ICT106 Data Communications and Networks
VerifiedAdded on 2022/08/18
|11
|681
|11
Presentation
AI Summary
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

ICT106 DATA
COMMUNICATIONS
AND NETWORKS
NAME OF THE STUDENT
NAME OF THE UNIVERSITY
COMMUNICATIONS
AND NETWORKS
NAME OF THE STUDENT
NAME OF THE UNIVERSITY
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

INTRODUCTION
• XYZ company have its main office in Sydney and the other
two remote office in Melbourne and Adelaide. The main aim
of the report is allocation of unreserved public IPv4 address
to the offices located in different geographical location. A
design and explanation of the LAN for the office is
presented and a discussion is made on the LAN topology
for the selection of the particular topology.
• XYZ company have its main office in Sydney and the other
two remote office in Melbourne and Adelaide. The main aim
of the report is allocation of unreserved public IPv4 address
to the offices located in different geographical location. A
design and explanation of the LAN for the office is
presented and a discussion is made on the LAN topology
for the selection of the particular topology.
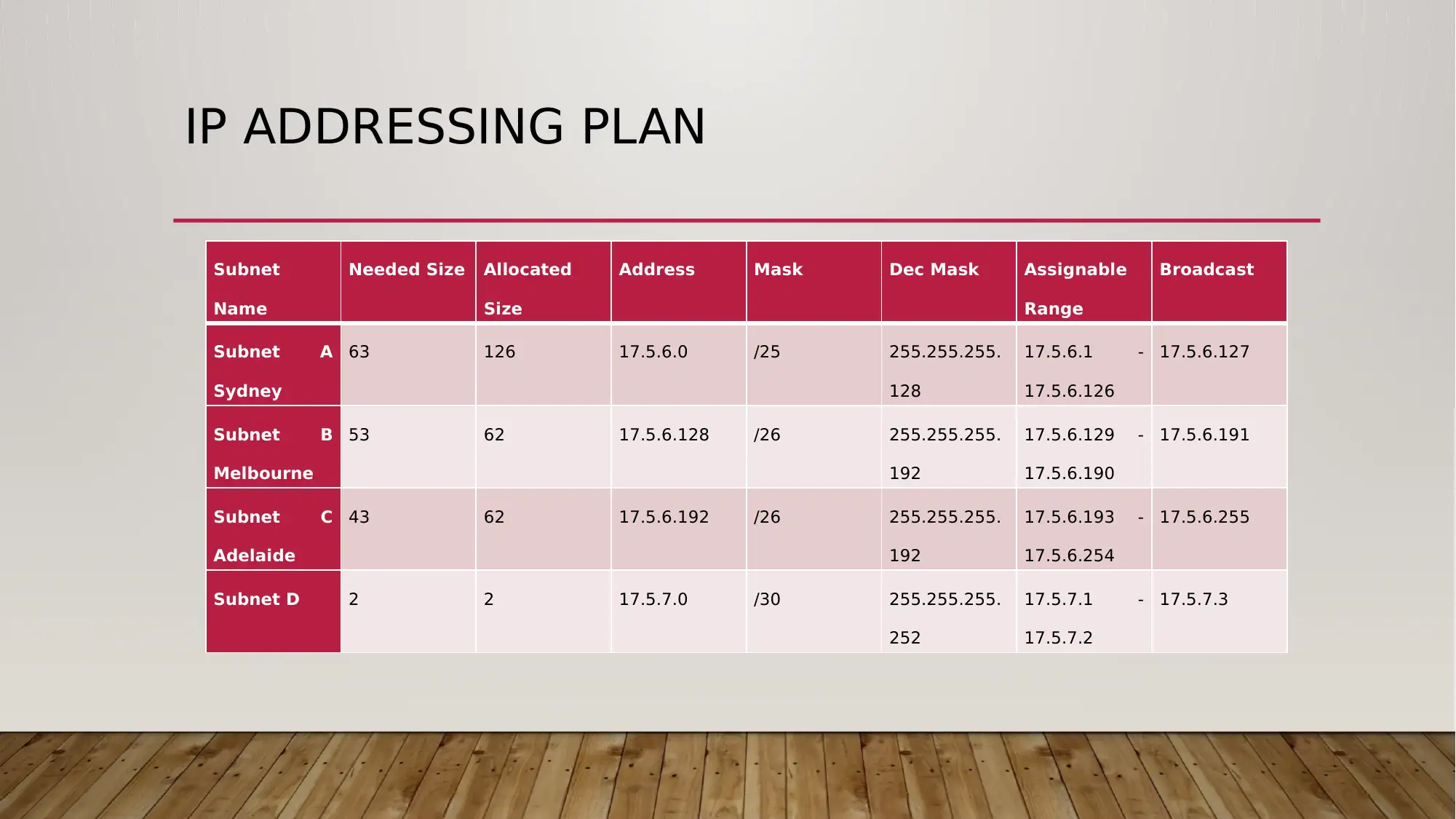
IP ADDRESSING PLAN
Subnet
Name
Needed Size Allocated
Size
Address Mask Dec Mask Assignable
Range
Broadcast
Subnet A
Sydney
63 126 17.5.6.0 /25 255.255.255.
128
17.5.6.1 -
17.5.6.126
17.5.6.127
Subnet B
Melbourne
53 62 17.5.6.128 /26 255.255.255.
192
17.5.6.129 -
17.5.6.190
17.5.6.191
Subnet C
Adelaide
43 62 17.5.6.192 /26 255.255.255.
192
17.5.6.193 -
17.5.6.254
17.5.6.255
Subnet D 2 2 17.5.7.0 /30 255.255.255.
252
17.5.7.1 -
17.5.7.2
17.5.7.3
Subnet
Name
Needed Size Allocated
Size
Address Mask Dec Mask Assignable
Range
Broadcast
Subnet A
Sydney
63 126 17.5.6.0 /25 255.255.255.
128
17.5.6.1 -
17.5.6.126
17.5.6.127
Subnet B
Melbourne
53 62 17.5.6.128 /26 255.255.255.
192
17.5.6.129 -
17.5.6.190
17.5.6.191
Subnet C
Adelaide
43 62 17.5.6.192 /26 255.255.255.
192
17.5.6.193 -
17.5.6.254
17.5.6.255
Subnet D 2 2 17.5.7.0 /30 255.255.255.
252
17.5.7.1 -
17.5.7.2
17.5.7.3
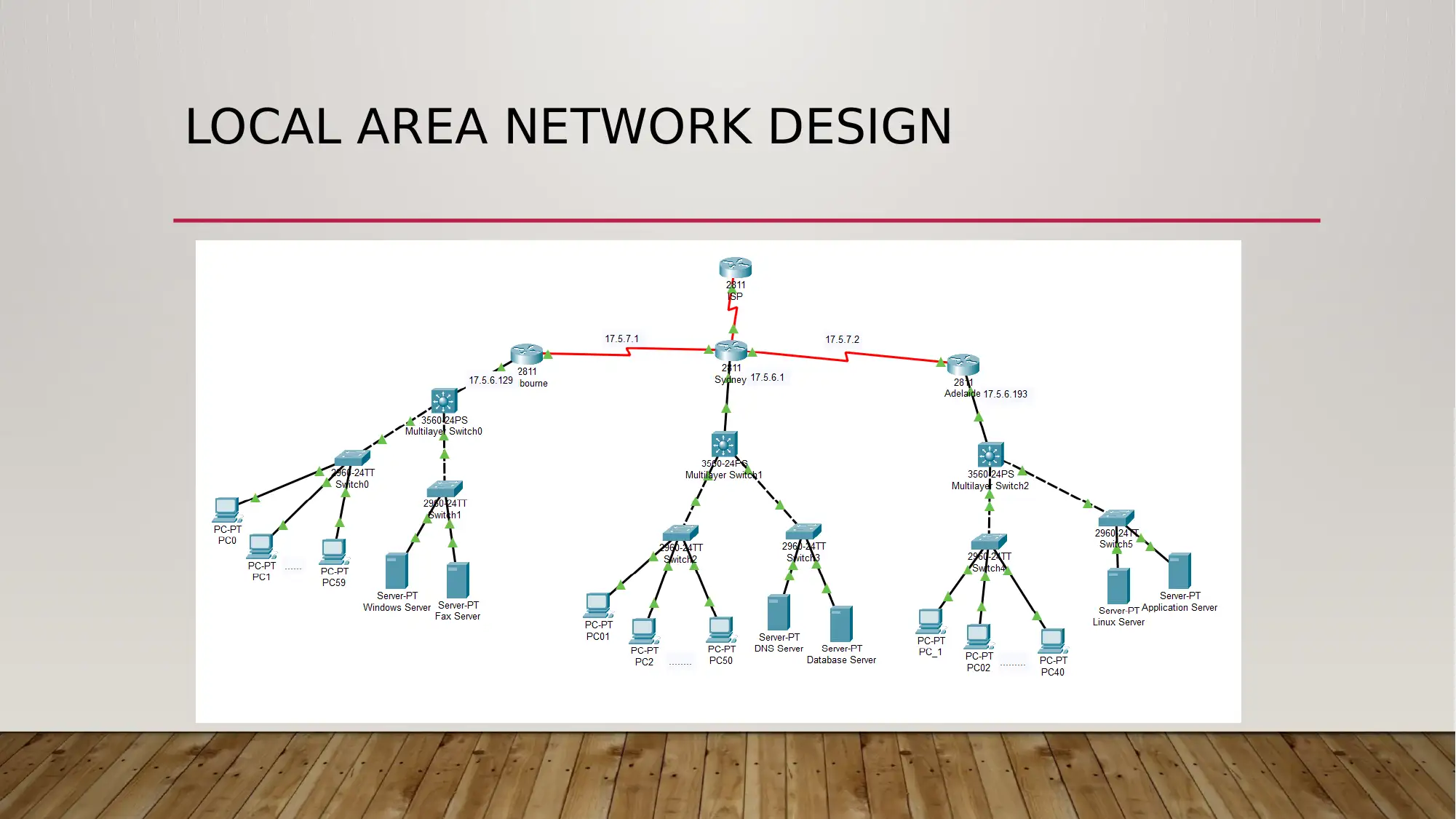
LOCAL AREA NETWORK DESIGN
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
NETWORK DESIGN JUSTIFICATION
• The LAN is designed such that the computer and the
servers are kept in different subnet such that the security
of the network is maintained. For each of the location
different routers are used and similar topology is followed
each of the office for decreasing the complication of the
network design.
• The LAN is designed such that the computer and the
servers are kept in different subnet such that the security
of the network is maintained. For each of the location
different routers are used and similar topology is followed
each of the office for decreasing the complication of the
network design.
LAN TOPOLOGY
• The network is developed following the three layer hierarchical
design topology such that the scalability, reliability and availability
of the network can be improved. This type of topology finds its
application for small, medium and large scale enterprise network
and the designed can be tailored based on the change in needs of
the organization. For a small network as for the branch office less
number of distribution level devices are needed and it can be
increased with the increase in number of users in the branch.
• The network is developed following the three layer hierarchical
design topology such that the scalability, reliability and availability
of the network can be improved. This type of topology finds its
application for small, medium and large scale enterprise network
and the designed can be tailored based on the change in needs of
the organization. For a small network as for the branch office less
number of distribution level devices are needed and it can be
increased with the increase in number of users in the branch.
LAN PROTOCOLS
• The layer 3 switch is configured with VLAN based on the number
of department in each of the branch or head office. The layer 2
device connected with the layer 3 switch is configured as client
for automatically getting the VLAN information and allow access
of the subnet for that department. The core device is configured
with VTP protocol such that it can share the VLAN information
with the connected client devices and reduces the complexity if
any change is needed to be made in the network.
• The layer 3 switch is configured with VLAN based on the number
of department in each of the branch or head office. The layer 2
device connected with the layer 3 switch is configured as client
for automatically getting the VLAN information and allow access
of the subnet for that department. The core device is configured
with VTP protocol such that it can share the VLAN information
with the connected client devices and reduces the complexity if
any change is needed to be made in the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
HARDWARE REQUIREMENT
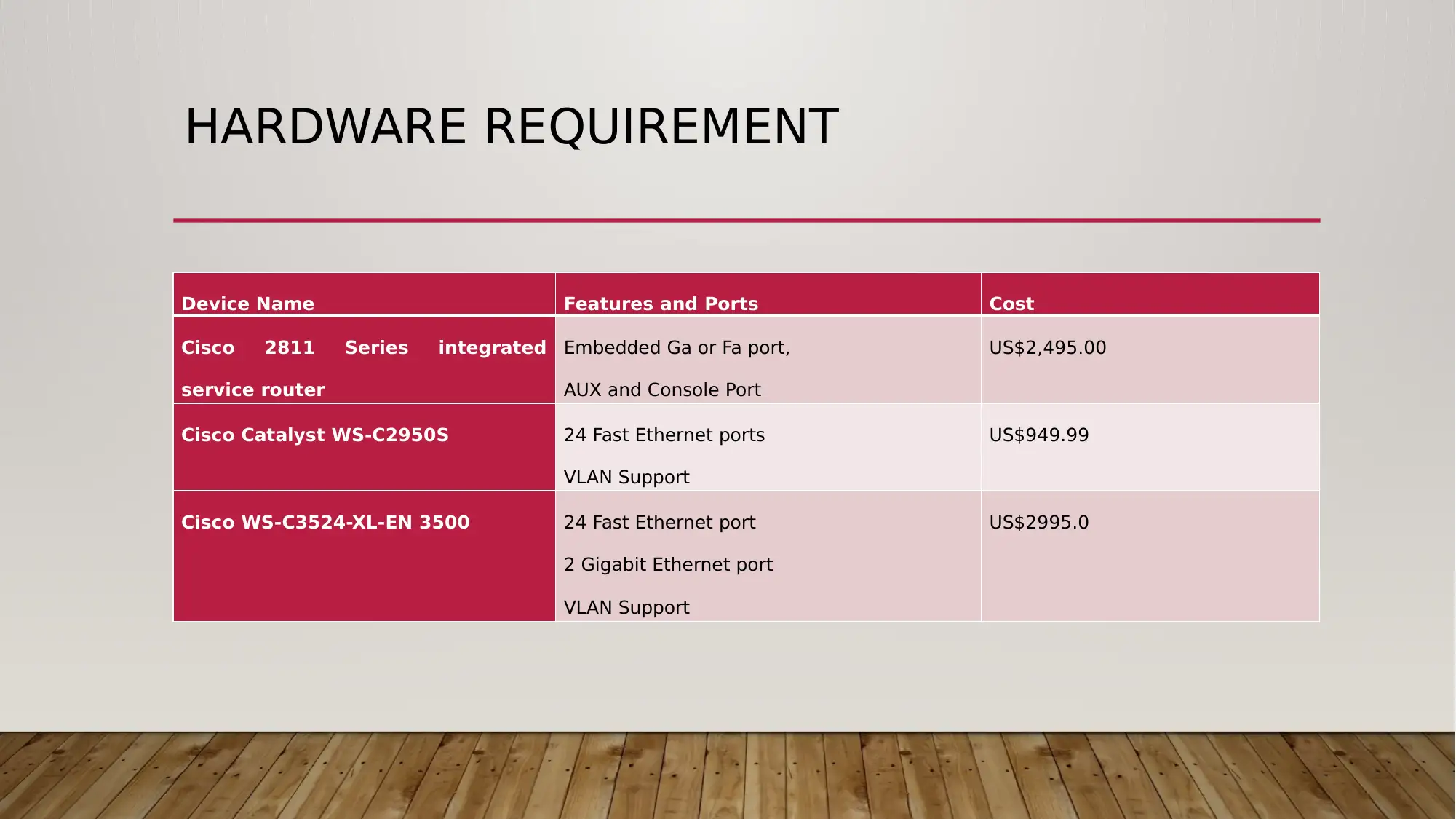
Device Name Features and Ports Cost
Cisco 2811 Series integrated
service router
Embedded Ga or Fa port,
AUX and Console Port
US$2,495.00
Cisco Catalyst WS-C2950S 24 Fast Ethernet ports
VLAN Support
US$949.99
Cisco WS-C3524-XL-EN 3500 24 Fast Ethernet port
2 Gigabit Ethernet port
VLAN Support
US$2995.0
Device Name Features and Ports Cost
Cisco 2811 Series integrated
service router
Embedded Ga or Fa port,
AUX and Console Port
US$2,495.00
Cisco Catalyst WS-C2950S 24 Fast Ethernet ports
VLAN Support
US$949.99
Cisco WS-C3524-XL-EN 3500 24 Fast Ethernet port
2 Gigabit Ethernet port
VLAN Support
US$2995.0

CONCLUSION
• Development of the subnet plan for the XYZ company can help in
increasing the efficiency of usability of the IP address. A design of
the LAN is created after analyzing the number of hosts that are
needed to be connected per subnet. The application usage and
the inter department data transfer needs is also analyzed for the
development of the network. The wireless access that is needed
to be maintained for the user and the communication needs is
analyzed for the development of the network.
• Development of the subnet plan for the XYZ company can help in
increasing the efficiency of usability of the IP address. A design of
the LAN is created after analyzing the number of hosts that are
needed to be connected per subnet. The application usage and
the inter department data transfer needs is also analyzed for the
development of the network. The wireless access that is needed
to be maintained for the user and the communication needs is
analyzed for the development of the network.

BIBLIOGRAPHY
• Ali, I., Hussain, S.S., Tak, A. and Ustun, T.S., 2017. Communication modeling for differential protection in IEC-61850-
based substations. IEEE Transactions on Industry Applications, 54(1), pp.135-142.
• Bae, M., Kim, K. and Kim, H., 2016. Preserving privacy and efficiency in data communication and aggregation for AMI
network. Journal of Network and Computer Applications, 59, pp.333-344.
• Cunha, F., Villas, L., Boukerche, A., Maia, G., Viana, A., Mini, R.A. and Loureiro, A.A., 2016. Data communication in
VANETs: Protocols, applications and challenges. Ad Hoc Networks, 44, pp.90-103.
• Dike, D.O., Obiora, V. and Eze, C., 2016. Improving congestion control in data communication network using queuing
theory model. IOSR Journal of Electrical and Electronics Engineering, 11(2), pp.49-53.
• Ito, K., Hashimoto, K. and Shibata, Y., 2017, November. V2X communication system for sharing road alert information
using cognitive network. In 2017 IEEE 8th International Conference on Awareness Science and Technology
(iCAST) (pp. 533-538). IEEE.
• Li, J., Peng, Z., Gao, S., Xiao, B. and Chan, H., 2017. Smartphone-assisted energy efficient data communication for
wearable devices. Computer Communications, 105, pp.33-43.
• Ali, I., Hussain, S.S., Tak, A. and Ustun, T.S., 2017. Communication modeling for differential protection in IEC-61850-
based substations. IEEE Transactions on Industry Applications, 54(1), pp.135-142.
• Bae, M., Kim, K. and Kim, H., 2016. Preserving privacy and efficiency in data communication and aggregation for AMI
network. Journal of Network and Computer Applications, 59, pp.333-344.
• Cunha, F., Villas, L., Boukerche, A., Maia, G., Viana, A., Mini, R.A. and Loureiro, A.A., 2016. Data communication in
VANETs: Protocols, applications and challenges. Ad Hoc Networks, 44, pp.90-103.
• Dike, D.O., Obiora, V. and Eze, C., 2016. Improving congestion control in data communication network using queuing
theory model. IOSR Journal of Electrical and Electronics Engineering, 11(2), pp.49-53.
• Ito, K., Hashimoto, K. and Shibata, Y., 2017, November. V2X communication system for sharing road alert information
using cognitive network. In 2017 IEEE 8th International Conference on Awareness Science and Technology
(iCAST) (pp. 533-538). IEEE.
• Li, J., Peng, Z., Gao, S., Xiao, B. and Chan, H., 2017. Smartphone-assisted energy efficient data communication for
wearable devices. Computer Communications, 105, pp.33-43.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





