Healthcare Systems
VerifiedAdded on 2023/01/10
|7
|1001
|58
AI Summary
This document discusses the main processes in the MHR scenario, including hospitals deleting data and doctors checking user login. It also covers error detection in bit transmission and the ACID property in databases. The document provides insights into the importance of these processes and their impact on the healthcare system.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: HEALTHCARE SYSTEMS
Healthcare System
Name of the Student:
Name of the University:
Author Note
Healthcare System
Name of the Student:
Name of the University:
Author Note
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1
HEALTHCARE SYSTEMS
Activity 1
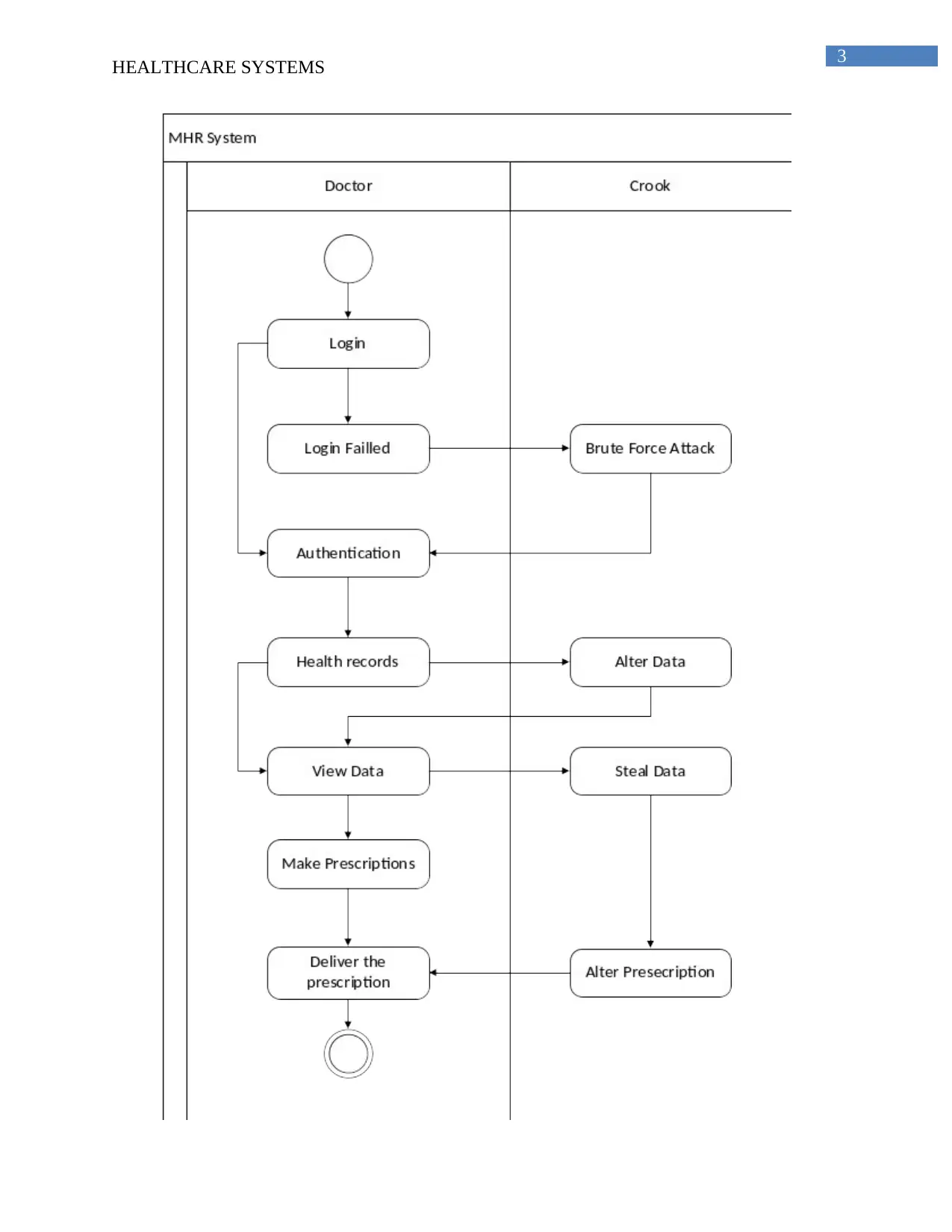
The two main processes that takes place within the MHR scenario are hospitals are
allowed to delete the data and can focus on maintaining health record data. Secondly the doctors
are allowed to check the user login so that the functioning can be processed effectively. This
processed are important to be focused so that they system can ensure better efficiency throughout
the system.
To login into the system process is mainly done for the purpose of getting into the
system. Once the user gets successfully logged in within the system than they can access all the
data related to doctors available.
The second process is to do lab test. In order to perform the lab test it becomes important
to have all details regarding the patients and should have proper access from hospital authorities.
The system gets accessible only when it allows the users to login into the system. The system can
be accessed by the users. The data can be deleted by the hospital authority for further cases.
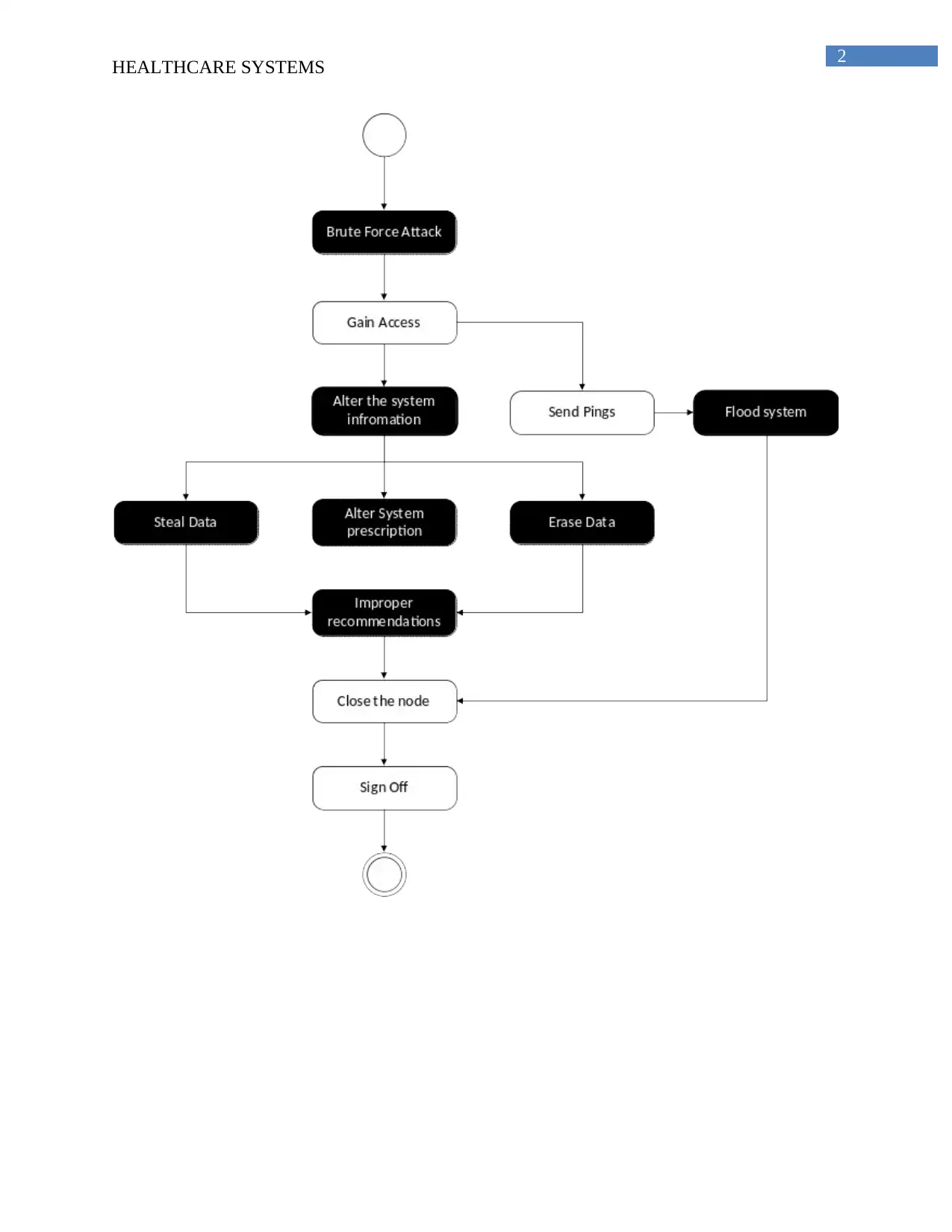
The malicious actions that can be taken against these activities are that if someone
manipulates the lab test results than it becomes difficult to address the accurate health conditions.
In addition to this log in should be provided to only authenticate users.
The Activity diagram for the malicious activities to be performed by a hacker is described
below:
HEALTHCARE SYSTEMS
Activity 1
The two main processes that takes place within the MHR scenario are hospitals are
allowed to delete the data and can focus on maintaining health record data. Secondly the doctors
are allowed to check the user login so that the functioning can be processed effectively. This
processed are important to be focused so that they system can ensure better efficiency throughout
the system.
To login into the system process is mainly done for the purpose of getting into the
system. Once the user gets successfully logged in within the system than they can access all the
data related to doctors available.
The second process is to do lab test. In order to perform the lab test it becomes important
to have all details regarding the patients and should have proper access from hospital authorities.
The system gets accessible only when it allows the users to login into the system. The system can
be accessed by the users. The data can be deleted by the hospital authority for further cases.
The malicious actions that can be taken against these activities are that if someone
manipulates the lab test results than it becomes difficult to address the accurate health conditions.
In addition to this log in should be provided to only authenticate users.
The Activity diagram for the malicious activities to be performed by a hacker is described
below:
2
HEALTHCARE SYSTEMS
HEALTHCARE SYSTEMS
3
HEALTHCARE SYSTEMS
HEALTHCARE SYSTEMS
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4
HEALTHCARE SYSTEMS
Activity 2
Error detection in bit transmission is performed by a redundancy check that is being
added towards the message so that it can easily detect the errors present within the bits. With the
help of error detection it becomes easy to perform proper encoding method that will ensure better
working of the system. Encoding and decoding becomes important as these method helps in
ensuring that the transmitted data is free from errors and no one has tampered the data. The
different schemes that are offered with error detection include repetition schemes, parity schemes
and checksums. The MHR system has successfully implemented cyclic redundancy check
method that helps in error control while transmitting a data. These uses effective error detection
codes so that proper way of encryption can be performed. On the other hand with the use of
parity schemes it becomes easy to detect the errors present within the bits.
Activity 3
ACID property is one of the important concepts for databases. This mainly stands for
atomicity, consistency, isolation and durability. Atomicity ensures that a transaction is being
performed effectively or will not get executed at all. The system of MHR ensures that all
transactions takes place effectively so that proper output can be obtained by the users.
Consistency is mainly performed for the purpose of maintaining proper values throughout the
objects (Kayes et al. 2018). The consistency will ensure a proper support towards all the data
stored. Isolation property of the system ensures that the system is allowed to make changes at a
time so that it does-not allow multiple data. Durability is referred to maintaining proper
transactions so that no update and data gets lost. The MHR system ensures that frequently the
data are updated within the system. With the proper maintenance of ACID property it becomes
HEALTHCARE SYSTEMS
Activity 2
Error detection in bit transmission is performed by a redundancy check that is being
added towards the message so that it can easily detect the errors present within the bits. With the
help of error detection it becomes easy to perform proper encoding method that will ensure better
working of the system. Encoding and decoding becomes important as these method helps in
ensuring that the transmitted data is free from errors and no one has tampered the data. The
different schemes that are offered with error detection include repetition schemes, parity schemes
and checksums. The MHR system has successfully implemented cyclic redundancy check
method that helps in error control while transmitting a data. These uses effective error detection
codes so that proper way of encryption can be performed. On the other hand with the use of
parity schemes it becomes easy to detect the errors present within the bits.
Activity 3
ACID property is one of the important concepts for databases. This mainly stands for
atomicity, consistency, isolation and durability. Atomicity ensures that a transaction is being
performed effectively or will not get executed at all. The system of MHR ensures that all
transactions takes place effectively so that proper output can be obtained by the users.
Consistency is mainly performed for the purpose of maintaining proper values throughout the
objects (Kayes et al. 2018). The consistency will ensure a proper support towards all the data
stored. Isolation property of the system ensures that the system is allowed to make changes at a
time so that it does-not allow multiple data. Durability is referred to maintaining proper
transactions so that no update and data gets lost. The MHR system ensures that frequently the
data are updated within the system. With the proper maintenance of ACID property it becomes

5
HEALTHCARE SYSTEMS
easy to maintain the working of the system without any issues. The atomicity property helps the
data and system to maintain confidentiality. In order to determine the proper working of database
transaction rules it becomes essential to ensure that the system is following all the necessary
procedure. The database needs to maintain proper check on the system so that each and every
activity can be understood efficiently.
The role based access control are mainly applied within the MHR system is to ensure that
only authorized person of the hospitals are allowed to access user data. This will restrict the users
from further modifying the data. Moreover this ensures that no one has got the opportunity to
impact the system. Role based access control is referred to the method that helps in restricting
the network access based on the individuals roles within the organization. With the
implementation of RBAC it will become easy to maintain security towards the MHR system.
This will ensure that a limited amount of access is provided towards the users. These will
safeguard the details regarding users and will protect the organization from further damages.
HEALTHCARE SYSTEMS
easy to maintain the working of the system without any issues. The atomicity property helps the
data and system to maintain confidentiality. In order to determine the proper working of database
transaction rules it becomes essential to ensure that the system is following all the necessary
procedure. The database needs to maintain proper check on the system so that each and every
activity can be understood efficiently.
The role based access control are mainly applied within the MHR system is to ensure that
only authorized person of the hospitals are allowed to access user data. This will restrict the users
from further modifying the data. Moreover this ensures that no one has got the opportunity to
impact the system. Role based access control is referred to the method that helps in restricting
the network access based on the individuals roles within the organization. With the
implementation of RBAC it will become easy to maintain security towards the MHR system.
This will ensure that a limited amount of access is provided towards the users. These will
safeguard the details regarding users and will protect the organization from further damages.

6
HEALTHCARE SYSTEMS
Bibliography
Cai, S., Gallina, B., Nyström, D. and Seceleanu, C., 2015, July. Trading-off data consistency for
timeliness in real-time database systems. In Proceedings of the 27th Euromicro Conference on
Real-Time Systems (pp. 13-16).
Hosseinzadeh, S., Virtanen, S., Díaz-Rodríguez, N. and Lilius, J., 2016, June. A semantic
security framework and context-aware role-based access control ontology for smart spaces. In
Proceedings of the International Workshop on Semantic Big Data (p. 8). ACM.
Kayes, A.S.M., Rahayu, W., Dillon, T. and Chang, E., 2018, August. Accessing data from
multiple sources through context-aware access control. In 2018 17th IEEE International
Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE
International Conference On Big Data Science And Engineering (TrustCom/BigDataSE) (pp.
551-559). IEEE.
Prabhakaran, S. and Selvadurai, K., 2018. Performance analysis of security requirements
engineering framework by measuring the vulnerabilities. Int. Arab J. Inf. Technol., 15(3),
pp.435-444.
HEALTHCARE SYSTEMS
Bibliography
Cai, S., Gallina, B., Nyström, D. and Seceleanu, C., 2015, July. Trading-off data consistency for
timeliness in real-time database systems. In Proceedings of the 27th Euromicro Conference on
Real-Time Systems (pp. 13-16).
Hosseinzadeh, S., Virtanen, S., Díaz-Rodríguez, N. and Lilius, J., 2016, June. A semantic
security framework and context-aware role-based access control ontology for smart spaces. In
Proceedings of the International Workshop on Semantic Big Data (p. 8). ACM.
Kayes, A.S.M., Rahayu, W., Dillon, T. and Chang, E., 2018, August. Accessing data from
multiple sources through context-aware access control. In 2018 17th IEEE International
Conference On Trust, Security And Privacy In Computing And Communications/12th IEEE
International Conference On Big Data Science And Engineering (TrustCom/BigDataSE) (pp.
551-559). IEEE.
Prabhakaran, S. and Selvadurai, K., 2018. Performance analysis of security requirements
engineering framework by measuring the vulnerabilities. Int. Arab J. Inf. Technol., 15(3),
pp.435-444.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





