Firewall and Configuration Report 2022
Added on 2022-09-27
22 Pages1741 Words23 Views
Firewall and Configuration 1
FIREWALL AND CONFIGURATION
By (Name)
(Class)
(Tutor)
(Institution)
(City)
(Date)
FIREWALL AND CONFIGURATION
By (Name)
(Class)
(Tutor)
(Institution)
(City)
(Date)

Firewall and Configuration 2
Executive summary
Canadian Cafe is among small business enterprise which comprises franchise at various
geographical locations. The company has the appropriate network facilities to meet its business
requirements. The major aim of the company is to secure its network across all its geographical
locations. The organization system administrator has realized that the organization network
security needs to be addressed. The company needs to impose a certain level of filtering for its
organization network to be secure. For organization network security to be achieved then the
network administrator needs to have a good understanding of various network attacks and
appropriate network attack mitigation strategies.
Outline
This report which is divided into two parts will highlight how to go about network attack
identification. The first part outlines how a network administrator can use Nmap to gather more
information about their network. Also, this paper has highlighted how network administrators
can use Nmap to detect network vulnerabilities and attacks. The second part outlines how one
can use Linux commands to gather more information about network firewall i.e. check firewall
status and its settings.
Executive summary
Canadian Cafe is among small business enterprise which comprises franchise at various
geographical locations. The company has the appropriate network facilities to meet its business
requirements. The major aim of the company is to secure its network across all its geographical
locations. The organization system administrator has realized that the organization network
security needs to be addressed. The company needs to impose a certain level of filtering for its
organization network to be secure. For organization network security to be achieved then the
network administrator needs to have a good understanding of various network attacks and
appropriate network attack mitigation strategies.
Outline
This report which is divided into two parts will highlight how to go about network attack
identification. The first part outlines how a network administrator can use Nmap to gather more
information about their network. Also, this paper has highlighted how network administrators
can use Nmap to detect network vulnerabilities and attacks. The second part outlines how one
can use Linux commands to gather more information about network firewall i.e. check firewall
status and its settings.

Firewall and Configuration 3
Part A: Nmap
1. Kali Linux on Virtual Box and Nmap running
Shown by the figure below
2. Description of Nmap
Network Mapper (Nmap) is one of free and open-source network scanner that was
created by Gordon Lynon. The tool is widely used to discover services and host on one computer
network by analyzing and sending packets. The tool comes with a number of features for probing
a computer network which includes host discovery, operating system detection, and service. The
four Nmap features include host discovery; here the tool can identify hosts on a computer
network. It does this by listing hosts which respond to ICMP and TCP requests. The second
feature is port scanning, here the tool enumerates open ports on the target hosts. The third is
version detection, the tool achieves this feature by interrogating network services on all remote
Part A: Nmap
1. Kali Linux on Virtual Box and Nmap running
Shown by the figure below
2. Description of Nmap
Network Mapper (Nmap) is one of free and open-source network scanner that was
created by Gordon Lynon. The tool is widely used to discover services and host on one computer
network by analyzing and sending packets. The tool comes with a number of features for probing
a computer network which includes host discovery, operating system detection, and service. The
four Nmap features include host discovery; here the tool can identify hosts on a computer
network. It does this by listing hosts which respond to ICMP and TCP requests. The second
feature is port scanning, here the tool enumerates open ports on the target hosts. The third is
version detection, the tool achieves this feature by interrogating network services on all remote
Firewall and Configuration 4
devices. Forth is OS detection, the tool does this by determining the hardware and operating
characteristics of network devices. The last feature is scriptable interaction with the target where
NMap achieves this by using Nmap scripting engine (Collins, 2002, p. 116).
3. Nmap demonstration
Nmap tool is widely known for its mapping capabilities. Nmap assists in mitigating
network attacks through vulnerability scanning using NSE scripts. Together with Nmap
commands and NSE scripts then one is able to fetch the most popular Common Vulnerabilities
and Exposure (CVEs) from any target system. Also through Nmap, one has the ability to detect
backdoors and malware by running a number of extensive tests on popular OS services like
Proftpd, SMTP, SMB, Vsftpd, and Identd. The tool also has the ability to check for popular
malware signs inside remote servers (Orebaugh, 2011, p. 39).
a) Host discovery
The first step during network reconnaissance is to reduce a set of IP ranges into a list of
interesting or active hosts into a list of interesting or active hosts. Nmap tool offers a wide range
of options to customize the techniques using for host discovery. Example a sample NMAP
detection without the use of NSE scripts covered one of SSH service on port 22 using the
OpenSSH 4.3 version
Figure 1: SSH service port 22 detection using Nmap
devices. Forth is OS detection, the tool does this by determining the hardware and operating
characteristics of network devices. The last feature is scriptable interaction with the target where
NMap achieves this by using Nmap scripting engine (Collins, 2002, p. 116).
3. Nmap demonstration
Nmap tool is widely known for its mapping capabilities. Nmap assists in mitigating
network attacks through vulnerability scanning using NSE scripts. Together with Nmap
commands and NSE scripts then one is able to fetch the most popular Common Vulnerabilities
and Exposure (CVEs) from any target system. Also through Nmap, one has the ability to detect
backdoors and malware by running a number of extensive tests on popular OS services like
Proftpd, SMTP, SMB, Vsftpd, and Identd. The tool also has the ability to check for popular
malware signs inside remote servers (Orebaugh, 2011, p. 39).
a) Host discovery
The first step during network reconnaissance is to reduce a set of IP ranges into a list of
interesting or active hosts into a list of interesting or active hosts. Nmap tool offers a wide range
of options to customize the techniques using for host discovery. Example a sample NMAP
detection without the use of NSE scripts covered one of SSH service on port 22 using the
OpenSSH 4.3 version
Figure 1: SSH service port 22 detection using Nmap

Firewall and Configuration 5
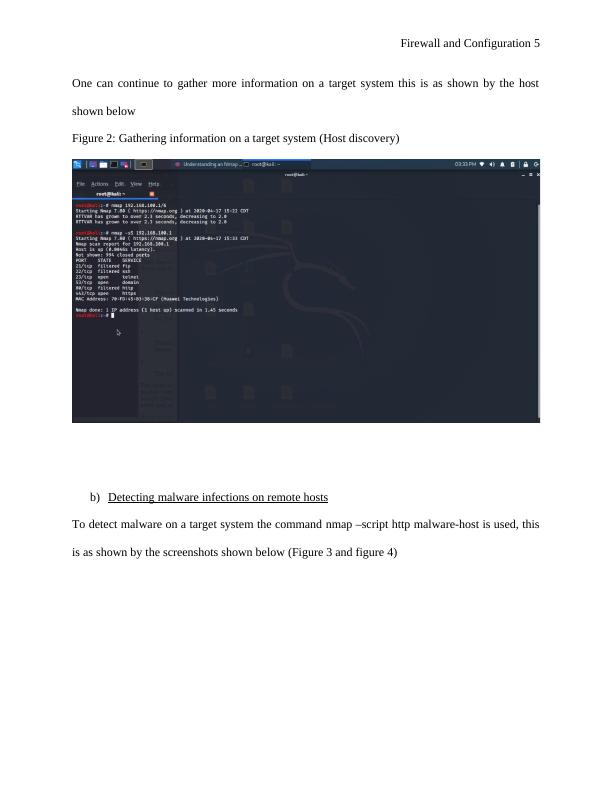
One can continue to gather more information on a target system this is as shown by the host
shown below
Figure 2: Gathering information on a target system (Host discovery)
b) Detecting malware infections on remote hosts
To detect malware on a target system the command nmap –script http malware-host is used, this
is as shown by the screenshots shown below (Figure 3 and figure 4)
One can continue to gather more information on a target system this is as shown by the host
shown below
Figure 2: Gathering information on a target system (Host discovery)
b) Detecting malware infections on remote hosts
To detect malware on a target system the command nmap –script http malware-host is used, this
is as shown by the screenshots shown below (Figure 3 and figure 4)
Firewall and Configuration 6
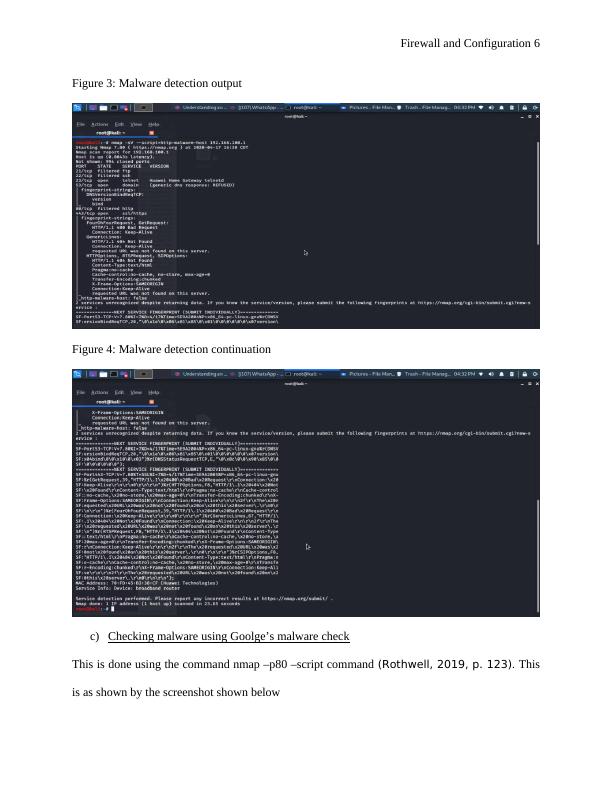
Figure 3: Malware detection output
Figure 4: Malware detection continuation
c) Checking malware using Goolge’s malware check
This is done using the command nmap –p80 –script command (Rothwell, 2019, p. 123). This
is as shown by the screenshot shown below
Figure 3: Malware detection output
Figure 4: Malware detection continuation
c) Checking malware using Goolge’s malware check
This is done using the command nmap –p80 –script command (Rothwell, 2019, p. 123). This
is as shown by the screenshot shown below
End of preview
Want to access all the pages? Upload your documents or become a member.
Related Documents
Assessment :Firewall Setup & Configurationlg...
|14
|1431
|14
Firewall Testing on Kali Linux using Nmaplg...
|18
|1810
|98
Overview of Network Securitylg...
|11
|1474
|434
Network Vulnerability And Cyber Securitylg...
|15
|1453
|15
Reflective Critical Analysis | Web Application Securitylg...
|5
|1203
|10
Network Security Tools: Nmap and Metasploitlg...
|9
|1824
|206
