keeps the company system secure in such a way that all the attacks are detected even
those using different evasion tactics.
The Rapid Response application also offers organization on-site incident response facilities to
help bail out the company in times of difficulties and just in case the company Information
technology engineers are not on the ground.
The primary project objective is ensuring that we have a secure computer system in either home-
based or organizational context. Incorporation of security as a service is an excellent way of
having safe operations with the use of current technologies such as big data and artificial
is frame a joint endeavor with outsider specialist organizations where the aggregate costs
engaged with executing the big data technology would be shared among the partners included.
Product
When attackers are lucky to gain access to an organization’s system, it is either using a loophole
in the system or by use of phishing using emails of the company or the employees of the
company. The attackers then work on the contrary by gaining access to the company data.
Attackers will use administrator tools and rights to control and manipulate the system in a
malicious way.
The use of F-Secure system Rapid Detection and Response application identifies all the
intrusions, endpoint attacks, networks, and any server attacks and use a cloud-based approach to
record real-time attacks and ways of mitigating the attacks (Fernandes, Soares, Gomes, Freire
and Inácio 147). The cloud-based technologies are vast and fast in detecting any system
abnormalities with the use of high-end technologies like big data, real-time, and reputational
analytics. The purpose of these technologies in combination with artificial intelligence detects
the known and unknown malicious system behaviors. The use of these different analytics
methods keeps the company system secure in such a way that all the attacks are detected even
those using different evasion tactics.
The Rapid Response application also offers organization on-site incident response facilities to
help bail out the company in times of difficulties and just in case the company Information
technology engineers are not on the ground.
The primary project objective is ensuring that we have a secure computer system in either home-
based or organizational context. Incorporation of security as a service is an excellent way of
having safe operations with the use of current technologies such as big data and artificial

Surname 9
intelligence. The design of incorporating cloud-based application meets the requirements of the
organization since all the current information technology solutions are in cloud-based platforms.
Team
Unlike the company own IT team, I would recommend an outsourced Personnel which is
available all round the clock to provide support and technical advice. With an external support
team, it means at any particular time the company will not be stuck and waiting for one person to
come to their aid, but anyone available will be able to help (Kopetz 52).
For the F-Secure system to operate as intended, there has to be a full constituted IT department
with support officers who are responsible for providing support and assistance with all the
computer hardware and software devices. The IT support will be on the lookout to help with the
operation and integration of the F-secure system. The companies looking forward to using the F-
Secure system will need strong internal system maintenance to ensure that the company does not
have any system malfunctioning before the adoption of the new security system (Giannone,
Domenico, Lucrezia and David 672). Ensure that the computer system does not have any other
software that may prevent the F-secure system from operating to full implementation. The team
should ensure that the company follows the instructions for installation and maintenance of the
system to avoid breach and enhance efficiency.
Business Model
The consideration was in the form of special operations. Initially, there was no primary emphasis
on the individual activities of the system. The only focus was on product development. There is
increased research in all the fields of business and not limited to only one area of business
specialization. I have incorporated the exotic security research to bring about a merge in
providing a secure system regarding both the hardware and the software deployed. The f-secure
intelligence. The design of incorporating cloud-based application meets the requirements of the
organization since all the current information technology solutions are in cloud-based platforms.
Team
Unlike the company own IT team, I would recommend an outsourced Personnel which is
available all round the clock to provide support and technical advice. With an external support
team, it means at any particular time the company will not be stuck and waiting for one person to
come to their aid, but anyone available will be able to help (Kopetz 52).
For the F-Secure system to operate as intended, there has to be a full constituted IT department
with support officers who are responsible for providing support and assistance with all the
computer hardware and software devices. The IT support will be on the lookout to help with the
operation and integration of the F-secure system. The companies looking forward to using the F-
Secure system will need strong internal system maintenance to ensure that the company does not
have any system malfunctioning before the adoption of the new security system (Giannone,
Domenico, Lucrezia and David 672). Ensure that the computer system does not have any other
software that may prevent the F-secure system from operating to full implementation. The team
should ensure that the company follows the instructions for installation and maintenance of the
system to avoid breach and enhance efficiency.
Business Model
The consideration was in the form of special operations. Initially, there was no primary emphasis
on the individual activities of the system. The only focus was on product development. There is
increased research in all the fields of business and not limited to only one area of business
specialization. I have incorporated the exotic security research to bring about a merge in
providing a secure system regarding both the hardware and the software deployed. The f-secure

Surname 10
system has henceforth increased the areas of study to provide an all-round solution for not only
business-oriented organizations but also for non-business-oriented organizations. In this regard
B2B will work best as the model of choice (Doganova and Marie 1563).
Research has not only concentrated on product development but also on the incorporation of
hardware and software features that can fully support security as a service. The building of
compatible software will ensure that the deployment of the security system is smooth and has a
sustainability factor.
The introduction of a new system in the organization brings about new challenges to
management. However, the management team for information technology and system support
should be much better equipped with the right training and skills to guide the rest of the
organization in achieving new dawn of the most secure system.
Competition
Distributed computing, Big Data technology and Business Analytics as innovations have upset
the manner in which transactions are being done. They are technologies which utilizes the
computational intensity of framework, stockpiling and joint effort to give benefits that meet
clients’ requests for satisfaction purposes Polidoro and Matt 1144). The analytics framework in
this situation speaks to the principle figuring components that help the business performance.
These components comprise of servers and centralized computer frameworks with the ability of
giving high analytics capability and limit over the big data access giving the market structure and
predictions.
The data analytics entails putting together all the activities somewhere in a database located in
the business premise or in the cloud. With this being bolstered by establishing offices with a
huge data processing capacity, for example a server farm, which is a part of the framework.
system has henceforth increased the areas of study to provide an all-round solution for not only
business-oriented organizations but also for non-business-oriented organizations. In this regard
B2B will work best as the model of choice (Doganova and Marie 1563).
Research has not only concentrated on product development but also on the incorporation of
hardware and software features that can fully support security as a service. The building of
compatible software will ensure that the deployment of the security system is smooth and has a
sustainability factor.
The introduction of a new system in the organization brings about new challenges to
management. However, the management team for information technology and system support
should be much better equipped with the right training and skills to guide the rest of the
organization in achieving new dawn of the most secure system.
Competition
Distributed computing, Big Data technology and Business Analytics as innovations have upset
the manner in which transactions are being done. They are technologies which utilizes the
computational intensity of framework, stockpiling and joint effort to give benefits that meet
clients’ requests for satisfaction purposes Polidoro and Matt 1144). The analytics framework in
this situation speaks to the principle figuring components that help the business performance.
These components comprise of servers and centralized computer frameworks with the ability of
giving high analytics capability and limit over the big data access giving the market structure and
predictions.
The data analytics entails putting together all the activities somewhere in a database located in
the business premise or in the cloud. With this being bolstered by establishing offices with a
huge data processing capacity, for example a server farm, which is a part of the framework.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
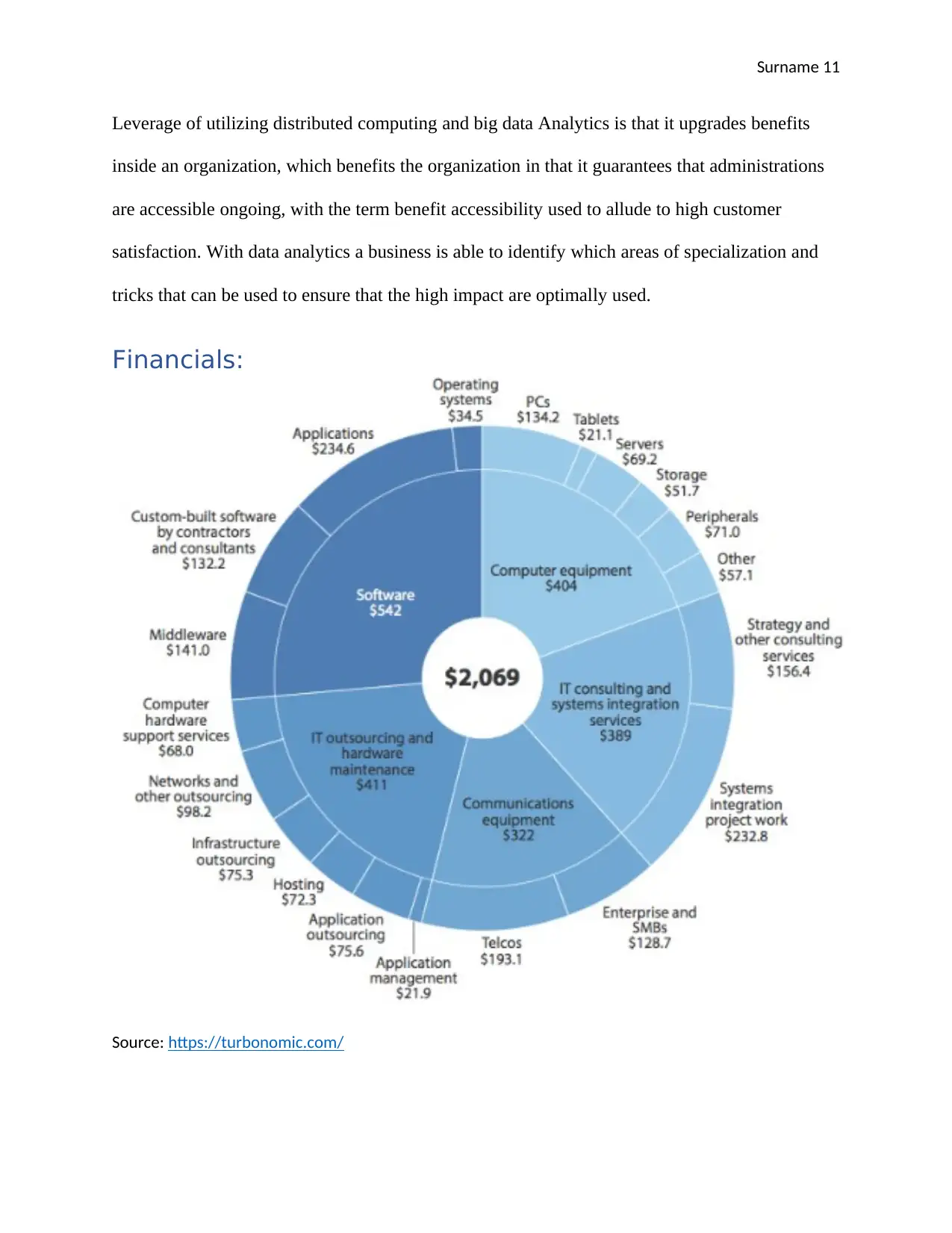
Surname 11
Leverage of utilizing distributed computing and big data Analytics is that it upgrades benefits
inside an organization, which benefits the organization in that it guarantees that administrations
are accessible ongoing, with the term benefit accessibility used to allude to high customer
satisfaction. With data analytics a business is able to identify which areas of specialization and
tricks that can be used to ensure that the high impact are optimally used.
Financials:
Source: https://turbonomic.com/
Leverage of utilizing distributed computing and big data Analytics is that it upgrades benefits
inside an organization, which benefits the organization in that it guarantees that administrations
are accessible ongoing, with the term benefit accessibility used to allude to high customer
satisfaction. With data analytics a business is able to identify which areas of specialization and
tricks that can be used to ensure that the high impact are optimally used.
Financials:
Source: https://turbonomic.com/

Surname 12
Works Cited
Benson, William E., et al. "Surgical management of macular holes: a report by the American
Academy of Ophthalmology." Ophthalmology 108.7 (2001): 1328-1335.
Doganova, Liliana, and Marie Eyquem-Renault. "What do business models do?: Innovation
devices in technology entrepreneurship." Research Policy 38.10 (2009): 1559-1570.
Fernandes, D. A., Soares, L. F., Gomes, J. V., Freire, M. M., & Inácio, P. R. "Security issues in
cloud environments: a survey." International Journal of Information Security 13.2
(2014): 113-170.
Giannone, Domenico, Lucrezia Reichlin, and David Small. "Nowcasting: The real-time
informational content of macroeconomic data." Journal of Monetary Economics 55.4
(2008): 665-676.
Kankanhalli, Atreyi. "An integrative study of information systems security
effectiveness." International journal of information management 23.2 (2003): 139-154.
Kopetz, Hermann. Real-time systems: design principles for distributed embedded applications.
Springer Science & Business Media, 2011.
Näslund, Dag. "Lean, six sigma and lean sigma: fads or real process improvement
methods?." Business Process Management Journal 14.3 (2008): 269-287.
Polidoro Jr, Francisco, and Matt Theeke. "Getting competition down to a science: The effects of
technological competition on firms' scientific publications." Organization Science 23.4
(2012): 1135-1153.
Siponen, Mikko, and Anthony Vance. "Neutralization: new insights into the problem of
employee information systems security policy violations." MIS quarterly (2010): 487-
502.
Works Cited
Benson, William E., et al. "Surgical management of macular holes: a report by the American
Academy of Ophthalmology." Ophthalmology 108.7 (2001): 1328-1335.
Doganova, Liliana, and Marie Eyquem-Renault. "What do business models do?: Innovation
devices in technology entrepreneurship." Research Policy 38.10 (2009): 1559-1570.
Fernandes, D. A., Soares, L. F., Gomes, J. V., Freire, M. M., & Inácio, P. R. "Security issues in
cloud environments: a survey." International Journal of Information Security 13.2
(2014): 113-170.
Giannone, Domenico, Lucrezia Reichlin, and David Small. "Nowcasting: The real-time
informational content of macroeconomic data." Journal of Monetary Economics 55.4
(2008): 665-676.
Kankanhalli, Atreyi. "An integrative study of information systems security
effectiveness." International journal of information management 23.2 (2003): 139-154.
Kopetz, Hermann. Real-time systems: design principles for distributed embedded applications.
Springer Science & Business Media, 2011.
Näslund, Dag. "Lean, six sigma and lean sigma: fads or real process improvement
methods?." Business Process Management Journal 14.3 (2008): 269-287.
Polidoro Jr, Francisco, and Matt Theeke. "Getting competition down to a science: The effects of
technological competition on firms' scientific publications." Organization Science 23.4
(2012): 1135-1153.
Siponen, Mikko, and Anthony Vance. "Neutralization: new insights into the problem of
employee information systems security policy violations." MIS quarterly (2010): 487-
502.
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





