Financial Fraud Detection and Prevention | Research
VerifiedAdded on 2022/08/18
|72
|17573
|15
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: FINANCIAL FRAUD DETECTION AND PREVENTION
Financial Fraud Detection and Prevention
Name of the Student
Name of the University
Author’s Note
Financial Fraud Detection and Prevention
Name of the Student
Name of the University
Author’s Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1FINANCIAL FRAUD DETECTION AND PREVENTION
Acknowledgement
I would like to thank my University and the professor for allowing me to contribute as well as
providing opportunity to complete my research despite of all challenges that I have faced. It will
not forget the efforts that are made by the professors and other for guiding me with patience,
guidance and understanding. I would not have completed this research without their guidance
and understanding and you are all special to me.
Acknowledgement
I would like to thank my University and the professor for allowing me to contribute as well as
providing opportunity to complete my research despite of all challenges that I have faced. It will
not forget the efforts that are made by the professors and other for guiding me with patience,
guidance and understanding. I would not have completed this research without their guidance
and understanding and you are all special to me.

2FINANCIAL FRAUD DETECTION AND PREVENTION
Abstract
The research is mainly focused on the financial fraud detection and prevention that are associated
with measures of prevention and detection techniques. The primary chapter is the introduction
which centres out the common data around the thought in conjunction with the company. The
targets of the research generally has been talked around in this allocate another to the research
limitations. Other than, it in development cements the research questions close to point and
targets of the research. Insides the second chapter, it contain of composing layout which centres
out the factors that are to be tended to insides the research. It join of openings and dangers
adjoining appraisal of competitive advantage and methodologies for moving forward the
execution. In chapter three, it highlights the procedure which centres out the strategies through
which the research has been conducted. It sets the considering, approach, and organize, data
collection procedure and test of the research about sheds light. The fourth chapter joins the
results around and disclosures where the results almost about are to be surveyed and checked on
as per the current circumstance which it highlights the looking over, assessment, openings,
threats and competitive methodology. Inside the final chapter, it bargains with the conclusion
nearby proposition and utilization with the concluding contemplations have been said at the side
tending to the objectives and certain recommendation. The proposal that have been illustrated
would offer help the company to administer with the threats and challenges that are going up
against in current circumstance.
Abstract
The research is mainly focused on the financial fraud detection and prevention that are associated
with measures of prevention and detection techniques. The primary chapter is the introduction
which centres out the common data around the thought in conjunction with the company. The
targets of the research generally has been talked around in this allocate another to the research
limitations. Other than, it in development cements the research questions close to point and
targets of the research. Insides the second chapter, it contain of composing layout which centres
out the factors that are to be tended to insides the research. It join of openings and dangers
adjoining appraisal of competitive advantage and methodologies for moving forward the
execution. In chapter three, it highlights the procedure which centres out the strategies through
which the research has been conducted. It sets the considering, approach, and organize, data
collection procedure and test of the research about sheds light. The fourth chapter joins the
results around and disclosures where the results almost about are to be surveyed and checked on
as per the current circumstance which it highlights the looking over, assessment, openings,
threats and competitive methodology. Inside the final chapter, it bargains with the conclusion
nearby proposition and utilization with the concluding contemplations have been said at the side
tending to the objectives and certain recommendation. The proposal that have been illustrated
would offer help the company to administer with the threats and challenges that are going up
against in current circumstance.

3FINANCIAL FRAUD DETECTION AND PREVENTION
Table of Contents
Chapter 1: Introduction....................................................................................................................5
1.1 Background of the study........................................................................................................6
1.2 Problem statement.................................................................................................................7
1.3 Aims and Objectives..............................................................................................................8
1.4 Research Questions................................................................................................................9
1.5 Scope of the research.............................................................................................................9
Chapter 2: Literature Review.........................................................................................................11
2.1 Concept of financial fraud...................................................................................................11
2.2 Impact of financial fraud.....................................................................................................14
2.3 Prevention strategies of financial frauds..............................................................................17
Chapter 3: Research Methodology................................................................................................22
3.1 Research Onion....................................................................................................................22
3.2 Research Philosophy............................................................................................................23
3.3 Research Approach..............................................................................................................24
3.4 Research Design..................................................................................................................24
3.5 Data Collection Process.......................................................................................................25
3.6 Sampling method and sampling size...................................................................................25
3.7 Ethical Consideration...........................................................................................................26
Table of Contents
Chapter 1: Introduction....................................................................................................................5
1.1 Background of the study........................................................................................................6
1.2 Problem statement.................................................................................................................7
1.3 Aims and Objectives..............................................................................................................8
1.4 Research Questions................................................................................................................9
1.5 Scope of the research.............................................................................................................9
Chapter 2: Literature Review.........................................................................................................11
2.1 Concept of financial fraud...................................................................................................11
2.2 Impact of financial fraud.....................................................................................................14
2.3 Prevention strategies of financial frauds..............................................................................17
Chapter 3: Research Methodology................................................................................................22
3.1 Research Onion....................................................................................................................22
3.2 Research Philosophy............................................................................................................23
3.3 Research Approach..............................................................................................................24
3.4 Research Design..................................................................................................................24
3.5 Data Collection Process.......................................................................................................25
3.6 Sampling method and sampling size...................................................................................25
3.7 Ethical Consideration...........................................................................................................26
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4FINANCIAL FRAUD DETECTION AND PREVENTION
3.8 Summary..............................................................................................................................26
Chapter 4: Result and Analysis......................................................................................................28
Quantitative research.................................................................................................................28
Chapter 5: Discussions..................................................................................................................48
Chapter 6: Conclusion and Recommendation...............................................................................53
References and Bibliography.........................................................................................................60
Appendices....................................................................................................................................68
3.8 Summary..............................................................................................................................26
Chapter 4: Result and Analysis......................................................................................................28
Quantitative research.................................................................................................................28
Chapter 5: Discussions..................................................................................................................48
Chapter 6: Conclusion and Recommendation...............................................................................53
References and Bibliography.........................................................................................................60
Appendices....................................................................................................................................68

5FINANCIAL FRAUD DETECTION AND PREVENTION
Chapter 1: Introduction
Financial fraud detection and prevention is the procedure by which the both finances, as
well as the financial information are detected from being a fraud. Looking at the historical data
over the records which mainly stops the fraudulent activities that are associated with the business
(Olukowade and Balogun 2015). In the current world of advanced technologies, financial frauds
take place at most of the places along with its impact on the individual and organisations. In
recent years, the organisations are installed with certain fraud detection techniques which would
automatically detect the fraudulent activities that are going to take place. The automated fraud
management solution are also helpful which points out the unusual patters which are consist in
noticing the fraudulent activities and freezing the transaction before it actually takes place
(Othman et al. 2015). The fraudulent activities have special running methods which is almost
similar to genuine process but certain aspects is required to be considered for their identification.
The challenges that are faced in recent years are required to be controlled as most of the
transaction that takes place are fully automated which do not any person for its overall
verification. The sheer volume of data that are generally processed in the real time are required
to be enhanced with fraud detection techniques (Imam, Kumshe and Jajere 2015). The solution
for managing the tasks are required to be included with transaction that takes place in that period
of time.
In current world of technological advancement, there are different procedures which are
capable of mitigating the frauds and preventing them from taking place. The art of technology
can capture the nature of the frauds along with their fraudulent activities (Joseph, Albert and
Byaruhanga 2015). The transaction that takes place in recent years consist of several dollars that
are directly included with the method. The overall review of the customers for the transaction
Chapter 1: Introduction
Financial fraud detection and prevention is the procedure by which the both finances, as
well as the financial information are detected from being a fraud. Looking at the historical data
over the records which mainly stops the fraudulent activities that are associated with the business
(Olukowade and Balogun 2015). In the current world of advanced technologies, financial frauds
take place at most of the places along with its impact on the individual and organisations. In
recent years, the organisations are installed with certain fraud detection techniques which would
automatically detect the fraudulent activities that are going to take place. The automated fraud
management solution are also helpful which points out the unusual patters which are consist in
noticing the fraudulent activities and freezing the transaction before it actually takes place
(Othman et al. 2015). The fraudulent activities have special running methods which is almost
similar to genuine process but certain aspects is required to be considered for their identification.
The challenges that are faced in recent years are required to be controlled as most of the
transaction that takes place are fully automated which do not any person for its overall
verification. The sheer volume of data that are generally processed in the real time are required
to be enhanced with fraud detection techniques (Imam, Kumshe and Jajere 2015). The solution
for managing the tasks are required to be included with transaction that takes place in that period
of time.
In current world of technological advancement, there are different procedures which are
capable of mitigating the frauds and preventing them from taking place. The art of technology
can capture the nature of the frauds along with their fraudulent activities (Joseph, Albert and
Byaruhanga 2015). The transaction that takes place in recent years consist of several dollars that
are directly included with the method. The overall review of the customers for the transaction

6FINANCIAL FRAUD DETECTION AND PREVENTION
that has already taken place also points out the process of detection of frauds and preventing it as
much as possible. The patters of the financial frauds that takes place includes different aspects
that are required to be considered for the overall activities (Herawati 2015). The inclusion of
location, size and the overall frequency of the transaction are required to be considered for
detecting the frauds. More sophisticated metrics are required to be used for presenting the
financial frauds that includes the history of profiles of the customers (Enofe, Omagbon and
Ehigiator 2015). The list of the suspects are required to be kept in a safe place on which the
required is also to be reviewed as per the overall nature of the fraud along with its detection
techniques.
1.1 Background of the study
The research mainly highlights the financial frauds detection and prevention in which the
methods and the techniques have been discussed. It also includes the uniqueness of the fraud
detection techniques along with the prevention methods that are useful in mitigating the financial
loss (Zamzami, Nusa and Timur 2016). The research also sheds the light on the financial frauds
that mainly takes in place in recent world with implementation of advanced technologies which
would be helpful in preventing the financial frauds. The list of the suspect behaviour is required
to be kept which would combined to all of the issues that have been faced by the organisations
(Simha and Satyanarayan 2016). The database of the query for each of the transactions mainly
points out the detection of frauds which is required to be enables with the prevention system and
that have to be associated with faster process of massive amount of data (West and Bhattacharya
2016). The various sources of database is also required to be highlighted which includes the real
time solutions with batch data integration along with out of the box scenario for faster alerts.
that has already taken place also points out the process of detection of frauds and preventing it as
much as possible. The patters of the financial frauds that takes place includes different aspects
that are required to be considered for the overall activities (Herawati 2015). The inclusion of
location, size and the overall frequency of the transaction are required to be considered for
detecting the frauds. More sophisticated metrics are required to be used for presenting the
financial frauds that includes the history of profiles of the customers (Enofe, Omagbon and
Ehigiator 2015). The list of the suspects are required to be kept in a safe place on which the
required is also to be reviewed as per the overall nature of the fraud along with its detection
techniques.
1.1 Background of the study
The research mainly highlights the financial frauds detection and prevention in which the
methods and the techniques have been discussed. It also includes the uniqueness of the fraud
detection techniques along with the prevention methods that are useful in mitigating the financial
loss (Zamzami, Nusa and Timur 2016). The research also sheds the light on the financial frauds
that mainly takes in place in recent world with implementation of advanced technologies which
would be helpful in preventing the financial frauds. The list of the suspect behaviour is required
to be kept which would combined to all of the issues that have been faced by the organisations
(Simha and Satyanarayan 2016). The database of the query for each of the transactions mainly
points out the detection of frauds which is required to be enables with the prevention system and
that have to be associated with faster process of massive amount of data (West and Bhattacharya
2016). The various sources of database is also required to be highlighted which includes the real
time solutions with batch data integration along with out of the box scenario for faster alerts.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7FINANCIAL FRAUD DETECTION AND PREVENTION
The prevention of fraud is the technology that are required to be made with enormous
stride from the process of advanced computing and other form of machine learning. The forms of
artificial intelligence touches the every areas of live which are required to be raised with prices
and payment of goods and services (Mangala and Kumari 2015). In this case, the financial fraud
might happen which are required to be associated with the cost of the transactions that has
already taken place. The waste and abuse of improper payments is mainly referred as the fraud
which is also fragmented with the prevention with using of the rules. The different set of data is
also responsible for cross referencing the conventional tactics that are required to be associated
with the method of fraud detection (Bănărescu 2015). The overall development of the new
technologies are more inclined towards the frauds that are occurred in the organisations in real
time. The process of prevention of fraud is more like pay and chase which are required to be
traced and detected at a correct time. The complexities that have grown in the recent world are
mainly the state sponsored terrorism that are required to be included with the professional
criminals (McMahon et al. 2016). These criminals are expert in making financial frauds and that
particular fraud is required to be detected and prevented as early as possible. The comprehensive
approach of matching of data along with the activities that are associated with the fraud detection
is to be identified. The abnormal nature of the activities mainly refers to the frauds that points out
the sophisticated tactics which would be useful in digital event of data (Gbegi and Adebisi 2015).
Any kind of changes in the overall approaches also highlights the authentication, access,
location, devices and others.
1.2 Problem statement
The problem that is associated with the research mainly lies in the context itself which
mainly points out the fraudulent activities. The fraudulent activities are required to be stopped
The prevention of fraud is the technology that are required to be made with enormous
stride from the process of advanced computing and other form of machine learning. The forms of
artificial intelligence touches the every areas of live which are required to be raised with prices
and payment of goods and services (Mangala and Kumari 2015). In this case, the financial fraud
might happen which are required to be associated with the cost of the transactions that has
already taken place. The waste and abuse of improper payments is mainly referred as the fraud
which is also fragmented with the prevention with using of the rules. The different set of data is
also responsible for cross referencing the conventional tactics that are required to be associated
with the method of fraud detection (Bănărescu 2015). The overall development of the new
technologies are more inclined towards the frauds that are occurred in the organisations in real
time. The process of prevention of fraud is more like pay and chase which are required to be
traced and detected at a correct time. The complexities that have grown in the recent world are
mainly the state sponsored terrorism that are required to be included with the professional
criminals (McMahon et al. 2016). These criminals are expert in making financial frauds and that
particular fraud is required to be detected and prevented as early as possible. The comprehensive
approach of matching of data along with the activities that are associated with the fraud detection
is to be identified. The abnormal nature of the activities mainly refers to the frauds that points out
the sophisticated tactics which would be useful in digital event of data (Gbegi and Adebisi 2015).
Any kind of changes in the overall approaches also highlights the authentication, access,
location, devices and others.
1.2 Problem statement
The problem that is associated with the research mainly lies in the context itself which
mainly points out the fraudulent activities. The fraudulent activities are required to be stopped

8FINANCIAL FRAUD DETECTION AND PREVENTION
which mainly includes the identification procedures and accurately measuring the overall
experiences (Wong and Venkatraman 2015). The development of the sophisticated tactics as it
might help in changing the approaches for the total system of financial transaction. There are
certain steps that are required to be captured within the organisation along with improving the
experiences of individual as well as of the organisations. The steps are mainly mentioned in the
following part. The primary step is to capture the data that are available in nature from different
departments and includes them in the process of analysis (Kulikova and Satdarova 2016). The
monitoring of the transaction in a continuous manner also points out in the social networks that
are high risk in nature. The culture of enterprise wide is required to be installed by the process of
data visualisation along with investigating the optimisation of workflow. The security technique
is also to be introduced with different layered as it would help in preventing the financial frauds
by use of the technology.
1.3 Aims and Objectives
The aims and objectives of the study is to point out the factors that affects the financial
frauds detection and prevention along with providing with better benefits and solution for the
issues.
The aims and objectives of the study has been mentioned and discussed in the part below.
The main aim of the study is to highlight the financial fraud detection along with its
preventive measures which would be beneficial for the company. The fraudulent exercises have
uncommon running strategies which is nearly comparative to veritable handle but certain
perspectives is required to be considered for their identification (KABUE and ADUDA 2017).
The challenges that are confronted in later a long time are required to be controlled as most of
the exchange that takes put are completely mechanized which do not any individual for its
which mainly includes the identification procedures and accurately measuring the overall
experiences (Wong and Venkatraman 2015). The development of the sophisticated tactics as it
might help in changing the approaches for the total system of financial transaction. There are
certain steps that are required to be captured within the organisation along with improving the
experiences of individual as well as of the organisations. The steps are mainly mentioned in the
following part. The primary step is to capture the data that are available in nature from different
departments and includes them in the process of analysis (Kulikova and Satdarova 2016). The
monitoring of the transaction in a continuous manner also points out in the social networks that
are high risk in nature. The culture of enterprise wide is required to be installed by the process of
data visualisation along with investigating the optimisation of workflow. The security technique
is also to be introduced with different layered as it would help in preventing the financial frauds
by use of the technology.
1.3 Aims and Objectives
The aims and objectives of the study is to point out the factors that affects the financial
frauds detection and prevention along with providing with better benefits and solution for the
issues.
The aims and objectives of the study has been mentioned and discussed in the part below.
The main aim of the study is to highlight the financial fraud detection along with its
preventive measures which would be beneficial for the company. The fraudulent exercises have
uncommon running strategies which is nearly comparative to veritable handle but certain
perspectives is required to be considered for their identification (KABUE and ADUDA 2017).
The challenges that are confronted in later a long time are required to be controlled as most of
the exchange that takes put are completely mechanized which do not any individual for its

9FINANCIAL FRAUD DETECTION AND PREVENTION
generally confirmation. The sheer volume of information that are generally prepared within the
genuine time are required to be upgraded with extortion location methods. The arrangement for
overseeing the errands are required to be included with exchange that takes put in that period of
time. In later a long time, the associations are introduced with certain extortion location
procedures which would automatically detect the false exercises that are reaching to take put
(Abdallah, Maarof and Zainal 2016). The mechanized extortion administration arrangement are
too accommodating which focuses out the abnormal patters which are comprise in taking note
the false exercises and solidifying the exchange some time recently it really takes place. Looking
at the authentic information over the records which primarily stops the false exercises that are
related with the commerce. Within the current world of progressed innovations, budgetary frauds
take put at most of the places beside its effect on the person and associations.
1.4 Research Questions
The following are the research questions which has been gathered from different sources
about the financial fraud detection and prevention.
1. What are the impact of financial fraud on an organisation?
2. What are the detection procedures by which financial frauds can be detected?
3. What are preventive measures for financial frauds?
1.5 Scope of the research
The research is totally based on financial fraud detection and prevention and that have
been considered in the overall study. The patters of the financial frauds that takes put
incorporates diverse perspectives that are required to be considered for the generally exercises.
The consideration of area, estimate and the in general recurrence of the exchange are required to
generally confirmation. The sheer volume of information that are generally prepared within the
genuine time are required to be upgraded with extortion location methods. The arrangement for
overseeing the errands are required to be included with exchange that takes put in that period of
time. In later a long time, the associations are introduced with certain extortion location
procedures which would automatically detect the false exercises that are reaching to take put
(Abdallah, Maarof and Zainal 2016). The mechanized extortion administration arrangement are
too accommodating which focuses out the abnormal patters which are comprise in taking note
the false exercises and solidifying the exchange some time recently it really takes place. Looking
at the authentic information over the records which primarily stops the false exercises that are
related with the commerce. Within the current world of progressed innovations, budgetary frauds
take put at most of the places beside its effect on the person and associations.
1.4 Research Questions
The following are the research questions which has been gathered from different sources
about the financial fraud detection and prevention.
1. What are the impact of financial fraud on an organisation?
2. What are the detection procedures by which financial frauds can be detected?
3. What are preventive measures for financial frauds?
1.5 Scope of the research
The research is totally based on financial fraud detection and prevention and that have
been considered in the overall study. The patters of the financial frauds that takes put
incorporates diverse perspectives that are required to be considered for the generally exercises.
The consideration of area, estimate and the in general recurrence of the exchange are required to
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10FINANCIAL FRAUD DETECTION AND PREVENTION
be considered for identifying the frauds. More advanced measurements are required to be utilized
for showing the monetary frauds that incorporates the history of profiles of the clients (Mansor
2015). The list of the suspects are required to be kept in a secure put on which the specified is
additionally to be reviewed as per the by and large nature of the extortion together with its
location procedures. The exchange that takes put in later a long time comprise of a few dollars
that are specifically included with the method. The generally survey of the clients for the
exchange that has as of now taken put too focuses out the method of location of frauds and
anticipating it as much as conceivable (Lin et al. 2015). In current world of innovative
progression, there are distinctive methods which are competent of relieving the frauds and
avoiding them from taking put. The craftsmanship of innovation can capture the nature of the
frauds together with their fraudulent exercises.
be considered for identifying the frauds. More advanced measurements are required to be utilized
for showing the monetary frauds that incorporates the history of profiles of the clients (Mansor
2015). The list of the suspects are required to be kept in a secure put on which the specified is
additionally to be reviewed as per the by and large nature of the extortion together with its
location procedures. The exchange that takes put in later a long time comprise of a few dollars
that are specifically included with the method. The generally survey of the clients for the
exchange that has as of now taken put too focuses out the method of location of frauds and
anticipating it as much as conceivable (Lin et al. 2015). In current world of innovative
progression, there are distinctive methods which are competent of relieving the frauds and
avoiding them from taking put. The craftsmanship of innovation can capture the nature of the
frauds together with their fraudulent exercises.

11FINANCIAL FRAUD DETECTION AND PREVENTION
Chapter 2: Literature Review
This chapter mainly focused on the review of the overall literature that are included in the
research. It includes the overall concept of the topic on the research and the strategies that would
be useful for mitigating the issue. Moreover, it also deals with the impact that might affect the
event over the time and how it would also points out the benefits as well as the limitations of the
strategies.
2.1 Concept of financial fraud
The concept of financial fraud is the event where someone takes the money and other
assets from another people by the process of deception along with other criminal activity. The
detection and prevention of fraud is totally associated with certain perspective that would
beneficial for the organisation and the individuals (Sadgali, Sael and Benabbou 2019). The
overall concept of the financial fraud are associated with finances that includes money and other
form of assets which would be beneficial for their current period of time. The process of
detection and includes the technologies which would be helpful for the organisation and their
arrangement on the complex data form (Liu et al. 2015). There are different types of financial
frauds that are currently occurring in the modern world. Identity fraud is one of the common
financial fraud that takes place in most of the cases. It mainly points out to an individual who
impersonates other people and uses their secure personal information for stealing money. This
kind of activity is mainly referred to the financial fraud of identity which would be effectively
identified (Mallika 2017). This particular type of fraud mainly takes place on the field of internet
as all of the personal information are readily available on the internet. Phishing is also another
type of fraudulent activities that points out the methods of internet banking and that would be
useful for receiving the transaction details. The clients of internet banking receives the email
Chapter 2: Literature Review
This chapter mainly focused on the review of the overall literature that are included in the
research. It includes the overall concept of the topic on the research and the strategies that would
be useful for mitigating the issue. Moreover, it also deals with the impact that might affect the
event over the time and how it would also points out the benefits as well as the limitations of the
strategies.
2.1 Concept of financial fraud
The concept of financial fraud is the event where someone takes the money and other
assets from another people by the process of deception along with other criminal activity. The
detection and prevention of fraud is totally associated with certain perspective that would
beneficial for the organisation and the individuals (Sadgali, Sael and Benabbou 2019). The
overall concept of the financial fraud are associated with finances that includes money and other
form of assets which would be beneficial for their current period of time. The process of
detection and includes the technologies which would be helpful for the organisation and their
arrangement on the complex data form (Liu et al. 2015). There are different types of financial
frauds that are currently occurring in the modern world. Identity fraud is one of the common
financial fraud that takes place in most of the cases. It mainly points out to an individual who
impersonates other people and uses their secure personal information for stealing money. This
kind of activity is mainly referred to the financial fraud of identity which would be effectively
identified (Mallika 2017). This particular type of fraud mainly takes place on the field of internet
as all of the personal information are readily available on the internet. Phishing is also another
type of fraudulent activities that points out the methods of internet banking and that would be
useful for receiving the transaction details. The clients of internet banking receives the email

12FINANCIAL FRAUD DETECTION AND PREVENTION
which mainly asks for the account details such as their account number, password and personal
details (Hamdan 2018). These information are useful for withdrawing money from the account
and performing the fraudulent activities.
Card fraud is also another type of fraud which points out the financial fraudulent
activities which includes the effective type of financial fraudulent activities. At the initial level
the card of the bank is to be stolen which points out the cards that are usable (Bhardwaj and
Gupta 2016). The fraudulent activities makes different kinds of unauthorised purchases which
are not notified by the bank. In addition to this, skimming is the type of process which involves
the process of stealing the information that highlights the extraction of the information from the
bank cards that might be both credit card and debit card (Dong, Liao and Zhang 2018). The
stealing of information from the bank card at the time of legitimate transaction also points out the
skimming if information which drags the attention of the users. The process of swiping of cards
mainly points out the using of the electronic devices that functions on the wedge and the
skimming devices along with recording of information that contains on the magnetic strip (Dong,
Liao and Zhang 2018). This can be stopped with the process of stopping the online transaction
which mainly uses the card for the purchase. Moreover, the counterfeit cards are also used for
matching the transaction that are associated with the finances. The fraudulent activities are also
performed by the process of fund transfer where the individual is being asked to transfer certain
amount of money for receiving certain amount of commission. This kind of activity is a type of
financial fraud which is required to be detected and prevented.
The list of the suspect conduct is required to be kept which would combined to all of the
issues that have been confronted by the associations. The database of the inquiry for each of the
exchanges basically focuses out the location of frauds which is required to be empowers with the
which mainly asks for the account details such as their account number, password and personal
details (Hamdan 2018). These information are useful for withdrawing money from the account
and performing the fraudulent activities.
Card fraud is also another type of fraud which points out the financial fraudulent
activities which includes the effective type of financial fraudulent activities. At the initial level
the card of the bank is to be stolen which points out the cards that are usable (Bhardwaj and
Gupta 2016). The fraudulent activities makes different kinds of unauthorised purchases which
are not notified by the bank. In addition to this, skimming is the type of process which involves
the process of stealing the information that highlights the extraction of the information from the
bank cards that might be both credit card and debit card (Dong, Liao and Zhang 2018). The
stealing of information from the bank card at the time of legitimate transaction also points out the
skimming if information which drags the attention of the users. The process of swiping of cards
mainly points out the using of the electronic devices that functions on the wedge and the
skimming devices along with recording of information that contains on the magnetic strip (Dong,
Liao and Zhang 2018). This can be stopped with the process of stopping the online transaction
which mainly uses the card for the purchase. Moreover, the counterfeit cards are also used for
matching the transaction that are associated with the finances. The fraudulent activities are also
performed by the process of fund transfer where the individual is being asked to transfer certain
amount of money for receiving certain amount of commission. This kind of activity is a type of
financial fraud which is required to be detected and prevented.
The list of the suspect conduct is required to be kept which would combined to all of the
issues that have been confronted by the associations. The database of the inquiry for each of the
exchanges basically focuses out the location of frauds which is required to be empowers with the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

13FINANCIAL FRAUD DETECTION AND PREVENTION
anticipation framework which ought to be related with faster handle of enormous sum of
information (Huang et al. 2017). The different sources of database is additionally required to be
highlighted which incorporates the genuine time arrangements with bunch information
integration at the side out of the box situation for quicker cautions. It moreover incorporates the
uniqueness of the extortion location strategies alongside the anticipation strategies that are
valuable in moderating the monetary loss (Shi, Connelly and Hoskisson 2017). The inquire about
moreover sheds the light on the budgetary frauds that basically takes in put in later world with
usage of progressed innovations which would be supportive in anticipating the budgetary frauds.
The list of the suspect conduct is required to be kept which would combined for all of the
mentioned issues. The in general improvement of the new technologies are more slanted towards
the frauds that are happened within the organisations in genuine time (Klein 2015). The method
of anticipation of extortion is more like pay and chase which are required to be followed and
recognized at a correct time. The complexities that have developed within the later world are
primarily the state supported terrorism that are required to be included with the proficient
criminals. These offenders are master in making budgetary frauds which specific fraud is
required to be detected and anticipated as early as conceivable.
The comprehensive approach of coordinating of information together with the exercises
that are related with the extortion discovery is to be recognized (Umar, Samsudin and Mohamed
2016). The anomalous nature of the activities mainly alludes to the frauds that focuses out the
modern strategies which would be valuable in advanced occasion of information. Any kind of
changes within the generally approaches moreover highlights the verification, get to, area,
devices and others (Shimpi and Kadroli 2015). The avoidance of fraud is the innovation that are
required to be made with gigantic walk from the method of progressed computing and other
anticipation framework which ought to be related with faster handle of enormous sum of
information (Huang et al. 2017). The different sources of database is additionally required to be
highlighted which incorporates the genuine time arrangements with bunch information
integration at the side out of the box situation for quicker cautions. It moreover incorporates the
uniqueness of the extortion location strategies alongside the anticipation strategies that are
valuable in moderating the monetary loss (Shi, Connelly and Hoskisson 2017). The inquire about
moreover sheds the light on the budgetary frauds that basically takes in put in later world with
usage of progressed innovations which would be supportive in anticipating the budgetary frauds.
The list of the suspect conduct is required to be kept which would combined for all of the
mentioned issues. The in general improvement of the new technologies are more slanted towards
the frauds that are happened within the organisations in genuine time (Klein 2015). The method
of anticipation of extortion is more like pay and chase which are required to be followed and
recognized at a correct time. The complexities that have developed within the later world are
primarily the state supported terrorism that are required to be included with the proficient
criminals. These offenders are master in making budgetary frauds which specific fraud is
required to be detected and anticipated as early as conceivable.
The comprehensive approach of coordinating of information together with the exercises
that are related with the extortion discovery is to be recognized (Umar, Samsudin and Mohamed
2016). The anomalous nature of the activities mainly alludes to the frauds that focuses out the
modern strategies which would be valuable in advanced occasion of information. Any kind of
changes within the generally approaches moreover highlights the verification, get to, area,
devices and others (Shimpi and Kadroli 2015). The avoidance of fraud is the innovation that are
required to be made with gigantic walk from the method of progressed computing and other

14FINANCIAL FRAUD DETECTION AND PREVENTION
frame of machine learning. The shapes of counterfeit insights touches the each ranges of live
which are required to be raised with costs and instalment of products and administrations. In this
case, the financial fraud might happen which are required to be related with the fetched of the
exchanges that has as of now taken into consideration (Siering et al. 2017). The waste and
mishandle of inappropriate instalments is basically alluded as the extortion which is additionally
divided with the avoidance with utilizing of the rules. The diverse set of information is
additionally dependable for cross referencing the customary strategies that are required to be
related with the strategy of fraud location.
2.2 Impact of financial fraud
The impact of financial fraud is required to be highlighted on the business activities as
these help the companies to for defending against it. The attention on the financial frauds also
highlights the results that are quite alarming and that have to be targeted for the overall attempt
of financial fraud (Khan 2015). One of the key issues in a business is financial fraud that is
required to be highlighted by using different strategies. The companies that are suffering from
loss also included in the around 36 % of total profit. Despite of the risk, there are huge number of
business that fails for reviewing their financial frauds that take place in their business activities.
The appointed finance professionals have not reviewed the process of financial fraud in last few
years. It can also be seen that 18 % of the firms have never updated their financial statement for
detecting the financial frauds (Rahman and Iverson 2015). Fraudsters are pretty impressive on
the hit rate that are going to be the major slugger which might impact on the business. Other
authors have mentioned that, one out of six people are not aware that they are targeted for some
kind of fraudulent activities. The attempt to defraud the companies is to be prevalent and that is
required to be considered by the management (Singh and Singh 2015). The process of fraud
frame of machine learning. The shapes of counterfeit insights touches the each ranges of live
which are required to be raised with costs and instalment of products and administrations. In this
case, the financial fraud might happen which are required to be related with the fetched of the
exchanges that has as of now taken into consideration (Siering et al. 2017). The waste and
mishandle of inappropriate instalments is basically alluded as the extortion which is additionally
divided with the avoidance with utilizing of the rules. The diverse set of information is
additionally dependable for cross referencing the customary strategies that are required to be
related with the strategy of fraud location.
2.2 Impact of financial fraud
The impact of financial fraud is required to be highlighted on the business activities as
these help the companies to for defending against it. The attention on the financial frauds also
highlights the results that are quite alarming and that have to be targeted for the overall attempt
of financial fraud (Khan 2015). One of the key issues in a business is financial fraud that is
required to be highlighted by using different strategies. The companies that are suffering from
loss also included in the around 36 % of total profit. Despite of the risk, there are huge number of
business that fails for reviewing their financial frauds that take place in their business activities.
The appointed finance professionals have not reviewed the process of financial fraud in last few
years. It can also be seen that 18 % of the firms have never updated their financial statement for
detecting the financial frauds (Rahman and Iverson 2015). Fraudsters are pretty impressive on
the hit rate that are going to be the major slugger which might impact on the business. Other
authors have mentioned that, one out of six people are not aware that they are targeted for some
kind of fraudulent activities. The attempt to defraud the companies is to be prevalent and that is
required to be considered by the management (Singh and Singh 2015). The process of fraud

15FINANCIAL FRAUD DETECTION AND PREVENTION
prevention would be huge concern for the department of finance as it deals with monetary
transactions. The companies are required to review the process of fraud prevention and that are
required to be associated with the same financial year. The information are to be perspective and
that are required to be associated with the processes on the effective source of fraudulent
activities. There are around 130000 medium to large companies and the activities have been
segregated (Ahmed, Mahmood and Islam 2016). Out of the 130000 companies 98000 have been
directly targeted for successful attempt of financial fraud and 37500 are identified as the victim
of financial fraud. 7000 companies have been targeted for the execution of financial fraud and
have not a single idea about the loss that are incurred by the companies (Abu-Shanab and
Matalqa 2015). In addition to this, 45000 companies have successfully implemented the fraud
prevention policy for the current year. It can also be seen that 22000 companies have never
updated their overall process of fraud prevention along with the policies.
Fraudsters are pretty noteworthy on the hit rate that are progressing to be the major
slugger which might effect on the trade. Other creators have said that, one out of six individuals
are not mindful that they are focused on for a few kind of fraudulent exercises (Drogalas et al.
2017). The attempt to dupe the companies is to be predominant which is required to be
considered by the administration. The method of extortion avoidance would be tremendous
concern for the department of back because it bargains with financial transactions. The
companies are required to survey the method of extortion anticipation which are required to be
related with the same financial year (Ehioghiren and Atu 2016). The data are to be viewpoint
which are required to be related with the forms on the successful source of fraudulent exercises.
There are around 130000 medium to expansive companies and the exercises have been isolated.
The effect of financial fraud is required to be highlighted on the trade exercises as these offer
prevention would be huge concern for the department of finance as it deals with monetary
transactions. The companies are required to review the process of fraud prevention and that are
required to be associated with the same financial year. The information are to be perspective and
that are required to be associated with the processes on the effective source of fraudulent
activities. There are around 130000 medium to large companies and the activities have been
segregated (Ahmed, Mahmood and Islam 2016). Out of the 130000 companies 98000 have been
directly targeted for successful attempt of financial fraud and 37500 are identified as the victim
of financial fraud. 7000 companies have been targeted for the execution of financial fraud and
have not a single idea about the loss that are incurred by the companies (Abu-Shanab and
Matalqa 2015). In addition to this, 45000 companies have successfully implemented the fraud
prevention policy for the current year. It can also be seen that 22000 companies have never
updated their overall process of fraud prevention along with the policies.
Fraudsters are pretty noteworthy on the hit rate that are progressing to be the major
slugger which might effect on the trade. Other creators have said that, one out of six individuals
are not mindful that they are focused on for a few kind of fraudulent exercises (Drogalas et al.
2017). The attempt to dupe the companies is to be predominant which is required to be
considered by the administration. The method of extortion avoidance would be tremendous
concern for the department of back because it bargains with financial transactions. The
companies are required to survey the method of extortion anticipation which are required to be
related with the same financial year (Ehioghiren and Atu 2016). The data are to be viewpoint
which are required to be related with the forms on the successful source of fraudulent exercises.
There are around 130000 medium to expansive companies and the exercises have been isolated.
The effect of financial fraud is required to be highlighted on the trade exercises as these offer
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

16FINANCIAL FRAUD DETECTION AND PREVENTION
assistance the companies to for guarding against it. The consideration on the budgetary frauds
moreover highlights the outcomes about that are very disturbing which need to be focused on for
the in general endeavour of financial fraud (Aduwo 2016). One of the key issues in a commerce
is monetary extortion that is required to be highlighted by utilizing diverse procedures. The
companies that are enduring from loss moreover included within the around 36 % of add up to
benefit. In spite of the hazard, there are colossal number of trade that fails for checking on their
budgetary frauds that take put in their trade exercises. The designated back experts have not
checked on the method of financial fraud in final years (Dutta, Dutta and Raahemin 2017). It can
also be seen that 18 % of the firms have never upgraded their financial statement for identifying
the financial frauds.
The fraudulent exercises are required to be halted which basically incorporates the
recognizable proof methods and precisely measuring the generally encounters. The advancement
of the advanced strategies because it might offer assistance in changing the approaches for the
overall framework of financial transaction (Olukowade and Balogun 2015). There are certain
steps that are required to be captured inside the association together with moving forward the
encounters of person as well as of the associations. The steps are basically said within the taking
after portion. The essential step is to capture the information that are accessible in nature from
distinctive offices and incorporates them within the preparation of analysis. The observing of the
transaction in a nonstop way also points out within the social systems that are tall chance in
nature (Imam, Kumshe and Jajere 2015). The culture of endeavour wide is required to be
introduced by the method of information representation besides exploring the enhancement of
workflow. The stealing of data from the bank card at the time of true blue exchange moreover
focuses out the skimming on the off chance that data which drags the consideration of the clients
assistance the companies to for guarding against it. The consideration on the budgetary frauds
moreover highlights the outcomes about that are very disturbing which need to be focused on for
the in general endeavour of financial fraud (Aduwo 2016). One of the key issues in a commerce
is monetary extortion that is required to be highlighted by utilizing diverse procedures. The
companies that are enduring from loss moreover included within the around 36 % of add up to
benefit. In spite of the hazard, there are colossal number of trade that fails for checking on their
budgetary frauds that take put in their trade exercises. The designated back experts have not
checked on the method of financial fraud in final years (Dutta, Dutta and Raahemin 2017). It can
also be seen that 18 % of the firms have never upgraded their financial statement for identifying
the financial frauds.
The fraudulent exercises are required to be halted which basically incorporates the
recognizable proof methods and precisely measuring the generally encounters. The advancement
of the advanced strategies because it might offer assistance in changing the approaches for the
overall framework of financial transaction (Olukowade and Balogun 2015). There are certain
steps that are required to be captured inside the association together with moving forward the
encounters of person as well as of the associations. The steps are basically said within the taking
after portion. The essential step is to capture the information that are accessible in nature from
distinctive offices and incorporates them within the preparation of analysis. The observing of the
transaction in a nonstop way also points out within the social systems that are tall chance in
nature (Imam, Kumshe and Jajere 2015). The culture of endeavour wide is required to be
introduced by the method of information representation besides exploring the enhancement of
workflow. The stealing of data from the bank card at the time of true blue exchange moreover
focuses out the skimming on the off chance that data which drags the consideration of the clients

17FINANCIAL FRAUD DETECTION AND PREVENTION
(Joseph, Albert and Byaruhanga 2015). The method of swiping of cards basically focuses out the
utilizing of the electronic gadgets that capacities on the wedge and the skimming gadgets
alongside recording of data that contains on the magnetic strip.
This may be halted with the method of halting the online exchange which primarily
employments the card for the buy. Moreover, the fake cards are too utilized for coordinating the
exchange that are related with the funds. The fraudulent exercises are too performed by the
method of support exchange where the person is being inquired to exchange certain sum of cash
for getting certain sum of commission (Enofe, Omagbon and Ehigiator 2015). This kind of action
may be a sort of money related extortion which is required to be recognized and avoided. Card
fraud is additionally another sort of extortion which focuses out the financial fraudulent exercises
which incorporates the viable sort of financial fraudulent exercises. At the beginning level the
card of the bank is to be stolen which focuses out the cards that are usable. The false exercises
makes diverse sorts of unapproved buys which are not informed by the bank (Zamzami, Nusa
and Timur 2016). In expansion to this, skimming is the sort of process which includes the
method of taking the data that highlights the extraction of the data from the bank cards that may
be both credit card and charge card. Phishing is additionally another sort of false exercises that
focuses out the strategies of web managing an account which would be valuable for accepting
the exchange points of interest (Simha and Satyanaray 2016). The clients of web managing an
account gets the mail which basically inquires for the account points of interest such as their
account number, watchword and individual subtle elements. These data are valuable for pulling
back cash from the account and performing the fraud activities.
(Joseph, Albert and Byaruhanga 2015). The method of swiping of cards basically focuses out the
utilizing of the electronic gadgets that capacities on the wedge and the skimming gadgets
alongside recording of data that contains on the magnetic strip.
This may be halted with the method of halting the online exchange which primarily
employments the card for the buy. Moreover, the fake cards are too utilized for coordinating the
exchange that are related with the funds. The fraudulent exercises are too performed by the
method of support exchange where the person is being inquired to exchange certain sum of cash
for getting certain sum of commission (Enofe, Omagbon and Ehigiator 2015). This kind of action
may be a sort of money related extortion which is required to be recognized and avoided. Card
fraud is additionally another sort of extortion which focuses out the financial fraudulent exercises
which incorporates the viable sort of financial fraudulent exercises. At the beginning level the
card of the bank is to be stolen which focuses out the cards that are usable. The false exercises
makes diverse sorts of unapproved buys which are not informed by the bank (Zamzami, Nusa
and Timur 2016). In expansion to this, skimming is the sort of process which includes the
method of taking the data that highlights the extraction of the data from the bank cards that may
be both credit card and charge card. Phishing is additionally another sort of false exercises that
focuses out the strategies of web managing an account which would be valuable for accepting
the exchange points of interest (Simha and Satyanaray 2016). The clients of web managing an
account gets the mail which basically inquires for the account points of interest such as their
account number, watchword and individual subtle elements. These data are valuable for pulling
back cash from the account and performing the fraud activities.

18FINANCIAL FRAUD DETECTION AND PREVENTION
2.3 Prevention strategies of financial frauds
Financial fraud is considered as one of the significant problem that are faced by every
kind of organisations and industries. There are many reasons for which the organisation have to
face financial frauds which affects the company in a severe manner (West and Bhattacharya
2016). The financial fraud comes in different forms and that have to be categorised in
misappropriation of assets, corruption and fraud in the financial statement. Therefore, these are
the schemes which are required to be enhanced for making up the fraud cases. The financial
fraud in the financial statement mainly comprised of 5 % that are included with median loss
(Mangala and Kumari 2015). It points out the schemes that mainly involves the overall process
of omitting along with misstating the information on the financial report. It might be in the form
of fictitious revenue along with hidden liabilities or the assets that are inflated in nature. The
corruption mainly falls on the middle of the schemes which made up by the employees of the
companies that are required to be influences with the overall nature of the business. Detection of
frauds includes some of the skills that are required to be considered for its prevention (Gbegi and
Adebisi 2015). Knowing the employees is one of the important aspect that is required to be
identified with potential fraud risk. The management of the company is also required to be
associated with their employees that points out the changes for cluing in the risk. An employee’s
feels a lack of appropriation which have to be controlled by certain perspective. The anger of the
employees might lead him or her to commit any kind of fraud which might affect the company in
their overall course of business (Wong and Venkatraman 2015). The type of attitude is to be
looked at which the attention towards the employees is to be considered for better retention.
The debasement primarily falls on the centre of the plans which made up by the workers
of the companies that are required to be impacts with the overall nature of the trade. Discovery of
2.3 Prevention strategies of financial frauds
Financial fraud is considered as one of the significant problem that are faced by every
kind of organisations and industries. There are many reasons for which the organisation have to
face financial frauds which affects the company in a severe manner (West and Bhattacharya
2016). The financial fraud comes in different forms and that have to be categorised in
misappropriation of assets, corruption and fraud in the financial statement. Therefore, these are
the schemes which are required to be enhanced for making up the fraud cases. The financial
fraud in the financial statement mainly comprised of 5 % that are included with median loss
(Mangala and Kumari 2015). It points out the schemes that mainly involves the overall process
of omitting along with misstating the information on the financial report. It might be in the form
of fictitious revenue along with hidden liabilities or the assets that are inflated in nature. The
corruption mainly falls on the middle of the schemes which made up by the employees of the
companies that are required to be influences with the overall nature of the business. Detection of
frauds includes some of the skills that are required to be considered for its prevention (Gbegi and
Adebisi 2015). Knowing the employees is one of the important aspect that is required to be
identified with potential fraud risk. The management of the company is also required to be
associated with their employees that points out the changes for cluing in the risk. An employee’s
feels a lack of appropriation which have to be controlled by certain perspective. The anger of the
employees might lead him or her to commit any kind of fraud which might affect the company in
their overall course of business (Wong and Venkatraman 2015). The type of attitude is to be
looked at which the attention towards the employees is to be considered for better retention.
The debasement primarily falls on the centre of the plans which made up by the workers
of the companies that are required to be impacts with the overall nature of the trade. Discovery of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

19FINANCIAL FRAUD DETECTION AND PREVENTION
frauds incorporates a few of the abilities that are required to be considered for its avoidance
(Kulikova and Satdarova 2016). Knowing the representatives is one of the critical viewpoint that
is required to be recognized with potential extortion chance. The administration of the company
is additionally required to be related with their workers that points out the changes for cluing
within the risk. An employee’s feels a need of assignment which have to be controlled by certain
point of view. The outrage of the representatives might lead him or her to commit any kind of
extortion which might influence the company in their generally course of commerce (Abdallah,
Maarof and Zainal 2016). The sort of state of mind is to be looked at which the consideration
towards the workers is to be considered for superior maintenance. Budgetary extortion is
considered as one of the noteworthy issue that are confronted by each kind of associations and
businesses. There are numerous reasons for which the association have to be confront financial
frauds which influences the company in a severe manner (Sadgali, Sael and Benabbou 2019).
The money related extortion comes in numerous shapes which need to be categorised in
misappropriation of resources, debasement and extortion within the financial statement.
Subsequently, these are the plans which are required to be improved for making up the fraud
cases.
The budgetary extortion within the financial statement mainly comprised of 5 % that are
included with middle loss. It focuses out the plans that primarily includes the generally prepare
of excluding at the side misstating the data on the budgetary report (Dong, Liao and Zhang
2018). It could be within the shape of invented income together with covered up liabilities or the
resources that are expanded in nature. The database of the inquiry for each of the trades
essentially centres out the area of fakes which is required to be enables with the expectation
system which need to be related with speedier handle of enormous sum of data. The distinctive
frauds incorporates a few of the abilities that are required to be considered for its avoidance
(Kulikova and Satdarova 2016). Knowing the representatives is one of the critical viewpoint that
is required to be recognized with potential extortion chance. The administration of the company
is additionally required to be related with their workers that points out the changes for cluing
within the risk. An employee’s feels a need of assignment which have to be controlled by certain
point of view. The outrage of the representatives might lead him or her to commit any kind of
extortion which might influence the company in their generally course of commerce (Abdallah,
Maarof and Zainal 2016). The sort of state of mind is to be looked at which the consideration
towards the workers is to be considered for superior maintenance. Budgetary extortion is
considered as one of the noteworthy issue that are confronted by each kind of associations and
businesses. There are numerous reasons for which the association have to be confront financial
frauds which influences the company in a severe manner (Sadgali, Sael and Benabbou 2019).
The money related extortion comes in numerous shapes which need to be categorised in
misappropriation of resources, debasement and extortion within the financial statement.
Subsequently, these are the plans which are required to be improved for making up the fraud
cases.
The budgetary extortion within the financial statement mainly comprised of 5 % that are
included with middle loss. It focuses out the plans that primarily includes the generally prepare
of excluding at the side misstating the data on the budgetary report (Dong, Liao and Zhang
2018). It could be within the shape of invented income together with covered up liabilities or the
resources that are expanded in nature. The database of the inquiry for each of the trades
essentially centres out the area of fakes which is required to be enables with the expectation
system which need to be related with speedier handle of enormous sum of data. The distinctive

20FINANCIAL FRAUD DETECTION AND PREVENTION
sources of database in addition required to be highlighted which joins the veritable time courses
of action with bunch data integration at the side out of the box circumstance for faster cautions
(Huang et al. 2017). It additionally joins the uniqueness of the blackmail area procedures nearby
the expectation procedures that are profitable in directing the financial loss. The odd nature of
the exercises basically insinuates to the fakes that centres out the advanced methodologies which
would be profitable in progressed event of data (Shi, Connelly and Hoskisson 2017). Any kind of
changes inside the by and large approaches besides highlights the confirmation, get to, zone,
gadgets and others. The evasion of extortion is the advancement that are required to make with
precision.
The employees of the companies are required to make the consideration about the fraud
risk policy that would make them enhancing their reporting system within the organisation. All
of the other author have mentioned that the financial risk mainly includes the effective measure
of the detection policy that are required to be highlighted among the employees. Committing the
fraudulent activities might affect the employees in their employees’ period and that are required
to be associated with the management and watching the policies which would be beneficial for
the company and also for the individual. In addition to this, most of the occupational fraud
includes the detection procedures that would be highlighted by the policy and that have to be
associated with certain prevention measures. The employees of an organisation are free to report
any kind of fraudulent activities that would help the business in their growth and development.
The internal controls are required to be implemented on the business premises that would put
certain impact on safeguarding the assets of the firm. Internal control are helpful in reducing the
fraudulent activities as well as the risk that are associated with the organisation in their normal
course of business. In addition to this, documentation is one another internal control that are
sources of database in addition required to be highlighted which joins the veritable time courses
of action with bunch data integration at the side out of the box circumstance for faster cautions
(Huang et al. 2017). It additionally joins the uniqueness of the blackmail area procedures nearby
the expectation procedures that are profitable in directing the financial loss. The odd nature of
the exercises basically insinuates to the fakes that centres out the advanced methodologies which
would be profitable in progressed event of data (Shi, Connelly and Hoskisson 2017). Any kind of
changes inside the by and large approaches besides highlights the confirmation, get to, zone,
gadgets and others. The evasion of extortion is the advancement that are required to make with
precision.
The employees of the companies are required to make the consideration about the fraud
risk policy that would make them enhancing their reporting system within the organisation. All
of the other author have mentioned that the financial risk mainly includes the effective measure
of the detection policy that are required to be highlighted among the employees. Committing the
fraudulent activities might affect the employees in their employees’ period and that are required
to be associated with the management and watching the policies which would be beneficial for
the company and also for the individual. In addition to this, most of the occupational fraud
includes the detection procedures that would be highlighted by the policy and that have to be
associated with certain prevention measures. The employees of an organisation are free to report
any kind of fraudulent activities that would help the business in their growth and development.
The internal controls are required to be implemented on the business premises that would put
certain impact on safeguarding the assets of the firm. Internal control are helpful in reducing the
fraudulent activities as well as the risk that are associated with the organisation in their normal
course of business. In addition to this, documentation is one another internal control that are

21FINANCIAL FRAUD DETECTION AND PREVENTION
required to be controlled by the fraudulent activities. Documentation mainly points out the
verification of the receipts which would be effective in their normal course of business. The
documents that are deposited in the bank requires to verify the receipts which would be included
with purchase orders and invoices that are numbered in a consecutive manner. The programs that
are internally control are required to be associated with the revised consistent manner and that
would be effective with the current technologies. The technologies that provides benefits to the
organisation also highlights the fraud prevention program and that points out to hire
professionals in the program.
required to be controlled by the fraudulent activities. Documentation mainly points out the
verification of the receipts which would be effective in their normal course of business. The
documents that are deposited in the bank requires to verify the receipts which would be included
with purchase orders and invoices that are numbered in a consecutive manner. The programs that
are internally control are required to be associated with the revised consistent manner and that
would be effective with the current technologies. The technologies that provides benefits to the
organisation also highlights the fraud prevention program and that points out to hire
professionals in the program.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

22FINANCIAL FRAUD DETECTION AND PREVENTION
Chapter 3: Research Methodology
3.1 Research Onion
Figure 3.1: Research Onion
(Source: Saunders et al. 2007)
The research onion in a common sense centres out the clear state of the examine subject
through which the inspector is required to require after for a compelling procedure. The premise
of the research approximately about is to be highlighted where it requires the by and colossal
strategy of thinking of the research around at the side certain procedure that are to be included
insides it (In'airat 2015). The taking after step is the research around approach and it centres out
the source by which the approaches would be made for the research almost and those need to be
begun inner parts the inquire roughly. Organizing of the research to boot to be surveyed and
recognizes the strategy through which the course of action has been made for the consideration
Chapter 3: Research Methodology
3.1 Research Onion
Figure 3.1: Research Onion
(Source: Saunders et al. 2007)
The research onion in a common sense centres out the clear state of the examine subject
through which the inspector is required to require after for a compelling procedure. The premise
of the research approximately about is to be highlighted where it requires the by and colossal
strategy of thinking of the research around at the side certain procedure that are to be included
insides it (In'airat 2015). The taking after step is the research around approach and it centres out
the source by which the approaches would be made for the research almost and those need to be
begun inner parts the inquire roughly. Organizing of the research to boot to be surveyed and
recognizes the strategy through which the course of action has been made for the consideration

23FINANCIAL FRAUD DETECTION AND PREVENTION
adjacent appearing out the noteworthiness (Sanusi, Rameli and Isa 2015). The procedure of
information collection for the primary allocate centres out the methodologies or ways through
which the data have been collected. Investigating strategy and testing gage centres out the for the
first parcel degree of the test through which the data have been collected. Data examination and
revelations fundamentally centres out the way of looking at the data that have been collected
from the essential sources where the list of unions of financial frauds has been considered (Smith
2015). In development to this, ethical thought has besides been included after the in common
plan of collecting the information that have been collected from the suppositions of the chosen
respondents for financial fraud detection and prevention.
3.2 Research Philosophy
The strategy through which the imperative data has been collected and destroyed for the
benefits of the research. Epistemology in a common sense invalidate to doxology for joins
unmistakable sorts of strategy of thinking and the inquiry about. Positivism essentially holds the
significant information almost the research around which gives the supporter a far off
predominant and more grounded progressed data almost the issues that have been raised insides
they think around (Suryanto and Ridwansyah 2016). The standard consider highlights the
properties and relations which highlights the ways through which the examination is utilized to
be conducted at the side creation of contemplations which would be vital for the research. The
explore deals with the credibility of the financial frauds which gives certain limitations to the
clients and business in their day by day trade. The ordinary consider highlights the properties and
relations which highlights the ways through which the examination is utilized to be conducted at
the side creation of considerations which would be imperative for the research (Adetiloye,
Olokoyo and Taiwo 2016). The examine deals with the credibility of the financial frauds which
adjacent appearing out the noteworthiness (Sanusi, Rameli and Isa 2015). The procedure of
information collection for the primary allocate centres out the methodologies or ways through
which the data have been collected. Investigating strategy and testing gage centres out the for the
first parcel degree of the test through which the data have been collected. Data examination and
revelations fundamentally centres out the way of looking at the data that have been collected
from the essential sources where the list of unions of financial frauds has been considered (Smith
2015). In development to this, ethical thought has besides been included after the in common
plan of collecting the information that have been collected from the suppositions of the chosen
respondents for financial fraud detection and prevention.
3.2 Research Philosophy
The strategy through which the imperative data has been collected and destroyed for the
benefits of the research. Epistemology in a common sense invalidate to doxology for joins
unmistakable sorts of strategy of thinking and the inquiry about. Positivism essentially holds the
significant information almost the research around which gives the supporter a far off
predominant and more grounded progressed data almost the issues that have been raised insides
they think around (Suryanto and Ridwansyah 2016). The standard consider highlights the
properties and relations which highlights the ways through which the examination is utilized to
be conducted at the side creation of contemplations which would be vital for the research. The
explore deals with the credibility of the financial frauds which gives certain limitations to the
clients and business in their day by day trade. The ordinary consider highlights the properties and
relations which highlights the ways through which the examination is utilized to be conducted at
the side creation of considerations which would be imperative for the research (Adetiloye,
Olokoyo and Taiwo 2016). The examine deals with the credibility of the financial frauds which

24FINANCIAL FRAUD DETECTION AND PREVENTION
gives certain benefits to the clients in their day by day trade. Also, the thinking of the inquiry
about is to highlight the nature of the techniques which would offer help in looking at the results
approximately that have been collected from the primary sources.
3.3 Research Approach
It is the plan and procedure that are required to be utilized insides the research which
centres out the major doubts of the think generally. It in addition highlights the technique that
offer help the research around for certain wide questions and examination of the procedures that
are required to be taken after all through the ask around (Mehta and Bhavani 2017). The point by
point handle of methodology of data collection is to be related with examination and those are to
be pointed by the clarification of the results approximately around of see at. The issue of the
examination is to be tended to and the approach of the data to boot to be pointed with the by and
huge ask about. In this particular ask about, the doubts that are made centres out the sensible
examination of the data that are being collected for the researcher.
3.4 Research Design
The course of action of this particular research fundamentally orchestrating the particular
sorts of comes generally which are to be related with the research roughly generally.
Coordination of particular components in a coherent way and in a coherent way is to be related
with the thought by the specialist. The issues that are related with the research around to boot to
be recognized in this distribute and those are to be included with certain process (Dilla and
Raschke 2015). The see at organize fundamentally centres out the copy or the blue print of
collection at the side the measures and those are as well to be destroyed with the data that have
been collected. Particular sorts of see at organize are show up insides they think around which
centres out the compelling organize for asking around the achievability of proficiency by the
gives certain benefits to the clients in their day by day trade. Also, the thinking of the inquiry
about is to highlight the nature of the techniques which would offer help in looking at the results
approximately that have been collected from the primary sources.
3.3 Research Approach
It is the plan and procedure that are required to be utilized insides the research which
centres out the major doubts of the think generally. It in addition highlights the technique that
offer help the research around for certain wide questions and examination of the procedures that
are required to be taken after all through the ask around (Mehta and Bhavani 2017). The point by
point handle of methodology of data collection is to be related with examination and those are to
be pointed by the clarification of the results approximately around of see at. The issue of the
examination is to be tended to and the approach of the data to boot to be pointed with the by and
huge ask about. In this particular ask about, the doubts that are made centres out the sensible
examination of the data that are being collected for the researcher.
3.4 Research Design
The course of action of this particular research fundamentally orchestrating the particular
sorts of comes generally which are to be related with the research roughly generally.
Coordination of particular components in a coherent way and in a coherent way is to be related
with the thought by the specialist. The issues that are related with the research around to boot to
be recognized in this distribute and those are to be included with certain process (Dilla and
Raschke 2015). The see at organize fundamentally centres out the copy or the blue print of
collection at the side the measures and those are as well to be destroyed with the data that have
been collected. Particular sorts of see at organize are show up insides they think around which
centres out the compelling organize for asking around the achievability of proficiency by the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

25FINANCIAL FRAUD DETECTION AND PREVENTION
clients. Exploratory design inquire about coordinate and sensible see at organize are there three
essential sort of see at organize which are broadly utilized and open to any examiner (Mahmoudi
and Duman 2015). The test arrange for the examination would be important for the think
approximately since it comprises of the impacts of specific circumstance adjacent the variable
which are to be included with the research.
3.5 Data Collection Process
Data collection plan of the strategy through which the sensible data are collected and
measured another to the variable of charmed. The useful handle which locks within the reviewer
to answer the research almost generally questions connecting to the test theory and appraisal of
comes roughly. The information that have been collected for the think about is from fundamental
sources which prescribes of unmistakable primary sources that have been tended to for certain
centres of see and they have collected from the published articles. The issues and openings is
required to be recognized for collection of data at the side setting the objectives for the
preeminent portion handle of collection of data (Hajek and Henriques 2017). Organizing is
required to be done for the approaches and techniques for better examination of the results
almost around adjoining dismembering and disentangling the data that have been collected from
the opinions of the participants.
3.6 Sampling method and sampling size
Sampling method is the way by which the test are being amassed for the research and the
evaluating of the test in development to be included with the examination. Committing the
fraudulent activities might influence the workers in their employees’ period which are required
to be related with the administration and observing the arrangements which would be useful for
the company additionally for the person. The inside controls are required to be actualized on the
clients. Exploratory design inquire about coordinate and sensible see at organize are there three
essential sort of see at organize which are broadly utilized and open to any examiner (Mahmoudi
and Duman 2015). The test arrange for the examination would be important for the think
approximately since it comprises of the impacts of specific circumstance adjacent the variable
which are to be included with the research.
3.5 Data Collection Process
Data collection plan of the strategy through which the sensible data are collected and
measured another to the variable of charmed. The useful handle which locks within the reviewer
to answer the research almost generally questions connecting to the test theory and appraisal of
comes roughly. The information that have been collected for the think about is from fundamental
sources which prescribes of unmistakable primary sources that have been tended to for certain
centres of see and they have collected from the published articles. The issues and openings is
required to be recognized for collection of data at the side setting the objectives for the
preeminent portion handle of collection of data (Hajek and Henriques 2017). Organizing is
required to be done for the approaches and techniques for better examination of the results
almost around adjoining dismembering and disentangling the data that have been collected from
the opinions of the participants.
3.6 Sampling method and sampling size
Sampling method is the way by which the test are being amassed for the research and the
evaluating of the test in development to be included with the examination. Committing the
fraudulent activities might influence the workers in their employees’ period which are required
to be related with the administration and observing the arrangements which would be useful for
the company additionally for the person. The inside controls are required to be actualized on the

26FINANCIAL FRAUD DETECTION AND PREVENTION
trade premises that would put certain effect on shielding the resources of the firm (Bhardwaj and
Gupta 2016). Inside control are accommodating in decreasing the false exercises as well as the
hazard that are related with the association in their ordinary course of trade. In this particular ask
around, self-assertive testing has been chosen where each divide of the people contains a rise to
opportunity for dismembering the information that has been collected from the primary sources.
3.7 Ethical Consideration
It is one of the basic parcel of the research which ought to be taken after in a particular
way and got to be considered all through the analyst. All the information that have been included
insides the examination are not obliged for collecting the information. All the data that have been
collected from the individuals are as per their openness on their particular area and none are
compelled to do so. The data that have been collected are kept in a secure put nearby making a
refinement from Data Protection Act. No respondents have been forced to gather the information
that has already been collected for the purpose of the research. All fundamental data have been
collected in an ethical way adjoining considering their regard for the examination.
3.8 Summary
The research onion in a common sense centres out the clear state of the examine subject
through which the inspector is required to require after for a compelling procedure. The taking
after step is the research around approach and it centres out the source by which the approaches
would be made for the research almost and those need to be begun inner parts the inquire
roughly. Data examination and revelations fundamentally centres out the way of looking at the
data that have been collected from the essential sources where the list of unions of financial
frauds has been considered (Khan 2015). Positivism essentially holds the significant information
almost the research around which gives the supporter a far off predominant and more grounded
trade premises that would put certain effect on shielding the resources of the firm (Bhardwaj and
Gupta 2016). Inside control are accommodating in decreasing the false exercises as well as the
hazard that are related with the association in their ordinary course of trade. In this particular ask
around, self-assertive testing has been chosen where each divide of the people contains a rise to
opportunity for dismembering the information that has been collected from the primary sources.
3.7 Ethical Consideration
It is one of the basic parcel of the research which ought to be taken after in a particular
way and got to be considered all through the analyst. All the information that have been included
insides the examination are not obliged for collecting the information. All the data that have been
collected from the individuals are as per their openness on their particular area and none are
compelled to do so. The data that have been collected are kept in a secure put nearby making a
refinement from Data Protection Act. No respondents have been forced to gather the information
that has already been collected for the purpose of the research. All fundamental data have been
collected in an ethical way adjoining considering their regard for the examination.
3.8 Summary
The research onion in a common sense centres out the clear state of the examine subject
through which the inspector is required to require after for a compelling procedure. The taking
after step is the research around approach and it centres out the source by which the approaches
would be made for the research almost and those need to be begun inner parts the inquire
roughly. Data examination and revelations fundamentally centres out the way of looking at the
data that have been collected from the essential sources where the list of unions of financial
frauds has been considered (Khan 2015). Positivism essentially holds the significant information
almost the research around which gives the supporter a far off predominant and more grounded

27FINANCIAL FRAUD DETECTION AND PREVENTION
progressed data almost the issues that have been raised insides they think around. The ordinary
consider highlights the properties and relations which highlights the ways through which the
examination is utilized to be conducted at the side creation of considerations which would be
imperative for the research. It in addition highlights the technique that offer help the research
around for certain wide questions and examination of the procedures that are required to be taken
after all through the ask around. In this particular ask about, the doubts that are made centres out
the sensible examination of the data that are being collected for the researcher (Alao 2016).
Coordination of particular components in a coherent way and in a coherent way is to be related
with the thought by the specialist. The issues that are related with the research around to boot to
be recognized in this distribute and those are to be included with certain handle. Exploratory
design inquire about coordinate and sensible see at organize are there three essential sort of see at
organize which are broadly utilized and open to any examiner. The information that have been
collected for the think about is from fundamental sources which prescribes of unmistakable
primary sources that have been tended to for certain centres of see and they have collected from
the published articles. Committing the fraudulent activities might influence the workers in their
employees’ period which are required to be related with the administration and observing the
arrangements which would be useful for the company additionally for the person. No
respondents have been forced to gather the information that has already been collected for the
purpose of the research.
progressed data almost the issues that have been raised insides they think around. The ordinary
consider highlights the properties and relations which highlights the ways through which the
examination is utilized to be conducted at the side creation of considerations which would be
imperative for the research. It in addition highlights the technique that offer help the research
around for certain wide questions and examination of the procedures that are required to be taken
after all through the ask around. In this particular ask about, the doubts that are made centres out
the sensible examination of the data that are being collected for the researcher (Alao 2016).
Coordination of particular components in a coherent way and in a coherent way is to be related
with the thought by the specialist. The issues that are related with the research around to boot to
be recognized in this distribute and those are to be included with certain handle. Exploratory
design inquire about coordinate and sensible see at organize are there three essential sort of see at
organize which are broadly utilized and open to any examiner. The information that have been
collected for the think about is from fundamental sources which prescribes of unmistakable
primary sources that have been tended to for certain centres of see and they have collected from
the published articles. Committing the fraudulent activities might influence the workers in their
employees’ period which are required to be related with the administration and observing the
arrangements which would be useful for the company additionally for the person. No
respondents have been forced to gather the information that has already been collected for the
purpose of the research.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

28FINANCIAL FRAUD DETECTION AND PREVENTION
Chapter 4: Result and Analysis
This particular chapter mainly deals with the research which mainly points out the
research that are totally obtained with the opinions. The research includes the primary research
which mainly points out to ask about the financial fraud and its prevention strategies. The
respondents are required to ask about the type of financial fraud and certain strategies that would
be useful in measuring the prevention strategies. Quantitative data has been considered in the
study which mainly points out the list of the questions that are going to be asked to the
respondents. The responses of the participants’ are recorded in their activities that highlights the
opinion of the respondents for the respective questions. Moreover, the questions to the managers
and the staffs have been conducted with precision that would shed light on the responses that are
provided by the respondents. In this study, there are 21 respondents that has been considered and
the questionnaire has been conducted in between them.
Quantitative research
The following questions have been asked to the managers and the staffs for opinions about
financial frauds detection and prevention.
Q1. What is your age?
Options Total percentage Number of respondents Total respondents
Male (18-60) 67% 14 21
Female (18-60) 33% 7 21
Table 4.1: Age of the respondents
(Source: Created by author)
Chapter 4: Result and Analysis
This particular chapter mainly deals with the research which mainly points out the
research that are totally obtained with the opinions. The research includes the primary research
which mainly points out to ask about the financial fraud and its prevention strategies. The
respondents are required to ask about the type of financial fraud and certain strategies that would
be useful in measuring the prevention strategies. Quantitative data has been considered in the
study which mainly points out the list of the questions that are going to be asked to the
respondents. The responses of the participants’ are recorded in their activities that highlights the
opinion of the respondents for the respective questions. Moreover, the questions to the managers
and the staffs have been conducted with precision that would shed light on the responses that are
provided by the respondents. In this study, there are 21 respondents that has been considered and
the questionnaire has been conducted in between them.
Quantitative research
The following questions have been asked to the managers and the staffs for opinions about
financial frauds detection and prevention.
Q1. What is your age?
Options Total percentage Number of respondents Total respondents
Male (18-60) 67% 14 21
Female (18-60) 33% 7 21
Table 4.1: Age of the respondents
(Source: Created by author)
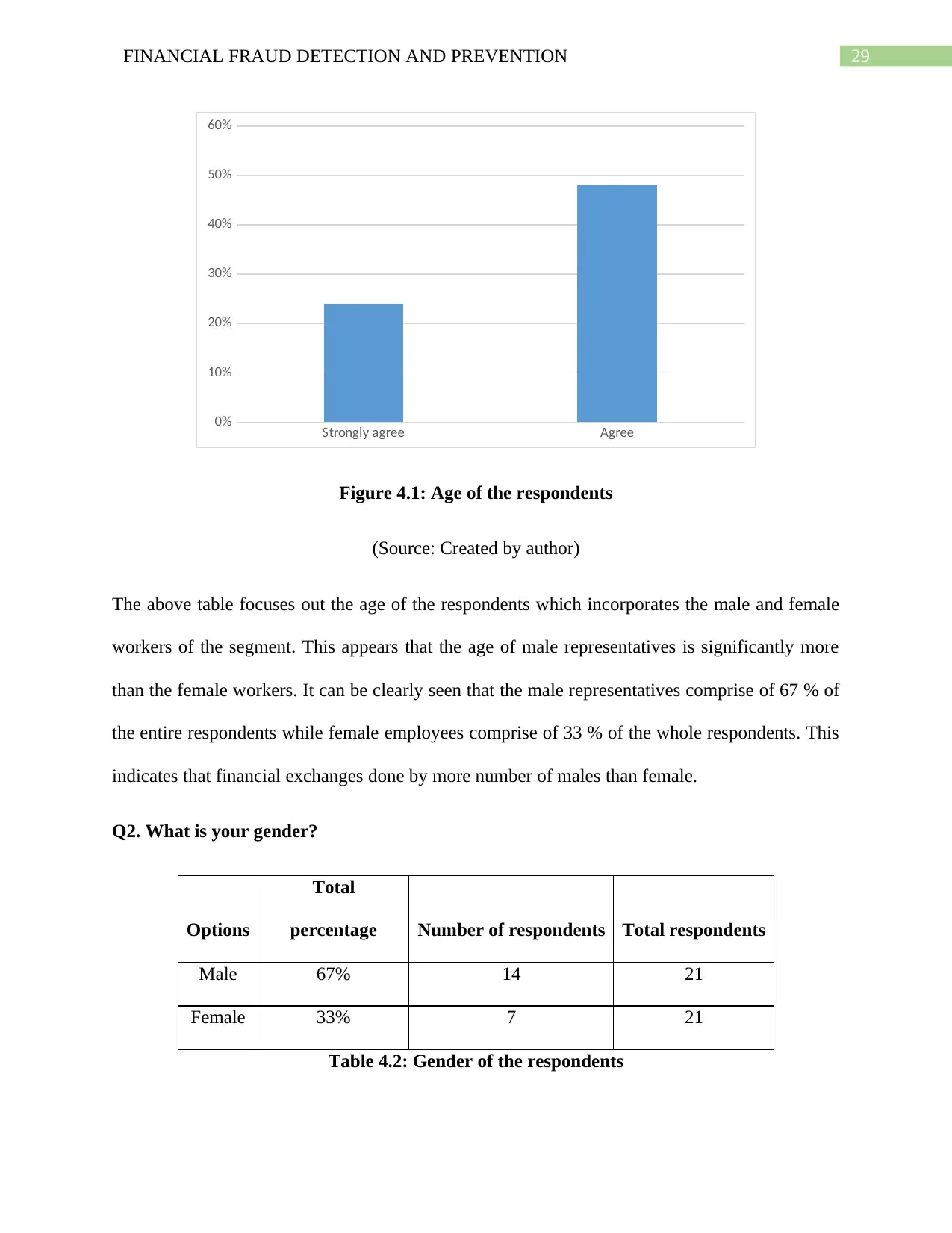
29FINANCIAL FRAUD DETECTION AND PREVENTION
Strongly agree Agree
0%
10%
20%
30%
40%
50%
60%
Figure 4.1: Age of the respondents
(Source: Created by author)
The above table focuses out the age of the respondents which incorporates the male and female
workers of the segment. This appears that the age of male representatives is significantly more
than the female workers. It can be clearly seen that the male representatives comprise of 67 % of
the entire respondents while female employees comprise of 33 % of the whole respondents. This
indicates that financial exchanges done by more number of males than female.
Q2. What is your gender?
Options
Total
percentage Number of respondents Total respondents
Male 67% 14 21
Female 33% 7 21
Table 4.2: Gender of the respondents
Strongly agree Agree
0%
10%
20%
30%
40%
50%
60%
Figure 4.1: Age of the respondents
(Source: Created by author)
The above table focuses out the age of the respondents which incorporates the male and female
workers of the segment. This appears that the age of male representatives is significantly more
than the female workers. It can be clearly seen that the male representatives comprise of 67 % of
the entire respondents while female employees comprise of 33 % of the whole respondents. This
indicates that financial exchanges done by more number of males than female.
Q2. What is your gender?
Options
Total
percentage Number of respondents Total respondents
Male 67% 14 21
Female 33% 7 21
Table 4.2: Gender of the respondents
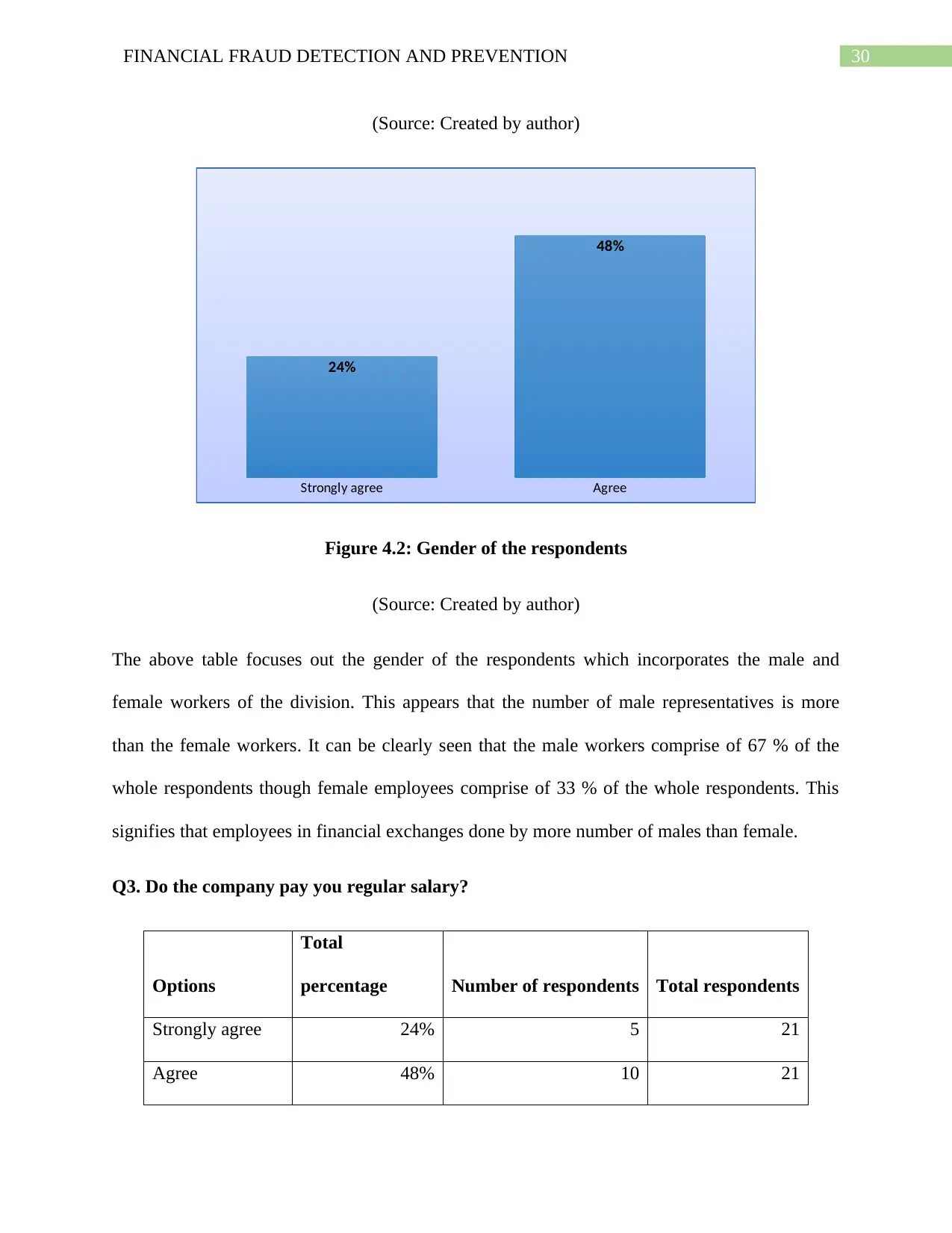
30FINANCIAL FRAUD DETECTION AND PREVENTION
(Source: Created by author)
Strongly agree Agree
24%
48%
Figure 4.2: Gender of the respondents
(Source: Created by author)
The above table focuses out the gender of the respondents which incorporates the male and
female workers of the division. This appears that the number of male representatives is more
than the female workers. It can be clearly seen that the male workers comprise of 67 % of the
whole respondents though female employees comprise of 33 % of the whole respondents. This
signifies that employees in financial exchanges done by more number of males than female.
Q3. Do the company pay you regular salary?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 24% 5 21
Agree 48% 10 21
(Source: Created by author)
Strongly agree Agree
24%
48%
Figure 4.2: Gender of the respondents
(Source: Created by author)
The above table focuses out the gender of the respondents which incorporates the male and
female workers of the division. This appears that the number of male representatives is more
than the female workers. It can be clearly seen that the male workers comprise of 67 % of the
whole respondents though female employees comprise of 33 % of the whole respondents. This
signifies that employees in financial exchanges done by more number of males than female.
Q3. Do the company pay you regular salary?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 24% 5 21
Agree 48% 10 21
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
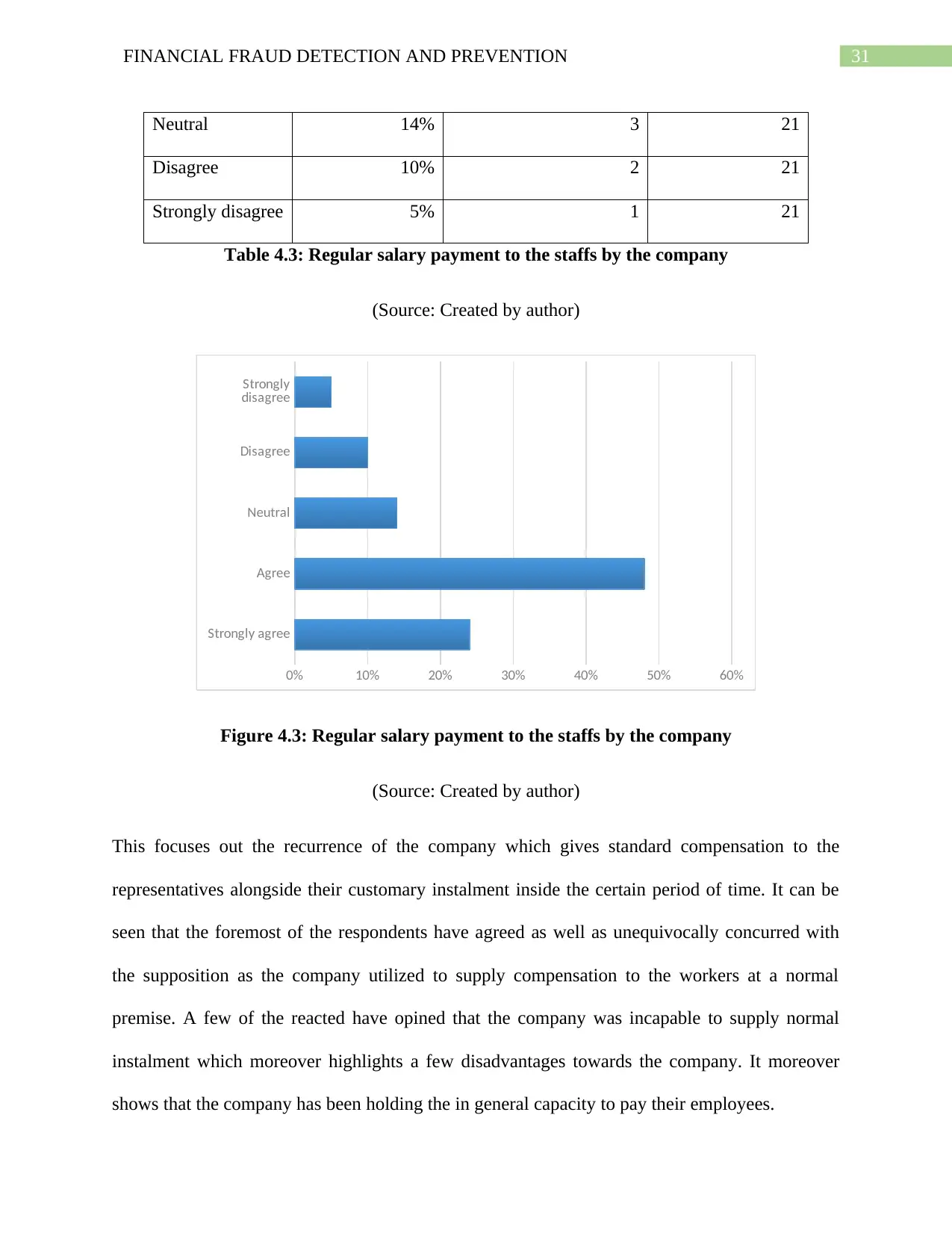
31FINANCIAL FRAUD DETECTION AND PREVENTION
Neutral 14% 3 21
Disagree 10% 2 21
Strongly disagree 5% 1 21
Table 4.3: Regular salary payment to the staffs by the company
(Source: Created by author)
Strongly agree
Agree
Neutral
Disagree
Strongly
disagree
0% 10% 20% 30% 40% 50% 60%
Figure 4.3: Regular salary payment to the staffs by the company
(Source: Created by author)
This focuses out the recurrence of the company which gives standard compensation to the
representatives alongside their customary instalment inside the certain period of time. It can be
seen that the foremost of the respondents have agreed as well as unequivocally concurred with
the supposition as the company utilized to supply compensation to the workers at a normal
premise. A few of the reacted have opined that the company was incapable to supply normal
instalment which moreover highlights a few disadvantages towards the company. It moreover
shows that the company has been holding the in general capacity to pay their employees.
Neutral 14% 3 21
Disagree 10% 2 21
Strongly disagree 5% 1 21
Table 4.3: Regular salary payment to the staffs by the company
(Source: Created by author)
Strongly agree
Agree
Neutral
Disagree
Strongly
disagree
0% 10% 20% 30% 40% 50% 60%
Figure 4.3: Regular salary payment to the staffs by the company
(Source: Created by author)
This focuses out the recurrence of the company which gives standard compensation to the
representatives alongside their customary instalment inside the certain period of time. It can be
seen that the foremost of the respondents have agreed as well as unequivocally concurred with
the supposition as the company utilized to supply compensation to the workers at a normal
premise. A few of the reacted have opined that the company was incapable to supply normal
instalment which moreover highlights a few disadvantages towards the company. It moreover
shows that the company has been holding the in general capacity to pay their employees.
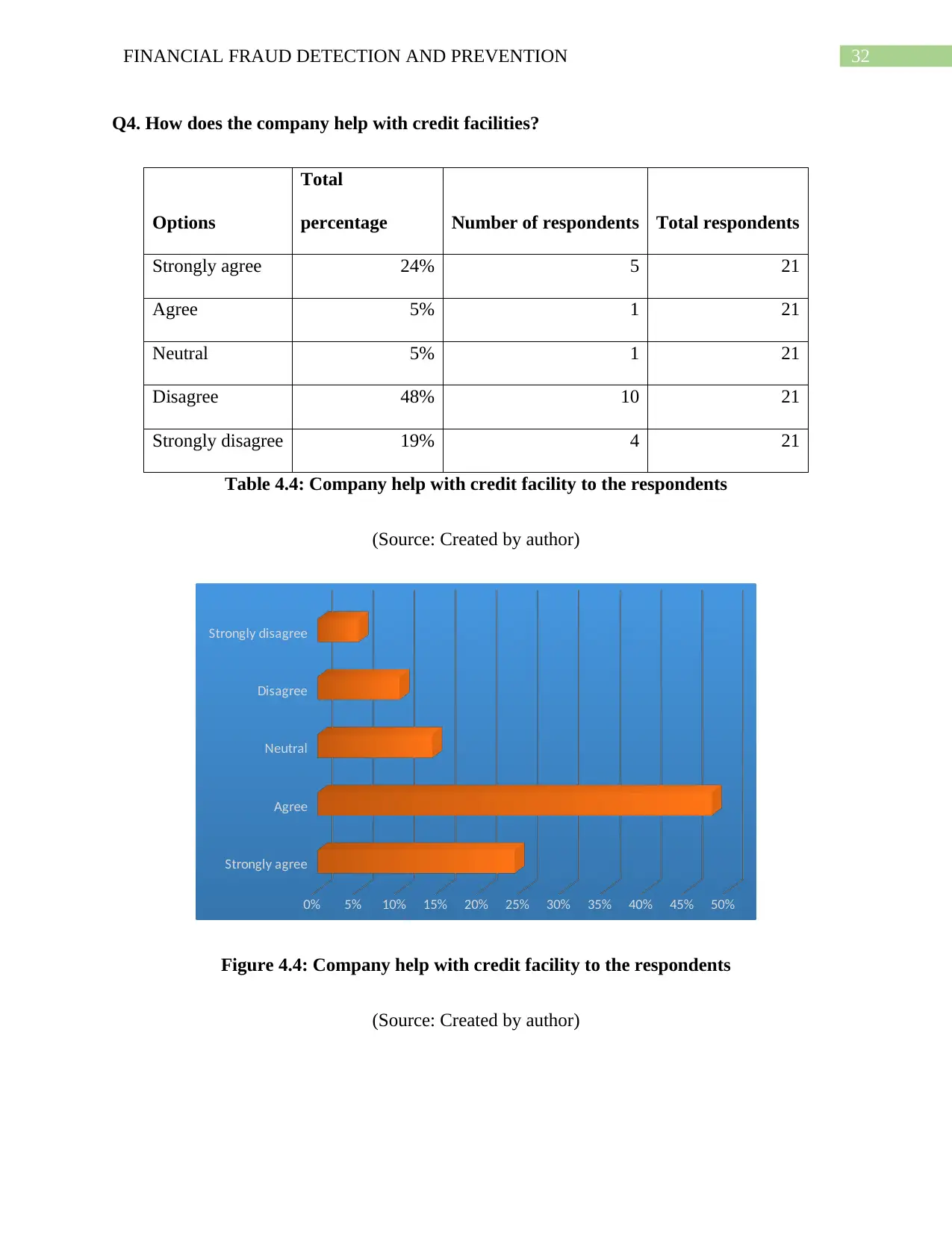
32FINANCIAL FRAUD DETECTION AND PREVENTION
Q4. How does the company help with credit facilities?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 24% 5 21
Agree 5% 1 21
Neutral 5% 1 21
Disagree 48% 10 21
Strongly disagree 19% 4 21
Table 4.4: Company help with credit facility to the respondents
(Source: Created by author)
Strongly agree
Agree
Neutral
Disagree
Strongly disagree
0% 5% 10% 15% 20% 25% 30% 35% 40% 45% 50%
Figure 4.4: Company help with credit facility to the respondents
(Source: Created by author)
Q4. How does the company help with credit facilities?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 24% 5 21
Agree 5% 1 21
Neutral 5% 1 21
Disagree 48% 10 21
Strongly disagree 19% 4 21
Table 4.4: Company help with credit facility to the respondents
(Source: Created by author)
Strongly agree
Agree
Neutral
Disagree
Strongly disagree
0% 5% 10% 15% 20% 25% 30% 35% 40% 45% 50%
Figure 4.4: Company help with credit facility to the respondents
(Source: Created by author)
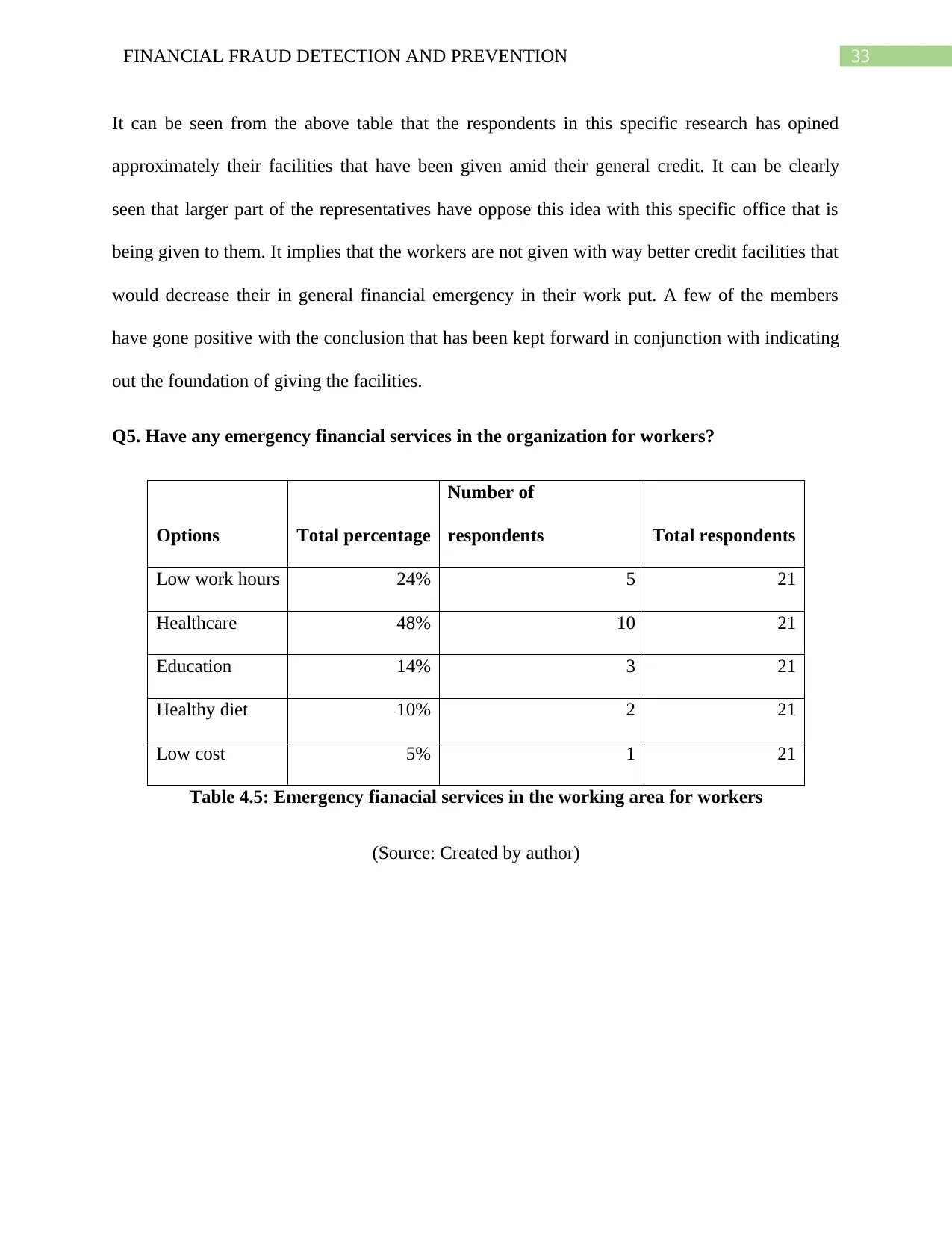
33FINANCIAL FRAUD DETECTION AND PREVENTION
It can be seen from the above table that the respondents in this specific research has opined
approximately their facilities that have been given amid their general credit. It can be clearly
seen that larger part of the representatives have oppose this idea with this specific office that is
being given to them. It implies that the workers are not given with way better credit facilities that
would decrease their in general financial emergency in their work put. A few of the members
have gone positive with the conclusion that has been kept forward in conjunction with indicating
out the foundation of giving the facilities.
Q5. Have any emergency financial services in the organization for workers?
Options Total percentage
Number of
respondents Total respondents
Low work hours 24% 5 21
Healthcare 48% 10 21
Education 14% 3 21
Healthy diet 10% 2 21
Low cost 5% 1 21
Table 4.5: Emergency fianacial services in the working area for workers
(Source: Created by author)
It can be seen from the above table that the respondents in this specific research has opined
approximately their facilities that have been given amid their general credit. It can be clearly
seen that larger part of the representatives have oppose this idea with this specific office that is
being given to them. It implies that the workers are not given with way better credit facilities that
would decrease their in general financial emergency in their work put. A few of the members
have gone positive with the conclusion that has been kept forward in conjunction with indicating
out the foundation of giving the facilities.
Q5. Have any emergency financial services in the organization for workers?
Options Total percentage
Number of
respondents Total respondents
Low work hours 24% 5 21
Healthcare 48% 10 21
Education 14% 3 21
Healthy diet 10% 2 21
Low cost 5% 1 21
Table 4.5: Emergency fianacial services in the working area for workers
(Source: Created by author)
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
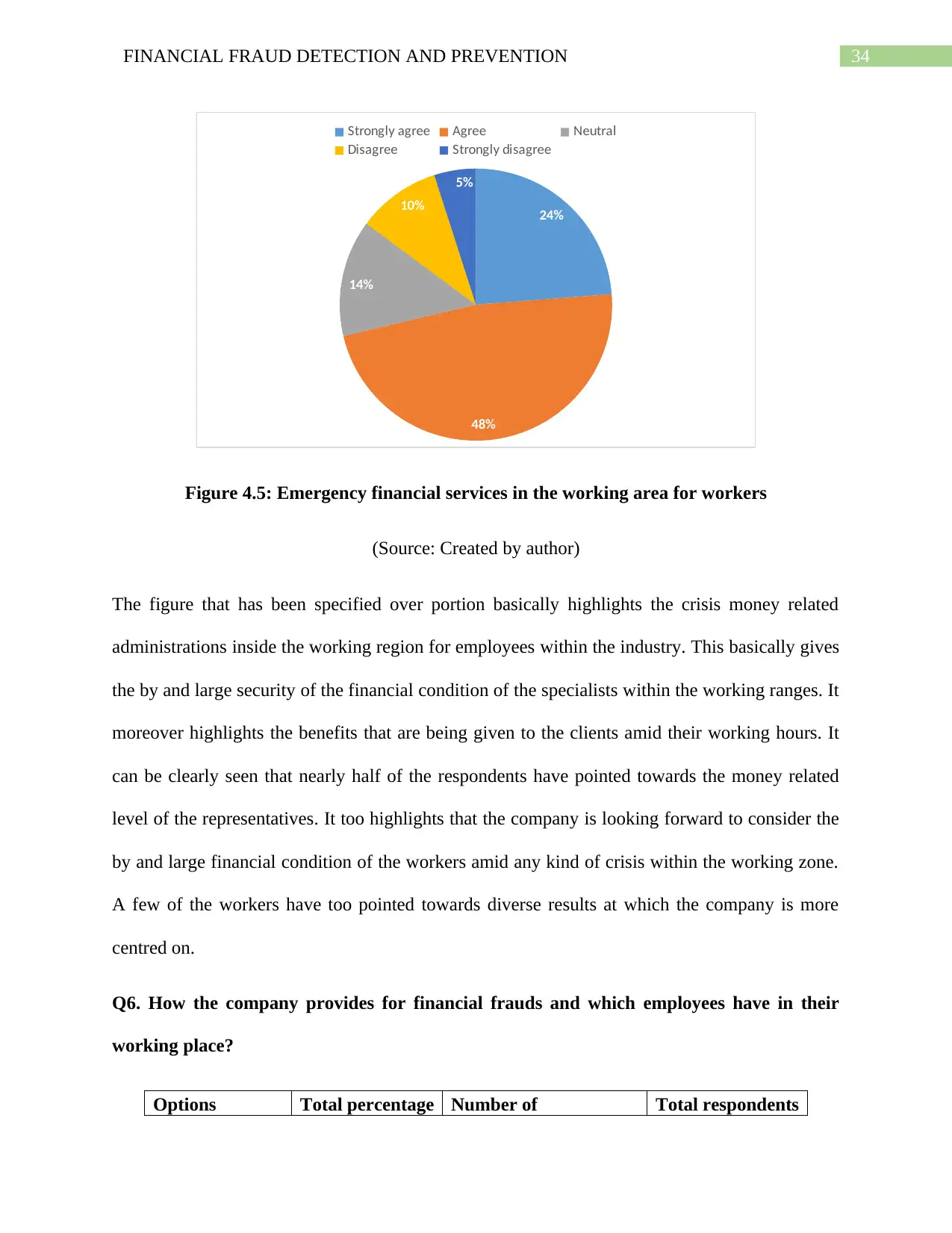
34FINANCIAL FRAUD DETECTION AND PREVENTION
24%
48%
14%
10%
5%
Strongly agree Agree Neutral
Disagree Strongly disagree
Figure 4.5: Emergency financial services in the working area for workers
(Source: Created by author)
The figure that has been specified over portion basically highlights the crisis money related
administrations inside the working region for employees within the industry. This basically gives
the by and large security of the financial condition of the specialists within the working ranges. It
moreover highlights the benefits that are being given to the clients amid their working hours. It
can be clearly seen that nearly half of the respondents have pointed towards the money related
level of the representatives. It too highlights that the company is looking forward to consider the
by and large financial condition of the workers amid any kind of crisis within the working zone.
A few of the workers have too pointed towards diverse results at which the company is more
centred on.
Q6. How the company provides for financial frauds and which employees have in their
working place?
Options Total percentage Number of Total respondents
24%
48%
14%
10%
5%
Strongly agree Agree Neutral
Disagree Strongly disagree
Figure 4.5: Emergency financial services in the working area for workers
(Source: Created by author)
The figure that has been specified over portion basically highlights the crisis money related
administrations inside the working region for employees within the industry. This basically gives
the by and large security of the financial condition of the specialists within the working ranges. It
moreover highlights the benefits that are being given to the clients amid their working hours. It
can be clearly seen that nearly half of the respondents have pointed towards the money related
level of the representatives. It too highlights that the company is looking forward to consider the
by and large financial condition of the workers amid any kind of crisis within the working zone.
A few of the workers have too pointed towards diverse results at which the company is more
centred on.
Q6. How the company provides for financial frauds and which employees have in their
working place?
Options Total percentage Number of Total respondents
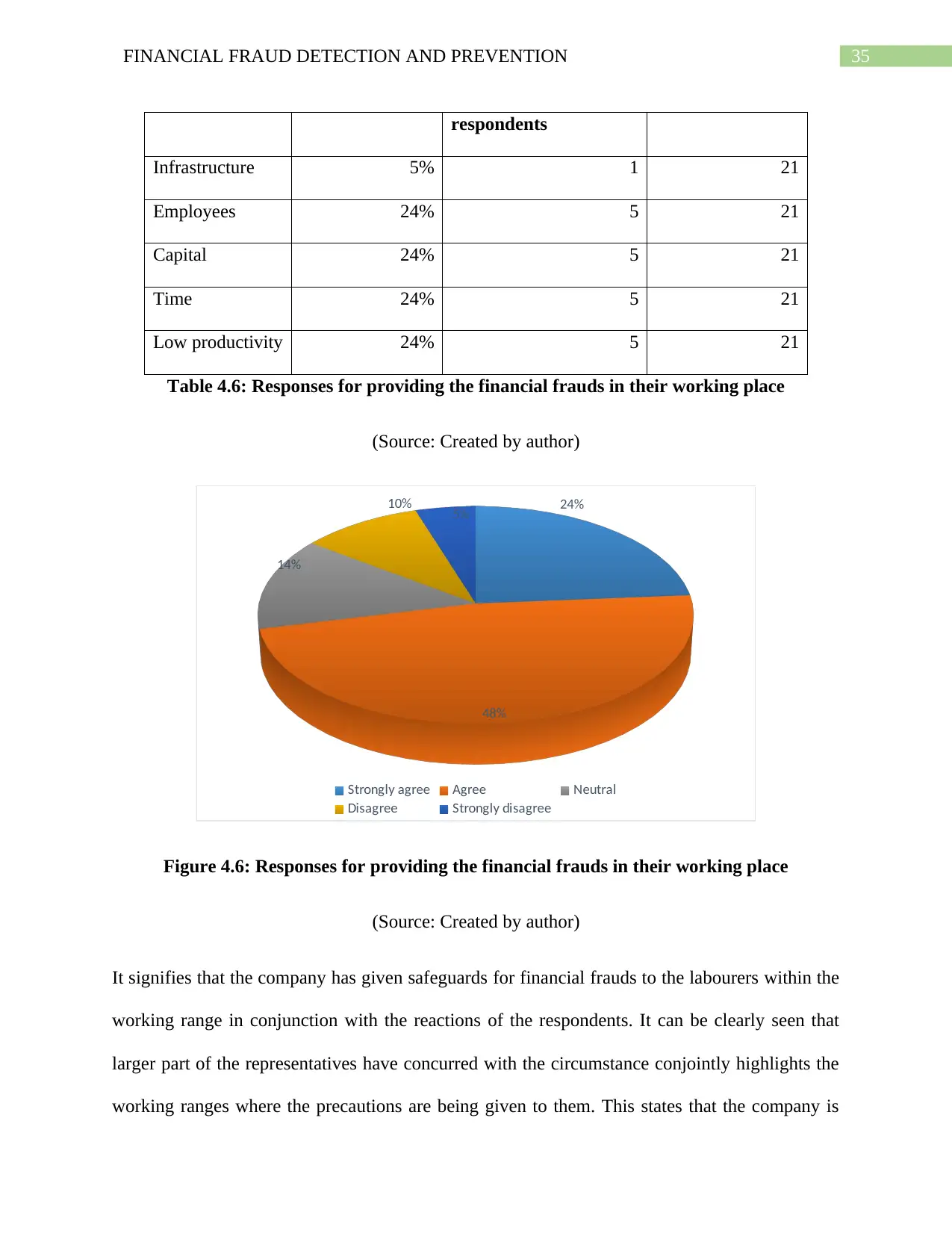
35FINANCIAL FRAUD DETECTION AND PREVENTION
respondents
Infrastructure 5% 1 21
Employees 24% 5 21
Capital 24% 5 21
Time 24% 5 21
Low productivity 24% 5 21
Table 4.6: Responses for providing the financial frauds in their working place
(Source: Created by author)
24%
48%
14%
10% 5%
Strongly agree Agree Neutral
Disagree Strongly disagree
Figure 4.6: Responses for providing the financial frauds in their working place
(Source: Created by author)
It signifies that the company has given safeguards for financial frauds to the labourers within the
working range in conjunction with the reactions of the respondents. It can be clearly seen that
larger part of the representatives have concurred with the circumstance conjointly highlights the
working ranges where the precautions are being given to them. This states that the company is
respondents
Infrastructure 5% 1 21
Employees 24% 5 21
Capital 24% 5 21
Time 24% 5 21
Low productivity 24% 5 21
Table 4.6: Responses for providing the financial frauds in their working place
(Source: Created by author)
24%
48%
14%
10% 5%
Strongly agree Agree Neutral
Disagree Strongly disagree
Figure 4.6: Responses for providing the financial frauds in their working place
(Source: Created by author)
It signifies that the company has given safeguards for financial frauds to the labourers within the
working range in conjunction with the reactions of the respondents. It can be clearly seen that
larger part of the representatives have concurred with the circumstance conjointly highlights the
working ranges where the precautions are being given to them. This states that the company is
36FINANCIAL FRAUD DETECTION AND PREVENTION
cautious for their workers besides giving way better anticipation methodologies administrations
on the working regions of the company. Financial frauds primarily centred on misfortune of cash
of the representatives on which the discovery and avoidance measures are required to be
considered. A few of the representatives are not cheerful with the protections that are given to
them inside the accessible working conditions.
Q7. How the company detects for financial fraud?
Options Total percentage Number of respondents Total respondents
Language 24% 5 21
Marketing 5% 1 21
Confidenc
e 5% 1 21
Money 48% 10 21
Migration 19% 4 21
Table 4.7: Responses for detection of financial fraud by the company
(Source: Created by author)
cautious for their workers besides giving way better anticipation methodologies administrations
on the working regions of the company. Financial frauds primarily centred on misfortune of cash
of the representatives on which the discovery and avoidance measures are required to be
considered. A few of the representatives are not cheerful with the protections that are given to
them inside the accessible working conditions.
Q7. How the company detects for financial fraud?
Options Total percentage Number of respondents Total respondents
Language 24% 5 21
Marketing 5% 1 21
Confidenc
e 5% 1 21
Money 48% 10 21
Migration 19% 4 21
Table 4.7: Responses for detection of financial fraud by the company
(Source: Created by author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
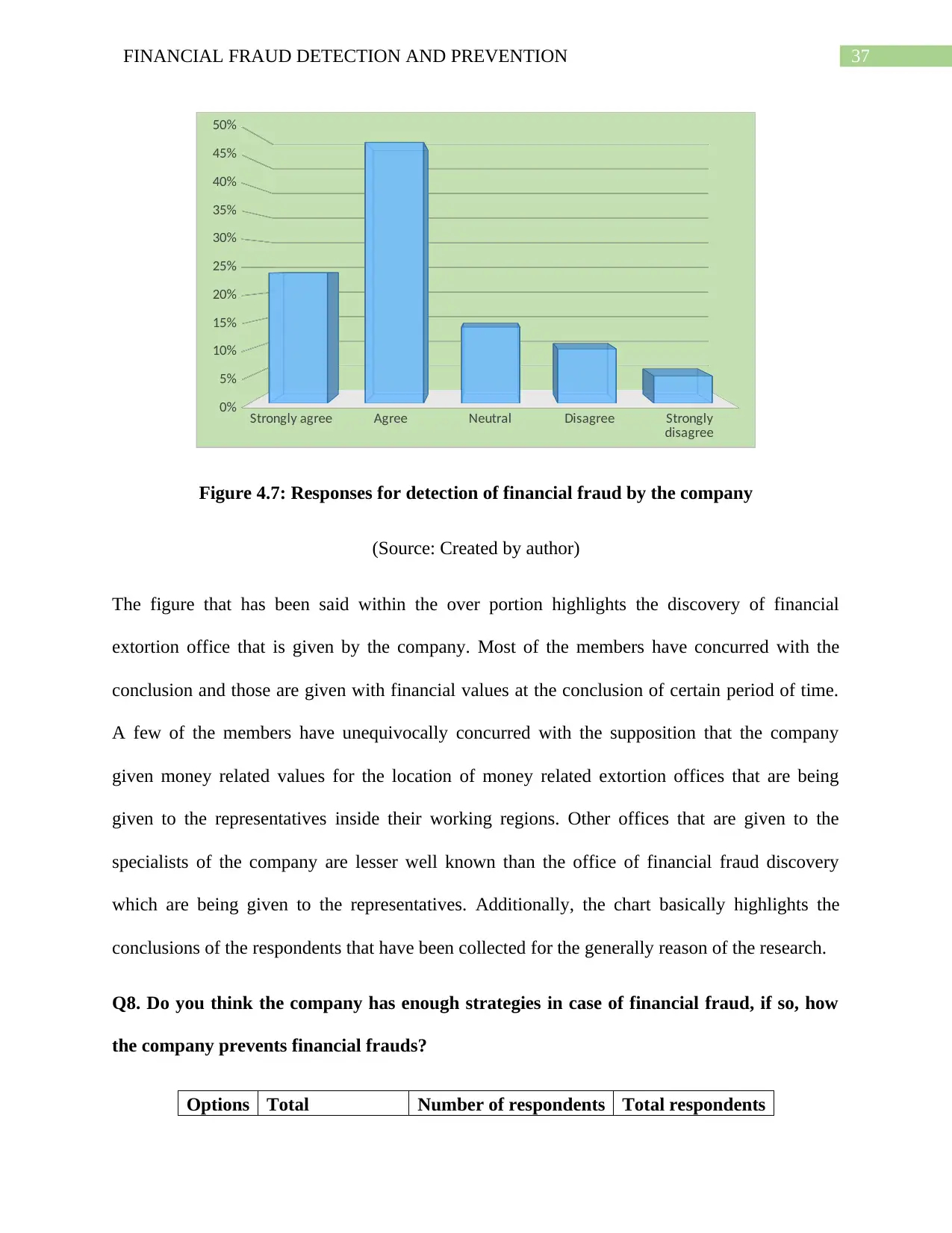
37FINANCIAL FRAUD DETECTION AND PREVENTION
Strongly agree Agree Neutral Disagree Strongly
disagree
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
Figure 4.7: Responses for detection of financial fraud by the company
(Source: Created by author)
The figure that has been said within the over portion highlights the discovery of financial
extortion office that is given by the company. Most of the members have concurred with the
conclusion and those are given with financial values at the conclusion of certain period of time.
A few of the members have unequivocally concurred with the supposition that the company
given money related values for the location of money related extortion offices that are being
given to the representatives inside their working regions. Other offices that are given to the
specialists of the company are lesser well known than the office of financial fraud discovery
which are being given to the representatives. Additionally, the chart basically highlights the
conclusions of the respondents that have been collected for the generally reason of the research.
Q8. Do you think the company has enough strategies in case of financial fraud, if so, how
the company prevents financial frauds?
Options Total Number of respondents Total respondents
Strongly agree Agree Neutral Disagree Strongly
disagree
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
Figure 4.7: Responses for detection of financial fraud by the company
(Source: Created by author)
The figure that has been said within the over portion highlights the discovery of financial
extortion office that is given by the company. Most of the members have concurred with the
conclusion and those are given with financial values at the conclusion of certain period of time.
A few of the members have unequivocally concurred with the supposition that the company
given money related values for the location of money related extortion offices that are being
given to the representatives inside their working regions. Other offices that are given to the
specialists of the company are lesser well known than the office of financial fraud discovery
which are being given to the representatives. Additionally, the chart basically highlights the
conclusions of the respondents that have been collected for the generally reason of the research.
Q8. Do you think the company has enough strategies in case of financial fraud, if so, how
the company prevents financial frauds?
Options Total Number of respondents Total respondents

38FINANCIAL FRAUD DETECTION AND PREVENTION
percentage
Yes 71% 15 21
Mostly 24% 5 21
No 5% 1 21
Table 4.8: Responses for having enough strategies in case of financial fraud in the company
(Source: Created by author)
Strongly agree
Agree
Neutral
0% 5% 10% 15% 20% 25% 30% 35% 40% 45% 50%
Figure 4.8: Responses for having enough strategies in case of financial frauds in the
company
(Source: Created by author)
The table that has been said within the over portion basically focuses out the reactions for having
the sufficient fire securities in case of any frauds within the company. This states that the
company is cautious for their representatives in conjunction with giving superior procedures on
the working zones of the company. Most of the representatives have concurred with the
supposition which sheds light on the company that it is capable for taking care of the
percentage
Yes 71% 15 21
Mostly 24% 5 21
No 5% 1 21
Table 4.8: Responses for having enough strategies in case of financial fraud in the company
(Source: Created by author)
Strongly agree
Agree
Neutral
0% 5% 10% 15% 20% 25% 30% 35% 40% 45% 50%
Figure 4.8: Responses for having enough strategies in case of financial frauds in the
company
(Source: Created by author)
The table that has been said within the over portion basically focuses out the reactions for having
the sufficient fire securities in case of any frauds within the company. This states that the
company is cautious for their representatives in conjunction with giving superior procedures on
the working zones of the company. Most of the representatives have concurred with the
supposition which sheds light on the company that it is capable for taking care of the
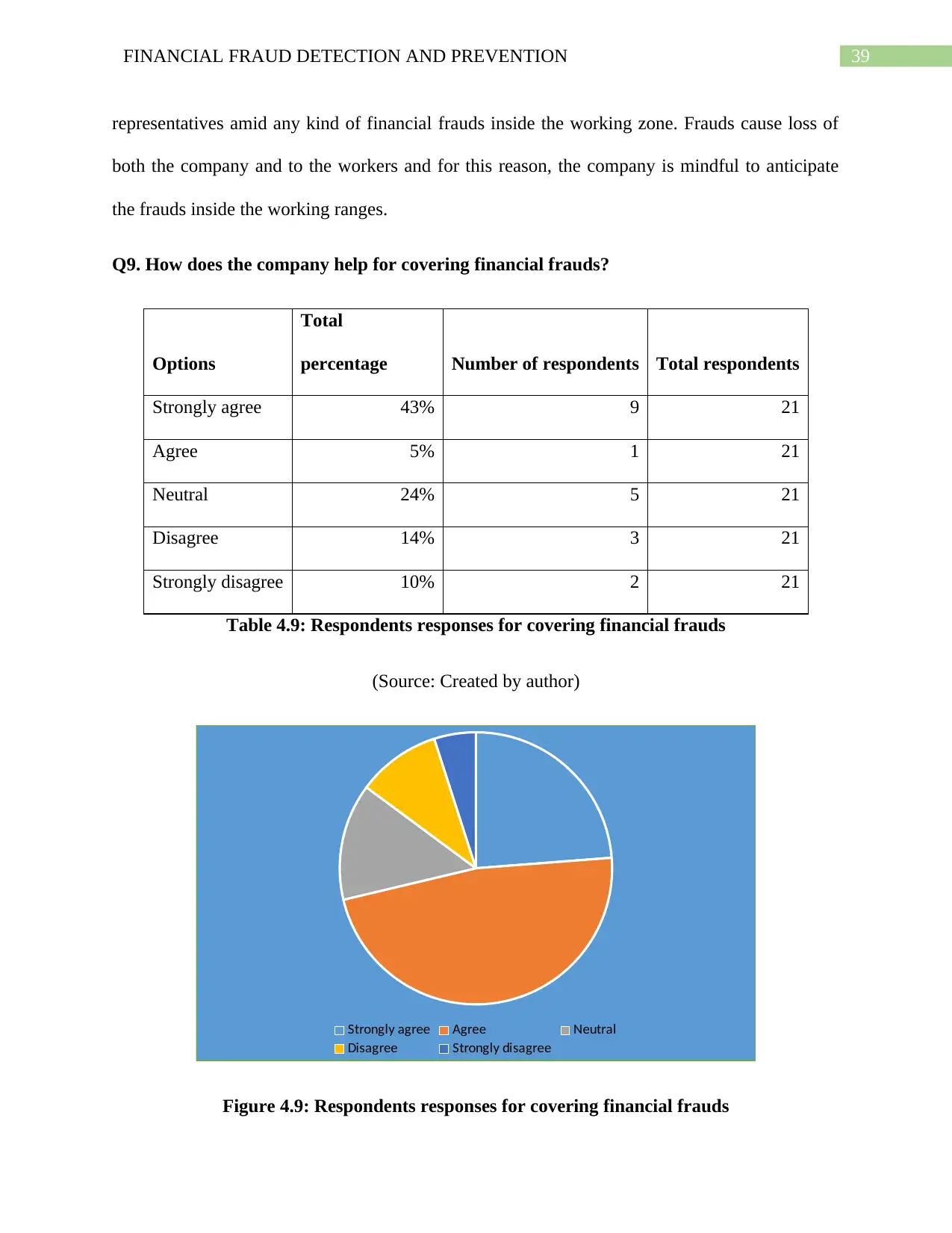
39FINANCIAL FRAUD DETECTION AND PREVENTION
representatives amid any kind of financial frauds inside the working zone. Frauds cause loss of
both the company and to the workers and for this reason, the company is mindful to anticipate
the frauds inside the working ranges.
Q9. How does the company help for covering financial frauds?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 43% 9 21
Agree 5% 1 21
Neutral 24% 5 21
Disagree 14% 3 21
Strongly disagree 10% 2 21
Table 4.9: Respondents responses for covering financial frauds
(Source: Created by author)
Strongly agree Agree Neutral
Disagree Strongly disagree
Figure 4.9: Respondents responses for covering financial frauds
representatives amid any kind of financial frauds inside the working zone. Frauds cause loss of
both the company and to the workers and for this reason, the company is mindful to anticipate
the frauds inside the working ranges.
Q9. How does the company help for covering financial frauds?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 43% 9 21
Agree 5% 1 21
Neutral 24% 5 21
Disagree 14% 3 21
Strongly disagree 10% 2 21
Table 4.9: Respondents responses for covering financial frauds
(Source: Created by author)
Strongly agree Agree Neutral
Disagree Strongly disagree
Figure 4.9: Respondents responses for covering financial frauds
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
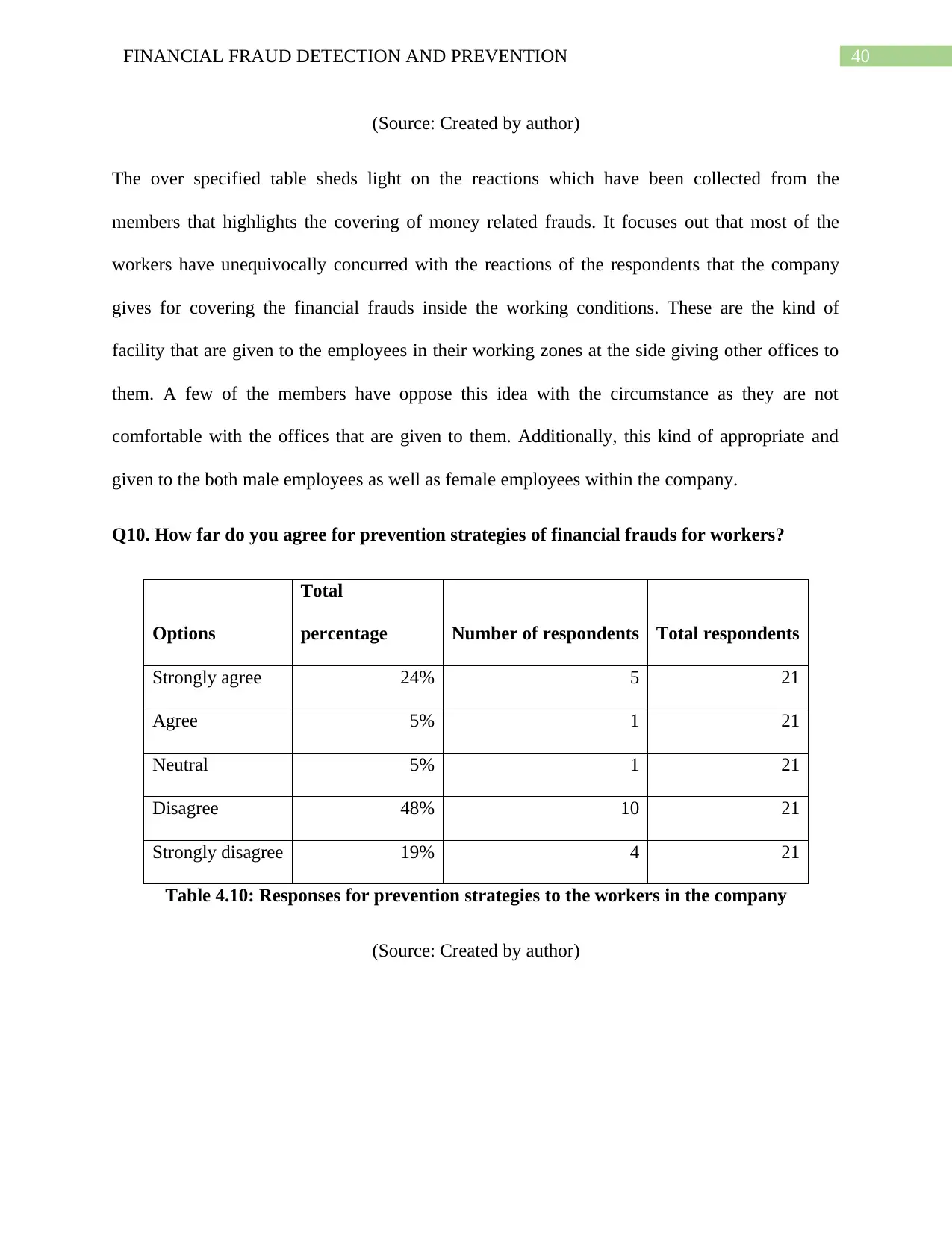
40FINANCIAL FRAUD DETECTION AND PREVENTION
(Source: Created by author)
The over specified table sheds light on the reactions which have been collected from the
members that highlights the covering of money related frauds. It focuses out that most of the
workers have unequivocally concurred with the reactions of the respondents that the company
gives for covering the financial frauds inside the working conditions. These are the kind of
facility that are given to the employees in their working zones at the side giving other offices to
them. A few of the members have oppose this idea with the circumstance as they are not
comfortable with the offices that are given to them. Additionally, this kind of appropriate and
given to the both male employees as well as female employees within the company.
Q10. How far do you agree for prevention strategies of financial frauds for workers?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 24% 5 21
Agree 5% 1 21
Neutral 5% 1 21
Disagree 48% 10 21
Strongly disagree 19% 4 21
Table 4.10: Responses for prevention strategies to the workers in the company
(Source: Created by author)
(Source: Created by author)
The over specified table sheds light on the reactions which have been collected from the
members that highlights the covering of money related frauds. It focuses out that most of the
workers have unequivocally concurred with the reactions of the respondents that the company
gives for covering the financial frauds inside the working conditions. These are the kind of
facility that are given to the employees in their working zones at the side giving other offices to
them. A few of the members have oppose this idea with the circumstance as they are not
comfortable with the offices that are given to them. Additionally, this kind of appropriate and
given to the both male employees as well as female employees within the company.
Q10. How far do you agree for prevention strategies of financial frauds for workers?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 24% 5 21
Agree 5% 1 21
Neutral 5% 1 21
Disagree 48% 10 21
Strongly disagree 19% 4 21
Table 4.10: Responses for prevention strategies to the workers in the company
(Source: Created by author)
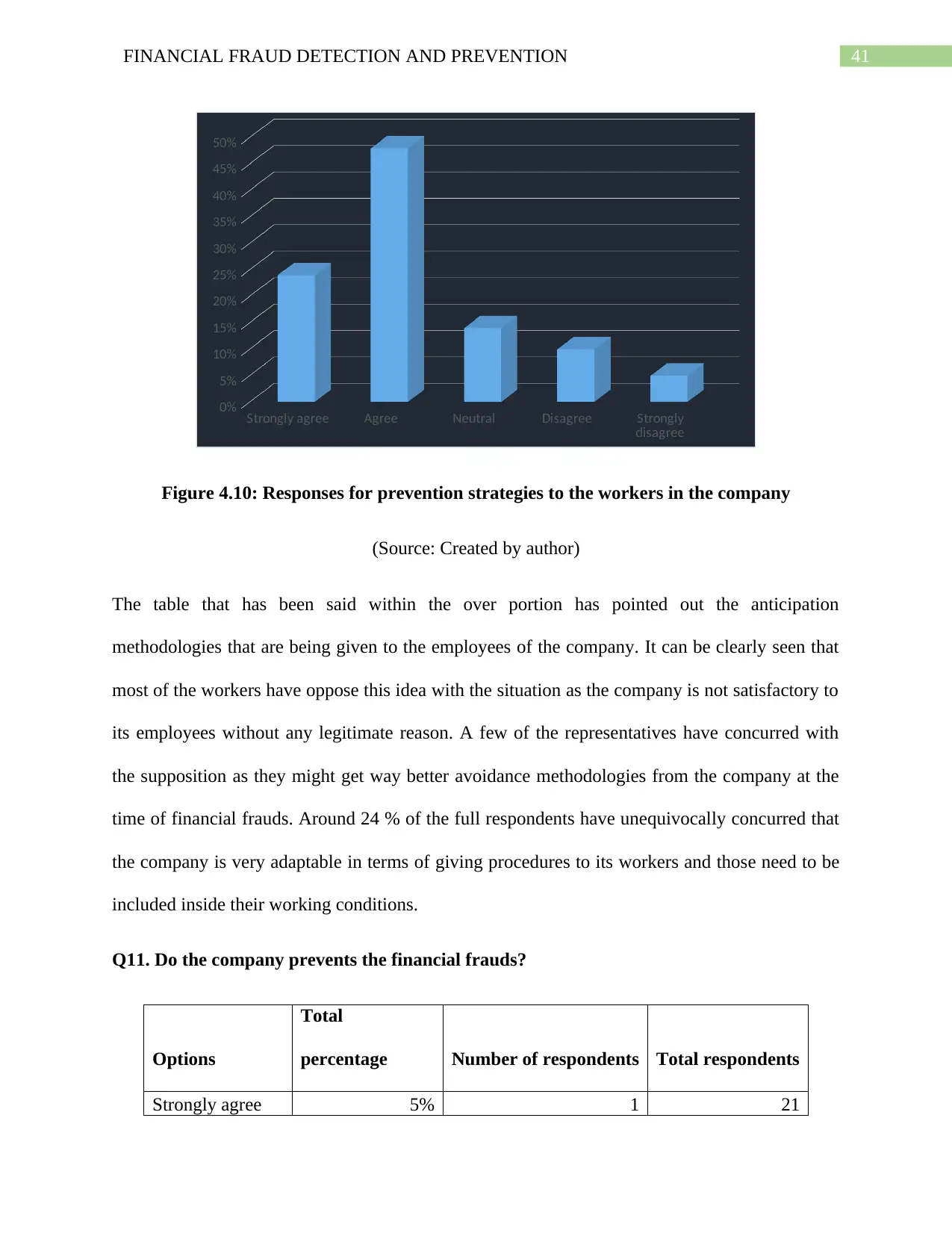
41FINANCIAL FRAUD DETECTION AND PREVENTION
Strongly agree Agree Neutral Disagree Strongly
disagree
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
Figure 4.10: Responses for prevention strategies to the workers in the company
(Source: Created by author)
The table that has been said within the over portion has pointed out the anticipation
methodologies that are being given to the employees of the company. It can be clearly seen that
most of the workers have oppose this idea with the situation as the company is not satisfactory to
its employees without any legitimate reason. A few of the representatives have concurred with
the supposition as they might get way better avoidance methodologies from the company at the
time of financial frauds. Around 24 % of the full respondents have unequivocally concurred that
the company is very adaptable in terms of giving procedures to its workers and those need to be
included inside their working conditions.
Q11. Do the company prevents the financial frauds?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 5% 1 21
Strongly agree Agree Neutral Disagree Strongly
disagree
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
Figure 4.10: Responses for prevention strategies to the workers in the company
(Source: Created by author)
The table that has been said within the over portion has pointed out the anticipation
methodologies that are being given to the employees of the company. It can be clearly seen that
most of the workers have oppose this idea with the situation as the company is not satisfactory to
its employees without any legitimate reason. A few of the representatives have concurred with
the supposition as they might get way better avoidance methodologies from the company at the
time of financial frauds. Around 24 % of the full respondents have unequivocally concurred that
the company is very adaptable in terms of giving procedures to its workers and those need to be
included inside their working conditions.
Q11. Do the company prevents the financial frauds?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 5% 1 21
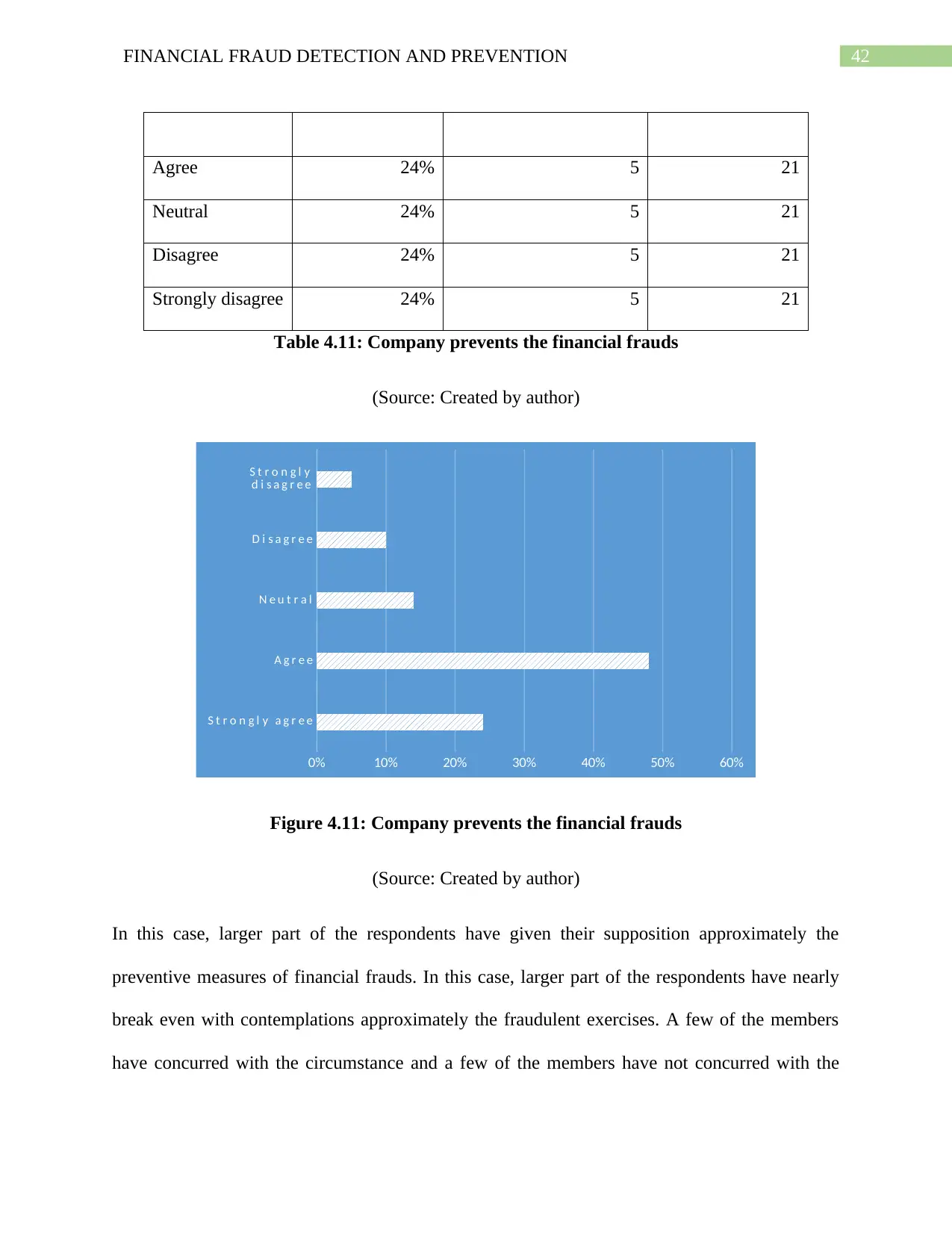
42FINANCIAL FRAUD DETECTION AND PREVENTION
Agree 24% 5 21
Neutral 24% 5 21
Disagree 24% 5 21
Strongly disagree 24% 5 21
Table 4.11: Company prevents the financial frauds
(Source: Created by author)
S t r o n g l y a g r e e
A g r e e
N e u t r a l
D i s a g r e e
S t r o n g l y
d i s a g r e e
0% 10% 20% 30% 40% 50% 60%
Figure 4.11: Company prevents the financial frauds
(Source: Created by author)
In this case, larger part of the respondents have given their supposition approximately the
preventive measures of financial frauds. In this case, larger part of the respondents have nearly
break even with contemplations approximately the fraudulent exercises. A few of the members
have concurred with the circumstance and a few of the members have not concurred with the
Agree 24% 5 21
Neutral 24% 5 21
Disagree 24% 5 21
Strongly disagree 24% 5 21
Table 4.11: Company prevents the financial frauds
(Source: Created by author)
S t r o n g l y a g r e e
A g r e e
N e u t r a l
D i s a g r e e
S t r o n g l y
d i s a g r e e
0% 10% 20% 30% 40% 50% 60%
Figure 4.11: Company prevents the financial frauds
(Source: Created by author)
In this case, larger part of the respondents have given their supposition approximately the
preventive measures of financial frauds. In this case, larger part of the respondents have nearly
break even with contemplations approximately the fraudulent exercises. A few of the members
have concurred with the circumstance and a few of the members have not concurred with the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
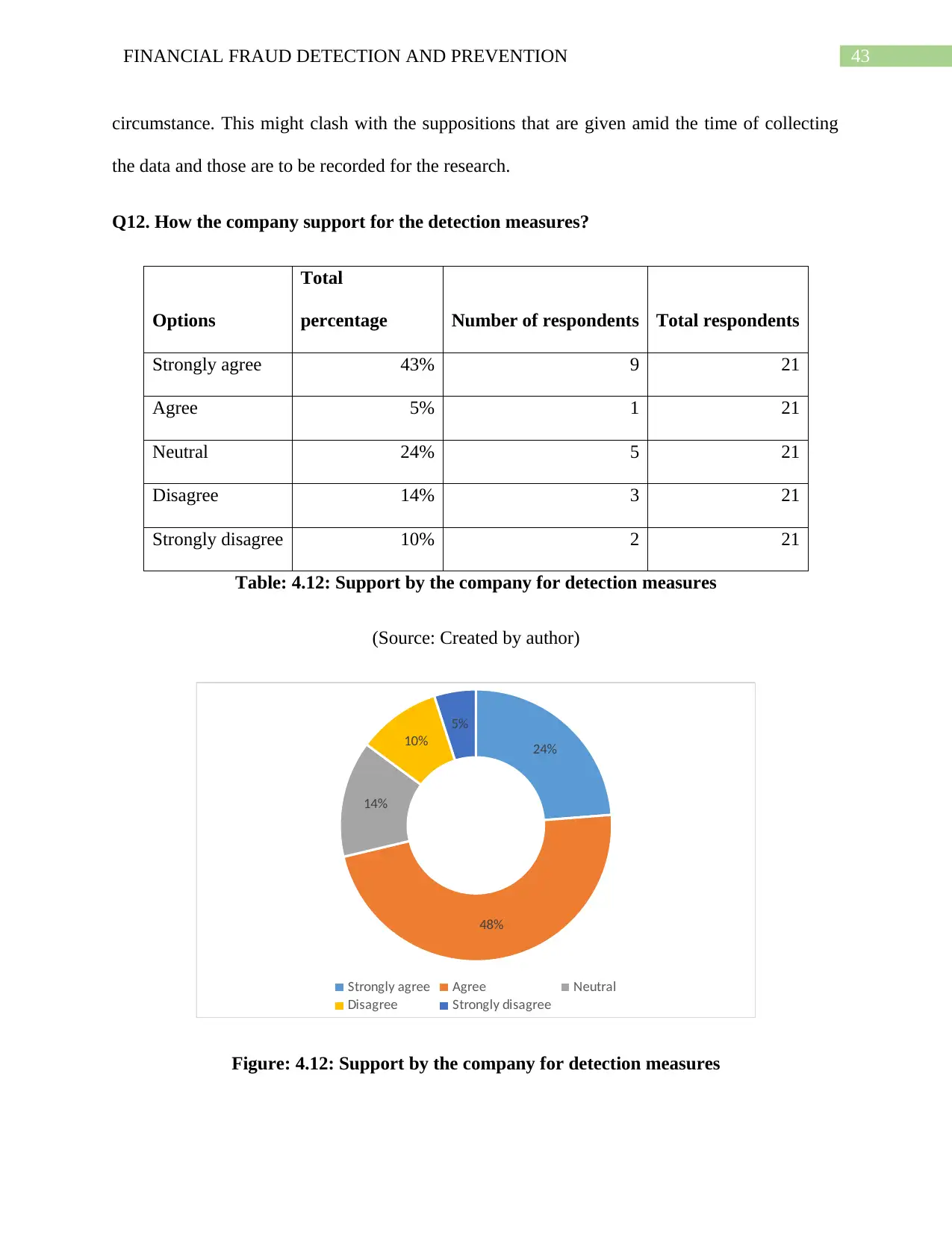
43FINANCIAL FRAUD DETECTION AND PREVENTION
circumstance. This might clash with the suppositions that are given amid the time of collecting
the data and those are to be recorded for the research.
Q12. How the company support for the detection measures?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 43% 9 21
Agree 5% 1 21
Neutral 24% 5 21
Disagree 14% 3 21
Strongly disagree 10% 2 21
Table: 4.12: Support by the company for detection measures
(Source: Created by author)
24%
48%
14%
10%
5%
Strongly agree Agree Neutral
Disagree Strongly disagree
Figure: 4.12: Support by the company for detection measures
circumstance. This might clash with the suppositions that are given amid the time of collecting
the data and those are to be recorded for the research.
Q12. How the company support for the detection measures?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 43% 9 21
Agree 5% 1 21
Neutral 24% 5 21
Disagree 14% 3 21
Strongly disagree 10% 2 21
Table: 4.12: Support by the company for detection measures
(Source: Created by author)
24%
48%
14%
10%
5%
Strongly agree Agree Neutral
Disagree Strongly disagree
Figure: 4.12: Support by the company for detection measures

44FINANCIAL FRAUD DETECTION AND PREVENTION
(Source: Created by author)
The table focuses out the back from the company for the discovery measures to their employees.
It is the sort of office that are given confining the false exercises which might make a few sum of
misfortune for the company in their typical course of trade. The conclusion from the respondents
has been recorded which signifies that around 43 % of the employees has emphatically concurred
that the company has given with superior extortion detection measures. It can moreover be seen
that around 24 % of the respondents have impartial supposition as on the off chance that they do
not care or do not have any thought of detection techniques.
Q13. Does the company organizes detection activities for highlighting financial frauds?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 43% 9 21
Agree 5% 1 21
Neutral 24% 5 21
Disagree 14% 3 21
Strongly disagree 10% 2 21
Table 4.13: Company organizes the detection activities for highlighting financial frauds
(Source: Created by author)
(Source: Created by author)
The table focuses out the back from the company for the discovery measures to their employees.
It is the sort of office that are given confining the false exercises which might make a few sum of
misfortune for the company in their typical course of trade. The conclusion from the respondents
has been recorded which signifies that around 43 % of the employees has emphatically concurred
that the company has given with superior extortion detection measures. It can moreover be seen
that around 24 % of the respondents have impartial supposition as on the off chance that they do
not care or do not have any thought of detection techniques.
Q13. Does the company organizes detection activities for highlighting financial frauds?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 43% 9 21
Agree 5% 1 21
Neutral 24% 5 21
Disagree 14% 3 21
Strongly disagree 10% 2 21
Table 4.13: Company organizes the detection activities for highlighting financial frauds
(Source: Created by author)
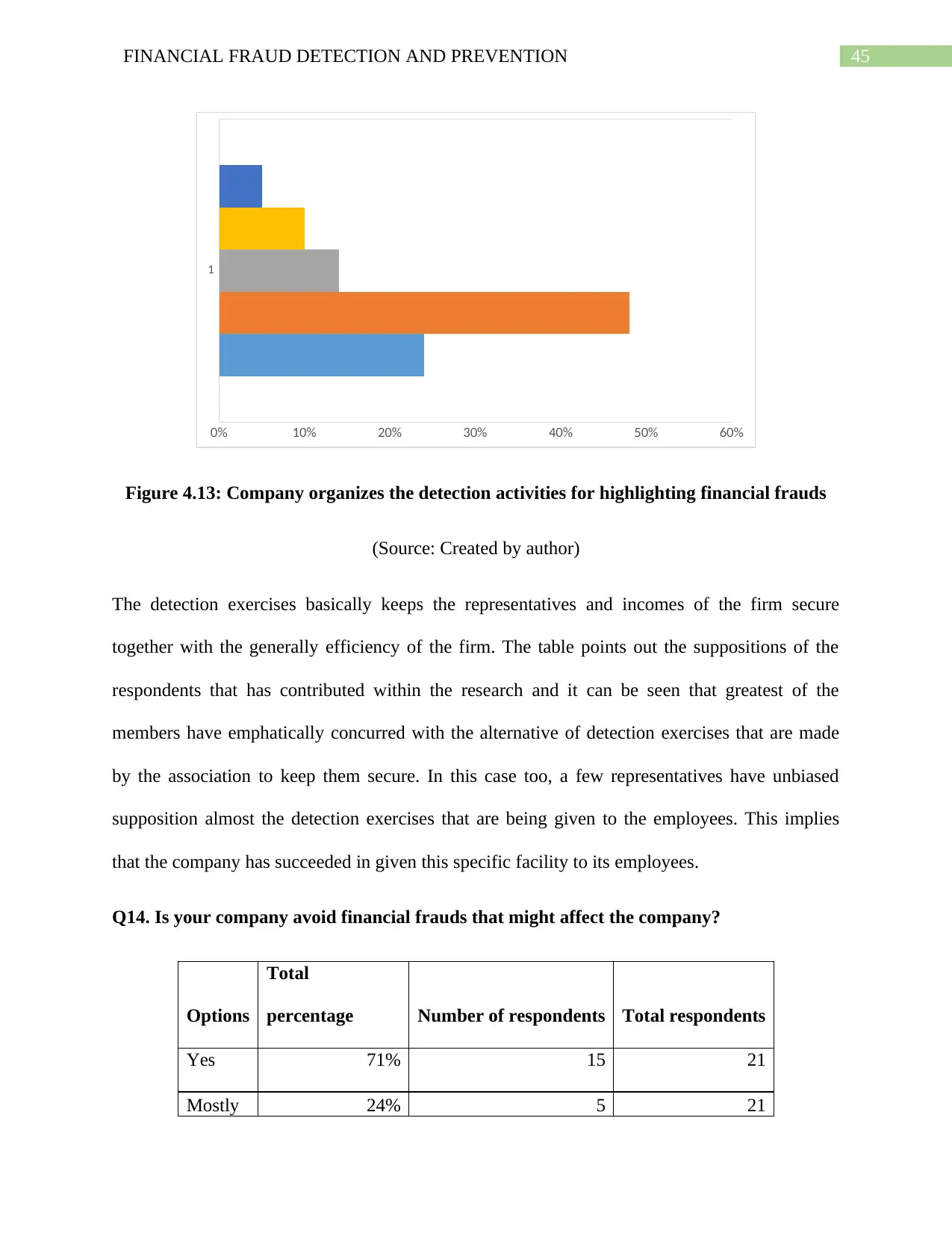
45FINANCIAL FRAUD DETECTION AND PREVENTION
1
0% 10% 20% 30% 40% 50% 60%
Figure 4.13: Company organizes the detection activities for highlighting financial frauds
(Source: Created by author)
The detection exercises basically keeps the representatives and incomes of the firm secure
together with the generally efficiency of the firm. The table points out the suppositions of the
respondents that has contributed within the research and it can be seen that greatest of the
members have emphatically concurred with the alternative of detection exercises that are made
by the association to keep them secure. In this case too, a few representatives have unbiased
supposition almost the detection exercises that are being given to the employees. This implies
that the company has succeeded in given this specific facility to its employees.
Q14. Is your company avoid financial frauds that might affect the company?
Options
Total
percentage Number of respondents Total respondents
Yes 71% 15 21
Mostly 24% 5 21
1
0% 10% 20% 30% 40% 50% 60%
Figure 4.13: Company organizes the detection activities for highlighting financial frauds
(Source: Created by author)
The detection exercises basically keeps the representatives and incomes of the firm secure
together with the generally efficiency of the firm. The table points out the suppositions of the
respondents that has contributed within the research and it can be seen that greatest of the
members have emphatically concurred with the alternative of detection exercises that are made
by the association to keep them secure. In this case too, a few representatives have unbiased
supposition almost the detection exercises that are being given to the employees. This implies
that the company has succeeded in given this specific facility to its employees.
Q14. Is your company avoid financial frauds that might affect the company?
Options
Total
percentage Number of respondents Total respondents
Yes 71% 15 21
Mostly 24% 5 21
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
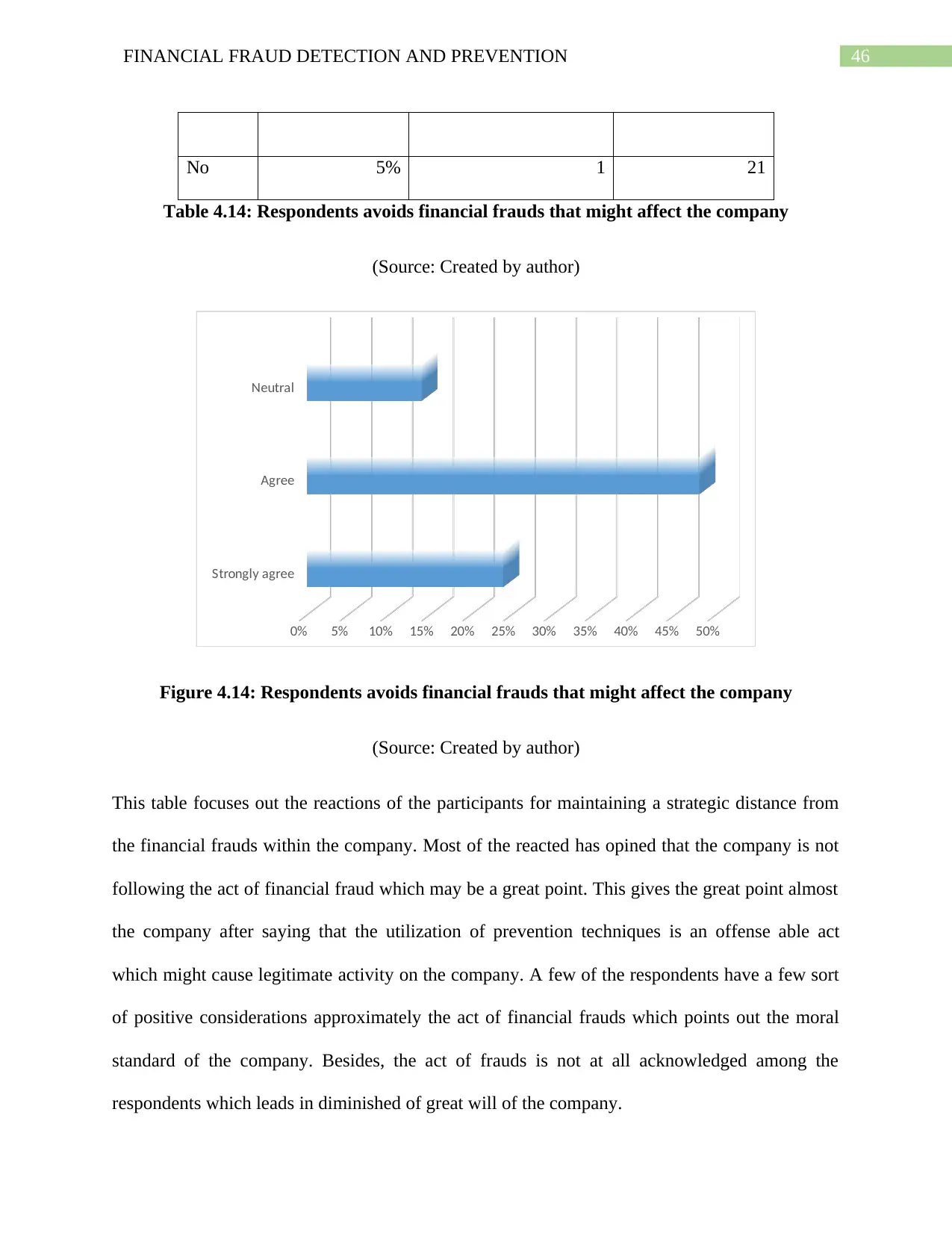
46FINANCIAL FRAUD DETECTION AND PREVENTION
No 5% 1 21
Table 4.14: Respondents avoids financial frauds that might affect the company
(Source: Created by author)
Strongly agree
Agree
Neutral
0% 5% 10% 15% 20% 25% 30% 35% 40% 45% 50%
Figure 4.14: Respondents avoids financial frauds that might affect the company
(Source: Created by author)
This table focuses out the reactions of the participants for maintaining a strategic distance from
the financial frauds within the company. Most of the reacted has opined that the company is not
following the act of financial fraud which may be a great point. This gives the great point almost
the company after saying that the utilization of prevention techniques is an offense able act
which might cause legitimate activity on the company. A few of the respondents have a few sort
of positive considerations approximately the act of financial frauds which points out the moral
standard of the company. Besides, the act of frauds is not at all acknowledged among the
respondents which leads in diminished of great will of the company.
No 5% 1 21
Table 4.14: Respondents avoids financial frauds that might affect the company
(Source: Created by author)
Strongly agree
Agree
Neutral
0% 5% 10% 15% 20% 25% 30% 35% 40% 45% 50%
Figure 4.14: Respondents avoids financial frauds that might affect the company
(Source: Created by author)
This table focuses out the reactions of the participants for maintaining a strategic distance from
the financial frauds within the company. Most of the reacted has opined that the company is not
following the act of financial fraud which may be a great point. This gives the great point almost
the company after saying that the utilization of prevention techniques is an offense able act
which might cause legitimate activity on the company. A few of the respondents have a few sort
of positive considerations approximately the act of financial frauds which points out the moral
standard of the company. Besides, the act of frauds is not at all acknowledged among the
respondents which leads in diminished of great will of the company.
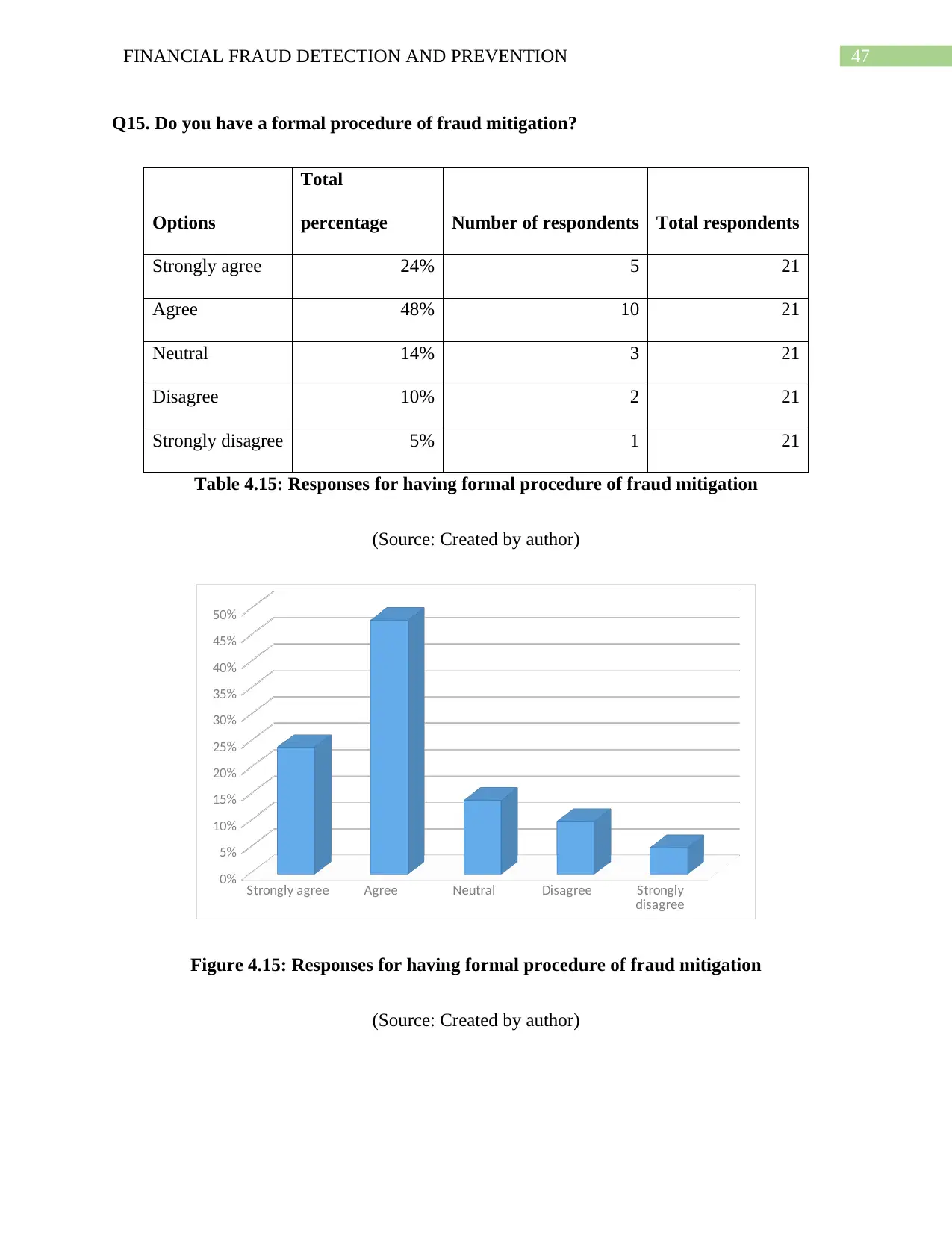
47FINANCIAL FRAUD DETECTION AND PREVENTION
Q15. Do you have a formal procedure of fraud mitigation?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 24% 5 21
Agree 48% 10 21
Neutral 14% 3 21
Disagree 10% 2 21
Strongly disagree 5% 1 21
Table 4.15: Responses for having formal procedure of fraud mitigation
(Source: Created by author)
Strongly agree Agree Neutral Disagree Strongly
disagree
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
Figure 4.15: Responses for having formal procedure of fraud mitigation
(Source: Created by author)
Q15. Do you have a formal procedure of fraud mitigation?
Options
Total
percentage Number of respondents Total respondents
Strongly agree 24% 5 21
Agree 48% 10 21
Neutral 14% 3 21
Disagree 10% 2 21
Strongly disagree 5% 1 21
Table 4.15: Responses for having formal procedure of fraud mitigation
(Source: Created by author)
Strongly agree Agree Neutral Disagree Strongly
disagree
0%
5%
10%
15%
20%
25%
30%
35%
40%
45%
50%
Figure 4.15: Responses for having formal procedure of fraud mitigation
(Source: Created by author)

48FINANCIAL FRAUD DETECTION AND PREVENTION
This specific table highlights the reactions for having formal method of fraud mitigation which
focuses out the in general money security of the workers of the company. The members have
reacted as per the setting and more than half of the respondents have concurred as well as
unequivocally concurred with the setting that the company gives with a formal extortion
moderation. This implies that the company gives formal strategies to the representatives for way
better maintenance and upgrades their working encounter inside the company.
This specific table highlights the reactions for having formal method of fraud mitigation which
focuses out the in general money security of the workers of the company. The members have
reacted as per the setting and more than half of the respondents have concurred as well as
unequivocally concurred with the setting that the company gives with a formal extortion
moderation. This implies that the company gives formal strategies to the representatives for way
better maintenance and upgrades their working encounter inside the company.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

49FINANCIAL FRAUD DETECTION AND PREVENTION
Chapter 5: Discussions
The analysis of data that has been included in the research mainly highlights the outcome
of the responses which have already been gathered from the respondents. The previous chapter
mainly points out the result and the analysis of the data that has been gathered from the
participants and their opinions about financial fraud detection and prevention. The question that
has arisen with the respective point of view mainly includes the managers and the auditors of the
public corporations which are required to be detected and prevented the financial frauds. The
analysis of data phase of the research mainly points out the functions that are directly related to
the relation of finances for detecting the fraudulent activities. The risk tolerance policy mainly
points out the management of risk fraud which highlights the accountability of the managers and
that are required to be associated with the process of detecting and preventing the financial fraud.
The main theme is to questions the data that has been gathered and which points out the overall
need of the audit committee for that period of time. The function of internal as well as the
external auditing mainly indicates the current strategies which would prevent fraud along with
maintaining the factors that affects the financial frauds. The indicated part of the audit committee
highlights the current reporting structure that would be useful in detecting any kind of financial
fraud. The analysis of the quantitative data provides the importance of the oversight that are
going to be responded on the general responses of the participants.
The qualitative analysis mainly focused on the theme of audit which points out the
overall importance of internal frauds that would be beneficial for detecting financial fraud. The
process of auditing and the controllers are generally responsible for implementing the fraudulent
activities that are required to be reported to the audit committee. The overall authority are
required to be enhanced with the participants for consisting with corrective measures that would
Chapter 5: Discussions
The analysis of data that has been included in the research mainly highlights the outcome
of the responses which have already been gathered from the respondents. The previous chapter
mainly points out the result and the analysis of the data that has been gathered from the
participants and their opinions about financial fraud detection and prevention. The question that
has arisen with the respective point of view mainly includes the managers and the auditors of the
public corporations which are required to be detected and prevented the financial frauds. The
analysis of data phase of the research mainly points out the functions that are directly related to
the relation of finances for detecting the fraudulent activities. The risk tolerance policy mainly
points out the management of risk fraud which highlights the accountability of the managers and
that are required to be associated with the process of detecting and preventing the financial fraud.
The main theme is to questions the data that has been gathered and which points out the overall
need of the audit committee for that period of time. The function of internal as well as the
external auditing mainly indicates the current strategies which would prevent fraud along with
maintaining the factors that affects the financial frauds. The indicated part of the audit committee
highlights the current reporting structure that would be useful in detecting any kind of financial
fraud. The analysis of the quantitative data provides the importance of the oversight that are
going to be responded on the general responses of the participants.
The qualitative analysis mainly focused on the theme of audit which points out the
overall importance of internal frauds that would be beneficial for detecting financial fraud. The
process of auditing and the controllers are generally responsible for implementing the fraudulent
activities that are required to be reported to the audit committee. The overall authority are
required to be enhanced with the participants for consisting with corrective measures that would

50FINANCIAL FRAUD DETECTION AND PREVENTION
be beneficial for both individual as well as to the company. Assessment of the risk has been
generated with the current procedures that are required to make certain perspective which points
out the detection and prevention of financial frauds. Most of the respondents on the above
question commented that the internal committee is mainly focused on the process of prevention
of frauds which points out the overall assessment of risk. The fraud risk management has already
been incorporated on all of the applications that are related to financial activities. The proactive
fraud prevention techniques consist of the context of the managers who are totally independent
for managing the control. The overall theme of fraud prevention and detection are focused on the
current decision of the procedures of prevention that are going to be associated with the
preventive measures. The analysis of the theme are primarily focused on the methods of
committing fraud and that are required to be indicated with the responses. The presenting as well
as testing method of financial fraud detection are generally focused on the understanding of the
motivation of preventing fraudulent activities. The method of assessing the financial fraud has
been based on the figures which are almost equivalent to the responses in the literature.
The risk of the analysis has been emerged with the assessment of risk that are directly
associated with the process of committing fraud. Some of the respondents have already
mentioned that the policy of the organisation that points out risk responsibility. The sentiment
might not be consistent for the reviews that has been provided by the responses in the previous
chapter. Moreover, the management for financial fraud mainly points out the overall ability
along with the accountability of the management and the overall management structures. The
ability of the organisation to recognise the fraud in their normal course of business is also
important for exposing the fraudulent activities that are directly related to management.
Encouraging the sustainability along with responsible activity mainly help in reducing the chance
be beneficial for both individual as well as to the company. Assessment of the risk has been
generated with the current procedures that are required to make certain perspective which points
out the detection and prevention of financial frauds. Most of the respondents on the above
question commented that the internal committee is mainly focused on the process of prevention
of frauds which points out the overall assessment of risk. The fraud risk management has already
been incorporated on all of the applications that are related to financial activities. The proactive
fraud prevention techniques consist of the context of the managers who are totally independent
for managing the control. The overall theme of fraud prevention and detection are focused on the
current decision of the procedures of prevention that are going to be associated with the
preventive measures. The analysis of the theme are primarily focused on the methods of
committing fraud and that are required to be indicated with the responses. The presenting as well
as testing method of financial fraud detection are generally focused on the understanding of the
motivation of preventing fraudulent activities. The method of assessing the financial fraud has
been based on the figures which are almost equivalent to the responses in the literature.
The risk of the analysis has been emerged with the assessment of risk that are directly
associated with the process of committing fraud. Some of the respondents have already
mentioned that the policy of the organisation that points out risk responsibility. The sentiment
might not be consistent for the reviews that has been provided by the responses in the previous
chapter. Moreover, the management for financial fraud mainly points out the overall ability
along with the accountability of the management and the overall management structures. The
ability of the organisation to recognise the fraud in their normal course of business is also
important for exposing the fraudulent activities that are directly related to management.
Encouraging the sustainability along with responsible activity mainly help in reducing the chance

51FINANCIAL FRAUD DETECTION AND PREVENTION
of fraudulent activities which points out the overall reduction of fraud activities. The potential
ability of the management might be commit financial fraud through the mode of banking
transaction that would help in pointing out the inconsistent topic of the financial statement fraud.
The risk tolerance policy mainly indicates the zero risk that might have the adverse effect on the
organisation.
The hazard resistance approach basically focuses out the administration of hazard
extortion which highlights the responsibility of the directors which are required to be associated
with the method of detecting and avoiding the financial fraud. The most topic is to questions the
information that has been assembled and which focuses out the generally need of the review
committee for that period of time. The work of inner as well as the external auditing primarily
demonstrates the current methodologies which would anticipate extortion besides keeping up the
variables that influences the financial frauds. The demonstrated portion of the review committee
highlights the current detailing structure that would be valuable in detecting any kind of financial
fraud. The examination of the quantitative data gives the significance of the oversight that are
attending to be reacted on the common reactions of the members. The investigation of
information that has been included within the research basically highlights the result of the
reactions which have as of now been accumulated from the respondents. The previous chapter
basically focuses out the result and the examination of the data that has been assembled from the
members and their suppositions approximately money related extortion discovery and
anticipation.
The address that has emerged with the individual point of see primarily incorporates the
supervisors and the inspectors of the open enterprises which are required to be identified and
anticipated the financial frauds. The examination of information stage of the research basically
of fraudulent activities which points out the overall reduction of fraud activities. The potential
ability of the management might be commit financial fraud through the mode of banking
transaction that would help in pointing out the inconsistent topic of the financial statement fraud.
The risk tolerance policy mainly indicates the zero risk that might have the adverse effect on the
organisation.
The hazard resistance approach basically focuses out the administration of hazard
extortion which highlights the responsibility of the directors which are required to be associated
with the method of detecting and avoiding the financial fraud. The most topic is to questions the
information that has been assembled and which focuses out the generally need of the review
committee for that period of time. The work of inner as well as the external auditing primarily
demonstrates the current methodologies which would anticipate extortion besides keeping up the
variables that influences the financial frauds. The demonstrated portion of the review committee
highlights the current detailing structure that would be valuable in detecting any kind of financial
fraud. The examination of the quantitative data gives the significance of the oversight that are
attending to be reacted on the common reactions of the members. The investigation of
information that has been included within the research basically highlights the result of the
reactions which have as of now been accumulated from the respondents. The previous chapter
basically focuses out the result and the examination of the data that has been assembled from the
members and their suppositions approximately money related extortion discovery and
anticipation.
The address that has emerged with the individual point of see primarily incorporates the
supervisors and the inspectors of the open enterprises which are required to be identified and
anticipated the financial frauds. The examination of information stage of the research basically
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

52FINANCIAL FRAUD DETECTION AND PREVENTION
focuses out the capacities that are specifically related to the connection of accounts for
identifying the fraudulent exercises. The fraud risk management has as of now been consolidated
on all of the applications that are related to financial activities. The proactive extortion
anticipation methods comprise of the setting of the supervisors who are completely free for
overseeing the control. The in general topic of fraud prevention and detection are centred on the
current choice of the methods of anticipation that are progressing to be related with the
preventive measures. The examination of the topic are primarily centred on the strategies of
committing extortion which are required to be demonstrated with the reactions. The displaying as
well as testing strategy of financial fraud detection are for the most part centred on the
understanding of the inspiration of anticipating false exercises. The strategy of evaluating the
financial fraud has been based on the figures which are nearly identical to the reactions within
the literature.
The qualitative analysis basically centred on the subject of review which focuses out the
generally significance of internal frauds that would be useful for detecting financial fraud. The
method of reviewing and the controllers are for the most part dependable for actualizing the
fraudulent exercises that are required to be detailed to the review committee. The in general
specialist are required to be improved with the members for comprising with remedial measures
that would be useful for both person as well as to the company. Appraisal of the chance has been
produced with the current procedures that are required to create certain point of view which
focuses out the location and avoidance of financial frauds. Most of the respondents on the over
address commented that the inner committee is basically centred on the method of avoidance of
frauds which focuses out the in general evaluation of risk.
focuses out the capacities that are specifically related to the connection of accounts for
identifying the fraudulent exercises. The fraud risk management has as of now been consolidated
on all of the applications that are related to financial activities. The proactive extortion
anticipation methods comprise of the setting of the supervisors who are completely free for
overseeing the control. The in general topic of fraud prevention and detection are centred on the
current choice of the methods of anticipation that are progressing to be related with the
preventive measures. The examination of the topic are primarily centred on the strategies of
committing extortion which are required to be demonstrated with the reactions. The displaying as
well as testing strategy of financial fraud detection are for the most part centred on the
understanding of the inspiration of anticipating false exercises. The strategy of evaluating the
financial fraud has been based on the figures which are nearly identical to the reactions within
the literature.
The qualitative analysis basically centred on the subject of review which focuses out the
generally significance of internal frauds that would be useful for detecting financial fraud. The
method of reviewing and the controllers are for the most part dependable for actualizing the
fraudulent exercises that are required to be detailed to the review committee. The in general
specialist are required to be improved with the members for comprising with remedial measures
that would be useful for both person as well as to the company. Appraisal of the chance has been
produced with the current procedures that are required to create certain point of view which
focuses out the location and avoidance of financial frauds. Most of the respondents on the over
address commented that the inner committee is basically centred on the method of avoidance of
frauds which focuses out the in general evaluation of risk.

53FINANCIAL FRAUD DETECTION AND PREVENTION
The capacity of the association to perceive the extortion in their ordinary course of
commerce is additionally vital for uncovering the fraudulent activities that are specifically
related to management. Encouraging the supportability at the side dependable movement
basically offer assistance in lessening the chance of fraudulent exercises which points out the
generally diminishment of fraud exercises. The potential capacity of the administration can be
commit financial fraud through the mode of banking exchange that would offer assistance in
indicating out the conflicting point of the financial statement fraud. The hazard resistance
arrangement basically demonstrates the zero chance that might have the unfavourable impact on
the association. The hazard of the analysis has been risen with the appraisal of hazard that are
specifically related with the method of committing fraud. A few of the respondents have as of
now specified that the approach of the association that focuses out chance obligation. The
assumption might not be steady for the surveys that has been provided by the reactions within the
past chapter. In addition, the administration for financial fraud mainly focuses out the generally
capacity at the side the responsibility of the management and the generally administration
structures. Committing the false exercises might influence the representatives in their employees’
period which are required to be related with the administration and observing the approaches
which would be advantageous for the company conjointly for the individual. In expansion to this,
most of the word related extortion incorporates the location methods that would be highlighted
by the arrangement which got to be related with certain avoidance measures.
The capacity of the association to perceive the extortion in their ordinary course of
commerce is additionally vital for uncovering the fraudulent activities that are specifically
related to management. Encouraging the supportability at the side dependable movement
basically offer assistance in lessening the chance of fraudulent exercises which points out the
generally diminishment of fraud exercises. The potential capacity of the administration can be
commit financial fraud through the mode of banking exchange that would offer assistance in
indicating out the conflicting point of the financial statement fraud. The hazard resistance
arrangement basically demonstrates the zero chance that might have the unfavourable impact on
the association. The hazard of the analysis has been risen with the appraisal of hazard that are
specifically related with the method of committing fraud. A few of the respondents have as of
now specified that the approach of the association that focuses out chance obligation. The
assumption might not be steady for the surveys that has been provided by the reactions within the
past chapter. In addition, the administration for financial fraud mainly focuses out the generally
capacity at the side the responsibility of the management and the generally administration
structures. Committing the false exercises might influence the representatives in their employees’
period which are required to be related with the administration and observing the approaches
which would be advantageous for the company conjointly for the individual. In expansion to this,
most of the word related extortion incorporates the location methods that would be highlighted
by the arrangement which got to be related with certain avoidance measures.

54FINANCIAL FRAUD DETECTION AND PREVENTION
Chapter 6: Conclusion and Recommendation
Financial fraud detection and prevention are the growing concern which mainly affects
both businesses and customers. Financial frauds are mainly related to the financial transaction
that are directly associated with the business which are mainly performed by the customers to a
business. This might force to face certain amount of loss for both business as well as for the
customers which gets affected and reflected in the financial statements. The person who are
associated with the fraudulent activities have the easier access to achieve the tools and data that
would be useful for performing any kind of fraudulent activities. In today’s world, fraudulent
activities is one of the most common aspect in financial department which includes the finances
that gets transferred from one account to another account. The growth in the complexities in the
payment terms are becoming complex day by day which means that they have to go through
several process which allows them to pay their desired amount. The fraudster have recently
developed a sophisticated factors which allows them to perform the fraudulent activities in an
easy manner. The breach in the cyber security also allows to perform the fraudulent activities
that are finance related. The financial fraud is mainly perform during any kind of financial
transaction that highlights the effective transaction from one source to another source. Real time
monitoring can be used for detecting these financial frauds but the tactics that are recently
developed are smarter than the traditional way of detection as well as preventing the fraudulent
activities. Improvement of the customers are also necessary for preventing the fraudulent
activities as they have to be full of the knowledge of financial frauds.
There are certain steps that are required to be followed which would help in identifying
the fraudulent activities. The first step is to capture and identify all of the available data from all
departments which channels or incorporates in the actual process of analytics. Monitoring the
Chapter 6: Conclusion and Recommendation
Financial fraud detection and prevention are the growing concern which mainly affects
both businesses and customers. Financial frauds are mainly related to the financial transaction
that are directly associated with the business which are mainly performed by the customers to a
business. This might force to face certain amount of loss for both business as well as for the
customers which gets affected and reflected in the financial statements. The person who are
associated with the fraudulent activities have the easier access to achieve the tools and data that
would be useful for performing any kind of fraudulent activities. In today’s world, fraudulent
activities is one of the most common aspect in financial department which includes the finances
that gets transferred from one account to another account. The growth in the complexities in the
payment terms are becoming complex day by day which means that they have to go through
several process which allows them to pay their desired amount. The fraudster have recently
developed a sophisticated factors which allows them to perform the fraudulent activities in an
easy manner. The breach in the cyber security also allows to perform the fraudulent activities
that are finance related. The financial fraud is mainly perform during any kind of financial
transaction that highlights the effective transaction from one source to another source. Real time
monitoring can be used for detecting these financial frauds but the tactics that are recently
developed are smarter than the traditional way of detection as well as preventing the fraudulent
activities. Improvement of the customers are also necessary for preventing the fraudulent
activities as they have to be full of the knowledge of financial frauds.
There are certain steps that are required to be followed which would help in identifying
the fraudulent activities. The first step is to capture and identify all of the available data from all
departments which channels or incorporates in the actual process of analytics. Monitoring the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

55FINANCIAL FRAUD DETECTION AND PREVENTION
transaction in a continuous manner is also important which includes the social network and the
high risk anomalies. The behavioural analytics is required to be applied which points out the
process of real time decision making. The secondary step is to focus on the enterprise wide
analytics culture which would be beneficial for pointing out the financial frauds in the overall
process. The visualisation of data at all levels is also to be monitored which includes the
investigation of workflow optimisation that would be beneficial for the company in detecting the
overall financial frauds. A layered of security techniques is also important for detecting the
fraudulent activities that are associated with the business. The prevention and detection
technology that have been chosen from the learning ability also points out the complex data
patters which integrates the effective analysis of the data that have been used. Machine learning
method can also be used for points out the detection techniques which would be useful in
highlighting the financial frauds. Financial fraud discovery and prevention are the developing
concern which basically influences both businesses and clients.
Financial frauds are primarily related to the financial exchange that are specifically
related with the trade which are basically performed by the clients to a trade. This might drive to
confront certain sum of misfortune for both trade as well as for the clients which get influenced
and reflected within the financial statements. The individual who are related with the fraudulent
exercises have the simpler get to to realize the apparatuses and information that would be
valuable for performing any kind of false activities. In today’s world, false exercises is one of the
foremost common angle in money related division which incorporates the finances that gets
transferred from one account to another account. The development within the complexities
within the instalment terms are getting to be complex day by day which suggests that they need
to go through a few handle which permits them to pay their amount which is desired in nature.
transaction in a continuous manner is also important which includes the social network and the
high risk anomalies. The behavioural analytics is required to be applied which points out the
process of real time decision making. The secondary step is to focus on the enterprise wide
analytics culture which would be beneficial for pointing out the financial frauds in the overall
process. The visualisation of data at all levels is also to be monitored which includes the
investigation of workflow optimisation that would be beneficial for the company in detecting the
overall financial frauds. A layered of security techniques is also important for detecting the
fraudulent activities that are associated with the business. The prevention and detection
technology that have been chosen from the learning ability also points out the complex data
patters which integrates the effective analysis of the data that have been used. Machine learning
method can also be used for points out the detection techniques which would be useful in
highlighting the financial frauds. Financial fraud discovery and prevention are the developing
concern which basically influences both businesses and clients.
Financial frauds are primarily related to the financial exchange that are specifically
related with the trade which are basically performed by the clients to a trade. This might drive to
confront certain sum of misfortune for both trade as well as for the clients which get influenced
and reflected within the financial statements. The individual who are related with the fraudulent
exercises have the simpler get to to realize the apparatuses and information that would be
valuable for performing any kind of false activities. In today’s world, false exercises is one of the
foremost common angle in money related division which incorporates the finances that gets
transferred from one account to another account. The development within the complexities
within the instalment terms are getting to be complex day by day which suggests that they need
to go through a few handle which permits them to pay their amount which is desired in nature.

56FINANCIAL FRAUD DETECTION AND PREVENTION
The fraudster have as of late created a modern components which permits them to perform the
false exercises in a straightforward way. The breach within the cyber security too permits to
perform the fraudulent exercises that are back related. The financial fraud is primarily perform
amid any kind of financial exchange that highlights the viable exchange from one source to
another source. Genuine time observing can be utilized for identifying these financial frauds but
the strategies that are as of late created are more brilliant than the conventional way of discovery
as well as anticipating the fraudulent exercises. Enhancement of the clients are also necessary for
avoiding the false exercises as they got to be full of the information of financial frauds.
There are certain steps that are required to be taken after which would offer assistance in
distinguishing the fraudulent exercises. The primary step is to capture and distinguish all of the
accessible information from all offices which channels or consolidates within the real process of
analytics. Monitoring the exchange in a ceaseless way is additionally critical which incorporates
the social organize and the high risk anomalies. The behavioural analytics is required to be
connected which focuses out the method of genuine time choice making. The secondary step is
to centre on the venture wide analytics culture which would be advantageous for pointing out the
financial frauds within the in general process. The representation of information at all levels is
additionally to be checked which includes the examination of workflow advancement that would
be advantageous for the company in recognizing the generally financial frauds. A layered of
security methods is additionally critical for recognizing the fraudulent exercises that are related
with the trade. The prevention and detection technology that have been chosen from the learning
capacity moreover focuses out the complex information patters which coordinating the
compelling analysis of the information that have been utilized.
The fraudster have as of late created a modern components which permits them to perform the
false exercises in a straightforward way. The breach within the cyber security too permits to
perform the fraudulent exercises that are back related. The financial fraud is primarily perform
amid any kind of financial exchange that highlights the viable exchange from one source to
another source. Genuine time observing can be utilized for identifying these financial frauds but
the strategies that are as of late created are more brilliant than the conventional way of discovery
as well as anticipating the fraudulent exercises. Enhancement of the clients are also necessary for
avoiding the false exercises as they got to be full of the information of financial frauds.
There are certain steps that are required to be taken after which would offer assistance in
distinguishing the fraudulent exercises. The primary step is to capture and distinguish all of the
accessible information from all offices which channels or consolidates within the real process of
analytics. Monitoring the exchange in a ceaseless way is additionally critical which incorporates
the social organize and the high risk anomalies. The behavioural analytics is required to be
connected which focuses out the method of genuine time choice making. The secondary step is
to centre on the venture wide analytics culture which would be advantageous for pointing out the
financial frauds within the in general process. The representation of information at all levels is
additionally to be checked which includes the examination of workflow advancement that would
be advantageous for the company in recognizing the generally financial frauds. A layered of
security methods is additionally critical for recognizing the fraudulent exercises that are related
with the trade. The prevention and detection technology that have been chosen from the learning
capacity moreover focuses out the complex information patters which coordinating the
compelling analysis of the information that have been utilized.

57FINANCIAL FRAUD DETECTION AND PREVENTION
Machine learning strategy can too be utilized for focuses out the detection methods which
would be valuable in highlighting the financial frauds. The suggestion that can be made for
recognizing and avoiding the financial frauds incorporates the method of forensic accounting
which consolidates the overall examination prepare within the process. The reasonableness of the
financial statement is to be carried out which got to be pointed by the subset of forensic
accounting. The premise of this specific accounting is to keeping up the accounting standard that
gives genuine and reasonable esteem of the financial articulations. It is additionally required to
be created in around the world where all associations are required to be goes with measurable
bookkeeping and redress accounting benchmarks. It can be seen that the developed countries
primarily utilized distinctive modes of accounting which offer assistance them in distinguishing
certain loop holes within the accounting standards and methods. Discovery of financial frauds
and anticipating it from any reasons is imperative because it would spare the reserves or the cash
from the company or from the person which would be captured by the fraudsters. The
confirmation suppliers are moreover required to be overviewed for identifying and anticipating
the financial fraudulent exercises in future a long time. The taking after step is the research
around approach and it centres out the source by which the approaches would be made for the
research about nearly and those ought to be started internal parts the ask generally.
Information examination and disclosures in a general sense centres out the way of
looking at the information that have been collected from the fundamental sources where the list
of unions of financial frauds has been considered. Positivism basically holds the noteworthy data
nearly the research around which gives the supporter a distant off overwhelming and more
grounded advanced information nearly the issues that have been raised internal parts they think
around. The standard consider highlights the properties and relations which highlights the ways
Machine learning strategy can too be utilized for focuses out the detection methods which
would be valuable in highlighting the financial frauds. The suggestion that can be made for
recognizing and avoiding the financial frauds incorporates the method of forensic accounting
which consolidates the overall examination prepare within the process. The reasonableness of the
financial statement is to be carried out which got to be pointed by the subset of forensic
accounting. The premise of this specific accounting is to keeping up the accounting standard that
gives genuine and reasonable esteem of the financial articulations. It is additionally required to
be created in around the world where all associations are required to be goes with measurable
bookkeeping and redress accounting benchmarks. It can be seen that the developed countries
primarily utilized distinctive modes of accounting which offer assistance them in distinguishing
certain loop holes within the accounting standards and methods. Discovery of financial frauds
and anticipating it from any reasons is imperative because it would spare the reserves or the cash
from the company or from the person which would be captured by the fraudsters. The
confirmation suppliers are moreover required to be overviewed for identifying and anticipating
the financial fraudulent exercises in future a long time. The taking after step is the research
around approach and it centres out the source by which the approaches would be made for the
research about nearly and those ought to be started internal parts the ask generally.
Information examination and disclosures in a general sense centres out the way of
looking at the information that have been collected from the fundamental sources where the list
of unions of financial frauds has been considered. Positivism basically holds the noteworthy data
nearly the research around which gives the supporter a distant off overwhelming and more
grounded advanced information nearly the issues that have been raised internal parts they think
around. The standard consider highlights the properties and relations which highlights the ways
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

58FINANCIAL FRAUD DETECTION AND PREVENTION
through which the examination is utilized to be conducted at the side creation of contemplations
which would be basic for the research. It in expansion highlights the procedure that offer
assistance the research about around for certain wide questions and examination of the strategies
that are required to be taken after all through the inquire around. In this specific inquire almost,
the questions that are made centres out the sensible examination of the information that are being
collected for the analyst. Coordination of specific components in a coherent way and in a
coherent way is to be related with the thought by the master. The issues that are related with the
research around to boot to be recognized in this convey and those are to be included with certain
handle. Exploratory plan ask approximately facilitate and sensible see at organize are there three
fundamental sort of see at organize which are broadly utilized and open to any analyst.
The data that have been collected for the research almost is from crucial sources which
endorses of unmistakable essential areas that have been tended to for certain centre of see and
they have collected from the published articles. Committing the fraudulent exercises might
impact the workers in their employees’ period which are required to be related with the
organization and watching the courses of action which would be valuable for the company
furthermore for the individual. No respondents have been constrained to assemble the data that
has as of now been collected for the reason of the research. Quantitative information has been
considered within the study which basically focuses out the list of the questions that are
progressing to be inquired to the respondents. The reactions of the participants’ are recorded in
their exercises that highlights the conclusion of the respondents for the individual questions. The
strategy of expectation of extortion is more like pay and chase which are required to be taken
after and recognized at a rectified time. The complexities that have created inside the afterward
world are essentially the state upheld fear based oppression that are required to be included with
through which the examination is utilized to be conducted at the side creation of contemplations
which would be basic for the research. It in expansion highlights the procedure that offer
assistance the research about around for certain wide questions and examination of the strategies
that are required to be taken after all through the inquire around. In this specific inquire almost,
the questions that are made centres out the sensible examination of the information that are being
collected for the analyst. Coordination of specific components in a coherent way and in a
coherent way is to be related with the thought by the master. The issues that are related with the
research around to boot to be recognized in this convey and those are to be included with certain
handle. Exploratory plan ask approximately facilitate and sensible see at organize are there three
fundamental sort of see at organize which are broadly utilized and open to any analyst.
The data that have been collected for the research almost is from crucial sources which
endorses of unmistakable essential areas that have been tended to for certain centre of see and
they have collected from the published articles. Committing the fraudulent exercises might
impact the workers in their employees’ period which are required to be related with the
organization and watching the courses of action which would be valuable for the company
furthermore for the individual. No respondents have been constrained to assemble the data that
has as of now been collected for the reason of the research. Quantitative information has been
considered within the study which basically focuses out the list of the questions that are
progressing to be inquired to the respondents. The reactions of the participants’ are recorded in
their exercises that highlights the conclusion of the respondents for the individual questions. The
strategy of expectation of extortion is more like pay and chase which are required to be taken
after and recognized at a rectified time. The complexities that have created inside the afterward
world are essentially the state upheld fear based oppression that are required to be included with

59FINANCIAL FRAUD DETECTION AND PREVENTION
the capable offenders. These wrongdoers are ace in making financial frauds which particular
extortion is required to be recognized and expected as early as conceivable. The comprehensive
approach of planning of data beside the works out that are related with the blackmail disclosure
is to be recognized. The evasion of extortion is the advancement that are required to be made
with tremendous walk from the strategy of advanced computing and other outline of machine
learning.
The shapes of fraud experiences touches the each ranges of live which are required to be
raised with costs and portion of items and organizations. Fraudsters are beautiful noteworthy on
the hit rate that are getting to be the major slugger which might effect on the trade. Other creators
have specified that, one out of six individuals are not mindful that they are focused on for a few
kind of fraudulent exercises. The attempt to swindle the companies is to be predominant which is
required to be considered by the administration. The method of extortion anticipation would be
colossal concern for the department of back because it bargains with financial exchanges. The
companies are required to audit the method of extortion anticipation which are required to be
related with the same money related year. The data are to be point of view which are required to
be related with the forms on the viable source of fraudulent exercises. The attempt to trick the
companies is to be overwhelming which is required to be considered by the organization.
The recommendation that can be made for detecting and preventing the financial frauds
includes the process of forensic accounting which incorporates the overall investigation process
in the process. The fairness of the financial statement is to be carried out and that have to be
pointed by the subset of forensic accounting. The basis of this particular accounting is to
maintaining the accounting standard that provides true and fair value of the financial statements.
It is also required to be developed in worldwide where all organisations are required to be
the capable offenders. These wrongdoers are ace in making financial frauds which particular
extortion is required to be recognized and expected as early as conceivable. The comprehensive
approach of planning of data beside the works out that are related with the blackmail disclosure
is to be recognized. The evasion of extortion is the advancement that are required to be made
with tremendous walk from the strategy of advanced computing and other outline of machine
learning.
The shapes of fraud experiences touches the each ranges of live which are required to be
raised with costs and portion of items and organizations. Fraudsters are beautiful noteworthy on
the hit rate that are getting to be the major slugger which might effect on the trade. Other creators
have specified that, one out of six individuals are not mindful that they are focused on for a few
kind of fraudulent exercises. The attempt to swindle the companies is to be predominant which is
required to be considered by the administration. The method of extortion anticipation would be
colossal concern for the department of back because it bargains with financial exchanges. The
companies are required to audit the method of extortion anticipation which are required to be
related with the same money related year. The data are to be point of view which are required to
be related with the forms on the viable source of fraudulent exercises. The attempt to trick the
companies is to be overwhelming which is required to be considered by the organization.
The recommendation that can be made for detecting and preventing the financial frauds
includes the process of forensic accounting which incorporates the overall investigation process
in the process. The fairness of the financial statement is to be carried out and that have to be
pointed by the subset of forensic accounting. The basis of this particular accounting is to
maintaining the accounting standard that provides true and fair value of the financial statements.
It is also required to be developed in worldwide where all organisations are required to be

60FINANCIAL FRAUD DETECTION AND PREVENTION
accompanies with forensic accounting and correct accounting standards. It can be seen that the
developed countries mainly used different modes of accounting which help them in identifying
certain loop holes in the accounting standards and procedures. Detection of financial frauds and
preventing it from any reasons is important as it would save the funds or the money from the
company or from the individual which would be captured by the fraudsters. The assurance
providers are also required to be surveyed for detecting and preventing the financial fraudulent
activities in future years. The financial institutions that are going are aware of the risk that are
going to be identified in the fraud detection.
Fraud is pervasive in which the investment of the business is to be tuned with the
detection system along with investigation of other interventions. The new accuracy method is
required to be efficient and consist of the ability with artificial intelligence. Detection of fraud
with the help of machine learning is also important for an organisation as it would help in
reduction of manual labour. The existing approaches are mainly helpful in pointing out the
digital payment model in which the half of the fraud case are highlighted. Using the machine
learning also help in improving the overall process of efficiency which would reduce the cost
that are directly associated with financial fraud. Most accurate detection model is required to be
selected which would apply on the organisation and would be helpful in detecting the financial
frauds.
accompanies with forensic accounting and correct accounting standards. It can be seen that the
developed countries mainly used different modes of accounting which help them in identifying
certain loop holes in the accounting standards and procedures. Detection of financial frauds and
preventing it from any reasons is important as it would save the funds or the money from the
company or from the individual which would be captured by the fraudsters. The assurance
providers are also required to be surveyed for detecting and preventing the financial fraudulent
activities in future years. The financial institutions that are going are aware of the risk that are
going to be identified in the fraud detection.
Fraud is pervasive in which the investment of the business is to be tuned with the
detection system along with investigation of other interventions. The new accuracy method is
required to be efficient and consist of the ability with artificial intelligence. Detection of fraud
with the help of machine learning is also important for an organisation as it would help in
reduction of manual labour. The existing approaches are mainly helpful in pointing out the
digital payment model in which the half of the fraud case are highlighted. Using the machine
learning also help in improving the overall process of efficiency which would reduce the cost
that are directly associated with financial fraud. Most accurate detection model is required to be
selected which would apply on the organisation and would be helpful in detecting the financial
frauds.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

61FINANCIAL FRAUD DETECTION AND PREVENTION
References and Bibliography
Abdallah, A., Maarof, M.A. and Zainal, A., 2016. Fraud detection system: A survey. Journal of
Network and Computer Applications, 68, pp.90-113.
Abu-Shanab, E. and Matalqa, S., 2015. Security and Fraud Issues of E-banking. International
Journal of Computer Networks and Applications, 2(4), pp.179-188.
Adetiloye, K.A., Olokoyo, F.O. and Taiwo, J.N., 2016. Fraud prevention and internal control in
the Nigerian banking system. International Journal of Economics and Financial Issues, 6(3),
pp.1172-1179.
Aduwo, O.O., 2016. The role of forensic accounting in combating the menace of corporate
failure. International Journal of Economics, Commerce and Management, 4(1), pp.640-649.
Ahmed, M., Mahmood, A.N. and Islam, M.R., 2016. A survey of anomaly detection techniques
in financial domain. Future Generation Computer Systems, 55, pp.278-288.
Alam, F. and Pachauri, S., 2017. Detection using weka. Advances in Computational Sciences
and Technology, 10(6), pp.1731-1743.
Alao, A.A., 2016. Forensic auditing and financial fraud in Nigerian deposit money banks
(DMBs). European Journal of Accounting, Auditing and Finance Research, 4(8), pp.1-19.
Bănărescu, A., 2015. Detecting and preventing fraud with data analytics. Procedia economics
and finance, 32, pp.1827-1836.
Bhardwaj, A. and Gupta, R., 2016. Financial frauds: data mining based detection-a
comprehensive survey. International Journal of Computer Applications, 156(10), pp.20-28.
References and Bibliography
Abdallah, A., Maarof, M.A. and Zainal, A., 2016. Fraud detection system: A survey. Journal of
Network and Computer Applications, 68, pp.90-113.
Abu-Shanab, E. and Matalqa, S., 2015. Security and Fraud Issues of E-banking. International
Journal of Computer Networks and Applications, 2(4), pp.179-188.
Adetiloye, K.A., Olokoyo, F.O. and Taiwo, J.N., 2016. Fraud prevention and internal control in
the Nigerian banking system. International Journal of Economics and Financial Issues, 6(3),
pp.1172-1179.
Aduwo, O.O., 2016. The role of forensic accounting in combating the menace of corporate
failure. International Journal of Economics, Commerce and Management, 4(1), pp.640-649.
Ahmed, M., Mahmood, A.N. and Islam, M.R., 2016. A survey of anomaly detection techniques
in financial domain. Future Generation Computer Systems, 55, pp.278-288.
Alam, F. and Pachauri, S., 2017. Detection using weka. Advances in Computational Sciences
and Technology, 10(6), pp.1731-1743.
Alao, A.A., 2016. Forensic auditing and financial fraud in Nigerian deposit money banks
(DMBs). European Journal of Accounting, Auditing and Finance Research, 4(8), pp.1-19.
Bănărescu, A., 2015. Detecting and preventing fraud with data analytics. Procedia economics
and finance, 32, pp.1827-1836.
Bhardwaj, A. and Gupta, R., 2016. Financial frauds: data mining based detection-a
comprehensive survey. International Journal of Computer Applications, 156(10), pp.20-28.

62FINANCIAL FRAUD DETECTION AND PREVENTION
Bhavani, G. and Amponsah, C.T., 2017. M-Score and Z-Score for detection of accounting
fraud. Accountancy Business and the Public Interest, pp.68-86.
de Sá, A.G., Pereira, A.C. and Pappa, G.L., 2018. A customized classification algorithm for
credit card fraud detection. Engineering Applications of Artificial Intelligence, 72, pp.21-29.
Dilla, W.N. and Raschke, R.L., 2015. Data visualization for fraud detection: Practice
implications and a call for future research. International Journal of Accounting Information
Systems, 16, pp.1-22.
Dimitrijević, D., 2015. The detection and prevention of manipulations in the balance sheet and
the cash flow statement. Ekonomski horizonti, 17(2), pp.137-153.
Dong, W., Liao, S. and Zhang, Z., 2018. Leveraging financial social media data for corporate
fraud detection. Journal of Management Information Systems, 35(2), pp.461-487.
Drogalas, G., Pazarskis, M., Anagnostopoulou, E. and Papachristou, A., 2017. The effect of
internal audit effectiveness, auditor responsibility and training in fraud detection. Accounting
and Management Information Systems, 16(4), pp.434-454.
Dutta, I., Dutta, S. and Raahemi, B., 2017. Detecting financial restatements using data mining
techniques. Expert Systems with Applications, 90, pp.374-393.
Ehioghiren, E.E. and Atu, O.O.K., 2016. Forensic accounting and fraud management: Evidence
from Nigeria. Igbinedion University Journal of Accounting, 2(8), pp.245-308.
Enofe, A.O., Omagbon, P. and Ehigiator, F.I., 2015. Forensic audit and corporate fraud. IIARD
International Journal of Economics and Business Management, 1(7), pp.1-10.
Bhavani, G. and Amponsah, C.T., 2017. M-Score and Z-Score for detection of accounting
fraud. Accountancy Business and the Public Interest, pp.68-86.
de Sá, A.G., Pereira, A.C. and Pappa, G.L., 2018. A customized classification algorithm for
credit card fraud detection. Engineering Applications of Artificial Intelligence, 72, pp.21-29.
Dilla, W.N. and Raschke, R.L., 2015. Data visualization for fraud detection: Practice
implications and a call for future research. International Journal of Accounting Information
Systems, 16, pp.1-22.
Dimitrijević, D., 2015. The detection and prevention of manipulations in the balance sheet and
the cash flow statement. Ekonomski horizonti, 17(2), pp.137-153.
Dong, W., Liao, S. and Zhang, Z., 2018. Leveraging financial social media data for corporate
fraud detection. Journal of Management Information Systems, 35(2), pp.461-487.
Drogalas, G., Pazarskis, M., Anagnostopoulou, E. and Papachristou, A., 2017. The effect of
internal audit effectiveness, auditor responsibility and training in fraud detection. Accounting
and Management Information Systems, 16(4), pp.434-454.
Dutta, I., Dutta, S. and Raahemi, B., 2017. Detecting financial restatements using data mining
techniques. Expert Systems with Applications, 90, pp.374-393.
Ehioghiren, E.E. and Atu, O.O.K., 2016. Forensic accounting and fraud management: Evidence
from Nigeria. Igbinedion University Journal of Accounting, 2(8), pp.245-308.
Enofe, A.O., Omagbon, P. and Ehigiator, F.I., 2015. Forensic audit and corporate fraud. IIARD
International Journal of Economics and Business Management, 1(7), pp.1-10.

63FINANCIAL FRAUD DETECTION AND PREVENTION
Fadaei Noghani, F. and Moattar, M., 2017. Ensemble classification and extended feature
selection for credit card fraud detection. Journal of AI and Data Mining, 5(2), pp.235-243.
Gbegi, D.O. and Adebisi, J.F., 2015. Analysis of fraud detection and prevention strategies in the
Nigerian public sector. Journal of Good Governance and Sustainable Development in Africa
(JGGSDA), 2(4), pp.109-128.
Goel, S. and Uzuner, O., 2016. Do sentiments matter in fraud detection? Estimating semantic
orientation of annual reports. Intelligent Systems in Accounting, Finance and
Management, 23(3), pp.215-239.
Hajek, P. and Henriques, R., 2017. Mining corporate annual reports for intelligent detection of
financial statement fraud–A comparative study of machine learning methods. Knowledge-Based
Systems, 128, pp.139-152.
Hamdan, M.W., 2018. The role of forensic accounting in discovering financial
fraud. International Journal of Accounting Research, 6(2), pp.1-6.
Herawati, N., 2015. Application of Beneish M-Score models and data mining to detect financial
fraud. Procedia-Social and Behavioral Sciences, 211, pp.924-930.
Huang, S.Y., Lin, C.C., Chiu, A.A. and Yen, D.C., 2017. Fraud detection using fraud triangle
risk factors. Information Systems Frontiers, 19(6), pp.1343-1356.
Imam, A., Kumshe, A.M. and Jajere, M.S., 2015. Applicability of forensic accounting services
for financial fraud detection and prevention in the public sector of Nigeria. International Journal
of Business and Management Studies, 4(01), pp.123-131.
Fadaei Noghani, F. and Moattar, M., 2017. Ensemble classification and extended feature
selection for credit card fraud detection. Journal of AI and Data Mining, 5(2), pp.235-243.
Gbegi, D.O. and Adebisi, J.F., 2015. Analysis of fraud detection and prevention strategies in the
Nigerian public sector. Journal of Good Governance and Sustainable Development in Africa
(JGGSDA), 2(4), pp.109-128.
Goel, S. and Uzuner, O., 2016. Do sentiments matter in fraud detection? Estimating semantic
orientation of annual reports. Intelligent Systems in Accounting, Finance and
Management, 23(3), pp.215-239.
Hajek, P. and Henriques, R., 2017. Mining corporate annual reports for intelligent detection of
financial statement fraud–A comparative study of machine learning methods. Knowledge-Based
Systems, 128, pp.139-152.
Hamdan, M.W., 2018. The role of forensic accounting in discovering financial
fraud. International Journal of Accounting Research, 6(2), pp.1-6.
Herawati, N., 2015. Application of Beneish M-Score models and data mining to detect financial
fraud. Procedia-Social and Behavioral Sciences, 211, pp.924-930.
Huang, S.Y., Lin, C.C., Chiu, A.A. and Yen, D.C., 2017. Fraud detection using fraud triangle
risk factors. Information Systems Frontiers, 19(6), pp.1343-1356.
Imam, A., Kumshe, A.M. and Jajere, M.S., 2015. Applicability of forensic accounting services
for financial fraud detection and prevention in the public sector of Nigeria. International Journal
of Business and Management Studies, 4(01), pp.123-131.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

64FINANCIAL FRAUD DETECTION AND PREVENTION
In'airat, M., 2015. The Role of Corporate Governance in Fraud Reduction-A Perception Study in
the Saudi Arabia Business Environment. Journal of Accounting & Finance (2158-3625), 15(2).
Joseph, O.N., Albert, O. and Byaruhanga, J., 2015. Effect of internal control on fraud detection
and prevention in district treasuries of Kakamega County. Int. J. Bus. Manag. Invent, 4(1),
pp.47-57.
KABUE, L.N. and ADUDA, D.J., 2017. Effect of internal controls on fraud the detection and
prevention among commercial banks in Kenya. European Journal of Business and Strategic
Management, 2(1), pp.52-68.
Khan, A., 2015. Bitcoin–payment method or fraud prevention tool?. Computer Fraud &
Security, 2015(5), pp.16-19.
Klein, R., 2015. How to avoid or minimize fraud exposures. The CPA Journal, 85(3), p.6.
Kulikova, L.I. and Satdarova, D.R., 2016. Internal control and compliance-control as effective
methods of management, detection and prevention of financial statement fraud. Academy of
Strategic Management Journal, 15, p.92.
Lin, C.C., Chiu, A.A., Huang, S.Y. and Yen, D.C., 2015. Detecting the financial statement fraud:
The analysis of the differences between data mining techniques and experts’
judgments. Knowledge-Based Systems, 89, pp.459-470.
Liu, C., Chan, Y., Kazmi, S.H.A. and Fu, H., 2015. Financial Fraud Detection Model: Based on
Random Forest. International journal of economics and finance, 7(7), pp.178-188.
In'airat, M., 2015. The Role of Corporate Governance in Fraud Reduction-A Perception Study in
the Saudi Arabia Business Environment. Journal of Accounting & Finance (2158-3625), 15(2).
Joseph, O.N., Albert, O. and Byaruhanga, J., 2015. Effect of internal control on fraud detection
and prevention in district treasuries of Kakamega County. Int. J. Bus. Manag. Invent, 4(1),
pp.47-57.
KABUE, L.N. and ADUDA, D.J., 2017. Effect of internal controls on fraud the detection and
prevention among commercial banks in Kenya. European Journal of Business and Strategic
Management, 2(1), pp.52-68.
Khan, A., 2015. Bitcoin–payment method or fraud prevention tool?. Computer Fraud &
Security, 2015(5), pp.16-19.
Klein, R., 2015. How to avoid or minimize fraud exposures. The CPA Journal, 85(3), p.6.
Kulikova, L.I. and Satdarova, D.R., 2016. Internal control and compliance-control as effective
methods of management, detection and prevention of financial statement fraud. Academy of
Strategic Management Journal, 15, p.92.
Lin, C.C., Chiu, A.A., Huang, S.Y. and Yen, D.C., 2015. Detecting the financial statement fraud:
The analysis of the differences between data mining techniques and experts’
judgments. Knowledge-Based Systems, 89, pp.459-470.
Liu, C., Chan, Y., Kazmi, S.H.A. and Fu, H., 2015. Financial Fraud Detection Model: Based on
Random Forest. International journal of economics and finance, 7(7), pp.178-188.

65FINANCIAL FRAUD DETECTION AND PREVENTION
Mahama, M., 2015. Detecting corporate fraud and financial distress using the Altman and
Beneish models. International Journal of Economics, Commerce and Management, 3(1), pp.1-
18.
Mahmoudi, N. and Duman, E., 2015. Detecting credit card fraud by modified Fisher discriminant
analysis. Expert Systems with Applications, 42(5), pp.2510-2516.
Mallika, R., 2017. Fraud Detection Using Supervised Learning Algorithms. International
Journal of Advanced Research in Computer and Communication Engineering, 6(6).
Mangala, D. and Kumari, P., 2015. Corporate fraud prevention and detection: Revisiting the
literature. Journal of Commerce & Accounting Research, 4(1), pp.35-45.
Mansor, N., 2015. Fraud triangle theory and fraud diamond theory. Understanding the
convergent and divergent for future research. International Journal of Academic Research in
Accounting, Finance and Management Science, 1, pp.38-45.
Matheswaran, P. and Rajesh, R., 2015. Fraud detection in credit card using datamining
techniques. International Journal for Research in Science Engineering & Technology, 2(1),
pp.11-18.
McMahon, R., Pence, D., Bressler, L. and Bressler, M.S., 2016. New tactics in fighting financial
crimes: Moving beyond the fraud triangle. Journal of Legal, Ethical and Regulatory
Issues, 19(1), p.16.
Mehta, A. and Bhavani, G., 2017. Application of forensic tools to detect fraud: the case of
Toshiba. Journal of Forensic and Investigative Accounting, 9(1), pp.692-710.
Mahama, M., 2015. Detecting corporate fraud and financial distress using the Altman and
Beneish models. International Journal of Economics, Commerce and Management, 3(1), pp.1-
18.
Mahmoudi, N. and Duman, E., 2015. Detecting credit card fraud by modified Fisher discriminant
analysis. Expert Systems with Applications, 42(5), pp.2510-2516.
Mallika, R., 2017. Fraud Detection Using Supervised Learning Algorithms. International
Journal of Advanced Research in Computer and Communication Engineering, 6(6).
Mangala, D. and Kumari, P., 2015. Corporate fraud prevention and detection: Revisiting the
literature. Journal of Commerce & Accounting Research, 4(1), pp.35-45.
Mansor, N., 2015. Fraud triangle theory and fraud diamond theory. Understanding the
convergent and divergent for future research. International Journal of Academic Research in
Accounting, Finance and Management Science, 1, pp.38-45.
Matheswaran, P. and Rajesh, R., 2015. Fraud detection in credit card using datamining
techniques. International Journal for Research in Science Engineering & Technology, 2(1),
pp.11-18.
McMahon, R., Pence, D., Bressler, L. and Bressler, M.S., 2016. New tactics in fighting financial
crimes: Moving beyond the fraud triangle. Journal of Legal, Ethical and Regulatory
Issues, 19(1), p.16.
Mehta, A. and Bhavani, G., 2017. Application of forensic tools to detect fraud: the case of
Toshiba. Journal of Forensic and Investigative Accounting, 9(1), pp.692-710.

66FINANCIAL FRAUD DETECTION AND PREVENTION
Nami, S. and Shajari, M., 2018. Cost-sensitive payment card fraud detection based on dynamic
random forest and k-nearest neighbors. Expert Systems with Applications, 110, pp.381-392.
Olukowade, E. and Balogun, E., 2015. Relevance of forensic accounting in the detection and
prevention of fraud in Nigeria. International Journal of Accounting Research, 42(2437), pp.1-11.
Othman, R., Aris, N.A., Mardziyah, A., Zainan, N. and Amin, N.M., 2015. Fraud detection and
prevention methods in the Malaysian public sector: Accountants’ and internal auditors’
perceptions. Procedia Economics and Finance, 28, pp.59-67.
Ozili, P.K., 2015. Forensic Accounting and Fraud: A Review of Literature and Policy
Implications. International Journal of Accounting and Economics Studies, 3(1), pp.63-68.
Patil, S., Nemade, V. and Soni, P.K., 2018. Predictive modelling for credit card fraud detection
using data analytics. Procedia computer science, 132, pp.385-395.
Prasmaulida, S., 2016. Financial statement fraud detection using perspective of fraud triangle
adopted by SAS No. 99. Asia Pacific Fraud Journal, 1(2), pp.317-335.
Rahman, N. and Iverson, S., 2015. Big data business intelligence in bank risk
analysis. International Journal of Business Intelligence Research (IJBIR), 6(2), pp.55-77.
Sadgali, I., Sael, N. and Benabbou, F., 2019. Performance of machine learning techniques in the
detection of financial frauds. Procedia computer science, 148, pp.45-54.
Sanusi, Z.M., Rameli, M.N.F. and Isa, Y.M., 2015. Fraud schemes in the banking institutions:
prevention measures to avoid severe financial loss. Procedia Economics and Finance, 28,
pp.107-113.
Nami, S. and Shajari, M., 2018. Cost-sensitive payment card fraud detection based on dynamic
random forest and k-nearest neighbors. Expert Systems with Applications, 110, pp.381-392.
Olukowade, E. and Balogun, E., 2015. Relevance of forensic accounting in the detection and
prevention of fraud in Nigeria. International Journal of Accounting Research, 42(2437), pp.1-11.
Othman, R., Aris, N.A., Mardziyah, A., Zainan, N. and Amin, N.M., 2015. Fraud detection and
prevention methods in the Malaysian public sector: Accountants’ and internal auditors’
perceptions. Procedia Economics and Finance, 28, pp.59-67.
Ozili, P.K., 2015. Forensic Accounting and Fraud: A Review of Literature and Policy
Implications. International Journal of Accounting and Economics Studies, 3(1), pp.63-68.
Patil, S., Nemade, V. and Soni, P.K., 2018. Predictive modelling for credit card fraud detection
using data analytics. Procedia computer science, 132, pp.385-395.
Prasmaulida, S., 2016. Financial statement fraud detection using perspective of fraud triangle
adopted by SAS No. 99. Asia Pacific Fraud Journal, 1(2), pp.317-335.
Rahman, N. and Iverson, S., 2015. Big data business intelligence in bank risk
analysis. International Journal of Business Intelligence Research (IJBIR), 6(2), pp.55-77.
Sadgali, I., Sael, N. and Benabbou, F., 2019. Performance of machine learning techniques in the
detection of financial frauds. Procedia computer science, 148, pp.45-54.
Sanusi, Z.M., Rameli, M.N.F. and Isa, Y.M., 2015. Fraud schemes in the banking institutions:
prevention measures to avoid severe financial loss. Procedia Economics and Finance, 28,
pp.107-113.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

67FINANCIAL FRAUD DETECTION AND PREVENTION
Schuchter, A. and Levi, M., 2016. The fraud triangle revisited. Security Journal, 29(2), pp.107-
121.
Shi, W., Connelly, B.L. and Hoskisson, R.E., 2017. External corporate governance and financial
fraud: Cognitive evaluation theory insights on agency theory prescriptions. Strategic
Management Journal, 38(6), pp.1268-1286.
Shimpi, P.R. and Kadroli, V., 2015. Survey on credit card fraud detection
techniques. International Journal Of Engineering And Computer Science, 4(11), pp.15010-
15015.
Siering, M., Clapham, B., Engel, O. and Gomber, P., 2017. A taxonomy of financial market
manipulations: establishing trust and market integrity in the financialized economy through
automated fraud detection. Journal of Information Technology, 32(3), pp.251-269.
Simha, A. and Satyanarayan, S., 2016. Straight from the Horse’s mouth: Auditors’ on Fraud
Detection and Prevention, Roles of Technology, and White-Collars Getting Splattered with
Red!. Journal of Accounting and Finance, 16(1).
Simha, A. and Satyanarayan, S., 2016. Straight from the Horse’s mouth: Auditors’ on Fraud
Detection and Prevention, Roles of Technology, and White-Collars Getting Splattered with
Red!. Journal of Accounting and Finance, 16(1).
Singh, P. and Singh, M., 2015. Fraud detection by monitoring customer behavior and
activities. International Journal of Computer Applications, 111(11).
Smith, G.S., 2015. The past, present, and future of forensic accounting. The CPA Journal, 85(3),
p.16.
Schuchter, A. and Levi, M., 2016. The fraud triangle revisited. Security Journal, 29(2), pp.107-
121.
Shi, W., Connelly, B.L. and Hoskisson, R.E., 2017. External corporate governance and financial
fraud: Cognitive evaluation theory insights on agency theory prescriptions. Strategic
Management Journal, 38(6), pp.1268-1286.
Shimpi, P.R. and Kadroli, V., 2015. Survey on credit card fraud detection
techniques. International Journal Of Engineering And Computer Science, 4(11), pp.15010-
15015.
Siering, M., Clapham, B., Engel, O. and Gomber, P., 2017. A taxonomy of financial market
manipulations: establishing trust and market integrity in the financialized economy through
automated fraud detection. Journal of Information Technology, 32(3), pp.251-269.
Simha, A. and Satyanarayan, S., 2016. Straight from the Horse’s mouth: Auditors’ on Fraud
Detection and Prevention, Roles of Technology, and White-Collars Getting Splattered with
Red!. Journal of Accounting and Finance, 16(1).
Simha, A. and Satyanarayan, S., 2016. Straight from the Horse’s mouth: Auditors’ on Fraud
Detection and Prevention, Roles of Technology, and White-Collars Getting Splattered with
Red!. Journal of Accounting and Finance, 16(1).
Singh, P. and Singh, M., 2015. Fraud detection by monitoring customer behavior and
activities. International Journal of Computer Applications, 111(11).
Smith, G.S., 2015. The past, present, and future of forensic accounting. The CPA Journal, 85(3),
p.16.

68FINANCIAL FRAUD DETECTION AND PREVENTION
Suryanto, T. and Ridwansyah, R., 2016. The Shariah financial accounting standards: How they
prevent fraud in Islamic Banking. European Research Studies, 19(4), p.140.
Umar, I., Samsudin, R.S. and Mohamed, M., 2016. Adoption of forensic accounting in fraud
detection process by anti-corruption agency: a conceptual framework. International Journal of
Management Research & Review, 6(2), pp.139-148.
Vadoodparast, M. and Hamdan, A.R., 2015. Fraudulent electronic transaction detection using
dynamic kda model. International Journal of Computer Science and Information Security, 13(3),
p.90.
Van Vlasselaer, V., Bravo, C., Caelen, O., Eliassi-Rad, T., Akoglu, L., Snoeck, M. and Baesens,
B., 2015. APATE: A novel approach for automated credit card transaction fraud detection using
network-based extensions. Decision Support Systems, 75, pp.38-48.
West, J. and Bhattacharya, M., 2016. Intelligent financial fraud detection: a comprehensive
review. Computers & security, 57, pp.47-66.
Wong, S. and Venkatraman, S., 2015. Financial accounting fraud detection using business
intelligence. Asian Economic and Financial Review, 5(11), p.1187.
Yee, O.S., Sagadevan, S. and Malim, N.H.A.H., 2018. Credit card fraud detection using machine
learning as data mining technique. Journal of Telecommunication, Electronic and Computer
Engineering (JTEC), 10(1-4), pp.23-27.
Zamzami, F., Nusa, N.D. and Timur, R.P., 2016. The effectiveness of fraud prevention and
detection methods at universities in Indonesia. International Journal of Economics and
Financial Issues, 6(3S), pp.66-69.
Suryanto, T. and Ridwansyah, R., 2016. The Shariah financial accounting standards: How they
prevent fraud in Islamic Banking. European Research Studies, 19(4), p.140.
Umar, I., Samsudin, R.S. and Mohamed, M., 2016. Adoption of forensic accounting in fraud
detection process by anti-corruption agency: a conceptual framework. International Journal of
Management Research & Review, 6(2), pp.139-148.
Vadoodparast, M. and Hamdan, A.R., 2015. Fraudulent electronic transaction detection using
dynamic kda model. International Journal of Computer Science and Information Security, 13(3),
p.90.
Van Vlasselaer, V., Bravo, C., Caelen, O., Eliassi-Rad, T., Akoglu, L., Snoeck, M. and Baesens,
B., 2015. APATE: A novel approach for automated credit card transaction fraud detection using
network-based extensions. Decision Support Systems, 75, pp.38-48.
West, J. and Bhattacharya, M., 2016. Intelligent financial fraud detection: a comprehensive
review. Computers & security, 57, pp.47-66.
Wong, S. and Venkatraman, S., 2015. Financial accounting fraud detection using business
intelligence. Asian Economic and Financial Review, 5(11), p.1187.
Yee, O.S., Sagadevan, S. and Malim, N.H.A.H., 2018. Credit card fraud detection using machine
learning as data mining technique. Journal of Telecommunication, Electronic and Computer
Engineering (JTEC), 10(1-4), pp.23-27.
Zamzami, F., Nusa, N.D. and Timur, R.P., 2016. The effectiveness of fraud prevention and
detection methods at universities in Indonesia. International Journal of Economics and
Financial Issues, 6(3S), pp.66-69.

69FINANCIAL FRAUD DETECTION AND PREVENTION
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

70FINANCIAL FRAUD DETECTION AND PREVENTION
Appendices
Appendix 1
Questionnaire
Q1. What is your age?
Q2. What is your gender?
Q3. Do the company pay you regular salary?
Q4. How does the company help with credit facilities?
Q5. Have any emergency financial services in the organization for workers?
Q6. How the company provides for financial frauds and which employees have in their working
place?
Q7. How the company detects for financial fraud?
Q8. Do you think the company has enough strategies in case of financial fraud, if so, how the
company prevents financial frauds?
Q9. How does the company help for covering financial frauds?
Q10. How far do you agree for prevention strategies of financial frauds for workers?
Q11. Do the company prevents the financial frauds?
Q12. How the company support for the detection measures?
Q13. Does the company organizes detection activities for highlighting financial frauds?
Q14. Is your company avoid financial frauds that might affect the company?
Appendices
Appendix 1
Questionnaire
Q1. What is your age?
Q2. What is your gender?
Q3. Do the company pay you regular salary?
Q4. How does the company help with credit facilities?
Q5. Have any emergency financial services in the organization for workers?
Q6. How the company provides for financial frauds and which employees have in their working
place?
Q7. How the company detects for financial fraud?
Q8. Do you think the company has enough strategies in case of financial fraud, if so, how the
company prevents financial frauds?
Q9. How does the company help for covering financial frauds?
Q10. How far do you agree for prevention strategies of financial frauds for workers?
Q11. Do the company prevents the financial frauds?
Q12. How the company support for the detection measures?
Q13. Does the company organizes detection activities for highlighting financial frauds?
Q14. Is your company avoid financial frauds that might affect the company?

71FINANCIAL FRAUD DETECTION AND PREVENTION
Q15. Do you have a formal procedure of fraud mitigation?
Q15. Do you have a formal procedure of fraud mitigation?
1 out of 72
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





