MN502: Security Challenges and Solutions for Healthcare Networks
VerifiedAdded on 2023/06/04
|8
|570
|309
Report
AI Summary
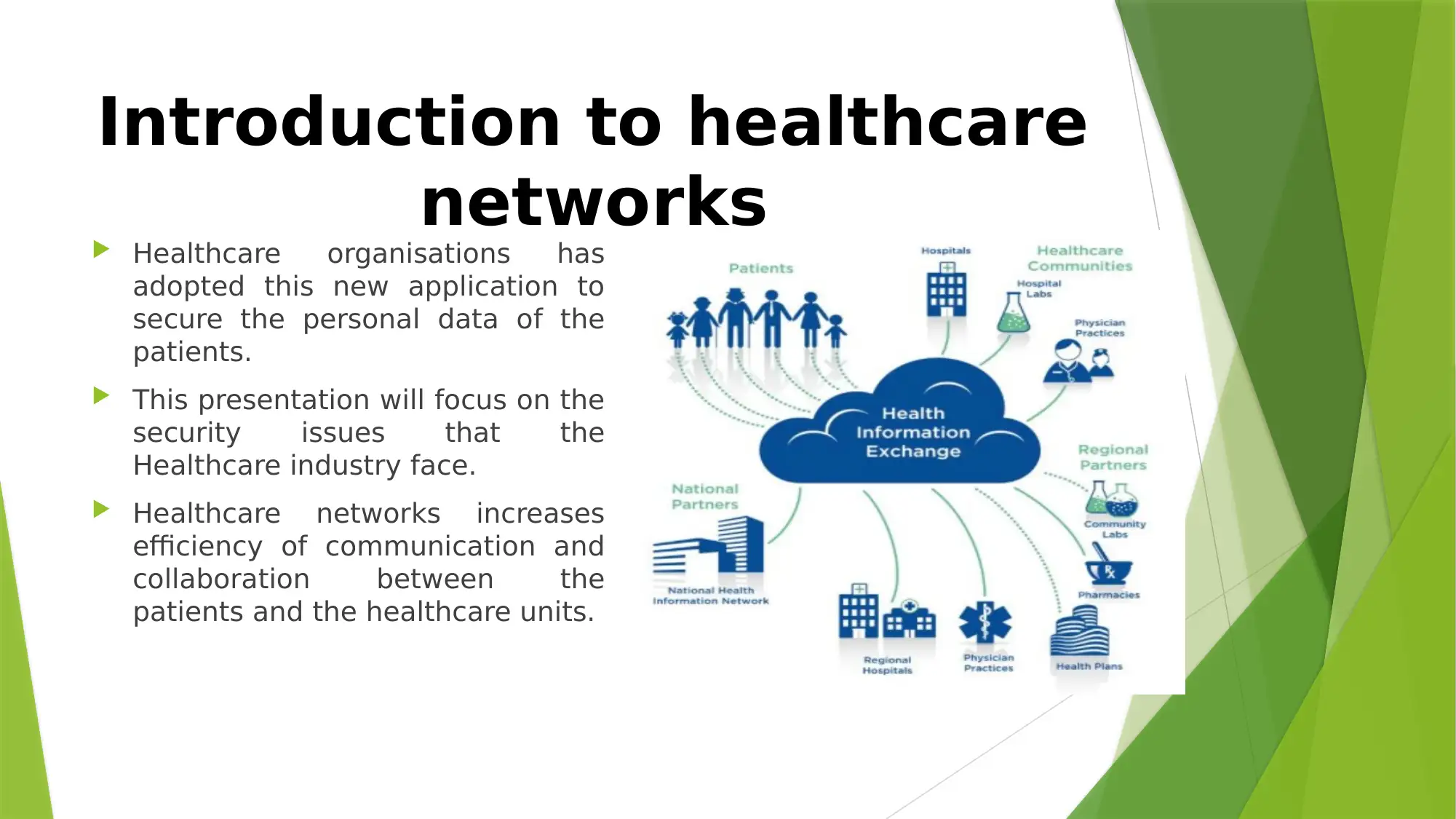
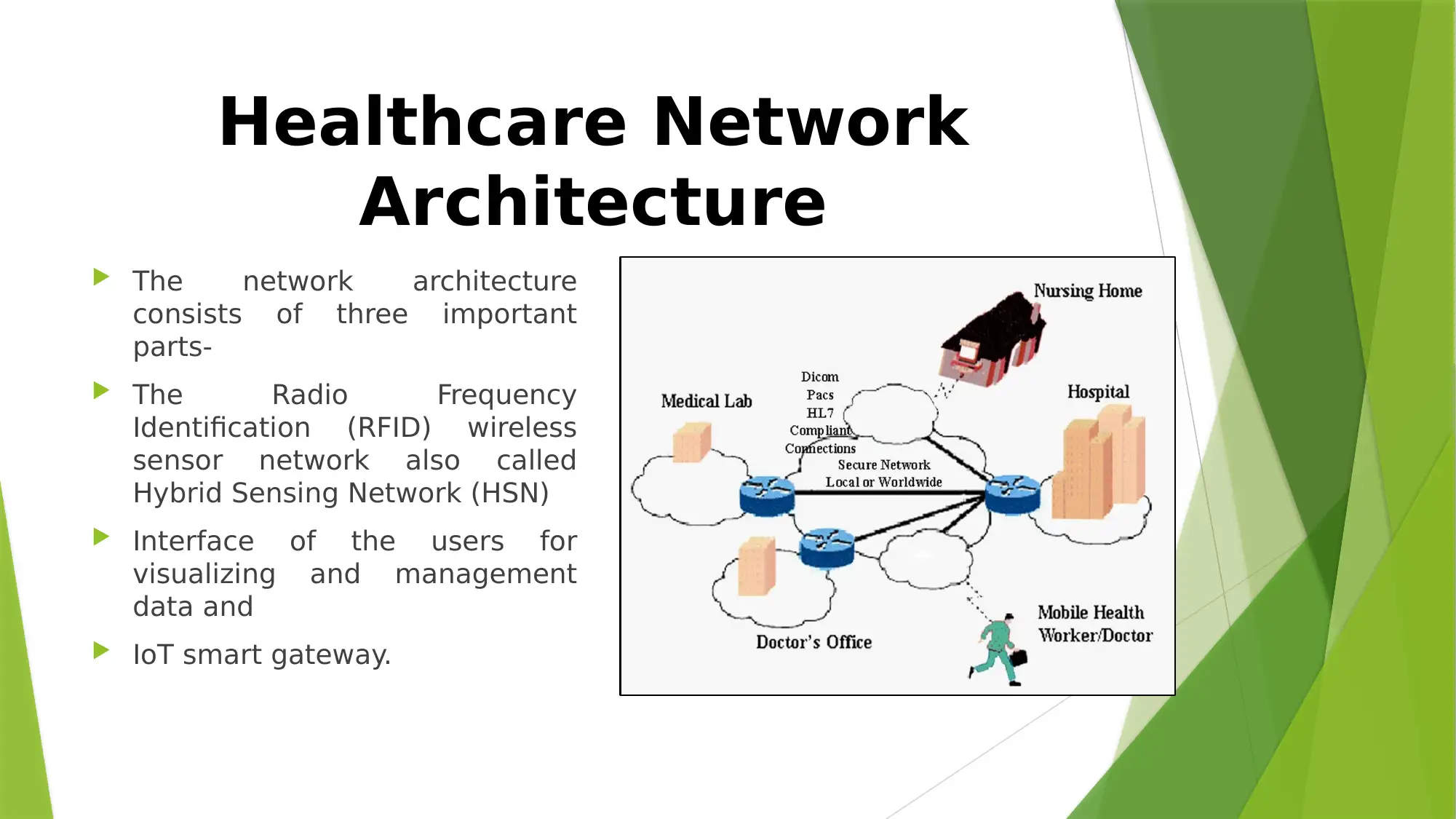
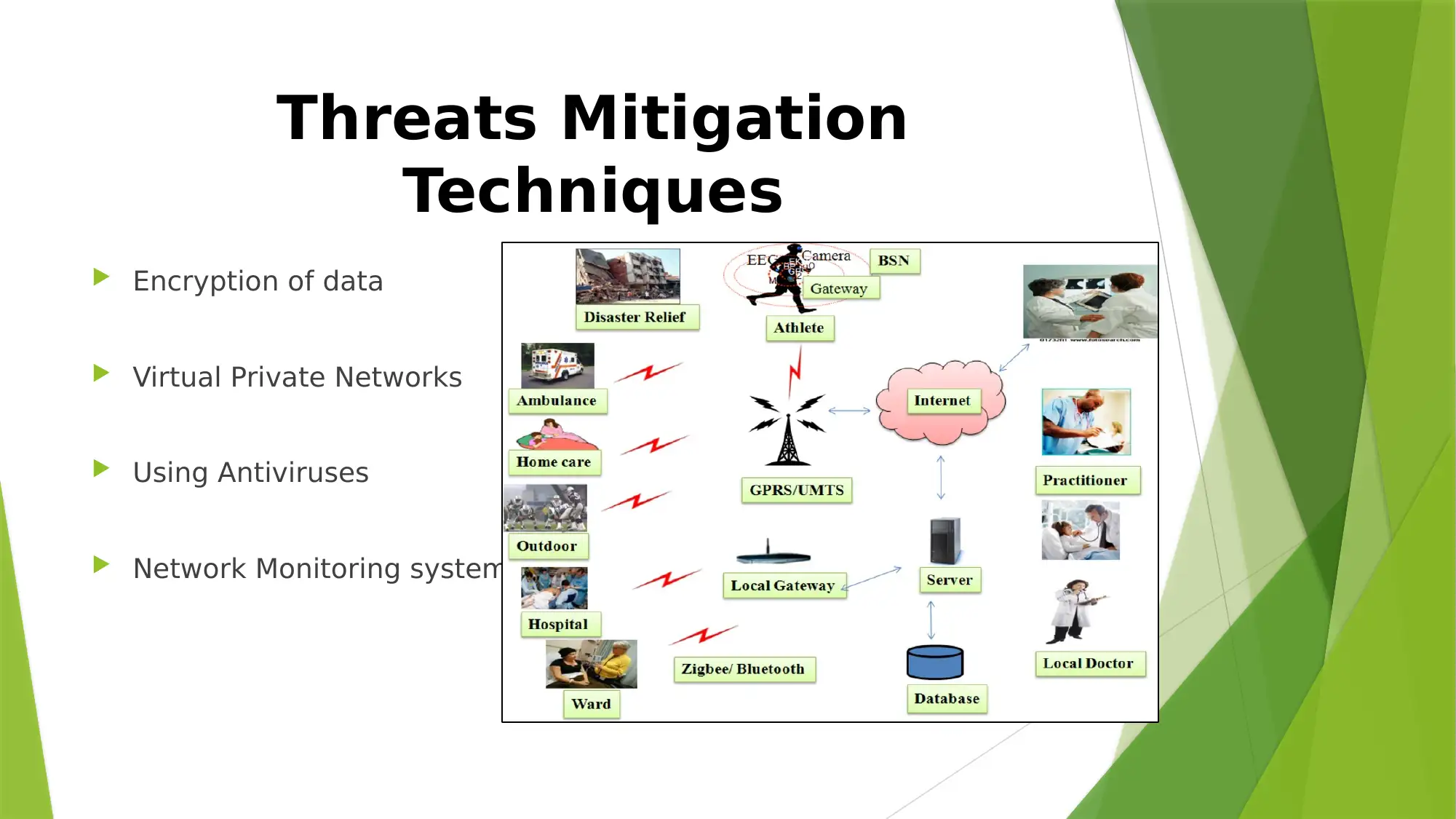
This report provides an overview of security challenges in healthcare networks, focusing on the increasing reliance on these networks for efficient communication and collaboration. It highlights the architecture of healthcare networks, including RFID wireless sensor networks, user interfaces, and IoT smart gateways. The report identifies key threats such as hackers, compromised WBAN nodes, packet sniffers, denial of service attacks, and malware. Mitigation techniques discussed include data encryption, virtual private networks, and network monitoring systems. The conclusion emphasizes the importance of strong security measures to maintain patient data confidentiality and prioritizes network security in healthcare organizations. References to various IEEE publications and online resources support the analysis and recommendations.
1 out of 8









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)