UMUC Network Solution White Paper
VerifiedAdded on 2019/10/18
|5
|1321
|43
Project
AI Summary
UMUC, a company with a rapidly growing business, faces a major problem with its telecommunications network, which is managed by an outside provider. The Chief Information Officer (CIO) has outlined key requirements for a new network that includes availability, reliability, scalability, security, flexibility, performance, and manageability. The CIO proposes designing and implementing a new network using advanced technologies to connect remote offices and users securely and facilitate company expansion. The goal is to create a 3-page white paper that defines the business problem, discusses it in the context of the scenario, recommends technology solutions, processes, and policies to solve the problem, and identifies potential risks and mitigation strategies.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

IFSM 370 Project 2: White Paper Instructions
Scenario
Ullman, Manly, & Ulysses Corporation
With 75,000 customers worldwide, 250 employees working in four locations in the
United States and three European offices, and a catalog of more than 100,000 parts,
Ullman, Manly & Ulysses Corporation (UMUC) relies on its network for its survival. In
the past decade, UMUC has seen its business grow from just one location and a few
local customers to the worldwide supplier it is today. But in the process of growing
exponentially, it has overwhelmed its telecommunications network, which is currently
managed by an outside telecommunications network management company. The
network crashes frequently, resulting in customer service and e-mail interruptions that
are costly to the company. The network management company is not responsive to
UMUC, a relatively small customer, and often disagrees that there is even a problem.
Since the contract with the service provider is about to expire, UMUC has decided to
seek a better network solution.
The Chief Information Officer (CIO) has outlined the key requirements for a new
network for UMUC. He has explained to the executive board that a new network would
have the following characteristics:
1. Availability: Business operations require maximum uptime, and quick repairs
when needed.
2. Reliability: The network must function as designed and produce accurate
results.
3. Scalability: UMUC continues to grow at a rapid rate, and there are plans for
acquisition of several small parts suppliers; the network must support this growth.
4. Security: The confidentiality and integrity of UMUC's data is of great importance,
as is the protection of its customers' data.
5. Flexibility: The new network must be responsive to the changing needs of the
business.
6. Performance: The network must provide quick access for employees and
customers.
7. Manageability: The network must be designed and implemented so that it can
be managed by a small team of centrally located IT specialists.
8. Economic efficiency: The ongoing operations and maintenance costs should
offset the initial investment costs, reducing the long-term total cost of ownership
of the network.
UMUC's executives have agreed that they need a business network with higher
reliability, security, and scalability, but with lower costs, than the existing externally
managed network. The CIO has proposed that UMUC design and implement its own
network, using advanced technologies for high availability, efficiency, and security
management, that can be operated by a very small IT department. He proposes to use
Page 1 of 5
Scenario
Ullman, Manly, & Ulysses Corporation
With 75,000 customers worldwide, 250 employees working in four locations in the
United States and three European offices, and a catalog of more than 100,000 parts,
Ullman, Manly & Ulysses Corporation (UMUC) relies on its network for its survival. In
the past decade, UMUC has seen its business grow from just one location and a few
local customers to the worldwide supplier it is today. But in the process of growing
exponentially, it has overwhelmed its telecommunications network, which is currently
managed by an outside telecommunications network management company. The
network crashes frequently, resulting in customer service and e-mail interruptions that
are costly to the company. The network management company is not responsive to
UMUC, a relatively small customer, and often disagrees that there is even a problem.
Since the contract with the service provider is about to expire, UMUC has decided to
seek a better network solution.
The Chief Information Officer (CIO) has outlined the key requirements for a new
network for UMUC. He has explained to the executive board that a new network would
have the following characteristics:
1. Availability: Business operations require maximum uptime, and quick repairs
when needed.
2. Reliability: The network must function as designed and produce accurate
results.
3. Scalability: UMUC continues to grow at a rapid rate, and there are plans for
acquisition of several small parts suppliers; the network must support this growth.
4. Security: The confidentiality and integrity of UMUC's data is of great importance,
as is the protection of its customers' data.
5. Flexibility: The new network must be responsive to the changing needs of the
business.
6. Performance: The network must provide quick access for employees and
customers.
7. Manageability: The network must be designed and implemented so that it can
be managed by a small team of centrally located IT specialists.
8. Economic efficiency: The ongoing operations and maintenance costs should
offset the initial investment costs, reducing the long-term total cost of ownership
of the network.
UMUC's executives have agreed that they need a business network with higher
reliability, security, and scalability, but with lower costs, than the existing externally
managed network. The CIO has proposed that UMUC design and implement its own
network, using advanced technologies for high availability, efficiency, and security
management, that can be operated by a very small IT department. He proposes to use
Page 1 of 5
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

IFSM 370 Project 2: White Paper Instructions
virtual private network technologies to connect remote offices and users securely and to
facilitate company expansion.
The Deliverable
The CIO has asked you to develop a 3-page white paper that provides the following:
definition of the business or technical problem
discussion of the problem within the context of the scenario
recommendation of the application of technology, processes, and policies that
solve the problem
discussion of the impact or risks of the applied solution within the context of
business strategy and managerial perspective
identification, analysis, and mitigation of risks of the recommended solution
Briefly define the business problem, and discuss it in the context of the scenario. Briefly
describe the proposed technology solution, processes, and policies to solve the
problem. You should demonstrate your critical thinking as you incorporate the course
concepts and explain the business needs and solutions. Then discuss the impact or
risks of the applied solution within the context of the business strategy and managerial
perspective. Then discuss the challenges and security risks that result from
implementing the proposed solution. Propose mitigation strategies for the challenges
and risks identified. The bolded attributes in the Scoring Rubric (see below) must be
used as the section headings in the white paper.
Your deliverable will be a white paper three pages in length, not counting the cover
page and references page. At least two (2) external sources (other than the assigned
readings and other course materials) must be used, and citations and references must
be in APA format. Your paper will be scored according to the Scoring Rubric below. Be
sure you have incorporated all required aspects of the assignment.
Page 2 of 5
virtual private network technologies to connect remote offices and users securely and to
facilitate company expansion.
The Deliverable
The CIO has asked you to develop a 3-page white paper that provides the following:
definition of the business or technical problem
discussion of the problem within the context of the scenario
recommendation of the application of technology, processes, and policies that
solve the problem
discussion of the impact or risks of the applied solution within the context of
business strategy and managerial perspective
identification, analysis, and mitigation of risks of the recommended solution
Briefly define the business problem, and discuss it in the context of the scenario. Briefly
describe the proposed technology solution, processes, and policies to solve the
problem. You should demonstrate your critical thinking as you incorporate the course
concepts and explain the business needs and solutions. Then discuss the impact or
risks of the applied solution within the context of the business strategy and managerial
perspective. Then discuss the challenges and security risks that result from
implementing the proposed solution. Propose mitigation strategies for the challenges
and risks identified. The bolded attributes in the Scoring Rubric (see below) must be
used as the section headings in the white paper.
Your deliverable will be a white paper three pages in length, not counting the cover
page and references page. At least two (2) external sources (other than the assigned
readings and other course materials) must be used, and citations and references must
be in APA format. Your paper will be scored according to the Scoring Rubric below. Be
sure you have incorporated all required aspects of the assignment.
Page 2 of 5
IFSM 370 Project 2: White Paper Instructions
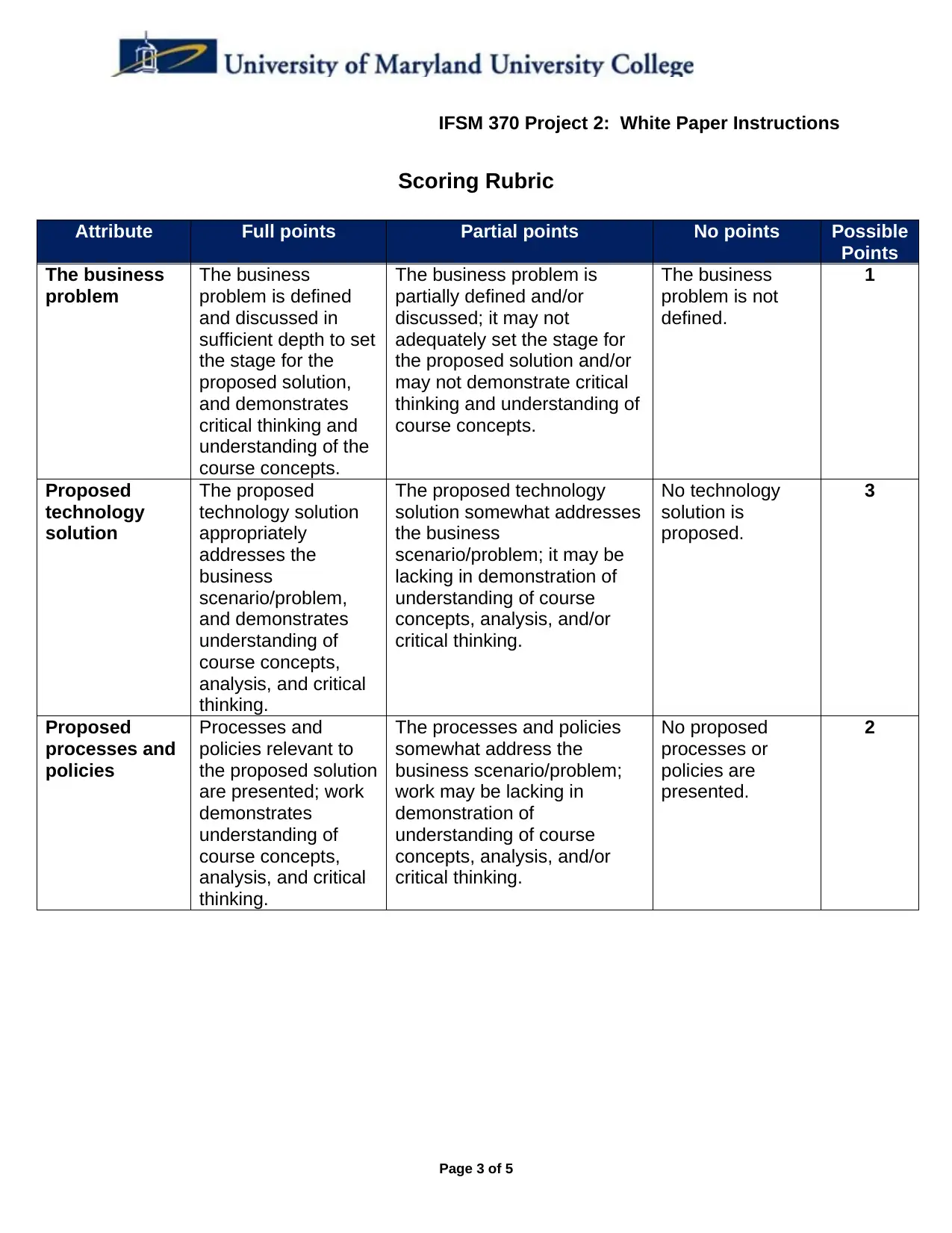
Scoring Rubric
Attribute Full points Partial points No points Possible
Points
The business
problem
The business
problem is defined
and discussed in
sufficient depth to set
the stage for the
proposed solution,
and demonstrates
critical thinking and
understanding of the
course concepts.
The business problem is
partially defined and/or
discussed; it may not
adequately set the stage for
the proposed solution and/or
may not demonstrate critical
thinking and understanding of
course concepts.
The business
problem is not
defined.
1
Proposed
technology
solution
The proposed
technology solution
appropriately
addresses the
business
scenario/problem,
and demonstrates
understanding of
course concepts,
analysis, and critical
thinking.
The proposed technology
solution somewhat addresses
the business
scenario/problem; it may be
lacking in demonstration of
understanding of course
concepts, analysis, and/or
critical thinking.
No technology
solution is
proposed.
3
Proposed
processes and
policies
Processes and
policies relevant to
the proposed solution
are presented; work
demonstrates
understanding of
course concepts,
analysis, and critical
thinking.
The processes and policies
somewhat address the
business scenario/problem;
work may be lacking in
demonstration of
understanding of course
concepts, analysis, and/or
critical thinking.
No proposed
processes or
policies are
presented.
2
Page 3 of 5
Scoring Rubric
Attribute Full points Partial points No points Possible
Points
The business
problem
The business
problem is defined
and discussed in
sufficient depth to set
the stage for the
proposed solution,
and demonstrates
critical thinking and
understanding of the
course concepts.
The business problem is
partially defined and/or
discussed; it may not
adequately set the stage for
the proposed solution and/or
may not demonstrate critical
thinking and understanding of
course concepts.
The business
problem is not
defined.
1
Proposed
technology
solution
The proposed
technology solution
appropriately
addresses the
business
scenario/problem,
and demonstrates
understanding of
course concepts,
analysis, and critical
thinking.
The proposed technology
solution somewhat addresses
the business
scenario/problem; it may be
lacking in demonstration of
understanding of course
concepts, analysis, and/or
critical thinking.
No technology
solution is
proposed.
3
Proposed
processes and
policies
Processes and
policies relevant to
the proposed solution
are presented; work
demonstrates
understanding of
course concepts,
analysis, and critical
thinking.
The processes and policies
somewhat address the
business scenario/problem;
work may be lacking in
demonstration of
understanding of course
concepts, analysis, and/or
critical thinking.
No proposed
processes or
policies are
presented.
2
Page 3 of 5
IFSM 370 Project 2: White Paper Instructions
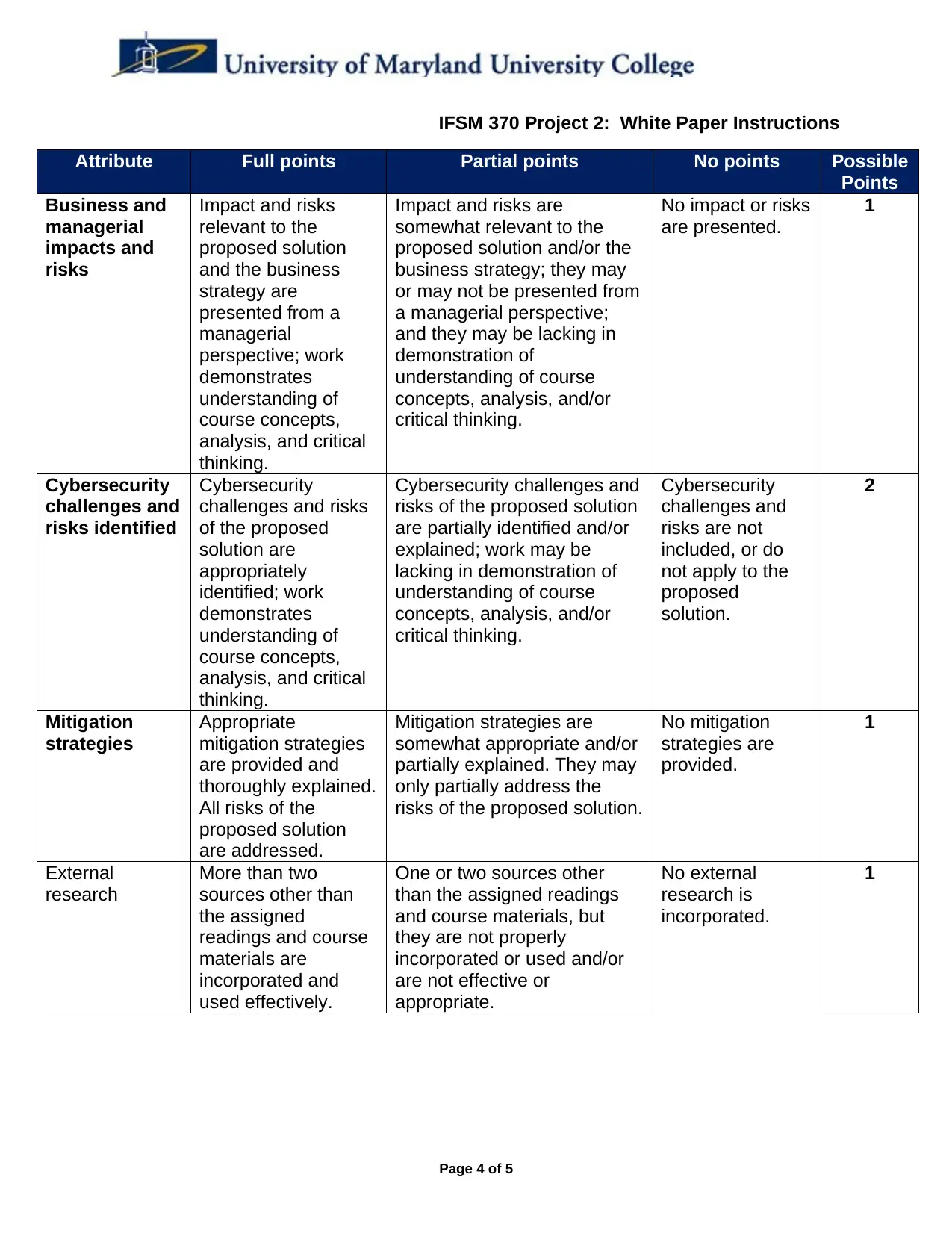
Attribute Full points Partial points No points Possible
Points
Business and
managerial
impacts and
risks
Impact and risks
relevant to the
proposed solution
and the business
strategy are
presented from a
managerial
perspective; work
demonstrates
understanding of
course concepts,
analysis, and critical
thinking.
Impact and risks are
somewhat relevant to the
proposed solution and/or the
business strategy; they may
or may not be presented from
a managerial perspective;
and they may be lacking in
demonstration of
understanding of course
concepts, analysis, and/or
critical thinking.
No impact or risks
are presented.
1
Cybersecurity
challenges and
risks identified
Cybersecurity
challenges and risks
of the proposed
solution are
appropriately
identified; work
demonstrates
understanding of
course concepts,
analysis, and critical
thinking.
Cybersecurity challenges and
risks of the proposed solution
are partially identified and/or
explained; work may be
lacking in demonstration of
understanding of course
concepts, analysis, and/or
critical thinking.
Cybersecurity
challenges and
risks are not
included, or do
not apply to the
proposed
solution.
2
Mitigation
strategies
Appropriate
mitigation strategies
are provided and
thoroughly explained.
All risks of the
proposed solution
are addressed.
Mitigation strategies are
somewhat appropriate and/or
partially explained. They may
only partially address the
risks of the proposed solution.
No mitigation
strategies are
provided.
1
External
research
More than two
sources other than
the assigned
readings and course
materials are
incorporated and
used effectively.
One or two sources other
than the assigned readings
and course materials, but
they are not properly
incorporated or used and/or
are not effective or
appropriate.
No external
research is
incorporated.
1
Page 4 of 5
Attribute Full points Partial points No points Possible
Points
Business and
managerial
impacts and
risks
Impact and risks
relevant to the
proposed solution
and the business
strategy are
presented from a
managerial
perspective; work
demonstrates
understanding of
course concepts,
analysis, and critical
thinking.
Impact and risks are
somewhat relevant to the
proposed solution and/or the
business strategy; they may
or may not be presented from
a managerial perspective;
and they may be lacking in
demonstration of
understanding of course
concepts, analysis, and/or
critical thinking.
No impact or risks
are presented.
1
Cybersecurity
challenges and
risks identified
Cybersecurity
challenges and risks
of the proposed
solution are
appropriately
identified; work
demonstrates
understanding of
course concepts,
analysis, and critical
thinking.
Cybersecurity challenges and
risks of the proposed solution
are partially identified and/or
explained; work may be
lacking in demonstration of
understanding of course
concepts, analysis, and/or
critical thinking.
Cybersecurity
challenges and
risks are not
included, or do
not apply to the
proposed
solution.
2
Mitigation
strategies
Appropriate
mitigation strategies
are provided and
thoroughly explained.
All risks of the
proposed solution
are addressed.
Mitigation strategies are
somewhat appropriate and/or
partially explained. They may
only partially address the
risks of the proposed solution.
No mitigation
strategies are
provided.
1
External
research
More than two
sources other than
the assigned
readings and course
materials are
incorporated and
used effectively.
One or two sources other
than the assigned readings
and course materials, but
they are not properly
incorporated or used and/or
are not effective or
appropriate.
No external
research is
incorporated.
1
Page 4 of 5
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
IFSM 370 Project 2: White Paper Instructions
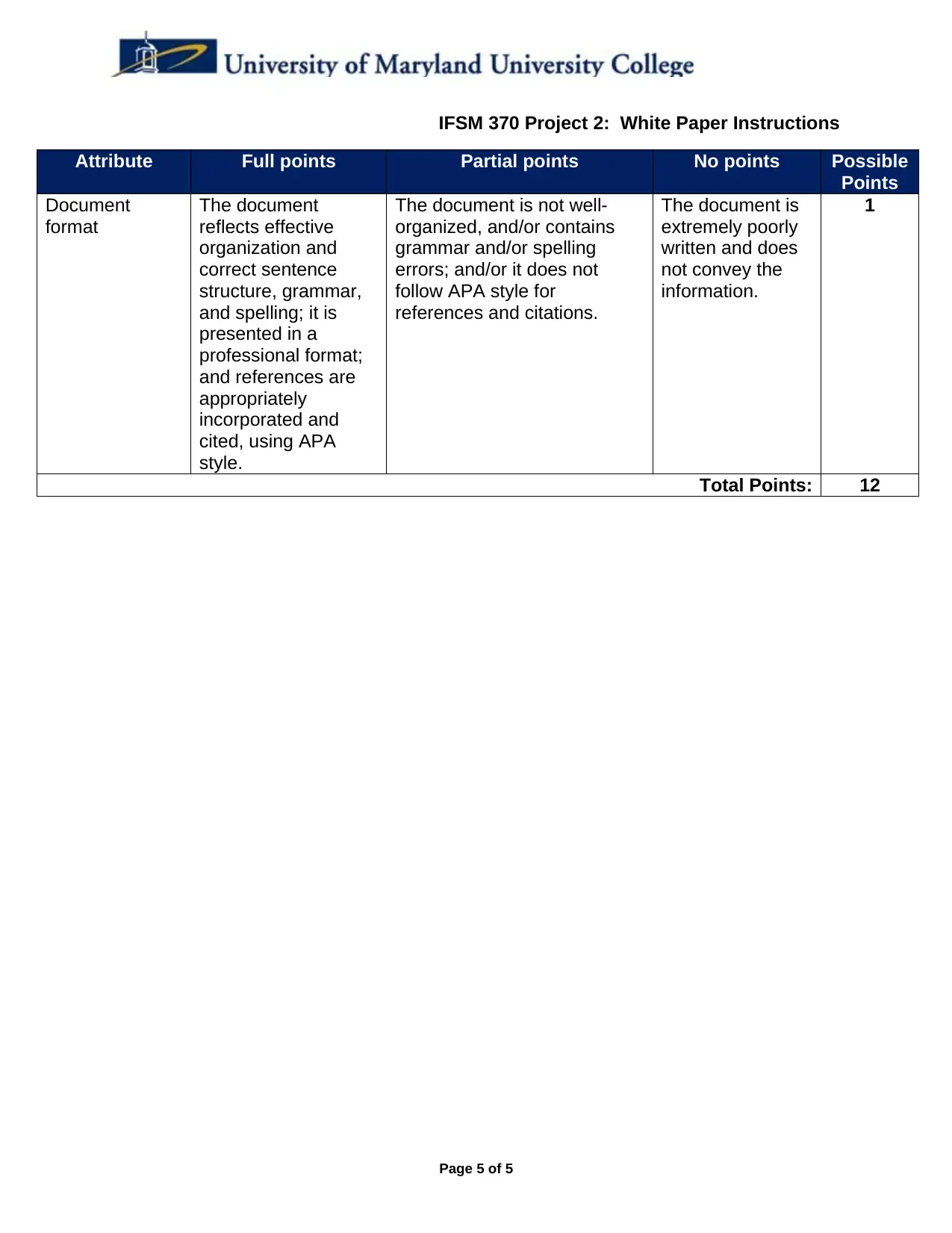
Attribute Full points Partial points No points Possible
Points
Document
format
The document
reflects effective
organization and
correct sentence
structure, grammar,
and spelling; it is
presented in a
professional format;
and references are
appropriately
incorporated and
cited, using APA
style.
The document is not well-
organized, and/or contains
grammar and/or spelling
errors; and/or it does not
follow APA style for
references and citations.
The document is
extremely poorly
written and does
not convey the
information.
1
Total Points: 12
Page 5 of 5
Attribute Full points Partial points No points Possible
Points
Document
format
The document
reflects effective
organization and
correct sentence
structure, grammar,
and spelling; it is
presented in a
professional format;
and references are
appropriately
incorporated and
cited, using APA
style.
The document is not well-
organized, and/or contains
grammar and/or spelling
errors; and/or it does not
follow APA style for
references and citations.
The document is
extremely poorly
written and does
not convey the
information.
1
Total Points: 12
Page 5 of 5
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





