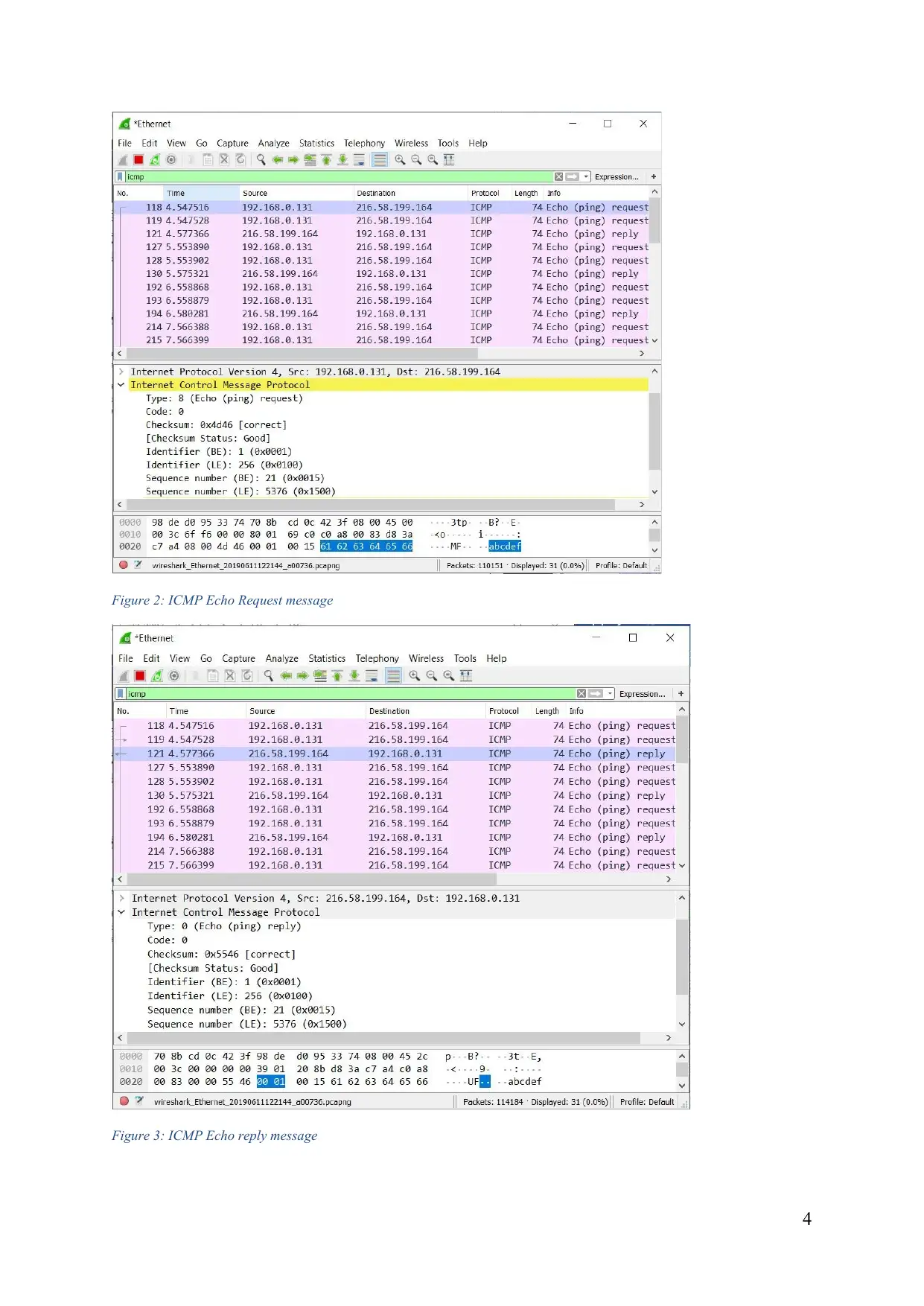
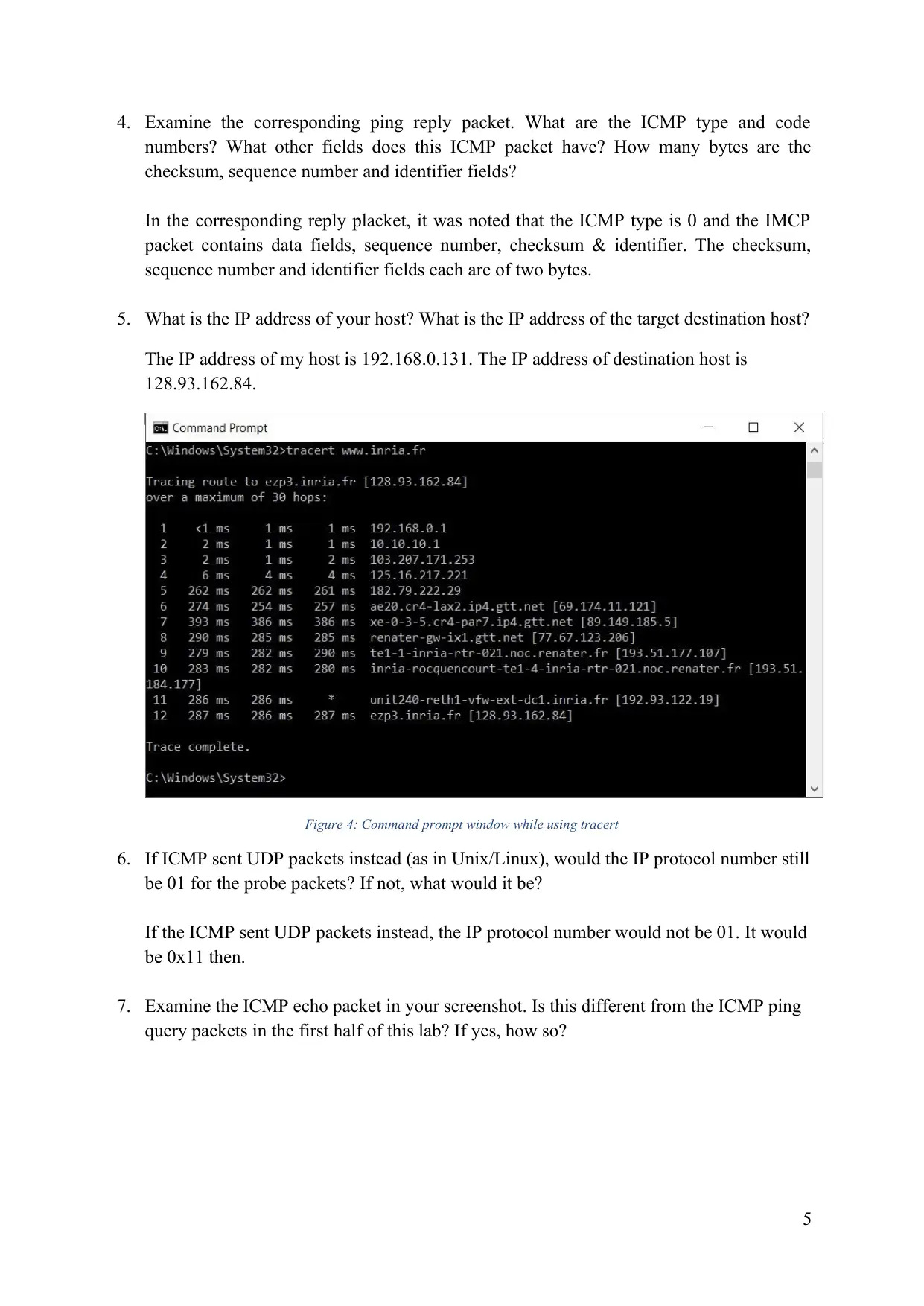
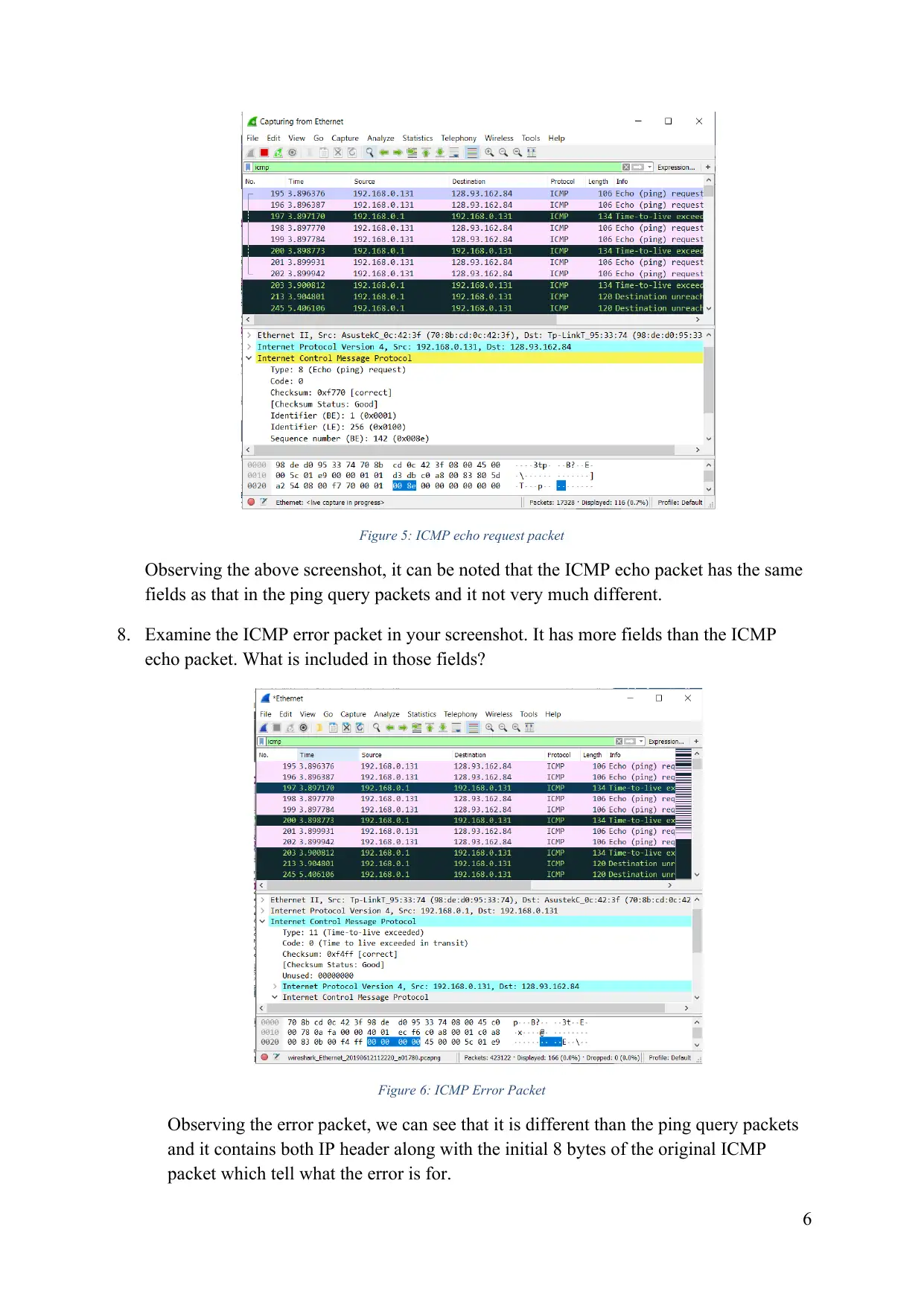
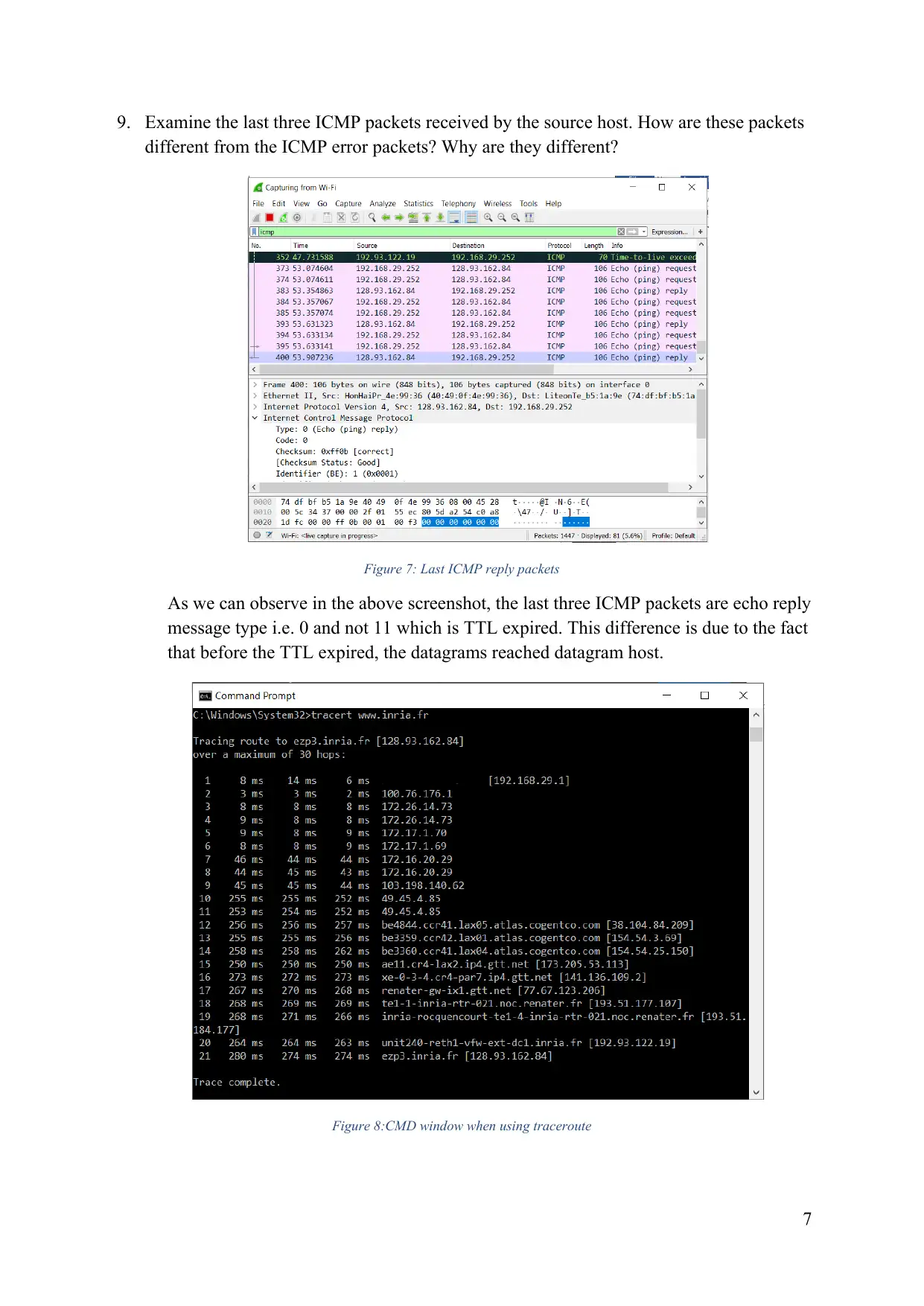
This lab report delves into the intricacies of ICMP (Internet Control Message Protocol) and its role in network communication. Through a series of experiments involving ping and tracert, we explore the structure of ICMP packets, their behavior in different scenarios, and the impact of fragmentation on data transmission. The report analyzes the various fields within ICMP packets, including type, code, identifier, sequence number, and checksum, and examines how these fields change in response to different network conditions. We also investigate the use of pingplotter to measure network latency and packet loss, providing insights into network performance and troubleshooting techniques. The lab concludes with a detailed analysis of IP fragmentation, demonstrating how large packets are divided into smaller fragments for efficient transmission across networks.
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)