Murdoch University ICT287: Computer Security Report - Analysis
VerifiedAdded on 2023/01/19
|14
|2703
|84
Report
AI Summary
This report, prepared for Murdoch University's ICT287 Computer Security course, examines the security posture of 'Planet of the Grapes,' a local wine and spirit merchant. The assignment is divided into two primary sections. The first section focuses on attack surface modeling, assessing potential network and physical attacks. This involves using tools like Nmap and Nessus to identify vulnerabilities, including open ports, outdated software, and misconfigurations. The analysis identifies vulnerabilities such as the lack of SMB signing and DCE Service Enumeration. The second section addresses legacy code vulnerabilities, particularly those related to offline credit card processing. The report highlights the risks associated with the existing system, like the use of spoofed cards and the limitations of the MOD 10 algorithm. The report recommends training for sales representatives, ensuring 24/7 payment partner support, and enforcing transaction limits for offline card processing. The report also includes a bibliography of relevant sources.

Running head: ICT287 COMPUTER SECURITY
ICT287 Computer Security: Planet of the Grapes
Name of the Student
Name of the University
Author’s Note
ICT287 Computer Security: Planet of the Grapes
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
ICT287 COMPUTER SECURITY
Answer 1: Attack Surface Modelling
For performing the auditing, the image of the server machine is downloaded and
configured with host only adapter for assessing the attacking surface for the machine. The
analysis is done for analyzing the network level attacks and the physical attacks that can
compromise the security of the organization and incur a huge loss for the organization.
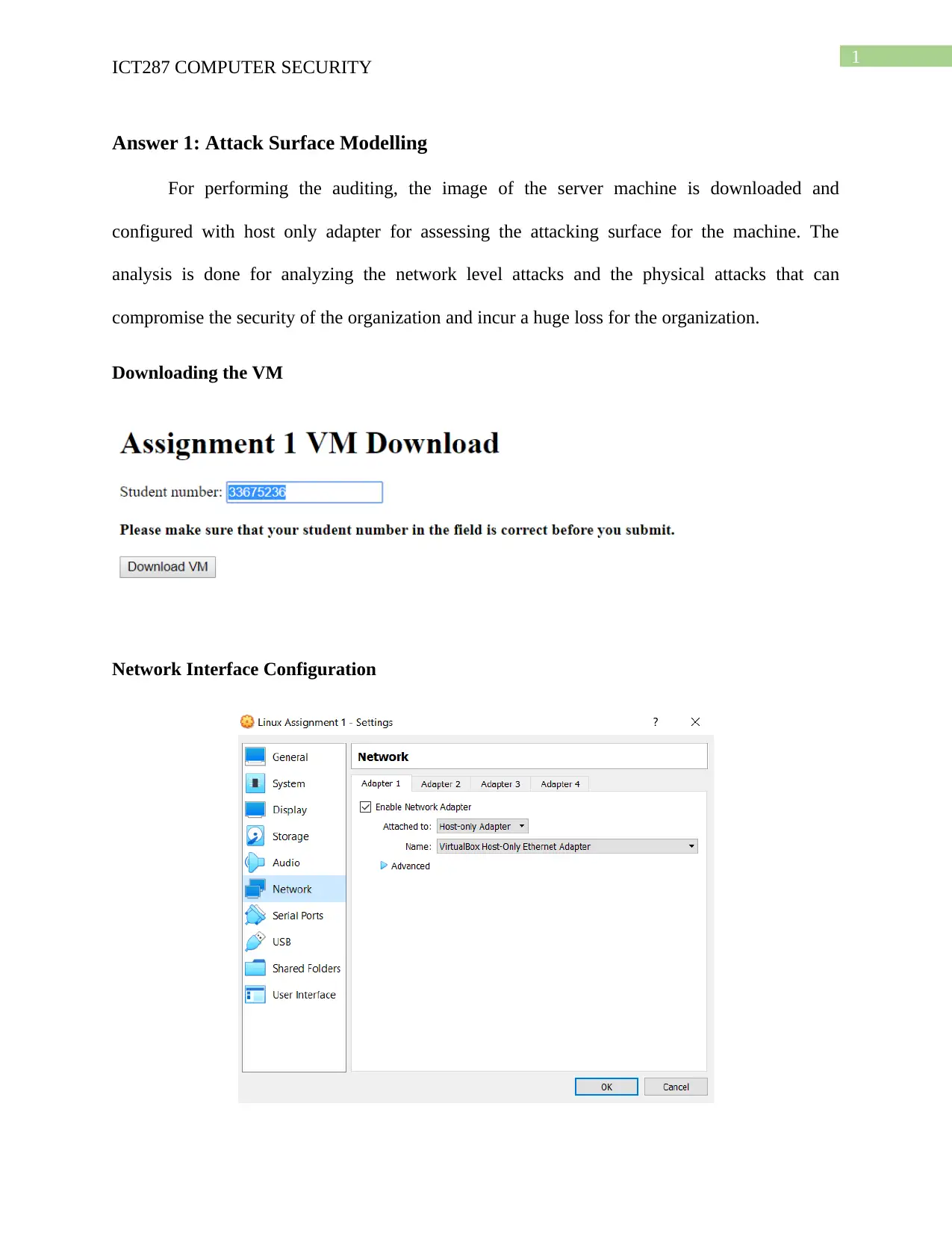
Downloading the VM
Network Interface Configuration
ICT287 COMPUTER SECURITY
Answer 1: Attack Surface Modelling
For performing the auditing, the image of the server machine is downloaded and
configured with host only adapter for assessing the attacking surface for the machine. The
analysis is done for analyzing the network level attacks and the physical attacks that can
compromise the security of the organization and incur a huge loss for the organization.
Downloading the VM
Network Interface Configuration
2
ICT287 COMPUTER SECURITY
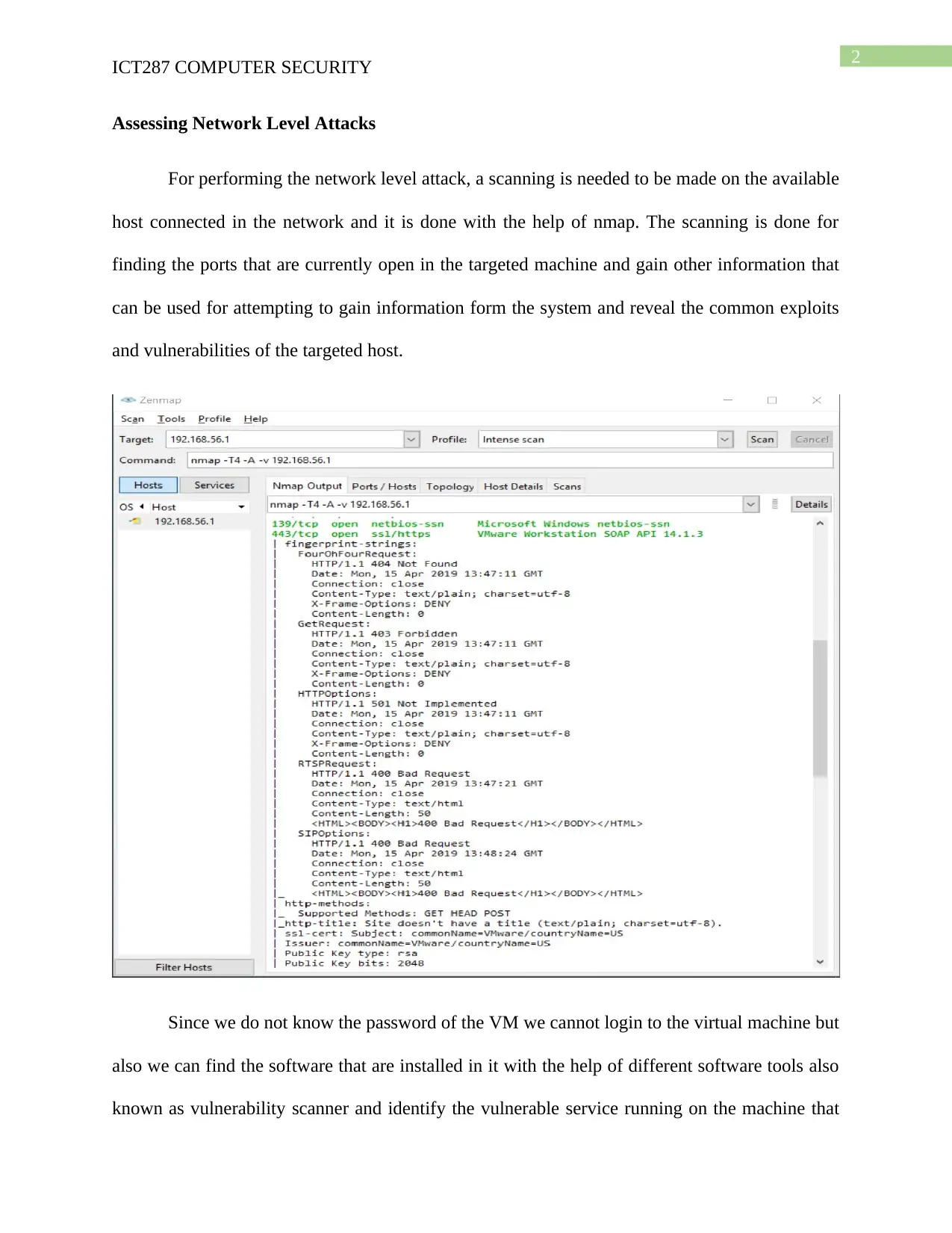
Assessing Network Level Attacks
For performing the network level attack, a scanning is needed to be made on the available
host connected in the network and it is done with the help of nmap. The scanning is done for
finding the ports that are currently open in the targeted machine and gain other information that
can be used for attempting to gain information form the system and reveal the common exploits
and vulnerabilities of the targeted host.
Since we do not know the password of the VM we cannot login to the virtual machine but
also we can find the software that are installed in it with the help of different software tools also
known as vulnerability scanner and identify the vulnerable service running on the machine that
ICT287 COMPUTER SECURITY
Assessing Network Level Attacks
For performing the network level attack, a scanning is needed to be made on the available
host connected in the network and it is done with the help of nmap. The scanning is done for
finding the ports that are currently open in the targeted machine and gain other information that
can be used for attempting to gain information form the system and reveal the common exploits
and vulnerabilities of the targeted host.
Since we do not know the password of the VM we cannot login to the virtual machine but
also we can find the software that are installed in it with the help of different software tools also
known as vulnerability scanner and identify the vulnerable service running on the machine that
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
ICT287 COMPUTER SECURITY
can be used for intercepting and monitoring the traffic in then network and compromise the
network security.
Nessus is used for scanning the current vulnerability of the network and identify the
potential holes such as outdated software, open ports and use of default password on the devices.
The hacking of a local area network can be done easily with running a vulnerability scanner and
then running a penetration testing on the targeted machine connected in the local area network.
The test of the vulnerability is done by following two steps such as scanning the vulnerability for
revealing the possibility of the problem and performing a penetration testing for exploitation of
the possible problem. Nessus is used for performing the vulnerability testing and since its free
version offers different tools for exploring the network it is selected. It also helps to point
different tools for performing a penetration test in the network. For using the Nessus an online
account is needed to be created for getting an activation code and downloading the software.
After the completion of the installation the Nessus account is needed to set up and the sign up
process is needed to be completed. While connecting for the first time a warning of connect not
secure is displayed in the web browser and the advanced option is needed to be selected for
ICT287 COMPUTER SECURITY
can be used for intercepting and monitoring the traffic in then network and compromise the
network security.
Nessus is used for scanning the current vulnerability of the network and identify the
potential holes such as outdated software, open ports and use of default password on the devices.
The hacking of a local area network can be done easily with running a vulnerability scanner and
then running a penetration testing on the targeted machine connected in the local area network.
The test of the vulnerability is done by following two steps such as scanning the vulnerability for
revealing the possibility of the problem and performing a penetration testing for exploitation of
the possible problem. Nessus is used for performing the vulnerability testing and since its free
version offers different tools for exploring the network it is selected. It also helps to point
different tools for performing a penetration test in the network. For using the Nessus an online
account is needed to be created for getting an activation code and downloading the software.
After the completion of the installation the Nessus account is needed to set up and the sign up
process is needed to be completed. While connecting for the first time a warning of connect not
secure is displayed in the web browser and the advanced option is needed to be selected for
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ICT287 COMPUTER SECURITY
proceeding with the local host and bypassing the warning. An account is created and named audit
and the activation code received via email is inputted for proceeding with the next step of
performing network level attacks. A number of tools and plugins are downloaded for scanning
the network and updating the utilities and it takes several minutes.
In the following step a vulnerability scan is performed on the network for testing the
network for identification of the problem and the basic network scan is used for performing most
of the test since a good overview can be obtained from using the option. Apart from the basic
scan the advanced scan can also be used for including more parameters such that the scan can be
narrowed, there are different scan such as Badlock detection scan used for analyzing the security
issues with the help of SAMBA, Shellsock scan used for analyzing the vulnerabilities of old
linux machines, Drown Scan for looking at the hosting sites of the computers that are susceptible
for Drown attack and other types of acute scans. The issues in the system can be picked from the
basic scan but the advanced scan can help beyond maintenance of a network and expose the
vulnerability of the private server that is exposed to the internet.
Assessing Physical Attacks
For analyzing the weakness and vulnerabilities in the system an evaluation is needed to
be made for the result. After finishing the network scan different color coded graphs are
generated for the device that refers the device connected in the network. Each of the color of the
graph demonstrates the danger of the identified vulnerability scaling from less to critical. All the
device of the network is included for performing the scan and the graph can be clicked for
getting more information about the vulnerability for each of the device. The list of the
vulnerabilities is provided under the plugins which demonstrates the methodology used by
Nessus to discover the vulnerability. More information can be found by clicking on the plugin
ICT287 COMPUTER SECURITY
proceeding with the local host and bypassing the warning. An account is created and named audit
and the activation code received via email is inputted for proceeding with the next step of
performing network level attacks. A number of tools and plugins are downloaded for scanning
the network and updating the utilities and it takes several minutes.
In the following step a vulnerability scan is performed on the network for testing the
network for identification of the problem and the basic network scan is used for performing most
of the test since a good overview can be obtained from using the option. Apart from the basic
scan the advanced scan can also be used for including more parameters such that the scan can be
narrowed, there are different scan such as Badlock detection scan used for analyzing the security
issues with the help of SAMBA, Shellsock scan used for analyzing the vulnerabilities of old
linux machines, Drown Scan for looking at the hosting sites of the computers that are susceptible
for Drown attack and other types of acute scans. The issues in the system can be picked from the
basic scan but the advanced scan can help beyond maintenance of a network and expose the
vulnerability of the private server that is exposed to the internet.
Assessing Physical Attacks
For analyzing the weakness and vulnerabilities in the system an evaluation is needed to
be made for the result. After finishing the network scan different color coded graphs are
generated for the device that refers the device connected in the network. Each of the color of the
graph demonstrates the danger of the identified vulnerability scaling from less to critical. All the
device of the network is included for performing the scan and the graph can be clicked for
getting more information about the vulnerability for each of the device. The list of the
vulnerabilities is provided under the plugins which demonstrates the methodology used by
Nessus to discover the vulnerability. More information can be found by clicking on the plugin
5
ICT287 COMPUTER SECURITY
and it also includes the white papers, patch notes and potential fixes. The vulnerability tab can
also be clicked for finding an overview of all the potential vulnerabilities as a whole of the
network.
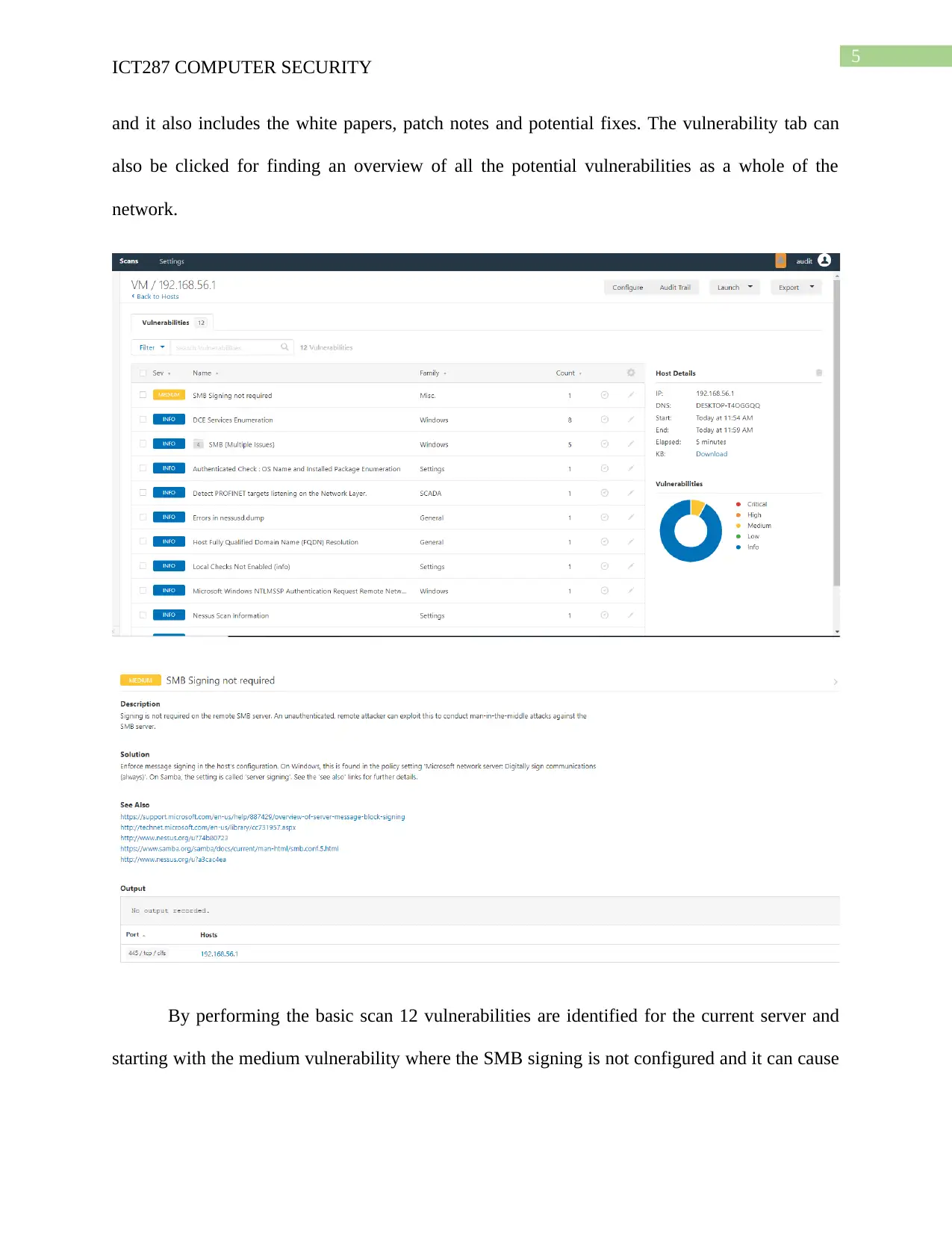
By performing the basic scan 12 vulnerabilities are identified for the current server and
starting with the medium vulnerability where the SMB signing is not configured and it can cause
ICT287 COMPUTER SECURITY
and it also includes the white papers, patch notes and potential fixes. The vulnerability tab can
also be clicked for finding an overview of all the potential vulnerabilities as a whole of the
network.
By performing the basic scan 12 vulnerabilities are identified for the current server and
starting with the medium vulnerability where the SMB signing is not configured and it can cause
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
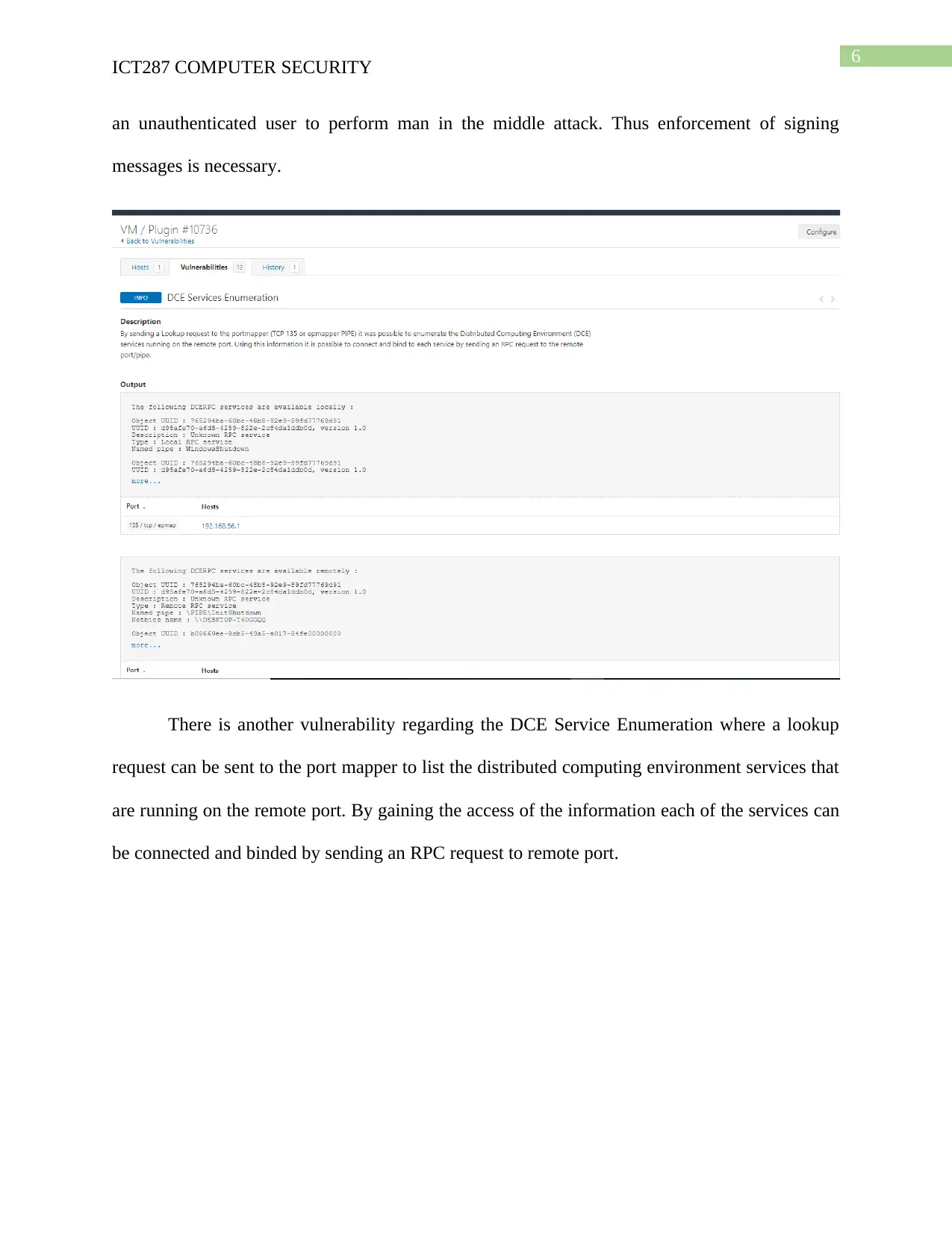
6
ICT287 COMPUTER SECURITY
an unauthenticated user to perform man in the middle attack. Thus enforcement of signing
messages is necessary.
There is another vulnerability regarding the DCE Service Enumeration where a lookup
request can be sent to the port mapper to list the distributed computing environment services that
are running on the remote port. By gaining the access of the information each of the services can
be connected and binded by sending an RPC request to remote port.
ICT287 COMPUTER SECURITY
an unauthenticated user to perform man in the middle attack. Thus enforcement of signing
messages is necessary.
There is another vulnerability regarding the DCE Service Enumeration where a lookup
request can be sent to the port mapper to list the distributed computing environment services that
are running on the remote port. By gaining the access of the information each of the services can
be connected and binded by sending an RPC request to remote port.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
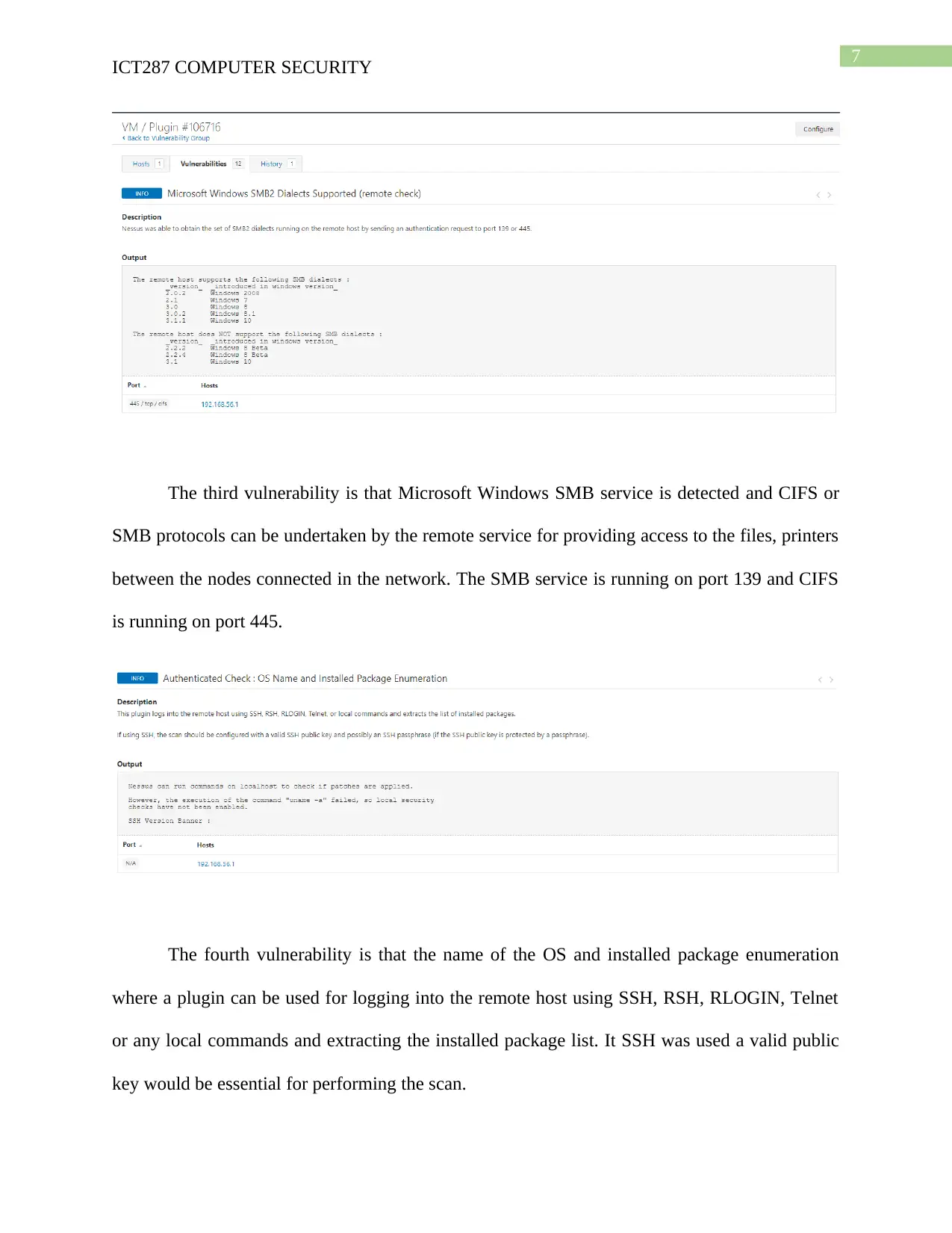
7
ICT287 COMPUTER SECURITY
The third vulnerability is that Microsoft Windows SMB service is detected and CIFS or
SMB protocols can be undertaken by the remote service for providing access to the files, printers
between the nodes connected in the network. The SMB service is running on port 139 and CIFS
is running on port 445.
The fourth vulnerability is that the name of the OS and installed package enumeration
where a plugin can be used for logging into the remote host using SSH, RSH, RLOGIN, Telnet
or any local commands and extracting the installed package list. It SSH was used a valid public
key would be essential for performing the scan.
ICT287 COMPUTER SECURITY
The third vulnerability is that Microsoft Windows SMB service is detected and CIFS or
SMB protocols can be undertaken by the remote service for providing access to the files, printers
between the nodes connected in the network. The SMB service is running on port 139 and CIFS
is running on port 445.
The fourth vulnerability is that the name of the OS and installed package enumeration
where a plugin can be used for logging into the remote host using SSH, RSH, RLOGIN, Telnet
or any local commands and extracting the installed package list. It SSH was used a valid public
key would be essential for performing the scan.

8
ICT287 COMPUTER SECURITY
The fifth vulnerability is the server is that it does not have support for identifying
requests
Answer 2: Legacy Code
There are different software security issues present in a business organization and the threat
can be identified by performing a penetration testing and implementing the cyber defense
strategies. The software vulnerabilities include SQL injection, OS command injection, buffer
overflow, uncontrolled format string, etc (Johnson et al., 2016). The SQL injection can cause
injection of malicious codes in the SQL statement and insert malicious data in the database. The
database can be used for constructing SQL statement by concatenating the string and modify the
database (Younis, Malaiya & Ray, 2016). The OS command injection can cause vulnerabilities
and it can occur when the user manageable data is integrated in a command. Software security
vulnerability can be glitch, weakness or flaws in the software and it severity advances at an
exponential rate and it can be explained with the help of three factors such as:
Existence – Vulnerability exists in the software
Access – Possibility that the access can be gained by the hackers
ICT287 COMPUTER SECURITY
The fifth vulnerability is the server is that it does not have support for identifying
requests
Answer 2: Legacy Code
There are different software security issues present in a business organization and the threat
can be identified by performing a penetration testing and implementing the cyber defense
strategies. The software vulnerabilities include SQL injection, OS command injection, buffer
overflow, uncontrolled format string, etc (Johnson et al., 2016). The SQL injection can cause
injection of malicious codes in the SQL statement and insert malicious data in the database. The
database can be used for constructing SQL statement by concatenating the string and modify the
database (Younis, Malaiya & Ray, 2016). The OS command injection can cause vulnerabilities
and it can occur when the user manageable data is integrated in a command. Software security
vulnerability can be glitch, weakness or flaws in the software and it severity advances at an
exponential rate and it can be explained with the help of three factors such as:
Existence – Vulnerability exists in the software
Access – Possibility that the access can be gained by the hackers
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
ICT287 COMPUTER SECURITY
Exploit – capability of the hacker to gain advantage of the vulnerability using different
tools and techniques.
Vulnerability
The software vulnerability can affect different types of systems and may cause it to crash, while
some of the bugs can cause denial of service and not letting the person to log in or cause
malfunction in the system (Cadariu et al., 2015). It can also cause unauthroised privilege for
leaking information and buffer overflow for letting the attacker to gain full access of the system.
The security vulnerability in a software can risk of malware attacks and exploitation of the
software. The exploitation may also help in immediately infecting a system with malware and
gaining control of the system by a remote user.
In case of the organization Planet of the Grapes the software used for allowing the users to
make offline purchase by verifying the credit card data offline has several vulnerabilities. The
user can provide spoofed card for making the payment and if later on it is found that the card was
not valid or a customer charge back the amount with the issuer of the card denying about the
transaction carried out a huge loss is to be bearded by the company.
The algorithm of the program works by validating MOD 10 algorithm for example if the
number 38520000023237 is needed to be checked as a valid credit card number the last digit is
ICT287 COMPUTER SECURITY
Exploit – capability of the hacker to gain advantage of the vulnerability using different
tools and techniques.
Vulnerability
The software vulnerability can affect different types of systems and may cause it to crash, while
some of the bugs can cause denial of service and not letting the person to log in or cause
malfunction in the system (Cadariu et al., 2015). It can also cause unauthroised privilege for
leaking information and buffer overflow for letting the attacker to gain full access of the system.
The security vulnerability in a software can risk of malware attacks and exploitation of the
software. The exploitation may also help in immediately infecting a system with malware and
gaining control of the system by a remote user.
In case of the organization Planet of the Grapes the software used for allowing the users to
make offline purchase by verifying the credit card data offline has several vulnerabilities. The
user can provide spoofed card for making the payment and if later on it is found that the card was
not valid or a customer charge back the amount with the issuer of the card denying about the
transaction carried out a huge loss is to be bearded by the company.
The algorithm of the program works by validating MOD 10 algorithm for example if the
number 38520000023237 is needed to be checked as a valid credit card number the last digit is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
ICT287 COMPUTER SECURITY
taken and for the check digit. The rest of the sequence is also taken and each of the number is
doubled from the right hand side. The digits of the products are needed to be summed and all the
digits are added together. The result is multiplied by 9 and the last digit is matched with the
result for checking the validity of the sequence. Since the result matches with the 7 the program
returns it as a valid credit card number.
There is different fake credit card number generator that uses the reverse formula for
calculating a valid credit card number and can be used by the user for fraud and thus the tool can
be directly manipulated for exploitation.
Mitigation
Since it in not possible to patch the code directly and there is no update available from the
vendor it is needed to be used. The following are the three recommendations that are made for
reducing the risk of the application:
The training is needed to be given to the sales representatives and they should be
aware of risk of offline credit card processing.
It is needed to be make sure that the payment partner has 24/7 support for the
customer and a chargeback can be frustrating and the payment processor should be
well known and it can be put on hold when things happened.
For the offline card processing a limit in transaction should be enforced and
authorization should be used for exceeding the limit of transaction.
Since the internet connection is down the offline credit card processing can be used
but there is high risk associated with the use of offline payment processing software. A
merchant offering offline credit card and debit transaction is needed to be selected and
ICT287 COMPUTER SECURITY
taken and for the check digit. The rest of the sequence is also taken and each of the number is
doubled from the right hand side. The digits of the products are needed to be summed and all the
digits are added together. The result is multiplied by 9 and the last digit is matched with the
result for checking the validity of the sequence. Since the result matches with the 7 the program
returns it as a valid credit card number.
There is different fake credit card number generator that uses the reverse formula for
calculating a valid credit card number and can be used by the user for fraud and thus the tool can
be directly manipulated for exploitation.
Mitigation
Since it in not possible to patch the code directly and there is no update available from the
vendor it is needed to be used. The following are the three recommendations that are made for
reducing the risk of the application:
The training is needed to be given to the sales representatives and they should be
aware of risk of offline credit card processing.
It is needed to be make sure that the payment partner has 24/7 support for the
customer and a chargeback can be frustrating and the payment processor should be
well known and it can be put on hold when things happened.
For the offline card processing a limit in transaction should be enforced and
authorization should be used for exceeding the limit of transaction.
Since the internet connection is down the offline credit card processing can be used
but there is high risk associated with the use of offline payment processing software. A
merchant offering offline credit card and debit transaction is needed to be selected and

11
ICT287 COMPUTER SECURITY
this can add flexibility to transfer the risk. This helps in taking precaution of the risk and
apply best practice in the business for minimizing the potential loss.
Bibliography
Aupetit, M., Zhauniarovich, Y., Vasiliadis, G., Dacier, M., & Boshmaf, Y. (2016, October).
Visualization of actionable knowledge to mitigate DRDoS attacks. In 2016 IEEE
Symposium on Visualization for Cyber Security (VizSec) (pp. 1-8). IEEE.
Cadariu, M., Bouwers, E., Visser, J., & van Deursen, A. (2015, March). Tracking known security
vulnerabilities in proprietary software systems. In 2015 IEEE 22nd International
Conference on Software Analysis, Evolution, and Reengineering (SANER) (pp. 516-519).
IEEE.
Felderer, M., Zech, P., Breu, R., Büchler, M., & Pretschner, A. (2016). Model‐based security
testing: a taxonomy and systematic classification. Software Testing, Verification and
Reliability, 26(2), 119-148.
Ghaffarian, S. M., & Shahriari, H. R. (2017). Software vulnerability analysis and discovery using
machine-learning and data-mining techniques: A survey. ACM Computing Surveys
(CSUR), 50(4), 56.
Hoole, A. M., Traore, I., Delaitre, A., & de Oliveira, C. (2016, June). Improving vulnerability
detection measurement:[test suites and software security assurance]. In Proceedings of
the 20th International Conference on Evaluation and Assessment in Software
Engineering (p. 27). ACM.
ICT287 COMPUTER SECURITY
this can add flexibility to transfer the risk. This helps in taking precaution of the risk and
apply best practice in the business for minimizing the potential loss.
Bibliography
Aupetit, M., Zhauniarovich, Y., Vasiliadis, G., Dacier, M., & Boshmaf, Y. (2016, October).
Visualization of actionable knowledge to mitigate DRDoS attacks. In 2016 IEEE
Symposium on Visualization for Cyber Security (VizSec) (pp. 1-8). IEEE.
Cadariu, M., Bouwers, E., Visser, J., & van Deursen, A. (2015, March). Tracking known security
vulnerabilities in proprietary software systems. In 2015 IEEE 22nd International
Conference on Software Analysis, Evolution, and Reengineering (SANER) (pp. 516-519).
IEEE.
Felderer, M., Zech, P., Breu, R., Büchler, M., & Pretschner, A. (2016). Model‐based security
testing: a taxonomy and systematic classification. Software Testing, Verification and
Reliability, 26(2), 119-148.
Ghaffarian, S. M., & Shahriari, H. R. (2017). Software vulnerability analysis and discovery using
machine-learning and data-mining techniques: A survey. ACM Computing Surveys
(CSUR), 50(4), 56.
Hoole, A. M., Traore, I., Delaitre, A., & de Oliveira, C. (2016, June). Improving vulnerability
detection measurement:[test suites and software security assurance]. In Proceedings of
the 20th International Conference on Evaluation and Assessment in Software
Engineering (p. 27). ACM.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





