Implementation of Secure Encryption Technologies
VerifiedAdded on 2023/01/13
|11
|2460
|38
AI Summary
This article discusses the implementation of secure encryption technologies for data security in the Royal Children Hospital (RCH). It analyzes the requirements of data security, proposes a new security plan, and explores five encryption technologies for RCH. The cost associated with two encryption technologies, LastPass and BitLocker, is also discussed. The article concludes with the impact of encryption technologies on daily duties in hospitals.
Contribute Materials
Your contribution can guide someone’s learning journey. Share your
documents today.

Running head: IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Implementation of Secure Encryption Technologies
Name of the Student
Name of the University
Author Note:
Implementation of Secure Encryption Technologies
Name of the Student
Name of the University
Author Note:
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

1IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
Analysis of requirement of Royal Children Hospital (RCH) Data Security...............................2
New Security Plan for RCH........................................................................................................3
Five Encryption Technologies for RCH and choice of Two best one.........................................4
Cost associated with two Encryption Technologies and implementation in RCH......................5
Method to application of the chosen Encryption Technologies in RCH.....................................7
Consequence of Chosen encryption technologies.......................................................................7
New Encryption Technologies and its effect on daily duties in hospitals...................................8
Conclusion.......................................................................................................................................8
Bibliography....................................................................................................................................9
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................2
Analysis of requirement of Royal Children Hospital (RCH) Data Security...............................2
New Security Plan for RCH........................................................................................................3
Five Encryption Technologies for RCH and choice of Two best one.........................................4
Cost associated with two Encryption Technologies and implementation in RCH......................5
Method to application of the chosen Encryption Technologies in RCH.....................................7
Consequence of Chosen encryption technologies.......................................................................7
New Encryption Technologies and its effect on daily duties in hospitals...................................8
Conclusion.......................................................................................................................................8
Bibliography....................................................................................................................................9

2IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Introduction
In the year 1870, the Royal Children Hospital (RCH) was established at Parkville in
Melbourne. In between the year 2010-2011, RCH has provided treatment to around 33,560 in
patients1. Around 210,956 outpatient clinic appointments and 10,741 have gone for surgery. In
the emergency department, RCH comes up with 70,036 children with approximate around 200
children. Being a healthcare provider, children hospital aims to understand the trust which is not
based on dedication2. It aims to produce best kind of medical attention for children care and
dedication for ensuring the records of the patient. Apart from this, RCH has another kind of
sensitive data of medical information which is protected in most of the cases.
In the coming pages of the report, an idea has been provided with respect to requirements
of data security at RCH. The current problem in RCH along with security plan for tackling it.
After that, an idea has been provided with respect to various encryption technologies.
Discussion
Analysis of requirement of Royal Children Hospital (RCH) Data Security
Royal children Hospital (RCH) focuses on dedication to ensuring the patient records
along with sensitive information is incomplete protection3. With increase in the number of
medical staff that travels beyond the extent of main campus along with emergency location.
RCH aims to be very much certain that it can protect all the required data that is stored in their
laptops.
1 Kaplan, David, Jeremy Powell, and Tom Woller. "AMD memory encryption." White paper (2016).
2 Liang, Kaitai, Man Ho Au, Joseph K. Liu, Willy Susilo, Duncan S. Wong, Guomin Yang, Yong Yu, and Anjia
Yang. "A secure and efficient ciphertext-policy attribute-based proxy re-encryption for cloud data sharing." Future
Generation Computer Systems 52 (2015): 95-108.
3 Batalla, Jordi Mongay, Athanasios Vasilakos, and Mariusz Gajewski. "Secure smart homes: Opportunities and
challenges." ACM Computing Surveys (CSUR) 50, no. 5 (2017): 75.
Introduction
In the year 1870, the Royal Children Hospital (RCH) was established at Parkville in
Melbourne. In between the year 2010-2011, RCH has provided treatment to around 33,560 in
patients1. Around 210,956 outpatient clinic appointments and 10,741 have gone for surgery. In
the emergency department, RCH comes up with 70,036 children with approximate around 200
children. Being a healthcare provider, children hospital aims to understand the trust which is not
based on dedication2. It aims to produce best kind of medical attention for children care and
dedication for ensuring the records of the patient. Apart from this, RCH has another kind of
sensitive data of medical information which is protected in most of the cases.
In the coming pages of the report, an idea has been provided with respect to requirements
of data security at RCH. The current problem in RCH along with security plan for tackling it.
After that, an idea has been provided with respect to various encryption technologies.
Discussion
Analysis of requirement of Royal Children Hospital (RCH) Data Security
Royal children Hospital (RCH) focuses on dedication to ensuring the patient records
along with sensitive information is incomplete protection3. With increase in the number of
medical staff that travels beyond the extent of main campus along with emergency location.
RCH aims to be very much certain that it can protect all the required data that is stored in their
laptops.
1 Kaplan, David, Jeremy Powell, and Tom Woller. "AMD memory encryption." White paper (2016).
2 Liang, Kaitai, Man Ho Au, Joseph K. Liu, Willy Susilo, Duncan S. Wong, Guomin Yang, Yong Yu, and Anjia
Yang. "A secure and efficient ciphertext-policy attribute-based proxy re-encryption for cloud data sharing." Future
Generation Computer Systems 52 (2015): 95-108.
3 Batalla, Jordi Mongay, Athanasios Vasilakos, and Mariusz Gajewski. "Secure smart homes: Opportunities and
challenges." ACM Computing Surveys (CSUR) 50, no. 5 (2017): 75.

3IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Doctors and Nurses at RCH aim to travel in Melbourne City on regular interval. The
hospital needs to assured about the data of patient that is collected on laptops is completely
secured. On regular basis, RCH doctors and nurses need to travel to Melbourne City on everyday
interval4. RCH needs to assured about the fact that the stored patient data is completely secured
with them. Laptops of Doctors and patient need to carry sensitive information and so they ensure
that lost or stolen data does not provide any kind of unauthorized access to important data.
New Security Plan for RCH
All the current issue in RCH can be easily tackled with the help of proper security plan in
RCH (Royal Children Hospital). The security plans in RCH compromises of four steps that are
Run Risk Assessment: Prior to development of effective security plan, an initial
assessment of risk is done. It is needed for analyzing the assets, system and associated devices of
doctor and nurse that require protection.
Building a Security Culture: At present, security plan and checklist are not enough for
developing a strong posture of security5. Protecting the vital data of the patient should be very
first aspect of healthcare organization.
Reviewing of IT Policies and Procedure: Analysing the security trends and overall
threats can be considered to be very much difficult. Policies should be there for proper protection
of data along with proper control measures of patient information.
Educating employees about security best practices: System hackers mainly look up for
weakest link in the overall security plan and their employees. Hackers can prey on hospital by
sending phishing emails.
4
Pancholi, Vishal R., and Bhadresh P. Patel. "Enhancement of cloud computing security with secure data storage
using AES." International Journal for Innovative Research in Science and Technology 2, no. 9 (2016): 18-21.
5 Rachmawanto, Eko Hari, and Christy Atika Sari. "Secure Image Steganography Algorithm Based on DCT with
OTP Encryption." Journal of Applied Intelligent System 2, no. 1 (2017): 1-11.
Doctors and Nurses at RCH aim to travel in Melbourne City on regular interval. The
hospital needs to assured about the data of patient that is collected on laptops is completely
secured. On regular basis, RCH doctors and nurses need to travel to Melbourne City on everyday
interval4. RCH needs to assured about the fact that the stored patient data is completely secured
with them. Laptops of Doctors and patient need to carry sensitive information and so they ensure
that lost or stolen data does not provide any kind of unauthorized access to important data.
New Security Plan for RCH
All the current issue in RCH can be easily tackled with the help of proper security plan in
RCH (Royal Children Hospital). The security plans in RCH compromises of four steps that are
Run Risk Assessment: Prior to development of effective security plan, an initial
assessment of risk is done. It is needed for analyzing the assets, system and associated devices of
doctor and nurse that require protection.
Building a Security Culture: At present, security plan and checklist are not enough for
developing a strong posture of security5. Protecting the vital data of the patient should be very
first aspect of healthcare organization.
Reviewing of IT Policies and Procedure: Analysing the security trends and overall
threats can be considered to be very much difficult. Policies should be there for proper protection
of data along with proper control measures of patient information.
Educating employees about security best practices: System hackers mainly look up for
weakest link in the overall security plan and their employees. Hackers can prey on hospital by
sending phishing emails.
4
Pancholi, Vishal R., and Bhadresh P. Patel. "Enhancement of cloud computing security with secure data storage
using AES." International Journal for Innovative Research in Science and Technology 2, no. 9 (2016): 18-21.
5 Rachmawanto, Eko Hari, and Christy Atika Sari. "Secure Image Steganography Algorithm Based on DCT with
OTP Encryption." Journal of Applied Intelligent System 2, no. 1 (2017): 1-11.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

4IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Five Encryption Technologies for RCH and choice of Two best one
Data encryption is all about translating data in the form of code to some specific people
can have access to secret key6. At present, encryption is known to be most popular and best
security method used by organization.
LastPass: It is known to be both password manager and generator and is mainly
recommended for securing the password and data which is personal. By the help of free
encryption software like this, staff of RCH does not need to remember the password.
Bit locker: At present, there is large number of encryption tool available for user that can
encrypt the data on local platform. The most suitable way of encrypting sensitive information by
making use of BitLocker software.
Vera Crypt: It is free encryption software which is available for use in Windows and
Linux operating system. It also supports the advanced encryption standard and encrypted volume
of data.
Disk Cryptor: It is another kind of windows based free encryption which is needed for
encrypting both external and internal data7. The software tools aim to provide various kind of
encryption like AES, Twofish. The file encryption software can be used for alternative to
TrueCrypt tool.
6 Gahi, Youssef, Mouhcine Guennoun, and Khalil El-Khatib. "A secure database system using homomorphic
encryption schemes." arXiv preprint arXiv:1512.03498 (2015).
7 He, Kun, Christophe Bidan, Gaëetan Le Guelvouit, and Cyrielle Feron. "Robust and secure image encryption
schemes during jpeg compression process." Electronic Imaging 2016, no. 11 (2016): 1-7.
Five Encryption Technologies for RCH and choice of Two best one
Data encryption is all about translating data in the form of code to some specific people
can have access to secret key6. At present, encryption is known to be most popular and best
security method used by organization.
LastPass: It is known to be both password manager and generator and is mainly
recommended for securing the password and data which is personal. By the help of free
encryption software like this, staff of RCH does not need to remember the password.
Bit locker: At present, there is large number of encryption tool available for user that can
encrypt the data on local platform. The most suitable way of encrypting sensitive information by
making use of BitLocker software.
Vera Crypt: It is free encryption software which is available for use in Windows and
Linux operating system. It also supports the advanced encryption standard and encrypted volume
of data.
Disk Cryptor: It is another kind of windows based free encryption which is needed for
encrypting both external and internal data7. The software tools aim to provide various kind of
encryption like AES, Twofish. The file encryption software can be used for alternative to
TrueCrypt tool.
6 Gahi, Youssef, Mouhcine Guennoun, and Khalil El-Khatib. "A secure database system using homomorphic
encryption schemes." arXiv preprint arXiv:1512.03498 (2015).
7 He, Kun, Christophe Bidan, Gaëetan Le Guelvouit, and Cyrielle Feron. "Robust and secure image encryption
schemes during jpeg compression process." Electronic Imaging 2016, no. 11 (2016): 1-7.

5IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
7-Zip: It is a free encryption software which is open source in nature. It is known to be
powerful and lightweight solution known for simplicity8. The tool comes up with ability to
extract archives by making use of AES-256 encryption.
RCH can go for two best encryption technique that is LastPass and Bit Locker.
LastPass tool aims to encourage unique set of password and even discourage the user to
use it. If doctors and nurses at RCH make use of same password for multiple accounts, then it is
recommended for setting up different password.
BitLocker can provide huge number of benefits to doctor and nurses at RCH like
Very much easy to use as it is already integrated into the Windows OS
It is a free data encryption software which helps in prevention of any kind of data
breaches.
It can easily encrypt the drive which can make the malicious actor steal the laptop or
remove hard drive and lastly read the files.
Cost associated with two Encryption Technologies and implementation in
RCH
LastPass comes up with free 30 days’ trial for use to its user. The premium is billed for
36 dollars for its user9. While the families come up with protecting data of 6 users. The annual
cost of the encryption of 48 dollars.
8
Lin, Zhuosheng, Simin Yu, Jinhu Lü, Shuting Cai, and Guanrong Chen. "Design and ARM-embedded
implementation of a chaotic map-based real-time secure video communication system." IEEE Transactions on
Circuits and Systems for Video Technology 25, no. 7 (2015): 1203-1216.
9 Du, Zhao-Hui, Zhiwei Ying, Zhenke Ma, Yufei Mai, Phoebe Wang, Jesse Liu, and Jesse Fang. "Secure encrypted
virtualization is unsecure." arXiv preprint arXiv:1712.05090 (2017).
7-Zip: It is a free encryption software which is open source in nature. It is known to be
powerful and lightweight solution known for simplicity8. The tool comes up with ability to
extract archives by making use of AES-256 encryption.
RCH can go for two best encryption technique that is LastPass and Bit Locker.
LastPass tool aims to encourage unique set of password and even discourage the user to
use it. If doctors and nurses at RCH make use of same password for multiple accounts, then it is
recommended for setting up different password.
BitLocker can provide huge number of benefits to doctor and nurses at RCH like
Very much easy to use as it is already integrated into the Windows OS
It is a free data encryption software which helps in prevention of any kind of data
breaches.
It can easily encrypt the drive which can make the malicious actor steal the laptop or
remove hard drive and lastly read the files.
Cost associated with two Encryption Technologies and implementation in
RCH
LastPass comes up with free 30 days’ trial for use to its user. The premium is billed for
36 dollars for its user9. While the families come up with protecting data of 6 users. The annual
cost of the encryption of 48 dollars.
8
Lin, Zhuosheng, Simin Yu, Jinhu Lü, Shuting Cai, and Guanrong Chen. "Design and ARM-embedded
implementation of a chaotic map-based real-time secure video communication system." IEEE Transactions on
Circuits and Systems for Video Technology 25, no. 7 (2015): 1203-1216.
9 Du, Zhao-Hui, Zhiwei Ying, Zhenke Ma, Yufei Mai, Phoebe Wang, Jesse Liu, and Jesse Fang. "Secure encrypted
virtualization is unsecure." arXiv preprint arXiv:1712.05090 (2017).
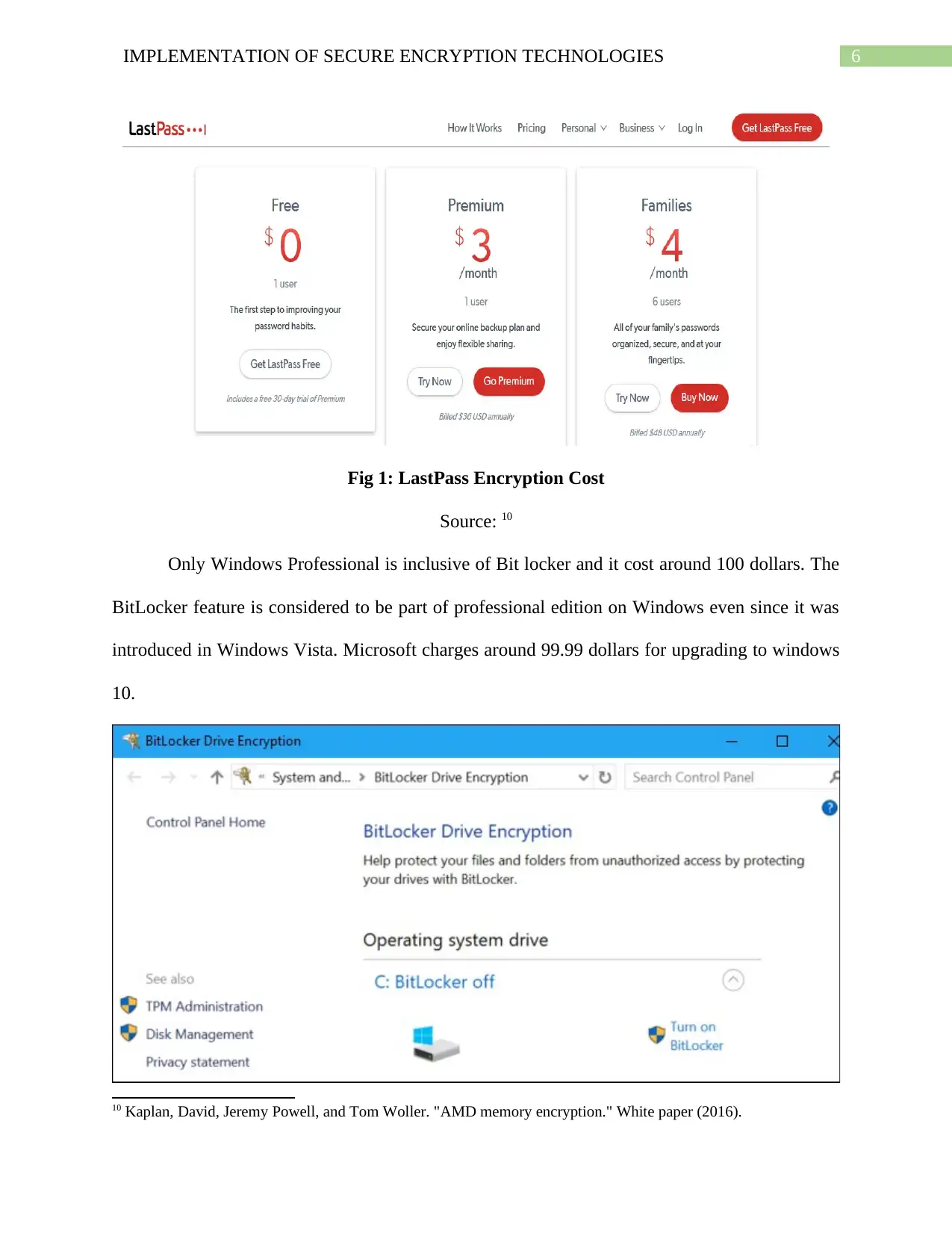
6IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Fig 1: LastPass Encryption Cost
Source: 10
Only Windows Professional is inclusive of Bit locker and it cost around 100 dollars. The
BitLocker feature is considered to be part of professional edition on Windows even since it was
introduced in Windows Vista. Microsoft charges around 99.99 dollars for upgrading to windows
10.
10 Kaplan, David, Jeremy Powell, and Tom Woller. "AMD memory encryption." White paper (2016).
Fig 1: LastPass Encryption Cost
Source: 10
Only Windows Professional is inclusive of Bit locker and it cost around 100 dollars. The
BitLocker feature is considered to be part of professional edition on Windows even since it was
introduced in Windows Vista. Microsoft charges around 99.99 dollars for upgrading to windows
10.
10 Kaplan, David, Jeremy Powell, and Tom Woller. "AMD memory encryption." White paper (2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Fig 2: BitLocker data encryption
Source: 11
Method to application of the chosen Encryption Technologies in RCH
LastPass is very much is easy to use and can easily simplify a large number of things. It
comes up with main extension in the browser like Google chrome and firefox. Doctors and
Nurses just need to create account as it offers the option to save the credential12. The particular
tools aim to encourage a unique and hard method to break password and discourage the user to
reuse it.
Consequence of Chosen encryption technologies
There are mainly two consequences of LastPass data encryption tool like
LastPass is a free data encryption tool which is needed for preventing any kind of data
breaches and exfiltration on the hard disk.
This software will encrypt the data which makes it impossible for attackers to steal the
data and read the files.
New Encryption Technologies and its effect on daily duties in hospitals
Data protection solution for data encryption can easily provide encryption of various
devices, mail and lastly data itself. Encryption function aims to meet with overall capabilities for
devices and data13. Doctors and Nurses can provide security for data at all times. The encrypted
data will maintain overall integrity.
11 Liang, Kaitai, Man Ho Au, Joseph K. Liu, Willy Susilo, Duncan S. Wong, Guomin Yang, Yong Yu, and Anjia
Yang. "A secure and efficient ciphertext-policy attribute-based proxy re-encryption for cloud data sharing." Future
Generation Computer Systems 52 (2015): 95-108.
12 Batalla, Jordi Mongay, Athanasios Vasilakos, and Mariusz Gajewski. "Secure smart homes: Opportunities and
challenges." ACM Computing Surveys (CSUR) 50, no. 5 (2017): 75.
13
Pancholi, Vishal R., and Bhadresh P. Patel. "Enhancement of cloud computing security with secure data storage
using AES." International Journal for Innovative Research in Science and Technology 2, no. 9 (2016): 18-21.
Fig 2: BitLocker data encryption
Source: 11
Method to application of the chosen Encryption Technologies in RCH
LastPass is very much is easy to use and can easily simplify a large number of things. It
comes up with main extension in the browser like Google chrome and firefox. Doctors and
Nurses just need to create account as it offers the option to save the credential12. The particular
tools aim to encourage a unique and hard method to break password and discourage the user to
reuse it.
Consequence of Chosen encryption technologies
There are mainly two consequences of LastPass data encryption tool like
LastPass is a free data encryption tool which is needed for preventing any kind of data
breaches and exfiltration on the hard disk.
This software will encrypt the data which makes it impossible for attackers to steal the
data and read the files.
New Encryption Technologies and its effect on daily duties in hospitals
Data protection solution for data encryption can easily provide encryption of various
devices, mail and lastly data itself. Encryption function aims to meet with overall capabilities for
devices and data13. Doctors and Nurses can provide security for data at all times. The encrypted
data will maintain overall integrity.
11 Liang, Kaitai, Man Ho Au, Joseph K. Liu, Willy Susilo, Duncan S. Wong, Guomin Yang, Yong Yu, and Anjia
Yang. "A secure and efficient ciphertext-policy attribute-based proxy re-encryption for cloud data sharing." Future
Generation Computer Systems 52 (2015): 95-108.
12 Batalla, Jordi Mongay, Athanasios Vasilakos, and Mariusz Gajewski. "Secure smart homes: Opportunities and
challenges." ACM Computing Surveys (CSUR) 50, no. 5 (2017): 75.
13
Pancholi, Vishal R., and Bhadresh P. Patel. "Enhancement of cloud computing security with secure data storage
using AES." International Journal for Innovative Research in Science and Technology 2, no. 9 (2016): 18-21.

8IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Conclusion
The above pages help in concluding the fact that the report is all about RCH (Royal
Children Hospital) that was established in the year 1870. With increase in the number of staff
members at RCH there is a need for protection of data on their laptops. Doctors and Nurses at
RCH need to travel to Melbourne city on everyday basis. RCH is very much focused on
protecting the data which is stored in the laptops. In the above pages, five encryption software
has been discussed in details.
Conclusion
The above pages help in concluding the fact that the report is all about RCH (Royal
Children Hospital) that was established in the year 1870. With increase in the number of staff
members at RCH there is a need for protection of data on their laptops. Doctors and Nurses at
RCH need to travel to Melbourne city on everyday basis. RCH is very much focused on
protecting the data which is stored in the laptops. In the above pages, five encryption software
has been discussed in details.

9IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Bibliography
Batalla, Jordi Mongay, Athanasios Vasilakos, and Mariusz Gajewski. "Secure smart homes:
Opportunities and challenges." ACM Computing Surveys (CSUR) 50, no. 5 (2017): 75.
Du, Zhao-Hui, Zhiwei Ying, Zhenke Ma, Yufei Mai, Phoebe Wang, Jesse Liu, and Jesse Fang.
"Secure encrypted virtualization is unsecure." arXiv preprint arXiv:1712.05090 (2017).
Gahi, Youssef, Mouhcine Guennoun, and Khalil El-Khatib. "A secure database system using
homomorphic encryption schemes." arXiv preprint arXiv:1512.03498 (2015).
He, Kun, Christophe Bidan, Gaëetan Le Guelvouit, and Cyrielle Feron. "Robust and secure
image encryption schemes during jpeg compression process." Electronic Imaging 2016, no. 11
(2016): 1-7.
Kaplan, David, Jeremy Powell, and Tom Woller. "AMD memory encryption." White paper
(2016).
Liang, Kaitai, Man Ho Au, Joseph K. Liu, Willy Susilo, Duncan S. Wong, Guomin Yang, Yong
Yu, and Anjia Yang. "A secure and efficient ciphertext-policy attribute-based proxy re-
encryption for cloud data sharing." Future Generation Computer Systems 52 (2015): 95-108.
Lin, Zhuosheng, Simin Yu, Jinhu Lü, Shuting Cai, and Guanrong Chen. "Design and ARM-
embedded implementation of a chaotic map-based real-time secure video communication
system." IEEE Transactions on Circuits and Systems for Video Technology 25, no. 7 (2015):
1203-1216.
Pancholi, Vishal R., and Bhadresh P. Patel. "Enhancement of cloud computing security with
secure data storage using AES." International Journal for Innovative Research in Science and
Technology 2, no. 9 (2016): 18-21.
Bibliography
Batalla, Jordi Mongay, Athanasios Vasilakos, and Mariusz Gajewski. "Secure smart homes:
Opportunities and challenges." ACM Computing Surveys (CSUR) 50, no. 5 (2017): 75.
Du, Zhao-Hui, Zhiwei Ying, Zhenke Ma, Yufei Mai, Phoebe Wang, Jesse Liu, and Jesse Fang.
"Secure encrypted virtualization is unsecure." arXiv preprint arXiv:1712.05090 (2017).
Gahi, Youssef, Mouhcine Guennoun, and Khalil El-Khatib. "A secure database system using
homomorphic encryption schemes." arXiv preprint arXiv:1512.03498 (2015).
He, Kun, Christophe Bidan, Gaëetan Le Guelvouit, and Cyrielle Feron. "Robust and secure
image encryption schemes during jpeg compression process." Electronic Imaging 2016, no. 11
(2016): 1-7.
Kaplan, David, Jeremy Powell, and Tom Woller. "AMD memory encryption." White paper
(2016).
Liang, Kaitai, Man Ho Au, Joseph K. Liu, Willy Susilo, Duncan S. Wong, Guomin Yang, Yong
Yu, and Anjia Yang. "A secure and efficient ciphertext-policy attribute-based proxy re-
encryption for cloud data sharing." Future Generation Computer Systems 52 (2015): 95-108.
Lin, Zhuosheng, Simin Yu, Jinhu Lü, Shuting Cai, and Guanrong Chen. "Design and ARM-
embedded implementation of a chaotic map-based real-time secure video communication
system." IEEE Transactions on Circuits and Systems for Video Technology 25, no. 7 (2015):
1203-1216.
Pancholi, Vishal R., and Bhadresh P. Patel. "Enhancement of cloud computing security with
secure data storage using AES." International Journal for Innovative Research in Science and
Technology 2, no. 9 (2016): 18-21.
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

10IMPLEMENTATION OF SECURE ENCRYPTION TECHNOLOGIES
Rachmawanto, Eko Hari, and Christy Atika Sari. "Secure Image Steganography Algorithm
Based on DCT with OTP Encryption." Journal of Applied Intelligent System 2, no. 1 (2017): 1-
11.
Rachmawanto, Eko Hari, and Christy Atika Sari. "Secure Image Steganography Algorithm
Based on DCT with OTP Encryption." Journal of Applied Intelligent System 2, no. 1 (2017): 1-
11.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





